Deakin University SIT216: Usability Evaluation of Wireshark Report
VerifiedAdded on 2022/08/29
|10
|2176
|27
Report
AI Summary
This report presents a usability evaluation of Wireshark, a network packet analyzer used in cyber security. It begins with an introduction to the importance of usability in software design and the selection of Wireshark for evaluation. The report discusses Wireshark's features, its role in network security, and its interactive system for troubleshooting. It then outlines user interface design guidelines and usability principles, emphasizing factors like system visibility, user control, and error prevention. A use case diagram illustrates Wireshark's functionalities. The methodology section justifies the approach, highlighting the evaluation of learnability, error detection, and user satisfaction. Findings reveal Wireshark's user-friendly features, including user manuals and the ability to resolve network issues. The conclusion summarizes the evaluation, emphasizing the importance of usability in cyber security applications and the effective use of methodologies for software performance assessment. References to academic sources support the analysis.

Running head: USABILITY EVALUATION
USABILITY EVALUATION
Name of the Student
Name of the University
Author Note
USABILITY EVALUATION
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1USABILITY EVALUATION
Introduction
The aim of this report is to design a usability guideline that will be suitable for
developing a website. The paper aims at offering better understanding towards the interface
design and usability principles that are associated with software. The different types of user
interfaces that are used within software will be discussed within this report. For the purpose of
developing the evaluation report the selected area is cyber security. Cyber security is a wide
topic that is used for the purpose of offering better support towards the users. The software tool
that is selected for evaluation is Wireshark.
About Wireshark
Wireshark is a cyber-security application tool that is used for the purpose of assessing the
vulnerability that arises within a network. With the help of this application it is expected that
proper security can be maintained over the network. Wireshark is a network packet analyzer that
is used for the purposes of managing the data packets efficiently. This is available for free and is
open source software. The Key features that are offered with the use of wireshark application are
that it is available for units as well as for the windows (Bullock and Parker 2017). This helps in
importing the package from text files efficiently. Cyber security is one of the major components
so it is important to use appropriate tool that will be capable of reducing the errors that are faced
within the network. With the use of proper cyber security application it becomes easy to manage
the overall data. Wireshark is network monitoring and analyzing tool that is used for the purpose
of checking different types of traffic going through the network (Iqbal and Naaz 2019). This
ensures that each packet is managed and analyzed efficiently and the system is capable of
Introduction
The aim of this report is to design a usability guideline that will be suitable for
developing a website. The paper aims at offering better understanding towards the interface
design and usability principles that are associated with software. The different types of user
interfaces that are used within software will be discussed within this report. For the purpose of
developing the evaluation report the selected area is cyber security. Cyber security is a wide
topic that is used for the purpose of offering better support towards the users. The software tool
that is selected for evaluation is Wireshark.
About Wireshark
Wireshark is a cyber-security application tool that is used for the purpose of assessing the
vulnerability that arises within a network. With the help of this application it is expected that
proper security can be maintained over the network. Wireshark is a network packet analyzer that
is used for the purposes of managing the data packets efficiently. This is available for free and is
open source software. The Key features that are offered with the use of wireshark application are
that it is available for units as well as for the windows (Bullock and Parker 2017). This helps in
importing the package from text files efficiently. Cyber security is one of the major components
so it is important to use appropriate tool that will be capable of reducing the errors that are faced
within the network. With the use of proper cyber security application it becomes easy to manage
the overall data. Wireshark is network monitoring and analyzing tool that is used for the purpose
of checking different types of traffic going through the network (Iqbal and Naaz 2019). This
ensures that each packet is managed and analyzed efficiently and the system is capable of

2USABILITY EVALUATION
reading all OSI layers separately hence making troubleshooting very effective. With the help of
Wireshark it becomes easy to trace, troubleshoot, analyze, and view a particular packet format.
However sometimes it has been observed the wireshark is used by hackers for hacking purpose.
Thus it can be stated that with the use of this application proper security can be offered towards a
network.
Interactive system and its users
The interactive system of Wireshark is designed for the purpose of providing better
support towards the troubleshoot network problems. This is also used for the purpose of
examining the sceurity problems that are faced within the network. It can be stated that with the
use of Wireshark, it becomes easy to protect the cyber sites from possible threats. In addition to
this the application Wireshark is also used for the purpose of verifying the network applications
effectively (Brokaw, Eckel and Brewer 2015). Wireshark offers a better platform towards the
developers for the purpose of debugging the protocol implementations. The users of the
application are network administrator, QA engineers, developers, normal users, and network
security engineers.
User interface design guidelines
User interface design guidelines are used for the purpose of determining whether the
interface is suitable for the users to access or not (Gorski and Iacono 2016). With the help of user
interface design it becomes easy to anticipate what the users might need to for interacting with an
interface (Paz and Pow-Sang 2016). Basic guidelines based on which the user interface design
easy will you date are listed below:
reading all OSI layers separately hence making troubleshooting very effective. With the help of
Wireshark it becomes easy to trace, troubleshoot, analyze, and view a particular packet format.
However sometimes it has been observed the wireshark is used by hackers for hacking purpose.
Thus it can be stated that with the use of this application proper security can be offered towards a
network.
Interactive system and its users
The interactive system of Wireshark is designed for the purpose of providing better
support towards the troubleshoot network problems. This is also used for the purpose of
examining the sceurity problems that are faced within the network. It can be stated that with the
use of Wireshark, it becomes easy to protect the cyber sites from possible threats. In addition to
this the application Wireshark is also used for the purpose of verifying the network applications
effectively (Brokaw, Eckel and Brewer 2015). Wireshark offers a better platform towards the
developers for the purpose of debugging the protocol implementations. The users of the
application are network administrator, QA engineers, developers, normal users, and network
security engineers.
User interface design guidelines
User interface design guidelines are used for the purpose of determining whether the
interface is suitable for the users to access or not (Gorski and Iacono 2016). With the help of user
interface design it becomes easy to anticipate what the users might need to for interacting with an
interface (Paz and Pow-Sang 2016). Basic guidelines based on which the user interface design
easy will you date are listed below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3USABILITY EVALUATION
Visibility of the system
User control and freedom
Error prevention capability
Flexibility and efficiency of a towards the users
Consistency and standards
Usability principles of Wireshark
Wireshark is designed with proper usability principles so that it becomes easy to offer
better support towards the users. The application is designed with several usability principles, so
that it becomes easy to enhance the performance. The application Wireshark offers huge
flexibility and efficiency towards the users and also ensures that a better platform for interaction
is offered towards the users (Louridas, Tsoukalas and Mitropoulos 2016). This enhances the
users experience and ensures that proper interactions are carried out between the users. In
addition to the application Wireshark allows the user to choose suitable system as per their
needs. The main benefit that is offered with the use of Wireshark application is that it offers high
visibility and ensures that each terms and conditions are mentioned towards the users at the
beginning (Rahman and Zin 2018). With the use of this application it becomes easy to maintain
the network troubleshooting and ensures that proper security is maintained towards the cyber
performance.
Visibility of the system
User control and freedom
Error prevention capability
Flexibility and efficiency of a towards the users
Consistency and standards
Usability principles of Wireshark
Wireshark is designed with proper usability principles so that it becomes easy to offer
better support towards the users. The application is designed with several usability principles, so
that it becomes easy to enhance the performance. The application Wireshark offers huge
flexibility and efficiency towards the users and also ensures that a better platform for interaction
is offered towards the users (Louridas, Tsoukalas and Mitropoulos 2016). This enhances the
users experience and ensures that proper interactions are carried out between the users. In
addition to the application Wireshark allows the user to choose suitable system as per their
needs. The main benefit that is offered with the use of Wireshark application is that it offers high
visibility and ensures that each terms and conditions are mentioned towards the users at the
beginning (Rahman and Zin 2018). With the use of this application it becomes easy to maintain
the network troubleshooting and ensures that proper security is maintained towards the cyber
performance.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4USABILITY EVALUATION
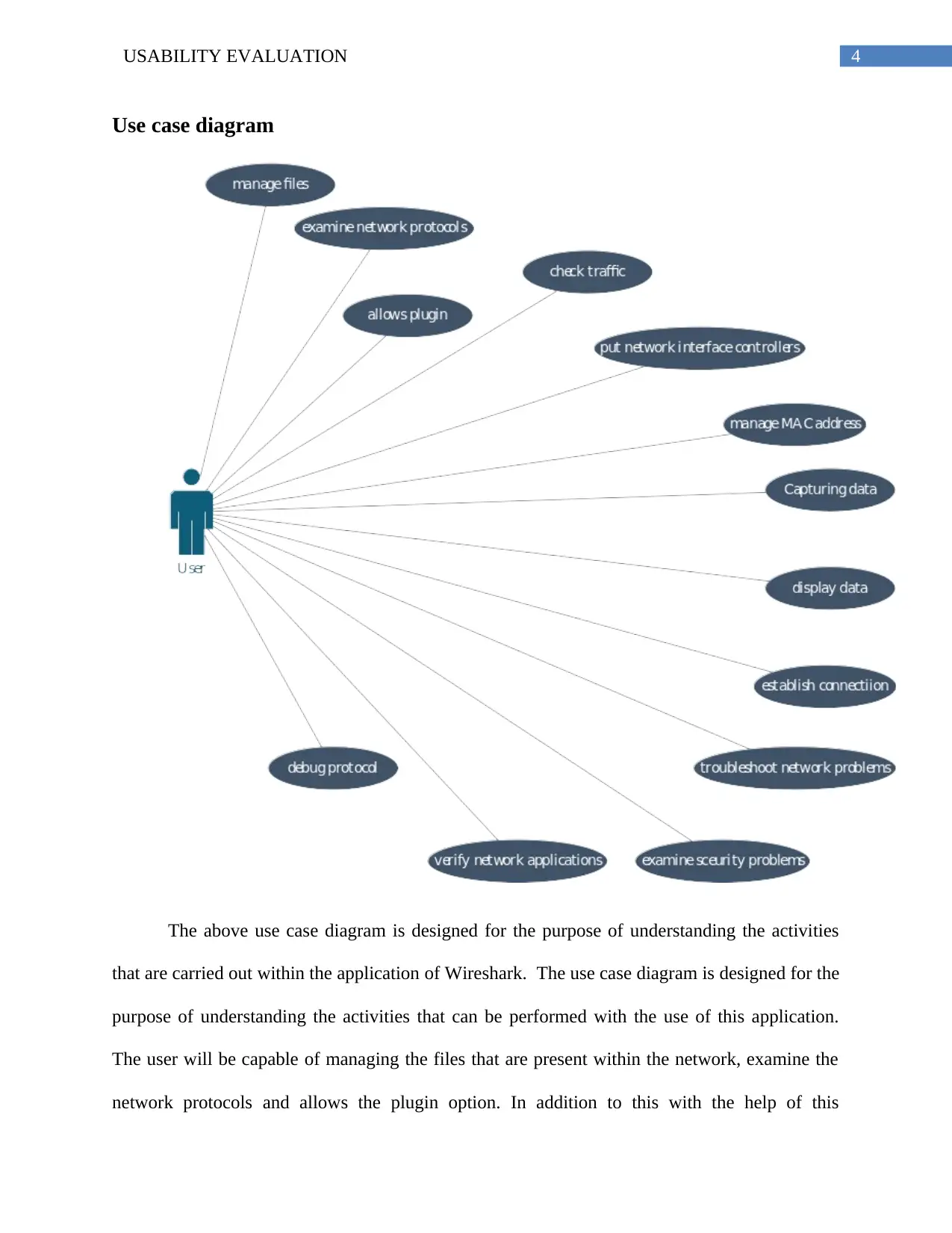
Use case diagram
The above use case diagram is designed for the purpose of understanding the activities
that are carried out within the application of Wireshark. The use case diagram is designed for the
purpose of understanding the activities that can be performed with the use of this application.
The user will be capable of managing the files that are present within the network, examine the
network protocols and allows the plugin option. In addition to this with the help of this
Use case diagram
The above use case diagram is designed for the purpose of understanding the activities
that are carried out within the application of Wireshark. The use case diagram is designed for the
purpose of understanding the activities that can be performed with the use of this application.
The user will be capable of managing the files that are present within the network, examine the
network protocols and allows the plugin option. In addition to this with the help of this

5USABILITY EVALUATION
application the user can check the traffic, put network interface controller and manage the MAC
address. Apart from this the other factors are capturing the data, displaying the data, establishing
a proper connection, managing the troubleshoot network problems, examining the security
problems, verifying the network application and debug protocol. Hence it can be stated that with
the use of this application it becomes easy to manage the performance.
Justification of the methodology
With the help of proper interface guidelines it becomes easy to determine the usability of
an application. Wireshark is an application that is used for the purpose of providing better
security towards the networks. This ensures that with the help of a wire shark the chances of
errors can be reduced (Sage, et al. 2015). This part of the report aims at evaluating the
methodology based on which the usability factors are determined. The usability evolution of the
wire shark is carried out for the purpose of understanding the way application platform is used by
the users. The software offers use efficiency, reliability and insures that the errors can be
resolved quickly (Marcilly and Peute 2017).
For the purposes of evaluating the learnability of the wireshark application certain users
are selected. Once they are selected then they will be allowed to perform certain tasks on the
platform (Shneiderman et al. 2016). The users are requested to examine the security problems
that are faced within a network. With successful execution of the network security evaluation it
will become easy to understand the performance.
Error Detection is considered as one of the biggest factor while evaluating and usability
of software. This involves evaluating the errors that are generated while using software or an
application. There are certain errors that are faced while accessing software. With the use of
application the user can check the traffic, put network interface controller and manage the MAC
address. Apart from this the other factors are capturing the data, displaying the data, establishing
a proper connection, managing the troubleshoot network problems, examining the security
problems, verifying the network application and debug protocol. Hence it can be stated that with
the use of this application it becomes easy to manage the performance.
Justification of the methodology
With the help of proper interface guidelines it becomes easy to determine the usability of
an application. Wireshark is an application that is used for the purpose of providing better
security towards the networks. This ensures that with the help of a wire shark the chances of
errors can be reduced (Sage, et al. 2015). This part of the report aims at evaluating the
methodology based on which the usability factors are determined. The usability evolution of the
wire shark is carried out for the purpose of understanding the way application platform is used by
the users. The software offers use efficiency, reliability and insures that the errors can be
resolved quickly (Marcilly and Peute 2017).
For the purposes of evaluating the learnability of the wireshark application certain users
are selected. Once they are selected then they will be allowed to perform certain tasks on the
platform (Shneiderman et al. 2016). The users are requested to examine the security problems
that are faced within a network. With successful execution of the network security evaluation it
will become easy to understand the performance.
Error Detection is considered as one of the biggest factor while evaluating and usability
of software. This involves evaluating the errors that are generated while using software or an
application. There are certain errors that are faced while accessing software. With the use of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6USABILITY EVALUATION
proper usability it becomes easy to operate the overall performance. Hence it can be stated that
once the error factor has been minimized properly then it becomes easy to understand the
evolution of Wireshark application.
For the purpose of understanding the usability of software it is important to check
whether the users are satisfied with the website or not. User satisfaction is considered as an
essential measure that is used for determining the acceptability that has been obtained by the
users while using the application (Kaur et al. 2016). Wireshark is considered to be the one of the
best tool for managing the troubleshooting problems that occurs within a network. It can be
stated that with the use of this tool the problems faced within a network and other security issues
can be resolved easily. Hence it can be stated that wireshark offers a wide usability features
towards the users.
Findings of the evaluation
After performing the usability evalaution on the selected application it has been observed
that the website offers a wide range of features towards the users. The main purpose of using
Wireshark application is to resolve the network issues that are faced by the users. In addition to
this it is also used for offering better security towards the data that are shared over the network.
Users are offered with a huge usability features so that they can interact effectively with the
Wireshark platform. Wireshark offers user manual so that it becomes easy for the users to
perform the activities on the application. With the help of these it becomes easy to understand
the problems that are faced with the use of the application (Kent et al. 2017). With proper
evaluation it becomes easy to use the application. Without proper knowledge about the
application it will become very difficult to access the data and features associated with the
proper usability it becomes easy to operate the overall performance. Hence it can be stated that
once the error factor has been minimized properly then it becomes easy to understand the
evolution of Wireshark application.
For the purpose of understanding the usability of software it is important to check
whether the users are satisfied with the website or not. User satisfaction is considered as an
essential measure that is used for determining the acceptability that has been obtained by the
users while using the application (Kaur et al. 2016). Wireshark is considered to be the one of the
best tool for managing the troubleshooting problems that occurs within a network. It can be
stated that with the use of this tool the problems faced within a network and other security issues
can be resolved easily. Hence it can be stated that wireshark offers a wide usability features
towards the users.
Findings of the evaluation
After performing the usability evalaution on the selected application it has been observed
that the website offers a wide range of features towards the users. The main purpose of using
Wireshark application is to resolve the network issues that are faced by the users. In addition to
this it is also used for offering better security towards the data that are shared over the network.
Users are offered with a huge usability features so that they can interact effectively with the
Wireshark platform. Wireshark offers user manual so that it becomes easy for the users to
perform the activities on the application. With the help of these it becomes easy to understand
the problems that are faced with the use of the application (Kent et al. 2017). With proper
evaluation it becomes easy to use the application. Without proper knowledge about the
application it will become very difficult to access the data and features associated with the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7USABILITY EVALUATION
website. Thus in order to successfully use the website it is important to have proper knowledge
about all the features.
Conclusion
The paper has evaluated the different components that are used with successful use of
Wireshark. Wireshark is an application that offers better usability features towards the users. The
report has discussed about the interface design/usability guidelines that are associated with the
selected interface. Cyber security has become one of the major concerns and thus it becomes
essential to ensure that proper applications are used for enhancing the business performance.
With the use of this evaluation it becomes easy to manage the performance. Hence it can be
concluded that with the proper evaluation of methodologies and heuristic evaluation it becomes
easy to manage the performance of the software.
website. Thus in order to successfully use the website it is important to have proper knowledge
about all the features.
Conclusion
The paper has evaluated the different components that are used with successful use of
Wireshark. Wireshark is an application that offers better usability features towards the users. The
report has discussed about the interface design/usability guidelines that are associated with the
selected interface. Cyber security has become one of the major concerns and thus it becomes
essential to ensure that proper applications are used for enhancing the business performance.
With the use of this evaluation it becomes easy to manage the performance. Hence it can be
concluded that with the proper evaluation of methodologies and heuristic evaluation it becomes
easy to manage the performance of the software.

8USABILITY EVALUATION
References
Brokaw, E.B., Eckel, E. and Brewer, B.R., 2015. Usability evaluation of a kinematics focused
Kinect therapy program for individuals with stroke. Technology and Health Care, 23(2), pp.143-
151.
Bullock, J. and Parker, J.T., 2017. Wireshark for Security Professionals: Using Wireshark and
the Metasploit Framework. John Wiley & Sons.
Gorski, P.L. and Iacono, L.L., 2016, July. Towards the Usability Evaluation of Security APIs.
In HAISA (pp. 252-265).
Iqbal, H. and Naaz, S., 2019. Wireshark as a Tool for Detection of Various LAN Attacks.
Kaur, S., Kaur, K. and Kaur, P., 2016, March. Analysis of website usability evaluation methods.
In 2016 3rd International Conference on Computing for Sustainable Global Development
(INDIACom) (pp. 1043-1046). IEEE.
Kent, T.M., Carswell, C.M., Lee, M. and Sublette, M.A., 2017, September. Do Aesthetic Design
Principles Predict Visual Appeal of a Simple Control Panel?. In Proceedings of the Human
Factors and Ergonomics Society Annual Meeting (Vol. 61, No. 1, pp. 1414-1418). Sage CA: Los
Angeles, CA: SAGE Publications.
Louridas, P., Tsoukalas, G. and Mitropoulos, D., 2016. Requirements and User Interface Design.
Marcilly, R. and Peute, L.W., 2017, January. How to Reach Evidence-Based Usability
Evaluation Methods. In ITCH (pp. 211-216).
References
Brokaw, E.B., Eckel, E. and Brewer, B.R., 2015. Usability evaluation of a kinematics focused
Kinect therapy program for individuals with stroke. Technology and Health Care, 23(2), pp.143-
151.
Bullock, J. and Parker, J.T., 2017. Wireshark for Security Professionals: Using Wireshark and
the Metasploit Framework. John Wiley & Sons.
Gorski, P.L. and Iacono, L.L., 2016, July. Towards the Usability Evaluation of Security APIs.
In HAISA (pp. 252-265).
Iqbal, H. and Naaz, S., 2019. Wireshark as a Tool for Detection of Various LAN Attacks.
Kaur, S., Kaur, K. and Kaur, P., 2016, March. Analysis of website usability evaluation methods.
In 2016 3rd International Conference on Computing for Sustainable Global Development
(INDIACom) (pp. 1043-1046). IEEE.
Kent, T.M., Carswell, C.M., Lee, M. and Sublette, M.A., 2017, September. Do Aesthetic Design
Principles Predict Visual Appeal of a Simple Control Panel?. In Proceedings of the Human
Factors and Ergonomics Society Annual Meeting (Vol. 61, No. 1, pp. 1414-1418). Sage CA: Los
Angeles, CA: SAGE Publications.
Louridas, P., Tsoukalas, G. and Mitropoulos, D., 2016. Requirements and User Interface Design.
Marcilly, R. and Peute, L.W., 2017, January. How to Reach Evidence-Based Usability
Evaluation Methods. In ITCH (pp. 211-216).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9USABILITY EVALUATION
Paz, F. and Pow-Sang, J.A., 2016. A systematic mapping review of usability evaluation methods
for software development process. International Journal of Software Engineering and Its
Applications, 10(1), pp.165-178.
Rahman, N.A. and Zin, N.A.M., 2018. Visualizing Requirements using Use Case Diagram and
Diagram 0 for Compound Information System. Journal of Mathematics & Computing
Science, 3(1), pp.34-38.
Sage, D., Kirshner, H., Pengo, T., Stuurman, N., Min, J., Manley, S. and Unser, M., 2015.
Quantitative evaluation of software packages for single-molecule localization
microscopy. Nature methods, 12(8), p.717.
Sanders, C., 2017. Practical packet analysis: Using Wireshark to solve real-world network
problems. No Starch Press.
Shneiderman, B., Plaisant, C., Cohen, M., Jacobs, S., Elmqvist, N. and Diakopoulos, N.,
2016. Designing the user interface: strategies for effective human-computer interaction. Pearson.
Paz, F. and Pow-Sang, J.A., 2016. A systematic mapping review of usability evaluation methods
for software development process. International Journal of Software Engineering and Its
Applications, 10(1), pp.165-178.
Rahman, N.A. and Zin, N.A.M., 2018. Visualizing Requirements using Use Case Diagram and
Diagram 0 for Compound Information System. Journal of Mathematics & Computing
Science, 3(1), pp.34-38.
Sage, D., Kirshner, H., Pengo, T., Stuurman, N., Min, J., Manley, S. and Unser, M., 2015.
Quantitative evaluation of software packages for single-molecule localization
microscopy. Nature methods, 12(8), p.717.
Sanders, C., 2017. Practical packet analysis: Using Wireshark to solve real-world network
problems. No Starch Press.
Shneiderman, B., Plaisant, C., Cohen, M., Jacobs, S., Elmqvist, N. and Diakopoulos, N.,
2016. Designing the user interface: strategies for effective human-computer interaction. Pearson.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




