MITS5004 IT Security Assignment: Threats, Attacks, and Malware Review
VerifiedAdded on 2022/10/05
|12
|1198
|192
Presentation
AI Summary
This presentation reviews the academic article "Cyber Security and the Internet of Things: Vulnerabilities, Threats, Intruders and Attacks" by Mohamed Abomhara and Geir M. Køien. The presentation explores the vulnerabilities, threats, and various types of attacks, including physical, reconnaissance, and denial-of-service attacks. It categorizes threats as natural and human-caused, and classifies intruders. The presentation also addresses malware used by different groups. The article emphasizes the importance of robust security for IoT devices and the increasing complexity of threats. It highlights various types of attacks, including access attacks, attacks on privacy, cybercrimes, and destructive attacks, while also discussing the threats to SCADA systems. The presentation concludes by summarizing the key findings and suggesting ways to deal with the issues. The presentation uses references to support its claims and findings.

Threats, Attacks and
Malware
Presented By: (Add Names)
Malware
Presented By: (Add Names)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTRODUCTION
The aim of this presentation is to do provide a
review about recent academic articles on IT security.
To help with the review, the article chosen is titled,
“Cyber Security and the Internet of Things:
Vulnerabilities, Threats, Intruders and Attacks,”
authored by Mohamed Abomhara and Geir M. Køien
[1]
This is to help in reviewing issues facing IT security
and specifically in Threats, Attacks and Malware.
The aim of this presentation is to do provide a
review about recent academic articles on IT security.
To help with the review, the article chosen is titled,
“Cyber Security and the Internet of Things:
Vulnerabilities, Threats, Intruders and Attacks,”
authored by Mohamed Abomhara and Geir M. Køien
[1]
This is to help in reviewing issues facing IT security
and specifically in Threats, Attacks and Malware.

Intention and Content of The Article
The intention of the article is to classify the security threats and
attacks facing IT industry and specifically in the field of IoT.
IoT has been named as the fasted growing technology and has
permeated in almost all sectors of people’s life nowadays [2].
This calls for a robust security that will adequately secure the big
number of devices and services that are connected to the internet all
over the word.
However, the number of threats and their complexity keeps on
increasing every day
The intention of the article is to classify the security threats and
attacks facing IT industry and specifically in the field of IoT.
IoT has been named as the fasted growing technology and has
permeated in almost all sectors of people’s life nowadays [2].
This calls for a robust security that will adequately secure the big
number of devices and services that are connected to the internet all
over the word.
However, the number of threats and their complexity keeps on
increasing every day
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Vulnerabilities
They can be defined as weakness within as system that gives room to
an intruder to carry out his/malicious intentions [3]. For example, IoT
vulnerabilities can be found in the software, hardware, policies or the
users of the devices.
Exposure
A mistake or a problem in the configuration of a system that enables
an attacker to conduct information gathering tasks is referred to as
exposure.
They can be defined as weakness within as system that gives room to
an intruder to carry out his/malicious intentions [3]. For example, IoT
vulnerabilities can be found in the software, hardware, policies or the
users of the devices.
Exposure
A mistake or a problem in the configuration of a system that enables
an attacker to conduct information gathering tasks is referred to as
exposure.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Threats
A threat can be defined as an action that takes a result of the
perpetrator identifying a weakness a security weakness in the
target system and leaves a negative impact on the system [4].
They are divided into the following categories; categories;
natural and human threats [5].
Natural threats are those that occur without human intervention
such as earthquakes, floods, hurricanes and lightning
Human threats are the ones that originate from people (either
accidentally or intentionally) for malicious purposes.
A threat can be defined as an action that takes a result of the
perpetrator identifying a weakness a security weakness in the
target system and leaves a negative impact on the system [4].
They are divided into the following categories; categories;
natural and human threats [5].
Natural threats are those that occur without human intervention
such as earthquakes, floods, hurricanes and lightning
Human threats are the ones that originate from people (either
accidentally or intentionally) for malicious purposes.

Attacks
Refers to actions that are taken with the aim of causing harm to a
system or causing a disruption in the usual operations by means of
exploitation of vulnerabilities that exist in the system with the help of
various tools and techniques.
Refers to actions that are taken with the aim of causing harm to a
system or causing a disruption in the usual operations by means of
exploitation of vulnerabilities that exist in the system with the help of
various tools and techniques.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Types Of Attacks
Physical attacks
These are the attacks that interfere with the hardware parts of the
system
Reconnaissance attacks
Refers to when attackers use their tools and techniques to illegally
discover and map services, systems and vulnerabilities. It includes;
ports scanning [7], traffic analysis, packet sniffing [6], and pinging IPs.
Denial-of-service (DoS)
This attack has the aim of making a network resource or machine to be
unavailable to the intended users
Access attacks
It occurs when people who are not authorized to access a particular
network or device manage to gain access illegally.
Physical attacks
These are the attacks that interfere with the hardware parts of the
system
Reconnaissance attacks
Refers to when attackers use their tools and techniques to illegally
discover and map services, systems and vulnerabilities. It includes;
ports scanning [7], traffic analysis, packet sniffing [6], and pinging IPs.
Denial-of-service (DoS)
This attack has the aim of making a network resource or machine to be
unavailable to the intended users
Access attacks
It occurs when people who are not authorized to access a particular
network or device manage to gain access illegally.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
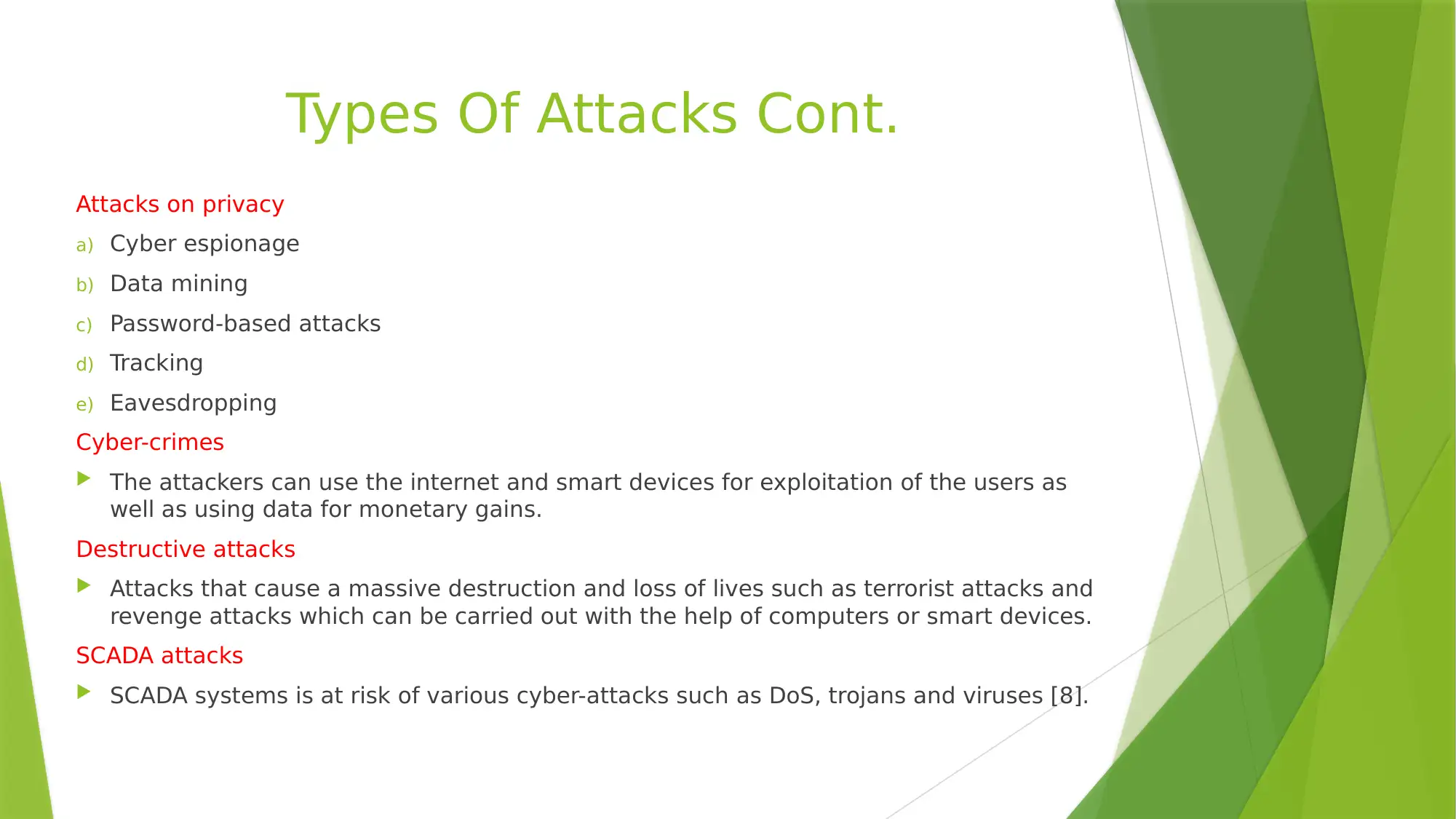
Types Of Attacks Cont.
Attacks on privacy
a) Cyber espionage
b) Data mining
c) Password-based attacks
d) Tracking
e) Eavesdropping
Cyber-crimes
The attackers can use the internet and smart devices for exploitation of the users as
well as using data for monetary gains.
Destructive attacks
Attacks that cause a massive destruction and loss of lives such as terrorist attacks and
revenge attacks which can be carried out with the help of computers or smart devices.
SCADA attacks
SCADA systems is at risk of various cyber-attacks such as DoS, trojans and viruses [8].
Attacks on privacy
a) Cyber espionage
b) Data mining
c) Password-based attacks
d) Tracking
e) Eavesdropping
Cyber-crimes
The attackers can use the internet and smart devices for exploitation of the users as
well as using data for monetary gains.
Destructive attacks
Attacks that cause a massive destruction and loss of lives such as terrorist attacks and
revenge attacks which can be carried out with the help of computers or smart devices.
SCADA attacks
SCADA systems is at risk of various cyber-attacks such as DoS, trojans and viruses [8].

Classification of Possible Intruders & Types of Malware Used
Individuals
Refers to professional hackers who operate alone and their main targets
are the less secure systems [9].
They use various tools like worms, viruses and sniffers to perform
exploitation of a system
Organized groups
These are a group of hackers that unite with various motivation and
targets.
They use numerous types of malware and tools such as botnets, DoS,
malicious software like viruses and scareware [10].
Intelligence agency
Conducted by intelligence agencies sponsored by governments and use
advanced tools
Individuals
Refers to professional hackers who operate alone and their main targets
are the less secure systems [9].
They use various tools like worms, viruses and sniffers to perform
exploitation of a system
Organized groups
These are a group of hackers that unite with various motivation and
targets.
They use numerous types of malware and tools such as botnets, DoS,
malicious software like viruses and scareware [10].
Intelligence agency
Conducted by intelligence agencies sponsored by governments and use
advanced tools
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Conclusion
This presentation has managed to do a review of the article and
explained the threats and attacks and suggested some ways of
dealing with some of the issues.
It has highlighted the various malware that the attackers use to
perpetrate their attacks depending on their targets.
Although the article under review was based in IoT, it has given an
overview of the problems that are facing the other sectors of IT since
most of them are connected to the internet and are at susceptible to
those problems too.
This presentation has managed to do a review of the article and
explained the threats and attacks and suggested some ways of
dealing with some of the issues.
It has highlighted the various malware that the attackers use to
perpetrate their attacks depending on their targets.
Although the article under review was based in IoT, it has given an
overview of the problems that are facing the other sectors of IT since
most of them are connected to the internet and are at susceptible to
those problems too.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
[1] M. Abomhara and G. Kø ien, "Cyber Security and the Internet of Things:
Vulnerabilities, Threats, Intruders and Attacks", Journal of Cyber Security and
Mobility, vol. 4, no. 1, pp. 65-88, 2015. Available: 10.13052/jcsm2245-1439.414.
[2] "Internet of Things, Smart Spaces, and Next Generation Networks and
Systems", Lecture Notes in Computer Science, p. 464, 2018. Available:
10.1007/978-3-030-01168-0
[3] E. Bertino, L. Martino, F. Paci and A. Squicciarini, Security for Web Services
and Service-Oriented Architectures. Berlin, Heidelberg: Springer-Verlag Berlin
Heidelberg, 2010, pp. 25-44.
[4] H. Brauch, Coping with global environmental change, disasters and security.
Berlin: Springer, 2011, pp. 61-106.
[5] K. Dahbur, B. Mohammad and A. Tarakji, "A survey of risks, threats and
vulnerabilities in cloud computing", Proceedings of the 2011 International
Conference on Intelligent Semantic Web-Services and Applications - ISWSA '11,
p. 12, 2011. Available: 10.1145/1980822.1980834
[1] M. Abomhara and G. Kø ien, "Cyber Security and the Internet of Things:
Vulnerabilities, Threats, Intruders and Attacks", Journal of Cyber Security and
Mobility, vol. 4, no. 1, pp. 65-88, 2015. Available: 10.13052/jcsm2245-1439.414.
[2] "Internet of Things, Smart Spaces, and Next Generation Networks and
Systems", Lecture Notes in Computer Science, p. 464, 2018. Available:
10.1007/978-3-030-01168-0
[3] E. Bertino, L. Martino, F. Paci and A. Squicciarini, Security for Web Services
and Service-Oriented Architectures. Berlin, Heidelberg: Springer-Verlag Berlin
Heidelberg, 2010, pp. 25-44.
[4] H. Brauch, Coping with global environmental change, disasters and security.
Berlin: Springer, 2011, pp. 61-106.
[5] K. Dahbur, B. Mohammad and A. Tarakji, "A survey of risks, threats and
vulnerabilities in cloud computing", Proceedings of the 2011 International
Conference on Intelligent Semantic Web-Services and Applications - ISWSA '11,
p. 12, 2011. Available: 10.1145/1980822.1980834
References
[6] S. Ansari, S. Rajeev and H. Chandrashekar, "Packet sniffing: a brief
introduction", IEEE Potentials, vol. 21, no. 5, pp. 17-19, 2002. Available:
10.1109/mp.2002.1166620
[7] M. de Vivo, E. Carrasco, G. Isern and G. de Vivo, "A review of port scanning
techniques", ACM SIGCOMM Computer Communication Review, vol. 29, no. 2, p. 41,
1999.
[8] A. Daneels and W. Salter, “What is scada,” in International Conference on
Accelerator and Large Experimental Physics Control Systems, 1999, pp. 339–343.
[9] J. Sheldon, “State of the art: Attackers and targets in cyberspace,” Journal of
Military and Strategic Studies, vol. 14, no. 2, 2012.
[10] A. Nicholson, S. Webber, S. Dyer, T. Patel, and H. Janicke, “Scada security in the
light of cyber-warfare,” Computers & Security, vol. 31, no. 4, pp. 418–436, 2012.
[6] S. Ansari, S. Rajeev and H. Chandrashekar, "Packet sniffing: a brief
introduction", IEEE Potentials, vol. 21, no. 5, pp. 17-19, 2002. Available:
10.1109/mp.2002.1166620
[7] M. de Vivo, E. Carrasco, G. Isern and G. de Vivo, "A review of port scanning
techniques", ACM SIGCOMM Computer Communication Review, vol. 29, no. 2, p. 41,
1999.
[8] A. Daneels and W. Salter, “What is scada,” in International Conference on
Accelerator and Large Experimental Physics Control Systems, 1999, pp. 339–343.
[9] J. Sheldon, “State of the art: Attackers and targets in cyberspace,” Journal of
Military and Strategic Studies, vol. 14, no. 2, 2012.
[10] A. Nicholson, S. Webber, S. Dyer, T. Patel, and H. Janicke, “Scada security in the
light of cyber-warfare,” Computers & Security, vol. 31, no. 4, pp. 418–436, 2012.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





