Risk and Issue Management Report: Detailed Analysis of ICT
VerifiedAdded on 2023/04/08
|12
|1142
|486
Report
AI Summary
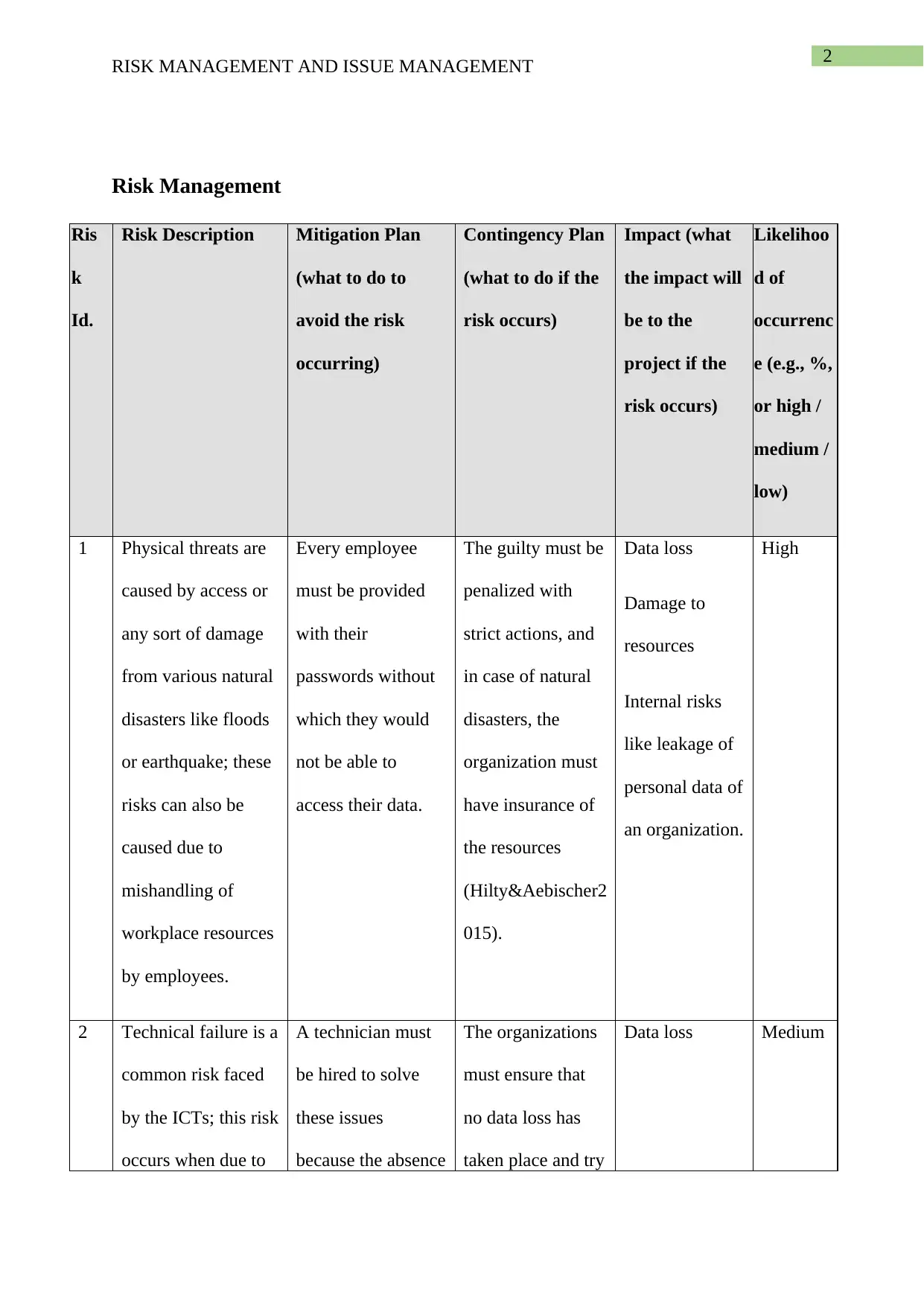
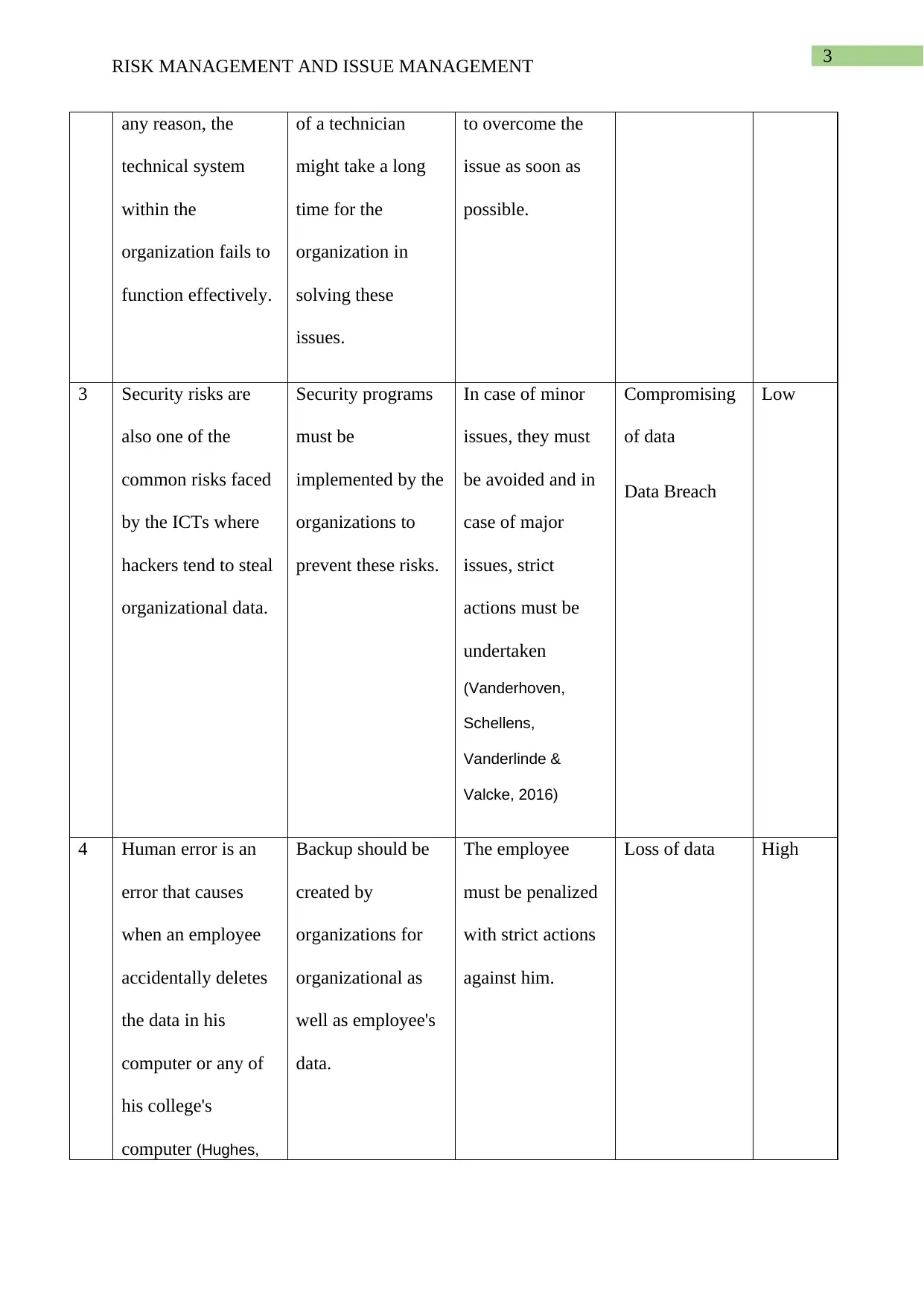
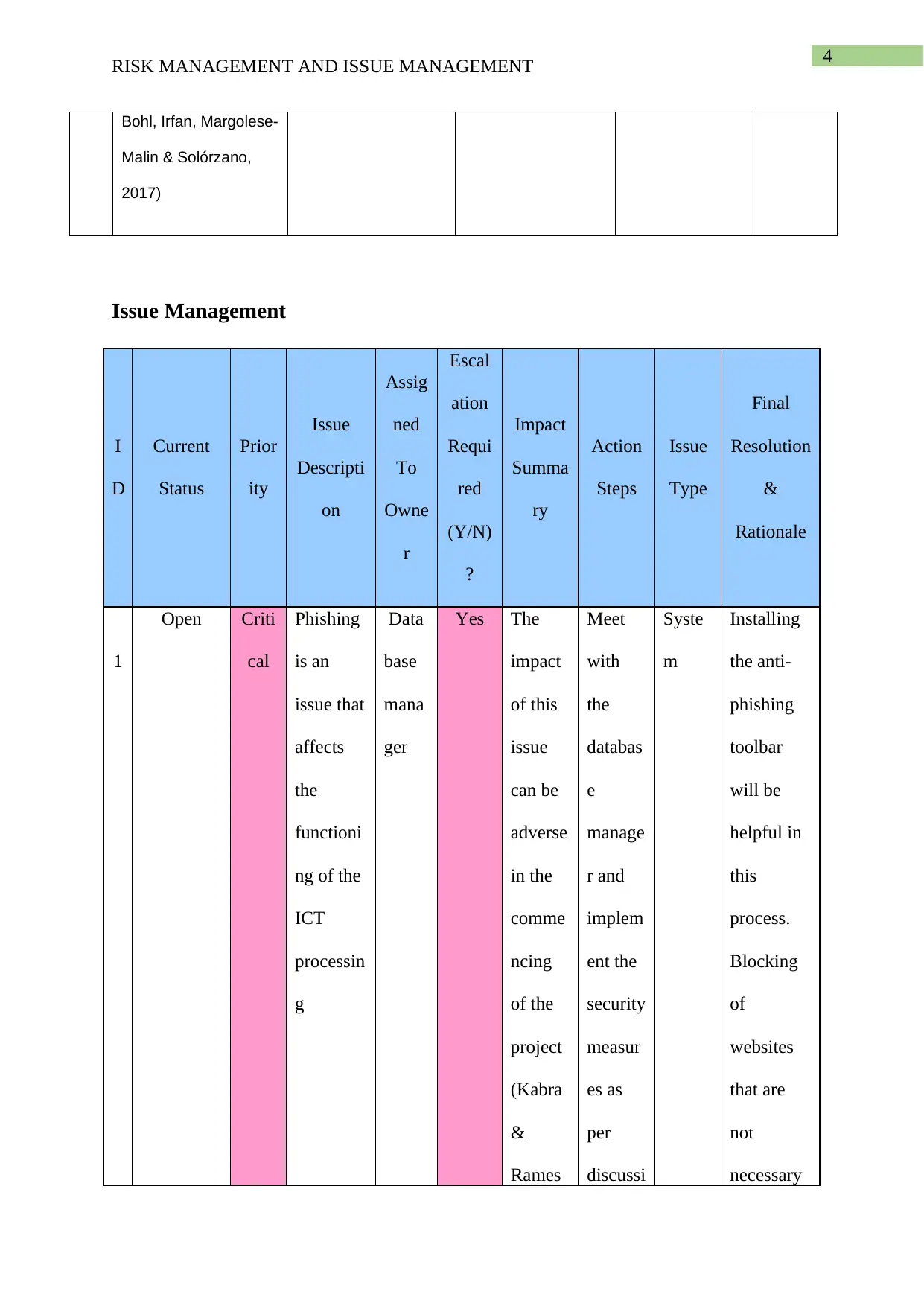
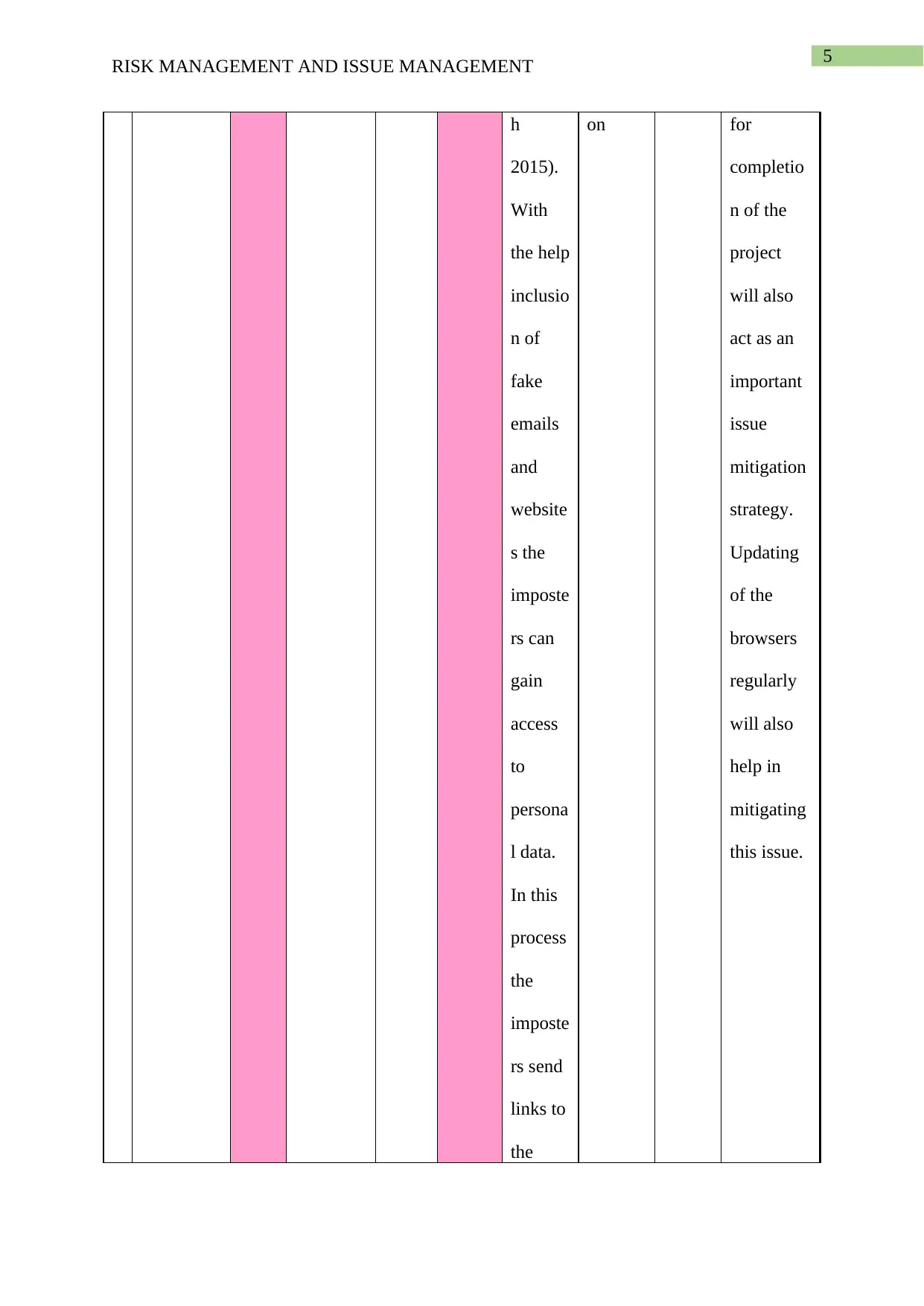
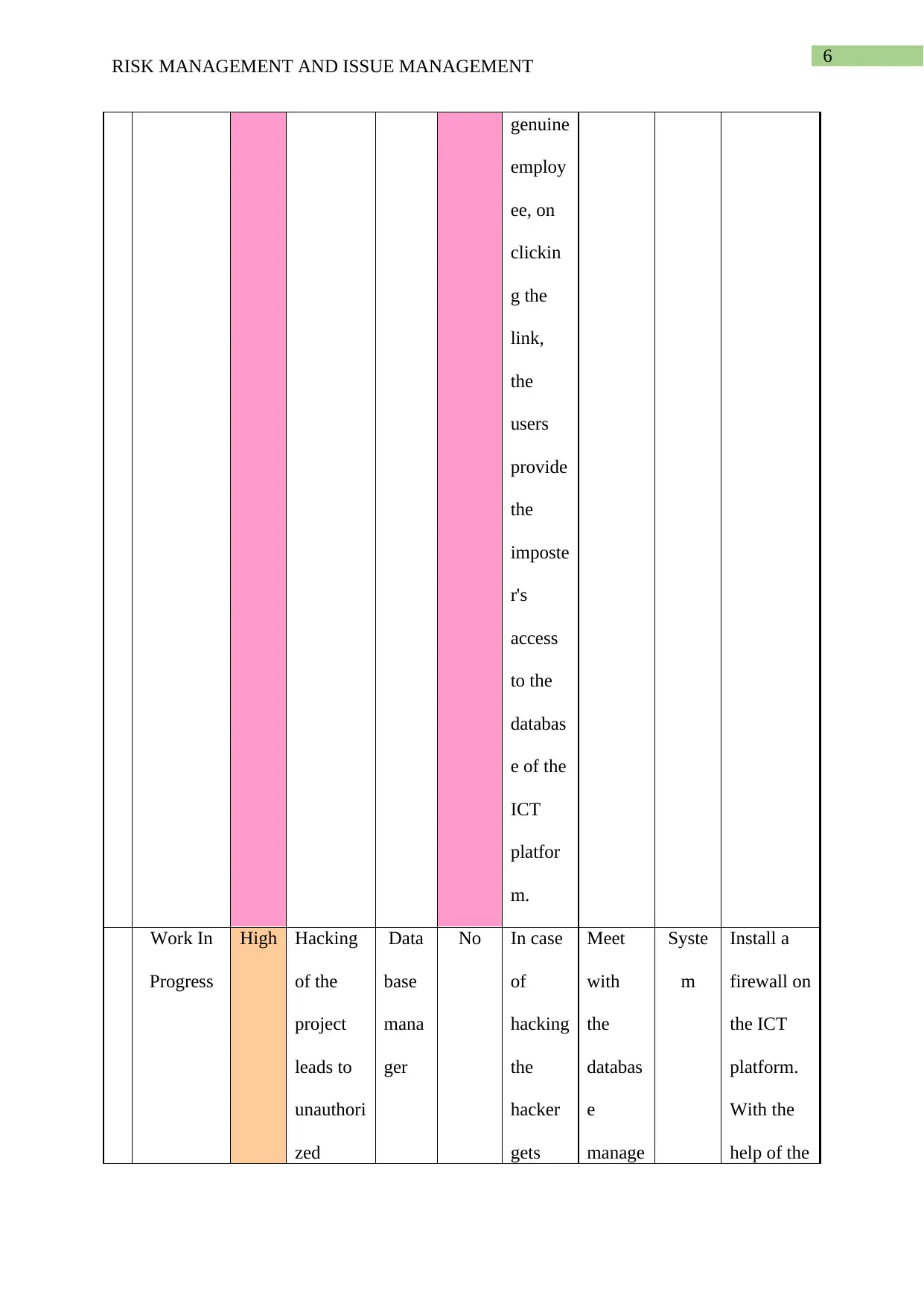
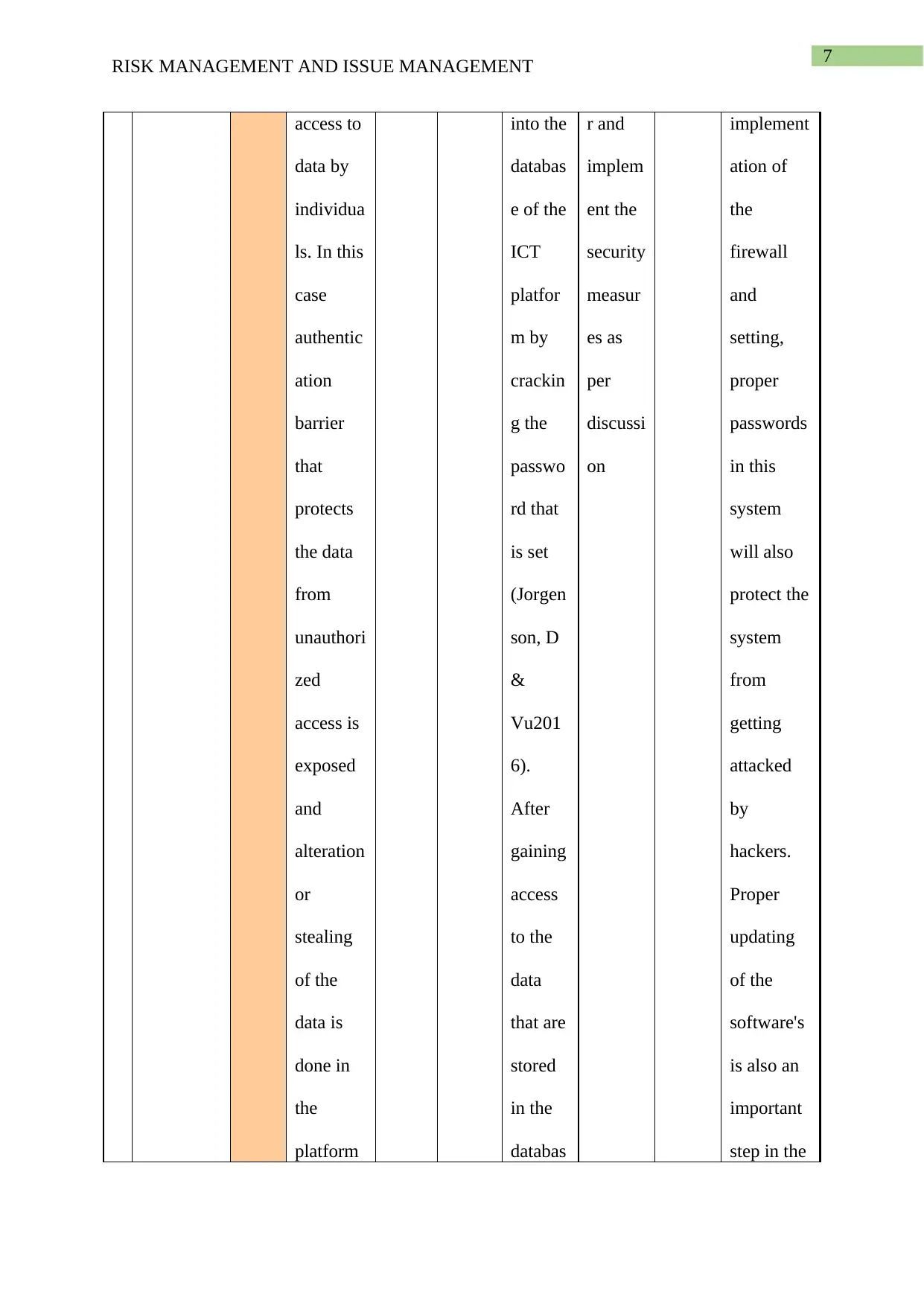
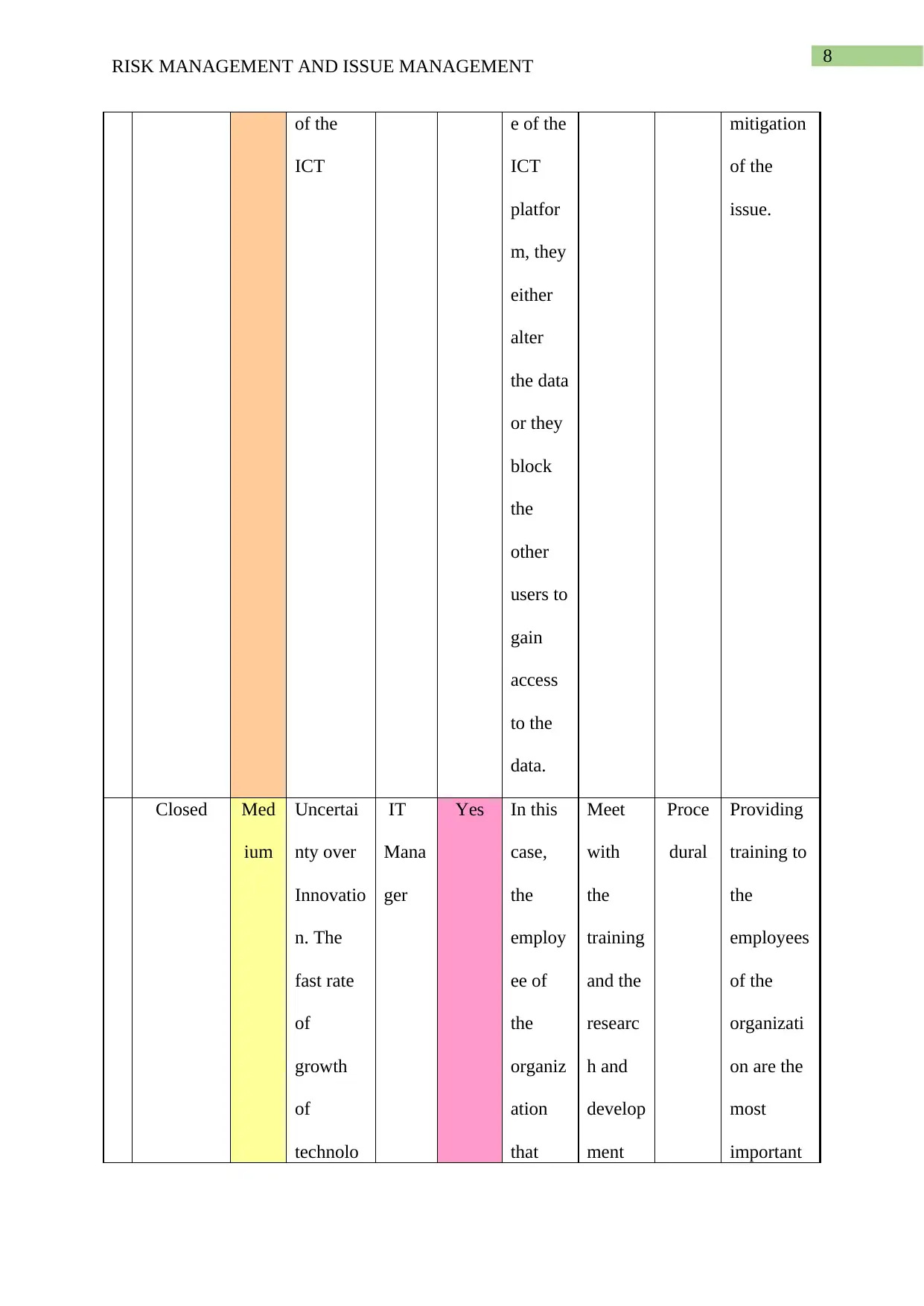
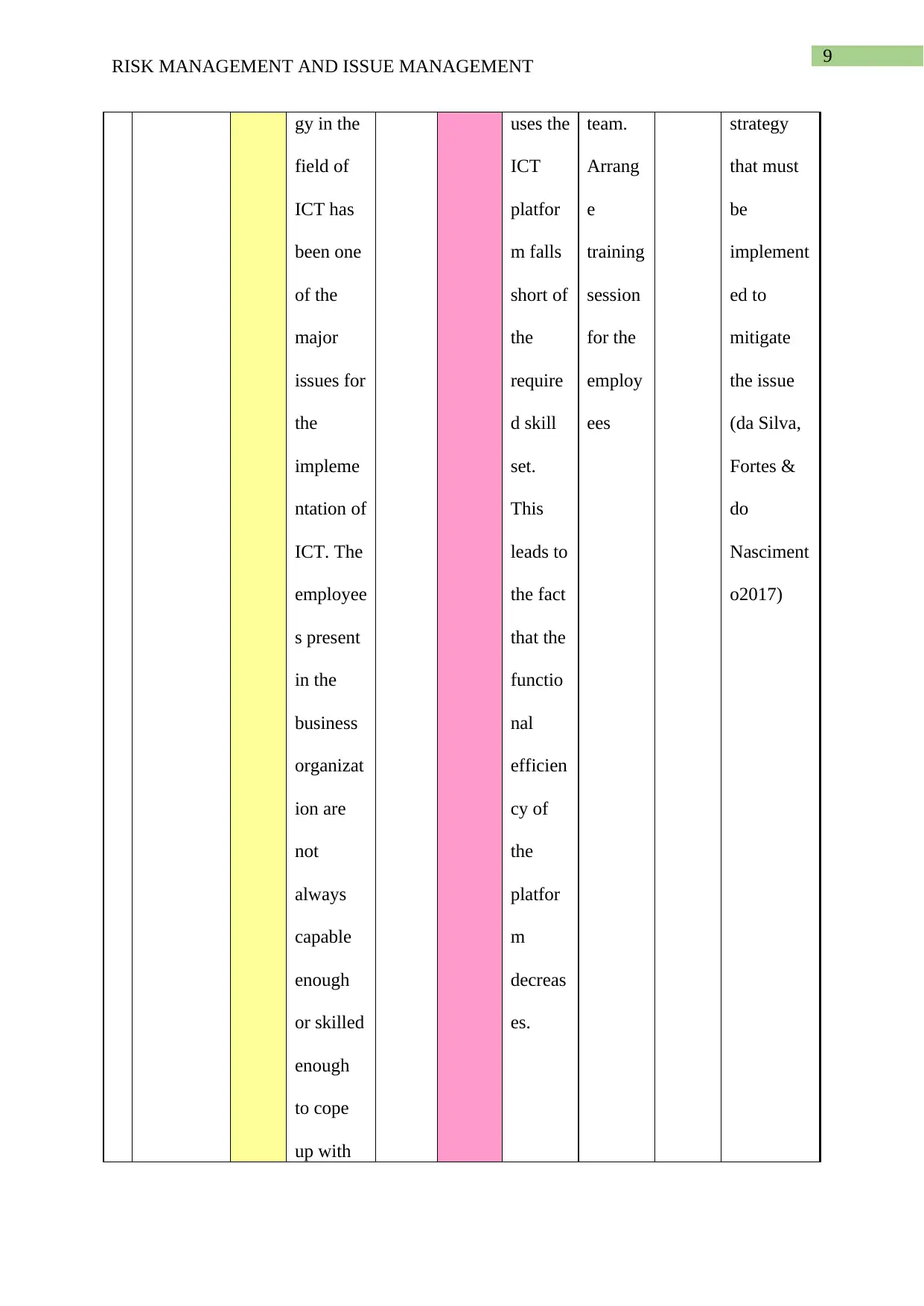
This report provides a comprehensive analysis of risk and issue management, particularly within the context of Information and Communication Technology (ICT) projects. The report begins by defining risk management, presenting a table that details various risks such as physical threats, technical failures, security risks, and human error, along with their mitigation plans, contingency plans, and potential impacts. The report also delves into issue management, presenting a table that outlines current issues, their descriptions, assigned owners, status, priority, and proposed resolutions. Specific issues like phishing, hacking, and operational uncertainty are analyzed, along with the proposed steps to mitigate them. The report references several academic sources to support its findings and conclusions, offering valuable insights into managing risks and issues effectively in ICT environments.
1 out of 12









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)