KIT201/501 Essay: Investigating and Preventing MitM Attacks
VerifiedAdded on 2022/10/09
|18
|3456
|309
Essay
AI Summary
This essay provides a comprehensive analysis of Man-in-the-Middle (MitM) attacks, a significant threat to network security. It begins by defining MitM attacks and discussing common types such as ARP spoofing, session hijacking, IP spoofing, and replay attacks. The essay then explores various MitM attack techniques, including rogue access points, MDNS spoofing, DNS spoofing, sniffing, packet injection, and SSL stripping. Furthermore, it discusses methods to prevent MitM attacks, such as strong WEP/WAP encryption, VPNs, forced HTTPS, and public key pair authentication. The essay also presents a recent example of a MitM attack, highlighting the real-world implications of these vulnerabilities. The goal is to provide a detailed understanding of MitM attacks and strategies to mitigate them.

Running head: MAN-IN-THE-MIDDLE ATTACK
Man-In-The-Middle Attack
Name of the Student
Name of the University
Author Note
Man-In-The-Middle Attack
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1MAN-IN-THE-MIDDLE ATTACK
Table of Contents
Introduction 2
Discussion 2
The Man-in-the-Middle (MitM) attack 2
ARP spoofing 3
Session Hijacking3
IP Spoofing 4
Replay 5
Man-in-the-Middle Attacks and their Types 7
Rogue Access Point 7
ARP Spoofing 8
MDNS Spoofing 8
DNS Spoofing 9
Man-in-the-Middle Attack Techniques9
Sniffing 9
Packet Injection 10
Session Hijacking 11
SSL Stripping 11
Preventing Man-in-the-Middle Attacks 11
Strong WEP/WAP Encryption on Access Points 11
Virtual Private Network 12
Force HTTPS 12
Public Key Pair Based Authentication 12
Recent example of the attack 12
Conclusion 14
References 15
Table of Contents
Introduction 2
Discussion 2
The Man-in-the-Middle (MitM) attack 2
ARP spoofing 3
Session Hijacking3
IP Spoofing 4
Replay 5
Man-in-the-Middle Attacks and their Types 7
Rogue Access Point 7
ARP Spoofing 8
MDNS Spoofing 8
DNS Spoofing 9
Man-in-the-Middle Attack Techniques9
Sniffing 9
Packet Injection 10
Session Hijacking 11
SSL Stripping 11
Preventing Man-in-the-Middle Attacks 11
Strong WEP/WAP Encryption on Access Points 11
Virtual Private Network 12
Force HTTPS 12
Public Key Pair Based Authentication 12
Recent example of the attack 12
Conclusion 14
References 15

2MAN-IN-THE-MIDDLE ATTACK
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3MAN-IN-THE-MIDDLE ATTACK
Introduction
The rate of cyber-attacks has gradually increased over years. The Small sized and
large sized enterprises are often targeted by the group of attackers. The governmental and
corporate offices have also been attacked several times in the last decade. The cyber-attacks
are mostly intentional and motivated criminally or either politically who breaks down the
system of the organization and creates delay in the operation of any organization (Uma and
Padmavathi 2013).
The cyber-attacks are any kind of offensive attacks or the actions that generally
attacks on the computer information systems or the organizational infrastructures that deals
with or runs on computer networks and devices and involves various methodologies that
helps them to steal the data from the organization’s system network (Kotenko and Chechulin
2013). The Cyber-attacks are of various kinds. Some of them are Man in the middle attacks,
denial of service DOS attacks, phishing as well as spear phishing attacks, password attacks,
drive by attacks, SQL injection attacks, XSS cross site scripting attacks.
The aim of the report is to evaluate one of the cyber-attacks which are known as the
MitM attack. The MitM attack happens or is done when an attacker or group or the hacker
gets himself between the transaction or communication process that is continued between the
client and a server or the authorities and stakeholders related to the organization.
Discussion
The Man-in-the-Middle (MitM) attack
The MitM attack has some general and common kinds of attack, which are namely:
Introduction
The rate of cyber-attacks has gradually increased over years. The Small sized and
large sized enterprises are often targeted by the group of attackers. The governmental and
corporate offices have also been attacked several times in the last decade. The cyber-attacks
are mostly intentional and motivated criminally or either politically who breaks down the
system of the organization and creates delay in the operation of any organization (Uma and
Padmavathi 2013).
The cyber-attacks are any kind of offensive attacks or the actions that generally
attacks on the computer information systems or the organizational infrastructures that deals
with or runs on computer networks and devices and involves various methodologies that
helps them to steal the data from the organization’s system network (Kotenko and Chechulin
2013). The Cyber-attacks are of various kinds. Some of them are Man in the middle attacks,
denial of service DOS attacks, phishing as well as spear phishing attacks, password attacks,
drive by attacks, SQL injection attacks, XSS cross site scripting attacks.
The aim of the report is to evaluate one of the cyber-attacks which are known as the
MitM attack. The MitM attack happens or is done when an attacker or group or the hacker
gets himself between the transaction or communication process that is continued between the
client and a server or the authorities and stakeholders related to the organization.
Discussion
The Man-in-the-Middle (MitM) attack
The MitM attack has some general and common kinds of attack, which are namely:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4MAN-IN-THE-MIDDLE ATTACK
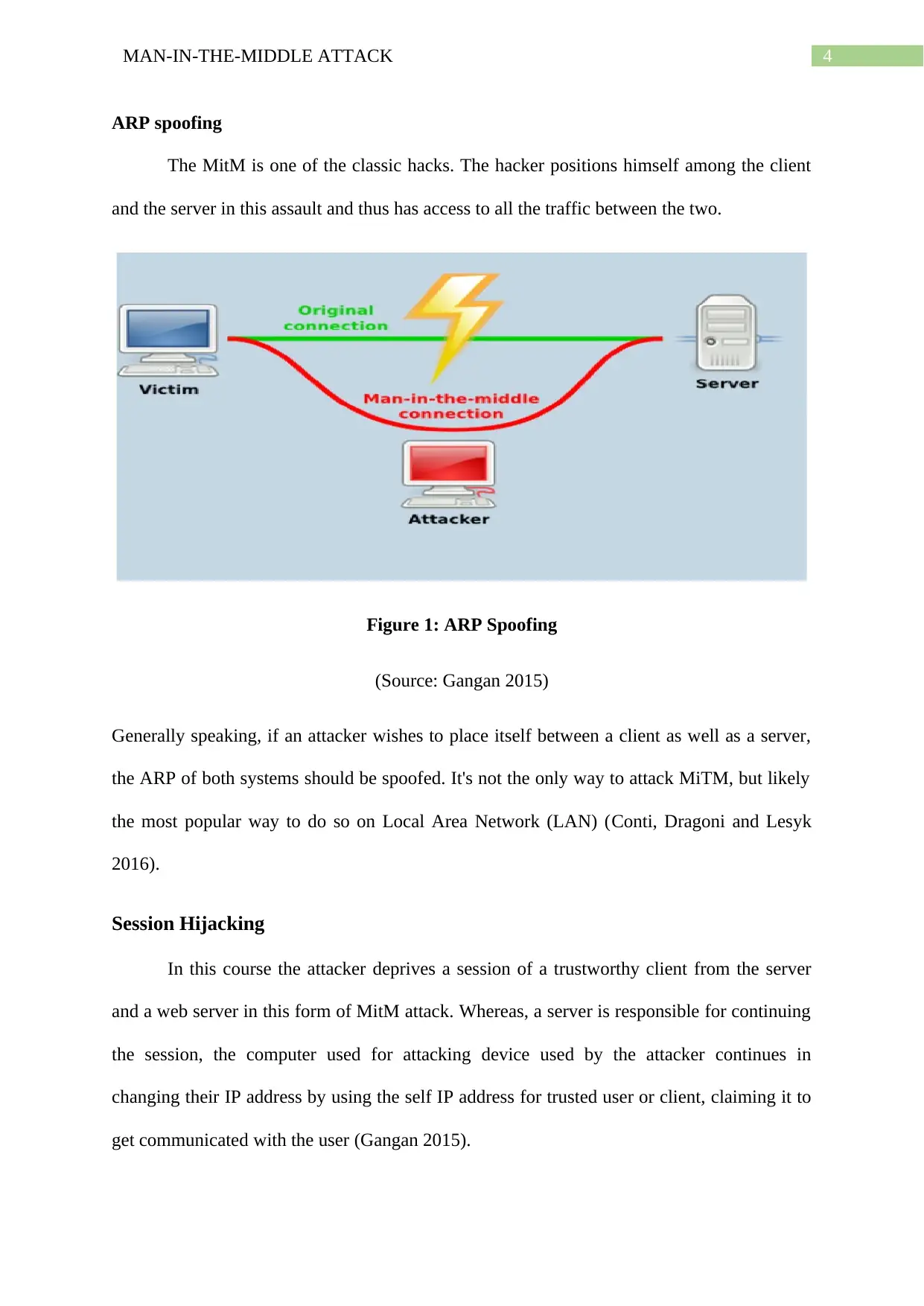
ARP spoofing
The MitM is one of the classic hacks. The hacker positions himself among the client
and the server in this assault and thus has access to all the traffic between the two.
Figure 1: ARP Spoofing
(Source: Gangan 2015)
Generally speaking, if an attacker wishes to place itself between a client as well as a server,
the ARP of both systems should be spoofed. It's not the only way to attack MiTM, but likely
the most popular way to do so on Local Area Network (LAN) (Conti, Dragoni and Lesyk
2016).
Session Hijacking
In this course the attacker deprives a session of a trustworthy client from the server
and a web server in this form of MitM attack. Whereas, a server is responsible for continuing
the session, the computer used for attacking device used by the attacker continues in
changing their IP address by using the self IP address for trusted user or client, claiming it to
get communicated with the user (Gangan 2015).
ARP spoofing
The MitM is one of the classic hacks. The hacker positions himself among the client
and the server in this assault and thus has access to all the traffic between the two.
Figure 1: ARP Spoofing
(Source: Gangan 2015)
Generally speaking, if an attacker wishes to place itself between a client as well as a server,
the ARP of both systems should be spoofed. It's not the only way to attack MiTM, but likely
the most popular way to do so on Local Area Network (LAN) (Conti, Dragoni and Lesyk
2016).
Session Hijacking
In this course the attacker deprives a session of a trustworthy client from the server
and a web server in this form of MitM attack. Whereas, a server is responsible for continuing
the session, the computer used for attacking device used by the attacker continues in
changing their IP address by using the self IP address for trusted user or client, claiming it to
get communicated with the user (Gangan 2015).

5MAN-IN-THE-MIDDLE ATTACK
The attack can be of these types:
1. A server is connected to a customer.
2. The client is controlled by the attacker's computer.
3. The computer of the attacker disconnects the client.
4. A device of the attacker substitutes the IP of the client in place with their own IP
addresses and then starts the malicious activities like the spoofing the section
amount of the client.
5. The machine of the attacker remains the server dialog and the server are confident
to communicate along the client or users.
IP Spoofing
IP spoofing can be referred to as an illegal activity or a technology which is
commonly used by an attacker to persuade a system to communicate and give the attacker
access to a recognized, trusted entity. Instead of sending the source address for the Internet
Protocol of the trusted and communicable host to a destination host, the attacker then sends a
packet to its own IP based source (Brooks and Yang 2015). The destination host could
acknowledge and act on the packet.
The attack can be of these types:
1. A server is connected to a customer.
2. The client is controlled by the attacker's computer.
3. The computer of the attacker disconnects the client.
4. A device of the attacker substitutes the IP of the client in place with their own IP
addresses and then starts the malicious activities like the spoofing the section
amount of the client.
5. The machine of the attacker remains the server dialog and the server are confident
to communicate along the client or users.
IP Spoofing
IP spoofing can be referred to as an illegal activity or a technology which is
commonly used by an attacker to persuade a system to communicate and give the attacker
access to a recognized, trusted entity. Instead of sending the source address for the Internet
Protocol of the trusted and communicable host to a destination host, the attacker then sends a
packet to its own IP based source (Brooks and Yang 2015). The destination host could
acknowledge and act on the packet.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6MAN-IN-THE-MIDDLE ATTACK
Figure 2: IP Spoofing
(Source: Jero et al. 2017)
Replay
A replay attack happens as an assailant communication and ends up costing ancient
emails and subsequently attempts to give them to the participant. Session timestamps can
readily counter this sort of device.
No single technology or setup is currently available to avoid all MitM-attacks
(Alqahtani and Iftikhar 2013). Encryption and digital certificates generally guarantee the
confidentiality and integrity of communications by effectively safeguarding MitM attacks.
But an assault by the man in the center can be injected into the records to prevent encryption
— for instance, assailant "A" intercepts the individual "P" public key and replaces the
individual with its own and general public key.
Figure 2: IP Spoofing
(Source: Jero et al. 2017)
Replay
A replay attack happens as an assailant communication and ends up costing ancient
emails and subsequently attempts to give them to the participant. Session timestamps can
readily counter this sort of device.
No single technology or setup is currently available to avoid all MitM-attacks
(Alqahtani and Iftikhar 2013). Encryption and digital certificates generally guarantee the
confidentiality and integrity of communications by effectively safeguarding MitM attacks.
But an assault by the man in the center can be injected into the records to prevent encryption
— for instance, assailant "A" intercepts the individual "P" public key and replaces the
individual with its own and general public key.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7MAN-IN-THE-MIDDLE ATTACK
When an encrypted signal is needed to be sent by any user with the public key of P to
P will then use the public key of A unknowingly. The system hence, provides the facility to A
to read the messages and attributes for P and then A can also send the message for P, encode
with a true public key of P, and P never notices that the message has been affected (Maynard,
McLaughlin and Haberler 2014). A may also change the email before sending it back to P. P
uses encryption, as we can see, and believes that its data is protected.
Where individual 2 (P2) wishes to drive a signal to P, the following technique must be
used if P wishes to ensure that A does not read or amend the text, and the message has
effectively been received from P2:
1. P2 generates and encrypts a symmetric key with the public key of P.
2. P2 transacts a symmetrical encrypted key to P.
3. P2 calculates and digitally signs the hash function of the email.
4. Using a symmetrical key, P2 encrypts its message and hash signed the email and
sends it to all P.
5. P can obtain the P2 symmetrical key, only since it has a personal encryption key,
and only P can decrypt the message which has been forwarded in a symmetrically
way of encryption. The attacker needs to assign the hash as the attacker already has
the symmetric based key.
6. He can confirm that the message was not changed because it is able to compute and
compare the hash of the message he got.
7. P can also demonstrate to himself that P2 is the sender because the hash can only be
signed by P2, so it can be confirmed with a government P2 key.
When an encrypted signal is needed to be sent by any user with the public key of P to
P will then use the public key of A unknowingly. The system hence, provides the facility to A
to read the messages and attributes for P and then A can also send the message for P, encode
with a true public key of P, and P never notices that the message has been affected (Maynard,
McLaughlin and Haberler 2014). A may also change the email before sending it back to P. P
uses encryption, as we can see, and believes that its data is protected.
Where individual 2 (P2) wishes to drive a signal to P, the following technique must be
used if P wishes to ensure that A does not read or amend the text, and the message has
effectively been received from P2:
1. P2 generates and encrypts a symmetric key with the public key of P.
2. P2 transacts a symmetrical encrypted key to P.
3. P2 calculates and digitally signs the hash function of the email.
4. Using a symmetrical key, P2 encrypts its message and hash signed the email and
sends it to all P.
5. P can obtain the P2 symmetrical key, only since it has a personal encryption key,
and only P can decrypt the message which has been forwarded in a symmetrically
way of encryption. The attacker needs to assign the hash as the attacker already has
the symmetric based key.
6. He can confirm that the message was not changed because it is able to compute and
compare the hash of the message he got.
7. P can also demonstrate to himself that P2 is the sender because the hash can only be
signed by P2, so it can be confirmed with a government P2 key.

8MAN-IN-THE-MIDDLE ATTACK
Man-in - the-middle assaults are a popular cyber security-assault which enables
attackers to wake up between and arise between two clients-based target that are getting
connected interaction. The attack I generally found arising between two or more hosts that
are that communicate legally and allow the invader to "hear" the discussion that is the name
"man-in - the-center."
Figure 3: Replay Attacks
(Source: Conti, Dragoni and Lesyk 2016)
Man-in-the-Middle Attacks and their Types
Rogue Access Point
Wireless based IT devices like the computers connected with the internet often
attempt to link automatically to the Access Points which is responsible for sending the largest
bandwidth of signal. The online phishers are able to build up their own and potential wireless
connection to their domain and trick neighboring equipment. The attacker can now
manipulate all network traffic of the victim. These are hazardous as, attackers do not need to
stay on the network side or the positive network side, they merely require a sufficiently close
objective area for proceeding (Banu and Banu 2013).
Man-in - the-middle assaults are a popular cyber security-assault which enables
attackers to wake up between and arise between two clients-based target that are getting
connected interaction. The attack I generally found arising between two or more hosts that
are that communicate legally and allow the invader to "hear" the discussion that is the name
"man-in - the-center."
Figure 3: Replay Attacks
(Source: Conti, Dragoni and Lesyk 2016)
Man-in-the-Middle Attacks and their Types
Rogue Access Point
Wireless based IT devices like the computers connected with the internet often
attempt to link automatically to the Access Points which is responsible for sending the largest
bandwidth of signal. The online phishers are able to build up their own and potential wireless
connection to their domain and trick neighboring equipment. The attacker can now
manipulate all network traffic of the victim. These are hazardous as, attackers do not need to
stay on the network side or the positive network side, they merely require a sufficiently close
objective area for proceeding (Banu and Banu 2013).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9MAN-IN-THE-MIDDLE ATTACK
Figure 4: Rouge Access Point
(Source: Maynard, McLaughlin and Haberler 2014)
ARP Spoofing
ARP stands for the address resolution protocol. It is used for resolving IP addresses in
a local area network to physical MAC (mediate access control). In case the host has a specific
IP address to talk to a host, this refers to the ARP cache to solve the IP address of a MAC. If
the address is not known, the MAC that is sustained within the device and network along
with the IP address is often gets requested so as to complete the process.
An attacker who wishes to pretense as yet a different recipient can react to demands
that it does not have its own MAC address to answer. An intruder can sniff the personal
traffic among two hosts with some exactly positioned packets (Wang and Wyglinski 2016).
Valuable data such as exchanging tokens and providing complete access to request accounts
that should not be available to the attacker can be obtained from either the Traffic.
MDNS Spoofing
Multicast DNS is DNS-like but is made using broadcast like ARP on the local area
network (LAN). This makes it an ideal spoofing target. Network device setup should be made
Figure 4: Rouge Access Point
(Source: Maynard, McLaughlin and Haberler 2014)
ARP Spoofing
ARP stands for the address resolution protocol. It is used for resolving IP addresses in
a local area network to physical MAC (mediate access control). In case the host has a specific
IP address to talk to a host, this refers to the ARP cache to solve the IP address of a MAC. If
the address is not known, the MAC that is sustained within the device and network along
with the IP address is often gets requested so as to complete the process.
An attacker who wishes to pretense as yet a different recipient can react to demands
that it does not have its own MAC address to answer. An intruder can sniff the personal
traffic among two hosts with some exactly positioned packets (Wang and Wyglinski 2016).
Valuable data such as exchanging tokens and providing complete access to request accounts
that should not be available to the attacker can be obtained from either the Traffic.
MDNS Spoofing
Multicast DNS is DNS-like but is made using broadcast like ARP on the local area
network (LAN). This makes it an ideal spoofing target. Network device setup should be made
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10MAN-IN-THE-MIDDLE ATTACK
incredibly easy through the local name resolution scheme. Users don't need to understand
precisely what addresses their phones should contact; they can solve the scheme for them.
This protocol is used by devices like TVs, printers and entertainment systems, as they
are generally on trusted Internet networks. An intruder can readily react with false
information to an application that wants to understand the address that has been created or
stays for a certain device like tv. local, so that they can solve the problem to an address they
control. Since systems maintain a local address cache, the perpetrator will now see the
appliance of the attacker as being trusted for a long time (Agarwal, Biswas and Nandi 2015).
DNS Spoofing
Like the manner ARP solves MAC IP addresses on a LAN, DNS solves IP Domain
Names. The situation during the DNS spoofing attack is used, an attacker tries to enter a host
with corrupted DNS cache details in order to access a further host using its domain name.
This causes the victim to send a malicious host which is a kind of sensitive data along with
the conviction where they send data to a trusted source (Jero et al. 2017). An intruder who
has authenticated an IP address could spoof DNS much simpler by merely removing the
address of the target from a DNS server.
Man-in-the-Middle Attack Techniques
Sniffing
For inspecting packets at the low level, assailants use packet capture instruments.
Using certain wireless equipment that are permitted to be monitored or promiscuous, an
intruder can view packets not meant to be viewed, for example packets that are directed to
others.
incredibly easy through the local name resolution scheme. Users don't need to understand
precisely what addresses their phones should contact; they can solve the scheme for them.
This protocol is used by devices like TVs, printers and entertainment systems, as they
are generally on trusted Internet networks. An intruder can readily react with false
information to an application that wants to understand the address that has been created or
stays for a certain device like tv. local, so that they can solve the problem to an address they
control. Since systems maintain a local address cache, the perpetrator will now see the
appliance of the attacker as being trusted for a long time (Agarwal, Biswas and Nandi 2015).
DNS Spoofing
Like the manner ARP solves MAC IP addresses on a LAN, DNS solves IP Domain
Names. The situation during the DNS spoofing attack is used, an attacker tries to enter a host
with corrupted DNS cache details in order to access a further host using its domain name.
This causes the victim to send a malicious host which is a kind of sensitive data along with
the conviction where they send data to a trusted source (Jero et al. 2017). An intruder who
has authenticated an IP address could spoof DNS much simpler by merely removing the
address of the target from a DNS server.
Man-in-the-Middle Attack Techniques
Sniffing
For inspecting packets at the low level, assailants use packet capture instruments.
Using certain wireless equipment that are permitted to be monitored or promiscuous, an
intruder can view packets not meant to be viewed, for example packets that are directed to
others.
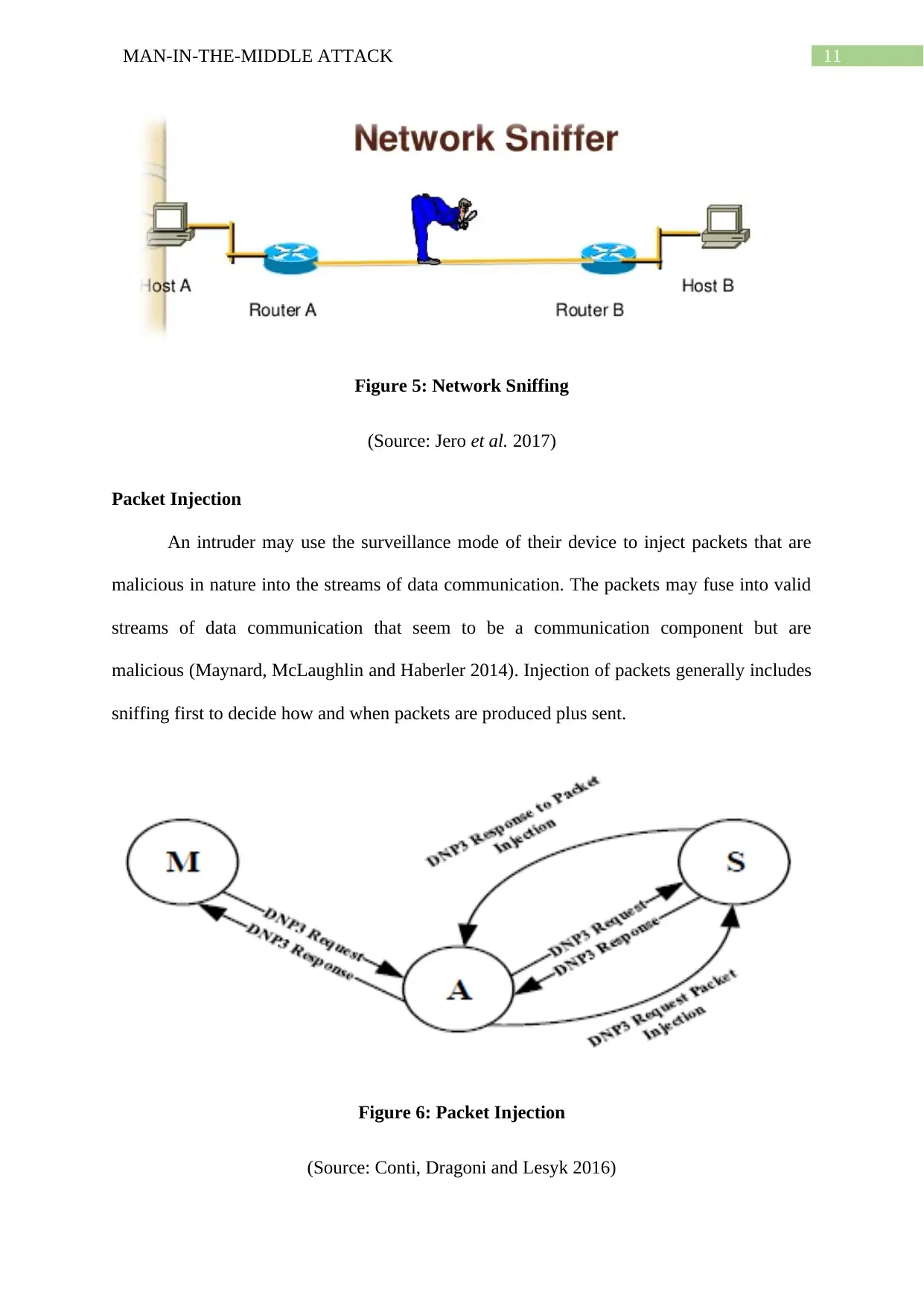
11MAN-IN-THE-MIDDLE ATTACK
Figure 5: Network Sniffing
(Source: Jero et al. 2017)
Packet Injection
An intruder may use the surveillance mode of their device to inject packets that are
malicious in nature into the streams of data communication. The packets may fuse into valid
streams of data communication that seem to be a communication component but are
malicious (Maynard, McLaughlin and Haberler 2014). Injection of packets generally includes
sniffing first to decide how and when packets are produced plus sent.
Figure 6: Packet Injection
(Source: Conti, Dragoni and Lesyk 2016)
Figure 5: Network Sniffing
(Source: Jero et al. 2017)
Packet Injection
An intruder may use the surveillance mode of their device to inject packets that are
malicious in nature into the streams of data communication. The packets may fuse into valid
streams of data communication that seem to be a communication component but are
malicious (Maynard, McLaughlin and Haberler 2014). Injection of packets generally includes
sniffing first to decide how and when packets are produced plus sent.
Figure 6: Packet Injection
(Source: Conti, Dragoni and Lesyk 2016)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




