Uber Security Breach: Analysis of Problem Solving Techniques
VerifiedAdded on 2020/10/23
|12
|3308
|422
Report
AI Summary
This report analyzes the security breach experienced by Uber in the UK in October 2016, where 2.7 million users were affected. It investigates the problem-solving techniques used by Uber, particularly the zero-trust approach, and critically evaluates its effectiveness. The report explores alternative approaches Uber could have employed, such as network security models and the 5 Why model, and conducts a SAF (Suitability, Acceptability, and Feasibility) analysis to determine the best approach. Furthermore, it includes a stock market analysis to assess the impact of the breach on Uber's share price and investor reaction. The report concludes with recommendations for Uber to improve its cybersecurity practices and prevent future breaches, emphasizing the importance of proactive measures and robust security protocols to maintain user trust and protect sensitive data. It highlights the significance of decision-making in crisis management and the need for continuous improvement in cybersecurity strategies.

DECISION MAKING &
PROBLEM SOLVING
PROBLEM SOLVING
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1.0 INTRODUCTION.....................................................................................................................1
1.1 Purpose of the Report............................................................................................................1
1.2 Company Overview..............................................................................................................1
1.3 Description of the problem...................................................................................................2
1.4 Description of Approaches used by Uber to solve the problem............................................2
2.0 Analysis......................................................................................................................................3
2.1 Critically evaluation of approach used .................................................................................3
2.2 Improvement in the approach used by Uber.........................................................................3
2.3 Other Available approaches Uber could have use................................................................5
2.4 Best approach for Uber.........................................................................................................6
3.0 Stock market analysis................................................................................................................6
3.1 Trend analysis of share price.................................................................................................6
3.2 Investors reaction..................................................................................................................7
CONCLUSION................................................................................................................................8
RECOMMENDATION...................................................................................................................9
REFERENCES.............................................................................................................................10
1.0 INTRODUCTION.....................................................................................................................1
1.1 Purpose of the Report............................................................................................................1
1.2 Company Overview..............................................................................................................1
1.3 Description of the problem...................................................................................................2
1.4 Description of Approaches used by Uber to solve the problem............................................2
2.0 Analysis......................................................................................................................................3
2.1 Critically evaluation of approach used .................................................................................3
2.2 Improvement in the approach used by Uber.........................................................................3
2.3 Other Available approaches Uber could have use................................................................5
2.4 Best approach for Uber.........................................................................................................6
3.0 Stock market analysis................................................................................................................6
3.1 Trend analysis of share price.................................................................................................6
3.2 Investors reaction..................................................................................................................7
CONCLUSION................................................................................................................................8
RECOMMENDATION...................................................................................................................9
REFERENCES.............................................................................................................................10
1.0 INTRODUCTION
1.1 Purpose of the Report
The purpose of this report is to understand and analyse problem faced by Uber in order
to use various techniques of decision- making and problem solving to solve the issue of Uber.
This report will assist in identifying various approaches in order to choose the best approach for
the solving problem. Furthermore, this assignment will critically evaluate the issue of Uber and
also assist in stock market analysis of Uber during the issue period and their inverters reaction on
issue faced by Uber. This report will assist in identifying various methods to solve the problem
of security breach occurred in Uber to gain popularity and to retain its investors. The purpose of
this report is to identify the problem in order to make effective decisions to solve the problem.
1.2 Company Overview
Uber is a private company involved in Transportation and delivery. It was founded in
2009 by Travis Kalanick and Garrett Camp. Uber is offering its services worldwide and have its
headquarter in San Francisco, California, United States. It provides products and services such as
Mobile app, website and vehicle for hire delivery. Uber is having Uber eats, Jump bikes an Otto
as its subsidiaries. Uber is employing employees more than 12000 and generate revenue which is
US$6.5 billion.
Company origin San Francisco in 2009
Company core values Uber is customer obsessed
Work to gain customer trust by solving their
problems.
Uber is involved in reducing the difference
between people come from different
backgrounds.
Key competitors Lyft, Curb, Ola, Didi Chuxing
Major shareholders SoftBank, Benchmark, Travis kalanick
Share price $1B as of 10 November 2018
Revenue US $6.5 billion (2016)
Website www.uber.com
1
1.1 Purpose of the Report
The purpose of this report is to understand and analyse problem faced by Uber in order
to use various techniques of decision- making and problem solving to solve the issue of Uber.
This report will assist in identifying various approaches in order to choose the best approach for
the solving problem. Furthermore, this assignment will critically evaluate the issue of Uber and
also assist in stock market analysis of Uber during the issue period and their inverters reaction on
issue faced by Uber. This report will assist in identifying various methods to solve the problem
of security breach occurred in Uber to gain popularity and to retain its investors. The purpose of
this report is to identify the problem in order to make effective decisions to solve the problem.
1.2 Company Overview
Uber is a private company involved in Transportation and delivery. It was founded in
2009 by Travis Kalanick and Garrett Camp. Uber is offering its services worldwide and have its
headquarter in San Francisco, California, United States. It provides products and services such as
Mobile app, website and vehicle for hire delivery. Uber is having Uber eats, Jump bikes an Otto
as its subsidiaries. Uber is employing employees more than 12000 and generate revenue which is
US$6.5 billion.
Company origin San Francisco in 2009
Company core values Uber is customer obsessed
Work to gain customer trust by solving their
problems.
Uber is involved in reducing the difference
between people come from different
backgrounds.
Key competitors Lyft, Curb, Ola, Didi Chuxing
Major shareholders SoftBank, Benchmark, Travis kalanick
Share price $1B as of 10 November 2018
Revenue US $6.5 billion (2016)
Website www.uber.com
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1.3 Description of the problem
In October 2016, Uber experienced security breach in UK due to which 2.7 million
people of UK were affected. Due to this data breach , Names of customers, their email address
and phone numbers were stolen. Uber get know the fact that the hackers have deleted the data
from the system which leads to no evidence of fraud. Uber took immediate steps in order to
secure the data . Uber in order to delete the hack data paid $100000 to hackers. This issue
affected the people at Large in UK. Security breach happened in Uber in UK caused a great
reduction in the reputation of Uber due to which its profitability reduced.
1.4 Description of Approaches used by Uber to solve the problem
Uber in order to solve the issue relating to security breach which affected 2.7 million in UK.
Zero trust approach is used by Uber in order to resolve the issue. Zero trust approach is assist the
firm in securing the data and this approach abolishes the trusted network inside and outside its
perimeters and verify everything trying to connect to system before granting access to anyone.
This model supported Uber in protecting the data and information of users (Junginger, 2014).
There are different approaches of decision making and problem solving to identify the causes of
issue in order to solve that problem .
2
Illustration 1: Zero- trust approach
(Source : Zero Trust Security Defined, 2017
In October 2016, Uber experienced security breach in UK due to which 2.7 million
people of UK were affected. Due to this data breach , Names of customers, their email address
and phone numbers were stolen. Uber get know the fact that the hackers have deleted the data
from the system which leads to no evidence of fraud. Uber took immediate steps in order to
secure the data . Uber in order to delete the hack data paid $100000 to hackers. This issue
affected the people at Large in UK. Security breach happened in Uber in UK caused a great
reduction in the reputation of Uber due to which its profitability reduced.
1.4 Description of Approaches used by Uber to solve the problem
Uber in order to solve the issue relating to security breach which affected 2.7 million in UK.
Zero trust approach is used by Uber in order to resolve the issue. Zero trust approach is assist the
firm in securing the data and this approach abolishes the trusted network inside and outside its
perimeters and verify everything trying to connect to system before granting access to anyone.
This model supported Uber in protecting the data and information of users (Junginger, 2014).
There are different approaches of decision making and problem solving to identify the causes of
issue in order to solve that problem .
2
Illustration 1: Zero- trust approach
(Source : Zero Trust Security Defined, 2017
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2.0 Analysis
2.1 Critically evaluation of approach used
Zero – trust approach that helps in protecting the network from unauthorised access.
Zero – trust approach provide trust to the firm about their network security. These model is
necessary to implement to reduce the issue relating to data security to protect the user from
harmful affects of hackers (Cromwell, Amabile and Harvey, 2018). Traditionally Uber used,
GitHub approach due to which security breach happened. Uber is using this system as they
though username and passwords are enough to know about person accessing the network.
In order to critically evaluate the Zero – trust approach used by user to resolve the issue must
identify various benefits and drawbacks of implementing Zero – trust model.
Benefits
Implementing Zero – trust model which will benefit Uber to ensure that proper
network security is maintained by providing access only to trusted user.
It reduces the total cost for firm by using a single platform for entire process.
It helps in improving the experience of end – users.
This approach makes decision by making in- depth understanding of the problem.
Zero- trust approach assist in protecting the users from threats when they are on or
off networks
Zero – trust approach helps in easily detecting the unauthorised users.
Drawbacks
There is a lack of Intra- zone traffic inspection in implementing Zero- trust approach.
There is a lack of flexibility in host placement as it reduce decision – making and
problem solving.
This model identify root cause which is different from casual factors.
Single points of failure.
Zero trust model is implemented by Uber in order to reduce the internal and external
threat of network security (Garg, 2016). It assists Uber in protecting the data of its users such as
names, email address, phone numbers etc.
2.2 Improvement in the approach used by Uber
What Uber has done What Uber should have done
3
2.1 Critically evaluation of approach used
Zero – trust approach that helps in protecting the network from unauthorised access.
Zero – trust approach provide trust to the firm about their network security. These model is
necessary to implement to reduce the issue relating to data security to protect the user from
harmful affects of hackers (Cromwell, Amabile and Harvey, 2018). Traditionally Uber used,
GitHub approach due to which security breach happened. Uber is using this system as they
though username and passwords are enough to know about person accessing the network.
In order to critically evaluate the Zero – trust approach used by user to resolve the issue must
identify various benefits and drawbacks of implementing Zero – trust model.
Benefits
Implementing Zero – trust model which will benefit Uber to ensure that proper
network security is maintained by providing access only to trusted user.
It reduces the total cost for firm by using a single platform for entire process.
It helps in improving the experience of end – users.
This approach makes decision by making in- depth understanding of the problem.
Zero- trust approach assist in protecting the users from threats when they are on or
off networks
Zero – trust approach helps in easily detecting the unauthorised users.
Drawbacks
There is a lack of Intra- zone traffic inspection in implementing Zero- trust approach.
There is a lack of flexibility in host placement as it reduce decision – making and
problem solving.
This model identify root cause which is different from casual factors.
Single points of failure.
Zero trust model is implemented by Uber in order to reduce the internal and external
threat of network security (Garg, 2016). It assists Uber in protecting the data of its users such as
names, email address, phone numbers etc.
2.2 Improvement in the approach used by Uber
What Uber has done What Uber should have done
3

According to the analysis it has
identified about that two hackers broke
the Git hub account, cloud based
service used by companies to secure
network. Hackers by hacking the
username and password which were
requires accessing the data . This data
security breach could have been
prevented if Uber implemented strong
cybersecurity practices.
Uber in order to improve the approach
made analysis of the thing which have
resulted in data security breach.
According to the analysis it has
identified about that two hackers broke
the Git hub account, cloud based
service used by companies to secure
network. Hackers by hacking the
username and password which were
requires accessing the data . This data
security breach could have been
prevented if Uber implemented strong
cybersecurity practices (Goetsch and
Davis, 2014).
Uber made a big mistake by providing
ransom to hackers of$100000 instead of
alerting the users about the security
breach of their information. This data
security breach happens due to poor
cybersecurity practises adopted by
Uber.
Uber in order to improve the
approach uses Zero – trust approach
for network security which involves
strong cybersecurity. Zero – trust
approach assist in protecting the user's
information to reduce unauthorised
access of the account.
Uber in order to make effective
cybersecurity must improve its
approach used for maintaining the
network security. Zero – trust model
is implemented and improved by
making strong cloud environment to
reduce the defects. Improvements are
needed to provide users with trust
about company (Tyson,
Rongruengphant and Aggarwal,
2015).
Gaining trust of company is important
for Uber to attract more customer by
resolving the issues of security breach
by implementing strong cybersecurity
which provide access only authorised
users.
Uber must have implemented strong
cybersecurity in order to resolve the
problem which caused breach of
security.
4
identified about that two hackers broke
the Git hub account, cloud based
service used by companies to secure
network. Hackers by hacking the
username and password which were
requires accessing the data . This data
security breach could have been
prevented if Uber implemented strong
cybersecurity practices.
Uber in order to improve the approach
made analysis of the thing which have
resulted in data security breach.
According to the analysis it has
identified about that two hackers broke
the Git hub account, cloud based
service used by companies to secure
network. Hackers by hacking the
username and password which were
requires accessing the data . This data
security breach could have been
prevented if Uber implemented strong
cybersecurity practices (Goetsch and
Davis, 2014).
Uber made a big mistake by providing
ransom to hackers of$100000 instead of
alerting the users about the security
breach of their information. This data
security breach happens due to poor
cybersecurity practises adopted by
Uber.
Uber in order to improve the
approach uses Zero – trust approach
for network security which involves
strong cybersecurity. Zero – trust
approach assist in protecting the user's
information to reduce unauthorised
access of the account.
Uber in order to make effective
cybersecurity must improve its
approach used for maintaining the
network security. Zero – trust model
is implemented and improved by
making strong cloud environment to
reduce the defects. Improvements are
needed to provide users with trust
about company (Tyson,
Rongruengphant and Aggarwal,
2015).
Gaining trust of company is important
for Uber to attract more customer by
resolving the issues of security breach
by implementing strong cybersecurity
which provide access only authorised
users.
Uber must have implemented strong
cybersecurity in order to resolve the
problem which caused breach of
security.
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2.3 Other Available approaches Uber could have use
Zero- based model
On the basis of evaluation it has been identified that approach used by Uber to solve the
problem of security breach in order to gain the trust of users by adopting strong cybersecurity
practices. Uber must adopt Zero -trust model instead of GitHub system to prevent the system
from unauthorised access of the people.
There are other approaches which can be adopted by Uber to resolve the issue of security
breach due to which 1.2 million people of UK were affected.
Uber to resolve the problem provided users with high network security. There are other
approaches other than Zero- trust approach which assist Uber in implementing high security to
reduce the security breach. ]
It consists of network security model. It is approach of securing the network by dividing
the network infrastructure into seven manageable sections. This model will assist Uber in data
loss prevention, Access control, application security, email security, firewall etc. Network
security model assist in protecting against threat coming from outside. It is a seven layer model
to secure the network from unauthorised access.
There are various advantages and disadvantages of this model. Advantages of this model
is it provide high security for network by using seven layer (Minda, 2015). Disadvantage of this
model is that it lack independence as this model depends on various layers to protect the
network. These model will assist in decision making and problem solving regarding network
security.
5 why model
The other available approach for decision making and problem solving consist focus
model and 5 why model to identify the issue. Focus model of problem solving is related to
identification of root cause of problem to make decision to reduce the effect of the problem.
Uber In order to identify the root cause of problem adopted this model and implemented
Zero- trust approach to have strong cybersecurity. This 5 why model is practised by Toyota to
identify different problems affecting the working of organisation. By implementing 5 Why
5
Zero- based model
On the basis of evaluation it has been identified that approach used by Uber to solve the
problem of security breach in order to gain the trust of users by adopting strong cybersecurity
practices. Uber must adopt Zero -trust model instead of GitHub system to prevent the system
from unauthorised access of the people.
There are other approaches which can be adopted by Uber to resolve the issue of security
breach due to which 1.2 million people of UK were affected.
Uber to resolve the problem provided users with high network security. There are other
approaches other than Zero- trust approach which assist Uber in implementing high security to
reduce the security breach. ]
It consists of network security model. It is approach of securing the network by dividing
the network infrastructure into seven manageable sections. This model will assist Uber in data
loss prevention, Access control, application security, email security, firewall etc. Network
security model assist in protecting against threat coming from outside. It is a seven layer model
to secure the network from unauthorised access.
There are various advantages and disadvantages of this model. Advantages of this model
is it provide high security for network by using seven layer (Minda, 2015). Disadvantage of this
model is that it lack independence as this model depends on various layers to protect the
network. These model will assist in decision making and problem solving regarding network
security.
5 why model
The other available approach for decision making and problem solving consist focus
model and 5 why model to identify the issue. Focus model of problem solving is related to
identification of root cause of problem to make decision to reduce the effect of the problem.
Uber In order to identify the root cause of problem adopted this model and implemented
Zero- trust approach to have strong cybersecurity. This 5 why model is practised by Toyota to
identify different problems affecting the working of organisation. By implementing 5 Why
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

model in Uber can assist them in identifying the root cause of the problem by asking Why
(Schoenfeld, 2014). Uber must focus on casual factor before focusing on the root cause to
successfully provide solution to problem and to build strong network to reduce security breach
such as Zero- trust approach to prevent unauthorised access.
Focus model
Focus model of problem solving consist of finding the problem, organize a team, clarify
the problem, understand the problem and then select a solution. This model is practised by ford
motor to solve various issues affecting the business. Focus model is a approach used for decision
making to identify the problem to make effective decision – making.
2.4 Best approach for Uber
SAF analysis
This analysis is done to choose the right option or strategy for business SAF is an
acronym for Suitability , acceptability and feasibility. Suitability is identified in order to
determine if that option is suitable for business or not. Uber in order to choose the best approach
must identify the suitability of the option. Acceptability is the another factor in choosing the best
approach for business. It measures the return , risk etc. before following the approach. Uber must
identify the risk and return \associated with the particular approach. Feasibility is the another
factors which helps in identifying the best approach. Uber in order to choose the approach must
identify the financial feasibility.
Uber in order to solve the problem must use decision – making and problem solving
model which assist in implementing Zero – trust approach for solving the problems. This
approach will assist in solving the problem and reducing chances of security breach. 5 why
model of problem solving helps in identifying about the root cause of security breach on the
basis of which zero- trust approach is implemented (Russell and Norvig, 2016). Uber in order to
solve the problem of security breach must use 5 why model to identify the root cause of the
problem in ordr to solve the problem. 5 why model will help Uber in identifying the root cause
of security breach which helps in implementing Zero – trust approach which prevent system
from unauthorised access.
3.0 Stock market analysis
This task will assist in identifying the share prices and investors reaction when Uber face
the problem of security breach.
6
(Schoenfeld, 2014). Uber must focus on casual factor before focusing on the root cause to
successfully provide solution to problem and to build strong network to reduce security breach
such as Zero- trust approach to prevent unauthorised access.
Focus model
Focus model of problem solving consist of finding the problem, organize a team, clarify
the problem, understand the problem and then select a solution. This model is practised by ford
motor to solve various issues affecting the business. Focus model is a approach used for decision
making to identify the problem to make effective decision – making.
2.4 Best approach for Uber
SAF analysis
This analysis is done to choose the right option or strategy for business SAF is an
acronym for Suitability , acceptability and feasibility. Suitability is identified in order to
determine if that option is suitable for business or not. Uber in order to choose the best approach
must identify the suitability of the option. Acceptability is the another factor in choosing the best
approach for business. It measures the return , risk etc. before following the approach. Uber must
identify the risk and return \associated with the particular approach. Feasibility is the another
factors which helps in identifying the best approach. Uber in order to choose the approach must
identify the financial feasibility.
Uber in order to solve the problem must use decision – making and problem solving
model which assist in implementing Zero – trust approach for solving the problems. This
approach will assist in solving the problem and reducing chances of security breach. 5 why
model of problem solving helps in identifying about the root cause of security breach on the
basis of which zero- trust approach is implemented (Russell and Norvig, 2016). Uber in order to
solve the problem of security breach must use 5 why model to identify the root cause of the
problem in ordr to solve the problem. 5 why model will help Uber in identifying the root cause
of security breach which helps in implementing Zero – trust approach which prevent system
from unauthorised access.
3.0 Stock market analysis
This task will assist in identifying the share prices and investors reaction when Uber face
the problem of security breach.
6
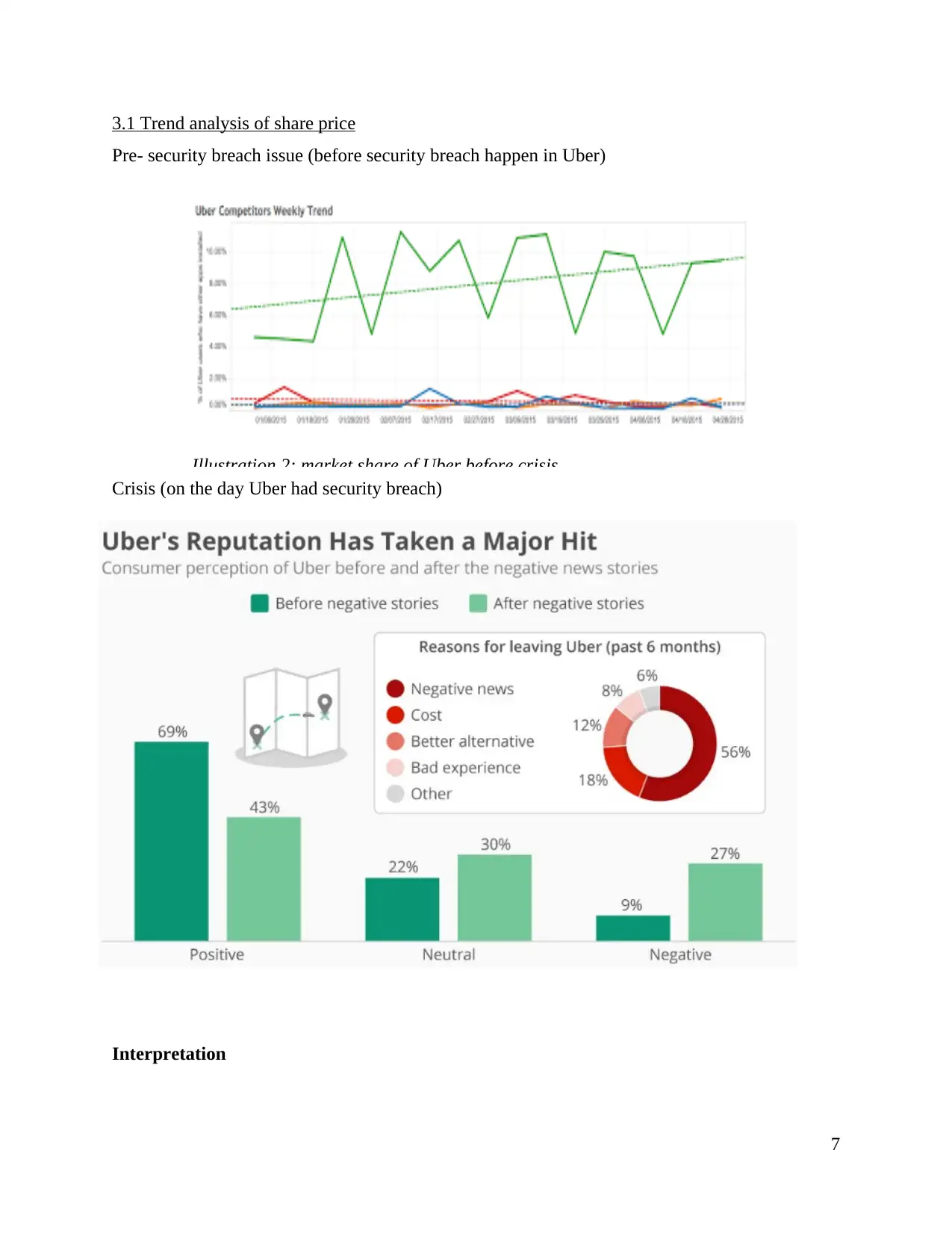
3.1 Trend analysis of share price
Pre- security breach issue (before security breach happen in Uber)
Crisis (on the day Uber had security breach)
Interpretation
7
Illustration 2: market share of Uber before crisis
Pre- security breach issue (before security breach happen in Uber)
Crisis (on the day Uber had security breach)
Interpretation
7
Illustration 2: market share of Uber before crisis
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
From the above graph it could be interpreted that before the security breach took place in
Uber, It was earning high revenues in Uk but due to the security breach which affected the
reputation of Uber and its share prices reduced which reduced their profit margins. Security
breach causes a negative imapct on the Uber which was 69%. Uber were having net revenue in
2014 of $0.5 billion. In 2015, Uber reached $1.5 billion. Uber due to security breach have
caused a great reduction in the share prices. Uber valuation of share got reduced due to negative
impact of security breach happened in 2016 which affected 2.7 million people in UK. Uber paid
$100000 to hackers to delete the data of users which is hacked.
3.2 Investors reaction
Investors of Uber were affected by the security breach which was known by the potential
investors of Ubers which consist of soft banks, Uber disclose about the breach occurred in to the
soft bank which was going to invest $10M in Uber. Uber informed soft bank that they were
investigating the data breach. Uber does not inform the riders and people associated with Uber
about the breach. Security breach of Uber resulted in reduction in its brand image, reduction in
their customer base, reduction in their investors etc (Martin and et.al., 2018). which caused a
great decline in the revenue generation and capital investment of Uber.
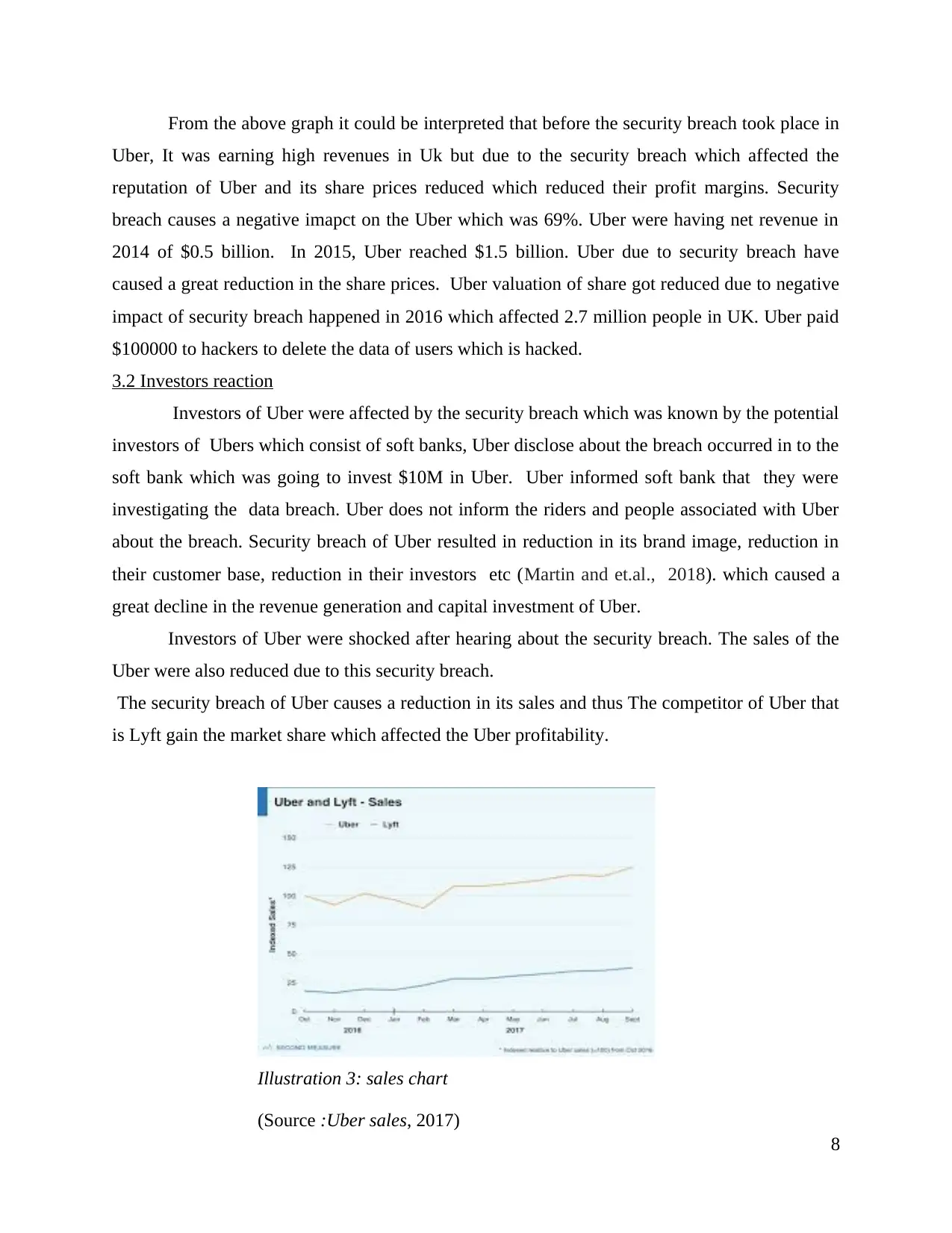
Investors of Uber were shocked after hearing about the security breach. The sales of the
Uber were also reduced due to this security breach.
The security breach of Uber causes a reduction in its sales and thus The competitor of Uber that
is Lyft gain the market share which affected the Uber profitability.
8
Illustration 3: sales chart
(Source :Uber sales, 2017)
Uber, It was earning high revenues in Uk but due to the security breach which affected the
reputation of Uber and its share prices reduced which reduced their profit margins. Security
breach causes a negative imapct on the Uber which was 69%. Uber were having net revenue in
2014 of $0.5 billion. In 2015, Uber reached $1.5 billion. Uber due to security breach have
caused a great reduction in the share prices. Uber valuation of share got reduced due to negative
impact of security breach happened in 2016 which affected 2.7 million people in UK. Uber paid
$100000 to hackers to delete the data of users which is hacked.
3.2 Investors reaction
Investors of Uber were affected by the security breach which was known by the potential
investors of Ubers which consist of soft banks, Uber disclose about the breach occurred in to the
soft bank which was going to invest $10M in Uber. Uber informed soft bank that they were
investigating the data breach. Uber does not inform the riders and people associated with Uber
about the breach. Security breach of Uber resulted in reduction in its brand image, reduction in
their customer base, reduction in their investors etc (Martin and et.al., 2018). which caused a
great decline in the revenue generation and capital investment of Uber.
Investors of Uber were shocked after hearing about the security breach. The sales of the
Uber were also reduced due to this security breach.
The security breach of Uber causes a reduction in its sales and thus The competitor of Uber that
is Lyft gain the market share which affected the Uber profitability.
8
Illustration 3: sales chart
(Source :Uber sales, 2017)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The above sales chart shows the sales of Uber and its competitor Lyft which gained popularity in
the market due to security breach of data in Uber (Zsambok and Klein, 2014). Uber in order to
retain its investors assure them to solve the problem of data breach and to gain the market share
in order to perform various activities to run the business.
CONCLUSION
From the above study it has concluded about different problem solving and decision
making techniques in order to identify the cause of problem. The Problem of security breach
which affected 2.7 million people of UK to solve this problem Uber has implemented zero –
trust approach which has helped Uber in reducing the security breach of data such as names,
email address and phone numbers of users. This approach is implemented after adopting % why
modal of problem solving which has helped Uber in decision – making regarding implementing
Zero- trust approach to make strong cybersecurity of network. There are different approaches of
problem solving which could be implemented to make effective decision to secure the networks
to reduce security breach issue. Uber adopted the 5 why modal in order to make a decision of
zero – trust approach for making strong network base to protect the user data. Furthermore, This
study has provided with stock market analysis of Uber to identify the share prices of Uber during
the phase of security breach in October 2016. This stock analysis of Uber has provided with
understanding of share reduction due to negative affect of security breach. Moreover, it has
provided with the understanding investors' reaction on the issue of security breach. The major
investor of Uber is Soft banks.
RECOMMENDATION
According to the report it has understood that the security breach is problem which is
faced by every organisation. Enterprise in order to reduce security breach of data must ensure
that strong cybersecurity network is implemented to reduce cybercrime. Uber in order to reduce
the issue must implement steps regarding various problem solving model. It is recommended to
uber to not to share the information about users to any third party as it may leads to security
breach of their data. Uber in order to attract investors to incest in the company must maintain a
good relationship with them. It is recommended to Uber to have proper security check to reduce
unauthorised access to any third person which may affect the data.
9
the market due to security breach of data in Uber (Zsambok and Klein, 2014). Uber in order to
retain its investors assure them to solve the problem of data breach and to gain the market share
in order to perform various activities to run the business.
CONCLUSION
From the above study it has concluded about different problem solving and decision
making techniques in order to identify the cause of problem. The Problem of security breach
which affected 2.7 million people of UK to solve this problem Uber has implemented zero –
trust approach which has helped Uber in reducing the security breach of data such as names,
email address and phone numbers of users. This approach is implemented after adopting % why
modal of problem solving which has helped Uber in decision – making regarding implementing
Zero- trust approach to make strong cybersecurity of network. There are different approaches of
problem solving which could be implemented to make effective decision to secure the networks
to reduce security breach issue. Uber adopted the 5 why modal in order to make a decision of
zero – trust approach for making strong network base to protect the user data. Furthermore, This
study has provided with stock market analysis of Uber to identify the share prices of Uber during
the phase of security breach in October 2016. This stock analysis of Uber has provided with
understanding of share reduction due to negative affect of security breach. Moreover, it has
provided with the understanding investors' reaction on the issue of security breach. The major
investor of Uber is Soft banks.
RECOMMENDATION
According to the report it has understood that the security breach is problem which is
faced by every organisation. Enterprise in order to reduce security breach of data must ensure
that strong cybersecurity network is implemented to reduce cybercrime. Uber in order to reduce
the issue must implement steps regarding various problem solving model. It is recommended to
uber to not to share the information about users to any third party as it may leads to security
breach of their data. Uber in order to attract investors to incest in the company must maintain a
good relationship with them. It is recommended to Uber to have proper security check to reduce
unauthorised access to any third person which may affect the data.
9

REFERENCES
Books and Journals
Cromwell, J.R., Amabile, T.M. and Harvey, J.F., 2018. An Integrated Model of Dynamic
Problem Solving Within Organizational Constraints. In Individual Creativity in the
Workplace. (pp. 53-81). Academic Press.
Garg, H., 2016. A novel accuracy function under interval-valued Pythagorean fuzzy environment
for solving multicriteria decision making problem. Journal of Intelligent & Fuzzy
Systems. 31(1). pp.529-540.
Goetsch, D.L. and Davis, S.B., 2014. Quality management for organizational excellence. Upper
Saddle River. NJ: pearson.
Junginger, S., 2014. Towards Policy-Making as Designing: Policy-Making Beyond Problem-
Solving & Decision-Making. In Design for policy. Gower Publishing Ltd.
Martin, R. and et.al., 2018. When leaders are in the numerical majority or minority: Differential
effects on problem‐solving. Journal of Social Issues.74(1). pp.93-111.
Minda, J.P., 2015. The psychology of thinking: Reasoning, decision-making and problem-
solving. Sage.
Russell, S.J. and Norvig, P., 2016. Artificial intelligence: a modern approach. Malaysia; Pearson
Education Limited.
Schoenfeld, A.H., 2014. Mathematical problem solving. Elsevier.
Tyson, P.D., Rongruengphant, R. and Aggarwal, B., 2015. Problem solving among nurses as a
strategy for coping with the stress of hospital restructuring. Journal of Science
Technology and Humanities. 1(1). pp.53-63.
Zsambok, C.E. and Klein, G. eds., 2014. Naturalistic decision making. Psychology Press.
Online
Uber sales. 2017. [Online]. Available through :
<https://www.recode.net/2017/11/5/16599156/uber-business-market-share-lyft-scandal-
delete-uber>
Zero Trust Security Defined. 2017. [Online]. Available through :<https://www.centrify.com/zero-
trust-security/>
10
Books and Journals
Cromwell, J.R., Amabile, T.M. and Harvey, J.F., 2018. An Integrated Model of Dynamic
Problem Solving Within Organizational Constraints. In Individual Creativity in the
Workplace. (pp. 53-81). Academic Press.
Garg, H., 2016. A novel accuracy function under interval-valued Pythagorean fuzzy environment
for solving multicriteria decision making problem. Journal of Intelligent & Fuzzy
Systems. 31(1). pp.529-540.
Goetsch, D.L. and Davis, S.B., 2014. Quality management for organizational excellence. Upper
Saddle River. NJ: pearson.
Junginger, S., 2014. Towards Policy-Making as Designing: Policy-Making Beyond Problem-
Solving & Decision-Making. In Design for policy. Gower Publishing Ltd.
Martin, R. and et.al., 2018. When leaders are in the numerical majority or minority: Differential
effects on problem‐solving. Journal of Social Issues.74(1). pp.93-111.
Minda, J.P., 2015. The psychology of thinking: Reasoning, decision-making and problem-
solving. Sage.
Russell, S.J. and Norvig, P., 2016. Artificial intelligence: a modern approach. Malaysia; Pearson
Education Limited.
Schoenfeld, A.H., 2014. Mathematical problem solving. Elsevier.
Tyson, P.D., Rongruengphant, R. and Aggarwal, B., 2015. Problem solving among nurses as a
strategy for coping with the stress of hospital restructuring. Journal of Science
Technology and Humanities. 1(1). pp.53-63.
Zsambok, C.E. and Klein, G. eds., 2014. Naturalistic decision making. Psychology Press.
Online
Uber sales. 2017. [Online]. Available through :
<https://www.recode.net/2017/11/5/16599156/uber-business-market-share-lyft-scandal-
delete-uber>
Zero Trust Security Defined. 2017. [Online]. Available through :<https://www.centrify.com/zero-
trust-security/>
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




