TNE80006 - Securing Linux Server and Network: A Project for Swinburne
VerifiedAdded on 2023/06/11
|15
|2540
|454
Project
AI Summary
This project report details the implementation of security measures for a Linux-based web server, addressing vulnerabilities and potential threats. The report covers network design, incorporating firewalls and proxy servers to create a Demilitarized Zone (DMZ). It discusses ModSecurity, a web application firewall, and its role in preventing SQL injection and cross-site scripting (XSS) attacks. The report identifies threats towards the Apache web server, including fire starter utilization, inside attacker GUI attacks, unwanted port liabilities, and secure shell access liabilities. Mitigation strategies, such as IP tables and TCP SYN flood protection, are also explored. Finally, the report outlines firewall and IPS/IDS policies to secure the network, providing a comprehensive overview of the implemented security solutions. Desklib provides more solved assignments for students.

Table of Contents
1. Introduction.............................................................................................................................................2
2. Network design........................................................................................................................................2
3. Modsecurity.............................................................................................................................................3
4. Mod Security against SQL injection.........................................................................................................3
5. Mod Security against Cross Site Scripting................................................................................................4
6. Threats towards the apache web servers................................................................................................4
7. Threads towards the network.................................................................................................................9
8. Firewall polices and IPS/IDS policies......................................................................................................12
9. Conclusion.............................................................................................................................................13
References............................................................................................................................................14
1
1. Introduction.............................................................................................................................................2
2. Network design........................................................................................................................................2
3. Modsecurity.............................................................................................................................................3
4. Mod Security against SQL injection.........................................................................................................3
5. Mod Security against Cross Site Scripting................................................................................................4
6. Threats towards the apache web servers................................................................................................4
7. Threads towards the network.................................................................................................................9
8. Firewall polices and IPS/IDS policies......................................................................................................12
9. Conclusion.............................................................................................................................................13
References............................................................................................................................................14
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. Introduction
In the modern internet, all the business is going toward the smart business. For achieving
that company uses the internet services. In this assignment a company they are market leaders in
textile business. They have very famous brand name “WEAR IT ON”. They also are plans to
implement the web server on the company for improving their business. They already have the
Apache-2.0 with Linux based server operating system. They appoint the trainee for manage the
network administration purpose. But the trainee doesn’t have the great understanding of the project.
During the general inspection they found that there was a flaw in the network systems. Someone
tried to perform the TCP scan on the server for attack the network system. This problem was
occurred when the server was connected with internet. The report contains the details about the
process involved in the network system implementation in this company. Here the main objective
was to find out the different kind of flaws in the network systems .The required anti attack actions
are also discussed in the report.
2. Network design
During the development of the web based servers by the company the main problem was it can be
accessed by the attacker. So it may be misused by the attackers. So the network design that must
provide the security for the server that acts as the companies’ web server. On the network there are
many antivirus servers are available. They are used to provide the security for the servers. The
routers installed in the company were acts as the default gate way for the internet. Here the entry as
well as exit point was called as the gate way. So all the data come into server and also send to other
devices by the server uses the gateway.
So we need to improve the security by providing the firewalls to servers. Here the server was placed
between the two firewalls. They are known as internal firewall as well as external firewall. They
2
In the modern internet, all the business is going toward the smart business. For achieving
that company uses the internet services. In this assignment a company they are market leaders in
textile business. They have very famous brand name “WEAR IT ON”. They also are plans to
implement the web server on the company for improving their business. They already have the
Apache-2.0 with Linux based server operating system. They appoint the trainee for manage the
network administration purpose. But the trainee doesn’t have the great understanding of the project.
During the general inspection they found that there was a flaw in the network systems. Someone
tried to perform the TCP scan on the server for attack the network system. This problem was
occurred when the server was connected with internet. The report contains the details about the
process involved in the network system implementation in this company. Here the main objective
was to find out the different kind of flaws in the network systems .The required anti attack actions
are also discussed in the report.
2. Network design
During the development of the web based servers by the company the main problem was it can be
accessed by the attacker. So it may be misused by the attackers. So the network design that must
provide the security for the server that acts as the companies’ web server. On the network there are
many antivirus servers are available. They are used to provide the security for the servers. The
routers installed in the company were acts as the default gate way for the internet. Here the entry as
well as exit point was called as the gate way. So all the data come into server and also send to other
devices by the server uses the gateway.
So we need to improve the security by providing the firewalls to servers. Here the server was placed
between the two firewalls. They are known as internal firewall as well as external firewall. They
2

give protection against internal attacks as well as external attacks. This process was known as the
Demilitarized zone. Also the proxy servers are implemented to control the public access. These are
the security measures they are planned for implement in the company network system.
3. Modsecurity
Its name describes about the function of this firewall. This is the commonly used web based
firewall application by the development of the security in the servers. It has the open source access
which means any one can make the changes in the software based on their purpose of use. When it’s
starting period they are mostly used to with HTTP service for providing the security to the data. But
it was implemented as the full security purpose. There are some other tools are also used for the
same purpose. And they are NGINX & IIS. But this software has the capability to handle the large
no of groups because it was open source access. For that tool there are huge no of rules as well as
policies are made. And also they are verified. They are known as “Sec Rules”. This software used in
the web server as the additional application. For some requirements they act similar to the proxy
servers. Here we would see about the various actions which are performed by this application was
listed below. And they are,
• Monitor the security of the server
• Provides access control to the users
• to log into the HTTP services
• Perform the security checking periodically
• Acts as the both Active security assessment as well as passive security assessment
• to do security auditing works
• Limit the memory consumed during the data downloading as well as uploading
• Create the server identification mask
4. Mod Security against SQL injection
It is easy to prevent the code. Mod security of the response in the access of the body it is
simply adding the rules for opening the tag of PHP.
The Perl and JSP code has prevent the work in a common manner.
3
Demilitarized zone. Also the proxy servers are implemented to control the public access. These are
the security measures they are planned for implement in the company network system.
3. Modsecurity
Its name describes about the function of this firewall. This is the commonly used web based
firewall application by the development of the security in the servers. It has the open source access
which means any one can make the changes in the software based on their purpose of use. When it’s
starting period they are mostly used to with HTTP service for providing the security to the data. But
it was implemented as the full security purpose. There are some other tools are also used for the
same purpose. And they are NGINX & IIS. But this software has the capability to handle the large
no of groups because it was open source access. For that tool there are huge no of rules as well as
policies are made. And also they are verified. They are known as “Sec Rules”. This software used in
the web server as the additional application. For some requirements they act similar to the proxy
servers. Here we would see about the various actions which are performed by this application was
listed below. And they are,
• Monitor the security of the server
• Provides access control to the users
• to log into the HTTP services
• Perform the security checking periodically
• Acts as the both Active security assessment as well as passive security assessment
• to do security auditing works
• Limit the memory consumed during the data downloading as well as uploading
• Create the server identification mask
4. Mod Security against SQL injection
It is easy to prevent the code. Mod security of the response in the access of the body it is
simply adding the rules for opening the tag of PHP.
The Perl and JSP code has prevent the work in a common manner.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
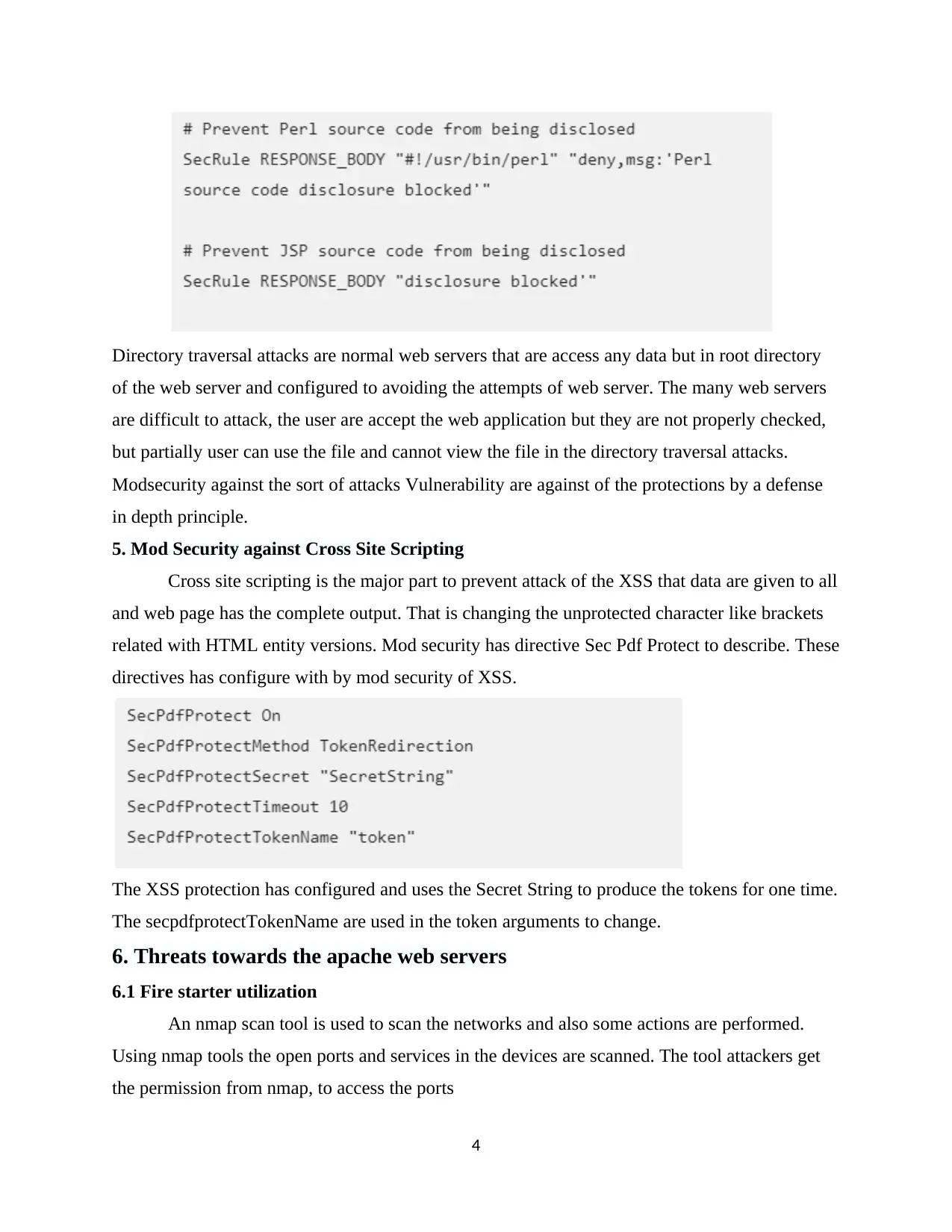
Directory traversal attacks are normal web servers that are access any data but in root directory
of the web server and configured to avoiding the attempts of web server. The many web servers
are difficult to attack, the user are accept the web application but they are not properly checked,
but partially user can use the file and cannot view the file in the directory traversal attacks.
Modsecurity against the sort of attacks Vulnerability are against of the protections by a defense
in depth principle.
5. Mod Security against Cross Site Scripting
Cross site scripting is the major part to prevent attack of the XSS that data are given to all
and web page has the complete output. That is changing the unprotected character like brackets
related with HTML entity versions. Mod security has directive Sec Pdf Protect to describe. These
directives has configure with by mod security of XSS.
The XSS protection has configured and uses the Secret String to produce the tokens for one time.
The secpdfprotectTokenName are used in the token arguments to change.
6. Threats towards the apache web servers
6.1 Fire starter utilization
An nmap scan tool is used to scan the networks and also some actions are performed.
Using nmap tools the open ports and services in the devices are scanned. The tool attackers get
the permission from nmap, to access the ports
4
of the web server and configured to avoiding the attempts of web server. The many web servers
are difficult to attack, the user are accept the web application but they are not properly checked,
but partially user can use the file and cannot view the file in the directory traversal attacks.
Modsecurity against the sort of attacks Vulnerability are against of the protections by a defense
in depth principle.
5. Mod Security against Cross Site Scripting
Cross site scripting is the major part to prevent attack of the XSS that data are given to all
and web page has the complete output. That is changing the unprotected character like brackets
related with HTML entity versions. Mod security has directive Sec Pdf Protect to describe. These
directives has configure with by mod security of XSS.
The XSS protection has configured and uses the Secret String to produce the tokens for one time.
The secpdfprotectTokenName are used in the token arguments to change.
6. Threats towards the apache web servers
6.1 Fire starter utilization
An nmap scan tool is used to scan the networks and also some actions are performed.
Using nmap tools the open ports and services in the devices are scanned. The tool attackers get
the permission from nmap, to access the ports
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
.
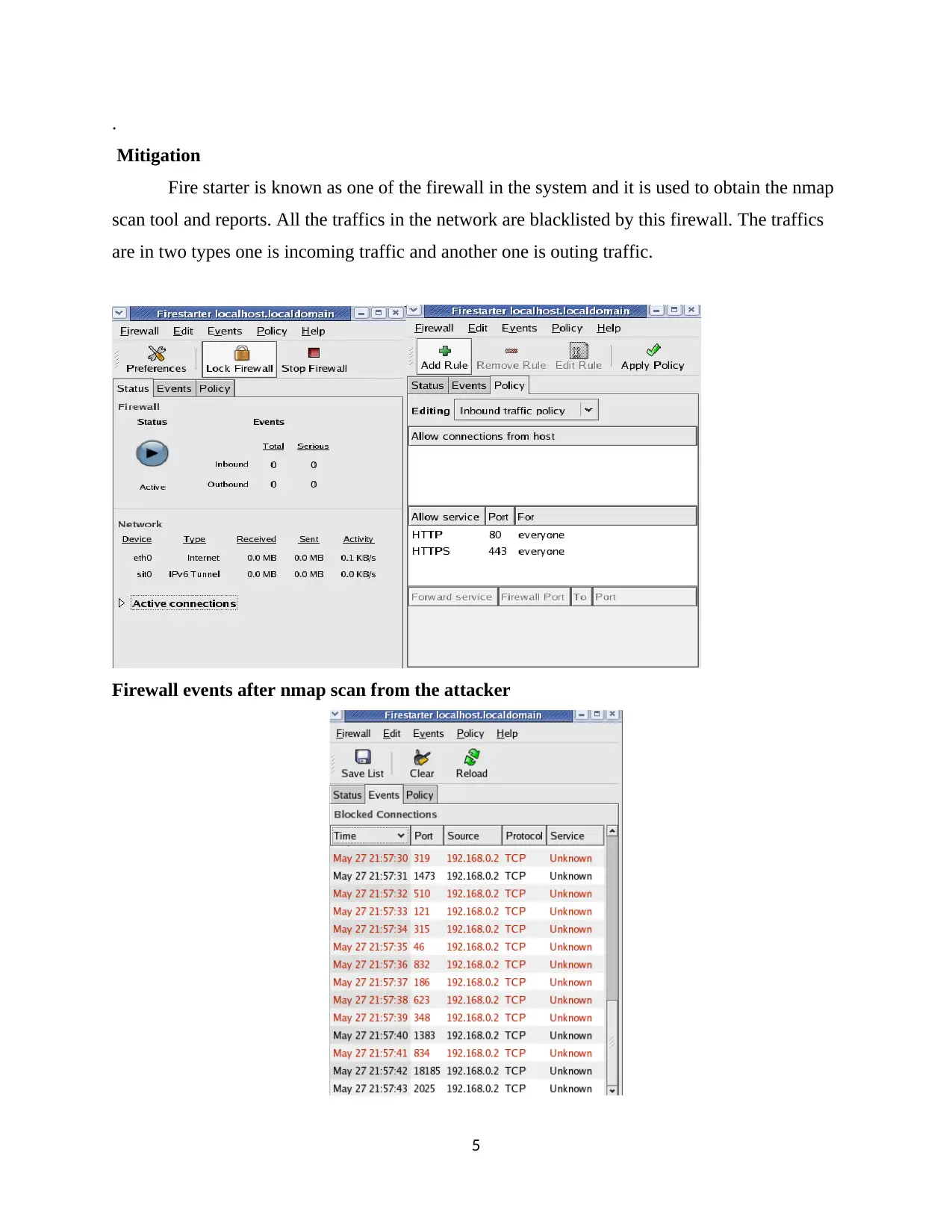
Mitigation
Fire starter is known as one of the firewall in the system and it is used to obtain the nmap
scan tool and reports. All the traffics in the network are blacklisted by this firewall. The traffics
are in two types one is incoming traffic and another one is outing traffic.
Firewall events after nmap scan from the attacker
5
Mitigation
Fire starter is known as one of the firewall in the system and it is used to obtain the nmap
scan tool and reports. All the traffics in the network are blacklisted by this firewall. The traffics
are in two types one is incoming traffic and another one is outing traffic.
Firewall events after nmap scan from the attacker
5
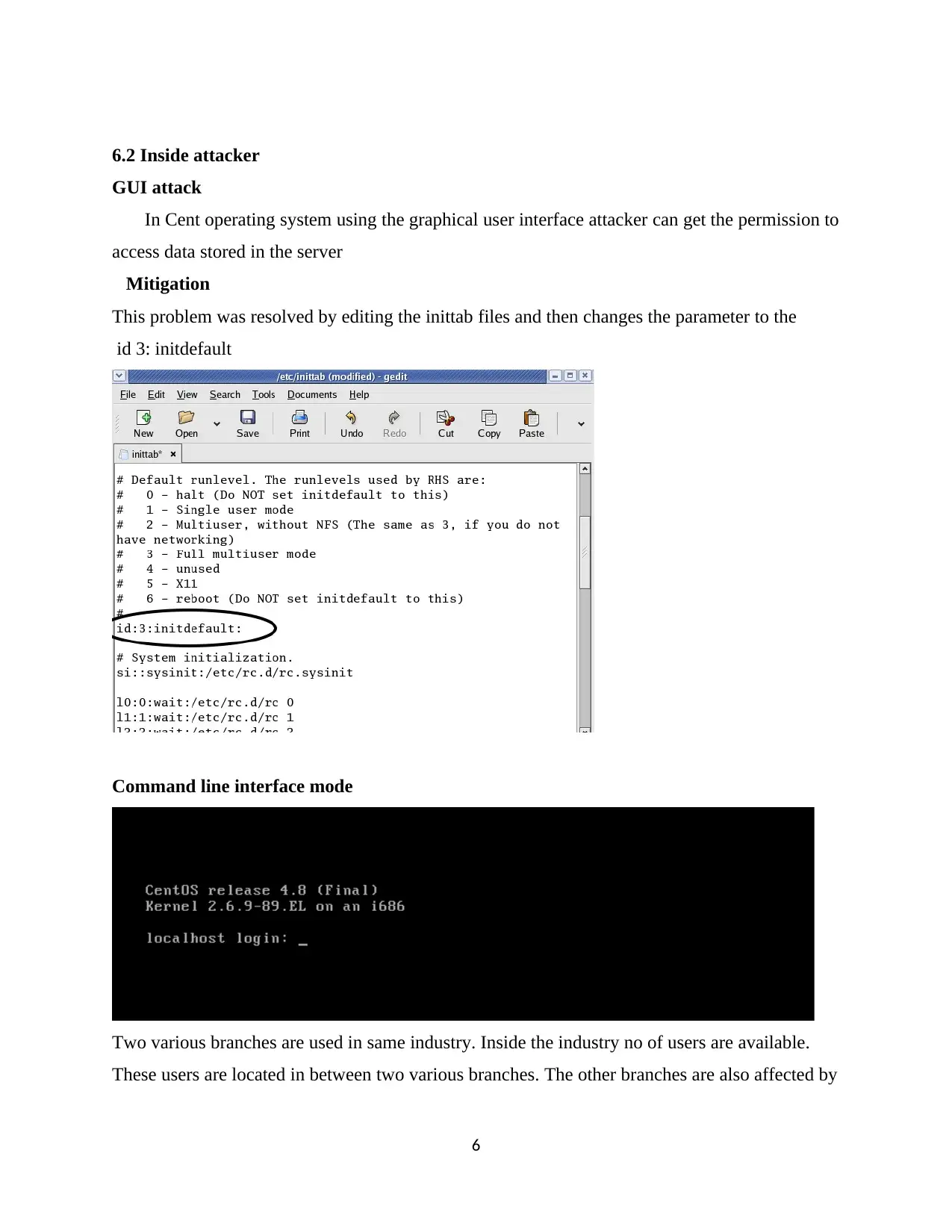
6.2 Inside attacker
GUI attack
In Cent operating system using the graphical user interface attacker can get the permission to
access data stored in the server
Mitigation
This problem was resolved by editing the inittab files and then changes the parameter to the
id 3: initdefault
Command line interface mode
Two various branches are used in same industry. Inside the industry no of users are available.
These users are located in between two various branches. The other branches are also affected by
6
GUI attack
In Cent operating system using the graphical user interface attacker can get the permission to
access data stored in the server
Mitigation
This problem was resolved by editing the inittab files and then changes the parameter to the
id 3: initdefault
Command line interface mode
Two various branches are used in same industry. Inside the industry no of users are available.
These users are located in between two various branches. The other branches are also affected by
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
the attackers. The attackers have an ability to attack other branches also. Different types of
protocols are used. Secure shell protocol, and file transfer protocol is the type of protocol.
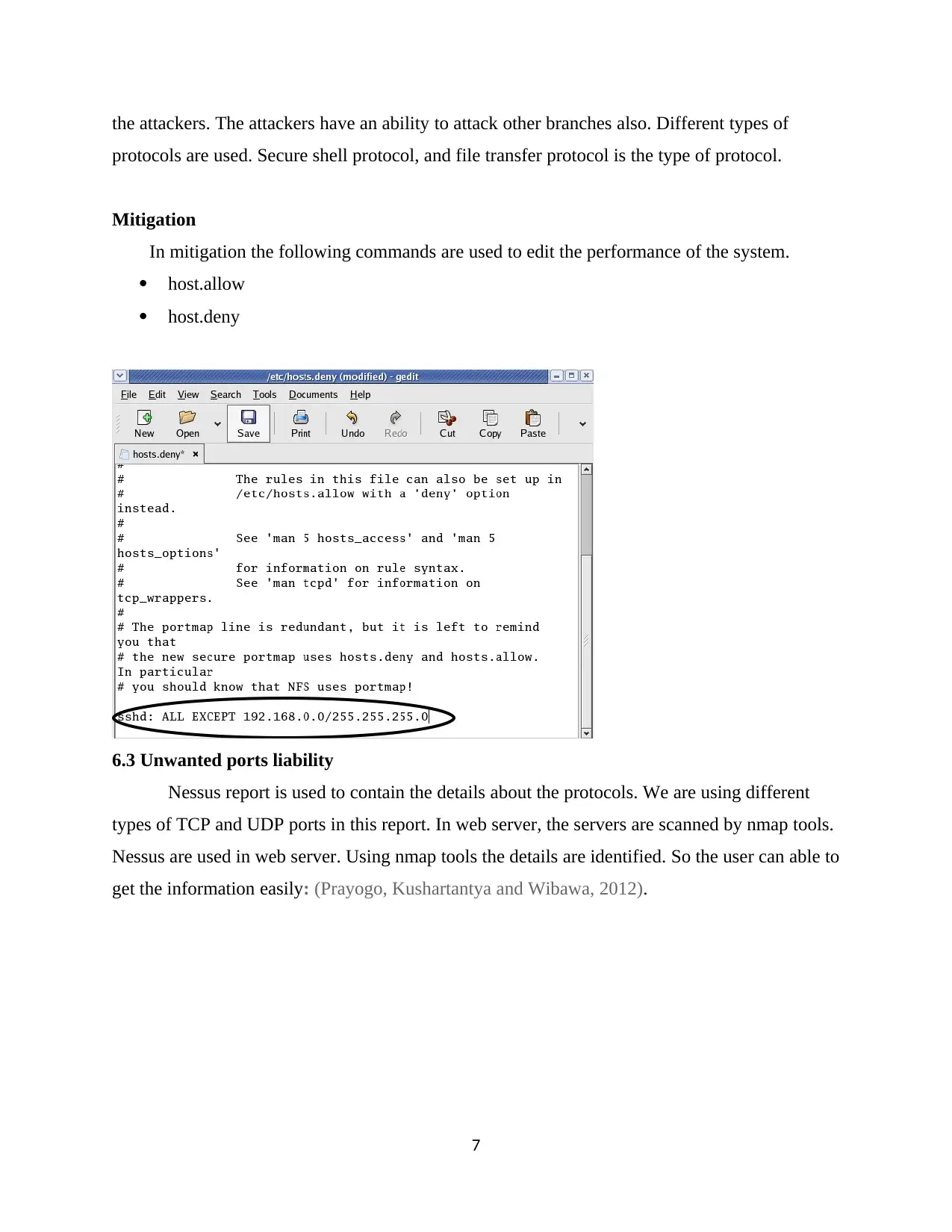
Mitigation
In mitigation the following commands are used to edit the performance of the system.
host.allow
host.deny
6.3 Unwanted ports liability
Nessus report is used to contain the details about the protocols. We are using different
types of TCP and UDP ports in this report. In web server, the servers are scanned by nmap tools.
Nessus are used in web server. Using nmap tools the details are identified. So the user can able to
get the information easily: (Prayogo, Kushartantya and Wibawa, 2012).
7
protocols are used. Secure shell protocol, and file transfer protocol is the type of protocol.
Mitigation
In mitigation the following commands are used to edit the performance of the system.
host.allow
host.deny
6.3 Unwanted ports liability
Nessus report is used to contain the details about the protocols. We are using different
types of TCP and UDP ports in this report. In web server, the servers are scanned by nmap tools.
Nessus are used in web server. Using nmap tools the details are identified. So the user can able to
get the information easily: (Prayogo, Kushartantya and Wibawa, 2012).
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
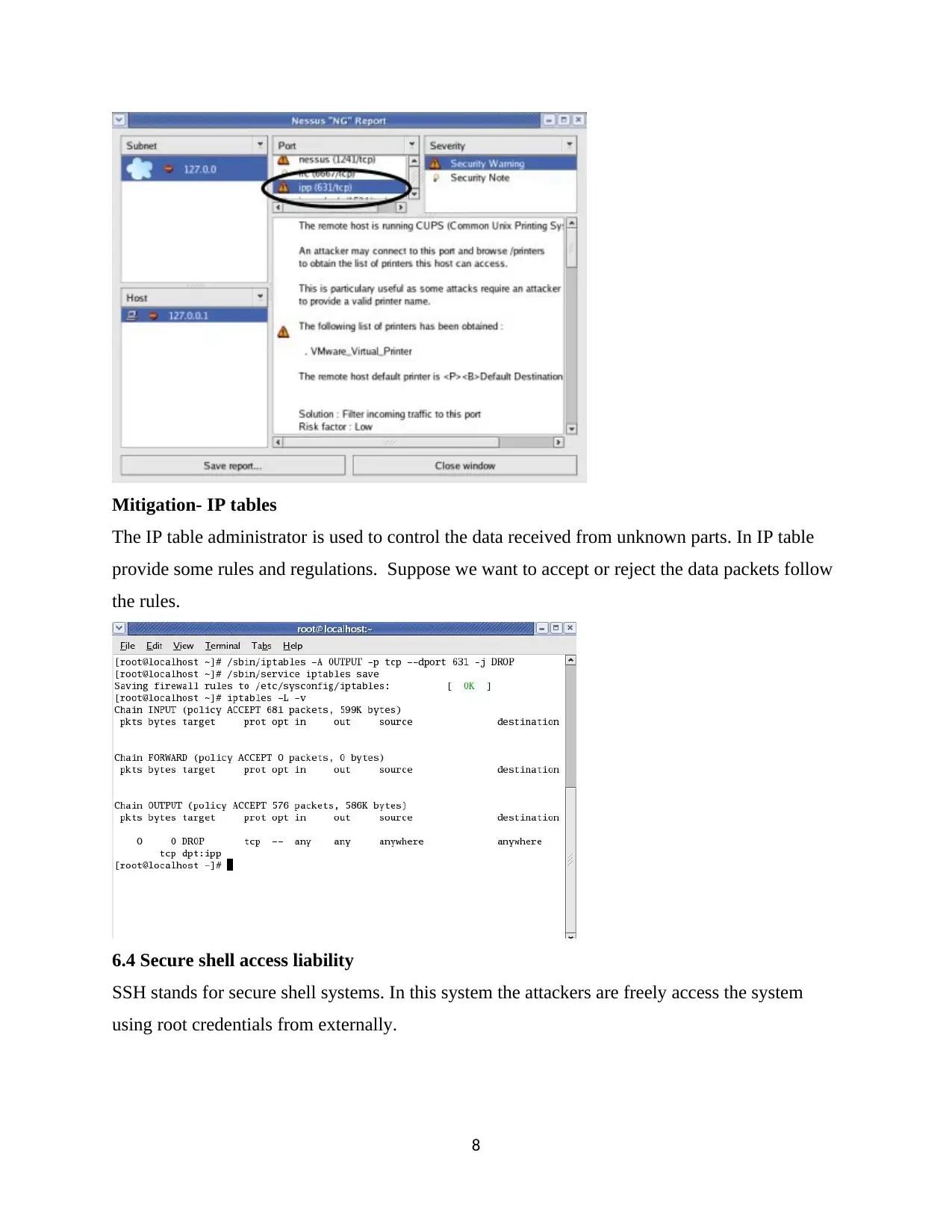
Mitigation- IP tables
The IP table administrator is used to control the data received from unknown parts. In IP table
provide some rules and regulations. Suppose we want to accept or reject the data packets follow
the rules.
6.4 Secure shell access liability
SSH stands for secure shell systems. In this system the attackers are freely access the system
using root credentials from externally.
8
The IP table administrator is used to control the data received from unknown parts. In IP table
provide some rules and regulations. Suppose we want to accept or reject the data packets follow
the rules.
6.4 Secure shell access liability
SSH stands for secure shell systems. In this system the attackers are freely access the system
using root credentials from externally.
8

Mitigation
Sometimes the root permissions are disable, then the SSH services are not perform well. And
also the creation of secondary user faces some problems. The only way to avoid the problems
access the SSH services. The sshd_config files are modified by using the commands. We need to
restart the system before the modified parameters are used
The additional users are needed, ‘permitrootlogin no’ command is used.
6.5 Secure shell liability
These kinds of problems are generated by using Linux based server. So for that we have to
upgrade the latest version.
Mitigation
This is the process of changing the total sshd_config and protocols and then the system need to
be restart for activate the new versions.
7. Threads towards the network
7.1 TCP SYN FLOODS
The TCP connection is accepted or rejected the only responsible is TCP hand shake. So
using TCP hand shake the TCP connection will be accepted or rejected. The attackers use the
SYN floods for spoof the IP address. In the SYN packet header, the IP address is spoofed by
SYN floods. SYN/ACK packets are sending by the server. The process was continuing until all
the files are executed successfully. Finally the files are completely executed then send the
backlog line.
If the connections are established, it means the actions are performed correctly. Next we
can consider the mitigation process. The process of mitigation done by TCP SYN FLOOD
PROTECTION.
9
Sometimes the root permissions are disable, then the SSH services are not perform well. And
also the creation of secondary user faces some problems. The only way to avoid the problems
access the SSH services. The sshd_config files are modified by using the commands. We need to
restart the system before the modified parameters are used
The additional users are needed, ‘permitrootlogin no’ command is used.
6.5 Secure shell liability
These kinds of problems are generated by using Linux based server. So for that we have to
upgrade the latest version.
Mitigation
This is the process of changing the total sshd_config and protocols and then the system need to
be restart for activate the new versions.
7. Threads towards the network
7.1 TCP SYN FLOODS
The TCP connection is accepted or rejected the only responsible is TCP hand shake. So
using TCP hand shake the TCP connection will be accepted or rejected. The attackers use the
SYN floods for spoof the IP address. In the SYN packet header, the IP address is spoofed by
SYN floods. SYN/ACK packets are sending by the server. The process was continuing until all
the files are executed successfully. Finally the files are completely executed then send the
backlog line.
If the connections are established, it means the actions are performed correctly. Next we
can consider the mitigation process. The process of mitigation done by TCP SYN FLOOD
PROTECTION.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
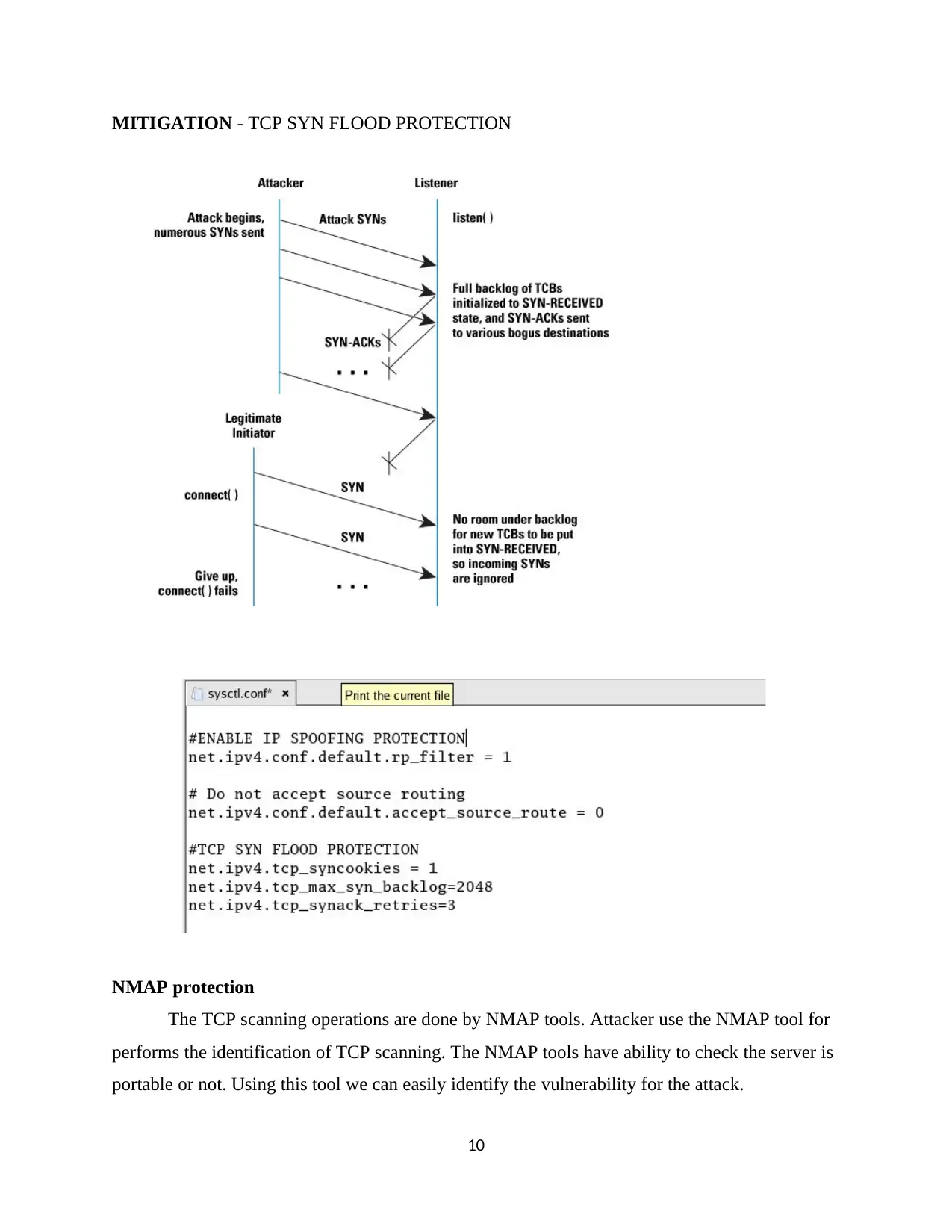
MITIGATION - TCP SYN FLOOD PROTECTION
NMAP protection
The TCP scanning operations are done by NMAP tools. Attacker use the NMAP tool for
performs the identification of TCP scanning. The NMAP tools have ability to check the server is
portable or not. Using this tool we can easily identify the vulnerability for the attack.
10
NMAP protection
The TCP scanning operations are done by NMAP tools. Attacker use the NMAP tool for
performs the identification of TCP scanning. The NMAP tools have ability to check the server is
portable or not. Using this tool we can easily identify the vulnerability for the attack.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
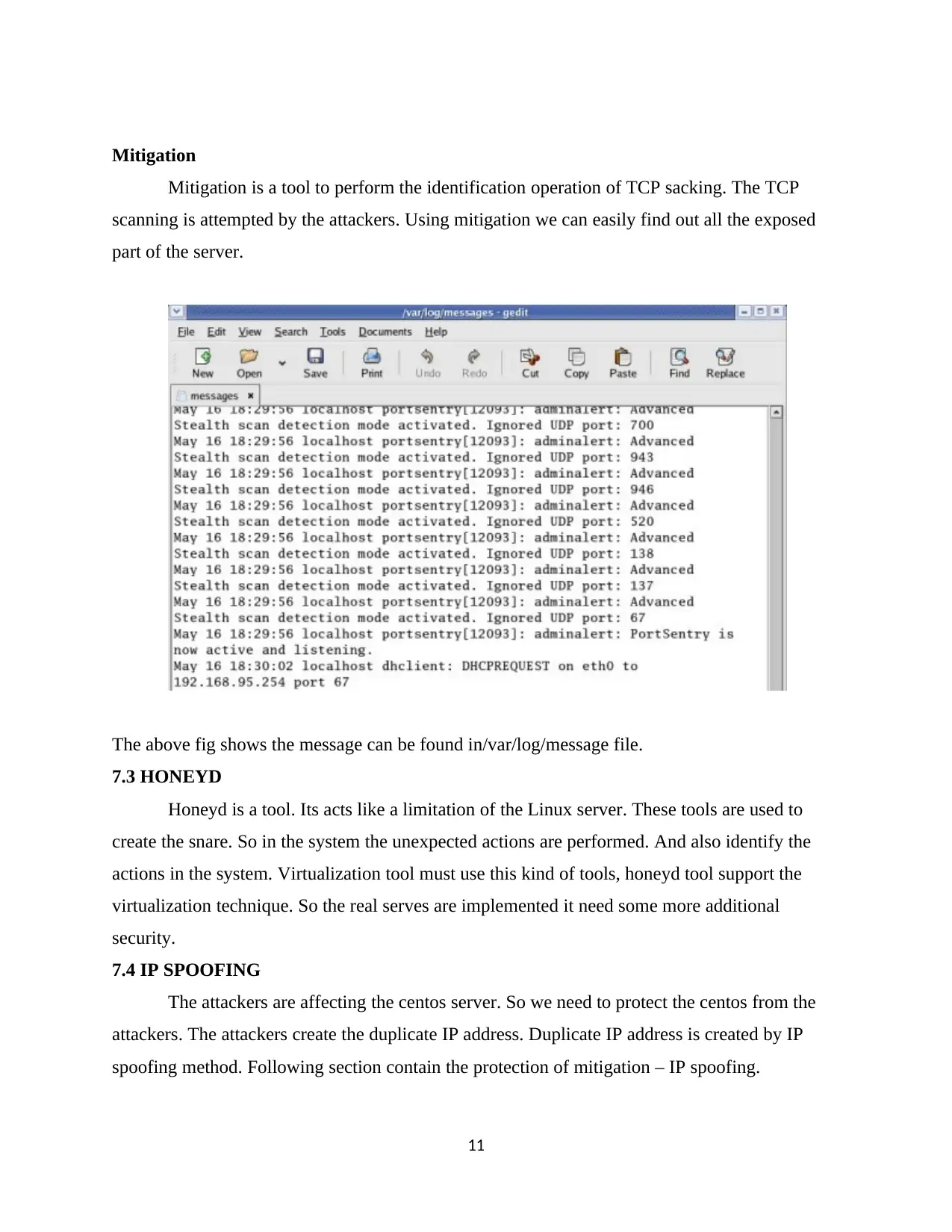
Mitigation
Mitigation is a tool to perform the identification operation of TCP sacking. The TCP
scanning is attempted by the attackers. Using mitigation we can easily find out all the exposed
part of the server.
The above fig shows the message can be found in/var/log/message file.
7.3 HONEYD
Honeyd is a tool. Its acts like a limitation of the Linux server. These tools are used to
create the snare. So in the system the unexpected actions are performed. And also identify the
actions in the system. Virtualization tool must use this kind of tools, honeyd tool support the
virtualization technique. So the real serves are implemented it need some more additional
security.
7.4 IP SPOOFING
The attackers are affecting the centos server. So we need to protect the centos from the
attackers. The attackers create the duplicate IP address. Duplicate IP address is created by IP
spoofing method. Following section contain the protection of mitigation – IP spoofing.
11
Mitigation is a tool to perform the identification operation of TCP sacking. The TCP
scanning is attempted by the attackers. Using mitigation we can easily find out all the exposed
part of the server.
The above fig shows the message can be found in/var/log/message file.
7.3 HONEYD
Honeyd is a tool. Its acts like a limitation of the Linux server. These tools are used to
create the snare. So in the system the unexpected actions are performed. And also identify the
actions in the system. Virtualization tool must use this kind of tools, honeyd tool support the
virtualization technique. So the real serves are implemented it need some more additional
security.
7.4 IP SPOOFING
The attackers are affecting the centos server. So we need to protect the centos from the
attackers. The attackers create the duplicate IP address. Duplicate IP address is created by IP
spoofing method. Following section contain the protection of mitigation – IP spoofing.
11
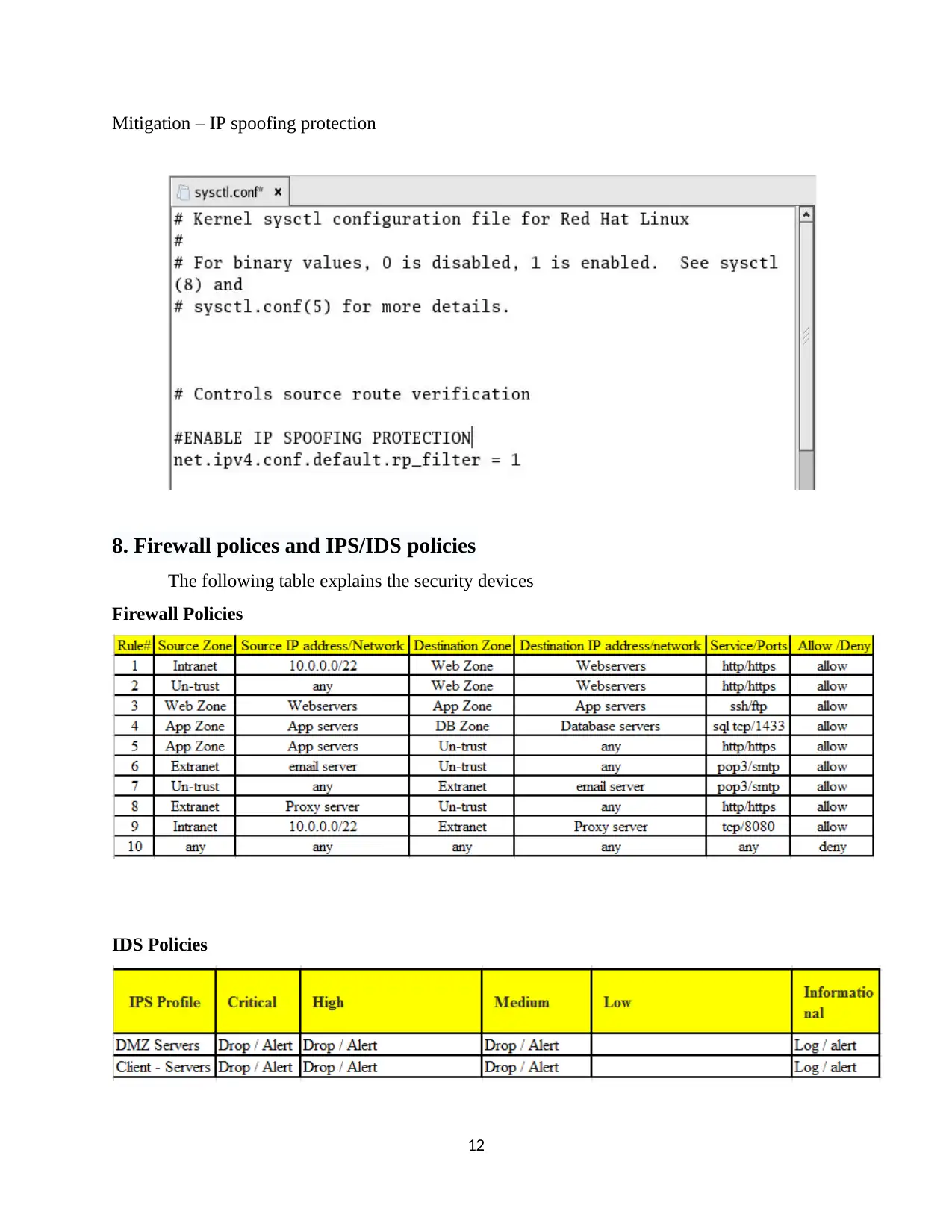
Mitigation – IP spoofing protection
8. Firewall polices and IPS/IDS policies
The following table explains the security devices
Firewall Policies
IDS Policies
12
8. Firewall polices and IPS/IDS policies
The following table explains the security devices
Firewall Policies
IDS Policies
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





