IT Risk Management: Analyzing Aztek Bank's Cloud Computing Case Study
VerifiedAdded on 2020/03/16
|20
|5821
|53
Case Study
AI Summary
This case study examines Aztek Bank, a Melbourne-based financial institution, and its approach to IT risk management, particularly concerning its adoption of outsourced cloud computing. The study delves into the bank's strategic initiatives, including the transfer of critical business applications and data to external cloud systems. It outlines the IT security risk factors, challenges, and the impact on current security measures. A detailed risk analysis is presented, identifying threats, vulnerabilities, and infrastructural frameworks. Data security, risk assessment methodologies, and insurance considerations are also discussed. The study further explores regulatory measures, best practices, and the development of a new IT plan to mitigate potential risks. The case study highlights the importance of risk management in the financial sector, emphasizing the need for proactive strategies to address operational, financial, and reputational risks. The conclusion underscores the significance of comprehensive risk management frameworks for ensuring the success and stability of financial institutions like Aztek Bank in a rapidly evolving technological landscape.

TRANSLATING IT RISK MANAGEMENT
Case Study
Case Study
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1.0 Executive Summary.........................................................................................................................3
2.0 Project Review.................................................................................................................................4
2.1 Outsourcing Cloud Computing....................................................................................................5
2.2 Transfer of IT Applications.........................................................................................................5
2.3 Definition of Risk........................................................................................................................5
2. 4 Regulatory measures and Best practice.......................................................................................7
3.0 Project Impact on Current Security..................................................................................................7
3.1 Current plans...............................................................................................................................7
3.2 IT Security Risk Factors..............................................................................................................8
3.3 The New Plan..............................................................................................................................8
3.4 Challenges...................................................................................................................................9
4.0 Risk Analysis.................................................................................................................................11
4.1 The Risks, Vulnerabilities and Threats..........................................................................................12
Threats.........................................................................................................................................12
Vulnerabilities.............................................................................................................................12
Risks............................................................................................................................................13
4.2 Infrastructural Framework.........................................................................................................13
5.0 Data Security.................................................................................................................................14
5.1 Assessing IT Risks.....................................................................................................................14
5.2 Insurance...................................................................................................................................16
5.3. Risk rating guide.......................................................................................................................16
6.0 Conclusion.....................................................................................................................................16
References...........................................................................................................................................17
1.0 Executive Summary.........................................................................................................................3
2.0 Project Review.................................................................................................................................4
2.1 Outsourcing Cloud Computing....................................................................................................5
2.2 Transfer of IT Applications.........................................................................................................5
2.3 Definition of Risk........................................................................................................................5
2. 4 Regulatory measures and Best practice.......................................................................................7
3.0 Project Impact on Current Security..................................................................................................7
3.1 Current plans...............................................................................................................................7
3.2 IT Security Risk Factors..............................................................................................................8
3.3 The New Plan..............................................................................................................................8
3.4 Challenges...................................................................................................................................9
4.0 Risk Analysis.................................................................................................................................11
4.1 The Risks, Vulnerabilities and Threats..........................................................................................12
Threats.........................................................................................................................................12
Vulnerabilities.............................................................................................................................12
Risks............................................................................................................................................13
4.2 Infrastructural Framework.........................................................................................................13
5.0 Data Security.................................................................................................................................14
5.1 Assessing IT Risks.....................................................................................................................14
5.2 Insurance...................................................................................................................................16
5.3. Risk rating guide.......................................................................................................................16
6.0 Conclusion.....................................................................................................................................16
References...........................................................................................................................................17

1.0 Executive Summary
Aztek is a banking institution situated in Melbourne Australia. Survival in the service
industry calls for a wide range of services including financial management, credit facilities,
savings, alternative investments, mortgages and loans. At the centre of its success is the IT
system, which affects all its functions and operations. The financial services encounter
numerous risks and exposure to unexpected events. In order to manage such challenges, the
banking institution safeguards from operation and financial related risks among others.
Aztecs IT management system protects different sectors and departments. The use of
innovation improves processes across the departments. It prevents losses, unexpected
occurrences and effects from the global markets. As part of strategic management, IT
contributes to the success of Aztek banks. The global market is highly volatile because of
changes in the industry and financial crisis. Cloud computing continues to transform
businesses today. Aztek’s adoption of an outsourced cloud system has benefits as well as
challenges. The risks involved place the company’s data system at a high risk. This report
narrows down its analysis on cloud computing and recommendations the management of
risks through project based approaches.
Designed to support its IT decisions, this Aztek Risk Management plan covers the operations,
financial, reputation, compliance and strategic risks factors (Aebi, Sabato, & Schmid, 2012).
Aztek is a reputable Australian bank charged with providing financial services. The company
has senior executives within its business and technology segments to manage the risks. In a
teamwork spirit, the Aztek divisions have in place a portfolio of projects from different
strategists scheduled for funding. The portfolio comprises of the following projects:
1) Employees use of mobile devices in the workplace for major tasks
2) Transfer of critical business applications and their connected data sources to an
externally managed Cloud hosting system
3) Outsourcing of crucial IT functions including network systems, desktop management
and application development for third party users
4) Upgrading and introduction of a major platform for technology applications including
mobile and migration for a better networking technology (e.g. IPv6).
Aztek is a banking institution situated in Melbourne Australia. Survival in the service
industry calls for a wide range of services including financial management, credit facilities,
savings, alternative investments, mortgages and loans. At the centre of its success is the IT
system, which affects all its functions and operations. The financial services encounter
numerous risks and exposure to unexpected events. In order to manage such challenges, the
banking institution safeguards from operation and financial related risks among others.
Aztecs IT management system protects different sectors and departments. The use of
innovation improves processes across the departments. It prevents losses, unexpected
occurrences and effects from the global markets. As part of strategic management, IT
contributes to the success of Aztek banks. The global market is highly volatile because of
changes in the industry and financial crisis. Cloud computing continues to transform
businesses today. Aztek’s adoption of an outsourced cloud system has benefits as well as
challenges. The risks involved place the company’s data system at a high risk. This report
narrows down its analysis on cloud computing and recommendations the management of
risks through project based approaches.
Designed to support its IT decisions, this Aztek Risk Management plan covers the operations,
financial, reputation, compliance and strategic risks factors (Aebi, Sabato, & Schmid, 2012).
Aztek is a reputable Australian bank charged with providing financial services. The company
has senior executives within its business and technology segments to manage the risks. In a
teamwork spirit, the Aztek divisions have in place a portfolio of projects from different
strategists scheduled for funding. The portfolio comprises of the following projects:
1) Employees use of mobile devices in the workplace for major tasks
2) Transfer of critical business applications and their connected data sources to an
externally managed Cloud hosting system
3) Outsourcing of crucial IT functions including network systems, desktop management
and application development for third party users
4) Upgrading and introduction of a major platform for technology applications including
mobile and migration for a better networking technology (e.g. IPv6).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
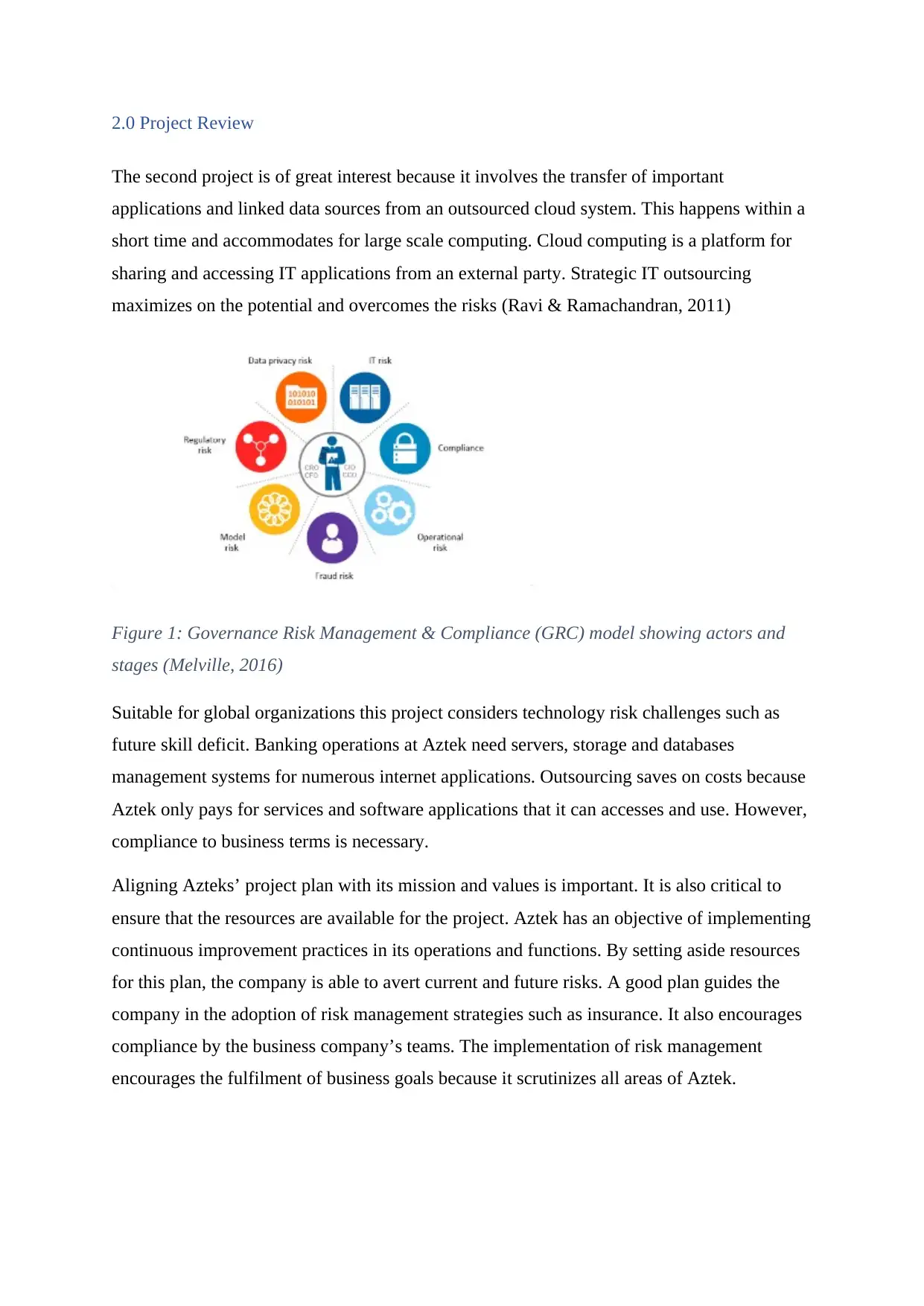
2.0 Project Review
The second project is of great interest because it involves the transfer of important
applications and linked data sources from an outsourced cloud system. This happens within a
short time and accommodates for large scale computing. Cloud computing is a platform for
sharing and accessing IT applications from an external party. Strategic IT outsourcing
maximizes on the potential and overcomes the risks (Ravi & Ramachandran, 2011)
Figure 1: Governance Risk Management & Compliance (GRC) model showing actors and
stages (Melville, 2016)
Suitable for global organizations this project considers technology risk challenges such as
future skill deficit. Banking operations at Aztek need servers, storage and databases
management systems for numerous internet applications. Outsourcing saves on costs because
Aztek only pays for services and software applications that it can accesses and use. However,
compliance to business terms is necessary.
Aligning Azteks’ project plan with its mission and values is important. It is also critical to
ensure that the resources are available for the project. Aztek has an objective of implementing
continuous improvement practices in its operations and functions. By setting aside resources
for this plan, the company is able to avert current and future risks. A good plan guides the
company in the adoption of risk management strategies such as insurance. It also encourages
compliance by the business company’s teams. The implementation of risk management
encourages the fulfilment of business goals because it scrutinizes all areas of Aztek.
The second project is of great interest because it involves the transfer of important
applications and linked data sources from an outsourced cloud system. This happens within a
short time and accommodates for large scale computing. Cloud computing is a platform for
sharing and accessing IT applications from an external party. Strategic IT outsourcing
maximizes on the potential and overcomes the risks (Ravi & Ramachandran, 2011)
Figure 1: Governance Risk Management & Compliance (GRC) model showing actors and
stages (Melville, 2016)
Suitable for global organizations this project considers technology risk challenges such as
future skill deficit. Banking operations at Aztek need servers, storage and databases
management systems for numerous internet applications. Outsourcing saves on costs because
Aztek only pays for services and software applications that it can accesses and use. However,
compliance to business terms is necessary.
Aligning Azteks’ project plan with its mission and values is important. It is also critical to
ensure that the resources are available for the project. Aztek has an objective of implementing
continuous improvement practices in its operations and functions. By setting aside resources
for this plan, the company is able to avert current and future risks. A good plan guides the
company in the adoption of risk management strategies such as insurance. It also encourages
compliance by the business company’s teams. The implementation of risk management
encourages the fulfilment of business goals because it scrutinizes all areas of Aztek.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
2.1 Outsourcing Cloud Computing
Economies of scale in cloud computing advocate for reduced costs for IT systems as an
operational risk management tactic. Risks present liabilities and high cost of management
(Benlian & Hess, 2011). Making wrong decisions about the IT capacity needs for Aztek
contributes to the risk factors. Websites operating on common applications like ecommerce
are at a high risk of manipulation from cybercriminals. An effective transfer of IT
app1.lications requires a reliable and safe infrastructure system. The company needs updated
cloud solutions for its mobile devices, webservers, and data storage or recovery. These must
be free from fraud. Making company websites accessible to multilevel, multidimensional and
group systems requires effective models within the legal framework. The development,
configuration and administration of applications in the global environment include privacy.
2.2 Transfer of IT Applications
Samandari, Havas, & Harle ( 2016) identify future risks in the banking industry to identify
technological disruptions among the issues of focus. Although innovation provides solutions
to banks and services, it presents fresh challenges every day. Aztek deals with metadata and
technology helps in portfolio management, detecting inconsistencies and making projections.
Accuracy in the banking sector is a necessity and automated machines such as the ATM and
mobile banking cannot afford to make mistakes. IT applications lower the risks giving the
bank a competitive advantage. Of concern are privacy issues, data protection and error free
business modelling.
2.3 Definition of Risk
E-commerce is a platform for business engagements using the internet (Chiu, Wang, Fang, &
Huang, 2014). Cloud computing used in the financial sector include the website links and
knowledge management systems. These allow for third party access hence security and
training concerns emerge. The use of cloud computing in banking services is questionable
because of the banking business model. Banks are financial companies but they also stand out
as well as high-risk businesses.
Economies of scale in cloud computing advocate for reduced costs for IT systems as an
operational risk management tactic. Risks present liabilities and high cost of management
(Benlian & Hess, 2011). Making wrong decisions about the IT capacity needs for Aztek
contributes to the risk factors. Websites operating on common applications like ecommerce
are at a high risk of manipulation from cybercriminals. An effective transfer of IT
app1.lications requires a reliable and safe infrastructure system. The company needs updated
cloud solutions for its mobile devices, webservers, and data storage or recovery. These must
be free from fraud. Making company websites accessible to multilevel, multidimensional and
group systems requires effective models within the legal framework. The development,
configuration and administration of applications in the global environment include privacy.
2.2 Transfer of IT Applications
Samandari, Havas, & Harle ( 2016) identify future risks in the banking industry to identify
technological disruptions among the issues of focus. Although innovation provides solutions
to banks and services, it presents fresh challenges every day. Aztek deals with metadata and
technology helps in portfolio management, detecting inconsistencies and making projections.
Accuracy in the banking sector is a necessity and automated machines such as the ATM and
mobile banking cannot afford to make mistakes. IT applications lower the risks giving the
bank a competitive advantage. Of concern are privacy issues, data protection and error free
business modelling.
2.3 Definition of Risk
E-commerce is a platform for business engagements using the internet (Chiu, Wang, Fang, &
Huang, 2014). Cloud computing used in the financial sector include the website links and
knowledge management systems. These allow for third party access hence security and
training concerns emerge. The use of cloud computing in banking services is questionable
because of the banking business model. Banks are financial companies but they also stand out
as well as high-risk businesses.

Figure 2: Risk Management Strategy development for Aztek
A risk in this case is the unexpected occurrence, which may hinder the successful
implementation of objective 2 of the planned portfolio. The foreseen danger may occur in any
form hence there is no certain definition of its magnitude or specific. The planning process
involves a cycle process of taking actions against the challenges and evaluating the controls.
This is a flow showing the mission, strategy, goals and goals of Aztek as a company and its
IT plans. Stakeholders play a key role in defining the process.
Figure 3: Aztek Stakeholders
2. 4 Regulatory measures and Best practice
Licensed under the Australian Banking Act, the financial regulations affect its operations
(Hooper, Martini, & Choo, 2013). Aztek also designs risks with consideration for the finance
Define the risk
Perform risk assessment planWrite a plan
Risk assessment team
IT department focusAssemble team
Execute plan
Determine the risk factorsRisk generation
Categories of the risksRationaize the list
Prioritize and rank
Write response plan
Review the process ( monitoring and controls)
Aztek
Stakeholders
Investors
Customers
Suppliers
Employees
A risk in this case is the unexpected occurrence, which may hinder the successful
implementation of objective 2 of the planned portfolio. The foreseen danger may occur in any
form hence there is no certain definition of its magnitude or specific. The planning process
involves a cycle process of taking actions against the challenges and evaluating the controls.
This is a flow showing the mission, strategy, goals and goals of Aztek as a company and its
IT plans. Stakeholders play a key role in defining the process.
Figure 3: Aztek Stakeholders
2. 4 Regulatory measures and Best practice
Licensed under the Australian Banking Act, the financial regulations affect its operations
(Hooper, Martini, & Choo, 2013). Aztek also designs risks with consideration for the finance
Define the risk
Perform risk assessment planWrite a plan
Risk assessment team
IT department focusAssemble team
Execute plan
Determine the risk factorsRisk generation
Categories of the risksRationaize the list
Prioritize and rank
Write response plan
Review the process ( monitoring and controls)
Aztek
Stakeholders
Investors
Customers
Suppliers
Employees
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

industry laws for credit facilities, labour laws, customer relations and banking services apply.
The harmonization is under the:
Good governance and conduct
Privacy and personal data protection
Business regulations and operations
E-commerce global regulations
3.0 Project Impact on Current Security
Aztek strategic risks cover wide areas including corporate banking, which accommodates for
its plans to venture into business alliances. Top on its plan is institutional compliance in
which the Bank fulfils its responsibilities of implementing, managing and providing financial
security (Rittinghouse & Ransome, 2016). The IT outsourcing plan expounds on its agenda of
providing reliable information to the stakeholders. Awareness creation and the
implementation of risk control is important for both internal and external stakeholders. The
bank has in place a system of risk management for its internal operations but it needs an
elaborate framework for an external IT related plan.
3.1 Current plans
Azteks Risk management plan comprises of an overall organizational design as well as the
departmental breakdown. The framework covers financial risks, governance, credit,
developmental, strategic and operational risk levels. This plan derives its motivation from the
global threats faced by the financial industry. Top on its list is the liquidity risk followed by
technology and organized crime (PWC, 2017). The Australian banking service is an industry,
which revolves around the consumer. Efficiency is an important factor in its value chain.
Innovation also has a major role in organizations and is a best practice for the banking
industry. Aztek as a company has a risk management team whose responsibility features:
A risk framework for Aztek and the financial industry
Development of a risk strategy and treatment plan
Oversight of the risk management agenda
Monitoring and ensuring compliance of the plan
Coordinating risk management activities across the business
The harmonization is under the:
Good governance and conduct
Privacy and personal data protection
Business regulations and operations
E-commerce global regulations
3.0 Project Impact on Current Security
Aztek strategic risks cover wide areas including corporate banking, which accommodates for
its plans to venture into business alliances. Top on its plan is institutional compliance in
which the Bank fulfils its responsibilities of implementing, managing and providing financial
security (Rittinghouse & Ransome, 2016). The IT outsourcing plan expounds on its agenda of
providing reliable information to the stakeholders. Awareness creation and the
implementation of risk control is important for both internal and external stakeholders. The
bank has in place a system of risk management for its internal operations but it needs an
elaborate framework for an external IT related plan.
3.1 Current plans
Azteks Risk management plan comprises of an overall organizational design as well as the
departmental breakdown. The framework covers financial risks, governance, credit,
developmental, strategic and operational risk levels. This plan derives its motivation from the
global threats faced by the financial industry. Top on its list is the liquidity risk followed by
technology and organized crime (PWC, 2017). The Australian banking service is an industry,
which revolves around the consumer. Efficiency is an important factor in its value chain.
Innovation also has a major role in organizations and is a best practice for the banking
industry. Aztek as a company has a risk management team whose responsibility features:
A risk framework for Aztek and the financial industry
Development of a risk strategy and treatment plan
Oversight of the risk management agenda
Monitoring and ensuring compliance of the plan
Coordinating risk management activities across the business
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Carrying out internal audits for new risk framework
3.2 IT Security Risk Factors
IT Security Policies and Procedures at the company also have structures laid out 3 years ago.
Its focus was initially on risk assessment but industry trends indicate the importance of risk
management. Its agenda was to address gaps in the infrastructure and they include three
levels namely, the infrastructural, software application and development (Zissis & Lekkas,
2012). Cloud computing is an advanced technology that falls under this docket. As a software
model, it comes with a structure and model that is distinct and critical to Aztek IT systems. It
comprises of the change in technology featuring systems designed for the banking services.
This change comes from demands in the global sector.
The complexity of technology systems and applications calls for risk management by
leveraging the company installations with global expectations. Risk assessment leads to
strategic approaches to combat and deal with the impending and potential risks. Supply chain
risks are inevitable and corporate governance regulations allow the bank to undertake these
risk analysis and implementation. The drivers of value creation in risk management is the
stakeholder who comprises of large and small companies (Upper, 2011). Risk assessment
considers:
Possible situations that could happen
Process of his could occur
What impact it could have on the system
Solution to this problem
3.3 The New Plan
In the new plan, risk management considers the risk assessment factors as well as crisis
management using a modern approach (Bessis, 2011). It incorporates liquidity risk
management and the use of technology services and products. The growth of the online
business brings fresh risks for the financial IT systems because consumers now have to make
most of their transactions using credit cards. Online transaction risks include credit risks,
market challenges, operational and liquidity challenges. The contemporary system has
3.2 IT Security Risk Factors
IT Security Policies and Procedures at the company also have structures laid out 3 years ago.
Its focus was initially on risk assessment but industry trends indicate the importance of risk
management. Its agenda was to address gaps in the infrastructure and they include three
levels namely, the infrastructural, software application and development (Zissis & Lekkas,
2012). Cloud computing is an advanced technology that falls under this docket. As a software
model, it comes with a structure and model that is distinct and critical to Aztek IT systems. It
comprises of the change in technology featuring systems designed for the banking services.
This change comes from demands in the global sector.
The complexity of technology systems and applications calls for risk management by
leveraging the company installations with global expectations. Risk assessment leads to
strategic approaches to combat and deal with the impending and potential risks. Supply chain
risks are inevitable and corporate governance regulations allow the bank to undertake these
risk analysis and implementation. The drivers of value creation in risk management is the
stakeholder who comprises of large and small companies (Upper, 2011). Risk assessment
considers:
Possible situations that could happen
Process of his could occur
What impact it could have on the system
Solution to this problem
3.3 The New Plan
In the new plan, risk management considers the risk assessment factors as well as crisis
management using a modern approach (Bessis, 2011). It incorporates liquidity risk
management and the use of technology services and products. The growth of the online
business brings fresh risks for the financial IT systems because consumers now have to make
most of their transactions using credit cards. Online transaction risks include credit risks,
market challenges, operational and liquidity challenges. The contemporary system has

configurations and computer applications to address these issues. Risk management planning
highlights the possible risk avenues in order to describe concrete solutions.
Outsourcing IT is a major factor affecting Azteks financials and business performance. Its
outsourcing framework is an interesting business model that involves a third party service
provider. Cloud computing is a new approach to collective operations. IT comprise of an
innovative structure that involves a third party supplier. This means the introduction of a new
security plan for Aztek communication and information systems plan. It starts with the
identification of its security threats and quality business processes. This brings in the IT and
Information Systems configuration.
3.4 Challenges
Advanced technology challenges keep advancing over time. This needs strategy
improvements to tackle its complex nature. The introduction of collective computing systems
provides opportunities and challenges. The new business model targets deeper connectivity
and quality management (Bessis, 2011). Reputable banks prepare for uncertainties across
through risk management services and products. Online credit risks include the protection of
customer’s personal data and unauthorized access to credit card data.
a) Value Creation
Reputational risks include loss of respect in public image or consumer trust. This happens
when the stakeholders question the capability of Aztek to carry out its financial services
effectively. Reports about the bank or its customers losing data gives a negative image on the
company. It gives a negative impression of the brand and customers lose confidence in the
company. The company needs a system for detecting crime and credit underwriting. Having
an early warning application gives it an edge over the competitions. In the IT financial
industry, having insight on the potential risks for outsourcing services is important (Low,
Chen, & Wu, 2011).
b) Operational risks
The introduction of an external cloud process brings new changes such as the introduction of
new people, systems and procedures. Change Management arrests the impending risks arising
from human and computer generated risks. The computing systems could relay incorrect data
highlights the possible risk avenues in order to describe concrete solutions.
Outsourcing IT is a major factor affecting Azteks financials and business performance. Its
outsourcing framework is an interesting business model that involves a third party service
provider. Cloud computing is a new approach to collective operations. IT comprise of an
innovative structure that involves a third party supplier. This means the introduction of a new
security plan for Aztek communication and information systems plan. It starts with the
identification of its security threats and quality business processes. This brings in the IT and
Information Systems configuration.
3.4 Challenges
Advanced technology challenges keep advancing over time. This needs strategy
improvements to tackle its complex nature. The introduction of collective computing systems
provides opportunities and challenges. The new business model targets deeper connectivity
and quality management (Bessis, 2011). Reputable banks prepare for uncertainties across
through risk management services and products. Online credit risks include the protection of
customer’s personal data and unauthorized access to credit card data.
a) Value Creation
Reputational risks include loss of respect in public image or consumer trust. This happens
when the stakeholders question the capability of Aztek to carry out its financial services
effectively. Reports about the bank or its customers losing data gives a negative image on the
company. It gives a negative impression of the brand and customers lose confidence in the
company. The company needs a system for detecting crime and credit underwriting. Having
an early warning application gives it an edge over the competitions. In the IT financial
industry, having insight on the potential risks for outsourcing services is important (Low,
Chen, & Wu, 2011).
b) Operational risks
The introduction of an external cloud process brings new changes such as the introduction of
new people, systems and procedures. Change Management arrests the impending risks arising
from human and computer generated risks. The computing systems could relay incorrect data
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

or it could leak information to criminals. Data management solves this problem by providing
security installations, making changes on personal data safety, permits or licenses. It checks
the facilities, capital, space, emergency, and the operational environment.
c) Liquidity risk
The reduction of losses is important for the business because it upholds the company’s assets
and customers. Liquidity risks include daily loses in cash transactions. Security installations
in mobile banking is an effort to reduce these risks. Globally secure mobile and internet
banking is a problem. Aztek needs concrete plans for this.
d) Credit risks
This covers the largest risk factor for banks in the global system. Customer’s access services
through cloud systems and installation applications. Its dangers come from loans, foreign
exchange, swiping, equities, trade financing and forex. The modern consumers uses the credit
card services for online shopping and payments. Banks face threats from unsuccessful
transactions arising from failed processes. The introduction of mobile banking services on
mobile devices is due to customer demands, and market changes. Other risks in credit loans
include credit delays, the loss of funds due to credit transactions, calculations, exchange rates
and exchange value settlement different.
e) Market risks
Economic recession and financial trends determine the pricing, interest rates, forex rates and
fines. Placed on consumers by the bank it brings about fluctuations in currency, commodity
and equity. The contemporary consumer prefers low interest costs and banks, which have
long-term strategies against their competition. Business risks include national, regional and
global management issues. There are risks arising from systematic risks, which affect the
economy of the bank. The external environment such as cloud computing shapes the trend in
the market systems. It comprise of perceived risks such as failed investor risks (Fahlenbrach
& Stiultz, 2011).
f) Compliance
security installations, making changes on personal data safety, permits or licenses. It checks
the facilities, capital, space, emergency, and the operational environment.
c) Liquidity risk
The reduction of losses is important for the business because it upholds the company’s assets
and customers. Liquidity risks include daily loses in cash transactions. Security installations
in mobile banking is an effort to reduce these risks. Globally secure mobile and internet
banking is a problem. Aztek needs concrete plans for this.
d) Credit risks
This covers the largest risk factor for banks in the global system. Customer’s access services
through cloud systems and installation applications. Its dangers come from loans, foreign
exchange, swiping, equities, trade financing and forex. The modern consumers uses the credit
card services for online shopping and payments. Banks face threats from unsuccessful
transactions arising from failed processes. The introduction of mobile banking services on
mobile devices is due to customer demands, and market changes. Other risks in credit loans
include credit delays, the loss of funds due to credit transactions, calculations, exchange rates
and exchange value settlement different.
e) Market risks
Economic recession and financial trends determine the pricing, interest rates, forex rates and
fines. Placed on consumers by the bank it brings about fluctuations in currency, commodity
and equity. The contemporary consumer prefers low interest costs and banks, which have
long-term strategies against their competition. Business risks include national, regional and
global management issues. There are risks arising from systematic risks, which affect the
economy of the bank. The external environment such as cloud computing shapes the trend in
the market systems. It comprise of perceived risks such as failed investor risks (Fahlenbrach
& Stiultz, 2011).
f) Compliance
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Contracts address issues such as leases and sponsorship for the projects. In a global
organization such as Aztek, the Australian regulations and statutory laws apply
(Governement, 2015). These involve employees and the community as well as company
installations. Engaging in a business model with an external service provider has challenges
among them is the challenge of breach of contract. The Codes of conduct ensure compliance
to the rules. Clients need a clear understanding of the terms and penalties, loss of revenue
purchasing practices, and litigation challenges.
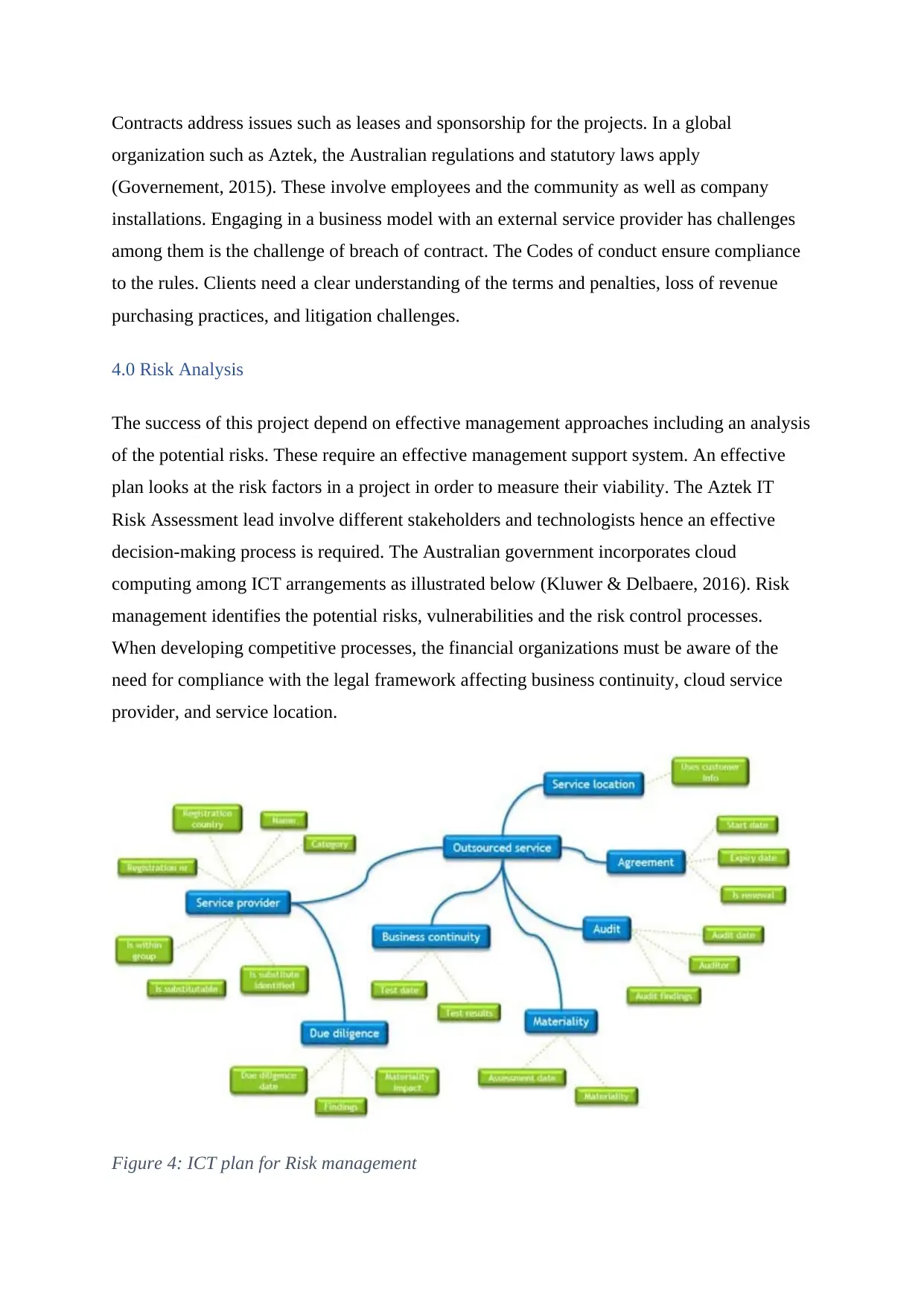
4.0 Risk Analysis
The success of this project depend on effective management approaches including an analysis
of the potential risks. These require an effective management support system. An effective
plan looks at the risk factors in a project in order to measure their viability. The Aztek IT
Risk Assessment lead involve different stakeholders and technologists hence an effective
decision-making process is required. The Australian government incorporates cloud
computing among ICT arrangements as illustrated below (Kluwer & Delbaere, 2016). Risk
management identifies the potential risks, vulnerabilities and the risk control processes.
When developing competitive processes, the financial organizations must be aware of the
need for compliance with the legal framework affecting business continuity, cloud service
provider, and service location.
Figure 4: ICT plan for Risk management
organization such as Aztek, the Australian regulations and statutory laws apply
(Governement, 2015). These involve employees and the community as well as company
installations. Engaging in a business model with an external service provider has challenges
among them is the challenge of breach of contract. The Codes of conduct ensure compliance
to the rules. Clients need a clear understanding of the terms and penalties, loss of revenue
purchasing practices, and litigation challenges.
4.0 Risk Analysis
The success of this project depend on effective management approaches including an analysis
of the potential risks. These require an effective management support system. An effective
plan looks at the risk factors in a project in order to measure their viability. The Aztek IT
Risk Assessment lead involve different stakeholders and technologists hence an effective
decision-making process is required. The Australian government incorporates cloud
computing among ICT arrangements as illustrated below (Kluwer & Delbaere, 2016). Risk
management identifies the potential risks, vulnerabilities and the risk control processes.
When developing competitive processes, the financial organizations must be aware of the
need for compliance with the legal framework affecting business continuity, cloud service
provider, and service location.
Figure 4: ICT plan for Risk management

4.1 The Risks, Vulnerabilities and Threats
Cloud computing and IT installation of technology from external sources poses risks. The
project plans to make installations on laptops, pads, tablets and mobile phone devices. Each
of these devices face challenges and exposure to malware and other effects. The
incorporation of a corporate-wide email for archive systems need a compatible and compliant
design. Upgrading applications on desktop operating systems also needs IT Security Policies
and procedures. In order to understand the risks, it is crucial to understand vulnerabilities,
threats and risks (Grobauer, Walloschek, & Stocker, 2011). This clarification provides a
guide on the types of risks involved in the process.
Threats
This is a potential cause of alarm for an organization. It includes system interference.
Different agents of these threats include criminals, bank fraudsters and organized criminals.
Aztek needs a plan that foresees this as a future challenge for the organization. The legal
framework admonishes the financial service provider from compromising client assets. In
order to prevent this failure, and combat theft, the plan makes provision for better security
software and the training of its employees with codes of conduct for risk aversion (Cappelli,
Moore, & Trzeciak, 2012). Employees can also become threats if they are not aware of the
risks. Competitors often use employees to steal crucial information and company data. The
company needs protection from hacking systems and unauthorised access. In some regions,
access by government and terror groups (Martini & Choo, 2012). Contemporary criminals
have the capacity to fabricate identity for unauthorised entries.
Vulnerabilities
Defined as weaknesses characterising a system, the vulnerabilities expose the system to
threats. An example is weak passwords, insecure online banking and constant cyber-attacks.
Data security requires privacy protection as one of the major safety measures (Chen & Zhao,
2012). This service delivery approach is crucial for cloud computing which involves different
IT experts and networking systems. Public clouding is vulnerable to software bugs and
information leaks. Broken financial processes also expose the system to such threats. This
calls for changes in hardware and software installations. Aztek needs effective measures such
as backup systems and prevention of human errors. As part of its customer service, the brand
Cloud computing and IT installation of technology from external sources poses risks. The
project plans to make installations on laptops, pads, tablets and mobile phone devices. Each
of these devices face challenges and exposure to malware and other effects. The
incorporation of a corporate-wide email for archive systems need a compatible and compliant
design. Upgrading applications on desktop operating systems also needs IT Security Policies
and procedures. In order to understand the risks, it is crucial to understand vulnerabilities,
threats and risks (Grobauer, Walloschek, & Stocker, 2011). This clarification provides a
guide on the types of risks involved in the process.
Threats
This is a potential cause of alarm for an organization. It includes system interference.
Different agents of these threats include criminals, bank fraudsters and organized criminals.
Aztek needs a plan that foresees this as a future challenge for the organization. The legal
framework admonishes the financial service provider from compromising client assets. In
order to prevent this failure, and combat theft, the plan makes provision for better security
software and the training of its employees with codes of conduct for risk aversion (Cappelli,
Moore, & Trzeciak, 2012). Employees can also become threats if they are not aware of the
risks. Competitors often use employees to steal crucial information and company data. The
company needs protection from hacking systems and unauthorised access. In some regions,
access by government and terror groups (Martini & Choo, 2012). Contemporary criminals
have the capacity to fabricate identity for unauthorised entries.
Vulnerabilities
Defined as weaknesses characterising a system, the vulnerabilities expose the system to
threats. An example is weak passwords, insecure online banking and constant cyber-attacks.
Data security requires privacy protection as one of the major safety measures (Chen & Zhao,
2012). This service delivery approach is crucial for cloud computing which involves different
IT experts and networking systems. Public clouding is vulnerable to software bugs and
information leaks. Broken financial processes also expose the system to such threats. This
calls for changes in hardware and software installations. Aztek needs effective measures such
as backup systems and prevention of human errors. As part of its customer service, the brand
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





