ITC505 Project Management: Risk Planning for Entry/Exit System Project
VerifiedAdded on 2022/10/15
|14
|3935
|14
Project
AI Summary
This project, for ITC505 Project Management, focuses on risk planning for a university dining cafe entry and exit system. It begins with an introduction to risk planning, defining risks and their impact. The project analyzes a previous proposal and outlines the student's solution, including new technology implementation, kitchen recording systems, and polling features. The approach involves strategic planning and risk evaluation, covering both ordinary and extraordinary circumstances. The methodology includes preliminary risk assessment, qualitative and quantitative risk analysis, and risk response planning. Techniques such as workshops, brainstorming, SWOT analysis, probability/impact evaluation, and expert judgment are employed. The project details roles and responsibilities, risk identification tools (interviews, brainstorming, checklists, cause-and-effect diagrams, and affinity diagrams), and identifies specific risks related to cost management, communication, training, design, requirements, and procurement. The assignment demonstrates a comprehensive approach to managing potential risks in a project setting, specifically within a university environment, highlighting the importance of proactive planning and mitigation strategies.

1
COURSE CODE: ITC505
TASK: Project Management
COURSE CODE: ITC505
TASK: Project Management
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
4.1 RISK PLANNING
(a) introduction
Risk planning is the process of identifying potential threats or risks to a particular system or
project, assessing the impact that could result from such a risk happening and identifying
mitigation strategies to curb those threats. A risk can be defined as potential occurrence of
damage or loss caused by either internal or external events that affect operations.
Technology is an enabler in most operations today. In businesses, transactions are carried out
both onsite and remotely utilizing the technology in place. Networks have improved how daily
business transactions are carried out. In school environments, technology has improved how
operations are carried out. For instance, automation in finance has seen great welcoming by most
education institutions. In Australian Universities, students finance operations are done
electronically mitigating potential mismanagement of funds by students and university staff.
Providing accommodation among universities has also seen a great impact in the use of
technology. Students can book residential halls online and may apply for other services at the
comfort of their homes.
Risk planning is an important process with regards to University operations. There is a
relationship between risk planning and profit realization. In this project planning, an assessment
into potential risks associated with system for entry and exit into dining café and kitchen
recording system is presented.
Previous company proposal
A company had previously been contracted to deliver the systems aforementioned. The proposal
was as follows;
Swipe card readers (Model A) and system has been ordered.
Cost: $12,000
Time to remove/re-order and re-install new system: 4 weeks
Re-order of special access cards (Model A)
Cost: $5,000
Time to re-order: 8 weeks
Different access cards are needed from accommodation access cards due to security and charging
model. A student could pay for accommodation and would self-cook. Some students might pay
for an evening meal but prefer to self-cook breakfast. The current system allows for these
flexibilities. The cards also operate via fingerprint recognition. This is to ensure that cards are
not passed on or exchanged among students. An alternative method is to hire staff to handle
checks at the door. This will be cumbersome, expensive and difficult to handle after-hours (at
night).
Technology has improved during the last three months. The new technology (Model B) encoded
with these cards will trigger a red light on the counter, if a student with food allergies try to pick
4.1 RISK PLANNING
(a) introduction
Risk planning is the process of identifying potential threats or risks to a particular system or
project, assessing the impact that could result from such a risk happening and identifying
mitigation strategies to curb those threats. A risk can be defined as potential occurrence of
damage or loss caused by either internal or external events that affect operations.
Technology is an enabler in most operations today. In businesses, transactions are carried out
both onsite and remotely utilizing the technology in place. Networks have improved how daily
business transactions are carried out. In school environments, technology has improved how
operations are carried out. For instance, automation in finance has seen great welcoming by most
education institutions. In Australian Universities, students finance operations are done
electronically mitigating potential mismanagement of funds by students and university staff.
Providing accommodation among universities has also seen a great impact in the use of
technology. Students can book residential halls online and may apply for other services at the
comfort of their homes.
Risk planning is an important process with regards to University operations. There is a
relationship between risk planning and profit realization. In this project planning, an assessment
into potential risks associated with system for entry and exit into dining café and kitchen
recording system is presented.
Previous company proposal
A company had previously been contracted to deliver the systems aforementioned. The proposal
was as follows;
Swipe card readers (Model A) and system has been ordered.
Cost: $12,000
Time to remove/re-order and re-install new system: 4 weeks
Re-order of special access cards (Model A)
Cost: $5,000
Time to re-order: 8 weeks
Different access cards are needed from accommodation access cards due to security and charging
model. A student could pay for accommodation and would self-cook. Some students might pay
for an evening meal but prefer to self-cook breakfast. The current system allows for these
flexibilities. The cards also operate via fingerprint recognition. This is to ensure that cards are
not passed on or exchanged among students. An alternative method is to hire staff to handle
checks at the door. This will be cumbersome, expensive and difficult to handle after-hours (at
night).
Technology has improved during the last three months. The new technology (Model B) encoded
with these cards will trigger a red light on the counter, if a student with food allergies try to pick

2
up food that contains that allergen. Setup, training and orientation to the new system will take
another $30,000.
Our own solution to the problem
Oder new technology model B cards
Set up train and orient students to its use
Acquire ,install and orient the kitchen recording system and control
The kitchen recording and control system should possess a polling feature
(b) The approach
We developed a strategic aspect of planning the project and the risks anticipated, either tangible
or intangible were evaluated. Risks that are ordinary to the normal running of the project will be
evaluated and also those that are anticipated to be from extraordinary circumstances.
(c) Methodology
The methodology used in risk management for this project will aim to have flexibility even in
identifying risks that have been omitted during the initial stages. We developed a risk based
project assessment approach, where iterative processes were done. These processes however
have some degree of uncertainties. A methodology was developed to help curb the possibility of
these uncertainties, to help review ongoing research and various methodologies. We therefore
arrived at a systematic approach to assess and manage potential threats that could arise during
project implementation process. Highlighted below were the most important aspects of the
methodology;
Preliminary risk assessment and scope of the risks
Elicitation of the risks in detail
Residual risks identification and communication
To enable us carry out preliminary risk assessment, it was important to take into consideration
two main mechanisms. These included;
Preliminary project risk session
We carried out a number of workshops to enable us brainstorm into the potential risks that would
arise in the implementation of the proposed systems. As part of the activities of the workshops,
an identification and categorization of the activities of the project process was done. Besides, the
different phases of implementation and commissioning were highlighted in which associated
impact could result.
After identification of each project activity, potential risks associated with that particular activity
was identified and a range assigned. The range identified the degree to which that risk would
impact the project. Risks were categorized as high level, moderate and low level. Knowledge
gaps were also identified and uncertainties were highlighted to influence the project design
during the initial phase of design.
up food that contains that allergen. Setup, training and orientation to the new system will take
another $30,000.
Our own solution to the problem
Oder new technology model B cards
Set up train and orient students to its use
Acquire ,install and orient the kitchen recording system and control
The kitchen recording and control system should possess a polling feature
(b) The approach
We developed a strategic aspect of planning the project and the risks anticipated, either tangible
or intangible were evaluated. Risks that are ordinary to the normal running of the project will be
evaluated and also those that are anticipated to be from extraordinary circumstances.
(c) Methodology
The methodology used in risk management for this project will aim to have flexibility even in
identifying risks that have been omitted during the initial stages. We developed a risk based
project assessment approach, where iterative processes were done. These processes however
have some degree of uncertainties. A methodology was developed to help curb the possibility of
these uncertainties, to help review ongoing research and various methodologies. We therefore
arrived at a systematic approach to assess and manage potential threats that could arise during
project implementation process. Highlighted below were the most important aspects of the
methodology;
Preliminary risk assessment and scope of the risks
Elicitation of the risks in detail
Residual risks identification and communication
To enable us carry out preliminary risk assessment, it was important to take into consideration
two main mechanisms. These included;
Preliminary project risk session
We carried out a number of workshops to enable us brainstorm into the potential risks that would
arise in the implementation of the proposed systems. As part of the activities of the workshops,
an identification and categorization of the activities of the project process was done. Besides, the
different phases of implementation and commissioning were highlighted in which associated
impact could result.
After identification of each project activity, potential risks associated with that particular activity
was identified and a range assigned. The range identified the degree to which that risk would
impact the project. Risks were categorized as high level, moderate and low level. Knowledge
gaps were also identified and uncertainties were highlighted to influence the project design
during the initial phase of design.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
Key activities were carried out during this phase. They include, risk identification,
brainstorming, interviews, checklist analysis and diagramming. SWOT analysis was also done
and ultimately the risks were analyzed.
Qualitative risk analysis
A number of techniques for qualitative risk analysis were employed. These are;
i. Risk probability/impact evaluation
For any identified risk, an investigation into possibility that that particular risk will occur was
done. Potential impact of a risk with regards to the project implementation was also done. The
risks associated with costs, scheduling and performance quality were categorized in this
technique. The negative impacts of the threats and the opportunities were assessed and defined in
levels. A documentation of the results was then drafted.
ii. Probability and impact matrix method
The likelihood of the occurrence of a risk was written quantitatively. The impact range was also
quantified in order to evaluate the importance associated with mitigation of that particular risk.
iii. Categorizing risks
It was important to categorize the risks to enable in determining the degree of attention that has
to be given to that particular threat. Risks were categorized as:
a. High possibility, high impact
With these risks, a lot of attention has to be provided. Since they have high probability of
occurrence and high impact associated, their occurrence has detrimental effects on the project
design and implementation.
b. High possibility, low impact
These risks have to be mitigated and contained at all costs
c. Low possibility, high impact
d. Low possibility, low impact
Less attention was given to these particular risks.
Risk urgency assessment
Risk sensitivity has to be assessed. It is a matter that project managers take this into
consideration for proper mitigation of the threats that could negatively impact the project
planning and implementation. The response time for those highlighted risks was derived,
enabling timely responses and timely contention of the risks.
Expert judgment
Key activities were carried out during this phase. They include, risk identification,
brainstorming, interviews, checklist analysis and diagramming. SWOT analysis was also done
and ultimately the risks were analyzed.
Qualitative risk analysis
A number of techniques for qualitative risk analysis were employed. These are;
i. Risk probability/impact evaluation
For any identified risk, an investigation into possibility that that particular risk will occur was
done. Potential impact of a risk with regards to the project implementation was also done. The
risks associated with costs, scheduling and performance quality were categorized in this
technique. The negative impacts of the threats and the opportunities were assessed and defined in
levels. A documentation of the results was then drafted.
ii. Probability and impact matrix method
The likelihood of the occurrence of a risk was written quantitatively. The impact range was also
quantified in order to evaluate the importance associated with mitigation of that particular risk.
iii. Categorizing risks
It was important to categorize the risks to enable in determining the degree of attention that has
to be given to that particular threat. Risks were categorized as:
a. High possibility, high impact
With these risks, a lot of attention has to be provided. Since they have high probability of
occurrence and high impact associated, their occurrence has detrimental effects on the project
design and implementation.
b. High possibility, low impact
These risks have to be mitigated and contained at all costs
c. Low possibility, high impact
d. Low possibility, low impact
Less attention was given to these particular risks.
Risk urgency assessment
Risk sensitivity has to be assessed. It is a matter that project managers take this into
consideration for proper mitigation of the threats that could negatively impact the project
planning and implementation. The response time for those highlighted risks was derived,
enabling timely responses and timely contention of the risks.
Expert judgment
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
There was need to involve experienced personnel in the analysis of the risks involved. Expertise
enables qualitative means of risk assessment and mitigation strategies that could act well for the
good of the project managers.
Quantitative risk analysis
A number of techniques were used to carry out quantitative risk analysis. Quantitative risk
analysis, in an important technique in project management (Jayadevappa & Soh, 2019)
Modeling & simulation
Modelling involves designing of a framework that resembles the actual execution environment.
It offers translation of the uncertainties and their impact in the project analysis (Nabaei,
Chandrawati, & Heidara, 2018)
Risk Response Planning
This refers to the process of developing options and actions to make good use of opportunities
that potential risks offer. The importance of risk response planning is to ensure that clear
procedures have been followed in identifying risks and rating the extent of their impacts.
Through it, proper actions to mitigate or eliminate risks are realized (Fang, Marle, Xie, & Zio,
2013)
Risk audits
Risks associated with audit process while examining the system occur when an auditor does not
detect errors in the auditing process. Risks can be categorized as control, detection and inherent
risks. Failure to clearly format audit and its objectives pose a great risk in project management.
Roles and responsibilities
Title role
Project management Responsible for coordinating activities
within between all stakeholders and
directing the project team towards the set
vision and mission
Stakeholders Responsible for providing feedback on their
areas of interest with regard to the system
under development
Financiers Responsible financing the development of
the system under consideration
Technical team Responsible for the provision of technical
skills for the development of the system
under consideration
Risk identification
There was need to involve experienced personnel in the analysis of the risks involved. Expertise
enables qualitative means of risk assessment and mitigation strategies that could act well for the
good of the project managers.
Quantitative risk analysis
A number of techniques were used to carry out quantitative risk analysis. Quantitative risk
analysis, in an important technique in project management (Jayadevappa & Soh, 2019)
Modeling & simulation
Modelling involves designing of a framework that resembles the actual execution environment.
It offers translation of the uncertainties and their impact in the project analysis (Nabaei,
Chandrawati, & Heidara, 2018)
Risk Response Planning
This refers to the process of developing options and actions to make good use of opportunities
that potential risks offer. The importance of risk response planning is to ensure that clear
procedures have been followed in identifying risks and rating the extent of their impacts.
Through it, proper actions to mitigate or eliminate risks are realized (Fang, Marle, Xie, & Zio,
2013)
Risk audits
Risks associated with audit process while examining the system occur when an auditor does not
detect errors in the auditing process. Risks can be categorized as control, detection and inherent
risks. Failure to clearly format audit and its objectives pose a great risk in project management.
Roles and responsibilities
Title role
Project management Responsible for coordinating activities
within between all stakeholders and
directing the project team towards the set
vision and mission
Stakeholders Responsible for providing feedback on their
areas of interest with regard to the system
under development
Financiers Responsible financing the development of
the system under consideration
Technical team Responsible for the provision of technical
skills for the development of the system
under consideration
Risk identification

5
A combination of these tools will be used for risk identification
Interviews
Key stakeholders of the university were interviewed. Questions were defined and a
documentation of the results was done.
Brainstorming
Members of the team were asked to brainstorm on risks that may arise in the course of project
design and the possibility of causing damage
Project objectives
The most important parts of the project were noted and a lot of attention given as to what degree
of risk is associated.
Project tasks
The activities and tasks associated with the project were highlighted. The risks associated with
each task were enumerated and assessed. They include risks associated with training and project
implementation.
Checklists
See if your company has a list of the most common risks. If not, you may want to create such a
list. After each project, conduct a post review where you capture the most significant risks. This
list may be used for subsequent projects. Warning – checklists are great, but no checklist
contains all the risks.
Cause and Effect Diagrams
Cause and Effect diagrams are powerful. Project managers can use this simple method to help
identify causes--facts that give rise to risks. If we address the causes, we can reduce or eliminate
the risks.
Affinity Diagrams
This technique is a fun, creative, and beneficial exercise. Participants are asked to brainstorm
risks. I ask participants to write each risk on a sticky note. Then participants sort the risks into
groups or categories. Each group is given a title.
Identified risks
Executive Support
i. The philanthropist turns down his support for the project
ii. The philanthropist disengages himself from the project
iii. The philanthropist disregards project communications and meetings.
iv. Disagreements between philanthropist and other stakeholders like campus
disrupts project
A combination of these tools will be used for risk identification
Interviews
Key stakeholders of the university were interviewed. Questions were defined and a
documentation of the results was done.
Brainstorming
Members of the team were asked to brainstorm on risks that may arise in the course of project
design and the possibility of causing damage
Project objectives
The most important parts of the project were noted and a lot of attention given as to what degree
of risk is associated.
Project tasks
The activities and tasks associated with the project were highlighted. The risks associated with
each task were enumerated and assessed. They include risks associated with training and project
implementation.
Checklists
See if your company has a list of the most common risks. If not, you may want to create such a
list. After each project, conduct a post review where you capture the most significant risks. This
list may be used for subsequent projects. Warning – checklists are great, but no checklist
contains all the risks.
Cause and Effect Diagrams
Cause and Effect diagrams are powerful. Project managers can use this simple method to help
identify causes--facts that give rise to risks. If we address the causes, we can reduce or eliminate
the risks.
Affinity Diagrams
This technique is a fun, creative, and beneficial exercise. Participants are asked to brainstorm
risks. I ask participants to write each risk on a sticky note. Then participants sort the risks into
groups or categories. Each group is given a title.
Identified risks
Executive Support
i. The philanthropist turns down his support for the project
ii. The philanthropist disengages himself from the project
iii. The philanthropist disregards project communications and meetings.
iv. Disagreements between philanthropist and other stakeholders like campus
disrupts project
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
Cost Management
1. Inaccurate cost estimates – cost estimate associated with the proposed system was observed to
be inaccurate.
2. Variability in exchange rate
When costs are incurred in foreign currencies exchange rates can have a dramatic impact.
3. Change management overload
A large number of change requests dramatically raises the complexity of the project and distracts
key resources.
4. Stakeholder conflict over proposed changes
If stakeholders have conflicts of interests, then it presents a potential risk to the design and
implementation of this project.
Change requests that make no sense in the context of the requirements.
Communication
1. Our team fails to understand requirements
When requirements are misinterpreted by the project team a gap develops between expectations,
requirements and work packages.
2. Communication overhead
When key project resources spend a high percentage of their time engaging stakeholders on
project issues and change requests their work may fall behind.
3. under communication
Communication is a challenge that's not to be underestimated. You may need to communicate
the same idea many times in different ways before people remember it.
Training
Training was identified as a risk area. Users have to be trained to adapt the new system and to
make good use of it to deliver the expected functions. Inadequate training may result in
undesirable system functions.
Design
Cost Management
1. Inaccurate cost estimates – cost estimate associated with the proposed system was observed to
be inaccurate.
2. Variability in exchange rate
When costs are incurred in foreign currencies exchange rates can have a dramatic impact.
3. Change management overload
A large number of change requests dramatically raises the complexity of the project and distracts
key resources.
4. Stakeholder conflict over proposed changes
If stakeholders have conflicts of interests, then it presents a potential risk to the design and
implementation of this project.
Change requests that make no sense in the context of the requirements.
Communication
1. Our team fails to understand requirements
When requirements are misinterpreted by the project team a gap develops between expectations,
requirements and work packages.
2. Communication overhead
When key project resources spend a high percentage of their time engaging stakeholders on
project issues and change requests their work may fall behind.
3. under communication
Communication is a challenge that's not to be underestimated. You may need to communicate
the same idea many times in different ways before people remember it.
Training
Training was identified as a risk area. Users have to be trained to adapt the new system and to
make good use of it to deliver the expected functions. Inadequate training may result in
undesirable system functions.
Design
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
The design of project is important.it poses a risk when it is infeasible in terms of cost and support
requirements. If the design is not flexible, changes in the future will not be realized easily. This
makes it a risk as far as project implementation is concerned.
Requirements
It is important to design a system to meet the requirements of the user. Both functional and non-
functional requirements have to be met. A risk associated with requirements is failure of the
elicited requirements to align with the business strategy, conflicting with the institution’s
strategy framework and a failure to meet the standards.
Procurement
Procurement plays an important role in project management. It sets out important policies that
have to be adhered to for successful implementation of the project. In public procurement,
tailored intermediation is key towards ensuring that projects are done accordingly (Edler &
Yeow, 2015). In our project report, we observed that procurement poses a risk in that it defines
how contracts are awarded and the terms over which the same contracts hold. The risks
associated with procurement include:
i. failure to negotiate contract price
ii. Inappropriate terms of contact.
Project Management
Project management in any organization serves a good tool of formulating effective strategies.
Project managers are responsibility in ensuring that every process in project management is
adhered to so as to mitigate any possibility of project failure (Schwalbe, 2015). Project
management therefore poses a risk as far as the implementation of this project is concerned.
1. Project management methodology
Different institutions have different project methodologies. Failing to work as per set
methodology of one organization may lead to project failure.
2. University lack of management control
Failure to clearly plan the control strategy of any organization means a failure to most business
operations. When such a case happens in a university environment, most activities including
procurement of information systems, finance management systems and so forth, pose a risk. We
documented this risk in our report since it causes a major impact in the project implementation
process.
User Acceptance
For successful implementation of any particular project, it is important that user experience is
taken into consideration (Kaasinen, Roto, Hakulinen, Heimonen, & Jokinen, 2015). Users are the
most important players that determine system usability. The risks associated with user
The design of project is important.it poses a risk when it is infeasible in terms of cost and support
requirements. If the design is not flexible, changes in the future will not be realized easily. This
makes it a risk as far as project implementation is concerned.
Requirements
It is important to design a system to meet the requirements of the user. Both functional and non-
functional requirements have to be met. A risk associated with requirements is failure of the
elicited requirements to align with the business strategy, conflicting with the institution’s
strategy framework and a failure to meet the standards.
Procurement
Procurement plays an important role in project management. It sets out important policies that
have to be adhered to for successful implementation of the project. In public procurement,
tailored intermediation is key towards ensuring that projects are done accordingly (Edler &
Yeow, 2015). In our project report, we observed that procurement poses a risk in that it defines
how contracts are awarded and the terms over which the same contracts hold. The risks
associated with procurement include:
i. failure to negotiate contract price
ii. Inappropriate terms of contact.
Project Management
Project management in any organization serves a good tool of formulating effective strategies.
Project managers are responsibility in ensuring that every process in project management is
adhered to so as to mitigate any possibility of project failure (Schwalbe, 2015). Project
management therefore poses a risk as far as the implementation of this project is concerned.
1. Project management methodology
Different institutions have different project methodologies. Failing to work as per set
methodology of one organization may lead to project failure.
2. University lack of management control
Failure to clearly plan the control strategy of any organization means a failure to most business
operations. When such a case happens in a university environment, most activities including
procurement of information systems, finance management systems and so forth, pose a risk. We
documented this risk in our report since it causes a major impact in the project implementation
process.
User Acceptance
For successful implementation of any particular project, it is important that user experience is
taken into consideration (Kaasinen, Roto, Hakulinen, Heimonen, & Jokinen, 2015). Users are the
most important players that determine system usability. The risks associated with user
8
experience range from inclusivity to usability of the system (Waller, Bradley, Hosking, &
Clarkson, 2015). Among
a. users rejecting the prototype
Users may approve the prototype of a system if it fits what they really wanted from the system
Usability in system design is the ability of a system to meet functional requirements.
b. poor user interface
The inability of the system to give users an interface that is comfortable to them makes the
system very unusable. Therefore, there is need to emphasize good user experience design
principles.
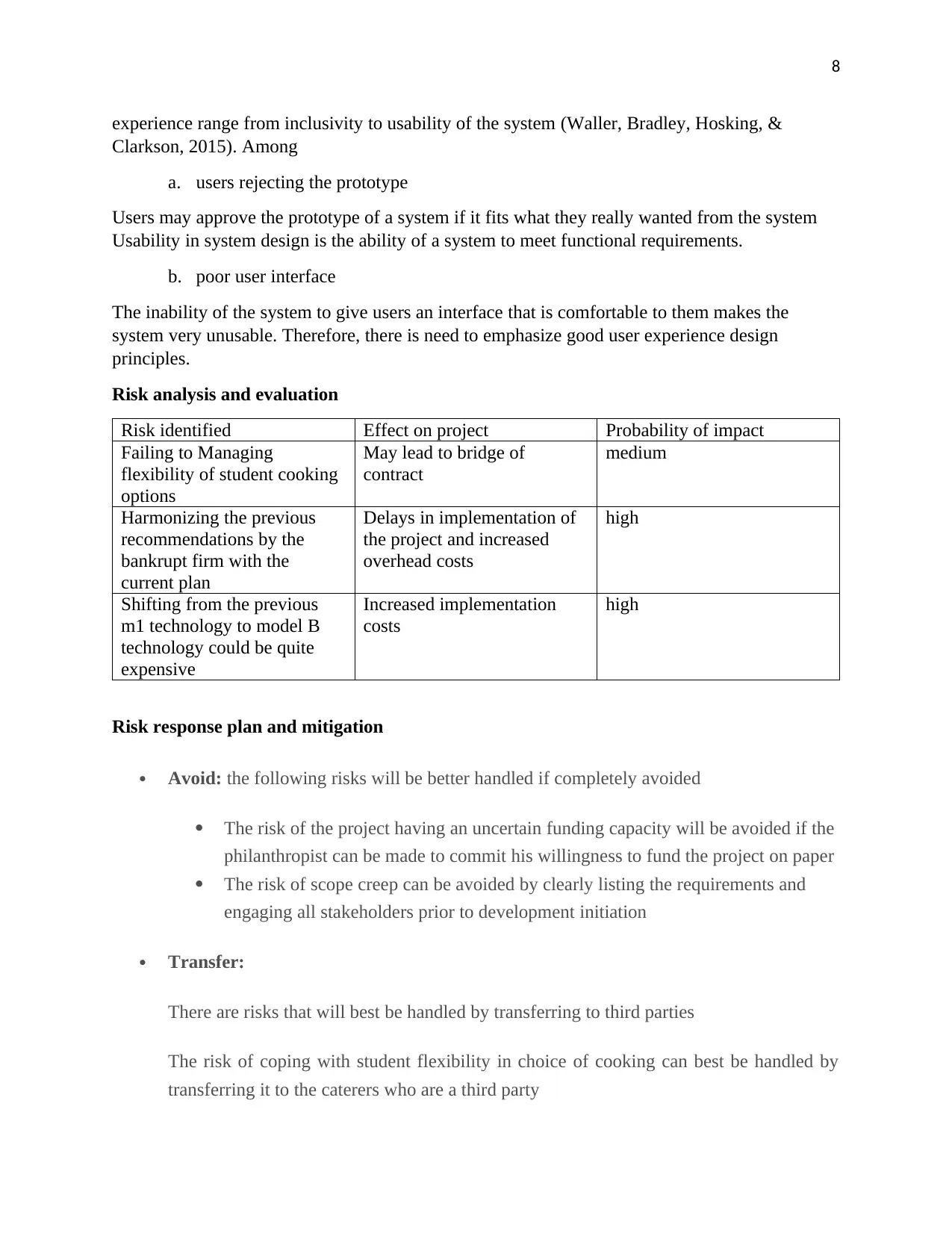
Risk analysis and evaluation
Risk identified Effect on project Probability of impact
Failing to Managing
flexibility of student cooking
options
May lead to bridge of
contract
medium
Harmonizing the previous
recommendations by the
bankrupt firm with the
current plan
Delays in implementation of
the project and increased
overhead costs
high
Shifting from the previous
m1 technology to model B
technology could be quite
expensive
Increased implementation
costs
high
Risk response plan and mitigation
Avoid: the following risks will be better handled if completely avoided
The risk of the project having an uncertain funding capacity will be avoided if the
philanthropist can be made to commit his willingness to fund the project on paper
The risk of scope creep can be avoided by clearly listing the requirements and
engaging all stakeholders prior to development initiation
Transfer:
There are risks that will best be handled by transferring to third parties
The risk of coping with student flexibility in choice of cooking can best be handled by
transferring it to the caterers who are a third party
experience range from inclusivity to usability of the system (Waller, Bradley, Hosking, &
Clarkson, 2015). Among
a. users rejecting the prototype
Users may approve the prototype of a system if it fits what they really wanted from the system
Usability in system design is the ability of a system to meet functional requirements.
b. poor user interface
The inability of the system to give users an interface that is comfortable to them makes the
system very unusable. Therefore, there is need to emphasize good user experience design
principles.
Risk analysis and evaluation
Risk identified Effect on project Probability of impact
Failing to Managing
flexibility of student cooking
options
May lead to bridge of
contract
medium
Harmonizing the previous
recommendations by the
bankrupt firm with the
current plan
Delays in implementation of
the project and increased
overhead costs
high
Shifting from the previous
m1 technology to model B
technology could be quite
expensive
Increased implementation
costs
high
Risk response plan and mitigation
Avoid: the following risks will be better handled if completely avoided
The risk of the project having an uncertain funding capacity will be avoided if the
philanthropist can be made to commit his willingness to fund the project on paper
The risk of scope creep can be avoided by clearly listing the requirements and
engaging all stakeholders prior to development initiation
Transfer:
There are risks that will best be handled by transferring to third parties
The risk of coping with student flexibility in choice of cooking can best be handled by
transferring it to the caterers who are a third party
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
Mitigate: the risk of students rejecting the new system can be avoided by educating the
students about the benefits of the system prior to its full implementation
Accept: other risks that are likely to occur but can’t be prevented will be accepted. This
includes risks such as unprecedented technology change
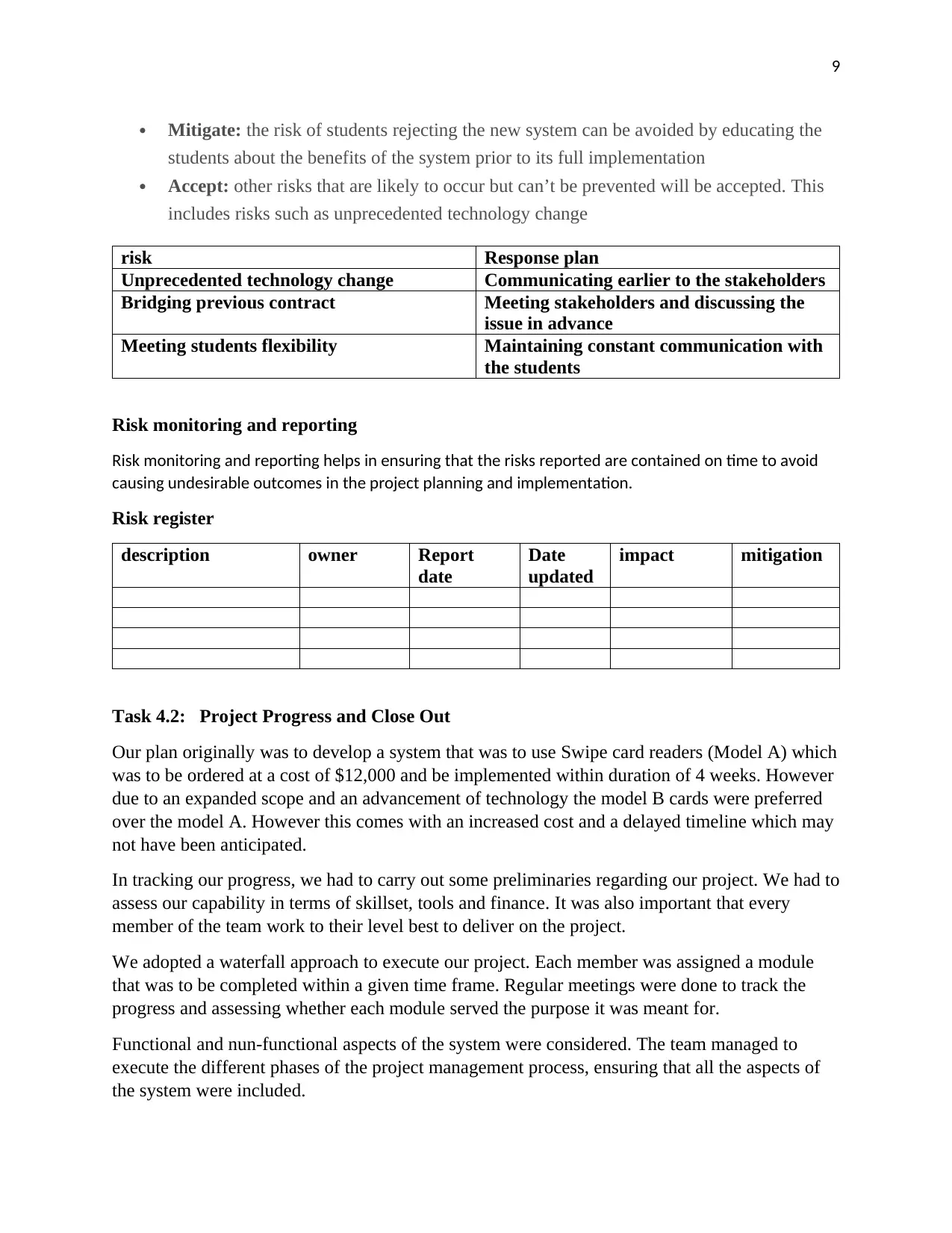
risk Response plan
Unprecedented technology change Communicating earlier to the stakeholders
Bridging previous contract Meeting stakeholders and discussing the
issue in advance
Meeting students flexibility Maintaining constant communication with
the students
Risk monitoring and reporting
Risk monitoring and reporting helps in ensuring that the risks reported are contained on time to avoid
causing undesirable outcomes in the project planning and implementation.
Risk register
description owner Report
date
Date
updated
impact mitigation
Task 4.2: Project Progress and Close Out
Our plan originally was to develop a system that was to use Swipe card readers (Model A) which
was to be ordered at a cost of $12,000 and be implemented within duration of 4 weeks. However
due to an expanded scope and an advancement of technology the model B cards were preferred
over the model A. However this comes with an increased cost and a delayed timeline which may
not have been anticipated.
In tracking our progress, we had to carry out some preliminaries regarding our project. We had to
assess our capability in terms of skillset, tools and finance. It was also important that every
member of the team work to their level best to deliver on the project.
We adopted a waterfall approach to execute our project. Each member was assigned a module
that was to be completed within a given time frame. Regular meetings were done to track the
progress and assessing whether each module served the purpose it was meant for.
Functional and nun-functional aspects of the system were considered. The team managed to
execute the different phases of the project management process, ensuring that all the aspects of
the system were included.
Mitigate: the risk of students rejecting the new system can be avoided by educating the
students about the benefits of the system prior to its full implementation
Accept: other risks that are likely to occur but can’t be prevented will be accepted. This
includes risks such as unprecedented technology change
risk Response plan
Unprecedented technology change Communicating earlier to the stakeholders
Bridging previous contract Meeting stakeholders and discussing the
issue in advance
Meeting students flexibility Maintaining constant communication with
the students
Risk monitoring and reporting
Risk monitoring and reporting helps in ensuring that the risks reported are contained on time to avoid
causing undesirable outcomes in the project planning and implementation.
Risk register
description owner Report
date
Date
updated
impact mitigation
Task 4.2: Project Progress and Close Out
Our plan originally was to develop a system that was to use Swipe card readers (Model A) which
was to be ordered at a cost of $12,000 and be implemented within duration of 4 weeks. However
due to an expanded scope and an advancement of technology the model B cards were preferred
over the model A. However this comes with an increased cost and a delayed timeline which may
not have been anticipated.
In tracking our progress, we had to carry out some preliminaries regarding our project. We had to
assess our capability in terms of skillset, tools and finance. It was also important that every
member of the team work to their level best to deliver on the project.
We adopted a waterfall approach to execute our project. Each member was assigned a module
that was to be completed within a given time frame. Regular meetings were done to track the
progress and assessing whether each module served the purpose it was meant for.
Functional and nun-functional aspects of the system were considered. The team managed to
execute the different phases of the project management process, ensuring that all the aspects of
the system were included.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
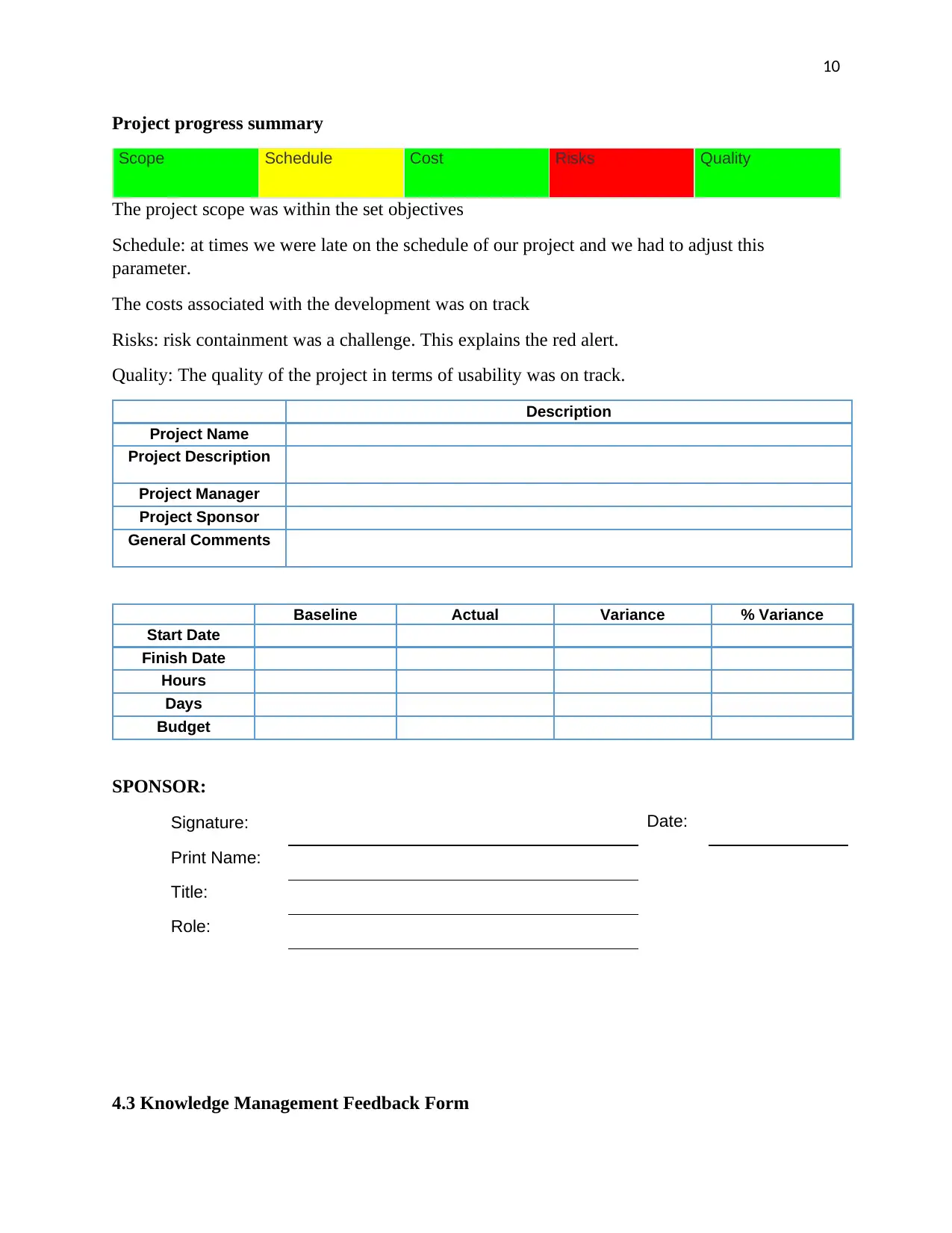
Project progress summary
Scope Schedule Cost Risks Quality
The project scope was within the set objectives
Schedule: at times we were late on the schedule of our project and we had to adjust this
parameter.
The costs associated with the development was on track
Risks: risk containment was a challenge. This explains the red alert.
Quality: The quality of the project in terms of usability was on track.
Description
Project Name
Project Description
Project Manager
Project Sponsor
General Comments
Baseline Actual Variance % Variance
Start Date
Finish Date
Hours
Days
Budget
SPONSOR:
Signature: Date:
Print Name:
Title:
Role:
4.3 Knowledge Management Feedback Form
Project progress summary
Scope Schedule Cost Risks Quality
The project scope was within the set objectives
Schedule: at times we were late on the schedule of our project and we had to adjust this
parameter.
The costs associated with the development was on track
Risks: risk containment was a challenge. This explains the red alert.
Quality: The quality of the project in terms of usability was on track.
Description
Project Name
Project Description
Project Manager
Project Sponsor
General Comments
Baseline Actual Variance % Variance
Start Date
Finish Date
Hours
Days
Budget
SPONSOR:
Signature: Date:
Print Name:
Title:
Role:
4.3 Knowledge Management Feedback Form
11
Getting feedback from clients/ customers is professionally good. It serves as a tool for
continuous improvements of the project system being developed. Any project is deemed
complete when feedback from the client has been received.
Student form: General
This form was used to gather important data from the end users mostly the students about their
perception for the new system
Assessment Question Strongly
Agree
Agree Somehow Disagree Strongly
Disagree
Has the system eased service delivery?
Do you think the system was well
thought of?
Did the system change your usual
eating habits?
Table 1: Student Survey: General
The feedback from this survey will be used as a basis for making adjustments in the future to suit
the students, taking into consideration that they were the key stakeholders in this particular
project.
Basic assessment
This customer feedback report is used by the customer to rate developer’s understanding of the
important aspects of the system
Assessment item Strongly
Agree
Agree Neither
Agree/Disa
gree
Disagree Strongly
Disagree
System solves real problem
All sections of system addressed
The system has good usability
Table 2: Basic Assessment
Team performance
The performance of the team needs to be evaluated based on the feedback that the client gives.
The following was a survey form that was used to rate the team’s performance in terms of the
attitude, level of expertise and their innovativeness with respect to the project undertaken.
In rating the team performance, customer rating will give the term an opportunity to explore
ways to enhance their team work.
Assessment item Strongly
Agree
Agree Neither
Agree/Di
Disagree Strongly
Disagree
Getting feedback from clients/ customers is professionally good. It serves as a tool for
continuous improvements of the project system being developed. Any project is deemed
complete when feedback from the client has been received.
Student form: General
This form was used to gather important data from the end users mostly the students about their
perception for the new system
Assessment Question Strongly
Agree
Agree Somehow Disagree Strongly
Disagree
Has the system eased service delivery?
Do you think the system was well
thought of?
Did the system change your usual
eating habits?
Table 1: Student Survey: General
The feedback from this survey will be used as a basis for making adjustments in the future to suit
the students, taking into consideration that they were the key stakeholders in this particular
project.
Basic assessment
This customer feedback report is used by the customer to rate developer’s understanding of the
important aspects of the system
Assessment item Strongly
Agree
Agree Neither
Agree/Disa
gree
Disagree Strongly
Disagree
System solves real problem
All sections of system addressed
The system has good usability
Table 2: Basic Assessment
Team performance
The performance of the team needs to be evaluated based on the feedback that the client gives.
The following was a survey form that was used to rate the team’s performance in terms of the
attitude, level of expertise and their innovativeness with respect to the project undertaken.
In rating the team performance, customer rating will give the term an opportunity to explore
ways to enhance their team work.
Assessment item Strongly
Agree
Agree Neither
Agree/Di
Disagree Strongly
Disagree
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




