University System Design and Development: ICT 7002 Assignment 3
VerifiedAdded on 2022/10/02
|14
|2094
|211
Project
AI Summary
This project undertakes a system design for a business information system, building upon previous assignments. It begins with a high-level architectural design, detailing hosting options and the system's operational environment. Storyboards illustrate the user interface for key screens, with a discussion of best-practice UI design principles. The assignment then delves into security concerns, outlining potential threats and mitigation strategies. Finally, it describes the approach to planning and managing implementation, testing, and deployment, covering the system development life cycle (SDLC). The solution covers a range of topics, including the design of system components, user interface design, security considerations, and the approach to planning and managing the implementation, testing, and deployment of the system. References are provided, as well as diagrams, charts and tables.

1
System analysis and development
Student’s Name:
Institution Affiliation:
System analysis and development
Student’s Name:
Institution Affiliation:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
2
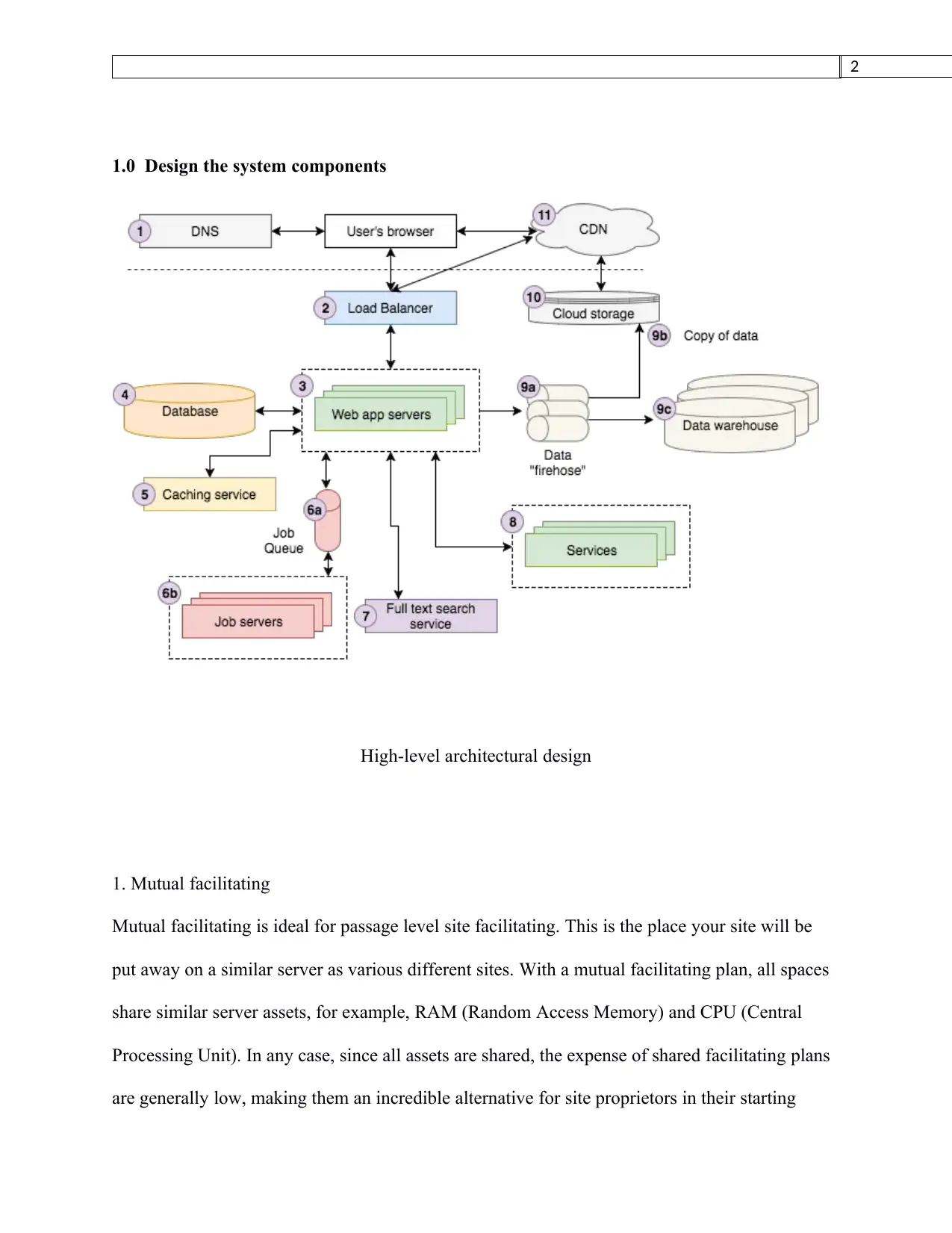
1.0 Design the system components
High-level architectural design
1. Mutual facilitating
Mutual facilitating is ideal for passage level site facilitating. This is the place your site will be
put away on a similar server as various different sites. With a mutual facilitating plan, all spaces
share similar server assets, for example, RAM (Random Access Memory) and CPU (Central
Processing Unit). In any case, since all assets are shared, the expense of shared facilitating plans
are generally low, making them an incredible alternative for site proprietors in their starting
1.0 Design the system components
High-level architectural design
1. Mutual facilitating
Mutual facilitating is ideal for passage level site facilitating. This is the place your site will be
put away on a similar server as various different sites. With a mutual facilitating plan, all spaces
share similar server assets, for example, RAM (Random Access Memory) and CPU (Central
Processing Unit). In any case, since all assets are shared, the expense of shared facilitating plans
are generally low, making them an incredible alternative for site proprietors in their starting

3
stages.
Much of the time, tenderfoots will discover shared the least complex technique for facilitating
their site; so paying little heed to whether you're an entrepreneur, a local gathering, or a
homemaker with a craving to blog, your webpage will be available on the web. Mutual
facilitating plans regularly accompanies numerous accommodating apparatuses, for example,
web designers, WordPress facilitating, and the capacity to email customers(Wu, 2017).
2. Virtual private server (VPS) facilitating
VPS facilitating is remarkable on the grounds that every site is facilitated inside its own space on
the server, however despite everything; it imparts a physical server to different clients. While
VPS facilitating furnishes site proprietors with more customization and extra room, they're as yet
not ready to deal with extraordinarily high traffic levels or spikes in utilization implying that the
site execution can even now be influenced by different destinations on the server (Afram, &
Janabi-Sharifi, 2015)
3. Committed server facilitating
Committed facilitating gives site proprietors the most power over the server that their site is put
away on. That is on the grounds that the server is solely leased by you, and your site is the just
one put away on it. This implies you have full root and administrator get to, so you can control
everything from security to the working framework that you run(Comer, 2015).
2.0 User interface
stages.
Much of the time, tenderfoots will discover shared the least complex technique for facilitating
their site; so paying little heed to whether you're an entrepreneur, a local gathering, or a
homemaker with a craving to blog, your webpage will be available on the web. Mutual
facilitating plans regularly accompanies numerous accommodating apparatuses, for example,
web designers, WordPress facilitating, and the capacity to email customers(Wu, 2017).
2. Virtual private server (VPS) facilitating
VPS facilitating is remarkable on the grounds that every site is facilitated inside its own space on
the server, however despite everything; it imparts a physical server to different clients. While
VPS facilitating furnishes site proprietors with more customization and extra room, they're as yet
not ready to deal with extraordinarily high traffic levels or spikes in utilization implying that the
site execution can even now be influenced by different destinations on the server (Afram, &
Janabi-Sharifi, 2015)
3. Committed server facilitating
Committed facilitating gives site proprietors the most power over the server that their site is put
away on. That is on the grounds that the server is solely leased by you, and your site is the just
one put away on it. This implies you have full root and administrator get to, so you can control
everything from security to the working framework that you run(Comer, 2015).
2.0 User interface
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4
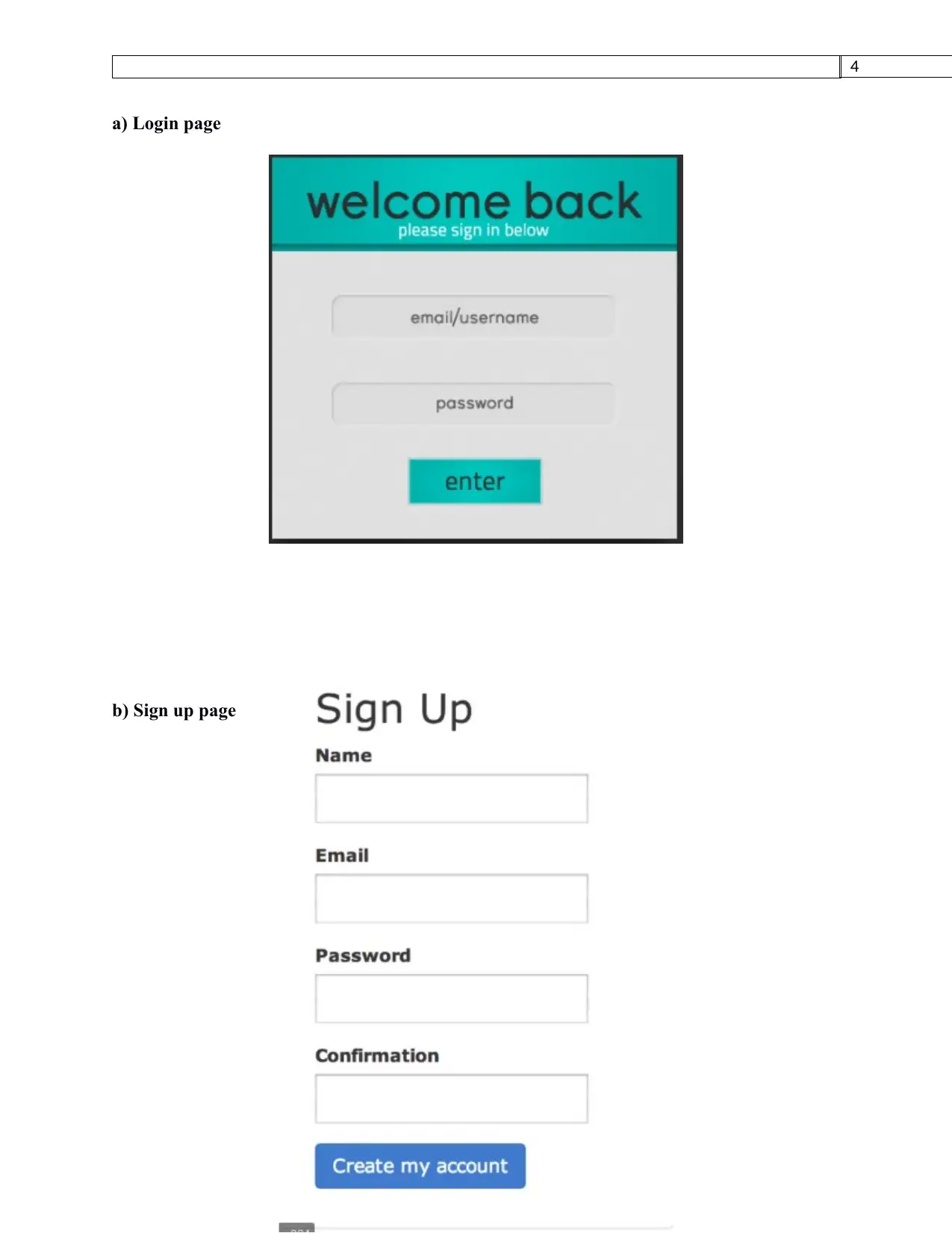
a) Login page
b) Sign up page
a) Login page
b) Sign up page
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5
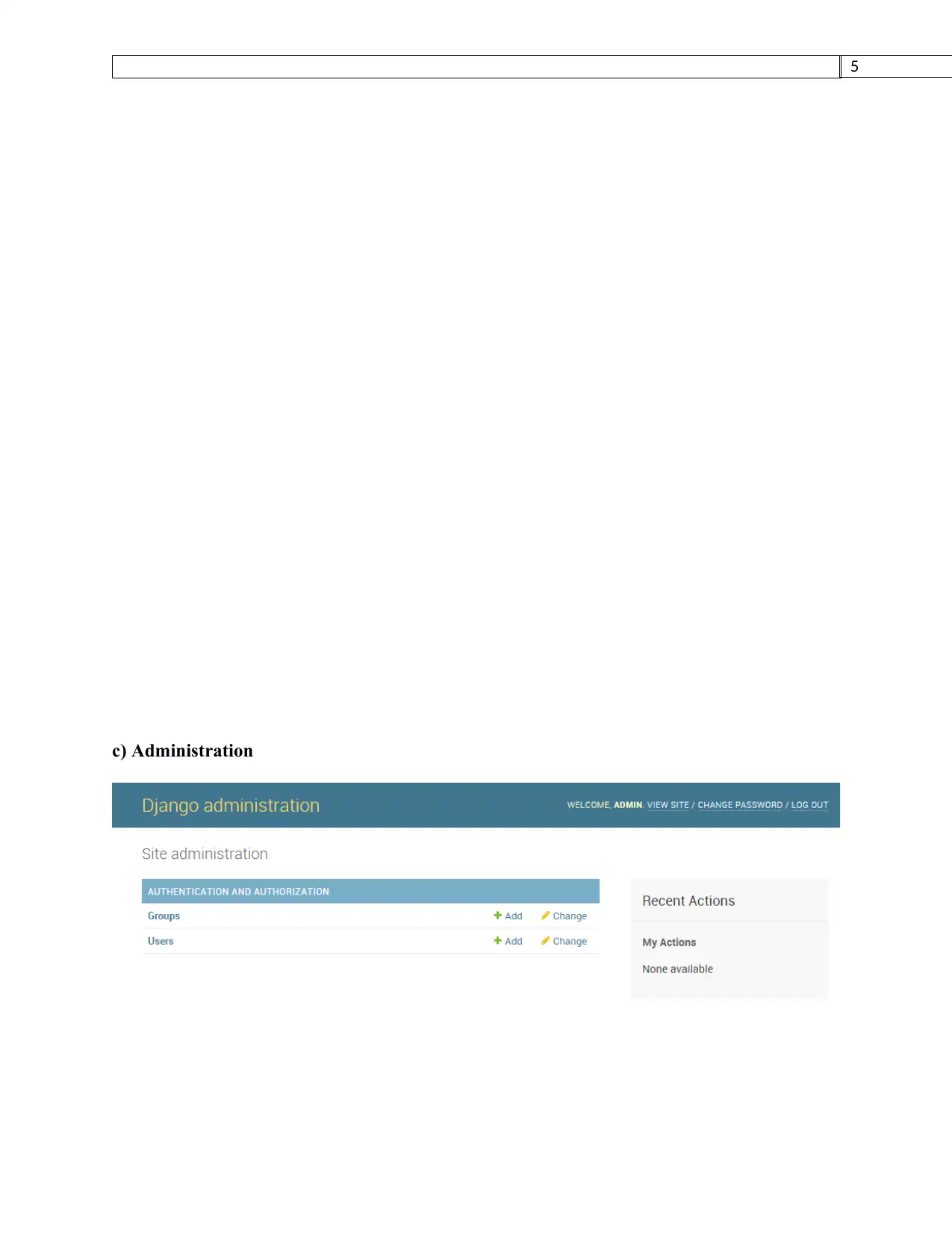
c) Administration
c) Administration
6
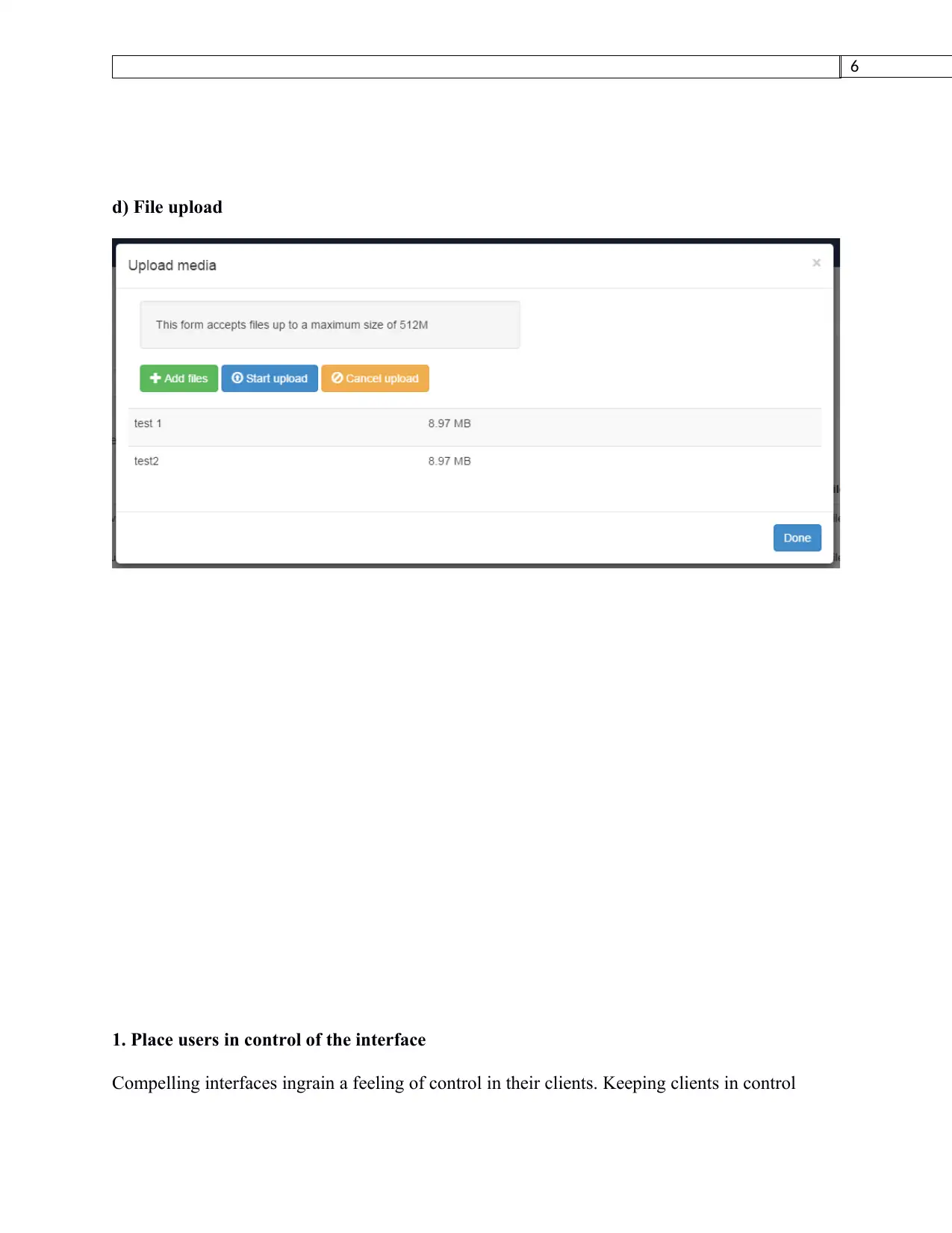
d) File upload
1. Place users in control of the interface
Compelling interfaces ingrain a feeling of control in their clients. Keeping clients in control
d) File upload
1. Place users in control of the interface
Compelling interfaces ingrain a feeling of control in their clients. Keeping clients in control
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
makes them agreeable; they will adapt rapidly and increase a quick feeling of authority.
Cause activities reversible (to excuse)
This standard implies that the client ought to consistently have the option to backtrack whatever
they are doing rapidly. This enables clients to investigate the item without the steady dread of
disappointment — when a client realizes that mistakes can be effectively fixed, this supports the
investigation of new alternatives. Despite what might be expected, if a client must be amazingly
cautious with each move they make, it prompts a more slow investigation and frightening
knowledge that nobody needs(Rappaport, MacCartney, Samimi, & Sun, 2015).
2. Make it comfortable for a user to interact with a product
Interfaces shouldn't contain data that is unimportant or once in a while required. Superfluous data
in UI contends with the applicable data and reduces its relative permeability. Improve interfaces
by evacuating superfluous components or substance that doesn't straightforwardly bolster client
undertakings. Endeavor to plan your application such that all data displayed on the screen will be
significant and important. Analyze each component and ask, "Is this truly required?"
3. Reduce cognitive loads
The intellectual burden is the measure of mental preparing force required to utilize an item. It's
smarter to abstain from making clients think/buckle down to utilize your item. In 1956, clinician
George Miller acquainted the world with the hypothesis of piecing.
4. Make user interfaces consistent
makes them agreeable; they will adapt rapidly and increase a quick feeling of authority.
Cause activities reversible (to excuse)
This standard implies that the client ought to consistently have the option to backtrack whatever
they are doing rapidly. This enables clients to investigate the item without the steady dread of
disappointment — when a client realizes that mistakes can be effectively fixed, this supports the
investigation of new alternatives. Despite what might be expected, if a client must be amazingly
cautious with each move they make, it prompts a more slow investigation and frightening
knowledge that nobody needs(Rappaport, MacCartney, Samimi, & Sun, 2015).
2. Make it comfortable for a user to interact with a product
Interfaces shouldn't contain data that is unimportant or once in a while required. Superfluous data
in UI contends with the applicable data and reduces its relative permeability. Improve interfaces
by evacuating superfluous components or substance that doesn't straightforwardly bolster client
undertakings. Endeavor to plan your application such that all data displayed on the screen will be
significant and important. Analyze each component and ask, "Is this truly required?"
3. Reduce cognitive loads
The intellectual burden is the measure of mental preparing force required to utilize an item. It's
smarter to abstain from making clients think/buckle down to utilize your item. In 1956, clinician
George Miller acquainted the world with the hypothesis of piecing.
4. Make user interfaces consistent
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
Clients ought to never scrutinize the uprightness of an item. Similar hues, textual styles, and
symbols ought to be available all through the item. Try not to change visual styles inside your
item for no clear reason. Consistency of conduct implies the article should work similarly all
through the interface.
3.0 Security concerns
Addressing various threats isn't a simple assignment. On the off chance that you don't have the
workforce set up to deal with your IT security, you are a helpless objective. By working with a
trusted oversaw administration accomplice, you can bring its experience and mastery into your
association to help you with your security act. In addition to the fact that this frees up your IT
staff to deal with undertakings that help you accomplish your business objectives, yet it puts
specialists at the controls so you can rest simpler, realizing that you are finding a way to shield
your organization from the hiding digital dangers.
Test web-confronting servers regularly and completely. Start computerized outputs and
physically filter your web servers in any event month to month. Use multi-layered examining –
don't utilize a similar output utility again and again. Sweep from inside and outside your system.
No one can tell where a programmer might sit.
Fix everything without exception. Remember that your safe condition from a month prior is
currently all the way open gratitude to Patch. Programmers are continually discovering new
assault gaps and strategies into framework programming. Patches and new forms of framework
programming are often discharged to fix these newly discovered issues. Programmers are an
affectionate network, and they are more than ready to impart your system's imperfections to their
Clients ought to never scrutinize the uprightness of an item. Similar hues, textual styles, and
symbols ought to be available all through the item. Try not to change visual styles inside your
item for no clear reason. Consistency of conduct implies the article should work similarly all
through the interface.
3.0 Security concerns
Addressing various threats isn't a simple assignment. On the off chance that you don't have the
workforce set up to deal with your IT security, you are a helpless objective. By working with a
trusted oversaw administration accomplice, you can bring its experience and mastery into your
association to help you with your security act. In addition to the fact that this frees up your IT
staff to deal with undertakings that help you accomplish your business objectives, yet it puts
specialists at the controls so you can rest simpler, realizing that you are finding a way to shield
your organization from the hiding digital dangers.
Test web-confronting servers regularly and completely. Start computerized outputs and
physically filter your web servers in any event month to month. Use multi-layered examining –
don't utilize a similar output utility again and again. Sweep from inside and outside your system.
No one can tell where a programmer might sit.
Fix everything without exception. Remember that your safe condition from a month prior is
currently all the way open gratitude to Patch. Programmers are continually discovering new
assault gaps and strategies into framework programming. Patches and new forms of framework
programming are often discharged to fix these newly discovered issues. Programmers are an
affectionate network, and they are more than ready to impart your system's imperfections to their

9
neighbors.
Increment your mindfulness. Buy into bulletins, sites, twitter channels, and so on that instruct
organization on the most proficient method to ensure your system. There is nothing of the sort as
being too taught with regards to verifying your frameworks and system(Miyazaki, Komiyama,
Kawanomoto, Doi, Furusawa, Hamana, & Koike, 2017).
Train, train, and retrain. Retrain your workers at regular intervals. Remind them about the harm
that should be possible by opening spontaneous messages/connections, stacking programming
projects got all things considered, and not securing their passwords(Li, Li, Yang, & Zheng, 2016,
June).
Discover what and who is on your system. Is it simply your hardware that is appended to your
system? System sweeps are incredible yet don't think little of the advantages of physical walk-
through of your area. Search for anything suspicious or strange. Physical key-lumberjacks can be
veiled as an innocuous mouse or console connectors. We regularly look at worker foundations;
however, shouldn't something be said about every other person who approaches your premises?
Cleaning workforce, utility sellers, and conveyance people are regularly disregarded. Try not to
think for a minute that programmers/social architects aren't mindful of this.
Screen against infection and hostile to malware programming. Guarantee the programmed update
highlight is empowered. Spot check the product frequently to guarantee that the program is
neighbors.
Increment your mindfulness. Buy into bulletins, sites, twitter channels, and so on that instruct
organization on the most proficient method to ensure your system. There is nothing of the sort as
being too taught with regards to verifying your frameworks and system(Miyazaki, Komiyama,
Kawanomoto, Doi, Furusawa, Hamana, & Koike, 2017).
Train, train, and retrain. Retrain your workers at regular intervals. Remind them about the harm
that should be possible by opening spontaneous messages/connections, stacking programming
projects got all things considered, and not securing their passwords(Li, Li, Yang, & Zheng, 2016,
June).
Discover what and who is on your system. Is it simply your hardware that is appended to your
system? System sweeps are incredible yet don't think little of the advantages of physical walk-
through of your area. Search for anything suspicious or strange. Physical key-lumberjacks can be
veiled as an innocuous mouse or console connectors. We regularly look at worker foundations;
however, shouldn't something be said about every other person who approaches your premises?
Cleaning workforce, utility sellers, and conveyance people are regularly disregarded. Try not to
think for a minute that programmers/social architects aren't mindful of this.
Screen against infection and hostile to malware programming. Guarantee the programmed update
highlight is empowered. Spot check the product frequently to guarantee that the program is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
running and that the updates are current. There are in excess of 55,000 new infections every day.
Infection
Trojans
Worms
Spyware
Key lumberjacks
Adware
Forswearing of Service Attacks
Conveyed Denial of Service Attacks
Unapproved access to PC frameworks assets, for example, information
Phishing
Misfortune or defilement of framework information
Upset business activities that depend on PC frameworks
Loss of delicate data
Unlawful checking of exercises on PC frameworks
Digital Security Breaches
4.0 Approach to planning
The frameworks improvement life cycle, or SDLC, is an arranging apparatus utilized by
designers to plan, assemble, and keep up top-notch items. Steps in the SDLC move groups
through arranging, improvement, development, and organization of new programming or stages.
Following the SDLC turns out to be progressively significant for each extra bit of programming
that the new framework cooperates or coordinates with on the client's end.
running and that the updates are current. There are in excess of 55,000 new infections every day.
Infection
Trojans
Worms
Spyware
Key lumberjacks
Adware
Forswearing of Service Attacks
Conveyed Denial of Service Attacks
Unapproved access to PC frameworks assets, for example, information
Phishing
Misfortune or defilement of framework information
Upset business activities that depend on PC frameworks
Loss of delicate data
Unlawful checking of exercises on PC frameworks
Digital Security Breaches
4.0 Approach to planning
The frameworks improvement life cycle, or SDLC, is an arranging apparatus utilized by
designers to plan, assemble, and keep up top-notch items. Steps in the SDLC move groups
through arranging, improvement, development, and organization of new programming or stages.
Following the SDLC turns out to be progressively significant for each extra bit of programming
that the new framework cooperates or coordinates with on the client's end.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11
Planning and Analysis
The initial phases in the SDLC are theoretical arranging and an investigation of the issue that the
framework means to settle. Arranging covers a gauge of all asset needs and engineer costs that
will be a piece of building up the new framework. Investigation in the SDLC is the assurance of
end-client needs and prerequisites to convey the new framework. During the investigation,
organizations frequently review clients about their current frameworks, and their particular needs
to guarantee the new framework is usable and matches client capacities.
Design and Coding
The structure period of the SDLC starts with mapping the proposed information stream,
stockpiling needs, and handling steps of the framework. Starting structure ordinarily happens in
diagrams, and procedures are checked against objectives set up during examination. Engineers,
at that point, start to code the framework itself just as its UI. Work can be separated among
various groups of software engineers to accelerate the framework advancement. The appropriate
structure incorporates the advancement and preparing of test information to guarantee that all
pieces of the framework can address one another.
Testing and Integration
Present-day SDLC joins testing of the framework itself with the trial of its capacity to work with
different stages and programming. On a fundamental level, this implies testing the framework or
Planning and Analysis
The initial phases in the SDLC are theoretical arranging and an investigation of the issue that the
framework means to settle. Arranging covers a gauge of all asset needs and engineer costs that
will be a piece of building up the new framework. Investigation in the SDLC is the assurance of
end-client needs and prerequisites to convey the new framework. During the investigation,
organizations frequently review clients about their current frameworks, and their particular needs
to guarantee the new framework is usable and matches client capacities.
Design and Coding
The structure period of the SDLC starts with mapping the proposed information stream,
stockpiling needs, and handling steps of the framework. Starting structure ordinarily happens in
diagrams, and procedures are checked against objectives set up during examination. Engineers,
at that point, start to code the framework itself just as its UI. Work can be separated among
various groups of software engineers to accelerate the framework advancement. The appropriate
structure incorporates the advancement and preparing of test information to guarantee that all
pieces of the framework can address one another.
Testing and Integration
Present-day SDLC joins testing of the framework itself with the trial of its capacity to work with
different stages and programming. On a fundamental level, this implies testing the framework or

12
programming on the working framework that will run it, for example, Linux or Windows.
Designers initially check the information stream and procedures inside the framework itself.
Next, designers test their new framework's capacity to speak with another programming a client
may utilize. Coordination testing is first performed on an in-house arrangement and after that on
client frameworks in rounds of alpha and beta tests.
Deployment
The organization stage is when clients get an affirmed, working framework. The framework is
authoritatively discharged and has moved out of all testing stages. For huge activities, the maker
may offer preparing projects or coordination help so clients can start utilizing the new
framework. The code itself isn't balanced during sending except if a significant programming
issue is found.
Maintenance
The last phase of the SDLC is upkeep and criticism gathering. Engineers build up an approach to
speak with customers about issues or wanted enhancements for future updates. The upkeep stage
is the longest stage since it proceeds for the full existence of the product and aides all
enhancements and backing. Present-day frameworks interface with numerous bits of outside
programming, so the support arranges additionally incorporates plans to coordinate with new
frameworks created by different organizations.
programming on the working framework that will run it, for example, Linux or Windows.
Designers initially check the information stream and procedures inside the framework itself.
Next, designers test their new framework's capacity to speak with another programming a client
may utilize. Coordination testing is first performed on an in-house arrangement and after that on
client frameworks in rounds of alpha and beta tests.
Deployment
The organization stage is when clients get an affirmed, working framework. The framework is
authoritatively discharged and has moved out of all testing stages. For huge activities, the maker
may offer preparing projects or coordination help so clients can start utilizing the new
framework. The code itself isn't balanced during sending except if a significant programming
issue is found.
Maintenance
The last phase of the SDLC is upkeep and criticism gathering. Engineers build up an approach to
speak with customers about issues or wanted enhancements for future updates. The upkeep stage
is the longest stage since it proceeds for the full existence of the product and aides all
enhancements and backing. Present-day frameworks interface with numerous bits of outside
programming, so the support arranges additionally incorporates plans to coordinate with new
frameworks created by different organizations.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
