UniSA: Stakeholder Engagement for Cloud Email Implementation
VerifiedAdded on 2022/12/27
|13
|2880
|68
Report
AI Summary
This report addresses the stakeholder engagement strategy for the University of South Australia (UniSA) as they transition from their on-premise Exchange 2013 email system to a cloud-based solution. The existing system is highly reliable and integrated with critical university functions like timetabling, HR, and course management. The report analyzes the current email environment, details the proposed changes, and identifies potential risks associated with the migration, including incomplete data deletion, increased complexity for stakeholders, data security concerns, and reduced stakeholder control. A communication plan is proposed to manage stakeholder expectations and address concerns, along with a governance framework for the new cloud-based email system. The report concludes by emphasizing the need for careful stakeholder engagement to ensure a smooth and successful transition, mitigating risks and maintaining effective communication within the university. The report also stresses on the need to adjust the system and make it compatible with the global and industrial requirements.

Running head: ENGAGEMENT OF STAKEHOLDERS IN IT ORGANIZATIONS
ENGAGEMENT OF STAKEHOLDERS IN IT ORGANIZATIONS
Name of the Student
Name of the University
Author Note
ENGAGEMENT OF STAKEHOLDERS IN IT ORGANIZATIONS
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ENGAGEMENT OF STAKEHOLDERS IN IT ORGANIZATIONS
Executive Summary
University of South Australia is trying to implement the new system of cloud in their
email functioning by replacing it with the existing Premise Exchange system. The
existing system is very reliable and is preferred by most of the stakeholders of the
university, but the authority wants to modernize their email system by implementing
cloud technology. The existing system is used in the daily operation of the university
like placement and study oriented purposes. The implementation of cloud based
email system will reduce the control of the stakeholders over the data. The
transformation from the Premise Exchange system to the cloud based email system
will not be easy for the stakeholders of the university as they have to get adjusted
with the new cloud based email system.
Executive Summary
University of South Australia is trying to implement the new system of cloud in their
email functioning by replacing it with the existing Premise Exchange system. The
existing system is very reliable and is preferred by most of the stakeholders of the
university, but the authority wants to modernize their email system by implementing
cloud technology. The existing system is used in the daily operation of the university
like placement and study oriented purposes. The implementation of cloud based
email system will reduce the control of the stakeholders over the data. The
transformation from the Premise Exchange system to the cloud based email system
will not be easy for the stakeholders of the university as they have to get adjusted
with the new cloud based email system.

2ENGAGEMENT OF STAKEHOLDERS IN IT ORGANIZATIONS
Table of Contents
1. Introduction...............................................................................................................3
2. Discussion................................................................................................................4
2.1. Analysis of current environment........................................................................4
2.2. Details of the change.........................................................................................4
2.3. Stakeholder identification / Risk analysis..........................................................5
2.3.1. Incomplete deletion of data.........................................................................5
2.3.2. Increase in the complexity for the stakeholders..........................................5
2.3.3. Credentials or data can be stolen...............................................................5
2.3.4. Reduced control and visibility of the stakeholders......................................6
2.4. Communication Plan..........................................................................................6
2.5. Proposed Governance Framework....................................................................7
3. Conclusion................................................................................................................8
4. References...............................................................................................................9
Appendix.....................................................................................................................10
1. Communication Plan...........................................................................................10
2. Proposed Governance Framework.....................................................................11
3. Risk Analysis.......................................................................................................12
Table of Contents
1. Introduction...............................................................................................................3
2. Discussion................................................................................................................4
2.1. Analysis of current environment........................................................................4
2.2. Details of the change.........................................................................................4
2.3. Stakeholder identification / Risk analysis..........................................................5
2.3.1. Incomplete deletion of data.........................................................................5
2.3.2. Increase in the complexity for the stakeholders..........................................5
2.3.3. Credentials or data can be stolen...............................................................5
2.3.4. Reduced control and visibility of the stakeholders......................................6
2.4. Communication Plan..........................................................................................6
2.5. Proposed Governance Framework....................................................................7
3. Conclusion................................................................................................................8
4. References...............................................................................................................9
Appendix.....................................................................................................................10
1. Communication Plan...........................................................................................10
2. Proposed Governance Framework.....................................................................11
3. Risk Analysis.......................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3ENGAGEMENT OF STAKEHOLDERS IN IT ORGANIZATIONS
1. Introduction
The University of South Australia is the biggest university in the South
Australia. It is located in the Adelaide having a great academic performance since its
establishment. The present system which prevails in this premium university for
email functioning is Premise Exchange system. This system for functioning of email
in this university have been established in 2013 and from then this system has
provided reliable service to the students, teachers and staffs of the organization. The
university authorities are thinking about changing the existing email system with a
cloud based email system.
The cloud based email system is much easier to access by the user as it does
not requires maintaining of hardware by the users. The developers of the cloud
based email system suggests user to use this system as it is more efficient and have
a seamless operation along with better security.
This report will discuss about the analysis of current email system used in the
university along with the details of the change required for implementing cloud based
email system. The impact of the change and the risk factors for the change will be
analyzed in the report along with the discussion of communication plan.
1. Introduction
The University of South Australia is the biggest university in the South
Australia. It is located in the Adelaide having a great academic performance since its
establishment. The present system which prevails in this premium university for
email functioning is Premise Exchange system. This system for functioning of email
in this university have been established in 2013 and from then this system has
provided reliable service to the students, teachers and staffs of the organization. The
university authorities are thinking about changing the existing email system with a
cloud based email system.
The cloud based email system is much easier to access by the user as it does
not requires maintaining of hardware by the users. The developers of the cloud
based email system suggests user to use this system as it is more efficient and have
a seamless operation along with better security.
This report will discuss about the analysis of current email system used in the
university along with the details of the change required for implementing cloud based
email system. The impact of the change and the risk factors for the change will be
analyzed in the report along with the discussion of communication plan.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4ENGAGEMENT OF STAKEHOLDERS IN IT ORGANIZATIONS
2. Discussion
2.1. Analysis of current environment
University of South Australia is currently using Premise Exchange system for
their email functioning. This system was established in the system of the university in
2013. The system was very reliable as this system was integrated with other
systems of the university. This system for the email is accessed by the students,
staff and the alumni. The routine for the students and the faculties are scheduled in
the system according to the organized events.
The system of PeopleSoft enrolment along with the HR system of the
university which is responsible for maintaining the database of the onboarding and
off boarding of the students uses the Premise Exchange system for communication
purposes (Hingorani and Askari-Danesh 2014). The onboarding and off boarding
system is directly linked with the database system of the Human Resource
department of any organization. Onboarding means the addition of the candidate in
the organization and off boarding means the exit or departure of the candidate from
the organization through mutual terms with HR (Anders 2017). These processes
requires a great amount of communication. The system of onboarding and off
boarding in the University of South Australia is completely dependent on the Premise
Exchange system.
The IT stakeholder engagement course of the university is also linked with the
Premise Exchange system. The engagement course is for the students who can
access the system for getting updates about the formation of class in the semester.
The course management system which is responsible for setting up the mailbox for
the students is also a part of this stakeholder engagement course. The mailbox
which is set-up by the management system will help the enrolled students to get their
attached study materials and the course learning sites which are required for their
purposes. The staff portals and other important updates about the students are
delivered to the staff and students through the email using Premise Exchange
system for functioning.
2.2. Details of the change
The University of South Australia wants to change their existing Premise
Exchange system for email with the cloud based email system for their daily
business operations. There are many units of the university which needs email to
support their daily business. The email system is the critical system for maintaining
communication with the stake holders on daily basis. The prevailing Premise
Exchange system for email in the university is very reliable and the change would be
very much difficult to adopt for the stake holders.
There are some changes which will happen due to the implementation of
cloud based email system in the place of the Premise Exchange system like the
hardware of the system will change (Rajaraman 2014). In the Premise Exchange
system the onsite servers needed attention for working perfectly but in the case of
2. Discussion
2.1. Analysis of current environment
University of South Australia is currently using Premise Exchange system for
their email functioning. This system was established in the system of the university in
2013. The system was very reliable as this system was integrated with other
systems of the university. This system for the email is accessed by the students,
staff and the alumni. The routine for the students and the faculties are scheduled in
the system according to the organized events.
The system of PeopleSoft enrolment along with the HR system of the
university which is responsible for maintaining the database of the onboarding and
off boarding of the students uses the Premise Exchange system for communication
purposes (Hingorani and Askari-Danesh 2014). The onboarding and off boarding
system is directly linked with the database system of the Human Resource
department of any organization. Onboarding means the addition of the candidate in
the organization and off boarding means the exit or departure of the candidate from
the organization through mutual terms with HR (Anders 2017). These processes
requires a great amount of communication. The system of onboarding and off
boarding in the University of South Australia is completely dependent on the Premise
Exchange system.
The IT stakeholder engagement course of the university is also linked with the
Premise Exchange system. The engagement course is for the students who can
access the system for getting updates about the formation of class in the semester.
The course management system which is responsible for setting up the mailbox for
the students is also a part of this stakeholder engagement course. The mailbox
which is set-up by the management system will help the enrolled students to get their
attached study materials and the course learning sites which are required for their
purposes. The staff portals and other important updates about the students are
delivered to the staff and students through the email using Premise Exchange
system for functioning.
2.2. Details of the change
The University of South Australia wants to change their existing Premise
Exchange system for email with the cloud based email system for their daily
business operations. There are many units of the university which needs email to
support their daily business. The email system is the critical system for maintaining
communication with the stake holders on daily basis. The prevailing Premise
Exchange system for email in the university is very reliable and the change would be
very much difficult to adopt for the stake holders.
There are some changes which will happen due to the implementation of
cloud based email system in the place of the Premise Exchange system like the
hardware of the system will change (Rajaraman 2014). In the Premise Exchange
system the onsite servers needed attention for working perfectly but in the case of

5ENGAGEMENT OF STAKEHOLDERS IN IT ORGANIZATIONS
cloud based e mail system the server does not need continuous surveillance. The IT
technician can give time on other projects rather than continuously looking after the
servers.
The implementation of cloud based email system can reduce disturbances in
the business activities which will help to increase the revenue. The software updates
and the various solutions or threats are also managed by the IT department of the
cloud based email service provider (Albakri et al. 2014). The IT technician of the
university will not have to think about these problems.
According to the service provider of the cloud based email, this system is
more secured than the Premise Exchange system. The system will be more secured
and there will be less complications. The servers of the system which is used in the
University of South Australia needs to be checked regularly by the IT technician.
Implementation of the cloud based email system will reduce that extra effort (Sharma
et al. 2016). The service provider would be responsible for any type of problem in the
system as they will provide complete software solution for the new cloud based IT
system.
The implementation of cloud based email system will also make the system
compatible with the global and industrial requirements like healthcare (HIPAA),
education (FERPA) and others (Glenn and Monteith 2014). It will also make the
system robust as it will make the system evolve according to the standards.
2.3. Stakeholder identification / Risk analysis
2.3.1. Incomplete deletion of data
The data which will be stored in the server will be uploaded to the cloud
servers through wired or wireless networking. In the university if any type of data is
uploaded by the user due to some mistake then it is impossible to delete every bit of
that data. The data will be already uploaded to the servers of the cloud and it is not
possible to delete all the data (Chou 2015). Some parts can be deleted but the data
will still be there in the server of the clouds.
2.3.2. Increase in the complexity for the stakeholders
The transformation from the Premise Exchange system to the cloud based
email system will not be very easy for the stakeholders of the university. The
students and the staff along with the other users of the email system of the university
will have to understand the new model or the infrastructures (Haimes et al. 2015).
There will be many changes in the system and the user will have to adjust to the
changes for maintaining the schedule of their work.
2.3.3. Credentials or data can be stolen
The data of the cloud based email service are stored in the database system
of the cloud. This system is usually much secured and only can be accessed by the
database administrator of the service provider and the user, but there can be case of
cloud based e mail system the server does not need continuous surveillance. The IT
technician can give time on other projects rather than continuously looking after the
servers.
The implementation of cloud based email system can reduce disturbances in
the business activities which will help to increase the revenue. The software updates
and the various solutions or threats are also managed by the IT department of the
cloud based email service provider (Albakri et al. 2014). The IT technician of the
university will not have to think about these problems.
According to the service provider of the cloud based email, this system is
more secured than the Premise Exchange system. The system will be more secured
and there will be less complications. The servers of the system which is used in the
University of South Australia needs to be checked regularly by the IT technician.
Implementation of the cloud based email system will reduce that extra effort (Sharma
et al. 2016). The service provider would be responsible for any type of problem in the
system as they will provide complete software solution for the new cloud based IT
system.
The implementation of cloud based email system will also make the system
compatible with the global and industrial requirements like healthcare (HIPAA),
education (FERPA) and others (Glenn and Monteith 2014). It will also make the
system robust as it will make the system evolve according to the standards.
2.3. Stakeholder identification / Risk analysis
2.3.1. Incomplete deletion of data
The data which will be stored in the server will be uploaded to the cloud
servers through wired or wireless networking. In the university if any type of data is
uploaded by the user due to some mistake then it is impossible to delete every bit of
that data. The data will be already uploaded to the servers of the cloud and it is not
possible to delete all the data (Chou 2015). Some parts can be deleted but the data
will still be there in the server of the clouds.
2.3.2. Increase in the complexity for the stakeholders
The transformation from the Premise Exchange system to the cloud based
email system will not be very easy for the stakeholders of the university. The
students and the staff along with the other users of the email system of the university
will have to understand the new model or the infrastructures (Haimes et al. 2015).
There will be many changes in the system and the user will have to adjust to the
changes for maintaining the schedule of their work.
2.3.3. Credentials or data can be stolen
The data of the cloud based email service are stored in the database system
of the cloud. This system is usually much secured and only can be accessed by the
database administrator of the service provider and the user, but there can be case of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6ENGAGEMENT OF STAKEHOLDERS IN IT ORGANIZATIONS
data stealing due to any type of breach in the system (Ali, Warren and Mathiassen
2017). The data is not always secured in the cloud based email system.
2.3.4. Reduced control and visibility of the stakeholders
The implementation of cloud based email system will reduce the control of the
stakeholders over the data. The university will lose many operations and data which
will be controlled by the service provider providing complete software solution. There
will be a shift of responsibility from the user to the service provider which depends on
the model of cloud service.
2.4. Communication Plan
The communication plan for the cloud based email can be described as the
process by which communication between various stakeholders can be maintained.
The main aim to implement the system of cloud based email is to enhance the
quality of communication along with the increased security and integrity.
The change in system will require the adoption of new type of strategy by the
stakeholders. The users will have to be careful before uploading any type of data
because the data cannot be deleted permanently.
The students, staffs and the alumni of the university should discuss in detail
about the communication with the IT technician of the organization for better
implementation of the new system (Zimmermann et al. 2017). The IT technician of
the university will be able to deliver the users with some effective ways to deal with
the new situation. The users have less control and visibility over the data in the
system thus security measures should be implemented by the users before
accessing the system.
data stealing due to any type of breach in the system (Ali, Warren and Mathiassen
2017). The data is not always secured in the cloud based email system.
2.3.4. Reduced control and visibility of the stakeholders
The implementation of cloud based email system will reduce the control of the
stakeholders over the data. The university will lose many operations and data which
will be controlled by the service provider providing complete software solution. There
will be a shift of responsibility from the user to the service provider which depends on
the model of cloud service.
2.4. Communication Plan
The communication plan for the cloud based email can be described as the
process by which communication between various stakeholders can be maintained.
The main aim to implement the system of cloud based email is to enhance the
quality of communication along with the increased security and integrity.
The change in system will require the adoption of new type of strategy by the
stakeholders. The users will have to be careful before uploading any type of data
because the data cannot be deleted permanently.
The students, staffs and the alumni of the university should discuss in detail
about the communication with the IT technician of the organization for better
implementation of the new system (Zimmermann et al. 2017). The IT technician of
the university will be able to deliver the users with some effective ways to deal with
the new situation. The users have less control and visibility over the data in the
system thus security measures should be implemented by the users before
accessing the system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7ENGAGEMENT OF STAKEHOLDERS IN IT ORGANIZATIONS
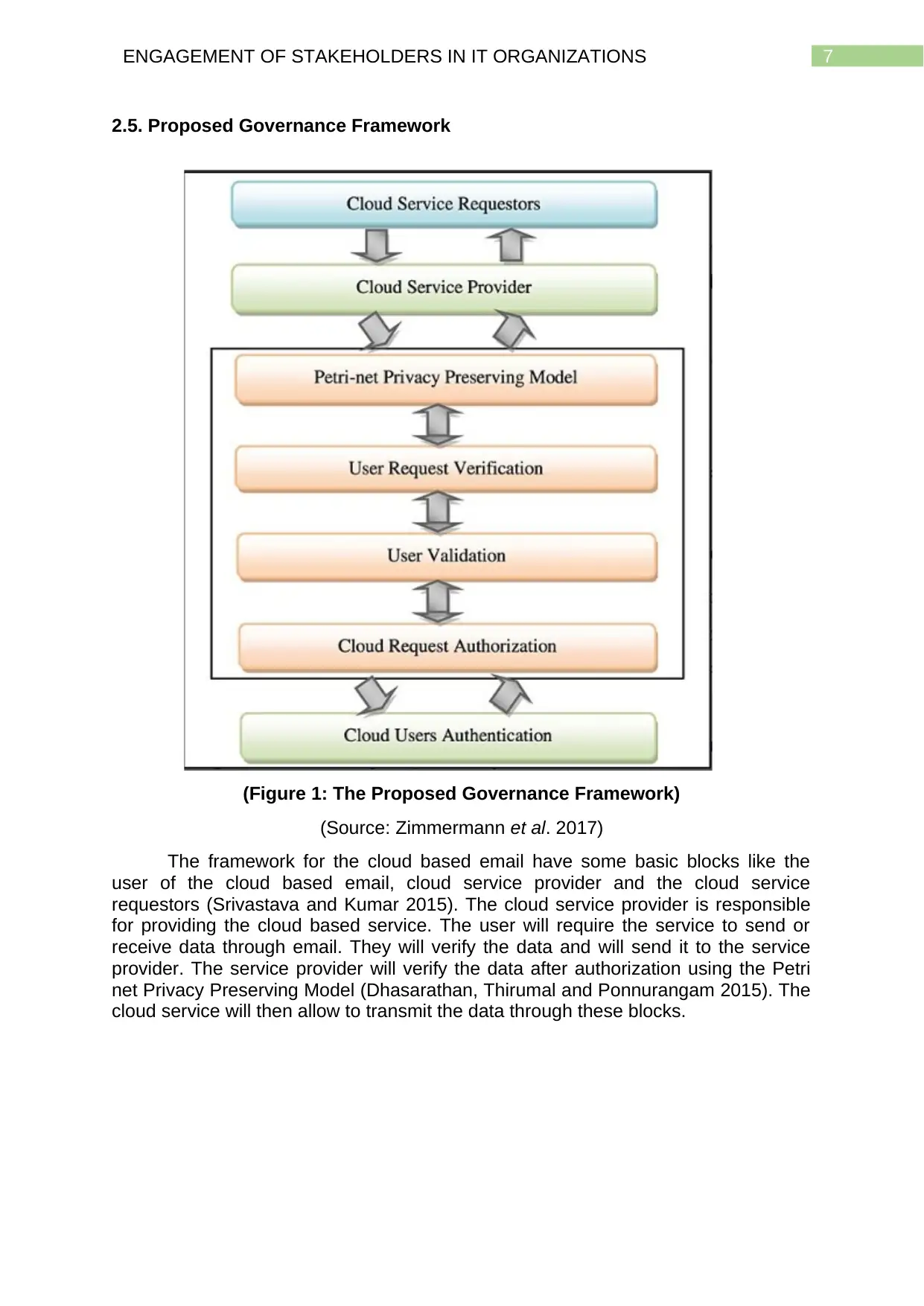
2.5. Proposed Governance Framework
(Figure 1: The Proposed Governance Framework)
(Source: Zimmermann et al. 2017)
The framework for the cloud based email have some basic blocks like the
user of the cloud based email, cloud service provider and the cloud service
requestors (Srivastava and Kumar 2015). The cloud service provider is responsible
for providing the cloud based service. The user will require the service to send or
receive data through email. They will verify the data and will send it to the service
provider. The service provider will verify the data after authorization using the Petri
net Privacy Preserving Model (Dhasarathan, Thirumal and Ponnurangam 2015). The
cloud service will then allow to transmit the data through these blocks.
2.5. Proposed Governance Framework
(Figure 1: The Proposed Governance Framework)
(Source: Zimmermann et al. 2017)
The framework for the cloud based email have some basic blocks like the
user of the cloud based email, cloud service provider and the cloud service
requestors (Srivastava and Kumar 2015). The cloud service provider is responsible
for providing the cloud based service. The user will require the service to send or
receive data through email. They will verify the data and will send it to the service
provider. The service provider will verify the data after authorization using the Petri
net Privacy Preserving Model (Dhasarathan, Thirumal and Ponnurangam 2015). The
cloud service will then allow to transmit the data through these blocks.

8ENGAGEMENT OF STAKEHOLDERS IN IT ORGANIZATIONS
3. Conclusion
It is concluded from the above report that the Premise Exchange system for
email will be changed to cloud based email service and the stakeholders of the
University of South Australia have to engage in the system for its proper
implementation. The University of South Australia wants to change their existing
Premise Exchange system for email with the cloud based email system for their daily
business operations. The authorities of the university wants to implement the new
system but there will be many complication for implementing this new system. The
existing system is very reliable and it is used in the daily operation of the university.
The Premise Exchange system is responsible for maintaining effective
communication between the stakeholders of the university. Essential factors are
maintained by this old system. There are various risk which can be identified for
implementing this system of cloud based email. These identified risk can be said as
reduced control and visibility of the stakeholders, the data is not always secured in
the cloud based email system, and incomplete deletion of data. The framework for
the cloud based email are based on some basic blocks like the user of the cloud
based email, cloud service provider and the cloud service requestors.
3. Conclusion
It is concluded from the above report that the Premise Exchange system for
email will be changed to cloud based email service and the stakeholders of the
University of South Australia have to engage in the system for its proper
implementation. The University of South Australia wants to change their existing
Premise Exchange system for email with the cloud based email system for their daily
business operations. The authorities of the university wants to implement the new
system but there will be many complication for implementing this new system. The
existing system is very reliable and it is used in the daily operation of the university.
The Premise Exchange system is responsible for maintaining effective
communication between the stakeholders of the university. Essential factors are
maintained by this old system. There are various risk which can be identified for
implementing this system of cloud based email. These identified risk can be said as
reduced control and visibility of the stakeholders, the data is not always secured in
the cloud based email system, and incomplete deletion of data. The framework for
the cloud based email are based on some basic blocks like the user of the cloud
based email, cloud service provider and the cloud service requestors.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9ENGAGEMENT OF STAKEHOLDERS IN IT ORGANIZATIONS
4. References
Albakri, S.H., Shanmugam, B., Samy, G.N., Idris, N.B. and Ahmed, A., 2014.
Security risk assessment framework for cloud computing environments. Security and
Communication Networks, 7(11), pp.2114-2124.
Ali, A., Warren, D. and Mathiassen, L., 2017. Cloud-based business services
innovation: A risk management model. International Journal of Information
Management, 37(6), pp.639-649.
Anders, S.B., 2017. Employer Internship and Recruitment Resources. The CPA
Journal, 87(12), pp.72-73.
Chou, D.C., 2015. Cloud computing risk and audit issues. Computer Standards &
Interfaces, 42, pp.137-142.
Dhasarathan, C., Thirumal, V. and Ponnurangam, D., 2015. Data privacy breach
prevention framework for the cloud service. Security and Communication
Networks, 8(6), pp.982-1005.
Glenn, T. and Monteith, S., 2014. Privacy in the digital world: medical and health
data outside of HIPAA protections. Current psychiatry reports, 16(11), p.494.
Haimes, Y.Y., Horowitz, B.M., Guo, Z., Andrijcic, E. and Bogdanor, J., 2015.
Assessing systemic risk to cloud‐computing technology as complex interconnected
systems of systems. Systems engineering, 18(3), pp.284-299.
Hingorani, K. and Askari-Danesh, N., 2014. Design and development of an academic
advising system for improving retention and graduation. Issues in Information
Systems, 15(2), pp.344-349.
Rajaraman, V., 2014. Cloud computing. Resonance, 19(3), pp.242-258.
Sharma, S., Chang, V., Tim, U., Wong, J. and Gadia, S., 2016. Cloud-based
emerging services systems. International Journal of Information Management, pp.1-
12.
Srivastava, H. and Kumar, S.A., 2015. Control framework for secure cloud
computing. Journal of Information Security, 6(1), p.12.
Zimmermann, V., Henhapl, B., Gerber, N. and Enzmann, M., 2017. Promoting
Secure Email Communication and Authentication. Mensch und Computer 2017-
Workshopband.
4. References
Albakri, S.H., Shanmugam, B., Samy, G.N., Idris, N.B. and Ahmed, A., 2014.
Security risk assessment framework for cloud computing environments. Security and
Communication Networks, 7(11), pp.2114-2124.
Ali, A., Warren, D. and Mathiassen, L., 2017. Cloud-based business services
innovation: A risk management model. International Journal of Information
Management, 37(6), pp.639-649.
Anders, S.B., 2017. Employer Internship and Recruitment Resources. The CPA
Journal, 87(12), pp.72-73.
Chou, D.C., 2015. Cloud computing risk and audit issues. Computer Standards &
Interfaces, 42, pp.137-142.
Dhasarathan, C., Thirumal, V. and Ponnurangam, D., 2015. Data privacy breach
prevention framework for the cloud service. Security and Communication
Networks, 8(6), pp.982-1005.
Glenn, T. and Monteith, S., 2014. Privacy in the digital world: medical and health
data outside of HIPAA protections. Current psychiatry reports, 16(11), p.494.
Haimes, Y.Y., Horowitz, B.M., Guo, Z., Andrijcic, E. and Bogdanor, J., 2015.
Assessing systemic risk to cloud‐computing technology as complex interconnected
systems of systems. Systems engineering, 18(3), pp.284-299.
Hingorani, K. and Askari-Danesh, N., 2014. Design and development of an academic
advising system for improving retention and graduation. Issues in Information
Systems, 15(2), pp.344-349.
Rajaraman, V., 2014. Cloud computing. Resonance, 19(3), pp.242-258.
Sharma, S., Chang, V., Tim, U., Wong, J. and Gadia, S., 2016. Cloud-based
emerging services systems. International Journal of Information Management, pp.1-
12.
Srivastava, H. and Kumar, S.A., 2015. Control framework for secure cloud
computing. Journal of Information Security, 6(1), p.12.
Zimmermann, V., Henhapl, B., Gerber, N. and Enzmann, M., 2017. Promoting
Secure Email Communication and Authentication. Mensch und Computer 2017-
Workshopband.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10ENGAGEMENT OF STAKEHOLDERS IN IT ORGANIZATIONS
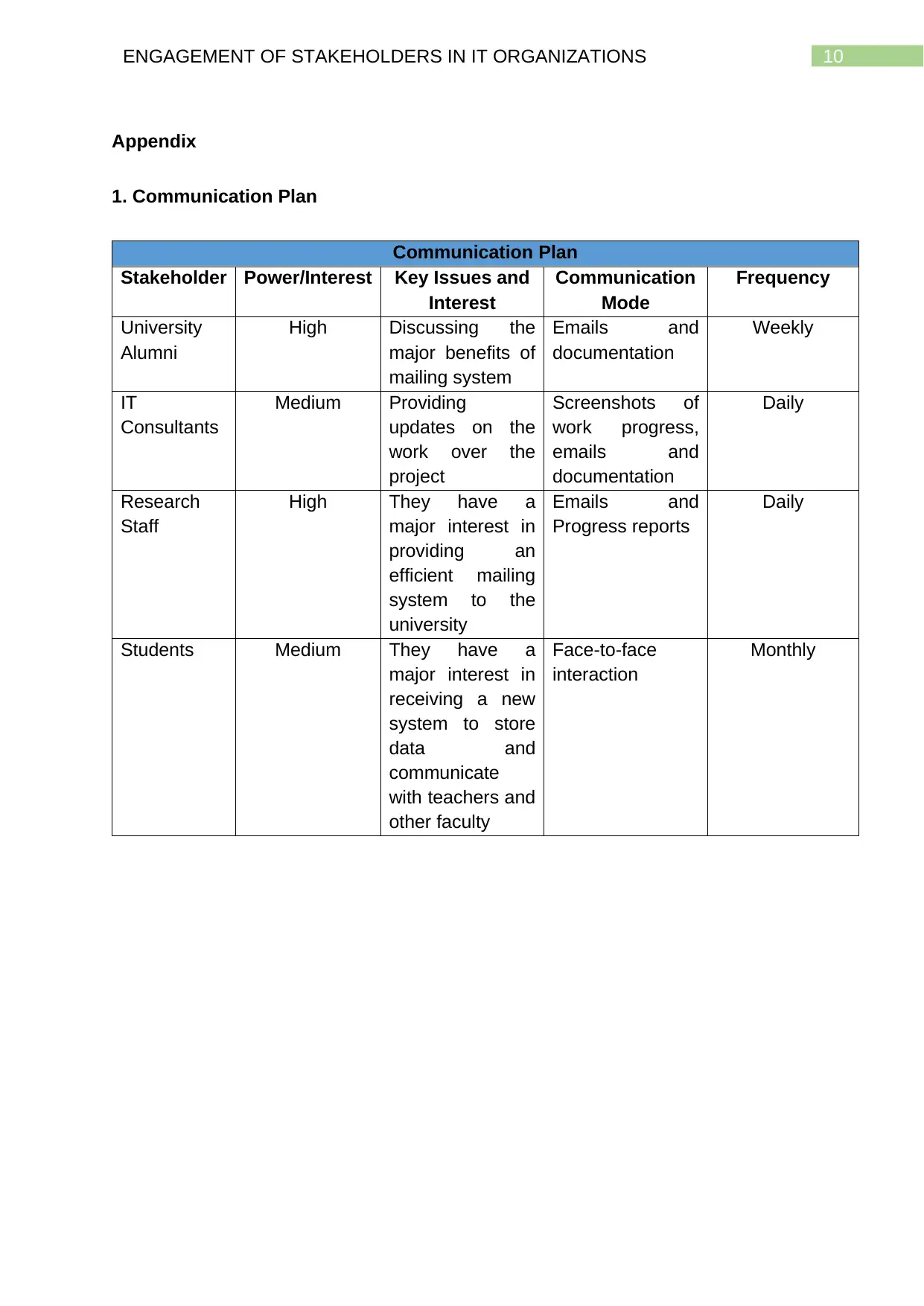
Appendix
1. Communication Plan
Communication Plan
Stakeholder Power/Interest Key Issues and
Interest
Communication
Mode
Frequency
University
Alumni
High Discussing the
major benefits of
mailing system
Emails and
documentation
Weekly
IT
Consultants
Medium Providing
updates on the
work over the
project
Screenshots of
work progress,
emails and
documentation
Daily
Research
Staff
High They have a
major interest in
providing an
efficient mailing
system to the
university
Emails and
Progress reports
Daily
Students Medium They have a
major interest in
receiving a new
system to store
data and
communicate
with teachers and
other faculty
Face-to-face
interaction
Monthly
Appendix
1. Communication Plan
Communication Plan
Stakeholder Power/Interest Key Issues and
Interest
Communication
Mode
Frequency
University
Alumni
High Discussing the
major benefits of
mailing system
Emails and
documentation
Weekly
IT
Consultants
Medium Providing
updates on the
work over the
project
Screenshots of
work progress,
emails and
documentation
Daily
Research
Staff
High They have a
major interest in
providing an
efficient mailing
system to the
university
Emails and
Progress reports
Daily
Students Medium They have a
major interest in
receiving a new
system to store
data and
communicate
with teachers and
other faculty
Face-to-face
interaction
Monthly
11ENGAGEMENT OF STAKEHOLDERS IN IT ORGANIZATIONS
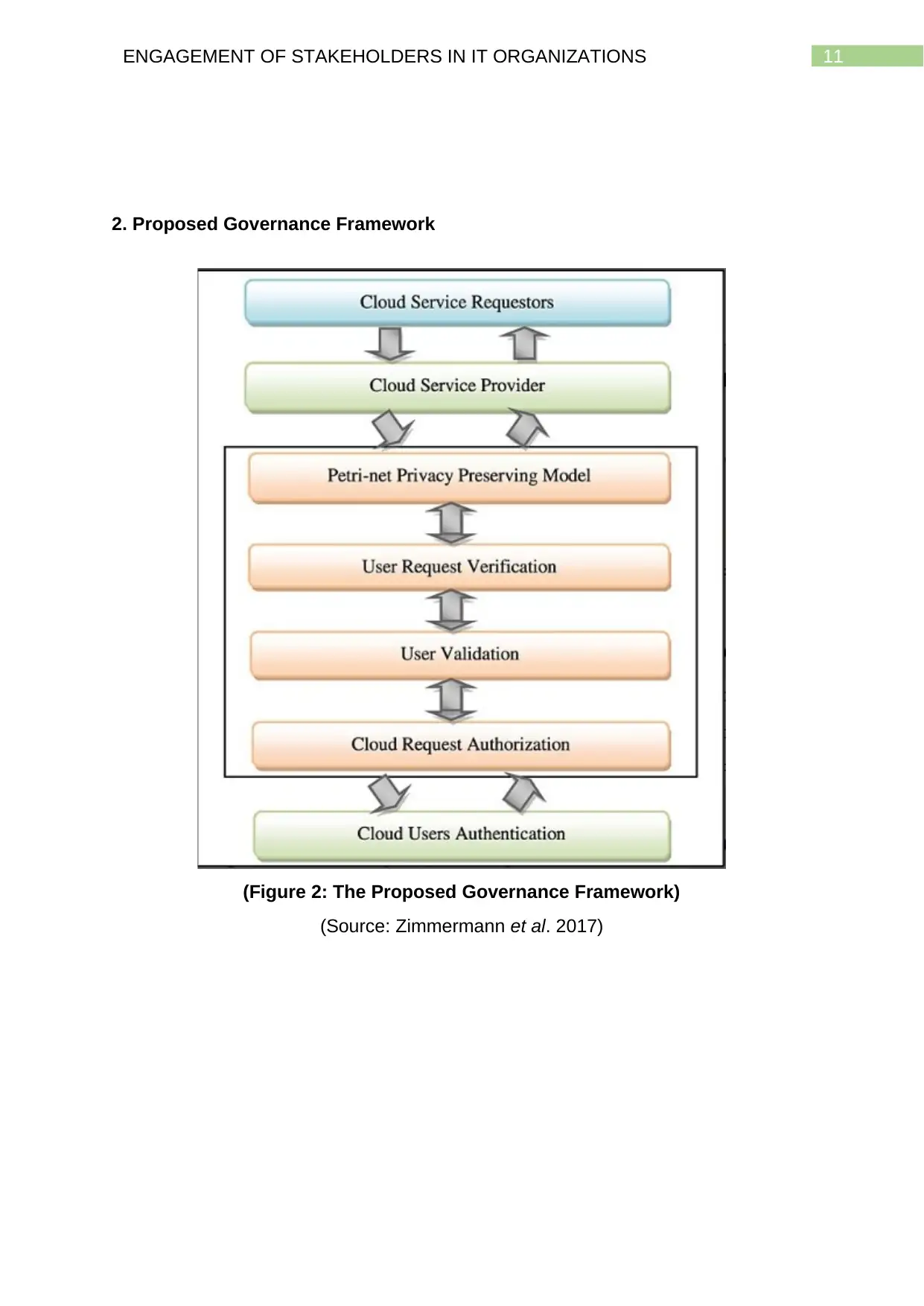
2. Proposed Governance Framework
(Figure 2: The Proposed Governance Framework)
(Source: Zimmermann et al. 2017)
2. Proposed Governance Framework
(Figure 2: The Proposed Governance Framework)
(Source: Zimmermann et al. 2017)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




