IT Impact on Tesco's Business Operations: A Foundation Year Report
VerifiedAdded on 2023/06/13
|13
|3397
|243
Report
AI Summary
This report investigates the impact of information technology on Tesco's business operations, covering key aspects such as system software, ethical and social issues in the digital world, networking technologies, the role of artificial intelligence, and the software development life cycle. It examines the types of system software used, ethical considerations, networking technologies employed, and the importance of AI in improving Tesco's business operations. The report also assesses the stages of the software development life cycle relevant to Tesco. It concludes by emphasizing the need for businesses to protect themselves from unethical practices and to adopt preventive measures, highlighting the suitability of WAN for improved connectivity and the importance of efficient system software utilization and adherence to all SDLC stages for effective software development.

BABS Foundation Year IIT
Introduction to Information Technology Project
Impact of Information Technology on
business operations of a Tesco
BA in Business Studies(Foundation Year)
Word Count:
I declare that this project is all my own work and that I have acknowledged all materials used
from the published or unpublished works of other people. All references have been duly
cited.
1 | P a g e
Introduction to Information Technology Project
Impact of Information Technology on
business operations of a Tesco
BA in Business Studies(Foundation Year)
Word Count:
I declare that this project is all my own work and that I have acknowledged all materials used
from the published or unpublished works of other people. All references have been duly
cited.
1 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

BABS Foundation Year IIT
Abstract
This report has a brief description on importance of system software, importance of
ethical and social issues in digital world, define and distinct among all the types of
networking technologies, impact of AI in improving business operations, measure all stages
of software development life cycle. Also from this report it is analysed that the business
should be protected from the unethical practices taking place in the market and adopt some
preventive measures. They will be getting a better connectivity from WAN so this is suitable
for the company. The company is using appropriate technologies network for their use of
system software so they should improve their efficiency in utilization. It is considered for
them to follow all the stages appropriately for developing their software.
2 | P a g e
Abstract
This report has a brief description on importance of system software, importance of
ethical and social issues in digital world, define and distinct among all the types of
networking technologies, impact of AI in improving business operations, measure all stages
of software development life cycle. Also from this report it is analysed that the business
should be protected from the unethical practices taking place in the market and adopt some
preventive measures. They will be getting a better connectivity from WAN so this is suitable
for the company. The company is using appropriate technologies network for their use of
system software so they should improve their efficiency in utilization. It is considered for
them to follow all the stages appropriately for developing their software.
2 | P a g e

BABS Foundation Year IIT
Table of Contents
1.Introduction........................................................................................................................................4
2. Literature Review ..............................................................................................................................5
2.1 Different types of System Software in general............................................................................6
2.2 Ethics and Social Issues of using technology in general..............................................................7
2.3 Networking Technology, different types in general....................................................................7
2.4 The Artificial Intelligence and its importance in general.............................................................8
2.5 Software Development Life Cycle...............................................................................................9
3. Analysis and Discussion...................................................................................................................10
3.1 System software and its types used in the <selected business>...............................................10
3.2 Ethics and social issues in selected business.............................................................................10
3.3 Types of Networking Technologies that are used in the selected business .............................11
3.4 The importance of Artificial Intelligence in the selected business............................................11
4. Conclusions......................................................................................................................................12
5.References .......................................................................................................................................13
3 | P a g e
Table of Contents
1.Introduction........................................................................................................................................4
2. Literature Review ..............................................................................................................................5
2.1 Different types of System Software in general............................................................................6
2.2 Ethics and Social Issues of using technology in general..............................................................7
2.3 Networking Technology, different types in general....................................................................7
2.4 The Artificial Intelligence and its importance in general.............................................................8
2.5 Software Development Life Cycle...............................................................................................9
3. Analysis and Discussion...................................................................................................................10
3.1 System software and its types used in the <selected business>...............................................10
3.2 Ethics and social issues in selected business.............................................................................10
3.3 Types of Networking Technologies that are used in the selected business .............................11
3.4 The importance of Artificial Intelligence in the selected business............................................11
4. Conclusions......................................................................................................................................12
5.References .......................................................................................................................................13
3 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

BABS Foundation Year IIT
1.Introduction
Information technology is a study or it is the work on systems for extracting, storing,
sending and getting back the information. It is used in business for the purpose of
communicating, safeguarding, creating and administrating the information and their
databases (Bai and Liesch, 2022).This project has a purpose for researching on importance of
system software, importance of ethical and social issues in digital world, define and distinct
among all the types of networking technologies, impact of AI in improving business
operations, measure all stages of software development life cycle. This report is in reference
to a business that is Tesco, it is a retailing sector that serves groceries in their stores and
supermarkets. It was established since 1919 by Jack Cohen and its headquartered offices are
situated in Hackney, London, England.
4 | P a g e
1.Introduction
Information technology is a study or it is the work on systems for extracting, storing,
sending and getting back the information. It is used in business for the purpose of
communicating, safeguarding, creating and administrating the information and their
databases (Bai and Liesch, 2022).This project has a purpose for researching on importance of
system software, importance of ethical and social issues in digital world, define and distinct
among all the types of networking technologies, impact of AI in improving business
operations, measure all stages of software development life cycle. This report is in reference
to a business that is Tesco, it is a retailing sector that serves groceries in their stores and
supermarkets. It was established since 1919 by Jack Cohen and its headquartered offices are
situated in Hackney, London, England.
4 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

BABS Foundation Year IIT
2. Literature Review
As per the author, Mr. Peter Dahlin, the information technology helps employees to
troubleshoot their issues faced in computers and mobile devices. The research work done by
author ensures that information technology also helps them to do a range of other task to
make sure the capabilities and safety of the information related to business. It analyses the
particular data and helps the company to plan for the business's operations. It knows about
the trends and the updated knowledge that can be used in business. This report conveys about
the ways in which information technology impacts the businesses.
5 | P a g e
2. Literature Review
As per the author, Mr. Peter Dahlin, the information technology helps employees to
troubleshoot their issues faced in computers and mobile devices. The research work done by
author ensures that information technology also helps them to do a range of other task to
make sure the capabilities and safety of the information related to business. It analyses the
particular data and helps the company to plan for the business's operations. It knows about
the trends and the updated knowledge that can be used in business. This report conveys about
the ways in which information technology impacts the businesses.
5 | P a g e

BABS Foundation Year IIT
2.1 Different types of System Software in general
It refers to the computer program which is made to work the hardware devices and
software applications and programs. It integrates the work of hardware and applications for
an example operating system. There are different types of system software that are as follow -
Operating system – This is a category in systems that stays in the middle of
computer hardware and the person using it. Primarily it should be installed in the
computer to make the devices and applications recognize their work before starting it.
It is important as it is to be loaded in the memory of computer initially before the the
system powers itself, for example windows 10 and ubuntu.
Device driver – This category of system software which runs the computer hard
wares and peripherals. Their importance is to be directed by operating system to
perform the activities instructed to the devices and other additional components. They
are completely depended on the instructions of drivers. The businesses take many
operating systems that contain their drivers in it for the devices in marketplace. So
from the starting keyboard and mouse have the drivers installed in them or they could
require manual installations separately (Balamurugan and et. al., 2022). Examples of
drivers are mouse, printer, keyboard, display card and more.
Firmware – The work firm in IT means a fixed software. It is the operational
software that is designed and built as an integral part in the flash, ROM or EPROM
memory chip so that operational software can recognise. It is important as it functions
and controls all the tasks assigned to hardware and thus can do the work to generate
all information for a company. For example firmware devices are TV tuner, scanner,
monitor and etc.
Translator – These are the programs dependent on software programmers to convert
code from one computer language to another. The businesses have significance for the
system as it helps them in translating the text or speech from a language to other.
They interpret programming code as it translates the commands recognised and
processed by a computer (Borisova and et. al., 2022). For example some codes are
Java, C++, Python, PHP and etc.
6 | P a g e
2.1 Different types of System Software in general
It refers to the computer program which is made to work the hardware devices and
software applications and programs. It integrates the work of hardware and applications for
an example operating system. There are different types of system software that are as follow -
Operating system – This is a category in systems that stays in the middle of
computer hardware and the person using it. Primarily it should be installed in the
computer to make the devices and applications recognize their work before starting it.
It is important as it is to be loaded in the memory of computer initially before the the
system powers itself, for example windows 10 and ubuntu.
Device driver – This category of system software which runs the computer hard
wares and peripherals. Their importance is to be directed by operating system to
perform the activities instructed to the devices and other additional components. They
are completely depended on the instructions of drivers. The businesses take many
operating systems that contain their drivers in it for the devices in marketplace. So
from the starting keyboard and mouse have the drivers installed in them or they could
require manual installations separately (Balamurugan and et. al., 2022). Examples of
drivers are mouse, printer, keyboard, display card and more.
Firmware – The work firm in IT means a fixed software. It is the operational
software that is designed and built as an integral part in the flash, ROM or EPROM
memory chip so that operational software can recognise. It is important as it functions
and controls all the tasks assigned to hardware and thus can do the work to generate
all information for a company. For example firmware devices are TV tuner, scanner,
monitor and etc.
Translator – These are the programs dependent on software programmers to convert
code from one computer language to another. The businesses have significance for the
system as it helps them in translating the text or speech from a language to other.
They interpret programming code as it translates the commands recognised and
processed by a computer (Borisova and et. al., 2022). For example some codes are
Java, C++, Python, PHP and etc.
6 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

BABS Foundation Year IIT
2.2 Ethics and Social Issues of using technology in general
The businesses in current world have some ethical and social challenges so they need
to decide with making sure that they secure their personal freedoms and function the data in a
right manner. The ethical and social issues faced by business in technology are specified
further on -
Personal privacy – IT serves the users hard-wares, operational systems and software
applications that are relied on each other for work. The distributional network which
transfers the information on a large scale so there is a chance the information can be
leaked which violated the security of an individual or the businesses. This makes hard
for the organisations to maintain the privacy and integrity of information.
Access right – This is the prioritised matter for IT as per the increments in
advancements in technology. This is reflected in electronic payment systems of a
business software. Their networks also can't be secured in order to prevent
unauthorized access. They need to use the intrusion detection system which ensure the
either the user is unauthorized or the authorized person.
Education – In the practice of research and writing work, the businesses are taking
help from the internet and other sources that lead to plagiarism and consequently they
are becoming less creative. The employees are also lacking in their thought process.
They get their information ready made and served on the world wide web that
discourages them to make ideas from their own mind. Resultantly this disaffects the
society in terms of education.
Copyright – The information security specialists are aware about the copyright and
the related laws. This functions as a vital legal tool in securing the software from a
security breach before it happens as well as after it happens. This lead to the misuse of
data, programs, documentation and related things. The businesses are secured after
they register them in copyright legislation as in some nations it is necessary and it is
made of explicit laws, thus this secures the businesses (Chaker and et. al., 2022).
2.3 Networking Technology, different types in general
Basis LAN MAN WAN
Definition This is Local This is This is Wide Area
7 | P a g e
2.2 Ethics and Social Issues of using technology in general
The businesses in current world have some ethical and social challenges so they need
to decide with making sure that they secure their personal freedoms and function the data in a
right manner. The ethical and social issues faced by business in technology are specified
further on -
Personal privacy – IT serves the users hard-wares, operational systems and software
applications that are relied on each other for work. The distributional network which
transfers the information on a large scale so there is a chance the information can be
leaked which violated the security of an individual or the businesses. This makes hard
for the organisations to maintain the privacy and integrity of information.
Access right – This is the prioritised matter for IT as per the increments in
advancements in technology. This is reflected in electronic payment systems of a
business software. Their networks also can't be secured in order to prevent
unauthorized access. They need to use the intrusion detection system which ensure the
either the user is unauthorized or the authorized person.
Education – In the practice of research and writing work, the businesses are taking
help from the internet and other sources that lead to plagiarism and consequently they
are becoming less creative. The employees are also lacking in their thought process.
They get their information ready made and served on the world wide web that
discourages them to make ideas from their own mind. Resultantly this disaffects the
society in terms of education.
Copyright – The information security specialists are aware about the copyright and
the related laws. This functions as a vital legal tool in securing the software from a
security breach before it happens as well as after it happens. This lead to the misuse of
data, programs, documentation and related things. The businesses are secured after
they register them in copyright legislation as in some nations it is necessary and it is
made of explicit laws, thus this secures the businesses (Chaker and et. al., 2022).
2.3 Networking Technology, different types in general
Basis LAN MAN WAN
Definition This is Local This is This is Wide Area
7 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
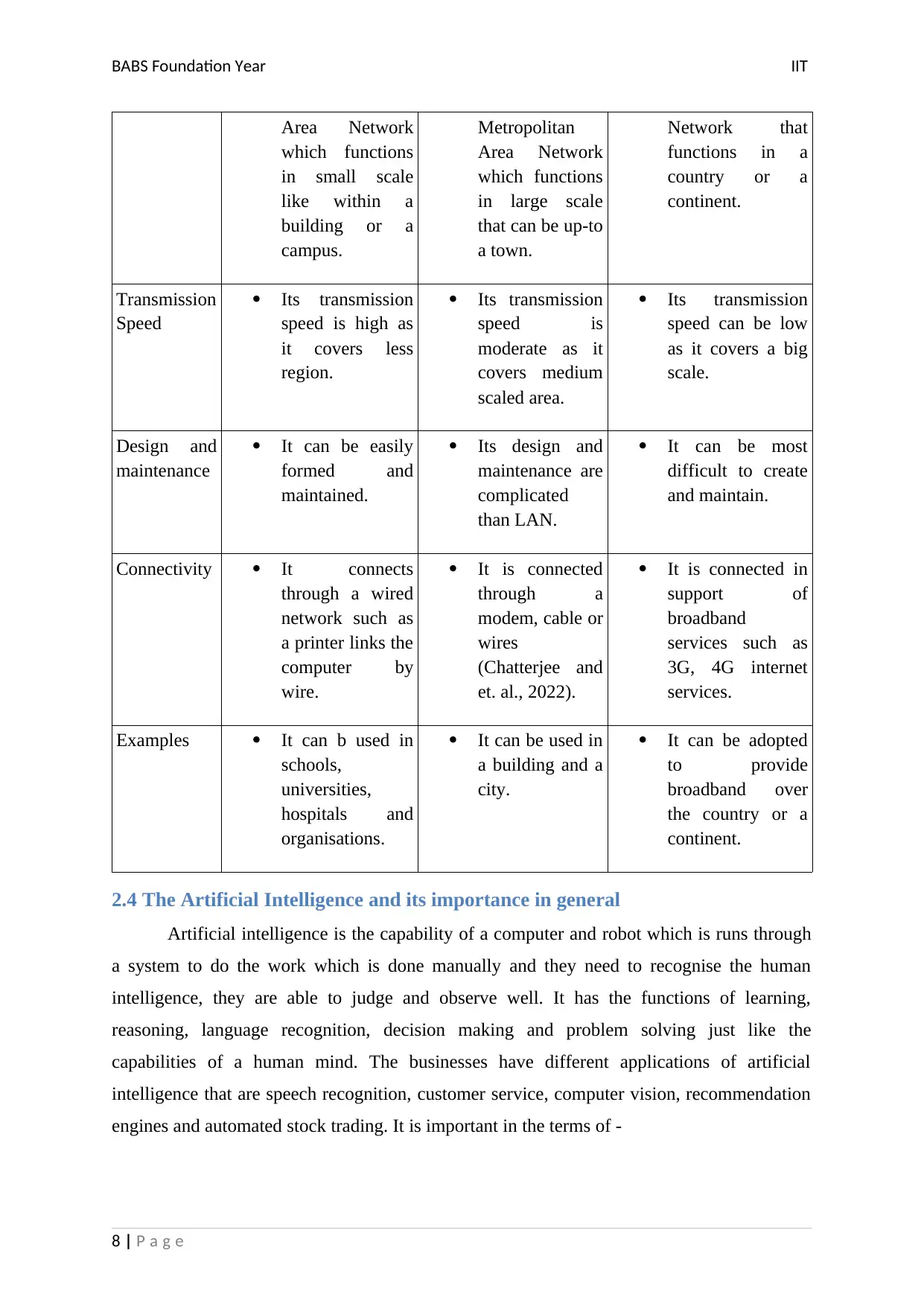
BABS Foundation Year IIT
Area Network
which functions
in small scale
like within a
building or a
campus.
Metropolitan
Area Network
which functions
in large scale
that can be up-to
a town.
Network that
functions in a
country or a
continent.
Transmission
Speed
Its transmission
speed is high as
it covers less
region.
Its transmission
speed is
moderate as it
covers medium
scaled area.
Its transmission
speed can be low
as it covers a big
scale.
Design and
maintenance
It can be easily
formed and
maintained.
Its design and
maintenance are
complicated
than LAN.
It can be most
difficult to create
and maintain.
Connectivity It connects
through a wired
network such as
a printer links the
computer by
wire.
It is connected
through a
modem, cable or
wires
(Chatterjee and
et. al., 2022).
It is connected in
support of
broadband
services such as
3G, 4G internet
services.
Examples It can b used in
schools,
universities,
hospitals and
organisations.
It can be used in
a building and a
city.
It can be adopted
to provide
broadband over
the country or a
continent.
2.4 The Artificial Intelligence and its importance in general
Artificial intelligence is the capability of a computer and robot which is runs through
a system to do the work which is done manually and they need to recognise the human
intelligence, they are able to judge and observe well. It has the functions of learning,
reasoning, language recognition, decision making and problem solving just like the
capabilities of a human mind. The businesses have different applications of artificial
intelligence that are speech recognition, customer service, computer vision, recommendation
engines and automated stock trading. It is important in the terms of -
8 | P a g e
Area Network
which functions
in small scale
like within a
building or a
campus.
Metropolitan
Area Network
which functions
in large scale
that can be up-to
a town.
Network that
functions in a
country or a
continent.
Transmission
Speed
Its transmission
speed is high as
it covers less
region.
Its transmission
speed is
moderate as it
covers medium
scaled area.
Its transmission
speed can be low
as it covers a big
scale.
Design and
maintenance
It can be easily
formed and
maintained.
Its design and
maintenance are
complicated
than LAN.
It can be most
difficult to create
and maintain.
Connectivity It connects
through a wired
network such as
a printer links the
computer by
wire.
It is connected
through a
modem, cable or
wires
(Chatterjee and
et. al., 2022).
It is connected in
support of
broadband
services such as
3G, 4G internet
services.
Examples It can b used in
schools,
universities,
hospitals and
organisations.
It can be used in
a building and a
city.
It can be adopted
to provide
broadband over
the country or a
continent.
2.4 The Artificial Intelligence and its importance in general
Artificial intelligence is the capability of a computer and robot which is runs through
a system to do the work which is done manually and they need to recognise the human
intelligence, they are able to judge and observe well. It has the functions of learning,
reasoning, language recognition, decision making and problem solving just like the
capabilities of a human mind. The businesses have different applications of artificial
intelligence that are speech recognition, customer service, computer vision, recommendation
engines and automated stock trading. It is important in the terms of -
8 | P a g e

BABS Foundation Year IIT
Saves time and money – The machines can do the work of working people more
efficiently. They can perform all the time without getting tired. The organisations
depends on them as they analyse big data in some seconds. They occupy less time,
cost and energy in decision making to serve a relevant and authenticate information.
Improves customer experience – They enhance customer experience by giving 24*7
customer care services as the computers nowadays have to interact in emails, online
communications and calls. They communicate with many customers over the world at
a time and reply them effectively for providing them their solutions.
Improves productivity – They decrease the tasks for employees so that they can
focus on what they are specialised. This results in boosting their productivity. If an
organisation has frequent communication with their clients so artificial intelligence
serves them a real time assistance (Khan and et. al., 2022).
2.5 Software Development Life Cycle
It is a process model that explains about the software development life cycle in a
diagrammatic and picture representation. There are various stages of SDLC which are as
follows -
Planning and requirement evaluation – In this initial stage the business analyst and
project organiser plans about the quality assurance needs and recognitions of risks
related to the project formation.
Knowing requirements – Then the document of software is showed to the
stakeholders so that they accept it after reviewing. Al, the product needs are made and
developed in the project life cycle.
Software designing – Then they need to know all the knowledge of needs, analysis
so as to design a software (Leirvik, 2022).
Developing project – This is a vital stage for developing and programming. The
developers have to write coding with the proper guidelines as mentioned by
management and programming tools.
Testing - Then there is a need to test the codes generated against the needs to ensure
the products to resolve the requirements known in requirement stage.
9 | P a g e
Saves time and money – The machines can do the work of working people more
efficiently. They can perform all the time without getting tired. The organisations
depends on them as they analyse big data in some seconds. They occupy less time,
cost and energy in decision making to serve a relevant and authenticate information.
Improves customer experience – They enhance customer experience by giving 24*7
customer care services as the computers nowadays have to interact in emails, online
communications and calls. They communicate with many customers over the world at
a time and reply them effectively for providing them their solutions.
Improves productivity – They decrease the tasks for employees so that they can
focus on what they are specialised. This results in boosting their productivity. If an
organisation has frequent communication with their clients so artificial intelligence
serves them a real time assistance (Khan and et. al., 2022).
2.5 Software Development Life Cycle
It is a process model that explains about the software development life cycle in a
diagrammatic and picture representation. There are various stages of SDLC which are as
follows -
Planning and requirement evaluation – In this initial stage the business analyst and
project organiser plans about the quality assurance needs and recognitions of risks
related to the project formation.
Knowing requirements – Then the document of software is showed to the
stakeholders so that they accept it after reviewing. Al, the product needs are made and
developed in the project life cycle.
Software designing – Then they need to know all the knowledge of needs, analysis
so as to design a software (Leirvik, 2022).
Developing project – This is a vital stage for developing and programming. The
developers have to write coding with the proper guidelines as mentioned by
management and programming tools.
Testing - Then there is a need to test the codes generated against the needs to ensure
the products to resolve the requirements known in requirement stage.
9 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

BABS Foundation Year IIT
Deployment – If the software becomes certified with no bugs, errors then it is to be
deployed. The the project is released with some recommendations and assessment of
the software.
Maintenance – At last the clients start utilising developed systems which leads to
some issues and resolving requirements at times. This is the stage of caring the ready
product.
3. Analysis and Discussion
3.1 System software and its types used in the <selected business>
The various categories of system software used in Tesco are defined below as follows -
Operating system – It is a group of software which maintains resources of Tesco and
serve them a general service for their applications (Lv and et. al., 2022). For example
Tesco operates on Microsoft Windows operational system software which is used in
every devices to manage the information of company in files and folders.
Device driver – It manages the hardware device that is connected to a computer,
Tesco adopts those drivers that are already installed in their devices such AS display
drivers, ROM drivers, USB drivers, printer drivers, etc. They help them to perform an
additional function in the system which is done by the exclusive device.
Firmware – It is not a temporary software and it is implanted inside the ROM(Read
Only Memory). It is a collection of commands stored ever lasting in the hardware. For
an instance, Tesco uses computer peripherals and embedded systems in their
company.
3.2 Ethics and social issues in selected business
The ethics and social issues faced by Tesco are explained in brief hereby -
Privacy – Tesco have some systems at their workplace that are computers, hardware,
software, operating systems to reach till the servers which are linked to each other and
the user through a network. As Tesco deals in a large scale distributional network so
they have trouble to share their private information without security.
10 | P a g e
Deployment – If the software becomes certified with no bugs, errors then it is to be
deployed. The the project is released with some recommendations and assessment of
the software.
Maintenance – At last the clients start utilising developed systems which leads to
some issues and resolving requirements at times. This is the stage of caring the ready
product.
3. Analysis and Discussion
3.1 System software and its types used in the <selected business>
The various categories of system software used in Tesco are defined below as follows -
Operating system – It is a group of software which maintains resources of Tesco and
serve them a general service for their applications (Lv and et. al., 2022). For example
Tesco operates on Microsoft Windows operational system software which is used in
every devices to manage the information of company in files and folders.
Device driver – It manages the hardware device that is connected to a computer,
Tesco adopts those drivers that are already installed in their devices such AS display
drivers, ROM drivers, USB drivers, printer drivers, etc. They help them to perform an
additional function in the system which is done by the exclusive device.
Firmware – It is not a temporary software and it is implanted inside the ROM(Read
Only Memory). It is a collection of commands stored ever lasting in the hardware. For
an instance, Tesco uses computer peripherals and embedded systems in their
company.
3.2 Ethics and social issues in selected business
The ethics and social issues faced by Tesco are explained in brief hereby -
Privacy – Tesco have some systems at their workplace that are computers, hardware,
software, operating systems to reach till the servers which are linked to each other and
the user through a network. As Tesco deals in a large scale distributional network so
they have trouble to share their private information without security.
10 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

BABS Foundation Year IIT
Access right – The company faces problems in the electronic payment systems and e-
commerce as there is an occurrence of frauds in payments (Simoni and et. al., 2022).
The networks of Tesco with internet are not safe at times in terms of unauthorised
access.
Piracy – There is a chance of someone in the market makes the illegal duplication of
the software made by the developers of Tesco. This is so common threat to the
company. There is a law based on the copyright protection as the company has
consideration to stop the unauthorised copy of software.
3.3 Types of Networking Technologies that are used in the selected business
Tesco has adopted various types of network technologies that are PAN, LAN, WAN,
VPN, SAN and many more. Some of the used networking technologies used in Tesco are
described further-
LAN – Tesco connects a group of computers in their working areas and low voltage
devices with each other in a short area. These networks can be used by the company
within a building or for a team so that the employees in the same team can
communicate and coordinate.
WAN – There is a need of WAN technology in Tesco for wireless connectivity such
as they use Wi-Fi. So they workers don't require any cables for connecting to the
network (Wall, 2022).
VPN – Tesco uses this network in case they want to extent their private network
across the internet. VPN enables their employees to transfer the data as their systems
are linked to a private network.
3.4 The importance of Artificial Intelligence in the selected business
Tesco gets advantage from artificial intelligence as this increases competency
and enhance their efficiency. They can get advance automated interactions with their clients,
customers partners and workers. They can multiply their revenue from the productivity as the
automating process makes the work of all the employees so easy. The importance of artificial
intelligence has been increasing the increase in technology and competition in the business
world. They test their products, use the transportation for delivering, surf in internet, maintain
the records of company in big data, communicate to clients / customers, do research and
development with the help of artificial intelligence (Wu, Liang and Chen, 2022).
11 | P a g e
Access right – The company faces problems in the electronic payment systems and e-
commerce as there is an occurrence of frauds in payments (Simoni and et. al., 2022).
The networks of Tesco with internet are not safe at times in terms of unauthorised
access.
Piracy – There is a chance of someone in the market makes the illegal duplication of
the software made by the developers of Tesco. This is so common threat to the
company. There is a law based on the copyright protection as the company has
consideration to stop the unauthorised copy of software.
3.3 Types of Networking Technologies that are used in the selected business
Tesco has adopted various types of network technologies that are PAN, LAN, WAN,
VPN, SAN and many more. Some of the used networking technologies used in Tesco are
described further-
LAN – Tesco connects a group of computers in their working areas and low voltage
devices with each other in a short area. These networks can be used by the company
within a building or for a team so that the employees in the same team can
communicate and coordinate.
WAN – There is a need of WAN technology in Tesco for wireless connectivity such
as they use Wi-Fi. So they workers don't require any cables for connecting to the
network (Wall, 2022).
VPN – Tesco uses this network in case they want to extent their private network
across the internet. VPN enables their employees to transfer the data as their systems
are linked to a private network.
3.4 The importance of Artificial Intelligence in the selected business
Tesco gets advantage from artificial intelligence as this increases competency
and enhance their efficiency. They can get advance automated interactions with their clients,
customers partners and workers. They can multiply their revenue from the productivity as the
automating process makes the work of all the employees so easy. The importance of artificial
intelligence has been increasing the increase in technology and competition in the business
world. They test their products, use the transportation for delivering, surf in internet, maintain
the records of company in big data, communicate to clients / customers, do research and
development with the help of artificial intelligence (Wu, Liang and Chen, 2022).
11 | P a g e

BABS Foundation Year IIT
4. Conclusions
This report about impact of information technology on business operations concludes
on the topics that are types of system software that were operating systems, drivers and so on.
The ethical and social issue for information technology were privacy, copyright and
education. There are differentiated networking technologies that concluded to opt the WAN
connection for the company. The effect of artificial intelligence were that the business can
increase efficiency, productivity and revenue. The seven stages of software were planning,
requirement analysis, designing, developing, testing, deployment and maintenance. These are
the stages used in the organisation to develop a software.
12 | P a g e
4. Conclusions
This report about impact of information technology on business operations concludes
on the topics that are types of system software that were operating systems, drivers and so on.
The ethical and social issue for information technology were privacy, copyright and
education. There are differentiated networking technologies that concluded to opt the WAN
connection for the company. The effect of artificial intelligence were that the business can
increase efficiency, productivity and revenue. The seven stages of software were planning,
requirement analysis, designing, developing, testing, deployment and maintenance. These are
the stages used in the organisation to develop a software.
12 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

