Analysis of VPN Applications, Security Protocols, and Key Exchange
VerifiedAdded on 2023/06/15
|8
|1128
|307
Report
AI Summary
This report delves into the applications and significance of Virtual Private Networks (VPNs), focusing on their role in securing network communications. It elucidates three mechanisms by which VPNs ensure user privacy, including secure encryption using AES, secure data transfer through private servers, and the use of encrypting protocols like IPSEC. A comparison is made between the Authentication Header (AH) and Encapsulating Security Payload (ESP) protocols, highlighting AH's data integrity protection versus ESP's provision of data confidentiality. The report also explains VPN tunnel modes and components for phase 2 of IKEv1, including Triple DES, AES-128, SHA1, and MODP groups. Furthermore, it addresses the Diffie-Hellman key exchange protocol, noting its vulnerability to man-in-the-middle attacks. The report concludes that VPNs are crucial for secure data transfer and network security, providing a detailed overview of their underlying mechanisms and protocols.

VPN APPLICATIONS AND
SIGNIFICANCE
SIGNIFICANCE
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENT
INTRODUCTION...........................................................................................................................3
MAIN BODY...................................................................................................................................3
TASK 3............................................................................................................................................3
Three possible mechanism...........................................................................................................3
TASK 4............................................................................................................................................4
a) Comparison between the authentication header (AH) and encapsulating security payload
(ESP) protocols............................................................................................................................4
TASK 5............................................................................................................................................4
CONCLUSION................................................................................................................................6
REFERENCES................................................................................................................................8
INTRODUCTION...........................................................................................................................3
MAIN BODY...................................................................................................................................3
TASK 3............................................................................................................................................3
Three possible mechanism...........................................................................................................3
TASK 4............................................................................................................................................4
a) Comparison between the authentication header (AH) and encapsulating security payload
(ESP) protocols............................................................................................................................4
TASK 5............................................................................................................................................4
CONCLUSION................................................................................................................................6
REFERENCES................................................................................................................................8

INTRODUCTION
Virtual private network is the encrypted network which is connected with the internet
through a device or object to network (Zhang, 2018). It is mainly used for remotely accessing
the private network. This report will carry out the three mechanism for VPN working along with
the authentication header and encapsulating security payload. It further explains the VPN tunnel
modes, and components for phase 2 IKEv1.
MAIN BODY
TASK 3
Three possible mechanism
VPN secure the privacy of the user by encrypting the computer traffic of the user's
system and then routed this traffic from an unidentified router. It means that only user and server
is able to decrypt the traffic that makes a VPN a private network.
Secure encryption: AES encryption is important as it helps to secure the data, without
encryption key it is impossible to access or read the data. Computer system will take millions of
years in order to decrypt data if there is no encrypted key.
Secure transferring of data: To access the network, VPN is important as it directly connects to
the private servers and enables the encryption method in order to avoid any risk for data transfer.
Encrypting protocol: IPSEC collection of the protocols that enables the private connectivity
between the two points, as it makes the VPN secure network which ensures the user's data
privacy (Karaymeh and et.al 2019).
Virtual private network is the encrypted network which is connected with the internet
through a device or object to network (Zhang, 2018). It is mainly used for remotely accessing
the private network. This report will carry out the three mechanism for VPN working along with
the authentication header and encapsulating security payload. It further explains the VPN tunnel
modes, and components for phase 2 IKEv1.
MAIN BODY
TASK 3
Three possible mechanism
VPN secure the privacy of the user by encrypting the computer traffic of the user's
system and then routed this traffic from an unidentified router. It means that only user and server
is able to decrypt the traffic that makes a VPN a private network.
Secure encryption: AES encryption is important as it helps to secure the data, without
encryption key it is impossible to access or read the data. Computer system will take millions of
years in order to decrypt data if there is no encrypted key.
Secure transferring of data: To access the network, VPN is important as it directly connects to
the private servers and enables the encryption method in order to avoid any risk for data transfer.
Encrypting protocol: IPSEC collection of the protocols that enables the private connectivity
between the two points, as it makes the VPN secure network which ensures the user's data
privacy (Karaymeh and et.al 2019).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

TASK 4
a) Comparison between the authentication header (AH) and encapsulating security payload
(ESP) protocols
Authentication header mainly gives the data integrity and complete protection, however it still
not provides the confidentiality for data, that means data can be seen clearly when it transfer.
Whereas ESP protocols enables the user to encrypt the data or authenticates the data packets by
using the VPN network. Therefore, the key difference can be seen in AH and ESP protocol is
that AH does not support the confidentiality but ESP provides the Confidentiality.
Characteristics of AH is that it helps to verify the packet's origin and it ensures that both
payload and the header are not tangle during the transmission. Whereas ESP characteristics is to
enable the different services as to manage the datagram confidentiality with encryption process.
b)
VPN tunnel mode is used between the gateways that may be routers or ASA firewalls. In which
the gateway is pretending as proxy for host. In this client can directly connect with the IPSec
gateway, in such the traffic is encrypted from the client side and encapsulated the other data
packet and sent it to the end.
TASK 5
a)
Illustration 1: Packet diagram
a) Comparison between the authentication header (AH) and encapsulating security payload
(ESP) protocols
Authentication header mainly gives the data integrity and complete protection, however it still
not provides the confidentiality for data, that means data can be seen clearly when it transfer.
Whereas ESP protocols enables the user to encrypt the data or authenticates the data packets by
using the VPN network. Therefore, the key difference can be seen in AH and ESP protocol is
that AH does not support the confidentiality but ESP provides the Confidentiality.
Characteristics of AH is that it helps to verify the packet's origin and it ensures that both
payload and the header are not tangle during the transmission. Whereas ESP characteristics is to
enable the different services as to manage the datagram confidentiality with encryption process.
b)
VPN tunnel mode is used between the gateways that may be routers or ASA firewalls. In which
the gateway is pretending as proxy for host. In this client can directly connect with the IPSec
gateway, in such the traffic is encrypted from the client side and encapsulated the other data
packet and sent it to the end.
TASK 5
a)
Illustration 1: Packet diagram
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Main function of the IKEv is to negotiate the IPSec Sas for setting down the IPSec tunnel, it
secures the SA parameters by using the IKE SA key. It is often called as the quickest mode as it
has only one mode. The main components are found as Triple DES, AES-128, it matches with
the same setting for the phase 1 (Zhou and Zhang, 2020). Also, SHA1, ESP mode of tunnel and
MODP group that's up to the 16.
b)
Diffie Hellman key exchange is the protocol that allows the communication between the parties
by using the public channel mode. In which the public channel is created to enable the mutual
secret that are uses over the internet. DH allows the two parties to encrypt or decrypt their data
by taking the use of the public key. AS DH is vulnerable in man in a middle attack, because it
does not verify other's identity on different side. As in which the attacker detains the exchange of
key and provides it to other sides. It is vulnerable to the attack, it allows the communication
between the parties by using the same key for creating the secure environment.
c)
IKEv, is mainly used for creating the secure authenticated conversation or transmission channel
by implementing the Diffie-Hellman key exchange process. It is used to develop the secret keys
that can be used for encryption the IKE communication. Although the negotiation outcomes can
be obtained in only by directional ISAKMP “Security association” (Lacković and Tomić, 2017).
Phase one tunnel is mainly used for managing the traffic, if it is not implemented then there
might be problem encounter related to the traffic over the network.
secures the SA parameters by using the IKE SA key. It is often called as the quickest mode as it
has only one mode. The main components are found as Triple DES, AES-128, it matches with
the same setting for the phase 1 (Zhou and Zhang, 2020). Also, SHA1, ESP mode of tunnel and
MODP group that's up to the 16.
b)
Diffie Hellman key exchange is the protocol that allows the communication between the parties
by using the public channel mode. In which the public channel is created to enable the mutual
secret that are uses over the internet. DH allows the two parties to encrypt or decrypt their data
by taking the use of the public key. AS DH is vulnerable in man in a middle attack, because it
does not verify other's identity on different side. As in which the attacker detains the exchange of
key and provides it to other sides. It is vulnerable to the attack, it allows the communication
between the parties by using the same key for creating the secure environment.
c)
IKEv, is mainly used for creating the secure authenticated conversation or transmission channel
by implementing the Diffie-Hellman key exchange process. It is used to develop the secret keys
that can be used for encryption the IKE communication. Although the negotiation outcomes can
be obtained in only by directional ISAKMP “Security association” (Lacković and Tomić, 2017).
Phase one tunnel is mainly used for managing the traffic, if it is not implemented then there
might be problem encounter related to the traffic over the network.
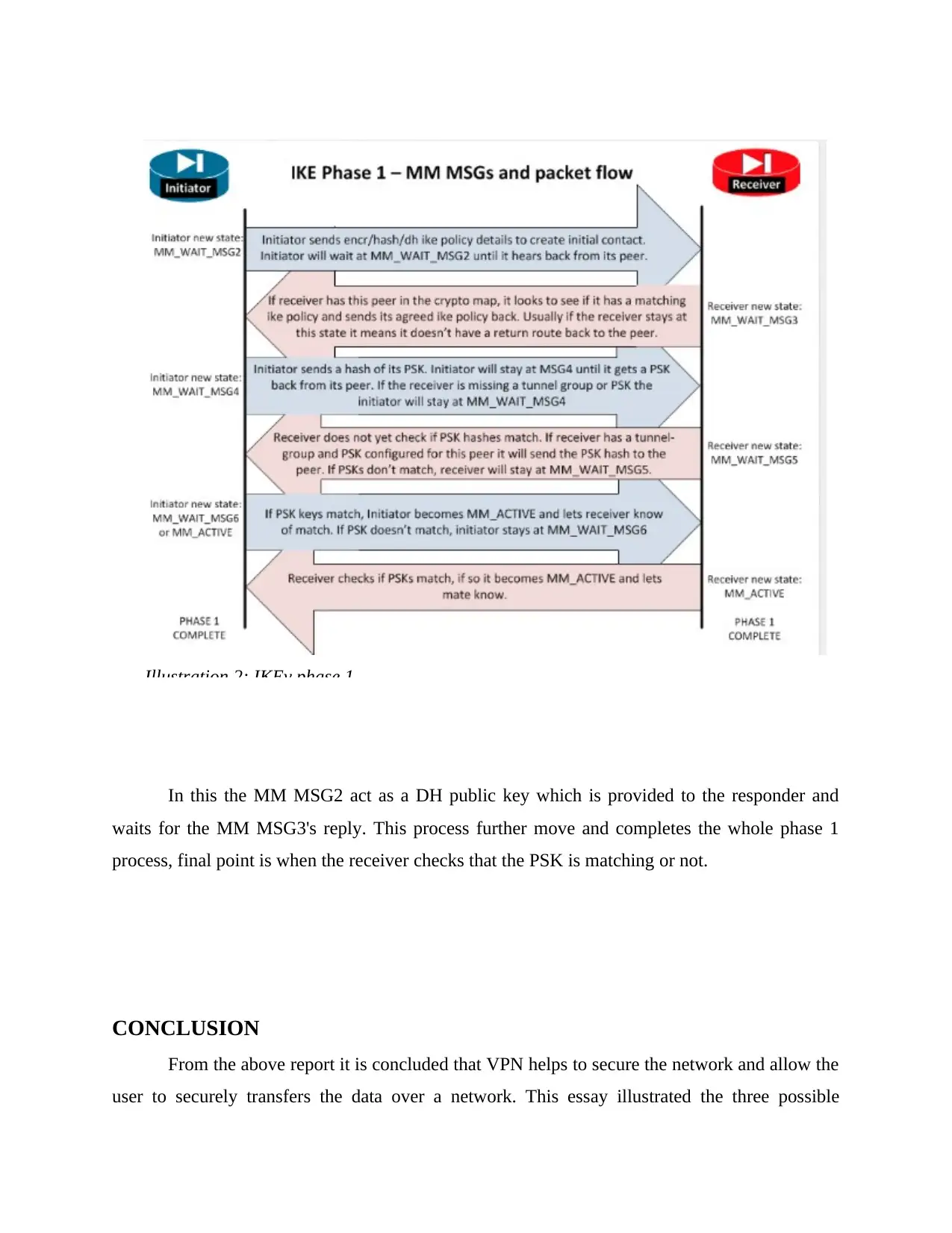
In this the MM MSG2 act as a DH public key which is provided to the responder and
waits for the MM MSG3's reply. This process further move and completes the whole phase 1
process, final point is when the receiver checks that the PSK is matching or not.
CONCLUSION
From the above report it is concluded that VPN helps to secure the network and allow the
user to securely transfers the data over a network. This essay illustrated the three possible
Illustration 2: IKEv phase 1
waits for the MM MSG3's reply. This process further move and completes the whole phase 1
process, final point is when the receiver checks that the PSK is matching or not.
CONCLUSION
From the above report it is concluded that VPN helps to secure the network and allow the
user to securely transfers the data over a network. This essay illustrated the three possible
Illustration 2: IKEv phase 1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

mechanism for the VPN along with the description about ESP and AH. It further carried out the
Diffie Hellman's vulnerability to attacks.
Diffie Hellman's vulnerability to attacks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Books and Journals
Karaymeh, A. and et.al 2019, October. Enhancing Data Protection Provided by VPN
Connections over Open WiFi Networks. In 2019 2nd International Conference on new
Trends in Computing Sciences (ICTCS) (pp. 1-6). IEEE.
Lacković, D. and Tomić, M., 2017, May. Performance analysis of virtualized VPN endpoints.
In 2017 40th International Convention on Information and Communication Technology,
Electronics and Microelectronics (MIPRO) (pp. 466-471). IEEE.
Zhang, J., 2018, December. Research on Key Technology of VPN Protocol Recognition. In 2018
IEEE International Conference of Safety Produce Informatization (IICSPI) (pp. 161-164).
IEEE.
Zhou, Y. and Zhang, K., 2020, June. DoS Vulnerability Verification of IPSec VPN. In 2020
IEEE International Conference on Artificial Intelligence and Computer Applications
(ICAICA) (pp. 698-702). IEEE.
Books and Journals
Karaymeh, A. and et.al 2019, October. Enhancing Data Protection Provided by VPN
Connections over Open WiFi Networks. In 2019 2nd International Conference on new
Trends in Computing Sciences (ICTCS) (pp. 1-6). IEEE.
Lacković, D. and Tomić, M., 2017, May. Performance analysis of virtualized VPN endpoints.
In 2017 40th International Convention on Information and Communication Technology,
Electronics and Microelectronics (MIPRO) (pp. 466-471). IEEE.
Zhang, J., 2018, December. Research on Key Technology of VPN Protocol Recognition. In 2018
IEEE International Conference of Safety Produce Informatization (IICSPI) (pp. 161-164).
IEEE.
Zhou, Y. and Zhang, K., 2020, June. DoS Vulnerability Verification of IPSec VPN. In 2020
IEEE International Conference on Artificial Intelligence and Computer Applications
(ICAICA) (pp. 698-702). IEEE.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



