Information Security Risk Assessment Plan for IT Infrastructure
VerifiedAdded on 2023/04/23
|7
|1064
|150
Report
AI Summary
This report presents a risk assessment plan developed for ISOL 533 at the University of the Cumberlands. It includes an executive summary outlining the risk management process, which begins with identifying risks, vulnerabilities, and threats, followed by their assessment based on likelihood and impact. The report details risks, threats, and weaknesses within different domains, such as remote access, LAN to WAN, user, system/application, and workstation, along with their corresponding impact factors. It also covers compliance with laws and regulations relevant to business operations, taxation policies, and employee-employer relationships. The document concludes with references to support the risk assessment methodologies and information security management practices discussed. This resource is available on Desklib, offering students access to a wealth of study materials and solved assignments.
ISOL 533 - Information Security and Risk Management RISK ASSESSMENT
PLAN
University of the Cumberlands
EXECUTIVE SUMMARY
The aspect of the risk management initiates with the identification of the risks,
vulnerabilities and the threats and then perform the assessment of them. The assessment of
the risk denotes to the evaluation of the risk in the term of two factors, which are the
evaluation of the each of the likelihood of occurring any situation, and second factor is
connected to the evaluation of the consequences or impacts of the risk on any organisation.
Both these factors are essential for understanding how the risk measures deals with the risks.
RISKS – THREATS – WEAKNESSES WITHIN EACH
DOMAIN
Table 1
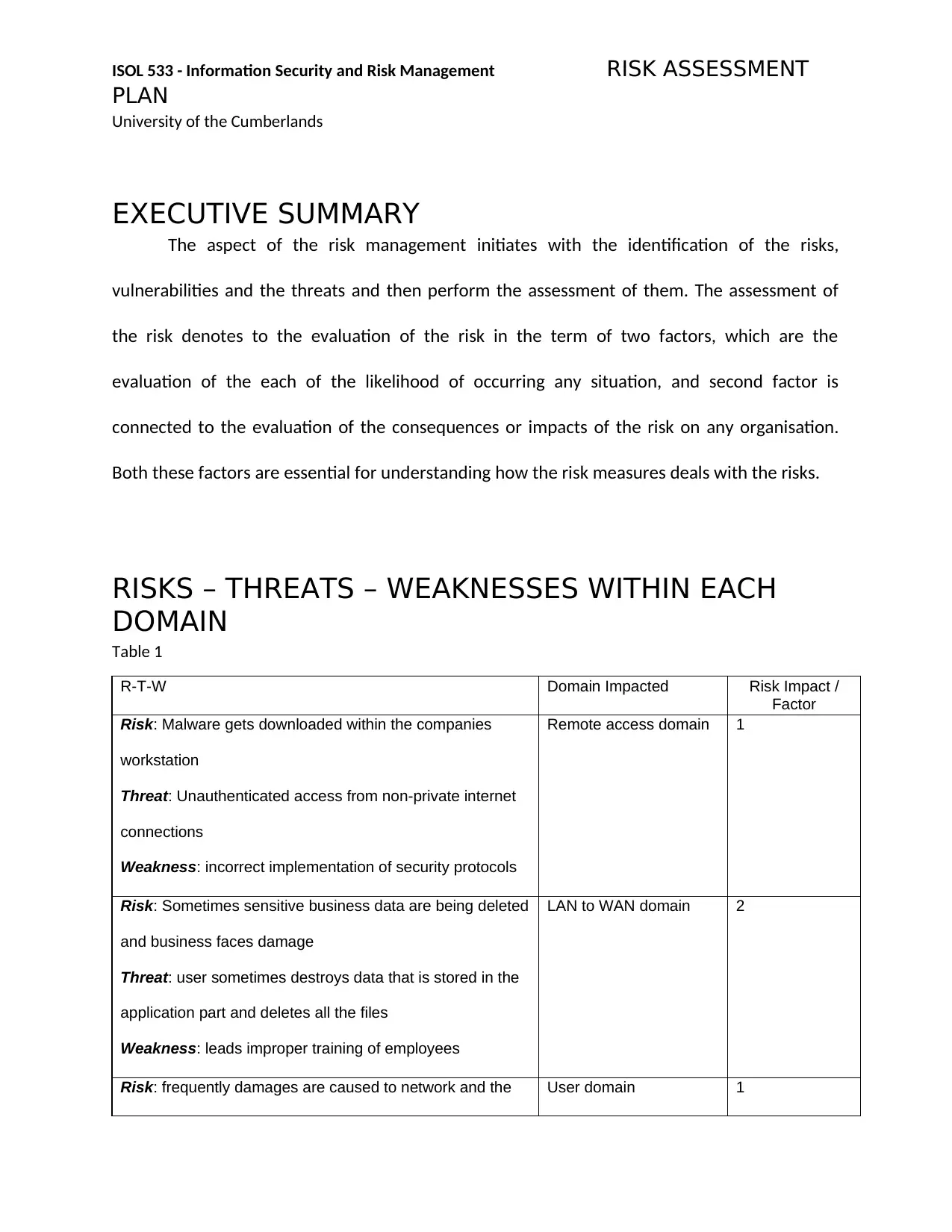
R-T-W Domain Impacted Risk Impact /
Factor
Risk: Malware gets downloaded within the companies
workstation
Threat: Unauthenticated access from non-private internet
connections
Weakness: incorrect implementation of security protocols
Remote access domain 1
Risk: Sometimes sensitive business data are being deleted
and business faces damage
Threat: user sometimes destroys data that is stored in the
application part and deletes all the files
Weakness: leads improper training of employees
LAN to WAN domain 2
Risk: frequently damages are caused to network and the User domain 1
PLAN
University of the Cumberlands
EXECUTIVE SUMMARY
The aspect of the risk management initiates with the identification of the risks,
vulnerabilities and the threats and then perform the assessment of them. The assessment of
the risk denotes to the evaluation of the risk in the term of two factors, which are the
evaluation of the each of the likelihood of occurring any situation, and second factor is
connected to the evaluation of the consequences or impacts of the risk on any organisation.
Both these factors are essential for understanding how the risk measures deals with the risks.
RISKS – THREATS – WEAKNESSES WITHIN EACH
DOMAIN
Table 1
R-T-W Domain Impacted Risk Impact /
Factor
Risk: Malware gets downloaded within the companies
workstation
Threat: Unauthenticated access from non-private internet
connections
Weakness: incorrect implementation of security protocols
Remote access domain 1
Risk: Sometimes sensitive business data are being deleted
and business faces damage
Threat: user sometimes destroys data that is stored in the
application part and deletes all the files
Weakness: leads improper training of employees
LAN to WAN domain 2
Risk: frequently damages are caused to network and the User domain 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
ISOL 533 - Information Security and Risk Management RISK ASSESSMENT
PLAN
University of the Cumberlands
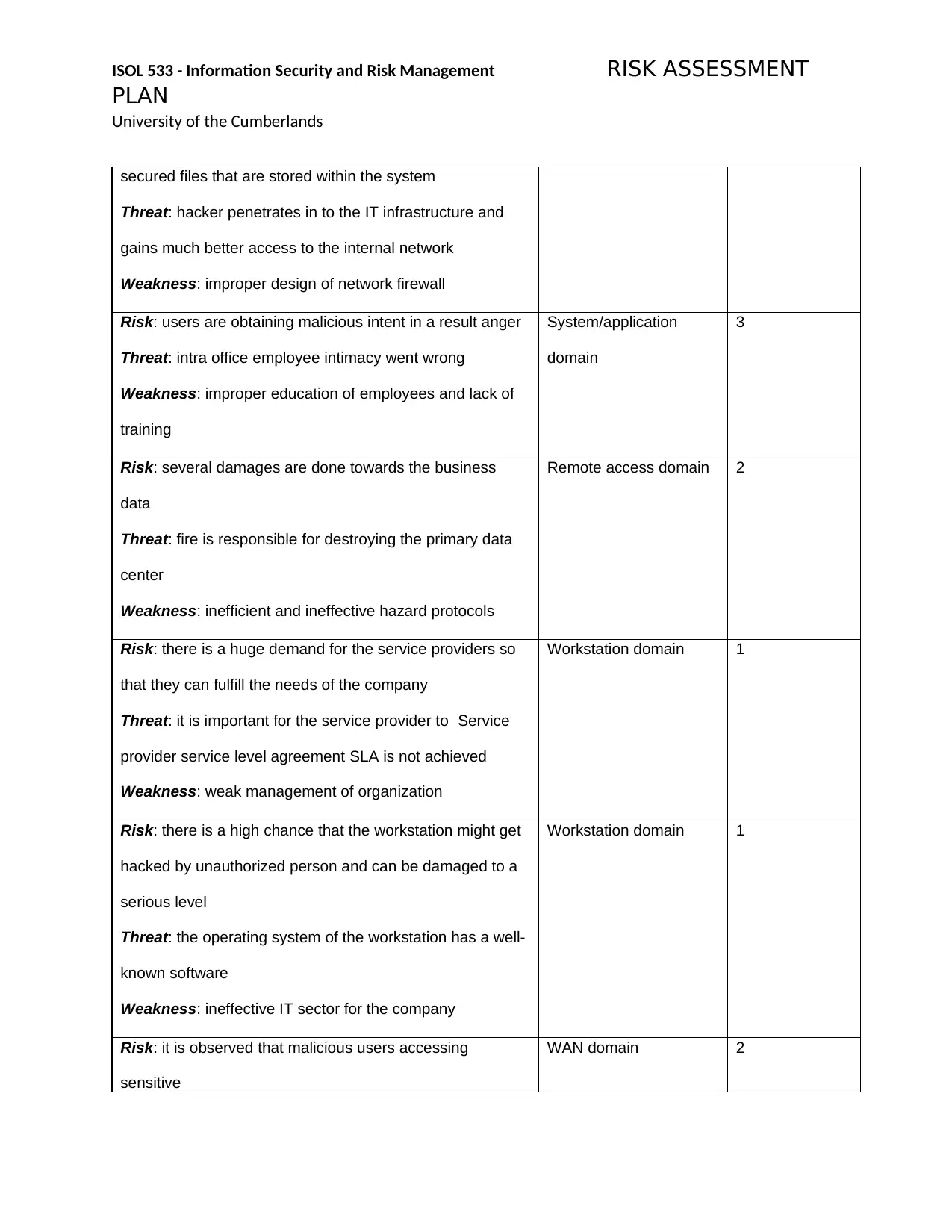
secured files that are stored within the system
Threat: hacker penetrates in to the IT infrastructure and
gains much better access to the internal network
Weakness: improper design of network firewall
Risk: users are obtaining malicious intent in a result anger
Threat: intra office employee intimacy went wrong
Weakness: improper education of employees and lack of
training
System/application
domain
3
Risk: several damages are done towards the business
data
Threat: fire is responsible for destroying the primary data
center
Weakness: inefficient and ineffective hazard protocols
Remote access domain 2
Risk: there is a huge demand for the service providers so
that they can fulfill the needs of the company
Threat: it is important for the service provider to Service
provider service level agreement SLA is not achieved
Weakness: weak management of organization
Workstation domain 1
Risk: there is a high chance that the workstation might get
hacked by unauthorized person and can be damaged to a
serious level
Threat: the operating system of the workstation has a well-
known software
Weakness: ineffective IT sector for the company
Workstation domain 1
Risk: it is observed that malicious users accessing
sensitive
WAN domain 2
PLAN
University of the Cumberlands
secured files that are stored within the system
Threat: hacker penetrates in to the IT infrastructure and
gains much better access to the internal network
Weakness: improper design of network firewall
Risk: users are obtaining malicious intent in a result anger
Threat: intra office employee intimacy went wrong
Weakness: improper education of employees and lack of
training
System/application
domain
3
Risk: several damages are done towards the business
data
Threat: fire is responsible for destroying the primary data
center
Weakness: inefficient and ineffective hazard protocols
Remote access domain 2
Risk: there is a huge demand for the service providers so
that they can fulfill the needs of the company
Threat: it is important for the service provider to Service
provider service level agreement SLA is not achieved
Weakness: weak management of organization
Workstation domain 1
Risk: there is a high chance that the workstation might get
hacked by unauthorized person and can be damaged to a
serious level
Threat: the operating system of the workstation has a well-
known software
Weakness: ineffective IT sector for the company
Workstation domain 1
Risk: it is observed that malicious users accessing
sensitive
WAN domain 2
ISOL 533 - Information Security and Risk Management RISK ASSESSMENT
PLAN
University of the Cumberlands
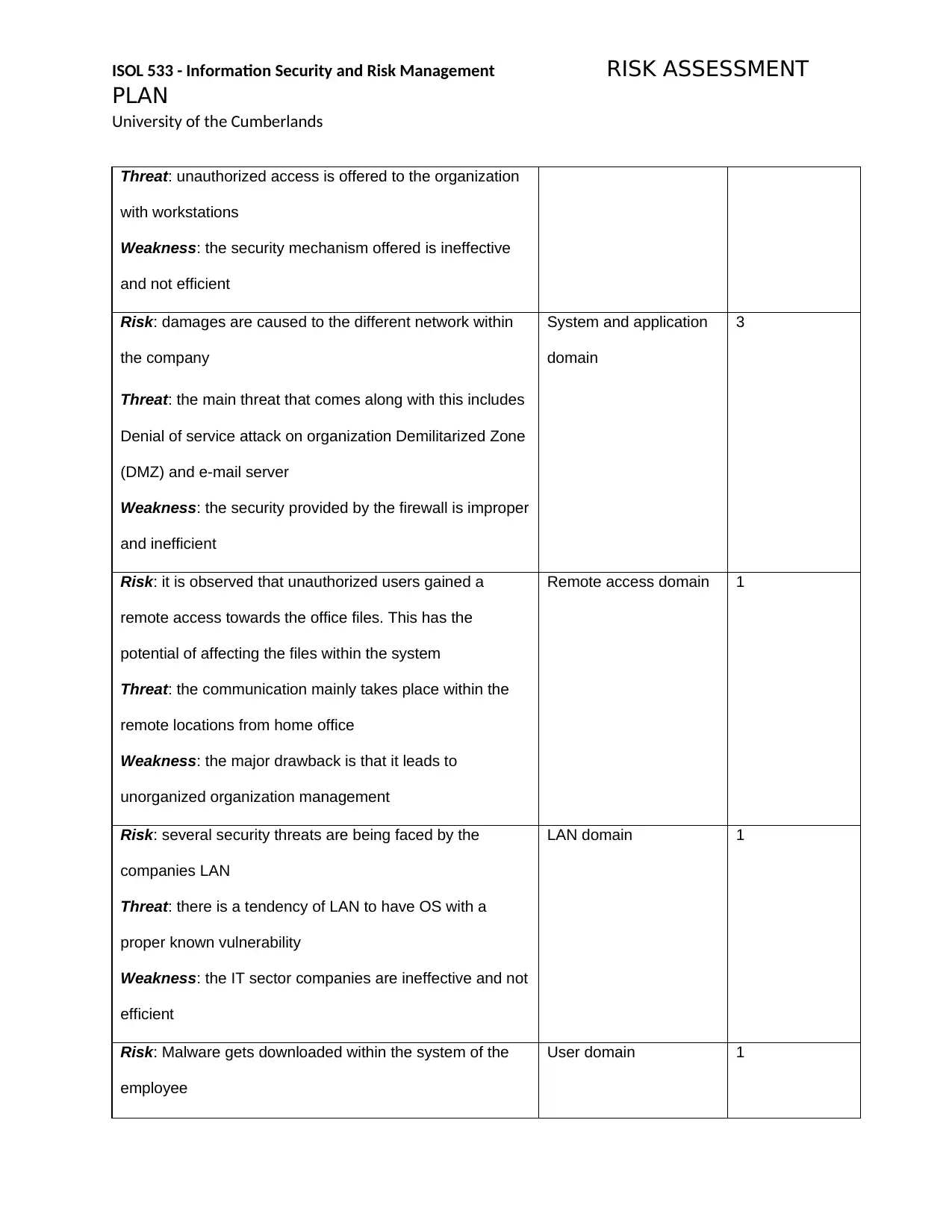
Threat: unauthorized access is offered to the organization
with workstations
Weakness: the security mechanism offered is ineffective
and not efficient
Risk: damages are caused to the different network within
the company
Threat: the main threat that comes along with this includes
Denial of service attack on organization Demilitarized Zone
(DMZ) and e-mail server
Weakness: the security provided by the firewall is improper
and inefficient
System and application
domain
3
Risk: it is observed that unauthorized users gained a
remote access towards the office files. This has the
potential of affecting the files within the system
Threat: the communication mainly takes place within the
remote locations from home office
Weakness: the major drawback is that it leads to
unorganized organization management
Remote access domain 1
Risk: several security threats are being faced by the
companies LAN
Threat: there is a tendency of LAN to have OS with a
proper known vulnerability
Weakness: the IT sector companies are ineffective and not
efficient
LAN domain 1
Risk: Malware gets downloaded within the system of the
employee
User domain 1
PLAN
University of the Cumberlands
Threat: unauthorized access is offered to the organization
with workstations
Weakness: the security mechanism offered is ineffective
and not efficient
Risk: damages are caused to the different network within
the company
Threat: the main threat that comes along with this includes
Denial of service attack on organization Demilitarized Zone
(DMZ) and e-mail server
Weakness: the security provided by the firewall is improper
and inefficient
System and application
domain
3
Risk: it is observed that unauthorized users gained a
remote access towards the office files. This has the
potential of affecting the files within the system
Threat: the communication mainly takes place within the
remote locations from home office
Weakness: the major drawback is that it leads to
unorganized organization management
Remote access domain 1
Risk: several security threats are being faced by the
companies LAN
Threat: there is a tendency of LAN to have OS with a
proper known vulnerability
Weakness: the IT sector companies are ineffective and not
efficient
LAN domain 1
Risk: Malware gets downloaded within the system of the
employee
User domain 1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
ISOL 533 - Information Security and Risk Management RISK ASSESSMENT
PLAN
University of the Cumberlands
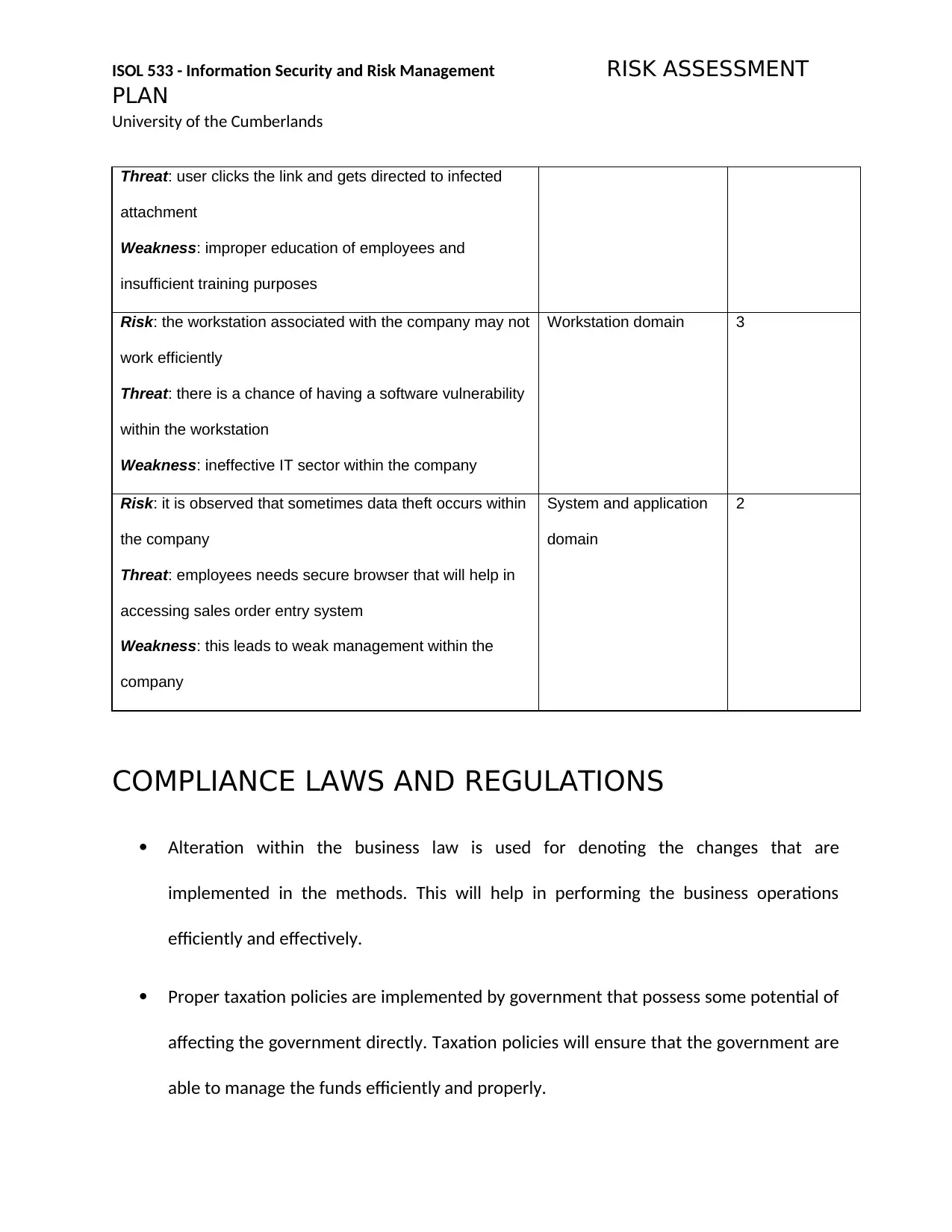
Threat: user clicks the link and gets directed to infected
attachment
Weakness: improper education of employees and
insufficient training purposes
Risk: the workstation associated with the company may not
work efficiently
Threat: there is a chance of having a software vulnerability
within the workstation
Weakness: ineffective IT sector within the company
Workstation domain 3
Risk: it is observed that sometimes data theft occurs within
the company
Threat: employees needs secure browser that will help in
accessing sales order entry system
Weakness: this leads to weak management within the
company
System and application
domain
2
COMPLIANCE LAWS AND REGULATIONS
Alteration within the business law is used for denoting the changes that are
implemented in the methods. This will help in performing the business operations
efficiently and effectively.
Proper taxation policies are implemented by government that possess some potential of
affecting the government directly. Taxation policies will ensure that the government are
able to manage the funds efficiently and properly.
PLAN
University of the Cumberlands
Threat: user clicks the link and gets directed to infected
attachment
Weakness: improper education of employees and
insufficient training purposes
Risk: the workstation associated with the company may not
work efficiently
Threat: there is a chance of having a software vulnerability
within the workstation
Weakness: ineffective IT sector within the company
Workstation domain 3
Risk: it is observed that sometimes data theft occurs within
the company
Threat: employees needs secure browser that will help in
accessing sales order entry system
Weakness: this leads to weak management within the
company
System and application
domain
2
COMPLIANCE LAWS AND REGULATIONS
Alteration within the business law is used for denoting the changes that are
implemented in the methods. This will help in performing the business operations
efficiently and effectively.
Proper taxation policies are implemented by government that possess some potential of
affecting the government directly. Taxation policies will ensure that the government are
able to manage the funds efficiently and properly.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ISOL 533 - Information Security and Risk Management RISK ASSESSMENT
PLAN
University of the Cumberlands
There are several laws associated with particular business that possess the ability to
affect relationships that is maintained between the employee and employer.
PLAN
University of the Cumberlands
There are several laws associated with particular business that possess the ability to
affect relationships that is maintained between the employee and employer.
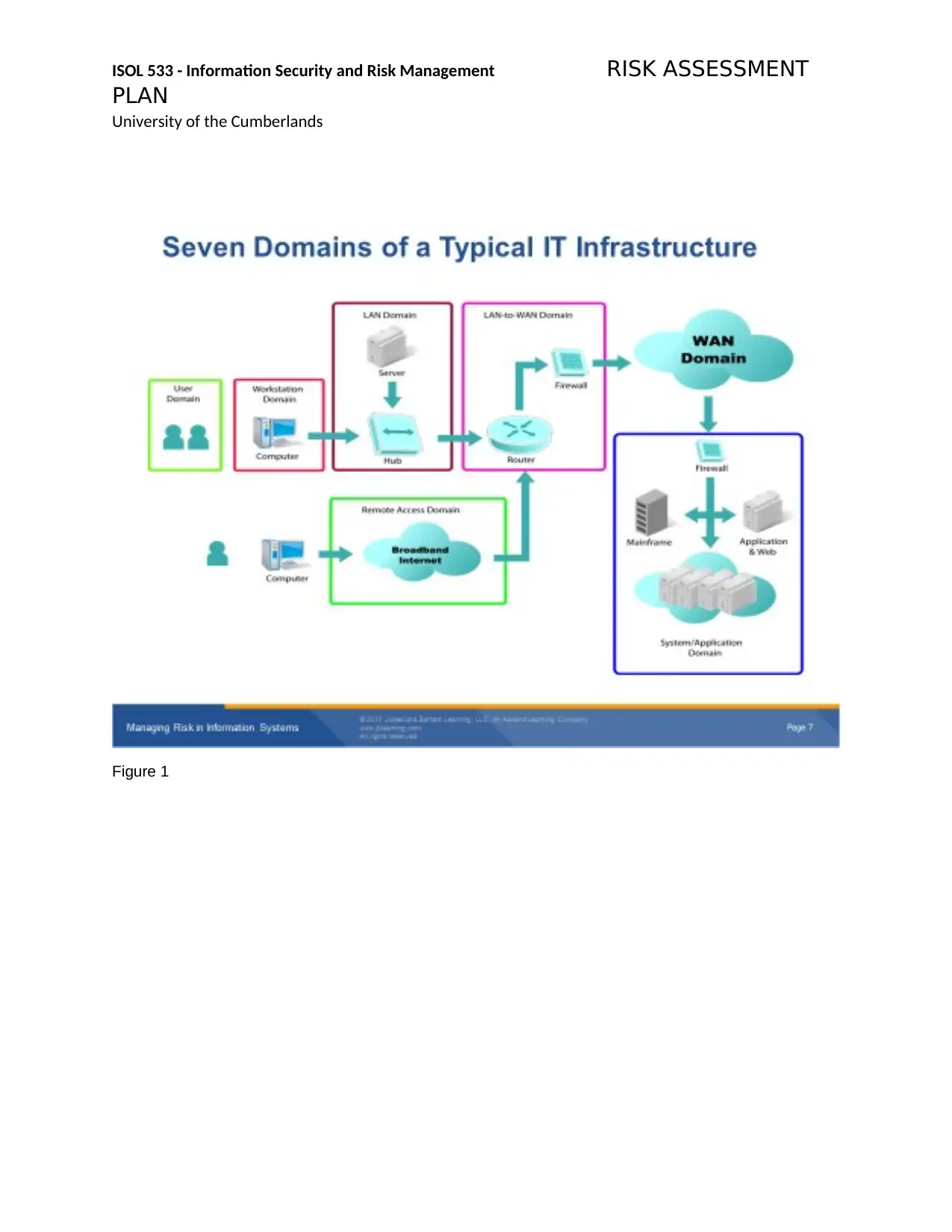
ISOL 533 - Information Security and Risk Management RISK ASSESSMENT
PLAN
University of the Cumberlands
Figure 1
PLAN
University of the Cumberlands
Figure 1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ISOL 533 - Information Security and Risk Management RISK ASSESSMENT
PLAN
University of the Cumberlands
REFERENCES
Gallina, V., Torresan, S., Critto, A., Sperotto, A., Glade, T., & Marcomini, A. (2016). A review of multi-risk
methodologies for natural hazards: Consequences and challenges for a climate change impact
assessment. Journal of environmental management, 168, 123-132.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for effective
information security management. Auerbach Publications.
Safa, N. S., Von Solms, R., & Furnell, S. (2016). Information security policy compliance model in
organizations. Computers & Security, 56, 70-82.
Soomro, Z. A., Shah, M. H., & Ahmed, J. (2016). Information security management needs more holistic
approach: A literature review. International Journal of Information Management, 36(2), 215-
225.
PLAN
University of the Cumberlands
REFERENCES
Gallina, V., Torresan, S., Critto, A., Sperotto, A., Glade, T., & Marcomini, A. (2016). A review of multi-risk
methodologies for natural hazards: Consequences and challenges for a climate change impact
assessment. Journal of environmental management, 168, 123-132.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for effective
information security management. Auerbach Publications.
Safa, N. S., Von Solms, R., & Furnell, S. (2016). Information security policy compliance model in
organizations. Computers & Security, 56, 70-82.
Soomro, Z. A., Shah, M. H., & Ahmed, J. (2016). Information security management needs more holistic
approach: A literature review. International Journal of Information Management, 36(2), 215-
225.
1 out of 7
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


