Challenges in Cyber Security Business of Thales Group: A Report
VerifiedAdded on 2020/02/24
|10
|1849
|81
Report
AI Summary
This report provides a comprehensive analysis of the cyber security challenges faced by the Thales Group, a prominent player in the Australian cyber security business. The study begins with an introduction that highlights the importance of cyber security and the specific challenges faced by the Thales Group. It includes a project objective to examine public awareness, investigate how Thales Group identifies and protects against threats, and find new methods to reduce cyber crimes. The report outlines the scope, literature review, research questions, and methodology, including research choices, strategies, and sampling methods. The core of the report presents a detailed analysis of challenges like data breaches, alert fatigue, and skill gaps, supported by a literature review and primary data collection through surveys. The research design employs quantitative data analysis using statistical tools like SPSS to identify relationships between cyber crimes and various factors. Ethical considerations are addressed to ensure the reliability and validity of the research. The report concludes with a discussion of the findings, limitations, and a time schedule for the research process, offering insights into the complexities of cyber security within the Thales Group and the broader implications for data protection and threat mitigation.

Running head: CHALLENGES IN CYBER SECURITY BUSINESS OF THALES GROUP
Challenges in Cyber Security Business of Thales Group
Name of the Student:
Name of the University:
Author’s Note:
Challenges in Cyber Security Business of Thales Group
Name of the Student:
Name of the University:
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CHALLENGES IN CYBER SECURITY BUSINESS OF THALES GROUP
Contents
Introduction......................................................................................................................................1
Project Objective.............................................................................................................................2
Project Scope...................................................................................................................................3
Literature Review............................................................................................................................3
Research Questions/Hypothesis.......................................................................................................4
Primary Question.........................................................................................................................4
Secondary Questions...................................................................................................................4
Research Design and Methodology.................................................................................................4
Research Choice..........................................................................................................................4
Research Strategy........................................................................................................................5
Sampling......................................................................................................................................5
Data Analysis...............................................................................................................................5
Ethical Considerations.................................................................................................................6
Research Limitations.......................................................................................................................6
Time Schedule.................................................................................................................................6
Conclusion.......................................................................................................................................7
Reference List..................................................................................................................................9
Contents
Introduction......................................................................................................................................1
Project Objective.............................................................................................................................2
Project Scope...................................................................................................................................3
Literature Review............................................................................................................................3
Research Questions/Hypothesis.......................................................................................................4
Primary Question.........................................................................................................................4
Secondary Questions...................................................................................................................4
Research Design and Methodology.................................................................................................4
Research Choice..........................................................................................................................4
Research Strategy........................................................................................................................5
Sampling......................................................................................................................................5
Data Analysis...............................................................................................................................5
Ethical Considerations.................................................................................................................6
Research Limitations.......................................................................................................................6
Time Schedule.................................................................................................................................6
Conclusion.......................................................................................................................................7
Reference List..................................................................................................................................9

2CHALLENGES IN CYBER SECURITY BUSINESS OF THALES GROUP
Introduction
Cyber security business is one of the leading business ventures of Australia. The
literature review which is carried out in the previous part has discussed the various challenges
which are being by the Thales Group in Australia. A critical literature review was carried out in
the entire paper. It is important for every organization to remove the challenges and thus identify
the important security gaps. Thales group has to work in collaboration with different
organizations and thus it has to overcome the various challenges in the operation of its business.
In the previous part, a close comparison and analysis of peer reviewed journals were done and it
was found that these cyber security businesses has identified the critical data and also provided
backup to the different fields which was affected by malware. The literature reviews also
depicted that these cyber security businesses has also helped to protect important government
data. The researcher who has worked in these topics has made a thorough and in-depth analysis
of the various problems which are faced by different organizations.
The research proposal will give a detailed analysis of the various challenges which are
faced by Thales Group. This proposal will also point out the important factors which will make
the study much easier and approachable. It will also give a detailed knowledge of Thales Group,
identify the challenges and provide substantial remedies to solve it. From the articles which were
analyzed in the literature review, it has been found that there are various challenges which are
faced by different cyber groups and it is a vital issue which needs to be understood because it
will help the Government as well as the other personnel in protecting important data.
Project Objective
To find a solution to the research question, the objectives mentioned has to be met:
Introduction
Cyber security business is one of the leading business ventures of Australia. The
literature review which is carried out in the previous part has discussed the various challenges
which are being by the Thales Group in Australia. A critical literature review was carried out in
the entire paper. It is important for every organization to remove the challenges and thus identify
the important security gaps. Thales group has to work in collaboration with different
organizations and thus it has to overcome the various challenges in the operation of its business.
In the previous part, a close comparison and analysis of peer reviewed journals were done and it
was found that these cyber security businesses has identified the critical data and also provided
backup to the different fields which was affected by malware. The literature reviews also
depicted that these cyber security businesses has also helped to protect important government
data. The researcher who has worked in these topics has made a thorough and in-depth analysis
of the various problems which are faced by different organizations.
The research proposal will give a detailed analysis of the various challenges which are
faced by Thales Group. This proposal will also point out the important factors which will make
the study much easier and approachable. It will also give a detailed knowledge of Thales Group,
identify the challenges and provide substantial remedies to solve it. From the articles which were
analyzed in the literature review, it has been found that there are various challenges which are
faced by different cyber groups and it is a vital issue which needs to be understood because it
will help the Government as well as the other personnel in protecting important data.
Project Objective
To find a solution to the research question, the objectives mentioned has to be met:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CHALLENGES IN CYBER SECURITY BUSINESS OF THALES GROUP
To examine the level of awareness among the general public regarding cyber
security crimes.
To investigate how Thales Group identifies the major crimes and also protects
important documents from malware and threats.
To find out new methods to reduce cyber security crimes.
Project Scope
This study will help to get a better insight in the business operation of cyber security
companies. It will help a researcher to get an idea how various cyber security crimes are
conducted and find out solutions to prevent it. It will also help a researcher in developing various
software which will help in reducing cyber security crimes.
Literature Review
Reddy and Reddy (2014) opined that privacy of data is an important issue which is to be
taken care by the organization. It is considered vital because there are various malicious software
which are destroying the database of the organizations and is also involved in hijacking
government reports and data. The web servers are engaged in protecting this important database
from malicious virus. Moreover, cloud computing is an important challenge of cyber security
personnel and various policy measure must be implemented so as to prevent the loss of data.
Baylon (2014) suggested that there are certain challenges which are to be faced by cyber
security personnel in military fields. The rapid use of dual technologies in the field of military is
trying to prevent the implementation of feasible and non-feasible technologies. Moreover,
penetration of a wide area network in the field of defence is considered important. The social
To examine the level of awareness among the general public regarding cyber
security crimes.
To investigate how Thales Group identifies the major crimes and also protects
important documents from malware and threats.
To find out new methods to reduce cyber security crimes.
Project Scope
This study will help to get a better insight in the business operation of cyber security
companies. It will help a researcher to get an idea how various cyber security crimes are
conducted and find out solutions to prevent it. It will also help a researcher in developing various
software which will help in reducing cyber security crimes.
Literature Review
Reddy and Reddy (2014) opined that privacy of data is an important issue which is to be
taken care by the organization. It is considered vital because there are various malicious software
which are destroying the database of the organizations and is also involved in hijacking
government reports and data. The web servers are engaged in protecting this important database
from malicious virus. Moreover, cloud computing is an important challenge of cyber security
personnel and various policy measure must be implemented so as to prevent the loss of data.
Baylon (2014) suggested that there are certain challenges which are to be faced by cyber
security personnel in military fields. The rapid use of dual technologies in the field of military is
trying to prevent the implementation of feasible and non-feasible technologies. Moreover,
penetration of a wide area network in the field of defence is considered important. The social
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CHALLENGES IN CYBER SECURITY BUSINESS OF THALES GROUP
networking sites are regarded as a weapon and threat in criticizing the government data. Thus,
identification of these threats is vital in launching various satellites and space assets.
Berg et al. (2014) have analyzed the various risks which are to be taken by the
management in cyber security business. The cyber actors in various domains must get exposure
while they are performing various cyber activities. The business organizations which are
involved in the cyber security must try to co-operate with the supply chain networks and various
actors globally. Identification of various kinds of risk is considered vital for these actors.
Ibrahim, Hamlyn-Harris and Grundy (2016) have tried to forecast the various challenges
in cloud computing system. It is challenging for the business organization to identify the zero
threats. These threats are increasing the complexities and destroying the creativity because it
becomes difficult predict and tarp the hackers. Thus, they have suggested certain techniques
which need to be focused on protecting the behavioral system.
Research Questions/Hypothesis
Primary Question
What are the challenges faced by Thales Group in its business operation such as breach
containment, alert fatigue and skill gap of the employees?
Secondary Questions
How to identify the critical data and provide backup to various fields which was
affected by malware?
How to assess the various fields where Cyber security programs are used by Thales
Group?
networking sites are regarded as a weapon and threat in criticizing the government data. Thus,
identification of these threats is vital in launching various satellites and space assets.
Berg et al. (2014) have analyzed the various risks which are to be taken by the
management in cyber security business. The cyber actors in various domains must get exposure
while they are performing various cyber activities. The business organizations which are
involved in the cyber security must try to co-operate with the supply chain networks and various
actors globally. Identification of various kinds of risk is considered vital for these actors.
Ibrahim, Hamlyn-Harris and Grundy (2016) have tried to forecast the various challenges
in cloud computing system. It is challenging for the business organization to identify the zero
threats. These threats are increasing the complexities and destroying the creativity because it
becomes difficult predict and tarp the hackers. Thus, they have suggested certain techniques
which need to be focused on protecting the behavioral system.
Research Questions/Hypothesis
Primary Question
What are the challenges faced by Thales Group in its business operation such as breach
containment, alert fatigue and skill gap of the employees?
Secondary Questions
How to identify the critical data and provide backup to various fields which was
affected by malware?
How to assess the various fields where Cyber security programs are used by Thales
Group?

5CHALLENGES IN CYBER SECURITY BUSINESS OF THALES GROUP
Research Design and Methodology
The methodology of a research discusses the underlying processes and methods followed
to meet the research objectives. The proposed research methodology has been stated below:
Research Choice
The research choice depicts the nature of data that will be used to meet the research
objectives and conduct the study. In this research, quantitative data will be used to find out the
challenges which are faced by Thales Group in its business operation. The choice of quantitative
data will help to find out how Thales Group provides backup to government data and also
protects critical data from threats and malware. Therefore, the choice of using quantitative data
over qualitative approach is suitable to meet the objectives of the research work (Bryman and
Bell 2015).
Research Strategy
The research strategy of a study involves the sources from where the data needs to be
gathered in order to meet the research objectives and to answer the research question. Based on
the nature on source, the research can be either primary or secondary in nature. For this study,
the primary data has been collected from Thales Group to identify the major challenges which
are faced by them through survey method. Thus, this methodology is suitable to meet the
research objectives. Moreover, some data were also collected from annual reports and journals of
Thales Group (Bryamn and Bell 2015).
Sampling
The process of sampling helps to select the participants from the target population. In this
case, the targeted sample is the Thales Group and the various cyber security experts who are
Research Design and Methodology
The methodology of a research discusses the underlying processes and methods followed
to meet the research objectives. The proposed research methodology has been stated below:
Research Choice
The research choice depicts the nature of data that will be used to meet the research
objectives and conduct the study. In this research, quantitative data will be used to find out the
challenges which are faced by Thales Group in its business operation. The choice of quantitative
data will help to find out how Thales Group provides backup to government data and also
protects critical data from threats and malware. Therefore, the choice of using quantitative data
over qualitative approach is suitable to meet the objectives of the research work (Bryman and
Bell 2015).
Research Strategy
The research strategy of a study involves the sources from where the data needs to be
gathered in order to meet the research objectives and to answer the research question. Based on
the nature on source, the research can be either primary or secondary in nature. For this study,
the primary data has been collected from Thales Group to identify the major challenges which
are faced by them through survey method. Thus, this methodology is suitable to meet the
research objectives. Moreover, some data were also collected from annual reports and journals of
Thales Group (Bryamn and Bell 2015).
Sampling
The process of sampling helps to select the participants from the target population. In this
case, the targeted sample is the Thales Group and the various cyber security experts who are
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CHALLENGES IN CYBER SECURITY BUSINESS OF THALES GROUP
engaged in securing the data (Bryman and Bell 2015). The data will be collected from 50
personnel’s through interviewing the cyber security experts of Thales Group in Australia. This
will be collected through random sampling and thus this will help to keep the sample as
homogenized as possible. It will also help to reduce the biasness of the research output.
Data Analysis
Data will be analyzed by using various statistical tools like SPSS via charts and graphs. It
will help to find out the relation between the dependent and the independent variable, which in
this case are cyber crimes, number of important data which are hacked, type of challenges which
are faced by Thales Group. The correlation conducted through regression and Pearson
correlation should help to meet the desired research objectives.
Ethical Considerations
Following an ethical approach to a study is essential in ensuring its reliability and
validity. This research work is based on ethical approach. It must be ensured that Thales group
must not be forced to give up the information. The purpose of data gathering will be fully
disclosed to them and they will also be given to quit the survey process whenever they want.
Moreover, it must also be ensured that the work is not plagiarized and the data gathered has not
been manipulated. Therefore, this will help to meet the research objectives (Bryman and Bell
2015).
Research Limitations
This research cannot give a proper idea of the various challenges which are faced by
Thales group because some important information cannot be disclosed to the researcher. This
research work is also expensive and time consuming. This type of research also requires careful
engaged in securing the data (Bryman and Bell 2015). The data will be collected from 50
personnel’s through interviewing the cyber security experts of Thales Group in Australia. This
will be collected through random sampling and thus this will help to keep the sample as
homogenized as possible. It will also help to reduce the biasness of the research output.
Data Analysis
Data will be analyzed by using various statistical tools like SPSS via charts and graphs. It
will help to find out the relation between the dependent and the independent variable, which in
this case are cyber crimes, number of important data which are hacked, type of challenges which
are faced by Thales Group. The correlation conducted through regression and Pearson
correlation should help to meet the desired research objectives.
Ethical Considerations
Following an ethical approach to a study is essential in ensuring its reliability and
validity. This research work is based on ethical approach. It must be ensured that Thales group
must not be forced to give up the information. The purpose of data gathering will be fully
disclosed to them and they will also be given to quit the survey process whenever they want.
Moreover, it must also be ensured that the work is not plagiarized and the data gathered has not
been manipulated. Therefore, this will help to meet the research objectives (Bryman and Bell
2015).
Research Limitations
This research cannot give a proper idea of the various challenges which are faced by
Thales group because some important information cannot be disclosed to the researcher. This
research work is also expensive and time consuming. This type of research also requires careful
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7CHALLENGES IN CYBER SECURITY BUSINESS OF THALES GROUP
planning and knowledge about conducting the research. Moreover, there may also be certain
problems in data analysis and it will be difficult for the researchers who are from non-statistical
background.
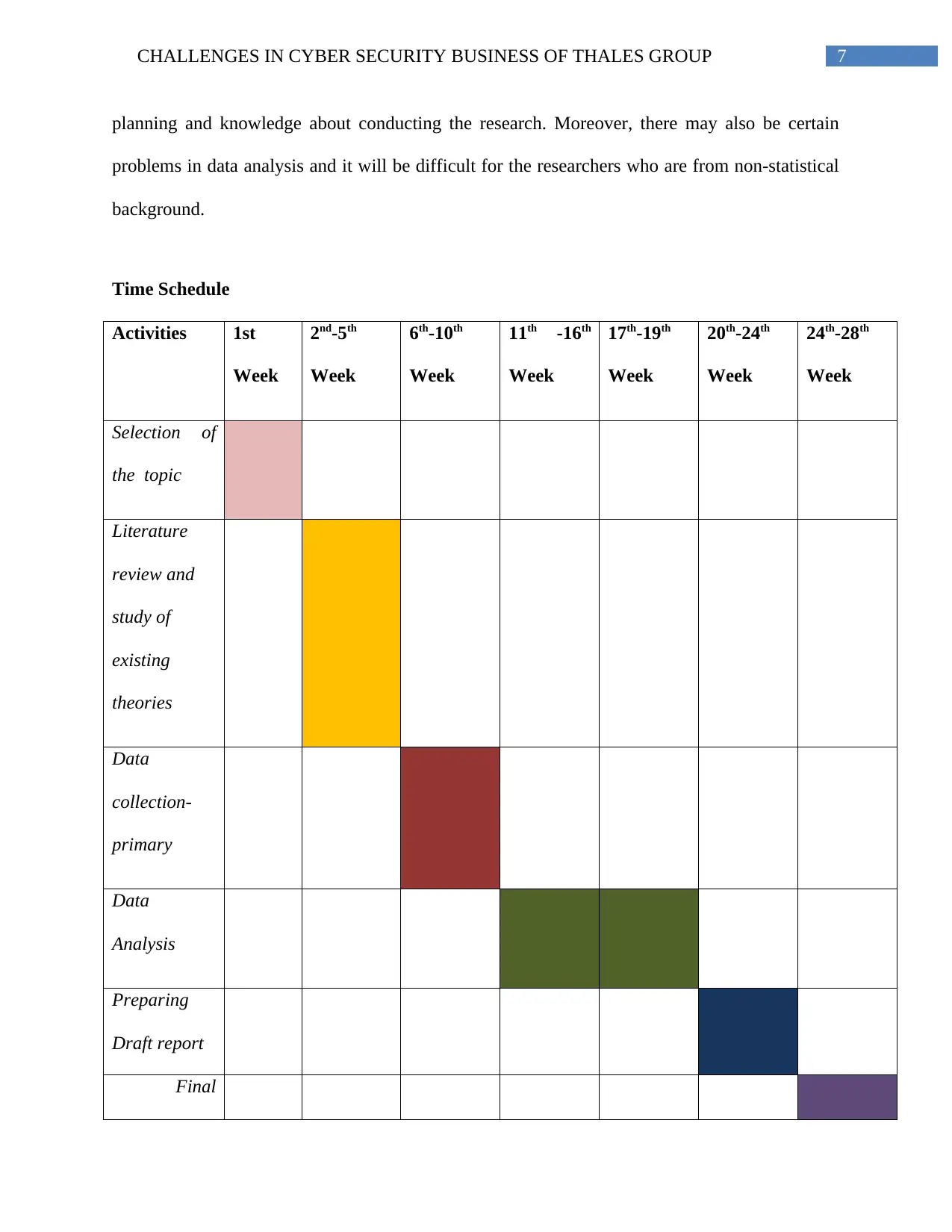
Time Schedule
Activities 1st
Week
2nd-5th
Week
6th-10th
Week
11th -16th
Week
17th-19th
Week
20th-24th
Week
24th-28th
Week
Selection of
the topic
Literature
review and
study of
existing
theories
Data
collection-
primary
Data
Analysis
Preparing
Draft report
Final
planning and knowledge about conducting the research. Moreover, there may also be certain
problems in data analysis and it will be difficult for the researchers who are from non-statistical
background.
Time Schedule
Activities 1st
Week
2nd-5th
Week
6th-10th
Week
11th -16th
Week
17th-19th
Week
20th-24th
Week
24th-28th
Week
Selection of
the topic
Literature
review and
study of
existing
theories
Data
collection-
primary
Data
Analysis
Preparing
Draft report
Final
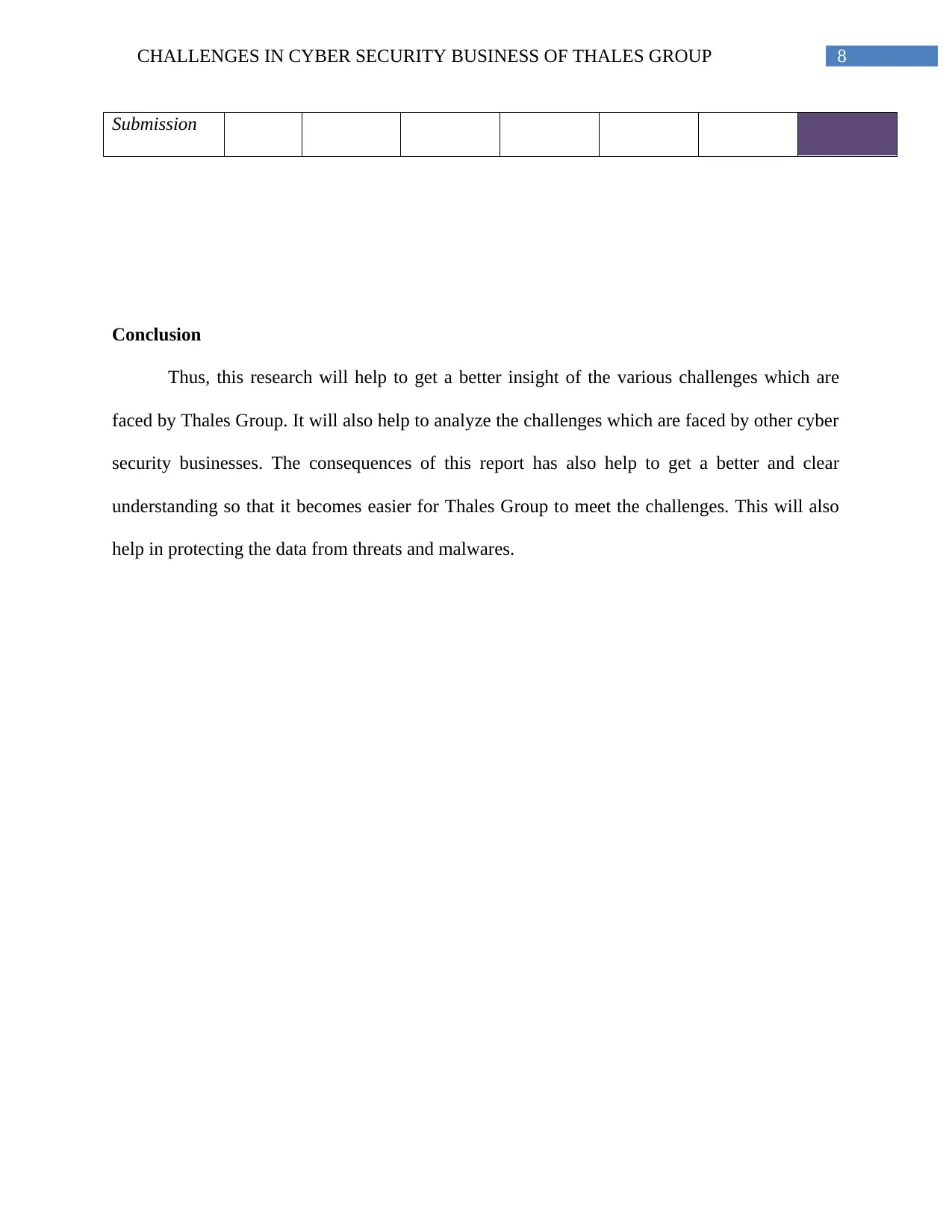
8CHALLENGES IN CYBER SECURITY BUSINESS OF THALES GROUP
Submission
Conclusion
Thus, this research will help to get a better insight of the various challenges which are
faced by Thales Group. It will also help to analyze the challenges which are faced by other cyber
security businesses. The consequences of this report has also help to get a better and clear
understanding so that it becomes easier for Thales Group to meet the challenges. This will also
help in protecting the data from threats and malwares.
Submission
Conclusion
Thus, this research will help to get a better insight of the various challenges which are
faced by Thales Group. It will also help to analyze the challenges which are faced by other cyber
security businesses. The consequences of this report has also help to get a better and clear
understanding so that it becomes easier for Thales Group to meet the challenges. This will also
help in protecting the data from threats and malwares.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CHALLENGES IN CYBER SECURITY BUSINESS OF THALES GROUP
Reference List
Baylon, C., 2014. Challenges at the Intersection of Cyber Security and Space
Security. International Security.
Bryman, A. and Bell, E., 2015. Business research methods. New York: Oxford University Press.
Ibrahim, A.S., Hamlyn-Harris, J. and Grundy, J., 2016. Emerging security challenges of cloud
virtual infrastructure. arXiv preprint arXiv:1612.09059.
Reddy, G.N. and Reddy, G.J., 2014. A Study of Cyber Security Challenges and its emerging
trends on latest technologies. arXiv preprint arXiv:1402.1842.
Van den Berg, J., Van Zoggel, J., Snels, M., Van Leeuwen, M., Boeke, S., van de Koppen, L.,
Van der Lubbe, J., Van den Berg, B. and De Bos, T., 2014. On (the Emergence of) Cyber
Security Science and its Challenges for Cyber Security Education. In Proceedings of the NATO
IST-122 Cyber Security Science and Engineering Symposium (pp. 13-14)
Reference List
Baylon, C., 2014. Challenges at the Intersection of Cyber Security and Space
Security. International Security.
Bryman, A. and Bell, E., 2015. Business research methods. New York: Oxford University Press.
Ibrahim, A.S., Hamlyn-Harris, J. and Grundy, J., 2016. Emerging security challenges of cloud
virtual infrastructure. arXiv preprint arXiv:1612.09059.
Reddy, G.N. and Reddy, G.J., 2014. A Study of Cyber Security Challenges and its emerging
trends on latest technologies. arXiv preprint arXiv:1402.1842.
Van den Berg, J., Van Zoggel, J., Snels, M., Van Leeuwen, M., Boeke, S., van de Koppen, L.,
Van der Lubbe, J., Van den Berg, B. and De Bos, T., 2014. On (the Emergence of) Cyber
Security Science and its Challenges for Cyber Security Education. In Proceedings of the NATO
IST-122 Cyber Security Science and Engineering Symposium (pp. 13-14)
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





