Network Analyzer Report: University Network Security Tools
VerifiedAdded on 2021/06/14
|23
|1414
|31
Report
AI Summary
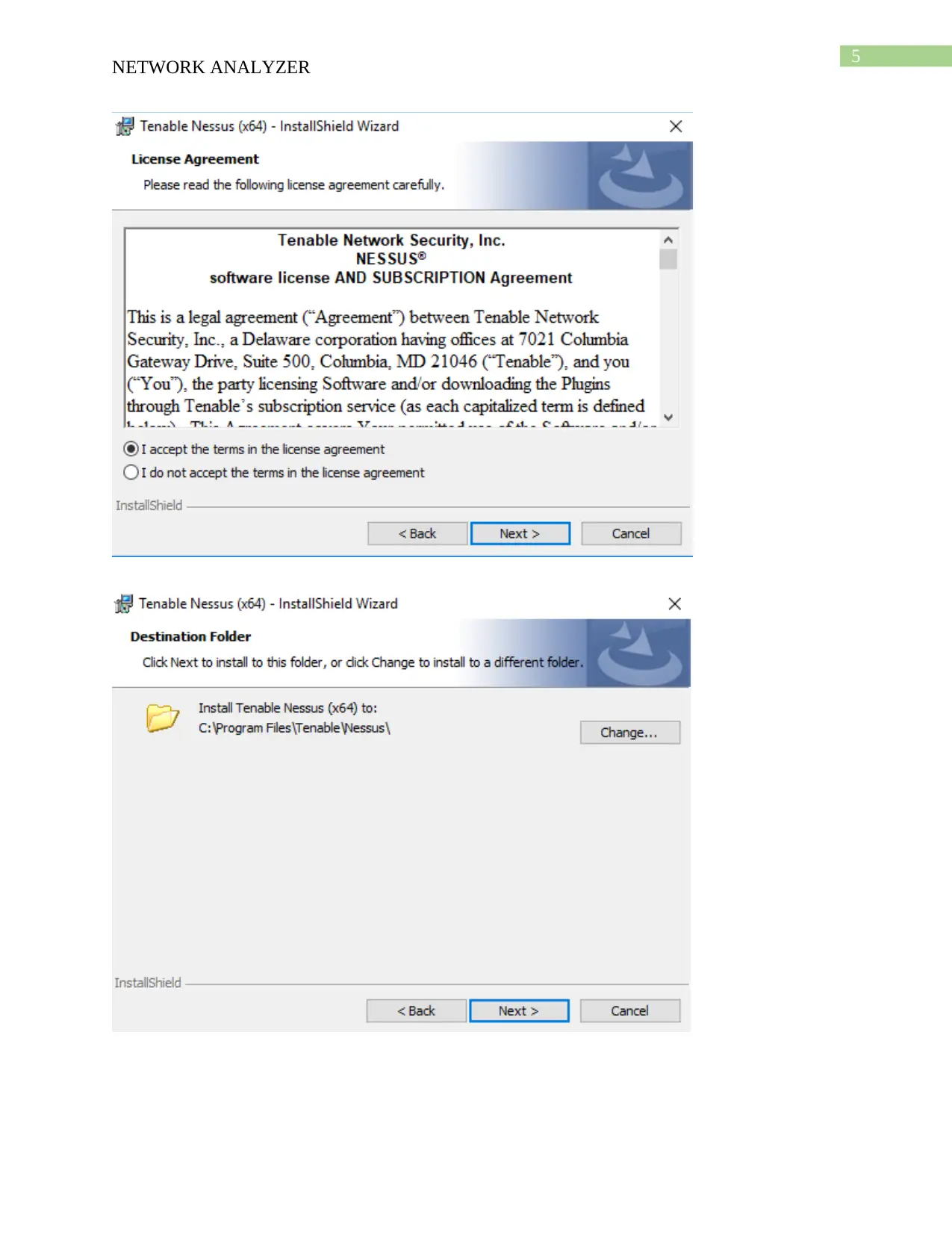
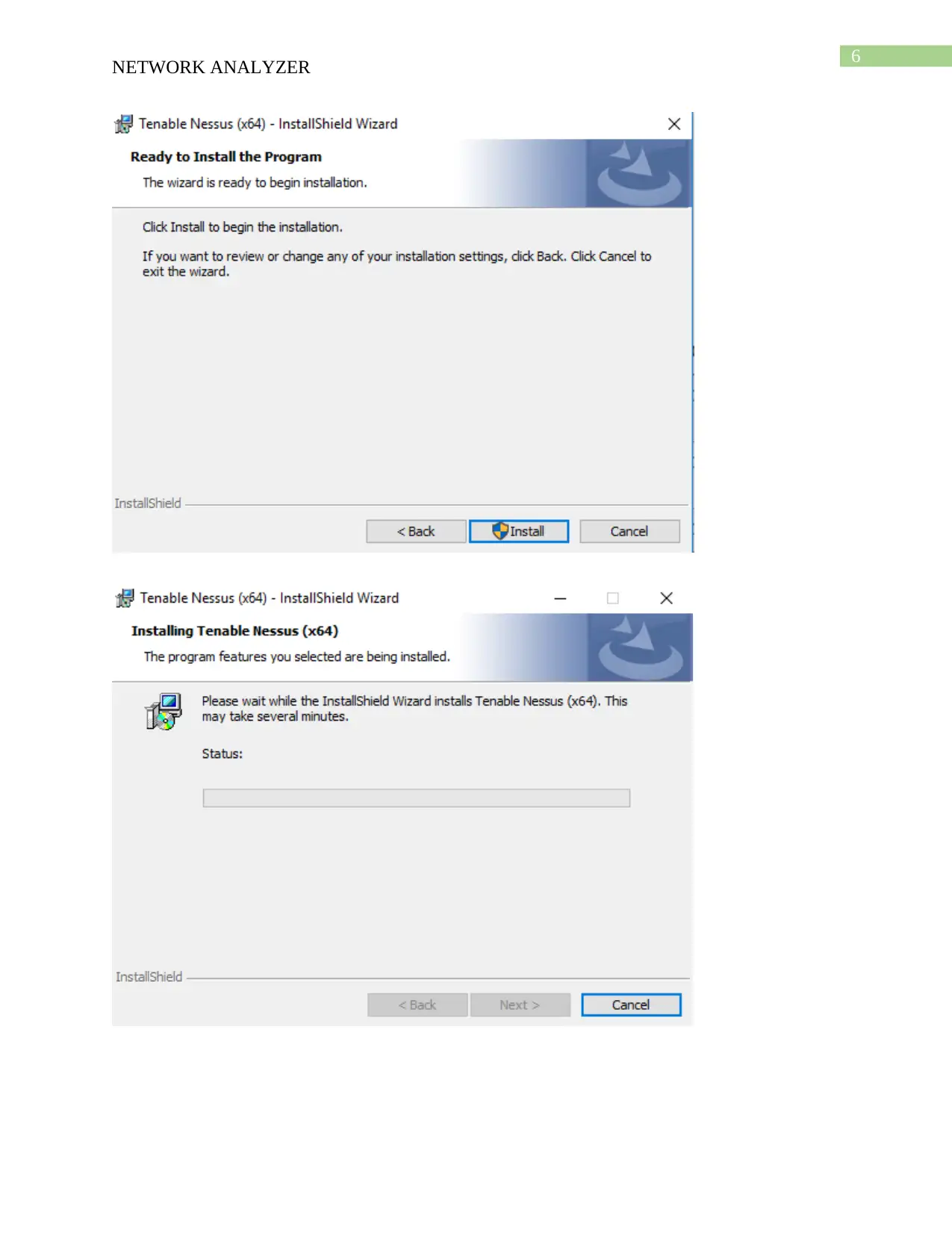
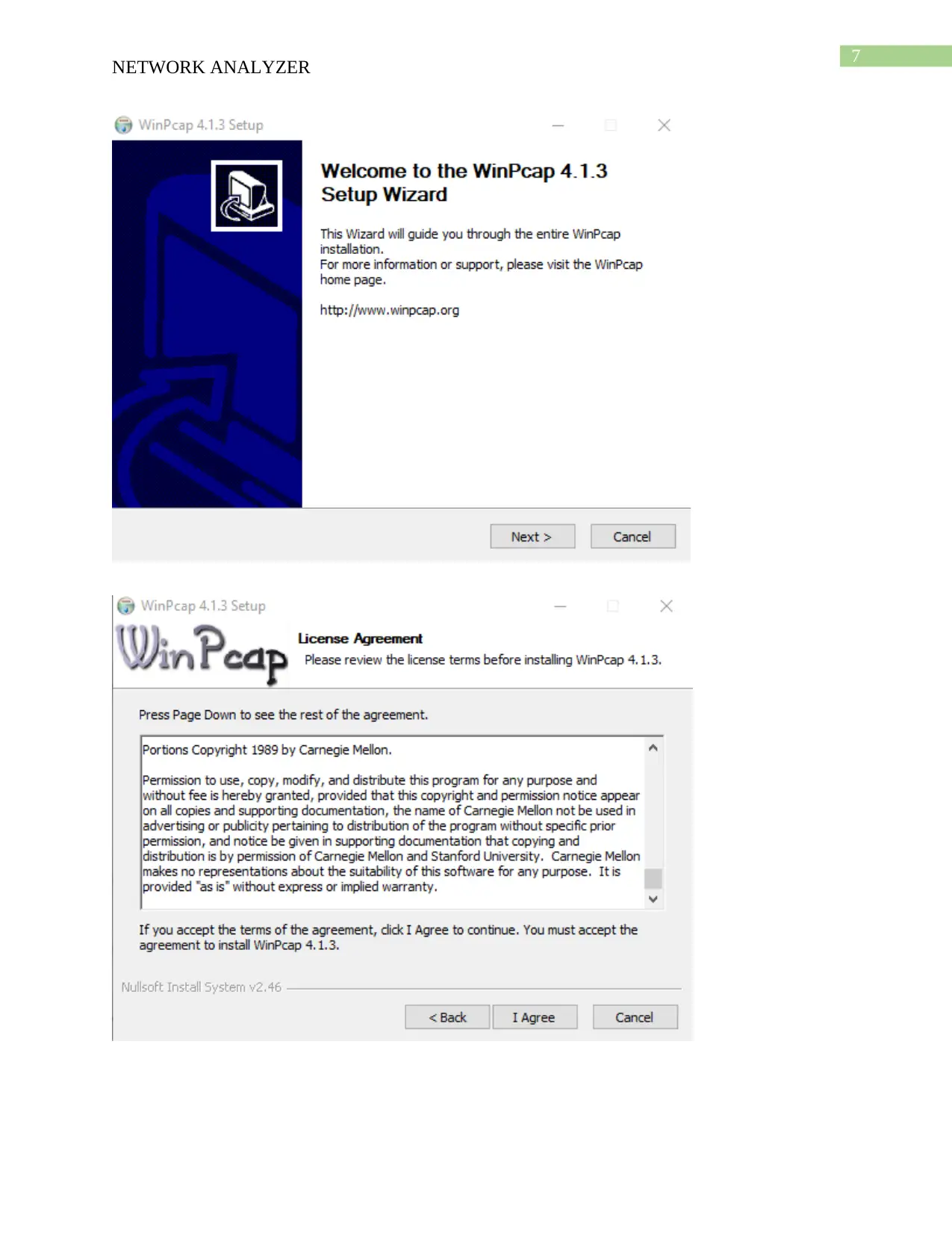
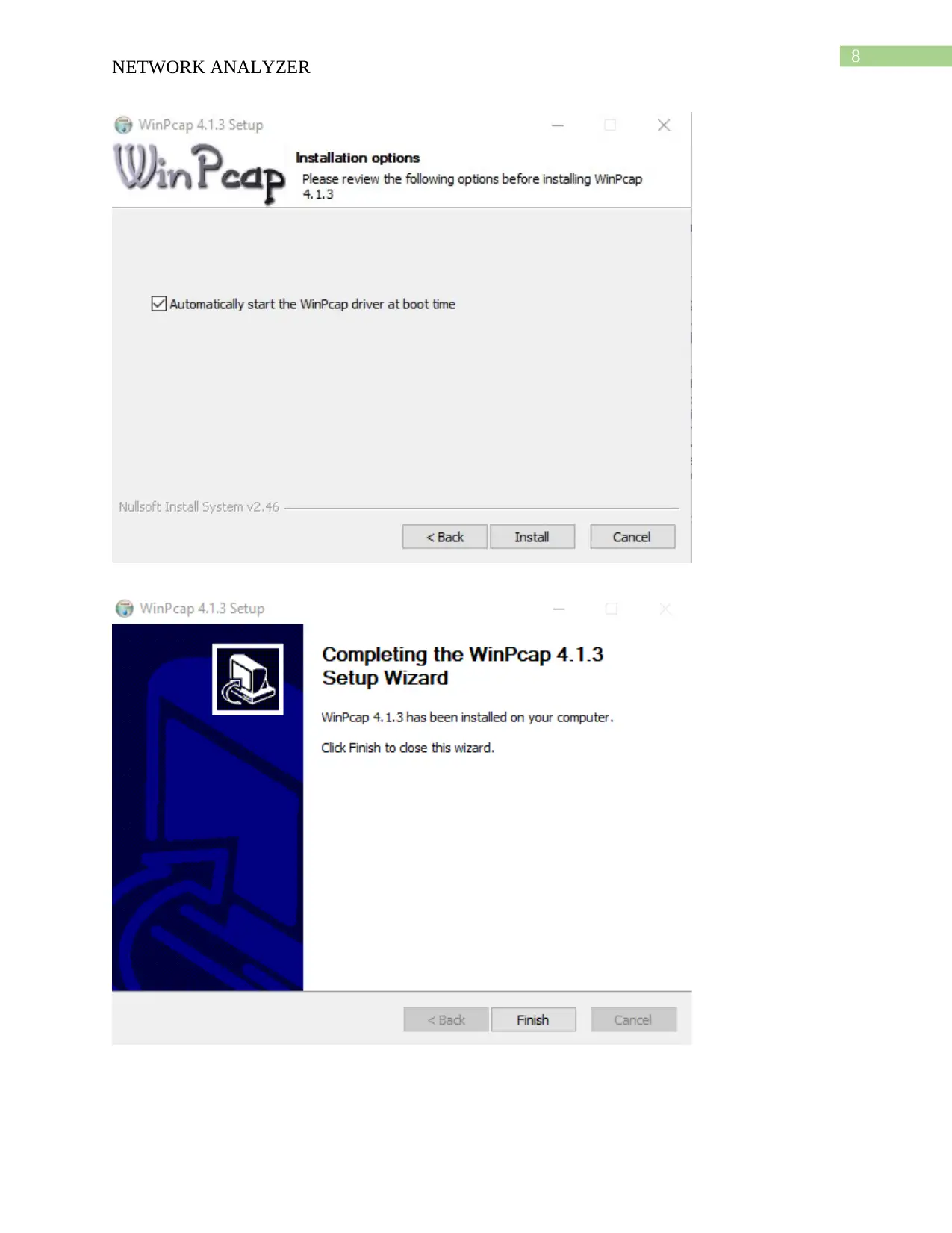
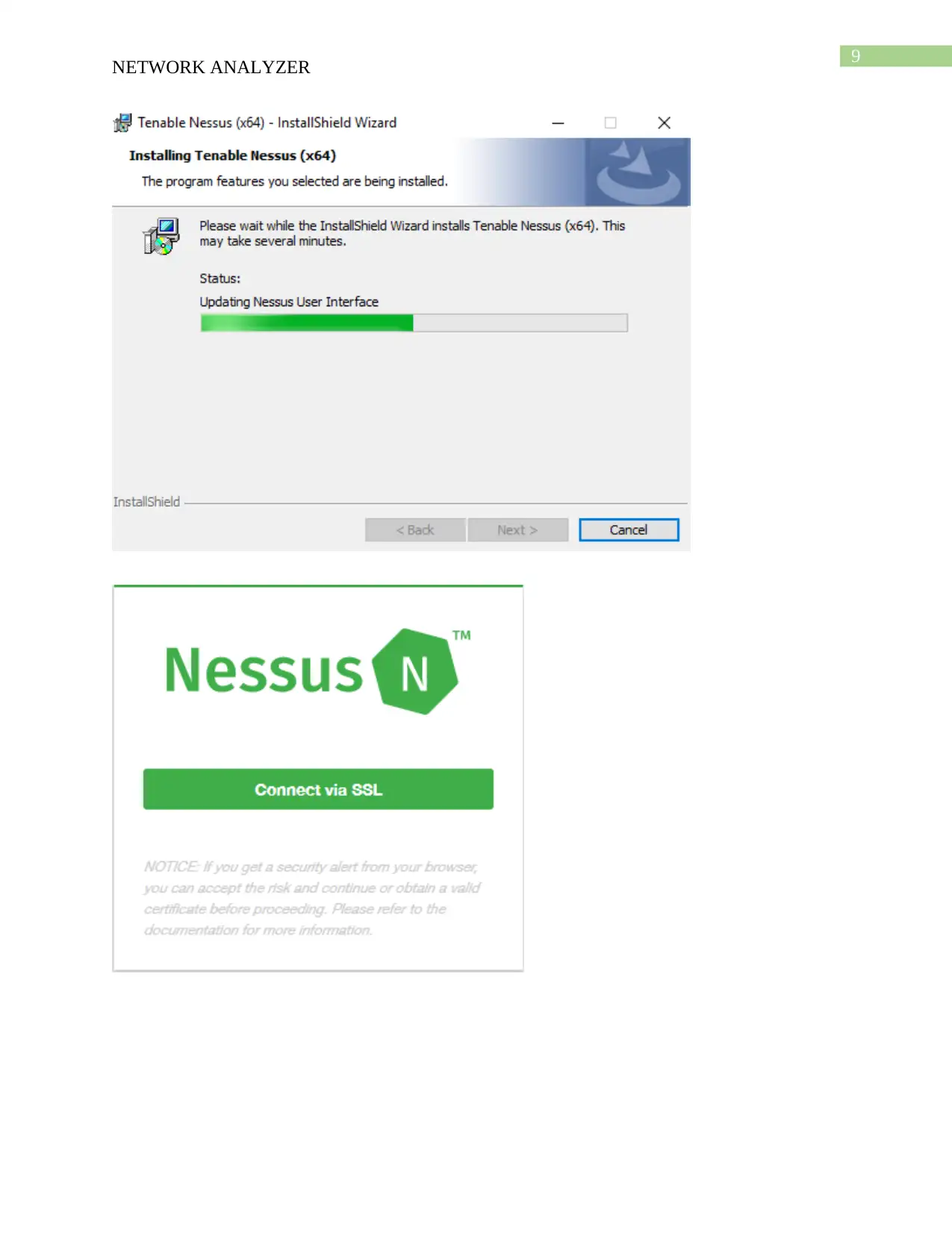
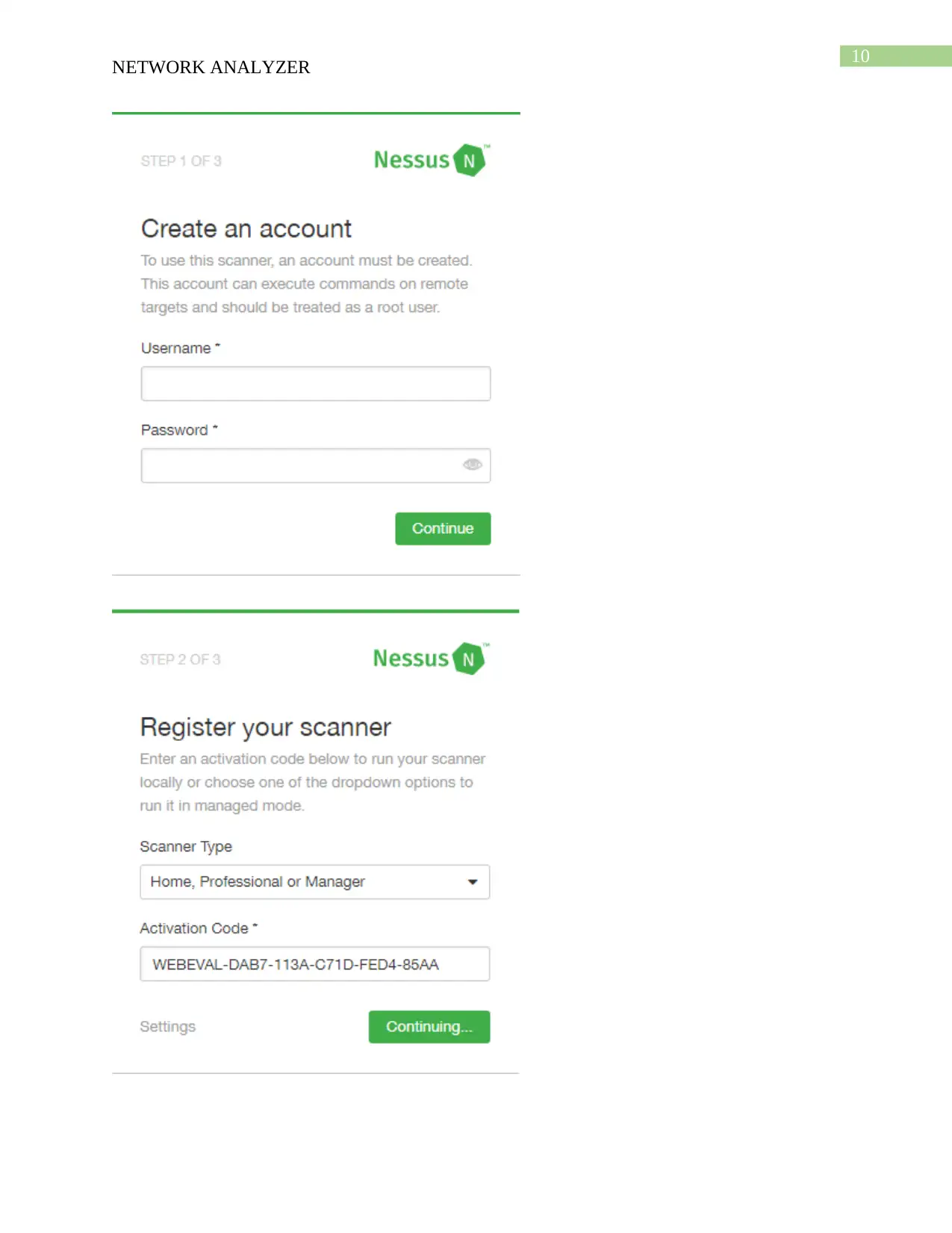
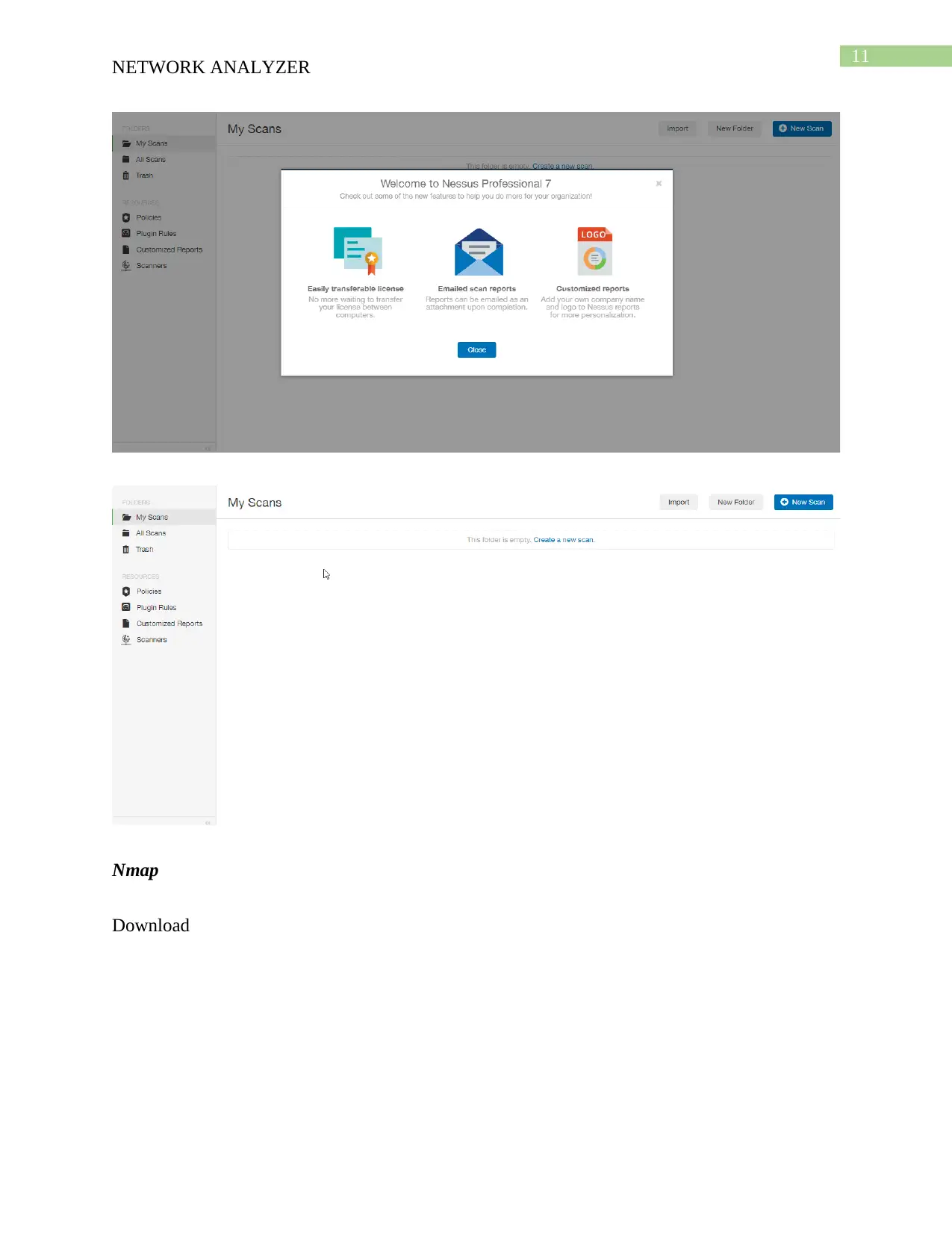
This report provides an overview of network security tools, focusing on Nessus and Nmap. It details the download and installation processes for both tools, followed by descriptions of their functionalities. Nessus is presented as a vulnerability scanner, utilizing tools like Nikto and Hydra, while Nmap is described as a network mapper, using tools like Nping, Ndiff, and Ncat. The report compares the two tools, highlighting Nessus's role in detecting vulnerabilities and Nmap's function in mapping network locations. An analysis of a scenario involving misuse of a classroom network is also included, discussing potential security threats and recommending solutions such as blocking inappropriate sites and installing firewalls. The report concludes with a bibliography of relevant sources.
1 out of 23








![[object Object]](/_next/static/media/star-bottom.7253800d.svg)