7COM1068 Penetration Testing Report: University of Hertfordshire
VerifiedAdded on 2022/08/17
|14
|3069
|417
Report
AI Summary
This report provides a comprehensive analysis of penetration testing, a crucial practice for identifying security vulnerabilities in computer networks, web applications, and systems. It begins with an introduction to penetration testing, highlighting its objectives and importance. The report then delves into the methodologies employed, including white box, black box, and gray box testing, comparing and contrasting their approaches and applications. Ethical considerations for penetration testers are thoroughly examined, emphasizing the importance of contracts, authorization, and adherence to legal and professional standards. Finally, the report outlines a standard operating procedure (SOP) for penetration testing, providing a structured approach to conducting assessments and mitigating risks. The report draws on various sources to provide a well-rounded understanding of the subject.

Running head: PENETRATION TESTING
PENETRATION TESTING
Name of the Student:
Name of the University:
Author Note:
PENETRATION TESTING
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1PENETRATION TESTING
Table of Contents
Introduction......................................................................................................................................2
Methodologies of Penetration Testing.............................................................................................2
White Box Testing.......................................................................................................................3
Black Box Testing.......................................................................................................................4
Gray Box Testing.........................................................................................................................4
Ethical Considerations.....................................................................................................................5
Standard Operating Procedure.........................................................................................................7
References......................................................................................................................................10
Table of Contents
Introduction......................................................................................................................................2
Methodologies of Penetration Testing.............................................................................................2
White Box Testing.......................................................................................................................3
Black Box Testing.......................................................................................................................4
Gray Box Testing.........................................................................................................................4
Ethical Considerations.....................................................................................................................5
Standard Operating Procedure.........................................................................................................7
References......................................................................................................................................10

2PENETRATION TESTING
Introduction
Penetration testing is practice to test computer network, web application or system for
finding security vulnerabilities which an attacker might exploit. The penetration testing could be
performed automated or manual to software applications. This process consists of collecting
information of target before this test, which identifies possible points of entry, trying to break
into either for virtually or in real as well as reporting back findings. Penetration testing’s primary
objective is identifying security’s weaknesses (Pozzobon et al. 2018). Penetration testing might
be used for testing of security policy of firm, its adherence in compliance the requirements,
security awareness of the employees as well as organization’s ability in identifying as well as
responding to the security incidents. Penetration test could highlight the weaknesses within
security policies of an organization.
This paper would identify and compare between the methodologies of penetration testing.
The paper would analyze about the statutory as well as ethical considerations for penetration
tester. Standard Operating Procedure along with decision tree for penetration testing would be
provided in the paper as well. SOP would define every step of the instructions that is compiled y
organization for helping the workers in carrying out the routine operations.
Methodologies of Penetration Testing
Penetration testing could be categorized depending on the different parameters such as
knowledge of target or areas where this is performed or position of penetration tester. There are
several methods that are used for getting into network of target system Penetration testing would
determine feasibility for specific set of the attack vendors (Denis, Zena and Hayajneh 2016). The
Introduction
Penetration testing is practice to test computer network, web application or system for
finding security vulnerabilities which an attacker might exploit. The penetration testing could be
performed automated or manual to software applications. This process consists of collecting
information of target before this test, which identifies possible points of entry, trying to break
into either for virtually or in real as well as reporting back findings. Penetration testing’s primary
objective is identifying security’s weaknesses (Pozzobon et al. 2018). Penetration testing might
be used for testing of security policy of firm, its adherence in compliance the requirements,
security awareness of the employees as well as organization’s ability in identifying as well as
responding to the security incidents. Penetration test could highlight the weaknesses within
security policies of an organization.
This paper would identify and compare between the methodologies of penetration testing.
The paper would analyze about the statutory as well as ethical considerations for penetration
tester. Standard Operating Procedure along with decision tree for penetration testing would be
provided in the paper as well. SOP would define every step of the instructions that is compiled y
organization for helping the workers in carrying out the routine operations.
Methodologies of Penetration Testing
Penetration testing could be categorized depending on the different parameters such as
knowledge of target or areas where this is performed or position of penetration tester. There are
several methods that are used for getting into network of target system Penetration testing would
determine feasibility for specific set of the attack vendors (Denis, Zena and Hayajneh 2016). The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3PENETRATION TESTING
testing would identify risk vulnerabilities which result from vulnerabilities’ lower risk’s
combination that are exploited in specific sequence. Penetration testing figures out the
vulnerabilities which might be tough to detect the network applications. Penetration testing
assesses potential business’s magnitude as well as successful attacks’ operational impacts.
Penetration testing provides evidence for supporting increased investment within security
personnel as well as technology (Casola et al. 2020). Every penetration testing could be
conducted by anyone of the methodologies: white box testing, black box testing and gray box
testing.
White Box Testing
This testing is penetration testing’s method which tests the internal structures as
well as workings of system or network as opposed with the functionality. In this testing, the
programming skills along with system’s internal perspective are used for designing the test
causes. Tester selects inputs for exercising paths by code as well as determining expected
outputs. It is method to test system or network at source code’s level. Such test cases could be
derived by design techniques’ use: testing of testing of data flow, control flow, path testing,
branch coverage, decision coverage, modified condition and statement coverage.
These techniques are used by it as guidelines to create environment that is free of error
through examining the network or the system. Techniques of white box testing are to build
blocks for this testing. White box testing allows in performing testing of system or network with
root level or admin access. It consists of access to documents, source code, specifications and
architecture. Though, the testing could be a bit time consuming as for the thorough approach
(Satria et al. 2018). White box testing’s objective is checking robustness of infrastructure within
testing would identify risk vulnerabilities which result from vulnerabilities’ lower risk’s
combination that are exploited in specific sequence. Penetration testing figures out the
vulnerabilities which might be tough to detect the network applications. Penetration testing
assesses potential business’s magnitude as well as successful attacks’ operational impacts.
Penetration testing provides evidence for supporting increased investment within security
personnel as well as technology (Casola et al. 2020). Every penetration testing could be
conducted by anyone of the methodologies: white box testing, black box testing and gray box
testing.
White Box Testing
This testing is penetration testing’s method which tests the internal structures as
well as workings of system or network as opposed with the functionality. In this testing, the
programming skills along with system’s internal perspective are used for designing the test
causes. Tester selects inputs for exercising paths by code as well as determining expected
outputs. It is method to test system or network at source code’s level. Such test cases could be
derived by design techniques’ use: testing of testing of data flow, control flow, path testing,
branch coverage, decision coverage, modified condition and statement coverage.
These techniques are used by it as guidelines to create environment that is free of error
through examining the network or the system. Techniques of white box testing are to build
blocks for this testing. White box testing allows in performing testing of system or network with
root level or admin access. It consists of access to documents, source code, specifications and
architecture. Though, the testing could be a bit time consuming as for the thorough approach
(Satria et al. 2018). White box testing’s objective is checking robustness of infrastructure within
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4PENETRATION TESTING
environment where the security information could not be strictly controlled. White box testing
gives information of exploitable flaws through prioritized manner.
Black Box Testing
This testing is penetration testing’s method which examines functionality of system
without peering in internal workings or structures. This testing could be virtually applied to
penetration testing’s every level: unit, acceptance, system and integration. There is no need of
specific knowledge about code of system, programming knowledge and internal structure. Tester
knows about the working procedure of the software, however does not know how it is done. Test
cases are created around requirements and specifications (Stefinko, Piskozub and Banakh 2016).
Test cases could be derived from software’s external descriptions which consist of specifications,
design parameters and requirements. Both valid as well as invalid inputs are selected by tester
and correct output is determined.
This testing refers to method where there is no knowledge of ethical hacker of system or
network that is attacked. Black box testing’s goal is simulating attack of cyber warfare or
external hacking. Testing of black box needs no previous information about target system or
network and is performed actually keeping this as scenario of real world hacking. Black box
testing enables security experts in looking at security’s several other levels, which includes
vulnerabilities of server level (Dawson and McDonald 2016). End goal of black box testing is
verifying integrity of network or system.
Gray Box Testing
It is technique for testing software application or product having partial knowledge for
application’s internal workings. Gray box testing’s purpose is searching for the defects for
environment where the security information could not be strictly controlled. White box testing
gives information of exploitable flaws through prioritized manner.
Black Box Testing
This testing is penetration testing’s method which examines functionality of system
without peering in internal workings or structures. This testing could be virtually applied to
penetration testing’s every level: unit, acceptance, system and integration. There is no need of
specific knowledge about code of system, programming knowledge and internal structure. Tester
knows about the working procedure of the software, however does not know how it is done. Test
cases are created around requirements and specifications (Stefinko, Piskozub and Banakh 2016).
Test cases could be derived from software’s external descriptions which consist of specifications,
design parameters and requirements. Both valid as well as invalid inputs are selected by tester
and correct output is determined.
This testing refers to method where there is no knowledge of ethical hacker of system or
network that is attacked. Black box testing’s goal is simulating attack of cyber warfare or
external hacking. Testing of black box needs no previous information about target system or
network and is performed actually keeping this as scenario of real world hacking. Black box
testing enables security experts in looking at security’s several other levels, which includes
vulnerabilities of server level (Dawson and McDonald 2016). End goal of black box testing is
verifying integrity of network or system.
Gray Box Testing
It is technique for testing software application or product having partial knowledge for
application’s internal workings. Gray box testing’s purpose is searching for the defects for

5PENETRATION TESTING
improper structure of code or improper usage of functions of application. It is method of
software testing that is combination of white box testing with black box testing. In this testing,
errors of context are identified which are related with web systems. This increases testing
coverage through concentrating on every layer of complex system. This testing gives combined
benefits for both black box testing and white box testing (Hatfield 2019). This testing combines
input of testers along with developers and also improves total product quality. This testing
reduces overhead of the long process to test functional along with non-functional kinds.
Testing is performed from user’s view instead of designer’s view. This testing provides
free time to developers for fixing the defects. For performing gray box testing, this is not
required that tester could access source code. The test could be designed depending on
knowledge about internal states, architectures, algorithm or other descriptions of program
behavior’s higher level. Black box testing’s straightforward technique is applied by gray box
testing (Najera-Gutierrez and Ansari 2018). This testing is dependent on generation of test case
of requirement, as such, this presents every conditions before program could be tested by the
assertion method.
Ethical Considerations
Penetration testing is proactive way to test web applications through performing attacks
which are same to real attack which could occur anytime. They could be executed in controlled
way having objective to find security flaws and for providing feedback about how these risks
could be mitigated by these flaws. When planning for executing penetration testing, there are
factors which should be considered before commencing the engagement (Chiong, Leonard and
Chang 2018). While performing penetration testing, the tester is breaking into computer system
improper structure of code or improper usage of functions of application. It is method of
software testing that is combination of white box testing with black box testing. In this testing,
errors of context are identified which are related with web systems. This increases testing
coverage through concentrating on every layer of complex system. This testing gives combined
benefits for both black box testing and white box testing (Hatfield 2019). This testing combines
input of testers along with developers and also improves total product quality. This testing
reduces overhead of the long process to test functional along with non-functional kinds.
Testing is performed from user’s view instead of designer’s view. This testing provides
free time to developers for fixing the defects. For performing gray box testing, this is not
required that tester could access source code. The test could be designed depending on
knowledge about internal states, architectures, algorithm or other descriptions of program
behavior’s higher level. Black box testing’s straightforward technique is applied by gray box
testing (Najera-Gutierrez and Ansari 2018). This testing is dependent on generation of test case
of requirement, as such, this presents every conditions before program could be tested by the
assertion method.
Ethical Considerations
Penetration testing is proactive way to test web applications through performing attacks
which are same to real attack which could occur anytime. They could be executed in controlled
way having objective to find security flaws and for providing feedback about how these risks
could be mitigated by these flaws. When planning for executing penetration testing, there are
factors which should be considered before commencing the engagement (Chiong, Leonard and
Chang 2018). While performing penetration testing, the tester is breaking into computer system
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6PENETRATION TESTING
or network. Ethical hackers could try in penetrating system at behest of operator or owner of
system. There are several different kinds of penetration testing. Review of software code for the
vulnerabilities could be part of penetration testing. Ping sweep could be penetration testing’s
part. It is crime in accessing or attempting to access computer system or network without having
authorization. Before starting penetration test, parties must enter into contract which indicates
exactly penetration tester would do as well as range of networks, IP addresses, devices, subnets
or systems which would be the subject of penetration testing (Opedal 2019). If penetration
testing consists of software decompiling and review, make sure software’s copyright permits
code review.
Penetration tester must get “get out of jail free” card by customer, which would indicate
penetration testing is not unauthorized, however would indicate also that customers has legal
authority for authorizing the penetration test. If penetration tester is authorized by cloud
customer for testing the network within cloud, that doesn’t mean there is authority for cloud
provider for penetration testing. Penetration testers’ another practical issue is getting scope of
penetration testing wrong. If IP addresses’ incorrect range is provided by customer for testing,
and these wrong IP addresses are tested, penetration tester might find him on wrong end (Sina
2019). Situation is worse even if correct range of IP address is provided by customer and wrong
range of IP addresses is attacked by penetration tester. Typical penetration tester might warrant
that penetration tester would use type of skills and professionalism found commonly in
organization, however not promise that test would find every or substantially every
misconfigurations and vulnerabilities.
It is essential in documenting lack of the findings as this should document itself. Another
key problem in contracts of penetration testing is determining where penetration would be
or network. Ethical hackers could try in penetrating system at behest of operator or owner of
system. There are several different kinds of penetration testing. Review of software code for the
vulnerabilities could be part of penetration testing. Ping sweep could be penetration testing’s
part. It is crime in accessing or attempting to access computer system or network without having
authorization. Before starting penetration test, parties must enter into contract which indicates
exactly penetration tester would do as well as range of networks, IP addresses, devices, subnets
or systems which would be the subject of penetration testing (Opedal 2019). If penetration
testing consists of software decompiling and review, make sure software’s copyright permits
code review.
Penetration tester must get “get out of jail free” card by customer, which would indicate
penetration testing is not unauthorized, however would indicate also that customers has legal
authority for authorizing the penetration test. If penetration tester is authorized by cloud
customer for testing the network within cloud, that doesn’t mean there is authority for cloud
provider for penetration testing. Penetration testers’ another practical issue is getting scope of
penetration testing wrong. If IP addresses’ incorrect range is provided by customer for testing,
and these wrong IP addresses are tested, penetration tester might find him on wrong end (Sina
2019). Situation is worse even if correct range of IP address is provided by customer and wrong
range of IP addresses is attacked by penetration tester. Typical penetration tester might warrant
that penetration tester would use type of skills and professionalism found commonly in
organization, however not promise that test would find every or substantially every
misconfigurations and vulnerabilities.
It is essential in documenting lack of the findings as this should document itself. Another
key problem in contracts of penetration testing is determining where penetration would be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7PENETRATION TESTING
conducted. Successful penetration testing could result in penetration tester getting in computer
network or system which they might not had ability in accessing. It might consist of accessing
databases or data that contain sensitive information. Penetration testing might expose tester to
this sensitive information. Penetration tester should understand scope as well as extent of duties
for protecting every data they would be accessing. Stating that report of penetration test is owned
by the customer creates another issue (Hussain, Hasan and Chughtai 2017). Networks are
interconnected. Agreement of penetration testing seems like simple document. Experienced
counsel and competent would be required for avoiding pitfalls. Agreement of penetration testing
must exactly specify what would and would not be performed as well assumptions which
underlie agreement. The assumptions should be defunded by penetration tester which underlie
penetration test.
Penetration tester would depend on customer for defining which system or network
should be tested. The date of penetration testing along with nature of access needed for
conducting penetration testing and nature of cooperation required for making test meaningful
should be defined also by penetration tester. Scope of the notice should be provided also for
initiating the penetration test. Another legal challenge which comes up for penetration test is
impact of penetration test upon users of system, when testing is performed on live system
(Knowles, Baron and McGarr 2016). Customer should understand that penetration testing could
disrupt brittle system. Penetration tester having contract specifically authorizes penetration
testing and penetration tester won’t be liable of the damages caused.
conducted. Successful penetration testing could result in penetration tester getting in computer
network or system which they might not had ability in accessing. It might consist of accessing
databases or data that contain sensitive information. Penetration testing might expose tester to
this sensitive information. Penetration tester should understand scope as well as extent of duties
for protecting every data they would be accessing. Stating that report of penetration test is owned
by the customer creates another issue (Hussain, Hasan and Chughtai 2017). Networks are
interconnected. Agreement of penetration testing seems like simple document. Experienced
counsel and competent would be required for avoiding pitfalls. Agreement of penetration testing
must exactly specify what would and would not be performed as well assumptions which
underlie agreement. The assumptions should be defunded by penetration tester which underlie
penetration test.
Penetration tester would depend on customer for defining which system or network
should be tested. The date of penetration testing along with nature of access needed for
conducting penetration testing and nature of cooperation required for making test meaningful
should be defined also by penetration tester. Scope of the notice should be provided also for
initiating the penetration test. Another legal challenge which comes up for penetration test is
impact of penetration test upon users of system, when testing is performed on live system
(Knowles, Baron and McGarr 2016). Customer should understand that penetration testing could
disrupt brittle system. Penetration tester having contract specifically authorizes penetration
testing and penetration tester won’t be liable of the damages caused.

8PENETRATION TESTING
Standard Operating Procedure
Penetration testing is cyberattack by penetration tester against a system or network for
checking exploitable vulnerabilities. Penetration test is kind of testing of security which uncovers
risks, threats and vulnerabilities within software application, web application or network which
tester could exploit. Penetration testing’s purpose is finding every vulnerabilities in security
which are present within system after testing. In context of web application’s security,
penetration testing could be used for augmenting web application firewall (WAF). This testing
could include attempted breach of several application systems such as backend servers, frontend
servers and application protocol interfaces (APIs) for uncovering vulnerabilities like unsanitized
inputs which are susceptible for coding attacks of injection. Vulnerability is risk which
penetration tester could gain or disrupt authorized access for system or data contained in it. The
vulnerabilities are introduced usually by accident in case of software development as well as
implementation phase (Dieber et al. 2020). The common vulnerabilities consist of software bugs,
configuration errors and design errors. Penetration analysis is dependent on two mechanisms
such as Penetration Testing and Vulnerability Assessment. Process of penetration testing could
be segmented in five phases:
Planning and Reconnaissance: It is first phase of penetration test which consists of defining
goals and scope of test that consists of systems which should be addresses along with methods of
testing being used. This phase collects intelligence such as mail server, network and domain
names to understanding better how the target works as well as the potential vulnerabilities.
Scanning: Next phase is understanding response of target application to several attempts of
intrusion. Application’s code is inspected by static analysis for estimating way this behaves
during running. Overall code could be scanned by such tools in single pass. Inspects
Standard Operating Procedure
Penetration testing is cyberattack by penetration tester against a system or network for
checking exploitable vulnerabilities. Penetration test is kind of testing of security which uncovers
risks, threats and vulnerabilities within software application, web application or network which
tester could exploit. Penetration testing’s purpose is finding every vulnerabilities in security
which are present within system after testing. In context of web application’s security,
penetration testing could be used for augmenting web application firewall (WAF). This testing
could include attempted breach of several application systems such as backend servers, frontend
servers and application protocol interfaces (APIs) for uncovering vulnerabilities like unsanitized
inputs which are susceptible for coding attacks of injection. Vulnerability is risk which
penetration tester could gain or disrupt authorized access for system or data contained in it. The
vulnerabilities are introduced usually by accident in case of software development as well as
implementation phase (Dieber et al. 2020). The common vulnerabilities consist of software bugs,
configuration errors and design errors. Penetration analysis is dependent on two mechanisms
such as Penetration Testing and Vulnerability Assessment. Process of penetration testing could
be segmented in five phases:
Planning and Reconnaissance: It is first phase of penetration test which consists of defining
goals and scope of test that consists of systems which should be addresses along with methods of
testing being used. This phase collects intelligence such as mail server, network and domain
names to understanding better how the target works as well as the potential vulnerabilities.
Scanning: Next phase is understanding response of target application to several attempts of
intrusion. Application’s code is inspected by static analysis for estimating way this behaves
during running. Overall code could be scanned by such tools in single pass. Inspects
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9PENETRATION TESTING
application’s code is inspected by dynamic analysis in the running state (Dürrwang et al. 2018).
It is more practical process to scan, for as this provides view of real time into performance of an
application.
Gaining Access: The phase uses attacks of web application like SQL injection, backdoors and
cross-site scripting to uncover target’s vulnerabilities. Penetration testers attempt and then
exploit such vulnerabilities by stealing data, escalating privileges and intercepting traffic for
understanding damage they could cause.
Maintaining Access: This phase’s goal is seeing if vulnerability might be used in achieving
persistent presence within exploited system. Idea is imitating threats of advanced persistent.
Analysis: Results of this testing are compiled within report. The report contains specific
vulnerabilities which were exploited, quantity of time penetration tester could remain in system
undetected and sensitive data which was accessed (Casola et al. 2018).
Security personnel analyses the information for helping configure WAF setting in an
organization and application security’s other solutions for patching vulnerabilities as well as
protecting against the attacks in the future.
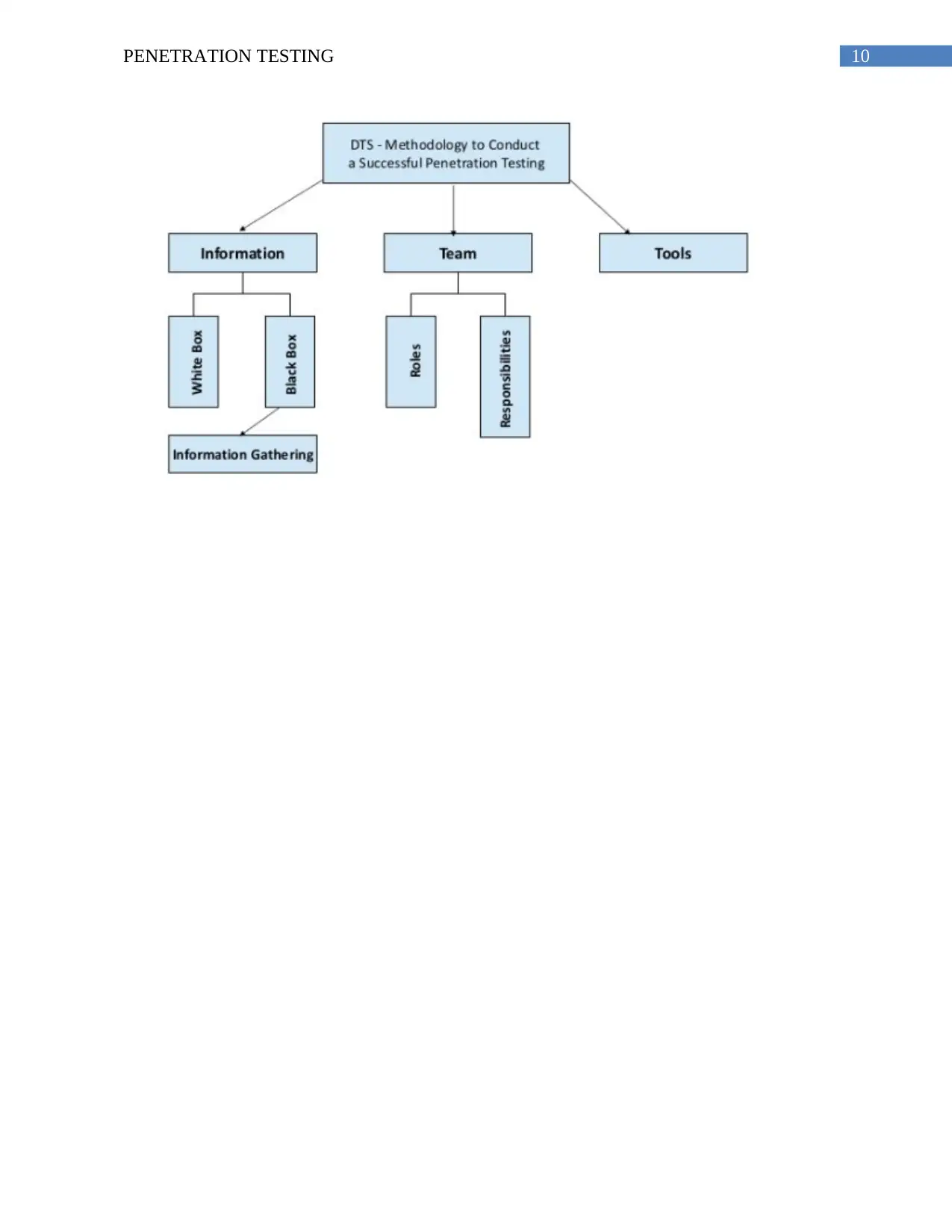
Decision Making Tree:
application’s code is inspected by dynamic analysis in the running state (Dürrwang et al. 2018).
It is more practical process to scan, for as this provides view of real time into performance of an
application.
Gaining Access: The phase uses attacks of web application like SQL injection, backdoors and
cross-site scripting to uncover target’s vulnerabilities. Penetration testers attempt and then
exploit such vulnerabilities by stealing data, escalating privileges and intercepting traffic for
understanding damage they could cause.
Maintaining Access: This phase’s goal is seeing if vulnerability might be used in achieving
persistent presence within exploited system. Idea is imitating threats of advanced persistent.
Analysis: Results of this testing are compiled within report. The report contains specific
vulnerabilities which were exploited, quantity of time penetration tester could remain in system
undetected and sensitive data which was accessed (Casola et al. 2018).
Security personnel analyses the information for helping configure WAF setting in an
organization and application security’s other solutions for patching vulnerabilities as well as
protecting against the attacks in the future.
Decision Making Tree:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10PENETRATION TESTING

11PENETRATION TESTING
References
Casola, V., Benedictis, A.D., Rak, M. and Villano, U., 2020. A methodology for automated
penetration testing of cloud applications. International Journal of Grid and Utility
Computing, 11(2), pp.267-277.
Casola, V., De Benedictis, A., Rak, M. and Villano, U., 2018, June. Towards automated
penetration testing for cloud applications. In 2018 IEEE 27th International Conference on
Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE) (pp. 24-29).
IEEE.
Chiong, W., Leonard, M.K. and Chang, E.F., 2018. Neurosurgical patients as human research
subjects: ethical considerations in intracranial electrophysiology research. Neurosurgery, 83(1),
pp.29-37.
Dawson, J. and McDonald, J.T., 2016, April. Improving Penetration Testing Methodologies for
Security-Based Risk Assessment. In 2016 Cybersecurity Symposium (CYBERSEC) (pp. 51-58).
IEEE.
Denis, M., Zena, C. and Hayajneh, T., 2016, April. Penetration testing: Concepts, attack
methods, and defense strategies. In 2016 IEEE Long Island Systems, Applications and
Technology Conference (LISAT) (pp. 1-6). IEEE.
Dieber, B., White, R., Taurer, S., Breiling, B., Caiazza, G., Christensen, H. and Cortesi, A.,
2020. Penetration testing ROS. In Robot Operating System (ROS) (pp. 183-225). Springer,
Cham.
References
Casola, V., Benedictis, A.D., Rak, M. and Villano, U., 2020. A methodology for automated
penetration testing of cloud applications. International Journal of Grid and Utility
Computing, 11(2), pp.267-277.
Casola, V., De Benedictis, A., Rak, M. and Villano, U., 2018, June. Towards automated
penetration testing for cloud applications. In 2018 IEEE 27th International Conference on
Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE) (pp. 24-29).
IEEE.
Chiong, W., Leonard, M.K. and Chang, E.F., 2018. Neurosurgical patients as human research
subjects: ethical considerations in intracranial electrophysiology research. Neurosurgery, 83(1),
pp.29-37.
Dawson, J. and McDonald, J.T., 2016, April. Improving Penetration Testing Methodologies for
Security-Based Risk Assessment. In 2016 Cybersecurity Symposium (CYBERSEC) (pp. 51-58).
IEEE.
Denis, M., Zena, C. and Hayajneh, T., 2016, April. Penetration testing: Concepts, attack
methods, and defense strategies. In 2016 IEEE Long Island Systems, Applications and
Technology Conference (LISAT) (pp. 1-6). IEEE.
Dieber, B., White, R., Taurer, S., Breiling, B., Caiazza, G., Christensen, H. and Cortesi, A.,
2020. Penetration testing ROS. In Robot Operating System (ROS) (pp. 183-225). Springer,
Cham.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





