University IoT Assignment: User Interface, Security, and Laws
VerifiedAdded on 2020/02/24
|12
|2117
|168
Homework Assignment
AI Summary
This assignment on the Internet of Things (IoT) explores various aspects of the technology. It begins by discussing the concept of a user interface, arguing that the best interface is often no user interface, and provides examples of easy and difficult user interfaces, including Nest thermostats, Windows 8 mobile, Convertbot Circular Menu, and parallax effects. The assignment then compares twisted pair, coaxial, and fiber optic cables based on bandwidth, distance, interference, cost, and security. It further examines different types of sensors, including sensor-based devices and RFID, detailing their advantages, disadvantages, key requirements, and examples. The assignment also addresses security issues in IoT applications, such as the need for firewalls, regular software updates, and data privacy concerns, including data-oriented and context-oriented privacy. It calculates the total time taken by an application and discusses the efficiency of a designed application, along with a comparison of Nielsen's Law and Moore's Law regarding bandwidth and processing speed improvements.

Running head: INTERNET OF THINGS
INTERNET OF THINGS
Name of Student
Name of University
Author’s Note
INTERNET OF THINGS
Name of Student
Name of University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INTERNET OF THINGS
Question 1:
Solution: The statement "the best interface for a system is no User Interface". Interface
simply is a platform where the user can communicate to the computer. The interface can be the
programme like java or C (Riahi et al 2014). in the give question the user interface is the screens
of the compute and mobile where the user can send the command to the computer. The user
interface does simply contained to the mobile screens which is constitutionally unnatural,
contains diminishing nature and are inhumane. To access the user interface and utilize it for own
purpose the knowledge of the coding is required and investment for the projects in terms of time
and money. Event after all the efforts only a fraction of the improvement is made. Thus the
according to the question the best interface is the no user interface. The no user interface helps in
producing the model or the design where there are no digital interfaces. The no user interface
gives the design model which has the relatively simple and modified technology without the help
of any interfaces. In order to use the natural process in designing the interface should be
eliminated from it. Instead of providing the computer what it needs and giving it a less priority.
A system should be made which is desgined on the thinking process of the humans not the
machines.
An example of the easy user interface
Some of the examples of an easy user interface are:
Nest thermostat:
A net thermostat is used as device for heating up the rooms and cooling up the rooms as
per the need (Miguelez, Esser & Slowik, 2015). It is an example of an user interface which
Question 1:
Solution: The statement "the best interface for a system is no User Interface". Interface
simply is a platform where the user can communicate to the computer. The interface can be the
programme like java or C (Riahi et al 2014). in the give question the user interface is the screens
of the compute and mobile where the user can send the command to the computer. The user
interface does simply contained to the mobile screens which is constitutionally unnatural,
contains diminishing nature and are inhumane. To access the user interface and utilize it for own
purpose the knowledge of the coding is required and investment for the projects in terms of time
and money. Event after all the efforts only a fraction of the improvement is made. Thus the
according to the question the best interface is the no user interface. The no user interface helps in
producing the model or the design where there are no digital interfaces. The no user interface
gives the design model which has the relatively simple and modified technology without the help
of any interfaces. In order to use the natural process in designing the interface should be
eliminated from it. Instead of providing the computer what it needs and giving it a less priority.
A system should be made which is desgined on the thinking process of the humans not the
machines.
An example of the easy user interface
Some of the examples of an easy user interface are:
Nest thermostat:
A net thermostat is used as device for heating up the rooms and cooling up the rooms as
per the need (Miguelez, Esser & Slowik, 2015). It is an example of an user interface which

2INTERNET OF THINGS
operates the entire function on a single switch for changing the temperature according to the user
needs.
The windows 8 mobile user interface:
The mobile company Nokia has designed a windows 8 version on its phone which is
quite similar to the desktop version of the windows in the year 2012. The windows 8 version
phone contains the features and functions very similar to the desktop versions which is easy to
operate and manage its applications. It is also a good example of the user interface.
Difficult User Interface-
The following are the two examples of easy user interface:
Parallax effect-
The Scrolling effect of parallax is 3D illusion in which the background is made up of
many layers that helps in making different types of movement having varying speed which
operate when they are scrolling (Rayes & Salam, 2017). The describes procees is a high and
complex process for the application of the user interface which happen when any website is
fragmented into its many parts of which is necessary and can be accessed with the help of by
oscillation of the side back and forth button which can comes into effect on the screen.
The Convertbot Circular Menu-
Convertbot application is the one of an user interfaces which is much complex and
difficult to operate to use as compared with the application function of the other user interface.
The convertbot application is used in mobile phones like phones and iPods and other apple
products (Hecht, 2015). The convertbot application is utilized as the basic units into a circular
operates the entire function on a single switch for changing the temperature according to the user
needs.
The windows 8 mobile user interface:
The mobile company Nokia has designed a windows 8 version on its phone which is
quite similar to the desktop version of the windows in the year 2012. The windows 8 version
phone contains the features and functions very similar to the desktop versions which is easy to
operate and manage its applications. It is also a good example of the user interface.
Difficult User Interface-
The following are the two examples of easy user interface:
Parallax effect-
The Scrolling effect of parallax is 3D illusion in which the background is made up of
many layers that helps in making different types of movement having varying speed which
operate when they are scrolling (Rayes & Salam, 2017). The describes procees is a high and
complex process for the application of the user interface which happen when any website is
fragmented into its many parts of which is necessary and can be accessed with the help of by
oscillation of the side back and forth button which can comes into effect on the screen.
The Convertbot Circular Menu-
Convertbot application is the one of an user interfaces which is much complex and
difficult to operate to use as compared with the application function of the other user interface.
The convertbot application is used in mobile phones like phones and iPods and other apple
products (Hecht, 2015). The convertbot application is utilized as the basic units into a circular
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INTERNET OF THINGS
motion. The applications and features which are capabilities of the convertbot applications have
simple and smooth functions with simple textures and different colors and the slick animation
which makes the phone and user friendly for the people.
Easy User Interface:
The easy user interface as discussed above is the net thermostat and a windows 8 mobile
application whose diagram is listed below.
Windows 8 mobile
Figure 1: Image of the windows 8 mobile phone
(Source: Rayes & Salam, 2017 , pp-80).
Nest Thermostat
motion. The applications and features which are capabilities of the convertbot applications have
simple and smooth functions with simple textures and different colors and the slick animation
which makes the phone and user friendly for the people.
Easy User Interface:
The easy user interface as discussed above is the net thermostat and a windows 8 mobile
application whose diagram is listed below.
Windows 8 mobile
Figure 1: Image of the windows 8 mobile phone
(Source: Rayes & Salam, 2017 , pp-80).
Nest Thermostat
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INTERNET OF THINGS
Figure 2: Net thermostat
(Source: Rayes & Salam, 2017 , pp-80).
Difficult User Interface:
The difficult user interface as discussed above is
Convertbot Circular Menu
Figure 3: A Convertbot Circular Menu
(Source: Velandia et al 2016 ,pp-72).
Parallax effect
Figure 2: Net thermostat
(Source: Rayes & Salam, 2017 , pp-80).
Difficult User Interface:
The difficult user interface as discussed above is
Convertbot Circular Menu
Figure 3: A Convertbot Circular Menu
(Source: Velandia et al 2016 ,pp-72).
Parallax effect
5INTERNET OF THINGS
Figure 4: Parallax effect
(Source: Velandia et al 2016).
The difficult user interface as discussed above is destined by machines and much difficult to
operate and understand its function thus cannot be a human friendly whereas the easy user
interface is user friendly and easy to operate thus comes under the easy user interface.
Questions 2
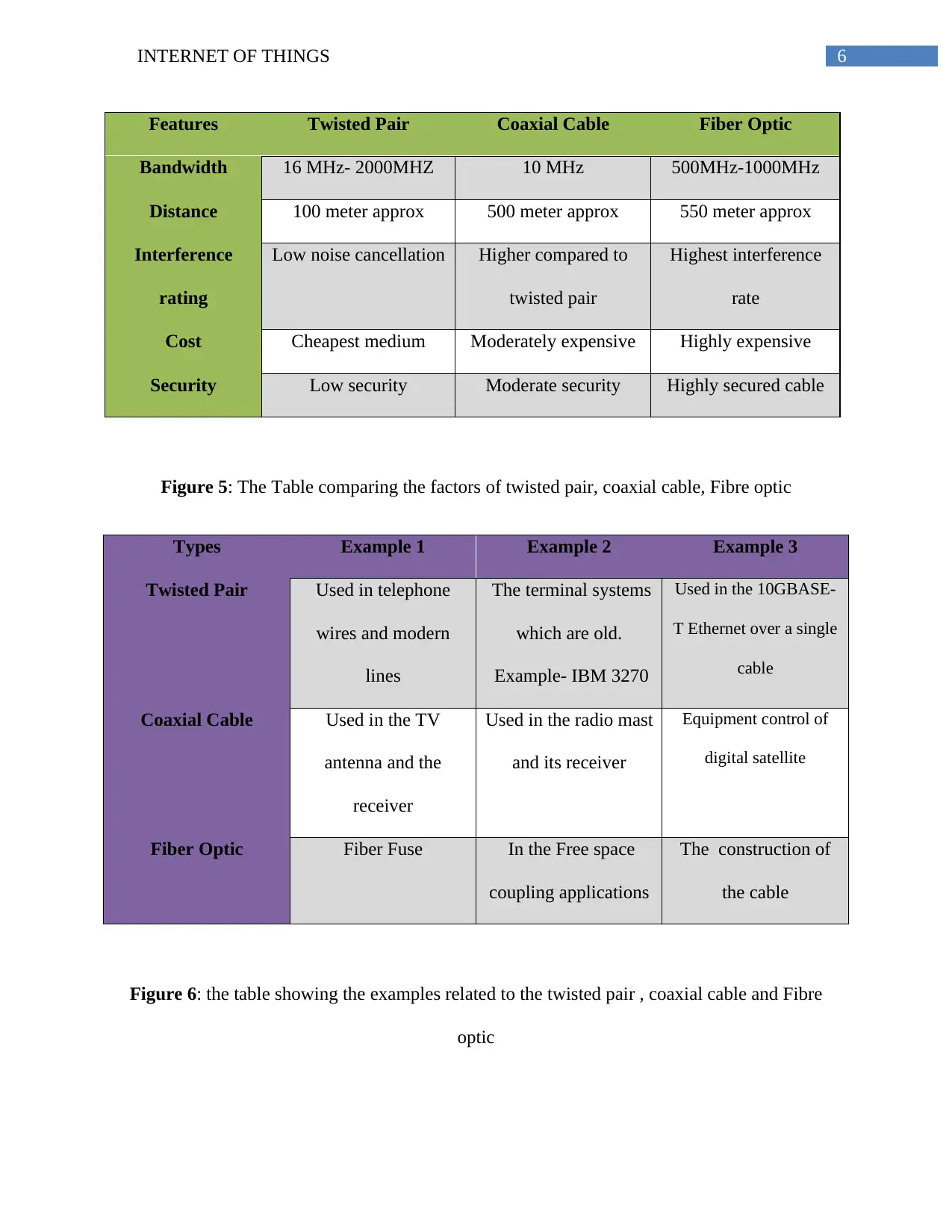
Solution:
The below table shows the comparisons twisted pair cable, coaxial cable and fiber optic cable
(Velandia et al 2016).
Figure 4: Parallax effect
(Source: Velandia et al 2016).
The difficult user interface as discussed above is destined by machines and much difficult to
operate and understand its function thus cannot be a human friendly whereas the easy user
interface is user friendly and easy to operate thus comes under the easy user interface.
Questions 2
Solution:
The below table shows the comparisons twisted pair cable, coaxial cable and fiber optic cable
(Velandia et al 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6INTERNET OF THINGS
Features Twisted Pair Coaxial Cable Fiber Optic
Bandwidth 16 MHz- 2000MHZ 10 MHz 500MHz-1000MHz
Distance 100 meter approx 500 meter approx 550 meter approx
Interference
rating
Low noise cancellation Higher compared to
twisted pair
Highest interference
rate
Cost Cheapest medium Moderately expensive Highly expensive
Security Low security Moderate security Highly secured cable
Figure 5: The Table comparing the factors of twisted pair, coaxial cable, Fibre optic
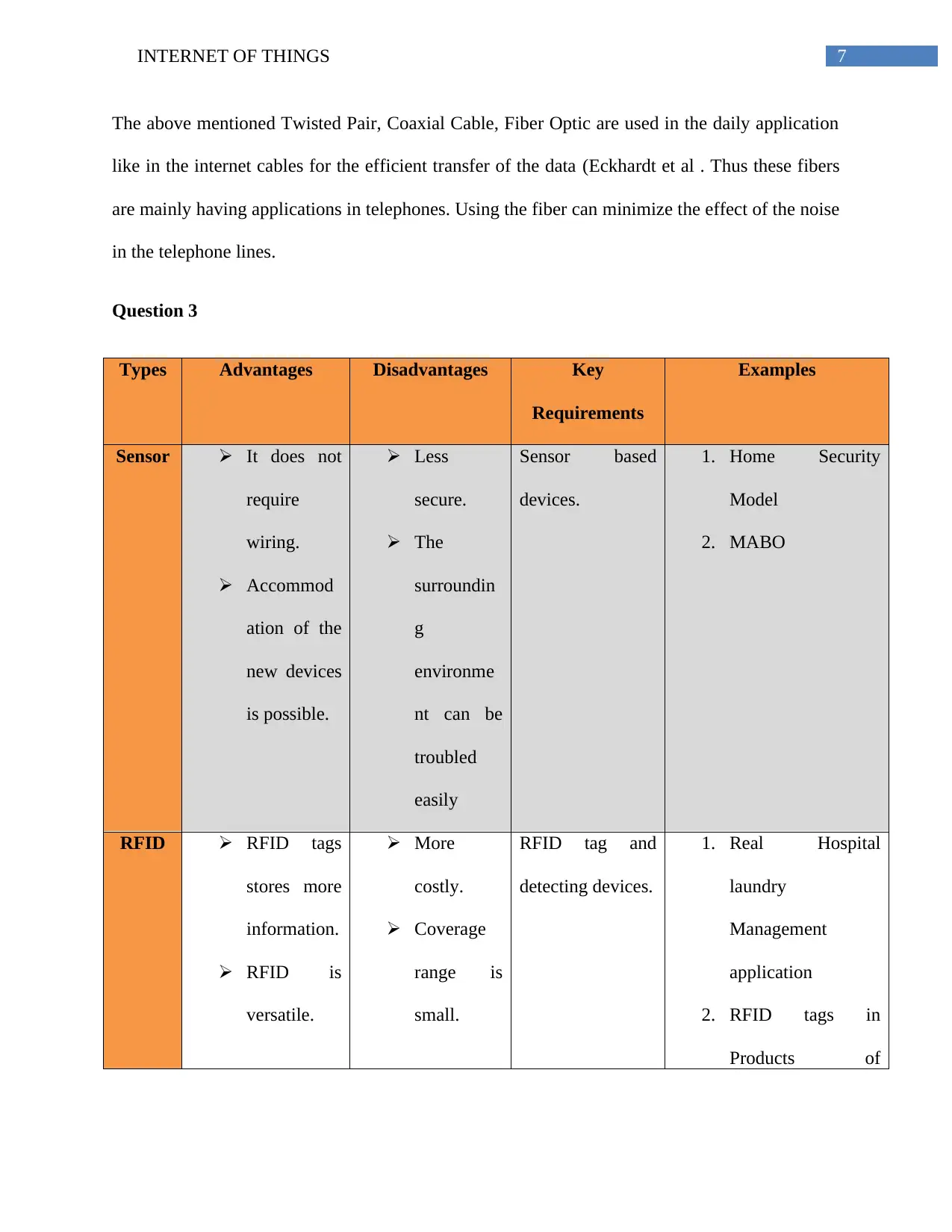
Types Example 1 Example 2 Example 3
Twisted Pair Used in telephone
wires and modern
lines
The terminal systems
which are old.
Example- IBM 3270
Used in the 10GBASE-
T Ethernet over a single
cable
Coaxial Cable Used in the TV
antenna and the
receiver
Used in the radio mast
and its receiver
Equipment control of
digital satellite
Fiber Optic Fiber Fuse In the Free space
coupling applications
The construction of
the cable
Figure 6: the table showing the examples related to the twisted pair , coaxial cable and Fibre
optic
Features Twisted Pair Coaxial Cable Fiber Optic
Bandwidth 16 MHz- 2000MHZ 10 MHz 500MHz-1000MHz
Distance 100 meter approx 500 meter approx 550 meter approx
Interference
rating
Low noise cancellation Higher compared to
twisted pair
Highest interference
rate
Cost Cheapest medium Moderately expensive Highly expensive
Security Low security Moderate security Highly secured cable
Figure 5: The Table comparing the factors of twisted pair, coaxial cable, Fibre optic
Types Example 1 Example 2 Example 3
Twisted Pair Used in telephone
wires and modern
lines
The terminal systems
which are old.
Example- IBM 3270
Used in the 10GBASE-
T Ethernet over a single
cable
Coaxial Cable Used in the TV
antenna and the
receiver
Used in the radio mast
and its receiver
Equipment control of
digital satellite
Fiber Optic Fiber Fuse In the Free space
coupling applications
The construction of
the cable
Figure 6: the table showing the examples related to the twisted pair , coaxial cable and Fibre
optic
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7INTERNET OF THINGS
The above mentioned Twisted Pair, Coaxial Cable, Fiber Optic are used in the daily application
like in the internet cables for the efficient transfer of the data (Eckhardt et al . Thus these fibers
are mainly having applications in telephones. Using the fiber can minimize the effect of the noise
in the telephone lines.
Question 3
Types Advantages Disadvantages Key
Requirements
Examples
Sensor It does not
require
wiring.
Accommod
ation of the
new devices
is possible.
Less
secure.
The
surroundin
g
environme
nt can be
troubled
easily
Sensor based
devices.
1. Home Security
Model
2. MABO
RFID RFID tags
stores more
information.
RFID is
versatile.
More
costly.
Coverage
range is
small.
RFID tag and
detecting devices.
1. Real Hospital
laundry
Management
application
2. RFID tags in
Products of
The above mentioned Twisted Pair, Coaxial Cable, Fiber Optic are used in the daily application
like in the internet cables for the efficient transfer of the data (Eckhardt et al . Thus these fibers
are mainly having applications in telephones. Using the fiber can minimize the effect of the noise
in the telephone lines.
Question 3
Types Advantages Disadvantages Key
Requirements
Examples
Sensor It does not
require
wiring.
Accommod
ation of the
new devices
is possible.
Less
secure.
The
surroundin
g
environme
nt can be
troubled
easily
Sensor based
devices.
1. Home Security
Model
2. MABO
RFID RFID tags
stores more
information.
RFID is
versatile.
More
costly.
Coverage
range is
small.
RFID tag and
detecting devices.
1. Real Hospital
laundry
Management
application
2. RFID tags in
Products of
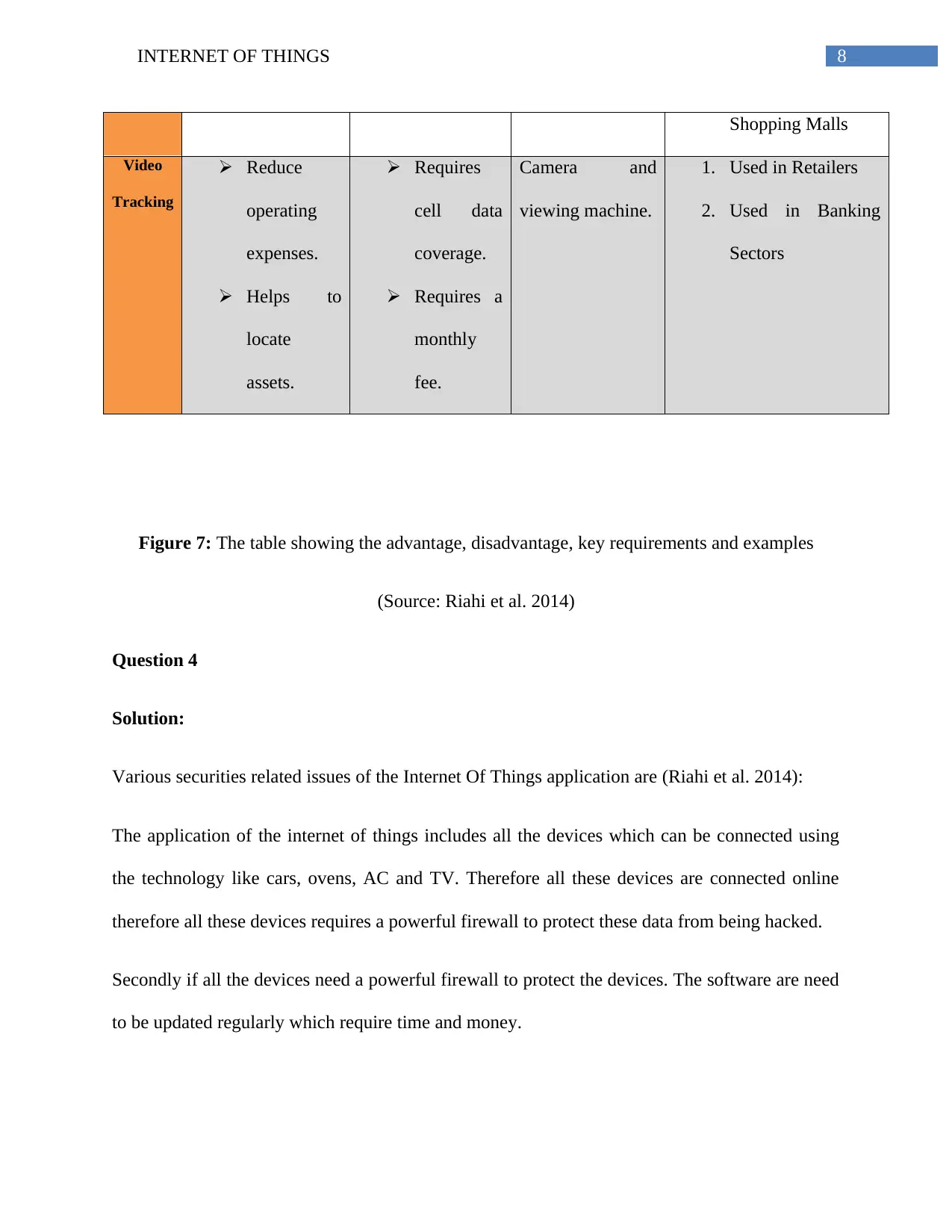
8INTERNET OF THINGS
Shopping Malls
Video
Tracking
Reduce
operating
expenses.
Helps to
locate
assets.
Requires
cell data
coverage.
Requires a
monthly
fee.
Camera and
viewing machine.
1. Used in Retailers
2. Used in Banking
Sectors
Figure 7: The table showing the advantage, disadvantage, key requirements and examples
(Source: Riahi et al. 2014)
Question 4
Solution:
Various securities related issues of the Internet Of Things application are (Riahi et al. 2014):
The application of the internet of things includes all the devices which can be connected using
the technology like cars, ovens, AC and TV. Therefore all these devices are connected online
therefore all these devices requires a powerful firewall to protect these data from being hacked.
Secondly if all the devices need a powerful firewall to protect the devices. The software are need
to be updated regularly which require time and money.
Shopping Malls
Video
Tracking
Reduce
operating
expenses.
Helps to
locate
assets.
Requires
cell data
coverage.
Requires a
monthly
fee.
Camera and
viewing machine.
1. Used in Retailers
2. Used in Banking
Sectors
Figure 7: The table showing the advantage, disadvantage, key requirements and examples
(Source: Riahi et al. 2014)
Question 4
Solution:
Various securities related issues of the Internet Of Things application are (Riahi et al. 2014):
The application of the internet of things includes all the devices which can be connected using
the technology like cars, ovens, AC and TV. Therefore all these devices are connected online
therefore all these devices requires a powerful firewall to protect these data from being hacked.
Secondly if all the devices need a powerful firewall to protect the devices. The software are need
to be updated regularly which require time and money.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INTERNET OF THINGS
Thirdly not only the hackers but also the organization are using the private and confidential of
the customer for its use.
Lastly many companies are still not ready to adapt the technology of the IOT over 85 percent of
the company admits that they are still undergoing the for the development of the IOT.
There are privacy issues which are related to the internet of things:
Data oriented privacy: privacy related to the control of the data system (Rayes & Salam,2017).
Context oriented privacy: The Contextual information privacy is those which provide timing and
location that are transmitted over the signals (Cui, 2016).
Question 5
Solution:
Given:
Given triggering time: 1s
The Round trip propagation delay between sensor and application: 12ms
Time for processing each request: 3ms
To send or receive any message: 2ms
Therefore the total time taken by the application is: 1ms + 12ms + 3ms + 2ms = 18ms
The budget of time that is saved is 18ms. The application that is designed will be more efficient
that the model that is present.
Thirdly not only the hackers but also the organization are using the private and confidential of
the customer for its use.
Lastly many companies are still not ready to adapt the technology of the IOT over 85 percent of
the company admits that they are still undergoing the for the development of the IOT.
There are privacy issues which are related to the internet of things:
Data oriented privacy: privacy related to the control of the data system (Rayes & Salam,2017).
Context oriented privacy: The Contextual information privacy is those which provide timing and
location that are transmitted over the signals (Cui, 2016).
Question 5
Solution:
Given:
Given triggering time: 1s
The Round trip propagation delay between sensor and application: 12ms
Time for processing each request: 3ms
To send or receive any message: 2ms
Therefore the total time taken by the application is: 1ms + 12ms + 3ms + 2ms = 18ms
The budget of time that is saved is 18ms. The application that is designed will be more efficient
that the model that is present.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10INTERNET OF THINGS
Question 6:
Solution:
Nielson's Law states that the bandwidth which is available for the connections of high end
broadband, it will increase by half of its available bandwidth each year, which can lead to
compound growth of 57 xs in capacity in ten years (Eckhart et al., 2015). The model’s strength is
shown in the fact that is true for more than 15 years.
Moore Law is the reliable law and controls the working speed of microprocessors, and decreases
the cost of the storage and the number of megapixel that a phone’s camera can load (Shack,
2017). The inexpensive transistors that can be placed in a microchip become doubles in 18
months.
Comparison: The Nielsen stated that that connection of high end broadband will increase by 50%
every year whereas Moore stated that it doubles itself in every 18 months. The law stated by
Jacob Nielsen is 10% less than Moore’s Law.
Question 6:
Solution:
Nielson's Law states that the bandwidth which is available for the connections of high end
broadband, it will increase by half of its available bandwidth each year, which can lead to
compound growth of 57 xs in capacity in ten years (Eckhart et al., 2015). The model’s strength is
shown in the fact that is true for more than 15 years.
Moore Law is the reliable law and controls the working speed of microprocessors, and decreases
the cost of the storage and the number of megapixel that a phone’s camera can load (Shack,
2017). The inexpensive transistors that can be placed in a microchip become doubles in 18
months.
Comparison: The Nielsen stated that that connection of high end broadband will increase by 50%
every year whereas Moore stated that it doubles itself in every 18 months. The law stated by
Jacob Nielsen is 10% less than Moore’s Law.

11INTERNET OF THINGS
References
Riahi, A., Natalizio, E., Challal, Y., Mitton, N., & Iera, A. (2014, February). A systemic and
cognitive approach for IoT security. In Computing, Networking and Communications
(ICNC), 2014 International Conference on (pp. 183-188). IEEE.Data privacy for IoT
systems: concepts, approaches, and research directions. In Big Data (Big Data), 2016
IEEE International Conference on (pp. 3645-3647). IEEE.
Eckhardt, S., Quennehen, B., Oliviè, D. J. L., Berntsen, T. K., Cherian, R., Christensen, J. H., ...
& Herber, A. (2015). Current model capabilities for simulating black carbon and sulfate
concentrations in the Arctic atmosphere: a multi-model evaluation using a comprehensive
measurement data set. Atmospheric Chemistry and Physics, 15(16), 9413-9433.
Hecht, J. (2015). Understanding fiber optics. Jeff Hecht.
Miguelez, P., Esser, S. M., & Slowik, F. (2015). U.S. Patent No. 8,958,694. Washington, DC:
U.S. Patent and Trademark Office.
Rayes, A., & Salam, S. (2017). Internet of Things (IoT) Overview. In Internet of Things From
Hype to Reality (pp. 1-34). Springer International Publishing.
Shack. (2017). Designshack.net. Retrieved 26 August 2017, from
https://designshack.net/articles/graphics/15-in-depth-examples-of-addictive-user-
experience/
References
Riahi, A., Natalizio, E., Challal, Y., Mitton, N., & Iera, A. (2014, February). A systemic and
cognitive approach for IoT security. In Computing, Networking and Communications
(ICNC), 2014 International Conference on (pp. 183-188). IEEE.Data privacy for IoT
systems: concepts, approaches, and research directions. In Big Data (Big Data), 2016
IEEE International Conference on (pp. 3645-3647). IEEE.
Eckhardt, S., Quennehen, B., Oliviè, D. J. L., Berntsen, T. K., Cherian, R., Christensen, J. H., ...
& Herber, A. (2015). Current model capabilities for simulating black carbon and sulfate
concentrations in the Arctic atmosphere: a multi-model evaluation using a comprehensive
measurement data set. Atmospheric Chemistry and Physics, 15(16), 9413-9433.
Hecht, J. (2015). Understanding fiber optics. Jeff Hecht.
Miguelez, P., Esser, S. M., & Slowik, F. (2015). U.S. Patent No. 8,958,694. Washington, DC:
U.S. Patent and Trademark Office.
Rayes, A., & Salam, S. (2017). Internet of Things (IoT) Overview. In Internet of Things From
Hype to Reality (pp. 1-34). Springer International Publishing.
Shack. (2017). Designshack.net. Retrieved 26 August 2017, from
https://designshack.net/articles/graphics/15-in-depth-examples-of-addictive-user-
experience/
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





