Comprehensive Report: Ubiquitous Media in Business Organizations
VerifiedAdded on 2020/03/01
|13
|3082
|293
Report
AI Summary
This report provides a comprehensive analysis of ubiquitous media in business organizations. It begins with an introduction to the concept and objectives, defining ubiquitous media as an invisible surveillance system present everywhere virtually. The project scope includes examining its importance in business, the companies utilizing it, and the associated challenges. The literature review covers conceptual frameworks, including ubiquitous computing and surveillance, and theoretical frameworks like environmental psychology theory. The report explores advantages such as assessing customer needs and detecting system errors, and disadvantages like high costs and legal risks. It also details the use of ubiquitous media by companies like Netflix and Uber and concludes with a discussion of the literature gap and a reference list.

USE OF UBIQUITOUS MEDIA IN BUSINESS ORGANIZATIONS
1
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of contents
Introduction......................................................................................................................................3
Project objectives.............................................................................................................................3
Project scope....................................................................................................................................3
Literature review..............................................................................................................................3
Literature gap.................................................................................................................................10
Conclusion.....................................................................................................................................10
Reference list.................................................................................................................................12
2
Introduction......................................................................................................................................3
Project objectives.............................................................................................................................3
Project scope....................................................................................................................................3
Literature review..............................................................................................................................3
Literature gap.................................................................................................................................10
Conclusion.....................................................................................................................................10
Reference list.................................................................................................................................12
2

Introduction
Ubiquitous media literally means that a medium or system that is present everywhere without
having a physical existence. This kind of surveillance system involves technologies that are
invisible to eyes but present everywhere virtually. This system stays active in day to day lives of
common people and remains embedded in the environment, systems used in daily basis,
transportation networks and so on. Ubiquitous surveillance helps to sense movements or
reactions of people and help system to adapt according to those reactions. Though this type of
computing system helps to mark out reactions of people and make profitable changes in the
system, yet there are risks regarding privacy of information which make this system a threat
towards legal acceptance of ubiquitous system.
Project objectives
● To determine the concept as well as usage of ubiquitous media system in a business
context
● To discuss the potentiality of the implementation ubiquitous surveillance in a day to day
basis
● To discuss various theoretical frameworks associated with ubiquitous system
● To critically analyze advantages and disadvantages of ubiquitous surveillance system
Project scope
This project would be helpful to provide insight into the concept of ubiquitous media system and
its importance in business organizations. It would also be helpful to provide an idea about
different companies which use this system as a part of their business and also problematic
aspects of using such system. Contrasting viewpoints on the implementation and use of this
system in day to day life would be helpful for depicting current threats associated with this
system too, which would in turn be helpful to prevent problems in future. Different theoretical
frameworks and concepts associated with this process would be helpful to install such systems in
future to sense activities of people and make changes for better adaptation.
Literature review
Conceptual framework
3
Ubiquitous media literally means that a medium or system that is present everywhere without
having a physical existence. This kind of surveillance system involves technologies that are
invisible to eyes but present everywhere virtually. This system stays active in day to day lives of
common people and remains embedded in the environment, systems used in daily basis,
transportation networks and so on. Ubiquitous surveillance helps to sense movements or
reactions of people and help system to adapt according to those reactions. Though this type of
computing system helps to mark out reactions of people and make profitable changes in the
system, yet there are risks regarding privacy of information which make this system a threat
towards legal acceptance of ubiquitous system.
Project objectives
● To determine the concept as well as usage of ubiquitous media system in a business
context
● To discuss the potentiality of the implementation ubiquitous surveillance in a day to day
basis
● To discuss various theoretical frameworks associated with ubiquitous system
● To critically analyze advantages and disadvantages of ubiquitous surveillance system
Project scope
This project would be helpful to provide insight into the concept of ubiquitous media system and
its importance in business organizations. It would also be helpful to provide an idea about
different companies which use this system as a part of their business and also problematic
aspects of using such system. Contrasting viewpoints on the implementation and use of this
system in day to day life would be helpful for depicting current threats associated with this
system too, which would in turn be helpful to prevent problems in future. Different theoretical
frameworks and concepts associated with this process would be helpful to install such systems in
future to sense activities of people and make changes for better adaptation.
Literature review
Conceptual framework
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
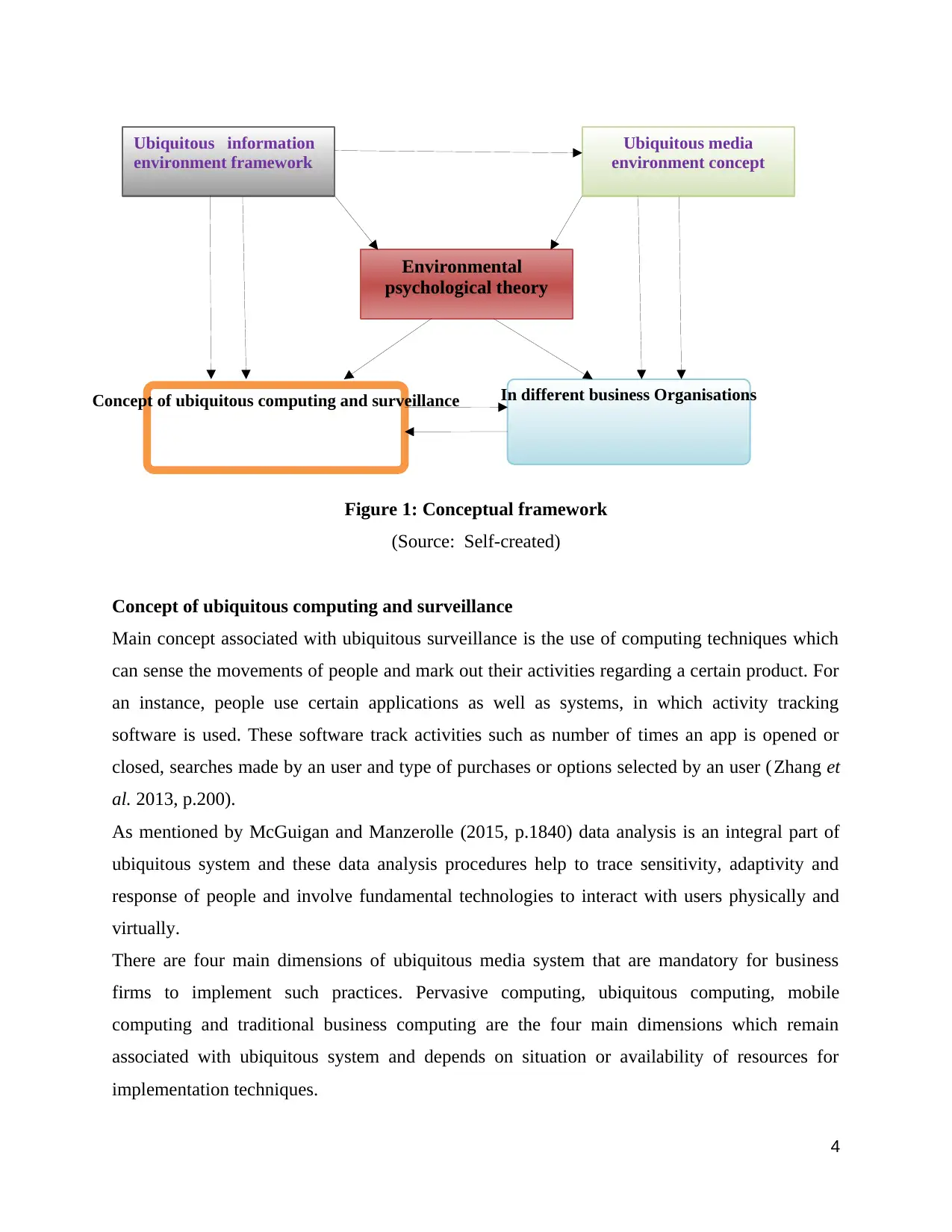
Concept of ubiquitous computing and surveillance
Ubiquitous information
environment framework
Environmental
psychological theory
Ubiquitous media
environment concept
In different business Organisations
Figure 1: Conceptual framework
(Source: Self-created)
Concept of ubiquitous computing and surveillance
Main concept associated with ubiquitous surveillance is the use of computing techniques which
can sense the movements of people and mark out their activities regarding a certain product. For
an instance, people use certain applications as well as systems, in which activity tracking
software is used. These software track activities such as number of times an app is opened or
closed, searches made by an user and type of purchases or options selected by an user (Zhang et
al. 2013, p.200).
As mentioned by McGuigan and Manzerolle (2015, p.1840) data analysis is an integral part of
ubiquitous system and these data analysis procedures help to trace sensitivity, adaptivity and
response of people and involve fundamental technologies to interact with users physically and
virtually.
There are four main dimensions of ubiquitous media system that are mandatory for business
firms to implement such practices. Pervasive computing, ubiquitous computing, mobile
computing and traditional business computing are the four main dimensions which remain
associated with ubiquitous system and depends on situation or availability of resources for
implementation techniques.
4
Ubiquitous information
environment framework
Environmental
psychological theory
Ubiquitous media
environment concept
In different business Organisations
Figure 1: Conceptual framework
(Source: Self-created)
Concept of ubiquitous computing and surveillance
Main concept associated with ubiquitous surveillance is the use of computing techniques which
can sense the movements of people and mark out their activities regarding a certain product. For
an instance, people use certain applications as well as systems, in which activity tracking
software is used. These software track activities such as number of times an app is opened or
closed, searches made by an user and type of purchases or options selected by an user (Zhang et
al. 2013, p.200).
As mentioned by McGuigan and Manzerolle (2015, p.1840) data analysis is an integral part of
ubiquitous system and these data analysis procedures help to trace sensitivity, adaptivity and
response of people and involve fundamental technologies to interact with users physically and
virtually.
There are four main dimensions of ubiquitous media system that are mandatory for business
firms to implement such practices. Pervasive computing, ubiquitous computing, mobile
computing and traditional business computing are the four main dimensions which remain
associated with ubiquitous system and depends on situation or availability of resources for
implementation techniques.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
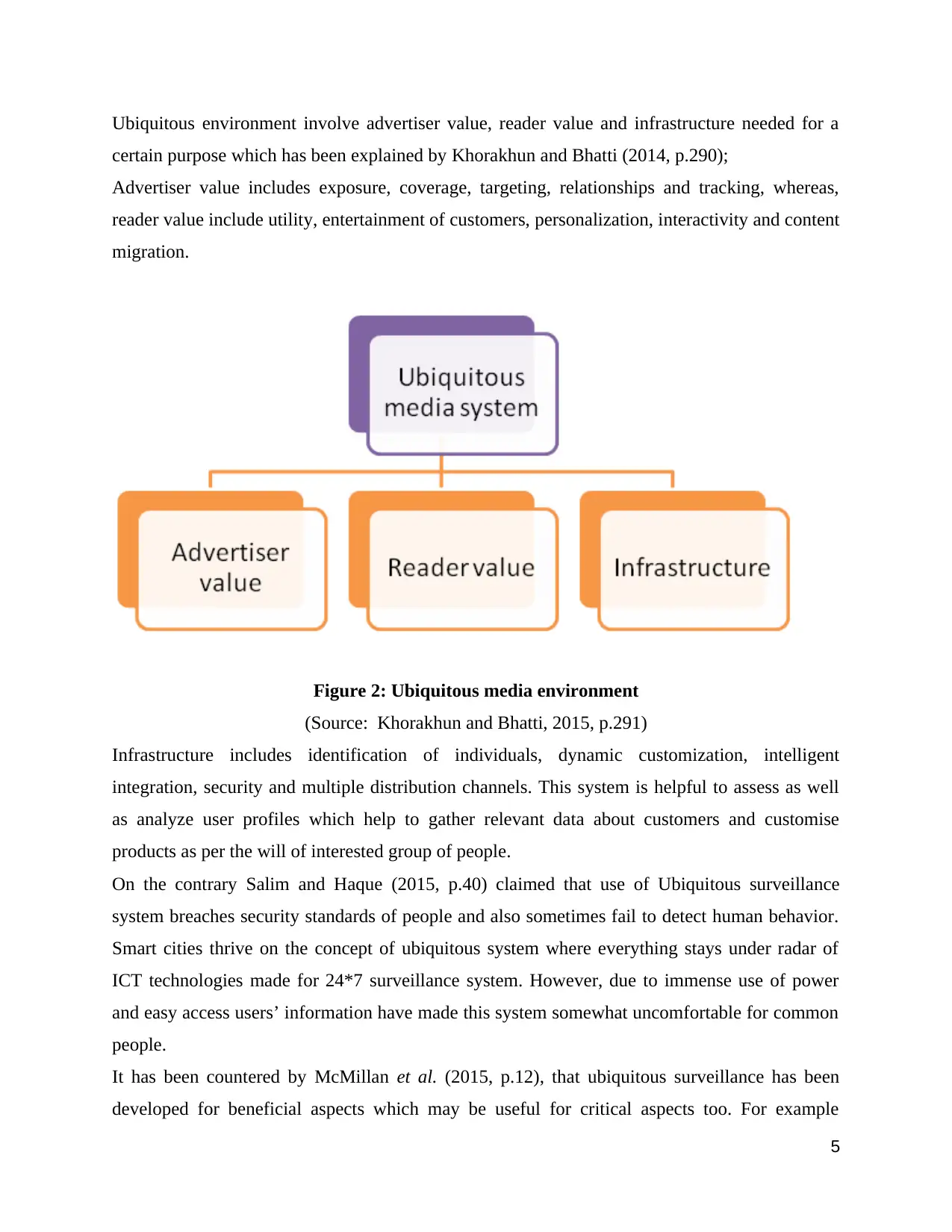
Ubiquitous environment involve advertiser value, reader value and infrastructure needed for a
certain purpose which has been explained by Khorakhun and Bhatti (2014, p.290);
Advertiser value includes exposure, coverage, targeting, relationships and tracking, whereas,
reader value include utility, entertainment of customers, personalization, interactivity and content
migration.
Figure 2: Ubiquitous media environment
(Source: Khorakhun and Bhatti, 2015, p.291)
Infrastructure includes identification of individuals, dynamic customization, intelligent
integration, security and multiple distribution channels. This system is helpful to assess as well
as analyze user profiles which help to gather relevant data about customers and customise
products as per the will of interested group of people.
On the contrary Salim and Haque (2015, p.40) claimed that use of Ubiquitous surveillance
system breaches security standards of people and also sometimes fail to detect human behavior.
Smart cities thrive on the concept of ubiquitous system where everything stays under radar of
ICT technologies made for 24*7 surveillance system. However, due to immense use of power
and easy access users’ information have made this system somewhat uncomfortable for common
people.
It has been countered by McMillan et al. (2015, p.12), that ubiquitous surveillance has been
developed for beneficial aspects which may be useful for critical aspects too. For example
5
certain purpose which has been explained by Khorakhun and Bhatti (2014, p.290);
Advertiser value includes exposure, coverage, targeting, relationships and tracking, whereas,
reader value include utility, entertainment of customers, personalization, interactivity and content
migration.
Figure 2: Ubiquitous media environment
(Source: Khorakhun and Bhatti, 2015, p.291)
Infrastructure includes identification of individuals, dynamic customization, intelligent
integration, security and multiple distribution channels. This system is helpful to assess as well
as analyze user profiles which help to gather relevant data about customers and customise
products as per the will of interested group of people.
On the contrary Salim and Haque (2015, p.40) claimed that use of Ubiquitous surveillance
system breaches security standards of people and also sometimes fail to detect human behavior.
Smart cities thrive on the concept of ubiquitous system where everything stays under radar of
ICT technologies made for 24*7 surveillance system. However, due to immense use of power
and easy access users’ information have made this system somewhat uncomfortable for common
people.
It has been countered by McMillan et al. (2015, p.12), that ubiquitous surveillance has been
developed for beneficial aspects which may be useful for critical aspects too. For example
5

London used live feed to deliver information about people; similarly business firms also use this
system to monitor their customers by accessing their database to increase sustainability of
products. It has also been mentioned that it is not mandatory to assess confidential information of
customers to carry out ubiquitous surveillance, rather can be done by involving simple video
surveillance too.
Theoretical frameworks that depict the procedure of ubiquitous system
The fundamental process involved in ubiquitous media surveillance can be described with the
help of environment psychology theory which is based on the interaction between customer
purchase as well as transactions (Tham, 2015, p.799).
Figure 3: Environment psychology theory
(Source: Tham, 2015, p.798)
This theory states the importance of ubiquitous system in a business context as it helps to analyze
primary goals or intentions of a customer before purchase of products and the ultimate or final
transaction. This process helps to assess the middle step that is the cognition or emotion
associated with the change of mind before the buying process and helps to focus on that
particular aspect for creating better products in future.
On another hand Hofacker and Belanche (2016, p.78) stated that even minute information about
transaction of customers can be accessed with the help of ICT technologies as well as ubiquitous
system and these information are extremely confidential for common masses. Moreover, it is not
always possible for ICT technologies to evaluate human behavior every time and most of the
time those are purely based on assumptions about the activity of people.
6
system to monitor their customers by accessing their database to increase sustainability of
products. It has also been mentioned that it is not mandatory to assess confidential information of
customers to carry out ubiquitous surveillance, rather can be done by involving simple video
surveillance too.
Theoretical frameworks that depict the procedure of ubiquitous system
The fundamental process involved in ubiquitous media surveillance can be described with the
help of environment psychology theory which is based on the interaction between customer
purchase as well as transactions (Tham, 2015, p.799).
Figure 3: Environment psychology theory
(Source: Tham, 2015, p.798)
This theory states the importance of ubiquitous system in a business context as it helps to analyze
primary goals or intentions of a customer before purchase of products and the ultimate or final
transaction. This process helps to assess the middle step that is the cognition or emotion
associated with the change of mind before the buying process and helps to focus on that
particular aspect for creating better products in future.
On another hand Hofacker and Belanche (2016, p.78) stated that even minute information about
transaction of customers can be accessed with the help of ICT technologies as well as ubiquitous
system and these information are extremely confidential for common masses. Moreover, it is not
always possible for ICT technologies to evaluate human behavior every time and most of the
time those are purely based on assumptions about the activity of people.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
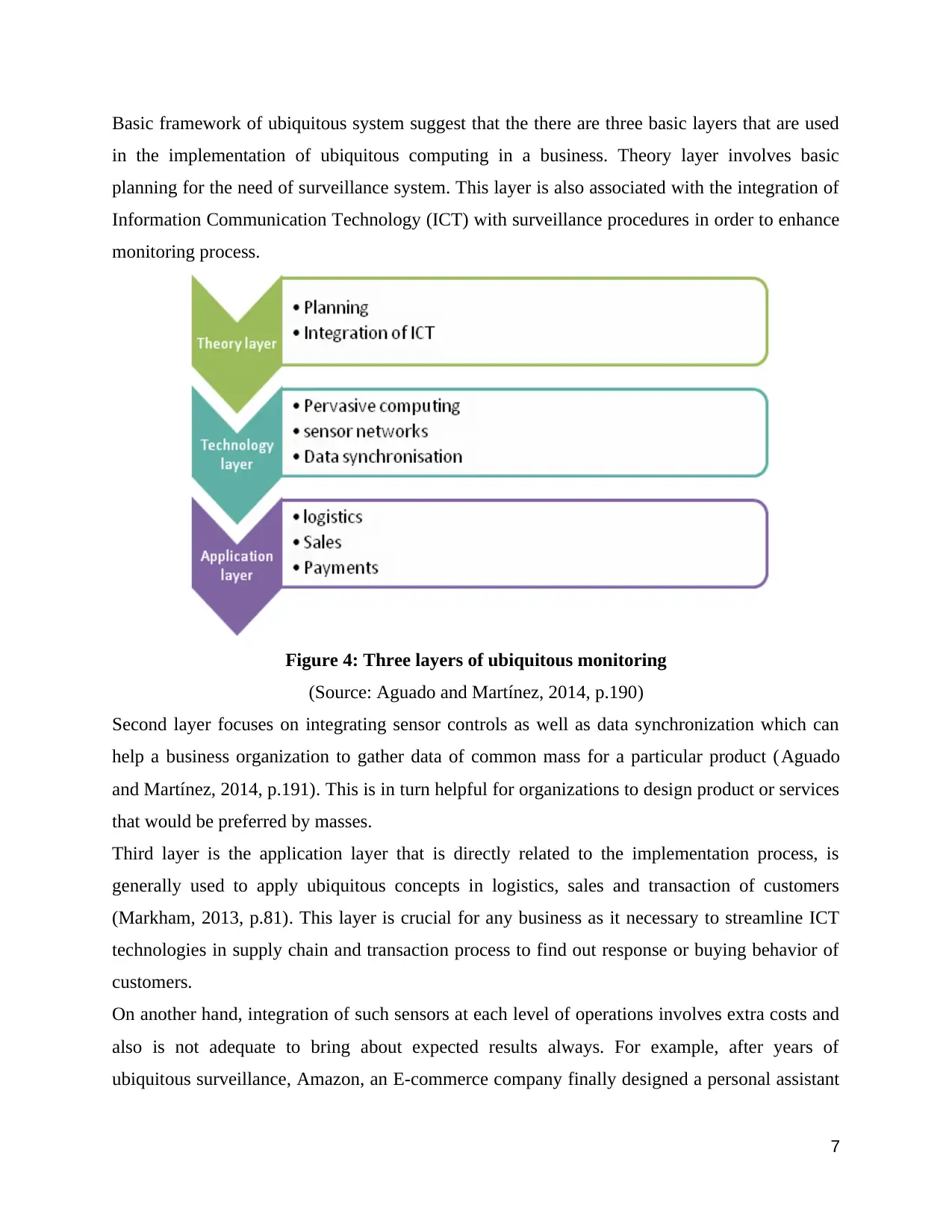
Basic framework of ubiquitous system suggest that the there are three basic layers that are used
in the implementation of ubiquitous computing in a business. Theory layer involves basic
planning for the need of surveillance system. This layer is also associated with the integration of
Information Communication Technology (ICT) with surveillance procedures in order to enhance
monitoring process.
Figure 4: Three layers of ubiquitous monitoring
(Source: Aguado and Martínez, 2014, p.190)
Second layer focuses on integrating sensor controls as well as data synchronization which can
help a business organization to gather data of common mass for a particular product (Aguado
and Martínez, 2014, p.191). This is in turn helpful for organizations to design product or services
that would be preferred by masses.
Third layer is the application layer that is directly related to the implementation process, is
generally used to apply ubiquitous concepts in logistics, sales and transaction of customers
(Markham, 2013, p.81). This layer is crucial for any business as it necessary to streamline ICT
technologies in supply chain and transaction process to find out response or buying behavior of
customers.
On another hand, integration of such sensors at each level of operations involves extra costs and
also is not adequate to bring about expected results always. For example, after years of
ubiquitous surveillance, Amazon, an E-commerce company finally designed a personal assistant
7
in the implementation of ubiquitous computing in a business. Theory layer involves basic
planning for the need of surveillance system. This layer is also associated with the integration of
Information Communication Technology (ICT) with surveillance procedures in order to enhance
monitoring process.
Figure 4: Three layers of ubiquitous monitoring
(Source: Aguado and Martínez, 2014, p.190)
Second layer focuses on integrating sensor controls as well as data synchronization which can
help a business organization to gather data of common mass for a particular product (Aguado
and Martínez, 2014, p.191). This is in turn helpful for organizations to design product or services
that would be preferred by masses.
Third layer is the application layer that is directly related to the implementation process, is
generally used to apply ubiquitous concepts in logistics, sales and transaction of customers
(Markham, 2013, p.81). This layer is crucial for any business as it necessary to streamline ICT
technologies in supply chain and transaction process to find out response or buying behavior of
customers.
On another hand, integration of such sensors at each level of operations involves extra costs and
also is not adequate to bring about expected results always. For example, after years of
ubiquitous surveillance, Amazon, an E-commerce company finally designed a personal assistant
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

named Alexa like Google and Apple but failed to meet certain satisfaction standards even after
prolonged surveillance. It is therefore stated that it is not possible for a technological platform to
understand human psychology merely by assessing their activities (Yousfi et al. 2016, p.630).
Organizations that use ubiquitous media system
Many business ventures are associated with ubiquitous surveillance system and use a concept
namely ubiquitous entertainment to implement the procedures in a fun way. This concept is
mostly famous in digital music or video streaming industries, where it is practically possible for
companies to assess the needs of customers with the help of their activities. For example Netflix,
Google play, Amazon instant video and BBC iPlayer track playlists, ratings, duration of playtime
of each music or video track and content aggregation methods to identify most preferable service
for users. Mobile devices also enable users to share files via various platforms which help these
companies even more to find most valuable services provided by them and set pricing standards
as per the values of people (Martínez-Torres et al. p.158).
Uber uses ubiquitous media system to identify as well as block regulators for restricting illegal
behavior. This technique has been termed as “eyeballing” which uses the concept of geo-fencing.
Uber uses this method to demarcate an area or a city to be monitored and keep a close eye on
people who frequently open and close the application (Yousfi et al. 2016, p.60). This method has
been coined as eyeballing which signifies location and frequent destination of a user. Other
techniques involved in their surveillance system are looking over credit card information,
payments made and so on.
Figure 5: Ubiquitous surveillance of Uber
(Source: Yousfi et al. 2016, p.61)
8
prolonged surveillance. It is therefore stated that it is not possible for a technological platform to
understand human psychology merely by assessing their activities (Yousfi et al. 2016, p.630).
Organizations that use ubiquitous media system
Many business ventures are associated with ubiquitous surveillance system and use a concept
namely ubiquitous entertainment to implement the procedures in a fun way. This concept is
mostly famous in digital music or video streaming industries, where it is practically possible for
companies to assess the needs of customers with the help of their activities. For example Netflix,
Google play, Amazon instant video and BBC iPlayer track playlists, ratings, duration of playtime
of each music or video track and content aggregation methods to identify most preferable service
for users. Mobile devices also enable users to share files via various platforms which help these
companies even more to find most valuable services provided by them and set pricing standards
as per the values of people (Martínez-Torres et al. p.158).
Uber uses ubiquitous media system to identify as well as block regulators for restricting illegal
behavior. This technique has been termed as “eyeballing” which uses the concept of geo-fencing.
Uber uses this method to demarcate an area or a city to be monitored and keep a close eye on
people who frequently open and close the application (Yousfi et al. 2016, p.60). This method has
been coined as eyeballing which signifies location and frequent destination of a user. Other
techniques involved in their surveillance system are looking over credit card information,
payments made and so on.
Figure 5: Ubiquitous surveillance of Uber
(Source: Yousfi et al. 2016, p.61)
8
This technology helps Uber to find out its potential customers and also help to find out if there is
any illegal process involved in the system. Credit card information and use of those cards by
users help to rectify actual identity of a user which is a beneficial aspect as stated by ( Rabari and
Storper, 2014, p.40).
On another hand, Kitchin (2014, p.12) commented that it is illegal for business firms to access
confidential information of users and if this tend to continue then business ventures associated
with such an amount of surveillance can face ethical dilemmas in future. Moreover, engaging
highly innovative technology can also pose as a risk to the business if an implementation process
fails to meet expected outcome. Processes such as integration of developed software, cloud
technologies and complex digital network may also face adaptation challenges at the early stage
of their usage and also involve certain code of ethics to maintain the integrity of data gathered
from users.
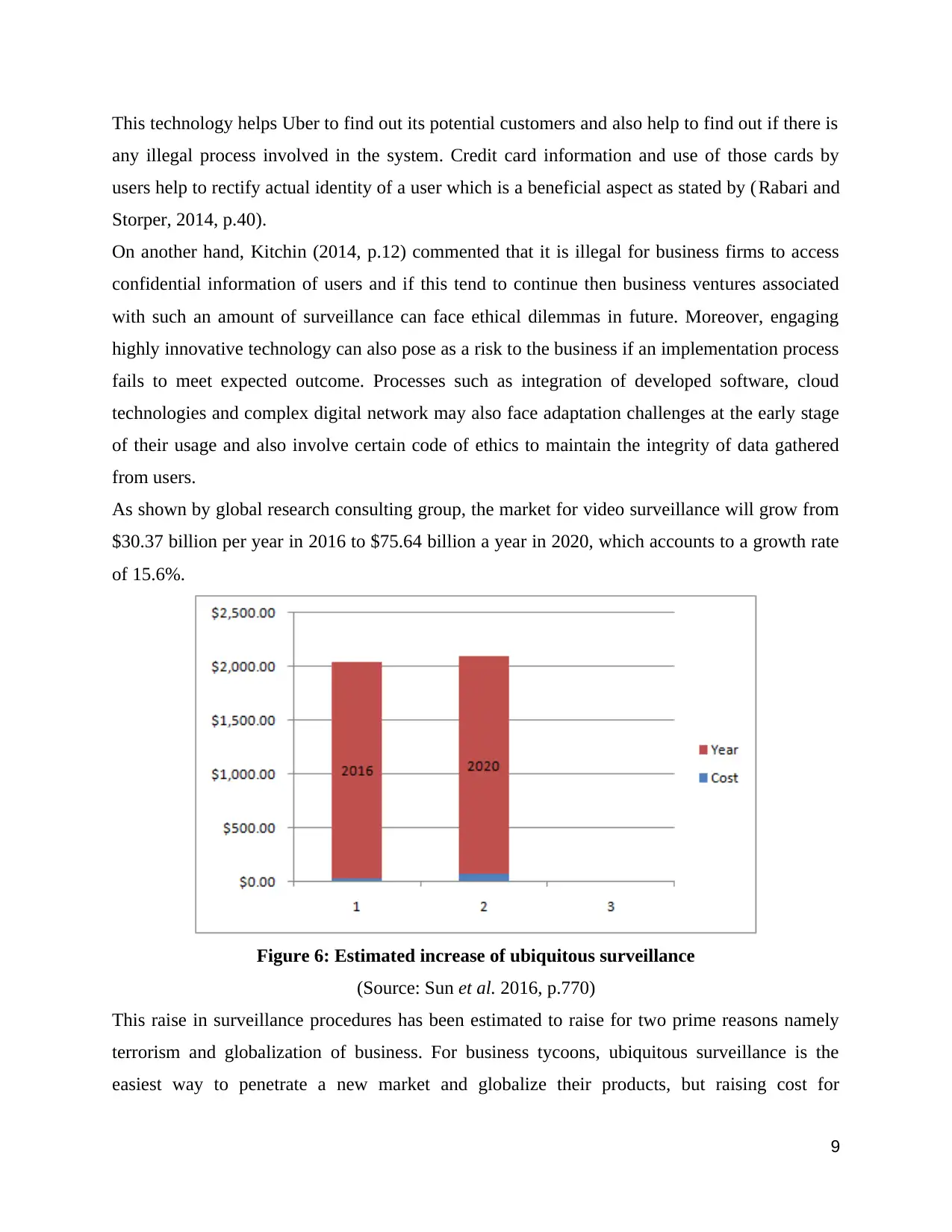
As shown by global research consulting group, the market for video surveillance will grow from
$30.37 billion per year in 2016 to $75.64 billion a year in 2020, which accounts to a growth rate
of 15.6%.
Figure 6: Estimated increase of ubiquitous surveillance
(Source: Sun et al. 2016, p.770)
This raise in surveillance procedures has been estimated to raise for two prime reasons namely
terrorism and globalization of business. For business tycoons, ubiquitous surveillance is the
easiest way to penetrate a new market and globalize their products, but raising cost for
9
any illegal process involved in the system. Credit card information and use of those cards by
users help to rectify actual identity of a user which is a beneficial aspect as stated by ( Rabari and
Storper, 2014, p.40).
On another hand, Kitchin (2014, p.12) commented that it is illegal for business firms to access
confidential information of users and if this tend to continue then business ventures associated
with such an amount of surveillance can face ethical dilemmas in future. Moreover, engaging
highly innovative technology can also pose as a risk to the business if an implementation process
fails to meet expected outcome. Processes such as integration of developed software, cloud
technologies and complex digital network may also face adaptation challenges at the early stage
of their usage and also involve certain code of ethics to maintain the integrity of data gathered
from users.
As shown by global research consulting group, the market for video surveillance will grow from
$30.37 billion per year in 2016 to $75.64 billion a year in 2020, which accounts to a growth rate
of 15.6%.
Figure 6: Estimated increase of ubiquitous surveillance
(Source: Sun et al. 2016, p.770)
This raise in surveillance procedures has been estimated to raise for two prime reasons namely
terrorism and globalization of business. For business tycoons, ubiquitous surveillance is the
easiest way to penetrate a new market and globalize their products, but raising cost for
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

installation of complex ICT technologies is the prime concern for not only business ventures but
also the government.
Advantages and disadvantages of ubiquitous surveillance
With every complex technology comes certain advantages and disadvantages and ubiquitous
computing or surveillance is not any exception.
Certain advantages has been stated by Sun et al. (2016, p.771);
Helps to assess customer needs and design products as per those
Ubiquitous system helps to aggregate choices of customers under certain criteria which in turn
help companies to design products as per the choice of customers. Most beneficial aspect of this
process is that it involves big data analysis to track intention and final decision of a customer.
For an instance, e-commerce companies track products viewed by customers the most and final
purchase. Amazon uses this technique to monitor customer purchase and set up prices as per the
popularity of a product (McGuigan and Manzerolle, 2015, p.1841).
Helpful to mark out errors in the system
Big data analysis associated with ubiquitous monitoring helps to detect any illegal entity
involved in operations.
On another hand disadvantages has been stated by Salim and Haque (2015, p.42);
Cost consuming process
Involvement of complex ICT technologies involves high costs and also requires huge financial
funding.
Can involve legal as well as monetary risks
Sometimes surveillance procedures outsmart the limits of privacy and ethical standards which
may cause moral dilemmas for organizations (McMillan et al. 2015, p.10).
Literature gap
Theories based on ubiquitous media do not properly depict the process of proper implementation
of such ideas. Researcher found it difficult to access statistical data associated with this concept.
There have also been lacks of data regarding companies that use virtual monitoring, which made
it difficult for organizations to draw out evaluations from theoretical concepts as well as gathered
data.
10
also the government.
Advantages and disadvantages of ubiquitous surveillance
With every complex technology comes certain advantages and disadvantages and ubiquitous
computing or surveillance is not any exception.
Certain advantages has been stated by Sun et al. (2016, p.771);
Helps to assess customer needs and design products as per those
Ubiquitous system helps to aggregate choices of customers under certain criteria which in turn
help companies to design products as per the choice of customers. Most beneficial aspect of this
process is that it involves big data analysis to track intention and final decision of a customer.
For an instance, e-commerce companies track products viewed by customers the most and final
purchase. Amazon uses this technique to monitor customer purchase and set up prices as per the
popularity of a product (McGuigan and Manzerolle, 2015, p.1841).
Helpful to mark out errors in the system
Big data analysis associated with ubiquitous monitoring helps to detect any illegal entity
involved in operations.
On another hand disadvantages has been stated by Salim and Haque (2015, p.42);
Cost consuming process
Involvement of complex ICT technologies involves high costs and also requires huge financial
funding.
Can involve legal as well as monetary risks
Sometimes surveillance procedures outsmart the limits of privacy and ethical standards which
may cause moral dilemmas for organizations (McMillan et al. 2015, p.10).
Literature gap
Theories based on ubiquitous media do not properly depict the process of proper implementation
of such ideas. Researcher found it difficult to access statistical data associated with this concept.
There have also been lacks of data regarding companies that use virtual monitoring, which made
it difficult for organizations to draw out evaluations from theoretical concepts as well as gathered
data.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Conclusion
Ubiquitous monitoring involves innovative yet complex technologies to monitor every action of
people. While this type of monitoring helps a lot to develop a business by studying consumer
behavior, this process also involve certain risk or threats too. The main risk of this kind of
surveillance system is the investment as well as engagement of monetary resources as if a plan
regarding virtual monitoring fails, it will damage the company revenue structure. On another
hand, if ubiquitous monitoring gets implemented in a proper format it can lead towards plethora
of opportunities. However, in order to consider practical impact of these kind of surveillance
procedures, it can be stated that this option is not completely reliable but can be used as a
supportive option.
11
Ubiquitous monitoring involves innovative yet complex technologies to monitor every action of
people. While this type of monitoring helps a lot to develop a business by studying consumer
behavior, this process also involve certain risk or threats too. The main risk of this kind of
surveillance system is the investment as well as engagement of monetary resources as if a plan
regarding virtual monitoring fails, it will damage the company revenue structure. On another
hand, if ubiquitous monitoring gets implemented in a proper format it can lead towards plethora
of opportunities. However, in order to consider practical impact of these kind of surveillance
procedures, it can be stated that this option is not completely reliable but can be used as a
supportive option.
11

Reference list
Aguado, J.M. and Martínez, I., (2014). Feeding digital omnivores: The impact of mobile media
in digital entertainment. The Routledge companion to mobile media, 3(21), pp.181-194.
Hofacker, C.F. and Belanche, D., (2016). Eight social media challenges for marketing
managers. Spanish Journal of Marketing-ESIC, 20(2), pp.73-80.
Khorakhun, C. and Bhatti, S.N., (2014), Using online social media platforms for ubiquitous,
personal health monitoring. e-Health Networking, Applications and Services (Healthcom), 2014
IEEE 16th International Conference on, 7(2), pp. 287-292.
Kitchin, R., (2014). The real-time city? Big data and smart urbanism. GeoJournal, 79(1), pp.1-
14.
Markham, A., (2013). Remix cultures, remix methods: Reframing qualitative inquiry for social
media contexts. Global dimensions of qualitative inquiry, 1(3), pp.63-81.
Martínez-Torres, M.D.R., Díaz-Fernández, M.D.C., Toral, S.L. and Barrero, F., (2015). The
moderating role of prior experience in technological acceptance models for ubiquitous
computing services in urban environments. Technological Forecasting and Social
Change, 91(1), pp.146-160.
McGuigan, L. and Manzerolle, V., (2015). “All the world’sa shopping cart”: Theorizing the
political economy of ubiquitous media and markets. new media & society, 17(11), pp.1830-1848.
McMillan, D., Brown, B., Sellen, A., Lindley, S. and Martens, R., (2015), Pick up and play:
understanding tangibility for cloud media. Proceedings of the 14th International Conference on
Mobile and Ubiquitous Multimedia, 7(1), pp. 1-13.
Rabari, C. and Storper, M., (2014). The digital skin of cities: urban theory and research in the
age of the sensored and metered city, ubiquitous computing and big data. Cambridge Journal of
Regions, Economy and Society, 8(1), pp.27-42.
Salim, F. and Haque, U., (2015). Urban computing in the wild: A survey on large scale
participation and citizen engagement with ubiquitous computing, cyber physical systems, and
Internet of Things. International Journal of Human-Computer Studies, 81(6), pp.31-48.
Sun, Y., Song, H., Jara, A.J. and Bie, R., (2016). Internet of things and big data analytics for
smart and connected communities. IEEE Access, 4(1), pp.766-773.
12
Aguado, J.M. and Martínez, I., (2014). Feeding digital omnivores: The impact of mobile media
in digital entertainment. The Routledge companion to mobile media, 3(21), pp.181-194.
Hofacker, C.F. and Belanche, D., (2016). Eight social media challenges for marketing
managers. Spanish Journal of Marketing-ESIC, 20(2), pp.73-80.
Khorakhun, C. and Bhatti, S.N., (2014), Using online social media platforms for ubiquitous,
personal health monitoring. e-Health Networking, Applications and Services (Healthcom), 2014
IEEE 16th International Conference on, 7(2), pp. 287-292.
Kitchin, R., (2014). The real-time city? Big data and smart urbanism. GeoJournal, 79(1), pp.1-
14.
Markham, A., (2013). Remix cultures, remix methods: Reframing qualitative inquiry for social
media contexts. Global dimensions of qualitative inquiry, 1(3), pp.63-81.
Martínez-Torres, M.D.R., Díaz-Fernández, M.D.C., Toral, S.L. and Barrero, F., (2015). The
moderating role of prior experience in technological acceptance models for ubiquitous
computing services in urban environments. Technological Forecasting and Social
Change, 91(1), pp.146-160.
McGuigan, L. and Manzerolle, V., (2015). “All the world’sa shopping cart”: Theorizing the
political economy of ubiquitous media and markets. new media & society, 17(11), pp.1830-1848.
McMillan, D., Brown, B., Sellen, A., Lindley, S. and Martens, R., (2015), Pick up and play:
understanding tangibility for cloud media. Proceedings of the 14th International Conference on
Mobile and Ubiquitous Multimedia, 7(1), pp. 1-13.
Rabari, C. and Storper, M., (2014). The digital skin of cities: urban theory and research in the
age of the sensored and metered city, ubiquitous computing and big data. Cambridge Journal of
Regions, Economy and Society, 8(1), pp.27-42.
Salim, F. and Haque, U., (2015). Urban computing in the wild: A survey on large scale
participation and citizen engagement with ubiquitous computing, cyber physical systems, and
Internet of Things. International Journal of Human-Computer Studies, 81(6), pp.31-48.
Sun, Y., Song, H., Jara, A.J. and Bie, R., (2016). Internet of things and big data analytics for
smart and connected communities. IEEE Access, 4(1), pp.766-773.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





