Project Management: Risk Mitigation Plan for Ticketing System
VerifiedAdded on 2020/03/02
|9
|1442
|98
Project
AI Summary
This project management assignment presents a risk management plan for the Silicon Forest State University's ticketing system. The plan addresses various risks, including cost, schedule, performance, governance, strategic, legal, and operational risks. The analysis identifies threats and vulnerabilities related to information security, employee roles and responsibilities, and project management. The assignment proposes a risk response plan with mitigation steps focused on information security, employee roles, and information confidentiality. Monitoring and controlling strategies, such as daily scrums and Kanban project management, are suggested to ensure effective communication and data flow. The conclusion emphasizes the importance of mitigating the identified risks through a well-defined plan and periodic evaluation.

Project Management 1
Project Management
Student's Name:
Instructor's Name:
Date:
Project Management
Student's Name:
Instructor's Name:
Date:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Project Management 2
Introduction
This risk management plan is for the Silicon Forest State University’s ticketing system.
Currently, the ticketing system plays an integral role in many departments. Though all
departments are not in need of the ticketing system, the new solution is customized and installed
at all levels. This has left many departments in jeopardy. Engineers are unable to blend with the
ticketing system’s features and platform. The University Office is not prepared to change the
system. Thus, they are trying to identify and mitigate all possible risks.
Executive Summary
Risk is an event that can have a negative impact on a project or system. At the Silicon Forest
State University, risk can introduce performance, functional and technological challenges into
the departments.
According to the current scenario, there are marked differences between the back end and front
end requirements at the Silicon Forest State University. The ticketing system is required for
communicating requests, reports and issues. When departments are not able to use the ticketing
systems efficiently, it would introduce a gap. There will be a prominent gap on how information
is conveyed. This is a critical risk to the entire university.
Background of case study
At the moment, the ticketing system relies on two different operating systems. Few departments
are used to UNIX and the others rely on Windows. Difference in operating systems can introduce
a prominent gap. Engineers at different departments will not be able to send and receive
messages seamlessly. They must engage in manual translation procedures. These procedures are
Introduction
This risk management plan is for the Silicon Forest State University’s ticketing system.
Currently, the ticketing system plays an integral role in many departments. Though all
departments are not in need of the ticketing system, the new solution is customized and installed
at all levels. This has left many departments in jeopardy. Engineers are unable to blend with the
ticketing system’s features and platform. The University Office is not prepared to change the
system. Thus, they are trying to identify and mitigate all possible risks.
Executive Summary
Risk is an event that can have a negative impact on a project or system. At the Silicon Forest
State University, risk can introduce performance, functional and technological challenges into
the departments.
According to the current scenario, there are marked differences between the back end and front
end requirements at the Silicon Forest State University. The ticketing system is required for
communicating requests, reports and issues. When departments are not able to use the ticketing
systems efficiently, it would introduce a gap. There will be a prominent gap on how information
is conveyed. This is a critical risk to the entire university.
Background of case study
At the moment, the ticketing system relies on two different operating systems. Few departments
are used to UNIX and the others rely on Windows. Difference in operating systems can introduce
a prominent gap. Engineers at different departments will not be able to send and receive
messages seamlessly. They must engage in manual translation procedures. These procedures are
Project Management 3
resource and time consuming. In the long run, it would influence the overall productivity of the
organization.
With the use of two different platforms, the company is facing serious cost issues. The software
licenses cost around 20,000 USD per year. This increases the need for open-source solutions.
Manual translation has increased the risks of lost or misinterpreted information too.
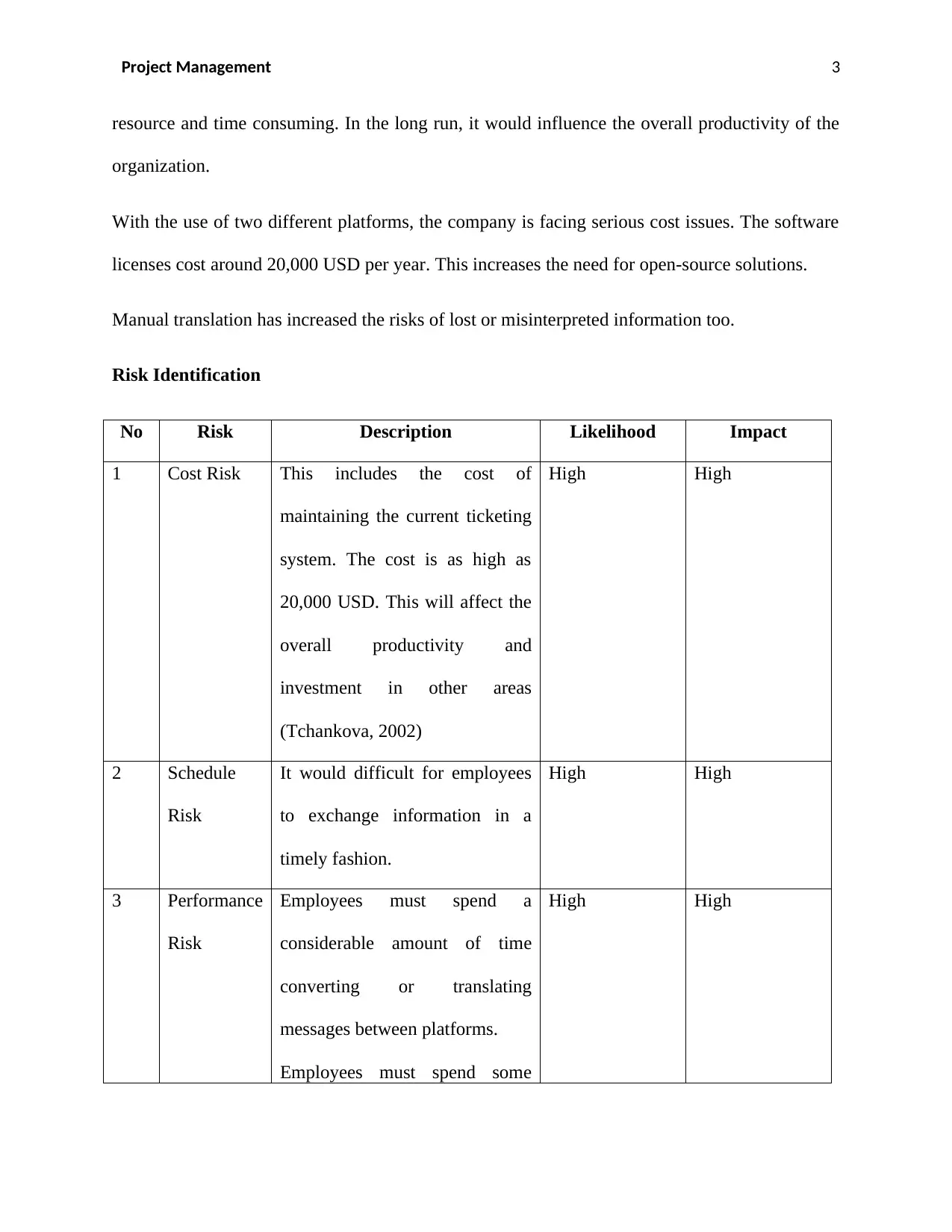
Risk Identification
No Risk Description Likelihood Impact
1 Cost Risk This includes the cost of
maintaining the current ticketing
system. The cost is as high as
20,000 USD. This will affect the
overall productivity and
investment in other areas
(Tchankova, 2002)
High High
2 Schedule
Risk
It would difficult for employees
to exchange information in a
timely fashion.
High High
3 Performance
Risk
Employees must spend a
considerable amount of time
converting or translating
messages between platforms.
Employees must spend some
High High
resource and time consuming. In the long run, it would influence the overall productivity of the
organization.
With the use of two different platforms, the company is facing serious cost issues. The software
licenses cost around 20,000 USD per year. This increases the need for open-source solutions.
Manual translation has increased the risks of lost or misinterpreted information too.
Risk Identification
No Risk Description Likelihood Impact
1 Cost Risk This includes the cost of
maintaining the current ticketing
system. The cost is as high as
20,000 USD. This will affect the
overall productivity and
investment in other areas
(Tchankova, 2002)
High High
2 Schedule
Risk
It would difficult for employees
to exchange information in a
timely fashion.
High High
3 Performance
Risk
Employees must spend a
considerable amount of time
converting or translating
messages between platforms.
Employees must spend some
High High
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Project Management 4
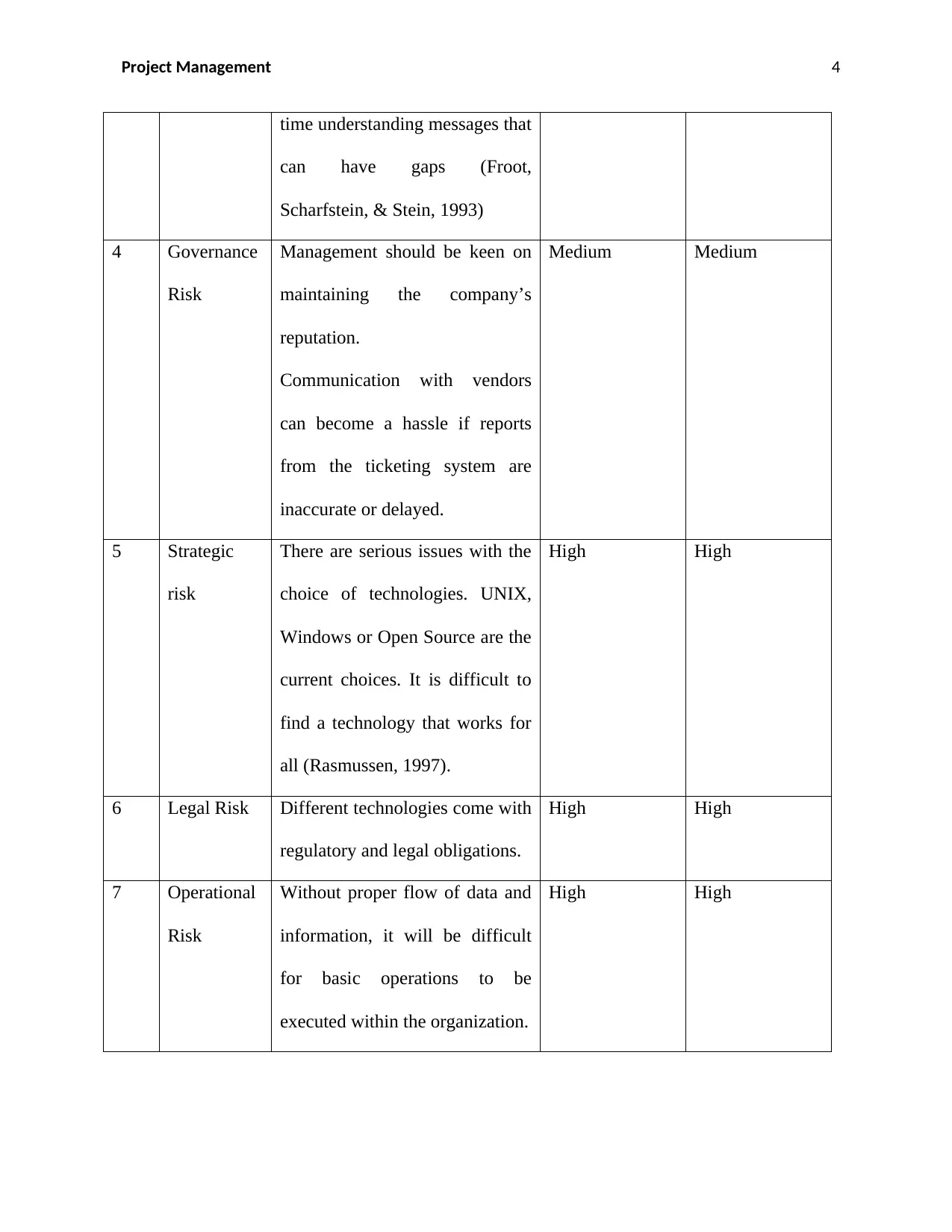
time understanding messages that
can have gaps (Froot,
Scharfstein, & Stein, 1993)
4 Governance
Risk
Management should be keen on
maintaining the company’s
reputation.
Communication with vendors
can become a hassle if reports
from the ticketing system are
inaccurate or delayed.
Medium Medium
5 Strategic
risk
There are serious issues with the
choice of technologies. UNIX,
Windows or Open Source are the
current choices. It is difficult to
find a technology that works for
all (Rasmussen, 1997).
High High
6 Legal Risk Different technologies come with
regulatory and legal obligations.
High High
7 Operational
Risk
Without proper flow of data and
information, it will be difficult
for basic operations to be
executed within the organization.
High High
time understanding messages that
can have gaps (Froot,
Scharfstein, & Stein, 1993)
4 Governance
Risk
Management should be keen on
maintaining the company’s
reputation.
Communication with vendors
can become a hassle if reports
from the ticketing system are
inaccurate or delayed.
Medium Medium
5 Strategic
risk
There are serious issues with the
choice of technologies. UNIX,
Windows or Open Source are the
current choices. It is difficult to
find a technology that works for
all (Rasmussen, 1997).
High High
6 Legal Risk Different technologies come with
regulatory and legal obligations.
High High
7 Operational
Risk
Without proper flow of data and
information, it will be difficult
for basic operations to be
executed within the organization.
High High
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Project Management 5
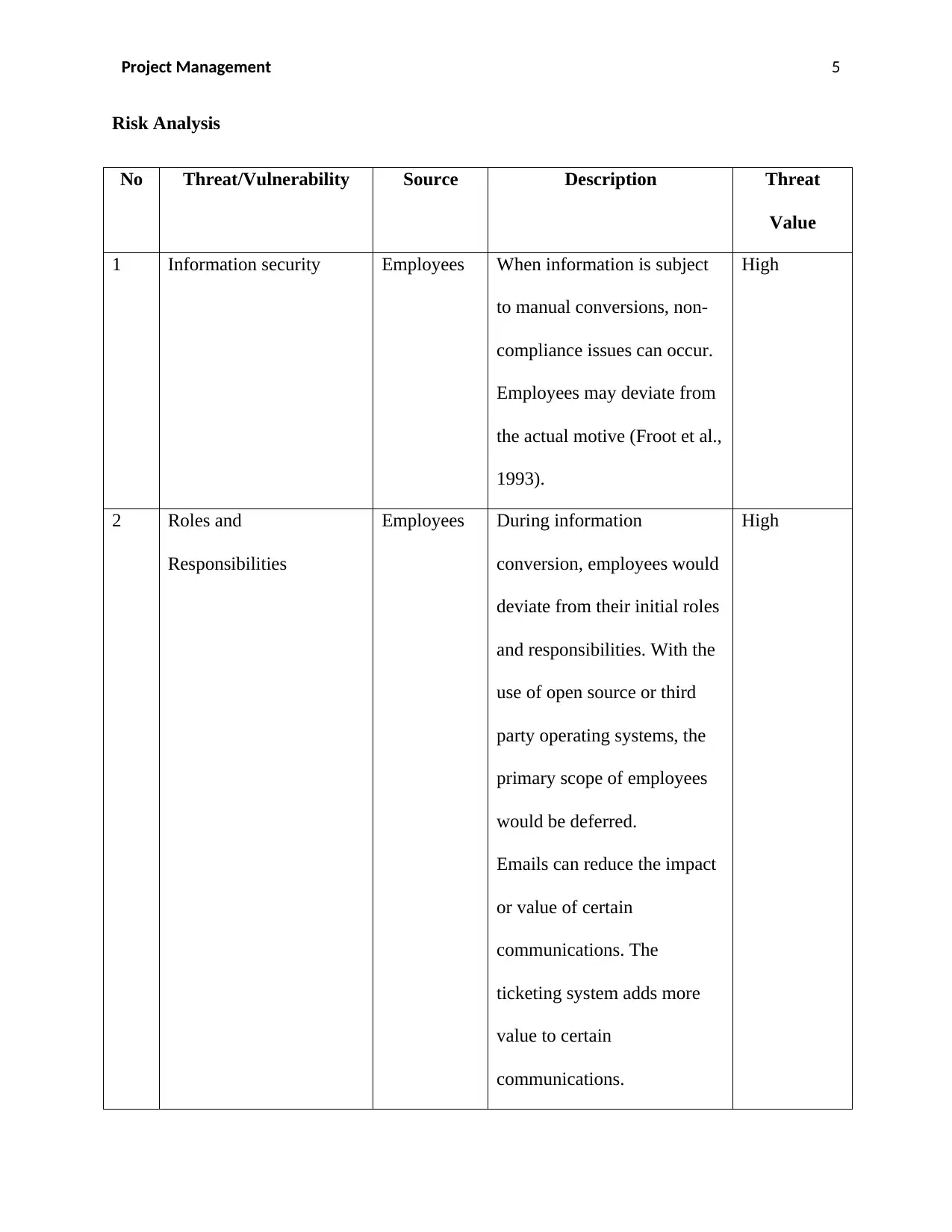
Risk Analysis
No Threat/Vulnerability Source Description Threat
Value
1 Information security Employees When information is subject
to manual conversions, non-
compliance issues can occur.
Employees may deviate from
the actual motive (Froot et al.,
1993).
High
2 Roles and
Responsibilities
Employees During information
conversion, employees would
deviate from their initial roles
and responsibilities. With the
use of open source or third
party operating systems, the
primary scope of employees
would be deferred.
Emails can reduce the impact
or value of certain
communications. The
ticketing system adds more
value to certain
communications.
High
Risk Analysis
No Threat/Vulnerability Source Description Threat
Value
1 Information security Employees When information is subject
to manual conversions, non-
compliance issues can occur.
Employees may deviate from
the actual motive (Froot et al.,
1993).
High
2 Roles and
Responsibilities
Employees During information
conversion, employees would
deviate from their initial roles
and responsibilities. With the
use of open source or third
party operating systems, the
primary scope of employees
would be deferred.
Emails can reduce the impact
or value of certain
communications. The
ticketing system adds more
value to certain
communications.
High
Project Management 6
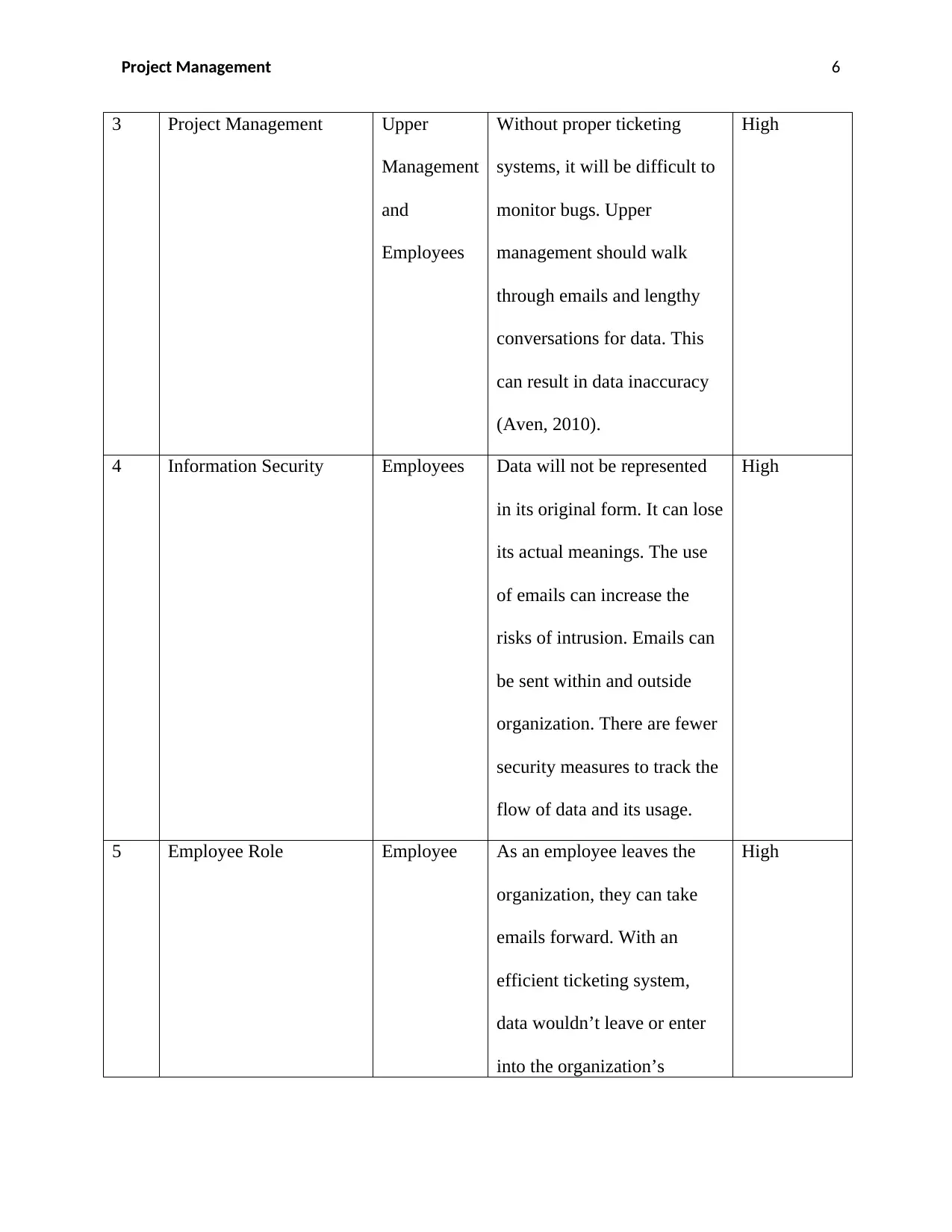
3 Project Management Upper
Management
and
Employees
Without proper ticketing
systems, it will be difficult to
monitor bugs. Upper
management should walk
through emails and lengthy
conversations for data. This
can result in data inaccuracy
(Aven, 2010).
High
4 Information Security Employees Data will not be represented
in its original form. It can lose
its actual meanings. The use
of emails can increase the
risks of intrusion. Emails can
be sent within and outside
organization. There are fewer
security measures to track the
flow of data and its usage.
High
5 Employee Role Employee As an employee leaves the
organization, they can take
emails forward. With an
efficient ticketing system,
data wouldn’t leave or enter
into the organization’s
High
3 Project Management Upper
Management
and
Employees
Without proper ticketing
systems, it will be difficult to
monitor bugs. Upper
management should walk
through emails and lengthy
conversations for data. This
can result in data inaccuracy
(Aven, 2010).
High
4 Information Security Employees Data will not be represented
in its original form. It can lose
its actual meanings. The use
of emails can increase the
risks of intrusion. Emails can
be sent within and outside
organization. There are fewer
security measures to track the
flow of data and its usage.
High
5 Employee Role Employee As an employee leaves the
organization, they can take
emails forward. With an
efficient ticketing system,
data wouldn’t leave or enter
into the organization’s
High
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Project Management 7
information system. Now,
there is room for data leakage.
Risk Response Plan
No Risk Mitigation Step Description
1 Information Security Team Mailing lists are created. All emails would
be circulated within employees in the mailing list.
If a new employee joins the team, the mailing list
would be updated. This is a method to prevent data
leakage (de Landa Farias, Travassons & Rocha,
2003).
2 Role and Responsibility The tickets are not communicated with everyone.
If the department uses a different platform, the
ticket would be assigned to a concerned employee.
This prevents tickets from reaching all
departments and reducing turnaround time
(Reason, 1997).
3 Information Confidentiality of Emails would be used as a mode of
communication. Every communication would be
recorded. It would originate and end at know
points. That ensures high information
confidentiality. The risks of data leakage are
information system. Now,
there is room for data leakage.
Risk Response Plan
No Risk Mitigation Step Description
1 Information Security Team Mailing lists are created. All emails would
be circulated within employees in the mailing list.
If a new employee joins the team, the mailing list
would be updated. This is a method to prevent data
leakage (de Landa Farias, Travassons & Rocha,
2003).
2 Role and Responsibility The tickets are not communicated with everyone.
If the department uses a different platform, the
ticket would be assigned to a concerned employee.
This prevents tickets from reaching all
departments and reducing turnaround time
(Reason, 1997).
3 Information Confidentiality of Emails would be used as a mode of
communication. Every communication would be
recorded. It would originate and end at know
points. That ensures high information
confidentiality. The risks of data leakage are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Project Management 8
eradicated (Purdy, 2010).
Risk Mitigation
It would take several months for the email communication solution and the risk response plan to
be implemented. The effectiveness of this solution depends on how it is understood and accepted
by the employees (Ahmed, Kayis & Amornsawadwatana, 2007).
Monitoring and Controlling
Over a period of time, the upper management should make sure data flows accurately and
seamlessly between departments. There should not be any gaps in communication. Meanwhile,
the tickets must be assigned and closed property. The upper management should engage in daily
scrums or Kanban project management strategies (Ahmed et al., 2007). These strategies help in
understanding how many tickets were communicated, a quick summary of the tickets and its
status. The scrums can happen in every department.
Conclusion
The current ticketing issue comes with a series of risks. These risks are associated with the
accuracy and flow of information. It can affect the functionality of the organization. Thus, the
above mentioned risks must be mitigated with the right plan and follow-up steps. They must be
evaluated periodically too.
eradicated (Purdy, 2010).
Risk Mitigation
It would take several months for the email communication solution and the risk response plan to
be implemented. The effectiveness of this solution depends on how it is understood and accepted
by the employees (Ahmed, Kayis & Amornsawadwatana, 2007).
Monitoring and Controlling
Over a period of time, the upper management should make sure data flows accurately and
seamlessly between departments. There should not be any gaps in communication. Meanwhile,
the tickets must be assigned and closed property. The upper management should engage in daily
scrums or Kanban project management strategies (Ahmed et al., 2007). These strategies help in
understanding how many tickets were communicated, a quick summary of the tickets and its
status. The scrums can happen in every department.
Conclusion
The current ticketing issue comes with a series of risks. These risks are associated with the
accuracy and flow of information. It can affect the functionality of the organization. Thus, the
above mentioned risks must be mitigated with the right plan and follow-up steps. They must be
evaluated periodically too.

Project Management 9
References
Tchankova, L. (2002). Risk identification – basic stage in risk management. Environment
Management and Health, 13(3), 290-297.
Froot, K.A., Scharfstein, D.S. & Stein, J.C. (1993). Risk management: coordinating corporate
investment and financing policies. The Journal of Finance, 48, 1629–1658.
doi:10.1111/j.1540-6261.1993.tb05123.x
Rasmussen, J. (1997). Risk management in a dynamic society: a modelling problem. Safety
Science, 27(2-3), 183-213
Aven, T. (2010). On some recent definitions and analysis frameworks for risk, vulnerability, and
resilience. Risk Analysis, 31, 515-522
de Landa Farias, L., Travassons, G.H. & Rocha, A.R. (2003). Managing organizational risk
knowledge. Journal of Universal Computer Science, 9(7), 670-681
Reason, J. (1997). Managing the risks of organizational accidents (1st ed.). Farnham, U.K.:
Ashgate
Purdy, G. (2010). ISO 31000:2009—Setting a new standard for risk management. Risk
Analysis, 30(6)
Ahmed, A., Kayis, B., & Amornsawadwatana, S. (2007). A review of techniques for risk
management in projects. Benchmarking: An International Journal, 14(1), 22-36
References
Tchankova, L. (2002). Risk identification – basic stage in risk management. Environment
Management and Health, 13(3), 290-297.
Froot, K.A., Scharfstein, D.S. & Stein, J.C. (1993). Risk management: coordinating corporate
investment and financing policies. The Journal of Finance, 48, 1629–1658.
doi:10.1111/j.1540-6261.1993.tb05123.x
Rasmussen, J. (1997). Risk management in a dynamic society: a modelling problem. Safety
Science, 27(2-3), 183-213
Aven, T. (2010). On some recent definitions and analysis frameworks for risk, vulnerability, and
resilience. Risk Analysis, 31, 515-522
de Landa Farias, L., Travassons, G.H. & Rocha, A.R. (2003). Managing organizational risk
knowledge. Journal of Universal Computer Science, 9(7), 670-681
Reason, J. (1997). Managing the risks of organizational accidents (1st ed.). Farnham, U.K.:
Ashgate
Purdy, G. (2010). ISO 31000:2009—Setting a new standard for risk management. Risk
Analysis, 30(6)
Ahmed, A., Kayis, B., & Amornsawadwatana, S. (2007). A review of techniques for risk
management in projects. Benchmarking: An International Journal, 14(1), 22-36
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





