Network Design and Implementation Plan for Talon Textile Fasteners
VerifiedAdded on 2020/10/20
|19
|3503
|206
Project
AI Summary
This project outlines a comprehensive network design and implementation plan for Talon Textile Fasteners (TTF), a growing peg manufacturing company aiming to upgrade its IT infrastructure. The plan includes a directory structure, site specifications for multiple locations, and organizational units for managing users and resources. It details server specifications, comparing Dell and Lenovo hardware options, and recommends a single physical server with multiple virtual machines for file sharing, printing, database management, backups, web hosting, applications, and email services. The project also covers approval sign-off, a server build task list, and a server test plan. Furthermore, it specifies router requirements, cable types, and protocols used, along with traffic monitoring processes. Security policies, including perimeter design, remote access, and site-to-site links, are defined, emphasizing a defense-in-depth approach and security auditing. The plan addresses threat identification, risk analysis, and response procedures. Finally, it includes user documentation, project sign-off, and ongoing maintenance considerations.

Network Design and Implementation Plan
For
Talon Textile Fasteners
For
Talon Textile Fasteners
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
a) Project Summary 3
b) Network Design and Supporting Documents 3
c) Directory Structure 4
Sites 4
Organizational Units 4
Groups 5
d) Server Specifications 6
Number and Location of Virtual and Physical Servers7
Roles of Servers 7
Approval Sign off Document8
e) Server Build Task List Template 9
f) Server Test Plan 9
g) Server Maintenance Plan 10
h) Router Specifications 10
Plan for Implementation 10
Cables Types Required 10
Protocols Used 11
Traffic Monitoring Process 11
i) Security Policy and Plan 11
Perimeter Design 11
Remote Access 11
Site to Site Links 12
Defense in Depth 13
Security Auditing 13
Threat Identification 13
Risk Analysis 13
Response Procedure 14
j) User Documents 14
Project Sign Off 15
k) Ongoing Maintenance 16
l) Reference 17
a) Project Summary 3
b) Network Design and Supporting Documents 3
c) Directory Structure 4
Sites 4
Organizational Units 4
Groups 5
d) Server Specifications 6
Number and Location of Virtual and Physical Servers7
Roles of Servers 7
Approval Sign off Document8
e) Server Build Task List Template 9
f) Server Test Plan 9
g) Server Maintenance Plan 10
h) Router Specifications 10
Plan for Implementation 10
Cables Types Required 10
Protocols Used 11
Traffic Monitoring Process 11
i) Security Policy and Plan 11
Perimeter Design 11
Remote Access 11
Site to Site Links 12
Defense in Depth 13
Security Auditing 13
Threat Identification 13
Risk Analysis 13
Response Procedure 14
j) User Documents 14
Project Sign Off 15
k) Ongoing Maintenance 16
l) Reference 17
a) Project Summary
Talon Textile Fasteners (TTF) are a peg manufacturing company that has steadily grown from a small
organisation into a multi-million-dollar enterprise. Whilst never being on the forefront of
technological advances TTF looks to upgrade their IT system in parallels with their growth as a
company. In order to keep up with global technological advances TFF has employed Skillage IT to
improve its IT infrastructure.
b) Network Design and Supporting Documents
Talon Textile Fasteners (TTF) are a peg manufacturing company that has steadily grown from a small
organisation into a multi-million-dollar enterprise. Whilst never being on the forefront of
technological advances TTF looks to upgrade their IT system in parallels with their growth as a
company. In order to keep up with global technological advances TFF has employed Skillage IT to
improve its IT infrastructure.
b) Network Design and Supporting Documents
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

c) Directory Structure
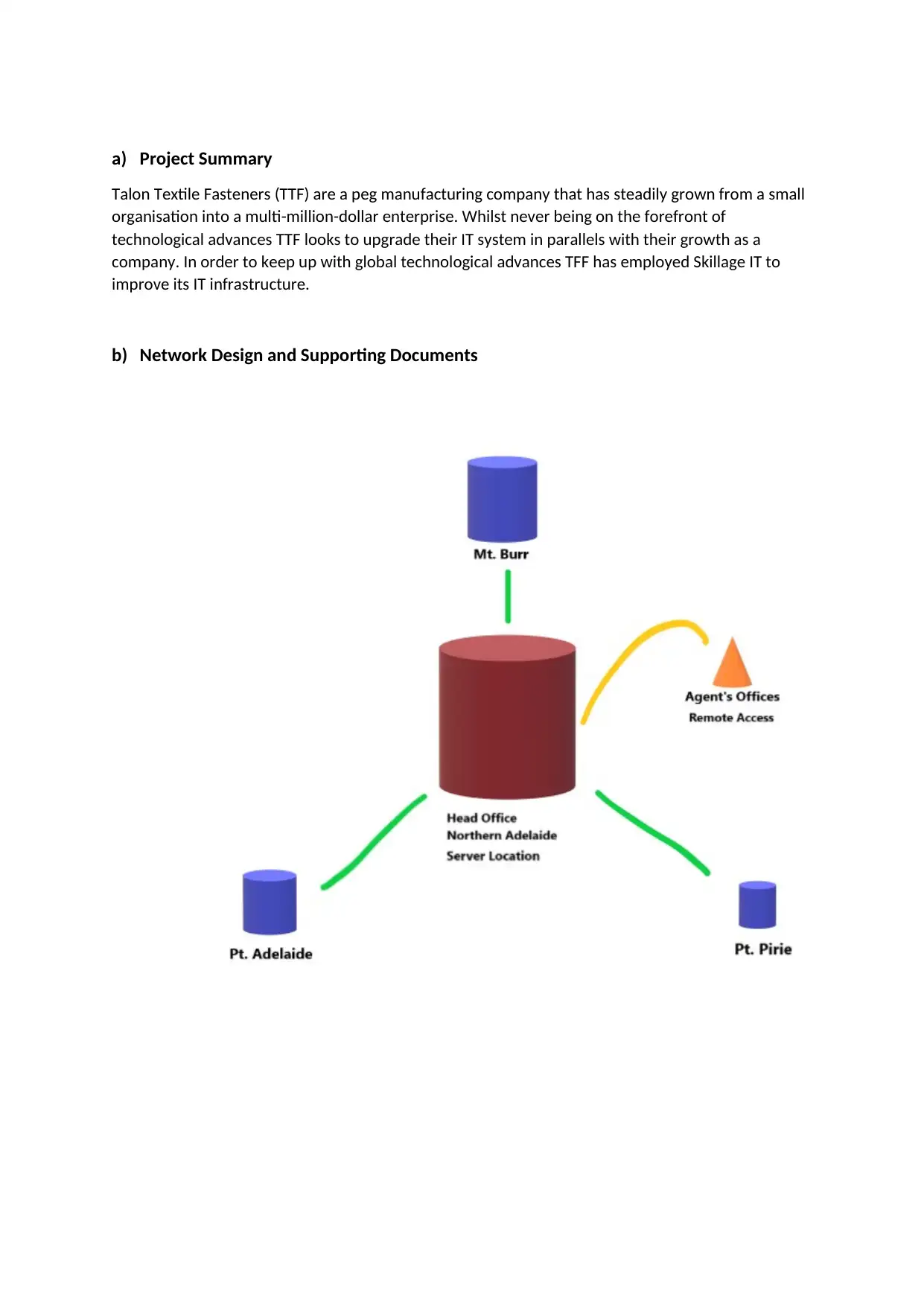
i. Sites
The separate sites for the TTF include:
Northern Adelaide
Head Office
Location of the Servers
40 staff require network access
Mt. Burr
Building a Saw Mill/Expanding the site
6 staff require network access
Pt. Adelaide
6 staff require network access
Pt. Pirie
1 staff accessing the network
Remote Access
Agents dotted around the globe require network access through VPN and remote
access.
ii. Organisational Units
An Organisational Unit (OU) is an Active Directory subdivision into which administrators can
place users, groups, computers and other organisational units such as printers. Here are the
purposed subdivisions for TTF:
Upper Management – CEO, CFO, CIO
Lower Management – Site Management
IT Department – Network Administration
Remote Agents – Agents who require remote access due to geographical location
Other Staff – Remaining staff located at sites who require access to the network
i. Sites
The separate sites for the TTF include:
Northern Adelaide
Head Office
Location of the Servers
40 staff require network access
Mt. Burr
Building a Saw Mill/Expanding the site
6 staff require network access
Pt. Adelaide
6 staff require network access
Pt. Pirie
1 staff accessing the network
Remote Access
Agents dotted around the globe require network access through VPN and remote
access.
ii. Organisational Units
An Organisational Unit (OU) is an Active Directory subdivision into which administrators can
place users, groups, computers and other organisational units such as printers. Here are the
purposed subdivisions for TTF:
Upper Management – CEO, CFO, CIO
Lower Management – Site Management
IT Department – Network Administration
Remote Agents – Agents who require remote access due to geographical location
Other Staff – Remaining staff located at sites who require access to the network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

iii. Groups
Administrators Group – Members of the Administrators group have complete and
unrestricted access to the computer, or if the computer is promoted to a domain controller,
members have unrestricted access to the domain.
Account Operators Group – Members of this group can create and modify most types of
accounts, including those of users, local groups, and global groups, and members can log in
locally to domain controllers.
Backup Operator Group – Members of the Backup Operators group can back up and restore
all files on a computer, regardless of the permissions that protect those files. Backup
Operators also can log on to and shut down the computer.
Domain Computers – This group can include all computers and servers that have joined the
domain, excluding domain controllers.
Domain Controllers – The Domain Controllers group can include all domain controllers in
the domain. New domain controllers are automatically added to this group.
Domain Users – The Domain Users group includes all user accounts in a domain. When you
create a user account in a domain, it is automatically added to this group.
Protected Users – Members of the Protected Users group are afforded additional protection
against the compromise of credentials during authentication processes.
Remote Desktop Users – The Remote Desktop Users group on an RD Session Host server is
used to grant users and groups permissions to remotely connect to an RD Session Host
server.
Administrators Group – Members of the Administrators group have complete and
unrestricted access to the computer, or if the computer is promoted to a domain controller,
members have unrestricted access to the domain.
Account Operators Group – Members of this group can create and modify most types of
accounts, including those of users, local groups, and global groups, and members can log in
locally to domain controllers.
Backup Operator Group – Members of the Backup Operators group can back up and restore
all files on a computer, regardless of the permissions that protect those files. Backup
Operators also can log on to and shut down the computer.
Domain Computers – This group can include all computers and servers that have joined the
domain, excluding domain controllers.
Domain Controllers – The Domain Controllers group can include all domain controllers in
the domain. New domain controllers are automatically added to this group.
Domain Users – The Domain Users group includes all user accounts in a domain. When you
create a user account in a domain, it is automatically added to this group.
Protected Users – Members of the Protected Users group are afforded additional protection
against the compromise of credentials during authentication processes.
Remote Desktop Users – The Remote Desktop Users group on an RD Session Host server is
used to grant users and groups permissions to remotely connect to an RD Session Host
server.

d) Server Specification
Two proposals using different hardware vendors – include:
Dell PowerEdge T440
Price: $9,316.56
Base: PowerEdge T440 Server
Motherboard: PowerEdge T440 MLK Motherboard, V2
Processor: Intel Xeon Silver 4215 2.5G, 8C/16T, 9.6GT/s, 11M Cache, Turbo, HT (85W) DDR4-
2400
Additional Processor: Intel® Xeon® Silver 4215 2.5G, 8C/16T, 9.6GT/s, 11M Cache, Turbo, HT
(85W) DDR4-2400
Memory DIMM Type and Speed: 2666MT/s RDIMMs
Memory: 2 x 8GB RDIMM, 2666MT/s, Single Rank
RAID: C7, Unconfigured RAID for HDDs or SSDs (Mixed Drive Types Allowed)
Hard Drive: 16TB Hard Drive 7K SAS 12Gbps 512e 3.5in Hot-Plug
NIC: Dual-Port 1GbE On-Board LOM
Operating System: Windows Server® 2019 Standard,16CORE,FI,No Med,No CAL, Multi
Language
Optical Drive: DVD +/-RW, SATA, Internal
(Dell PowerEdge T440 Tower Server : Servers | Dell Australia n.d.)
VS.
ThinkSystem ST250 E-2104G
Price: $4,199.43
Base: ThinkSystem ST250 3.5” Chassis Base
Motherboard: ThinkSystem ST250 Refresh Motherboard
Processor: Intel Xeon E-2288G 8C 95W 3.7GHz Proccessor
Memory: ThinkSystem 32GB TruDDR4 2666MHz (2Rx8, 1.2V) ECC UDIMM
Storage: ThinkSystem M.2 5300 480GB SATA 6Gbps Non-Hot Swap SSD
ThinkSystem ST250 4x3.5" SATA/SAS Backplane
NIC: Dual-Port 1GbE On-Board LOM
Operating System: Windows Server® 2019 Standard,16CORE.
Optical Drive: DVD +/-RW, SATA, Internal
(DCSC CTO | Lenovo Australia n.d.)
Two proposals using different hardware vendors – include:
Dell PowerEdge T440
Price: $9,316.56
Base: PowerEdge T440 Server
Motherboard: PowerEdge T440 MLK Motherboard, V2
Processor: Intel Xeon Silver 4215 2.5G, 8C/16T, 9.6GT/s, 11M Cache, Turbo, HT (85W) DDR4-
2400
Additional Processor: Intel® Xeon® Silver 4215 2.5G, 8C/16T, 9.6GT/s, 11M Cache, Turbo, HT
(85W) DDR4-2400
Memory DIMM Type and Speed: 2666MT/s RDIMMs
Memory: 2 x 8GB RDIMM, 2666MT/s, Single Rank
RAID: C7, Unconfigured RAID for HDDs or SSDs (Mixed Drive Types Allowed)
Hard Drive: 16TB Hard Drive 7K SAS 12Gbps 512e 3.5in Hot-Plug
NIC: Dual-Port 1GbE On-Board LOM
Operating System: Windows Server® 2019 Standard,16CORE,FI,No Med,No CAL, Multi
Language
Optical Drive: DVD +/-RW, SATA, Internal
(Dell PowerEdge T440 Tower Server : Servers | Dell Australia n.d.)
VS.
ThinkSystem ST250 E-2104G
Price: $4,199.43
Base: ThinkSystem ST250 3.5” Chassis Base
Motherboard: ThinkSystem ST250 Refresh Motherboard
Processor: Intel Xeon E-2288G 8C 95W 3.7GHz Proccessor
Memory: ThinkSystem 32GB TruDDR4 2666MHz (2Rx8, 1.2V) ECC UDIMM
Storage: ThinkSystem M.2 5300 480GB SATA 6Gbps Non-Hot Swap SSD
ThinkSystem ST250 4x3.5" SATA/SAS Backplane
NIC: Dual-Port 1GbE On-Board LOM
Operating System: Windows Server® 2019 Standard,16CORE.
Optical Drive: DVD +/-RW, SATA, Internal
(DCSC CTO | Lenovo Australia n.d.)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

i) Number and Location of virtual and Physical Servers
After considering the current size of TTF along with the expected future growth and network
requirements, I recommend that there be one physical server located at Head office in
Northern Adelaide. There will be separate Virtual machines/Servers running on this singular
physical server. I recommended no more than four virtual machines. For future expansion of
the company a second physical server can be bought in order to disperse and increase the
computing power. The virtual servers will be running independent of each other to ensure
maximum security. Hyper-V is my recommendation for Virtualisation software as it runs like
containers and provides maximum security and independence this way.
ii) Roles of servers
Based on the organisation’s requirements, the following virtual servers will be installed:
File Sharing Server – File sharing services make the network more convenient for users. A
file sharing feature allows files to be accessed on the network. The client can then read,
modify, create and write the file back to the server without moving the entire file from the
server to the client. This also acts as a centralised hub for all the organisations quick access
data and information.
Print Server – The Print server allows printers to be shared by clients on the network. With a
print server the company doesn’t require as much printing hardware or maintenance,
therefore saving dollars on unnecessary costs.
Database Server – The Database server refers to the ‘behind the scenes’ application used for
client/server interaction architecture. This application performs the tasks of data analysis,
storage, data manipulation, archiving and other non-user specific tasks. (Beal n.d.)
Backup Server – The Backup server’s role is to ensure data, file, application and database
backups either performed manually, automatically or both.
Web Server – The Web server displays web content to users by storing, processing and
delivering webpages to users through means of hardware and software.
Application Server – The Application server is designed to run applications. These
applications could include, but are not limited to; wed applications, hosting hypervisors and
virtual machines and distributing/monitoring software updates.
Mail Server – The Mail server acts as a system for sending and receiving emails using
standard email protocols.
After considering the current size of TTF along with the expected future growth and network
requirements, I recommend that there be one physical server located at Head office in
Northern Adelaide. There will be separate Virtual machines/Servers running on this singular
physical server. I recommended no more than four virtual machines. For future expansion of
the company a second physical server can be bought in order to disperse and increase the
computing power. The virtual servers will be running independent of each other to ensure
maximum security. Hyper-V is my recommendation for Virtualisation software as it runs like
containers and provides maximum security and independence this way.
ii) Roles of servers
Based on the organisation’s requirements, the following virtual servers will be installed:
File Sharing Server – File sharing services make the network more convenient for users. A
file sharing feature allows files to be accessed on the network. The client can then read,
modify, create and write the file back to the server without moving the entire file from the
server to the client. This also acts as a centralised hub for all the organisations quick access
data and information.
Print Server – The Print server allows printers to be shared by clients on the network. With a
print server the company doesn’t require as much printing hardware or maintenance,
therefore saving dollars on unnecessary costs.
Database Server – The Database server refers to the ‘behind the scenes’ application used for
client/server interaction architecture. This application performs the tasks of data analysis,
storage, data manipulation, archiving and other non-user specific tasks. (Beal n.d.)
Backup Server – The Backup server’s role is to ensure data, file, application and database
backups either performed manually, automatically or both.
Web Server – The Web server displays web content to users by storing, processing and
delivering webpages to users through means of hardware and software.
Application Server – The Application server is designed to run applications. These
applications could include, but are not limited to; wed applications, hosting hypervisors and
virtual machines and distributing/monitoring software updates.
Mail Server – The Mail server acts as a system for sending and receiving emails using
standard email protocols.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Consider there are Four Virtual machines, here is my recommendation for splitting the workload:
VM1 – File + Print Server
VM2 – Mail + Database Server
VM3 – Backup Server
VM4 – Web + Application Server
iii)
Approval Sign Off Document
The signing of this document confirms the acceptance and approval for the purchase and
installation of the below.
Product: Dell PowerEdge T440
Approved by CEO: ___________________________
Date: ___________________________
Approved by CIO: ___________________________
Date: ___________________________
VM1 – File + Print Server
VM2 – Mail + Database Server
VM3 – Backup Server
VM4 – Web + Application Server
iii)
Approval Sign Off Document
The signing of this document confirms the acceptance and approval for the purchase and
installation of the below.
Product: Dell PowerEdge T440
Approved by CEO: ___________________________
Date: ___________________________
Approved by CIO: ___________________________
Date: ___________________________
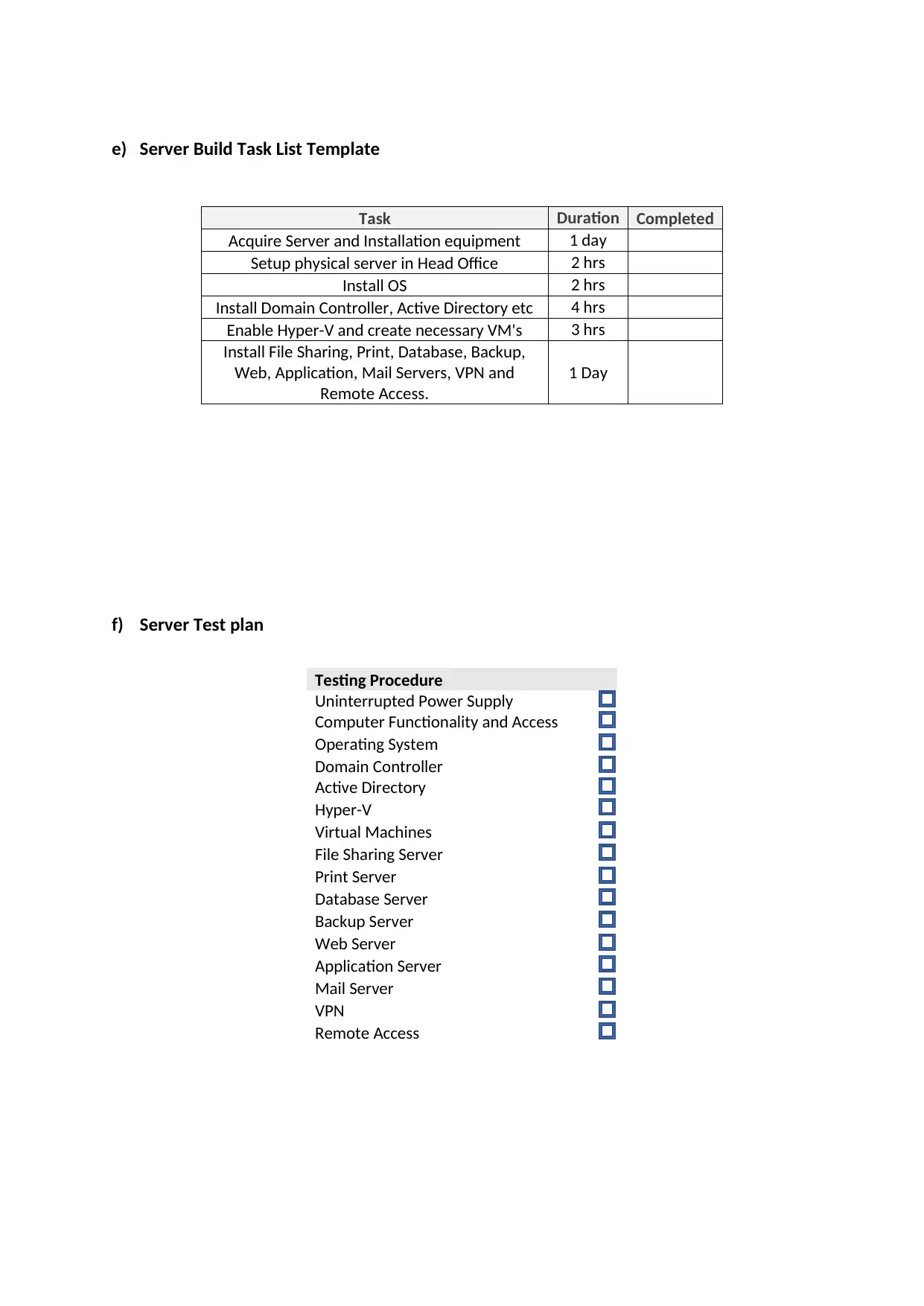
e) Server Build Task List Template
Task Duration Completed
Acquire Server and Installation equipment 1 day
Setup physical server in Head Office 2 hrs
Install OS 2 hrs
Install Domain Controller, Active Directory etc 4 hrs
Enable Hyper-V and create necessary VM's 3 hrs
Install File Sharing, Print, Database, Backup,
Web, Application, Mail Servers, VPN and
Remote Access.
1 Day
f) Server Test plan
Testing Procedure
Uninterrupted Power Supply
Computer Functionality and Access
Operating System
Domain Controller
Active Directory
Hyper-V
Virtual Machines
File Sharing Server
Print Server
Database Server
Backup Server
Web Server
Application Server
Mail Server
VPN
Remote Access
Task Duration Completed
Acquire Server and Installation equipment 1 day
Setup physical server in Head Office 2 hrs
Install OS 2 hrs
Install Domain Controller, Active Directory etc 4 hrs
Enable Hyper-V and create necessary VM's 3 hrs
Install File Sharing, Print, Database, Backup,
Web, Application, Mail Servers, VPN and
Remote Access.
1 Day
f) Server Test plan
Testing Procedure
Uninterrupted Power Supply
Computer Functionality and Access
Operating System
Domain Controller
Active Directory
Hyper-V
Virtual Machines
File Sharing Server
Print Server
Database Server
Backup Server
Web Server
Application Server
Mail Server
VPN
Remote Access
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

g) Server Maintenance plan
A server maintenance plan shall be created by a technical specialist. The plan shall include the
recommended maintenance specified for each piece of equipment to ensure the equipment’s
warranty and best performance. The maintenance plan should cover the following areas:
Scheduled Maintenance
o Physical Maintenance
o Software Maintenance
Updates and patch installation
Backup Maintenance and Integrity
h) Router specifications
The router will require a suitable throughput for the network demands. It will also require a VPN
feature to ensure business data is shielded from unapproved access. A router such as the Cisco
RV345P Duel WAN VPN Router would be suitable.
i) Plan for Implementation
Each Organisation site will have a router. This includes Head Office, Port Pirie, Mt.
Burr and Port Adelaide.
ii) Cable Types Required
The Cable used will be Cat 6 with likely RJ-45 connectors. See the table below for
when to use what type of cable.
Crossove
r Cable
Straight Through
Cable
Router to Router ü
Switch to Switch ü
PC to Router ü
PC to PC ü
PC to Switch ü
Router to Switch ü
iii) Protocols Used
A server maintenance plan shall be created by a technical specialist. The plan shall include the
recommended maintenance specified for each piece of equipment to ensure the equipment’s
warranty and best performance. The maintenance plan should cover the following areas:
Scheduled Maintenance
o Physical Maintenance
o Software Maintenance
Updates and patch installation
Backup Maintenance and Integrity
h) Router specifications
The router will require a suitable throughput for the network demands. It will also require a VPN
feature to ensure business data is shielded from unapproved access. A router such as the Cisco
RV345P Duel WAN VPN Router would be suitable.
i) Plan for Implementation
Each Organisation site will have a router. This includes Head Office, Port Pirie, Mt.
Burr and Port Adelaide.
ii) Cable Types Required
The Cable used will be Cat 6 with likely RJ-45 connectors. See the table below for
when to use what type of cable.
Crossove
r Cable
Straight Through
Cable
Router to Router ü
Switch to Switch ü
PC to Router ü
PC to PC ü
PC to Switch ü
Router to Switch ü
iii) Protocols Used
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TCP – Transmission Control Protocol establishes a network conversation so application
programs can transfer data.
UDP – User Datagram Protocol is a substitute to TCP that is more tolerant and lower
latency
IP – Internet Protocol is designed to act as an addressing protocol for computer
networks.
FTP – File Transfer Protocol allows files to be transferred from one machine to another.
DHCP – Dynamic Host Configuration Protocol is an automated protocol used to assign IP
to devices on a network.
SSH – Secure Shell allows for remote command-line login and remote execution.
SMTP – Simple Mail Transport Protocol is used to send and distribute outgoing Emails.
IMAP – Internet Message Access Protocol is a standard used by clients to retrieve email
and messages from a amil server.
HTTP – Hyper Text Transfer Protocol is designed for transferring a hypertext amongst
two or more systems.
HTTPS – Hyper Text Transfer Protocol Secure is the secure version of HTTP and is used
more often than HTTP for exchanging hypertext.
SNMP – Simple Network Management Protocol is protocol used for monitoring and
managing network devices.
iv) Traffic Monitoring Process
I recommend TTF uses SolarWinds Network Performance Monitor in order to monitor
Network traffic and identify network short-falls, vulnerabilities or possible
improvements. SolarWinds Network Performance Monitor pricing starts at $2,675 and
includes the first year of maintenance. (SolarWinds Makes Powerful Network
Monitoring Accessible to Masses n.d.) An alternative would be to utilise the PRTG
Network Monitor in combination with packet sniffing tools to compile and
analyse network data.
i) Security Policy and Plan
i) Perimeter Design
A perimeter solution requires employees of TTF to assess, analyse and design the best suited
solution for optimal design. Factors such as LAN connectivity, security and performance are
the factors that need analysing and assessing in order to gain the optimal functionality.
ii) Remote access
Software such as RemotePC should be used to ensure that those staff requiring remote
access can access the organisations network without compromising the network.
(Blechynden 2020)
iii) Site to site links
programs can transfer data.
UDP – User Datagram Protocol is a substitute to TCP that is more tolerant and lower
latency
IP – Internet Protocol is designed to act as an addressing protocol for computer
networks.
FTP – File Transfer Protocol allows files to be transferred from one machine to another.
DHCP – Dynamic Host Configuration Protocol is an automated protocol used to assign IP
to devices on a network.
SSH – Secure Shell allows for remote command-line login and remote execution.
SMTP – Simple Mail Transport Protocol is used to send and distribute outgoing Emails.
IMAP – Internet Message Access Protocol is a standard used by clients to retrieve email
and messages from a amil server.
HTTP – Hyper Text Transfer Protocol is designed for transferring a hypertext amongst
two or more systems.
HTTPS – Hyper Text Transfer Protocol Secure is the secure version of HTTP and is used
more often than HTTP for exchanging hypertext.
SNMP – Simple Network Management Protocol is protocol used for monitoring and
managing network devices.
iv) Traffic Monitoring Process
I recommend TTF uses SolarWinds Network Performance Monitor in order to monitor
Network traffic and identify network short-falls, vulnerabilities or possible
improvements. SolarWinds Network Performance Monitor pricing starts at $2,675 and
includes the first year of maintenance. (SolarWinds Makes Powerful Network
Monitoring Accessible to Masses n.d.) An alternative would be to utilise the PRTG
Network Monitor in combination with packet sniffing tools to compile and
analyse network data.
i) Security Policy and Plan
i) Perimeter Design
A perimeter solution requires employees of TTF to assess, analyse and design the best suited
solution for optimal design. Factors such as LAN connectivity, security and performance are
the factors that need analysing and assessing in order to gain the optimal functionality.
ii) Remote access
Software such as RemotePC should be used to ensure that those staff requiring remote
access can access the organisations network without compromising the network.
(Blechynden 2020)
iii) Site to site links
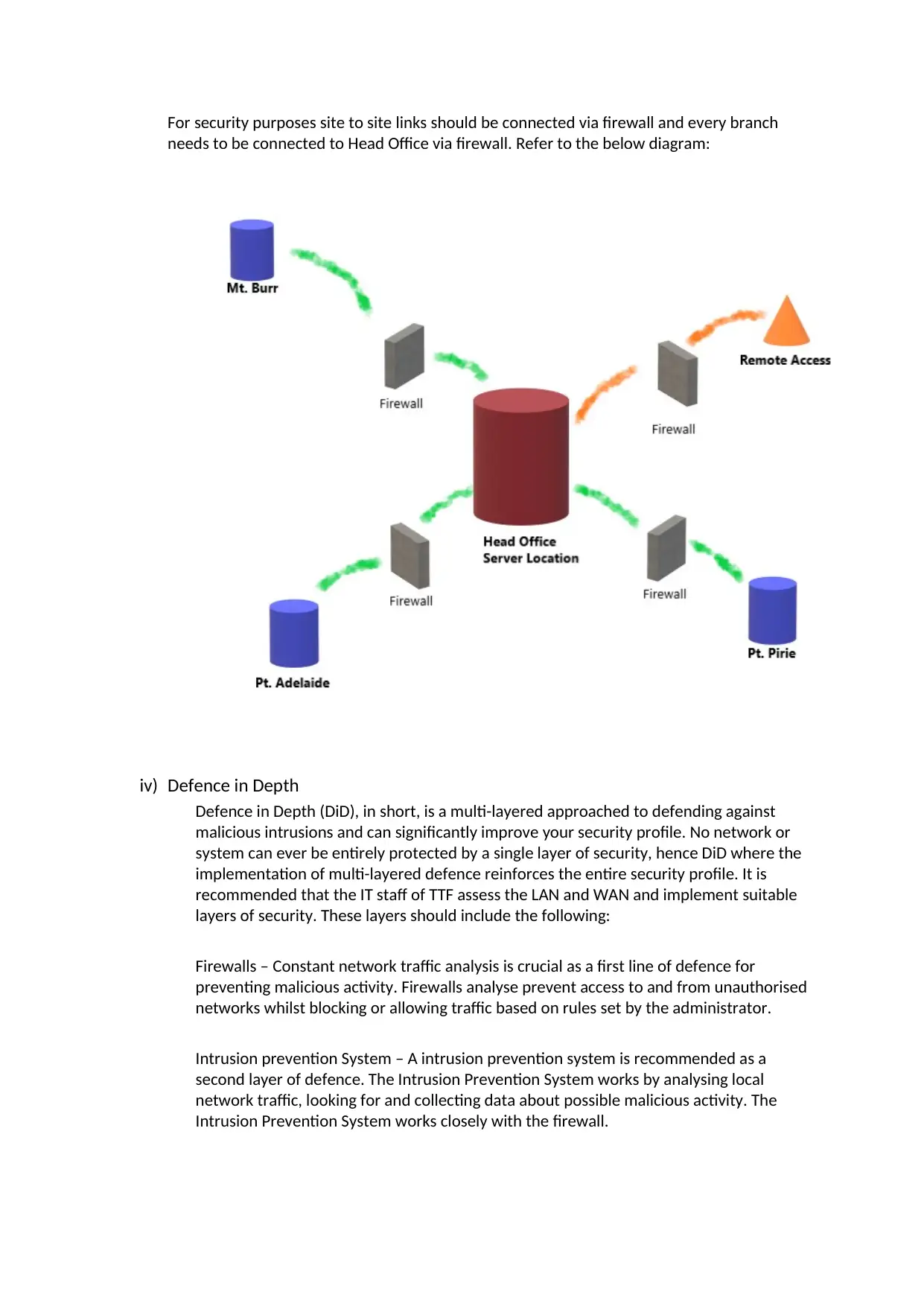
For security purposes site to site links should be connected via firewall and every branch
needs to be connected to Head Office via firewall. Refer to the below diagram:
iv) Defence in Depth
Defence in Depth (DiD), in short, is a multi-layered approached to defending against
malicious intrusions and can significantly improve your security profile. No network or
system can ever be entirely protected by a single layer of security, hence DiD where the
implementation of multi-layered defence reinforces the entire security profile. It is
recommended that the IT staff of TTF assess the LAN and WAN and implement suitable
layers of security. These layers should include the following:
Firewalls – Constant network traffic analysis is crucial as a first line of defence for
preventing malicious activity. Firewalls analyse prevent access to and from unauthorised
networks whilst blocking or allowing traffic based on rules set by the administrator.
Intrusion prevention System – A intrusion prevention system is recommended as a
second layer of defence. The Intrusion Prevention System works by analysing local
network traffic, looking for and collecting data about possible malicious activity. The
Intrusion Prevention System works closely with the firewall.
needs to be connected to Head Office via firewall. Refer to the below diagram:
iv) Defence in Depth
Defence in Depth (DiD), in short, is a multi-layered approached to defending against
malicious intrusions and can significantly improve your security profile. No network or
system can ever be entirely protected by a single layer of security, hence DiD where the
implementation of multi-layered defence reinforces the entire security profile. It is
recommended that the IT staff of TTF assess the LAN and WAN and implement suitable
layers of security. These layers should include the following:
Firewalls – Constant network traffic analysis is crucial as a first line of defence for
preventing malicious activity. Firewalls analyse prevent access to and from unauthorised
networks whilst blocking or allowing traffic based on rules set by the administrator.
Intrusion prevention System – A intrusion prevention system is recommended as a
second layer of defence. The Intrusion Prevention System works by analysing local
network traffic, looking for and collecting data about possible malicious activity. The
Intrusion Prevention System works closely with the firewall.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





