Analysis of a Tour and Travel Management System Business Case Report
VerifiedAdded on 2022/12/05
|6
|2259
|133
Report
AI Summary
This report presents a comprehensive business case for a Tour and Travel Management System, specifically tailored for the Northern Territory. It outlines the project's strategic goals, including enhancing online booking and improving customer satisfaction through custom travel packages and marketing campaigns. The report details the project's financial aspects, including estimated costs and expected returns, along with an analysis of potential risks, particularly those related to system security. It also covers functional and non-functional requirements, such as login functionality, security measures, and usability. Furthermore, the report explores the software reuse process, discussing its advantages, disadvantages, and mitigation strategies. Finally, it emphasizes the importance of cybersecurity in protecting sensitive data and ensuring system reliability, providing recommendations for security enhancements, including intrusion detection, user training, and regular system monitoring. The report concludes with a list of references used in the analysis.

Running Head:TOUR AND TRAVEL MANAGEMENT SYSTEM
TOUR AND TRAVEL MANAGEMENT SYSTEM
Insert Your Name Here
Insert Your Tutor’s Name Here
Institution Affiliation
Date
TOUR AND TRAVEL MANAGEMENT SYSTEM
Insert Your Name Here
Insert Your Tutor’s Name Here
Institution Affiliation
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Running Head:TOUR AND TRAVEL MANAGEMENT SYSTEM
1.
A Tour and Travel Management System is a system that could be very useful in the Northern Territory.
The Northern Territory is a dusty and a desolate of desert. Despite the desert nature of the area there are
waterways that churns with crocodiles, there are ochre sands of the Red Centre, there are waterfalls
and the untamed natural splendor and the spiritual allure. There are beautiful destinations such as
Darwin, Kakadu National Park, Katherine, Litchfield National Park, Tiwi islands, Uluru, Kings
Canyon, Kata Tjuta (the Olgas), Alice Springs and many more beautiful scenarios. These beautiful
scenes tend to attract more tourists. According to Whipple ( 2104), it will be easier if the government
set a system where local and the international tourists will be making to reservations online. These will
help track the records and profits gained from these beautiful sites. The government will also be in
position to tell most tourists are from which locations. Also the sites that are being visit frequently will
also be identified using the Tour and Travel Management System. (Chiang and Chen, 2014) This
system will help in making the reservation easier for the people involved. A lot of data will be collected
using the system. Hurley says (2012), the data can then be analyzed and displayed using graphical
representation.
The project should be funded because it will bring more tourist to the Northern territory. If the system
is advertised people to used for booking trips, then a lot of revenue will be generated. The total funds
required are an estimate of $75,000 . The government should fund $40,000 for the software
development and the hotels and the sites management in the Northern Territory should fund $35,000
for the project management and marketing costs. Parry says(2014), the graphs will help in identifying
the trend of business in the Northern Territory and also they will help the management teams in the
Northern Territory and the government to make valid decision regarding the area. Below is a business
case for the system development project.
Business Case
Project Name A Tour and Travel Management System
Project Sponsors 1. Government
2. Tourism Board in
Northern Territory
Project Manager John Kelvin
Date of Project
Approval
14th April 2019 Last Revision Date 10th April 2019
Business Strategy Our strategy is to provide a platform that will enhance easy booking of
tools. The business strategy will also revolve round the need of providing
quality services to the targeted customers. This will ensure that the
customers’ need are satisfied. This will be successful by providing great
deal custom travel packages and ensuring that the customer needs are
catered for.
Marketing campaign will also increase . Digital marketing will be done to
ensure most people do their booking thought the Tour and Travel
Management System.
We will also have well designed brochures about the tour packages that
we are offering to our customers. From time to time the system will
include discounts in the tour package to attract more customer to make
reservations.
Options Considered The options that are considered include:
1. Adding hotel booking module in the system.
2. Having a dedicated team in the Northern Territory to ensure all the
1.
A Tour and Travel Management System is a system that could be very useful in the Northern Territory.
The Northern Territory is a dusty and a desolate of desert. Despite the desert nature of the area there are
waterways that churns with crocodiles, there are ochre sands of the Red Centre, there are waterfalls
and the untamed natural splendor and the spiritual allure. There are beautiful destinations such as
Darwin, Kakadu National Park, Katherine, Litchfield National Park, Tiwi islands, Uluru, Kings
Canyon, Kata Tjuta (the Olgas), Alice Springs and many more beautiful scenarios. These beautiful
scenes tend to attract more tourists. According to Whipple ( 2104), it will be easier if the government
set a system where local and the international tourists will be making to reservations online. These will
help track the records and profits gained from these beautiful sites. The government will also be in
position to tell most tourists are from which locations. Also the sites that are being visit frequently will
also be identified using the Tour and Travel Management System. (Chiang and Chen, 2014) This
system will help in making the reservation easier for the people involved. A lot of data will be collected
using the system. Hurley says (2012), the data can then be analyzed and displayed using graphical
representation.
The project should be funded because it will bring more tourist to the Northern territory. If the system
is advertised people to used for booking trips, then a lot of revenue will be generated. The total funds
required are an estimate of $75,000 . The government should fund $40,000 for the software
development and the hotels and the sites management in the Northern Territory should fund $35,000
for the project management and marketing costs. Parry says(2014), the graphs will help in identifying
the trend of business in the Northern Territory and also they will help the management teams in the
Northern Territory and the government to make valid decision regarding the area. Below is a business
case for the system development project.
Business Case
Project Name A Tour and Travel Management System
Project Sponsors 1. Government
2. Tourism Board in
Northern Territory
Project Manager John Kelvin
Date of Project
Approval
14th April 2019 Last Revision Date 10th April 2019
Business Strategy Our strategy is to provide a platform that will enhance easy booking of
tools. The business strategy will also revolve round the need of providing
quality services to the targeted customers. This will ensure that the
customers’ need are satisfied. This will be successful by providing great
deal custom travel packages and ensuring that the customer needs are
catered for.
Marketing campaign will also increase . Digital marketing will be done to
ensure most people do their booking thought the Tour and Travel
Management System.
We will also have well designed brochures about the tour packages that
we are offering to our customers. From time to time the system will
include discounts in the tour package to attract more customer to make
reservations.
Options Considered The options that are considered include:
1. Adding hotel booking module in the system.
2. Having a dedicated team in the Northern Territory to ensure all the
Running Head:TOUR AND TRAVEL MANAGEMENT SYSTEM
tourist have fun visiting the sites.
3. Marketing the travel package in the Northern Territory.
Benefits The following are the benefits of the Tour and Travel Management
System:
1. To provide continuously enjoyable tour packages on budget.
2. The system will ensure that the customers were satisfied and they will
write their reviews about the tour packages they experienced in the
Northern Territory.
3. The system will help the responsible management team make valid
decisions from the data collected.
4. A market campaign will be undertaken to ensure that people make
reservations using the system
Timescale The analysis shows that the system development will take 3-4 months to
implement
Cost Software Development =$40,000
Project Management = $25,000
Marketing =$10,000
Total estimated cost = $75,000
Expected Return on
Investment
Year 1 = $0
Year 2 = $200,000
Year 3 = $350,000
Risks Security Risk- Since payment will be made through the system. The
system can be hacked. But system security will be highly enforced and
frequent monitoring of the system will be done to detect system intrusion.
2.
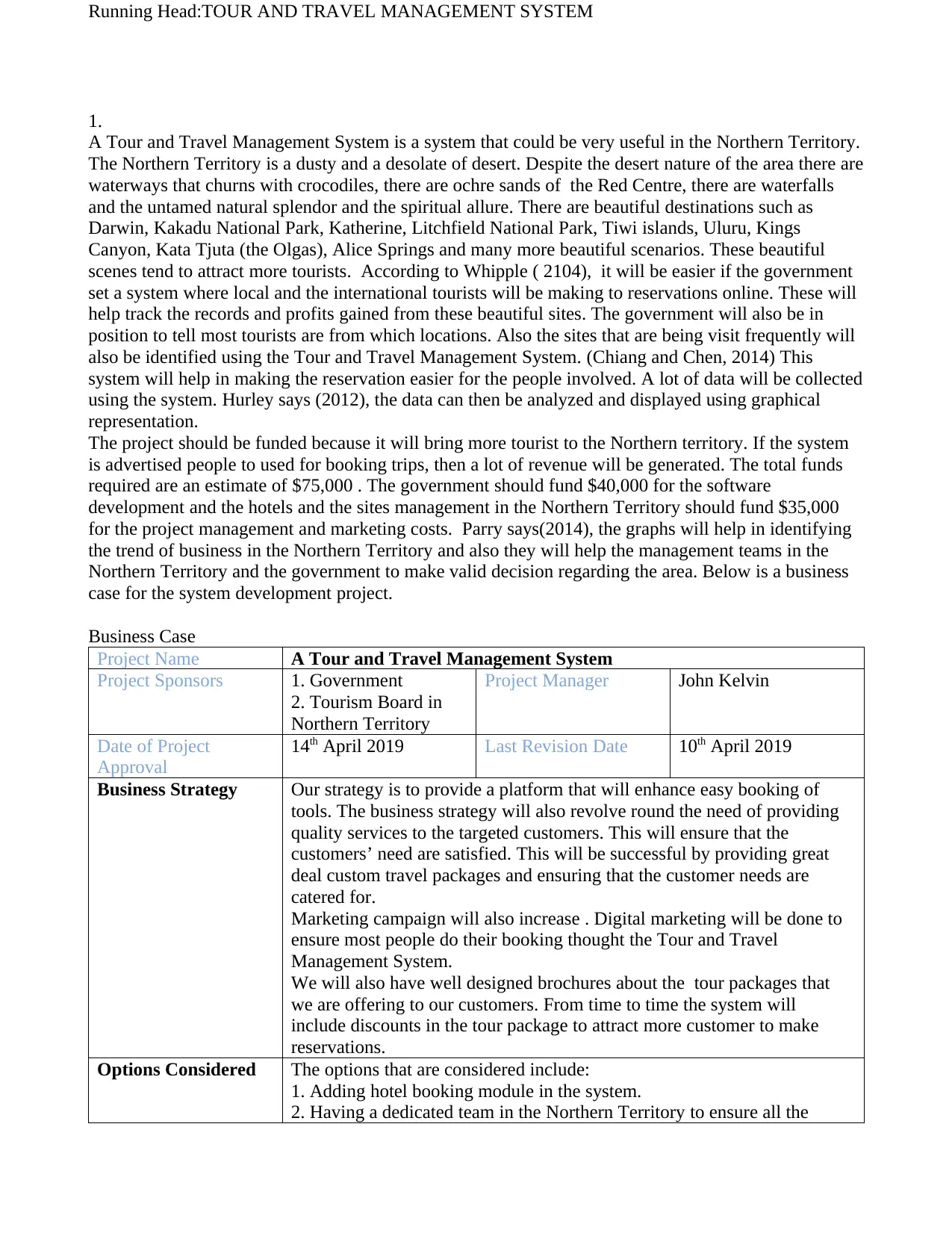
One of the functional requirement is making enabling the users to login into the system. There are a
number of tools that are used in test case scenarios. For example EasyQA and ReQtest
Steps for the test case scenario.
tourist have fun visiting the sites.
3. Marketing the travel package in the Northern Territory.
Benefits The following are the benefits of the Tour and Travel Management
System:
1. To provide continuously enjoyable tour packages on budget.
2. The system will ensure that the customers were satisfied and they will
write their reviews about the tour packages they experienced in the
Northern Territory.
3. The system will help the responsible management team make valid
decisions from the data collected.
4. A market campaign will be undertaken to ensure that people make
reservations using the system
Timescale The analysis shows that the system development will take 3-4 months to
implement
Cost Software Development =$40,000
Project Management = $25,000
Marketing =$10,000
Total estimated cost = $75,000
Expected Return on
Investment
Year 1 = $0
Year 2 = $200,000
Year 3 = $350,000
Risks Security Risk- Since payment will be made through the system. The
system can be hacked. But system security will be highly enforced and
frequent monitoring of the system will be done to detect system intrusion.
2.
One of the functional requirement is making enabling the users to login into the system. There are a
number of tools that are used in test case scenarios. For example EasyQA and ReQtest
Steps for the test case scenario.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Running Head:TOUR AND TRAVEL MANAGEMENT SYSTEM
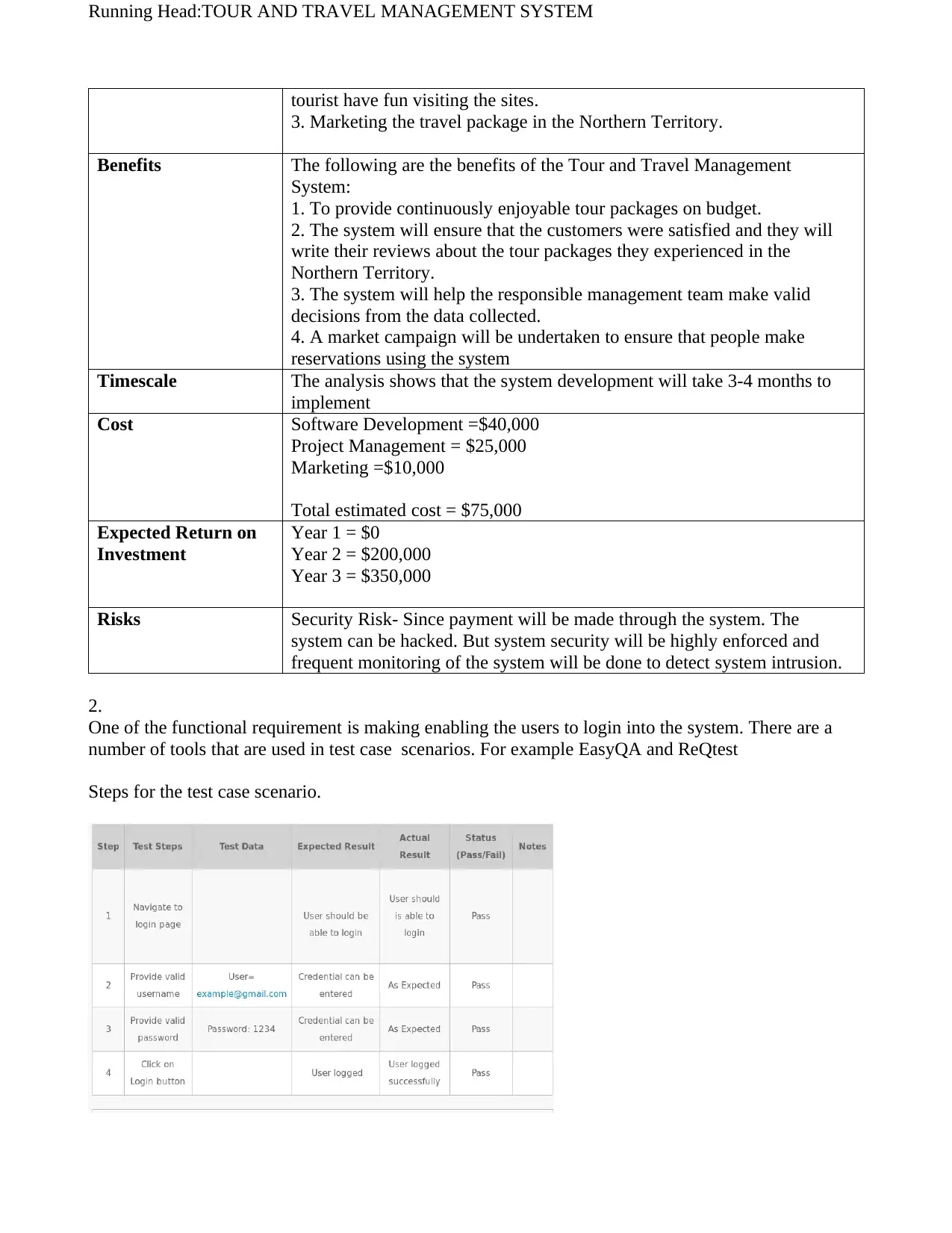
Conditions
Results
3. Non-functional requirements
The Tour and Travel Management system will have the following non-functional requirements.
Security: The system will be secure. All the people who have access to the system will be prompted to
login. Once the system detect a certain period of inactivity like 15 minutes, the system will log out the
person. The confidential data will be stored in a encrypted way. Frequent monitoring of the system be
done. This is to ensure there is no intrusion into the system (Alsaleh and Haron, 2016).
Reliability: According to Haigh (2010), the system should work for a long time without any problem.
Accuracy and Precision: The data and the information derived from the system should be accurate This
will result to making the right decisions.
Usability: According to Xu (2012), the software should be in a position to perform all the intended
tasks. This means that the users of the system can perform a specific task efficiently and effectively.
Maintainability: The code quality should be easy to understand by another developer. If the code is not
easy to understand. This means it can not be maintained by someone else only for the original
developers.
Legal: The system should ensure the right of privacy is enhance. The private information such as credit
card information should only be visible to the authenticated users.
Performance requirements: The performance requirements of a system is about the response time , the
transaction rates should be as expected and benchmarking the specification of the packages should be
as expected.
4. Software reuse process
The software reuse is a process of developing a software using predefined software components.
Theses component include the code, the design, the test cases,data, prototype, plans, documentation
and the framework. According to Manhas (2010), there are some advantages of using the software
reuse. The advantages include: increase in the software productivity, developing a software in less
Conditions
Results
3. Non-functional requirements
The Tour and Travel Management system will have the following non-functional requirements.
Security: The system will be secure. All the people who have access to the system will be prompted to
login. Once the system detect a certain period of inactivity like 15 minutes, the system will log out the
person. The confidential data will be stored in a encrypted way. Frequent monitoring of the system be
done. This is to ensure there is no intrusion into the system (Alsaleh and Haron, 2016).
Reliability: According to Haigh (2010), the system should work for a long time without any problem.
Accuracy and Precision: The data and the information derived from the system should be accurate This
will result to making the right decisions.
Usability: According to Xu (2012), the software should be in a position to perform all the intended
tasks. This means that the users of the system can perform a specific task efficiently and effectively.
Maintainability: The code quality should be easy to understand by another developer. If the code is not
easy to understand. This means it can not be maintained by someone else only for the original
developers.
Legal: The system should ensure the right of privacy is enhance. The private information such as credit
card information should only be visible to the authenticated users.
Performance requirements: The performance requirements of a system is about the response time , the
transaction rates should be as expected and benchmarking the specification of the packages should be
as expected.
4. Software reuse process
The software reuse is a process of developing a software using predefined software components.
Theses component include the code, the design, the test cases,data, prototype, plans, documentation
and the framework. According to Manhas (2010), there are some advantages of using the software
reuse. The advantages include: increase in the software productivity, developing a software in less
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running Head:TOUR AND TRAVEL MANAGEMENT SYSTEM
time, have fewer people in the development team, reduces the software development costs, the
developers also develop an more standardized software and enhance the software interoperability.
However, there are issues that arises due to software reuse. They include accepting the deliveries from
countries that do not match Austria's license, patents, innovation and copyrights. Other disadvantages is
that software reuse involves coordination cost, the cost of integration from the previous software and
there is too much dependency on another software.
The risks and disadvantages with software reuse could be solved by user only reusing code from trusted
sources. One should only reuse code that use the known libraries. If on may use code from unknown
libraries, in case the system crashes it will be difficult to solve the issue. Secondly, the developers
should use OWASP dependency check. This tool will help to identify the known vulnerability in the
third-party component that a developer may be using.Cheng argues (2013), one should also monitor the
external components that are being used. In case a vulnerability is identified then one will be alerted.
This method will help in fixing the issues instantly. Finally having a system security testing as part of
the development activities, will the developer develop a secure system and they will identify the risks
in a system and solve them at an early stage.
5.
As a cyber security specialist my function important is the development of Tours and Travel System
Management. Security enhancement is a very important aspect in all software. According to Mouratidis
(2011), when a software is not secure, the users may not trust the system and therefore, they would
evade using the system. The software will have critical data such as the users credit card information.
When a system has a security fault, hackers may use the opportunity to hack into the system and steal
the credit card information for various customers. The hackers may use this information to receive
money from the cards. The hackers may also make false reservation and fake the payment details in the
system and approve the payments themselves. This may result to offering free services to people,
which will in turn lead to losses in the companies. To avoid such issues, system security is very
important. Byun says (2015), system security ensures that all the processes are running efficiently and
the critical data such as login credentials and the credit card information is stored in an encrypted way.
There are many security loopholes that may be spotted by the hackers. The loop holes may be found in
the software, the network or even the users of the system. To avoid the insecurities in the system a plan
how the to get it of the risk is as shown below.
1. Designing the software solution for all the IT security requirement.
2. Ensuring the project is developed according to the security specifications
3. Perform intrusion detection in the system and the entire network.
4. Training the user on the importance of system security. This will involve advising the users to use
strong passwords in logging into the system. The users will also be advised not to share their login
details. The developer will also be trained on the need to develop a secure system.
5. Develop a monitoring system that will frequently monitor the servers and the network. In case of any
issues detected in the system, an alert should be sent to the responsible people to look into the issue.
5. Give a report on the security status on the system every day.
time, have fewer people in the development team, reduces the software development costs, the
developers also develop an more standardized software and enhance the software interoperability.
However, there are issues that arises due to software reuse. They include accepting the deliveries from
countries that do not match Austria's license, patents, innovation and copyrights. Other disadvantages is
that software reuse involves coordination cost, the cost of integration from the previous software and
there is too much dependency on another software.
The risks and disadvantages with software reuse could be solved by user only reusing code from trusted
sources. One should only reuse code that use the known libraries. If on may use code from unknown
libraries, in case the system crashes it will be difficult to solve the issue. Secondly, the developers
should use OWASP dependency check. This tool will help to identify the known vulnerability in the
third-party component that a developer may be using.Cheng argues (2013), one should also monitor the
external components that are being used. In case a vulnerability is identified then one will be alerted.
This method will help in fixing the issues instantly. Finally having a system security testing as part of
the development activities, will the developer develop a secure system and they will identify the risks
in a system and solve them at an early stage.
5.
As a cyber security specialist my function important is the development of Tours and Travel System
Management. Security enhancement is a very important aspect in all software. According to Mouratidis
(2011), when a software is not secure, the users may not trust the system and therefore, they would
evade using the system. The software will have critical data such as the users credit card information.
When a system has a security fault, hackers may use the opportunity to hack into the system and steal
the credit card information for various customers. The hackers may use this information to receive
money from the cards. The hackers may also make false reservation and fake the payment details in the
system and approve the payments themselves. This may result to offering free services to people,
which will in turn lead to losses in the companies. To avoid such issues, system security is very
important. Byun says (2015), system security ensures that all the processes are running efficiently and
the critical data such as login credentials and the credit card information is stored in an encrypted way.
There are many security loopholes that may be spotted by the hackers. The loop holes may be found in
the software, the network or even the users of the system. To avoid the insecurities in the system a plan
how the to get it of the risk is as shown below.
1. Designing the software solution for all the IT security requirement.
2. Ensuring the project is developed according to the security specifications
3. Perform intrusion detection in the system and the entire network.
4. Training the user on the importance of system security. This will involve advising the users to use
strong passwords in logging into the system. The users will also be advised not to share their login
details. The developer will also be trained on the need to develop a secure system.
5. Develop a monitoring system that will frequently monitor the servers and the network. In case of any
issues detected in the system, an alert should be sent to the responsible people to look into the issue.
5. Give a report on the security status on the system every day.

Running Head:TOUR AND TRAVEL MANAGEMENT SYSTEM
References
Whipple, T. (2014). Group Tour Management: Does Good Service Produce Satisfied Customers?.
Journal of Travel Research, 27(2), pp.16-21.
Chiang, C. and Chen, W. (2014). The Impression Management Techniques of Tour Leaders in Group
Package Tour Service Encounters. Journal of Travel & Tourism Marketing, 31(6), pp.747-762.
Hurley, C. (2012). Graphical Selection of Data Views. Journal of Computational and Graphical
Statistics, 9(3), p.558.
Parry, G. (2014). Using Data in Decision-Making. Strategic Change, 23(3-4), pp.265-277.
Alsaleh, S. and Haron, H. (2016). The Most Important Functional and Non-Functional Requirements of
Knowledge Sharing System: A Case Study. Lecture Notes on Software Engineering, 4(2), pp.157-161.
XU, P. (2012). Modeling Patterns: A Method to Evaluate Non-Functional Attributes of Software
Architectures. Journal of Software, 17(6), p.1318.
Haigh, M. (2010). Software quality, non-functional software requirements and IT-business alignment.
Software Quality Journal, 18(3), pp.361-385.
Manhas, S. (2010). Reusability Evaluation Model for Procedure Based Software Systems.
International Journal of Computer and Electrical Engineering, pp.1107-1111.
Cheng, J. (2013). Improving the software reusability in object-oriented programming. ACM SIGSOFT
Software Engineering Notes, 18(4), pp.70-74.
Mouratidis, H. (2011). Secure Software Systems Engineering: The Secure Tropos Approach (Invited
Paper). Journal of Software, 6(3).
Byun, J. (2015). Privacy preserving smartcard-based authentication system with provable security.
Security and Communication Networks, 8(17), pp.3028-3044.
References
Whipple, T. (2014). Group Tour Management: Does Good Service Produce Satisfied Customers?.
Journal of Travel Research, 27(2), pp.16-21.
Chiang, C. and Chen, W. (2014). The Impression Management Techniques of Tour Leaders in Group
Package Tour Service Encounters. Journal of Travel & Tourism Marketing, 31(6), pp.747-762.
Hurley, C. (2012). Graphical Selection of Data Views. Journal of Computational and Graphical
Statistics, 9(3), p.558.
Parry, G. (2014). Using Data in Decision-Making. Strategic Change, 23(3-4), pp.265-277.
Alsaleh, S. and Haron, H. (2016). The Most Important Functional and Non-Functional Requirements of
Knowledge Sharing System: A Case Study. Lecture Notes on Software Engineering, 4(2), pp.157-161.
XU, P. (2012). Modeling Patterns: A Method to Evaluate Non-Functional Attributes of Software
Architectures. Journal of Software, 17(6), p.1318.
Haigh, M. (2010). Software quality, non-functional software requirements and IT-business alignment.
Software Quality Journal, 18(3), pp.361-385.
Manhas, S. (2010). Reusability Evaluation Model for Procedure Based Software Systems.
International Journal of Computer and Electrical Engineering, pp.1107-1111.
Cheng, J. (2013). Improving the software reusability in object-oriented programming. ACM SIGSOFT
Software Engineering Notes, 18(4), pp.70-74.
Mouratidis, H. (2011). Secure Software Systems Engineering: The Secure Tropos Approach (Invited
Paper). Journal of Software, 6(3).
Byun, J. (2015). Privacy preserving smartcard-based authentication system with provable security.
Security and Communication Networks, 8(17), pp.3028-3044.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





