University of Southern Queensland CIS5205: Security Management Report
VerifiedAdded on 2023/06/11
|10
|2104
|490
Report
AI Summary
This report for the University of Southern Queensland's CIS5205 Management of Information Security course discusses the critical role of physical security and cryptography in protecting information technology assets. It identifies key risks to IT assets due to poor physical security, such as device theft and employee assault for information retrieval, and proposes physical security controls including locked server rooms, surveillance, rack mount servers, workstation security measures, and secure data backup storage. The report also explores the three main types of cryptography algorithms: secret key, public key, and hash functions, detailing their application in ensuring information security with examples like DES, RSA, and SHA-1. The document concludes by emphasizing the importance of integrating both physical and cryptographic measures to establish a robust security posture.

The University of Southern Queensland (USQ)
CIS5205 Management of Information Security
Assignment 2
27 August 2018
Submitted To:
Dr. Michael Lane (Course Examiner)
Submitted By:
Joe Bloggs (Student Name)
(USQ SID 12345678)
Total Words: About 1500 Words
1
CIS5205 Management of Information Security
Assignment 2
27 August 2018
Submitted To:
Dr. Michael Lane (Course Examiner)
Submitted By:
Joe Bloggs (Student Name)
(USQ SID 12345678)
Total Words: About 1500 Words
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Role of Physical Security in Information Security.................................................................................3
Key Risks to Information Technology Assets due to Poor Physical Security....................................3
Physical Security Controls.................................................................................................................4
Critical Role of Cryptography in Information Security.........................................................................6
Three Main Types of Cryptography Algorithms................................................................................6
Application of Cryptography Algorithms to ensure Information Security.........................................7
List of References................................................................................................................................10
2
Role of Physical Security in Information Security.................................................................................3
Key Risks to Information Technology Assets due to Poor Physical Security....................................3
Physical Security Controls.................................................................................................................4
Critical Role of Cryptography in Information Security.........................................................................6
Three Main Types of Cryptography Algorithms................................................................................6
Application of Cryptography Algorithms to ensure Information Security.........................................7
List of References................................................................................................................................10
2

Role of Physical Security in Information Security
Key Risks to Information Technology Assets due to Poor Physical Security
Stealing of Devices
The first form of security risk that may emerge due to poor physical security is the stealing of
information technology devices. There are mobile devices, such as Smartphones, laptops, and
tablets used by the employees in the organization to carry out the business tasks and
operations. These devices contain a lot of sensitive and critical information that needs to be
protected. Poor physical security provides the attackers with the chance to steal the devices
and explore the information stored within. The mobile devices can easily be kept hidden in
the bag or pockets to take away the same outside the organization without the due permission
to do so (Schultz, 2007).
Employee Assault for Information Retrieval
There are a lot of employees that work in the business organization and each of these
employees has access to certain data sets associated with the organization. The lack of
adequate physical security controls may allow the malevolent entities to enter in the premises
of the organization. These entities may belong to a competitor in the market and may assault
an employee to gain sensitive or critical pieces of information from the employee. This will
put the information sets at risk of losing the confidentiality and privacy of the data.
3
Key Risks to Information Technology Assets due to Poor Physical Security
Stealing of Devices
The first form of security risk that may emerge due to poor physical security is the stealing of
information technology devices. There are mobile devices, such as Smartphones, laptops, and
tablets used by the employees in the organization to carry out the business tasks and
operations. These devices contain a lot of sensitive and critical information that needs to be
protected. Poor physical security provides the attackers with the chance to steal the devices
and explore the information stored within. The mobile devices can easily be kept hidden in
the bag or pockets to take away the same outside the organization without the due permission
to do so (Schultz, 2007).
Employee Assault for Information Retrieval
There are a lot of employees that work in the business organization and each of these
employees has access to certain data sets associated with the organization. The lack of
adequate physical security controls may allow the malevolent entities to enter in the premises
of the organization. These entities may belong to a competitor in the market and may assault
an employee to gain sensitive or critical pieces of information from the employee. This will
put the information sets at risk of losing the confidentiality and privacy of the data.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Physical Security Controls
The business organizations handle abundant sets of data that comprise of private, public,
sensitive, critical, and non-critical data pieces. There are data servers that are used to manage
the databases of the company. These data servers and other servers are placed in the server
room. It is essential to lock up the server room so that none of the unauthorized entities may
gain access to the room. It is essential to develop the policies regarding locking and
unlocking of the room and the resources responsible for the same.
Surveillance is another important physical security control that shall be implemented with the
aid of security guards, audio and video surveillance tools. The security guards must be placed
at every entry and exit point of the organization. These guards must check for the identity of
the individual entering the organization and must also check the bags at the time of entry and
exit. Audio and video surveillance shall be used with the aid of microphones and video
cameras shall be carried out. These will capture all of the activities being done in the
organization. A surveillance manager along with the tea must review these recordings and
logs at all times (Sinha et al., 2015). Any of the deviations or suspicious activities shall be
identified and immediately reported.
Rack mount servers shall be used by the business organizations. These come with the
advantages as lesser floor space and easier to secure. These can be conveniently locked up in
the closed racks and can also be bolted to the floor. In this manner, the entire server set will
not be possible to be moved and the likelihood of the physical security attacks on the same
will come down (Hammonds, 2018).
There is a lot of information that a malevolent entity may obtain from the workstations of the
employees. For instance, if an employee does not lock the computer system being used to
handle the critical business applications and is not at the workstation, a malicious entity may
access the system and obtain all of the information. It is necessary to apply certain physical
security controls to avoid such occurrences. The computing resources at the workstations
shall be locked at all times when the employee is not available at the desk. There shall be use
of biometric recognition on the computer systems to unlock the device.
Backing up of the data is an essential activity that is done for the purpose of disaster
recovery. Most of these data backups are stored on the virtual storage spaces. However, there
is use of discs and tapes for backing up the data sets. These disks and tapes may be stolen by
4
The business organizations handle abundant sets of data that comprise of private, public,
sensitive, critical, and non-critical data pieces. There are data servers that are used to manage
the databases of the company. These data servers and other servers are placed in the server
room. It is essential to lock up the server room so that none of the unauthorized entities may
gain access to the room. It is essential to develop the policies regarding locking and
unlocking of the room and the resources responsible for the same.
Surveillance is another important physical security control that shall be implemented with the
aid of security guards, audio and video surveillance tools. The security guards must be placed
at every entry and exit point of the organization. These guards must check for the identity of
the individual entering the organization and must also check the bags at the time of entry and
exit. Audio and video surveillance shall be used with the aid of microphones and video
cameras shall be carried out. These will capture all of the activities being done in the
organization. A surveillance manager along with the tea must review these recordings and
logs at all times (Sinha et al., 2015). Any of the deviations or suspicious activities shall be
identified and immediately reported.
Rack mount servers shall be used by the business organizations. These come with the
advantages as lesser floor space and easier to secure. These can be conveniently locked up in
the closed racks and can also be bolted to the floor. In this manner, the entire server set will
not be possible to be moved and the likelihood of the physical security attacks on the same
will come down (Hammonds, 2018).
There is a lot of information that a malevolent entity may obtain from the workstations of the
employees. For instance, if an employee does not lock the computer system being used to
handle the critical business applications and is not at the workstation, a malicious entity may
access the system and obtain all of the information. It is necessary to apply certain physical
security controls to avoid such occurrences. The computing resources at the workstations
shall be locked at all times when the employee is not available at the desk. There shall be use
of biometric recognition on the computer systems to unlock the device.
Backing up of the data is an essential activity that is done for the purpose of disaster
recovery. Most of these data backups are stored on the virtual storage spaces. However, there
is use of discs and tapes for backing up the data sets. These disks and tapes may be stolen by
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

a malevolent entity and the information exposure may take place. These devices shall be
secured using physical security controls and shall not be allowed to be carried outside of the
office. These shall be placed in the secure vaults and must not be allowed to be accessed by
anyone except the vault manager. A log book of users accessing the vault with consent from
the manager must be prepared.
5
secured using physical security controls and shall not be allowed to be carried outside of the
office. These shall be placed in the secure vaults and must not be allowed to be accessed by
anyone except the vault manager. A log book of users accessing the vault with consent from
the manager must be prepared.
5

Critical Role of Cryptography in Information Security
Three Main Types of Cryptography Algorithms
Secret Key Algorithms
These are the cryptography algorithms that are also referred as the symmetric algorithms. In
these measures, there is a same key that is used for the purpose of data encryption and
decryption. For example, if in a string of text, every alphabet is replaced by its successor then
the receiver will not be able to guess the message unless the key is shared. One of the
problems of this form of cryptography algorithm is the security of the key that is involved.
The keys are transmitted from the sender to the receiver’s end and are exposed to security
threats and risks. Data Encryption Standard (DES) and Triple Data Encryption Standard (3-
DES) are the algorithms that are primarily used under this category.
Public Key Algorithms
Public Key Cryptography is also referred as asymmetric cryptography that makes use of
different keys for the purpose of encryption and decryption. In these algorithms, there are
public and private keys that are involved. The encryption of the message is done with the aid
of a public key and the decryption of the message is carried out using private key. Key
management and security of the keys in this case is better than symmetric algorithms. It is not
possible to guess or capture the private key using the public key used for encryption. RSA
and Elliptic Curve Cryptography are the examples of this algorithm.
Hash Functions
The third major category of cryptography algorithms is the hash functions. These are the
functions that take input in the form of message and provide a fixed size string of alpha-
numeric characters in response (Wang et al., 2017). These functions are applied in a variety
of applications, such as digital signatures, integrity checks, and likewise. SHA-256 is one of
the primary hash functions that is used for cryptography.
6
Three Main Types of Cryptography Algorithms
Secret Key Algorithms
These are the cryptography algorithms that are also referred as the symmetric algorithms. In
these measures, there is a same key that is used for the purpose of data encryption and
decryption. For example, if in a string of text, every alphabet is replaced by its successor then
the receiver will not be able to guess the message unless the key is shared. One of the
problems of this form of cryptography algorithm is the security of the key that is involved.
The keys are transmitted from the sender to the receiver’s end and are exposed to security
threats and risks. Data Encryption Standard (DES) and Triple Data Encryption Standard (3-
DES) are the algorithms that are primarily used under this category.
Public Key Algorithms
Public Key Cryptography is also referred as asymmetric cryptography that makes use of
different keys for the purpose of encryption and decryption. In these algorithms, there are
public and private keys that are involved. The encryption of the message is done with the aid
of a public key and the decryption of the message is carried out using private key. Key
management and security of the keys in this case is better than symmetric algorithms. It is not
possible to guess or capture the private key using the public key used for encryption. RSA
and Elliptic Curve Cryptography are the examples of this algorithm.
Hash Functions
The third major category of cryptography algorithms is the hash functions. These are the
functions that take input in the form of message and provide a fixed size string of alpha-
numeric characters in response (Wang et al., 2017). These functions are applied in a variety
of applications, such as digital signatures, integrity checks, and likewise. SHA-256 is one of
the primary hash functions that is used for cryptography.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
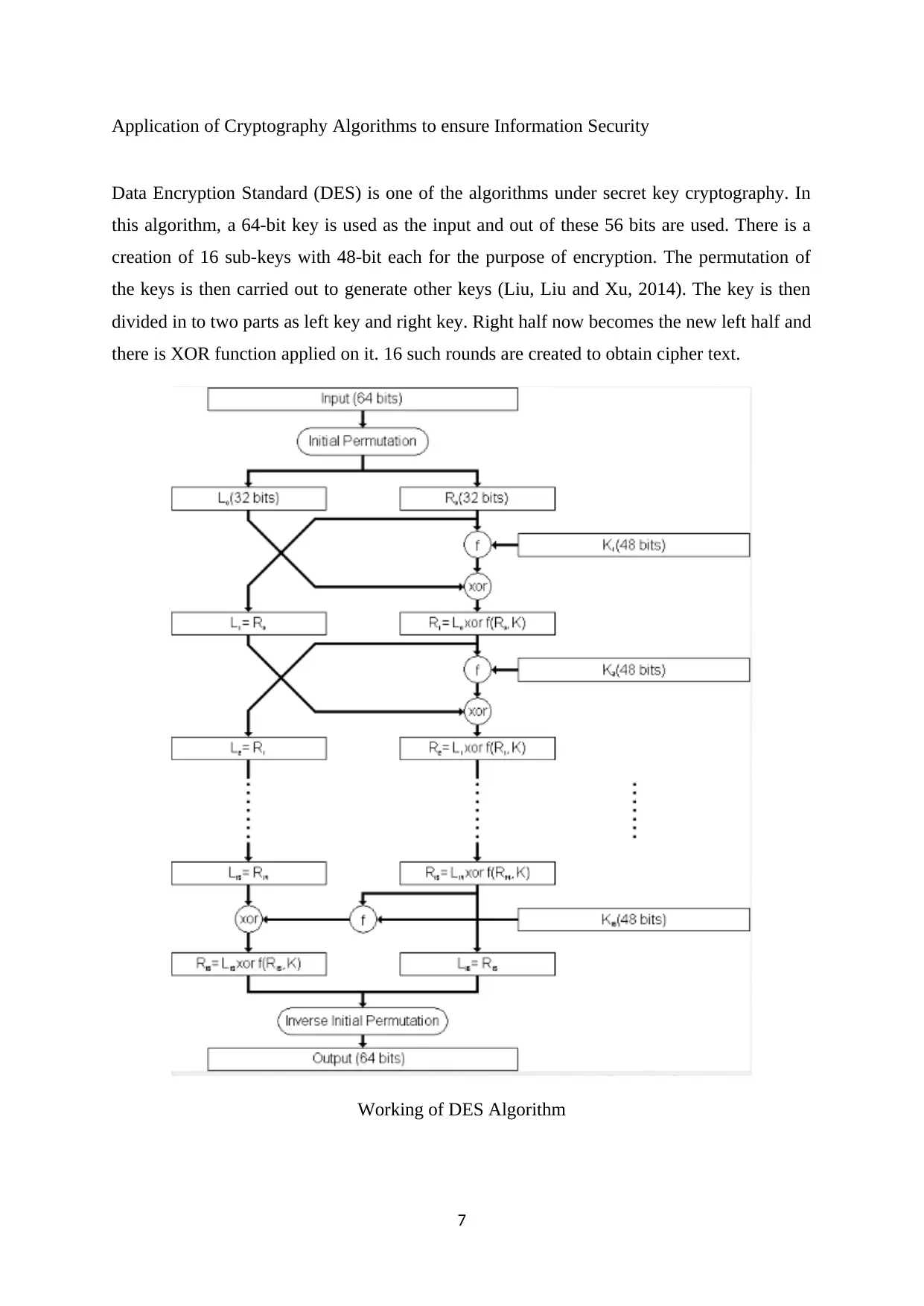
Application of Cryptography Algorithms to ensure Information Security
Data Encryption Standard (DES) is one of the algorithms under secret key cryptography. In
this algorithm, a 64-bit key is used as the input and out of these 56 bits are used. There is a
creation of 16 sub-keys with 48-bit each for the purpose of encryption. The permutation of
the keys is then carried out to generate other keys (Liu, Liu and Xu, 2014). The key is then
divided in to two parts as left key and right key. Right half now becomes the new left half and
there is XOR function applied on it. 16 such rounds are created to obtain cipher text.
Working of DES Algorithm
7
Data Encryption Standard (DES) is one of the algorithms under secret key cryptography. In
this algorithm, a 64-bit key is used as the input and out of these 56 bits are used. There is a
creation of 16 sub-keys with 48-bit each for the purpose of encryption. The permutation of
the keys is then carried out to generate other keys (Liu, Liu and Xu, 2014). The key is then
divided in to two parts as left key and right key. Right half now becomes the new left half and
there is XOR function applied on it. 16 such rounds are created to obtain cipher text.
Working of DES Algorithm
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
The algorithm is used and applied in the area of computer network data security and for
secure communications. Using the above flow, the text strings are converted to their cipher
forms and are transmitted over the networks. The attackers present on the network fail to
obtain the meaning and contents of the message without the presence of security key (Gong
et al., 2017).
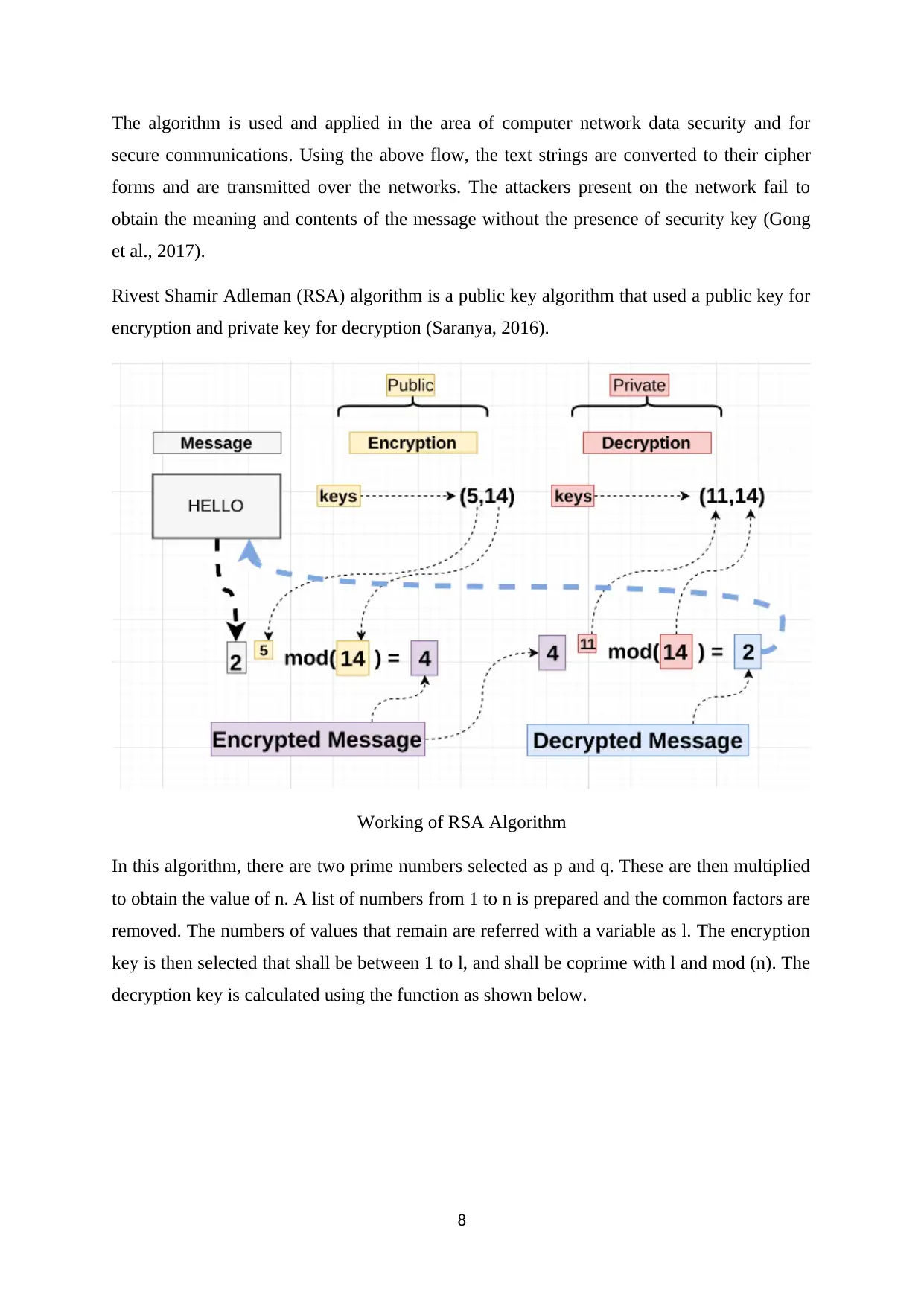
Rivest Shamir Adleman (RSA) algorithm is a public key algorithm that used a public key for
encryption and private key for decryption (Saranya, 2016).
Working of RSA Algorithm
In this algorithm, there are two prime numbers selected as p and q. These are then multiplied
to obtain the value of n. A list of numbers from 1 to n is prepared and the common factors are
removed. The numbers of values that remain are referred with a variable as l. The encryption
key is then selected that shall be between 1 to l, and shall be coprime with l and mod (n). The
decryption key is calculated using the function as shown below.
8
secure communications. Using the above flow, the text strings are converted to their cipher
forms and are transmitted over the networks. The attackers present on the network fail to
obtain the meaning and contents of the message without the presence of security key (Gong
et al., 2017).
Rivest Shamir Adleman (RSA) algorithm is a public key algorithm that used a public key for
encryption and private key for decryption (Saranya, 2016).
Working of RSA Algorithm
In this algorithm, there are two prime numbers selected as p and q. These are then multiplied
to obtain the value of n. A list of numbers from 1 to n is prepared and the common factors are
removed. The numbers of values that remain are referred with a variable as l. The encryption
key is then selected that shall be between 1 to l, and shall be coprime with l and mod (n). The
decryption key is calculated using the function as shown below.
8

Decryption Key
In this manner, the algorithm is used in hybrid encryptions along with the digital signatures.
SHA-1 is one of the hash functions that are used for the purpose of cryptography. The
function works by a set of steps. In the first step, five variables as H0, H1, H2, H3, and H4
are created. The work or message that shall be hashed is then determined. The work is then
converted to its ASCII form. The ASCII form of the work is then converted to its binary
form. The binary characters are joined and are added with a 1 at the end. There are zeros
appended at the end of the code such that the total length is 448 mod 512. The original
message length is then added to the 64 bit field left after appending the zeros. The message is
then broken up in to sixteen sections with each section of 32 bits. Step loop function is then
applied to convert it in to 80 words (Preneel, 2010). The five variables that were set up in the
initial phase are applied with AND, OR, and NOT functions. H variables are then converted
to hex. The variables are then joined to obtain the hash function.
9
In this manner, the algorithm is used in hybrid encryptions along with the digital signatures.
SHA-1 is one of the hash functions that are used for the purpose of cryptography. The
function works by a set of steps. In the first step, five variables as H0, H1, H2, H3, and H4
are created. The work or message that shall be hashed is then determined. The work is then
converted to its ASCII form. The ASCII form of the work is then converted to its binary
form. The binary characters are joined and are added with a 1 at the end. There are zeros
appended at the end of the code such that the total length is 448 mod 512. The original
message length is then added to the 64 bit field left after appending the zeros. The message is
then broken up in to sixteen sections with each section of 32 bits. Step loop function is then
applied to convert it in to 80 words (Preneel, 2010). The five variables that were set up in the
initial phase are applied with AND, OR, and NOT functions. H variables are then converted
to hex. The variables are then joined to obtain the hash function.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

List of References
Gong, L., Zhang, L., Zhang, W., Li, X., Wang, X. and Pan, W. (2017). The application of
data encryption technology in computer network communication security.
Hammonds, O. (2018). 3 Benefits Of Using Server Racks - 3 Benefits Of. [online] 3 Benefits
Of. Available at: http://www.3benefitsof.com/3-benefits-of-using-server-racks/ [Accessed 23
Aug. 2018].
Liu, D., Liu, W. and Xu, J. (2014). The Application of DES Encryption and Decryption
Algorithm in the STS Protocol. Applied Mechanics and Materials, 644-650, pp.2202-2205.
Preneel, B. (2010). Cryptographic hash functions. European Transactions on
Telecommunications, 5(4), pp.431-448.
Saranya, R. (2016). Image Encryption using RSA Algorithm with Biometric Recognition.
International Journal Of Engineering And Computer Science.
Schultz, E. (2007). Risks due to convergence of physical security systems and information
technology environments. Information Security Technical Report, 12(2), pp.80-84.
Sinha, A., Nguyen, T., Kar, D., Brown, M., Tambe, M. and Jiang, A. (2015). From physical
security to cybersecurity. Journal of Cybersecurity, p.tyv007.
Wang, D., Jiang, Y., Song, H., He, F., Gu, M. and Sun, J. (2017). Verification of
Implementations of Cryptographic Hash Functions. IEEE Access, 5, pp.7816-7825.
10
Gong, L., Zhang, L., Zhang, W., Li, X., Wang, X. and Pan, W. (2017). The application of
data encryption technology in computer network communication security.
Hammonds, O. (2018). 3 Benefits Of Using Server Racks - 3 Benefits Of. [online] 3 Benefits
Of. Available at: http://www.3benefitsof.com/3-benefits-of-using-server-racks/ [Accessed 23
Aug. 2018].
Liu, D., Liu, W. and Xu, J. (2014). The Application of DES Encryption and Decryption
Algorithm in the STS Protocol. Applied Mechanics and Materials, 644-650, pp.2202-2205.
Preneel, B. (2010). Cryptographic hash functions. European Transactions on
Telecommunications, 5(4), pp.431-448.
Saranya, R. (2016). Image Encryption using RSA Algorithm with Biometric Recognition.
International Journal Of Engineering And Computer Science.
Schultz, E. (2007). Risks due to convergence of physical security systems and information
technology environments. Information Security Technical Report, 12(2), pp.80-84.
Sinha, A., Nguyen, T., Kar, D., Brown, M., Tambe, M. and Jiang, A. (2015). From physical
security to cybersecurity. Journal of Cybersecurity, p.tyv007.
Wang, D., Jiang, Y., Song, H., He, F., Gu, M. and Sun, J. (2017). Verification of
Implementations of Cryptographic Hash Functions. IEEE Access, 5, pp.7816-7825.
10
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





