Comprehensive Review of VANET Routing Protocols in Information Systems
VerifiedAdded on 2022/01/18
|9
|2759
|177
Report
AI Summary
This report provides a comprehensive review and analysis of Vehicular Ad-hoc Network (VANET) routing protocols. It begins with an introduction to information systems and VANETs, highlighting their importance in modern applications, particularly in smart road safety and management. The report then delves into the main components of VANETs, including communication methods (V2V and V2I) and routing protocols. The core of the report focuses on the classification of VANET routing protocols, categorizing them into topology-based, position-based, multicast-based, and broadcast-based protocols. Detailed explanations are given for each type, including specific protocols like GPSR and GSR, and their applications. The report also covers the components of information systems, including hardware, software, and telecommunications. This detailed review provides insights into the complexities and advancements of VANET routing protocols, offering a valuable resource for understanding and further research in this field. The report is intended to be a resource for students, and similar assignments can be found on Desklib.

INTRODUCTION
Information system, an integrated set of components for collecting, storing, and processing
data and for providing information, knowledge, and digital products. Business firms and
other organizations rely on information systems to carry out and manage their operations,
interact with their customers and suppliers, and compete in the marketplace. Information
systems are used to run interorganizational supply chains and electronic markets. For
instance, corporations use information systems to process financial accounts, to manage their
human resources, and to reach their potential customers with online promotions. Many major
companies are built entirely around information systems. These include ebay, a largely
auction marketplace; amazon, an expanding electronic mall and provider of cloud
computing services; alibaba, a business-to-business e-marketplace; and google, a search
engine company that derives most of its revenue from keyword advertising
on internet searches. Governments deploy information systems to provide services cost-
effectively to citizens. Digital goods—such as electronic books, video products, and software
—and online services, such as gaming and social networking, are delivered with information
systems. Individuals rely on information systems, generally internet-based, for conducting
much of their personal lives: for socializing, study, shopping, banking, and entertainment
(Bengag et al., 2020).
The main reason why Vehicular Ad-hoc Network (VANET) has become the most popular
research study is due to the growing demand for smart road safety and management. VANET
is part or subclass of the mobile Ad-Hoc network (MANET)(Abu Taleb, 2018). Even though
VANET is the subclass of MANET but there is a difference between VANET and MANET.
The main difference between MANET and VANET is the mobility pattern and sudden
topologies changing. The basic component in VANET is Communication – Wireless Access
in Vehicular Environment (WAVE-IEEE 1609.2 also known as DSRC 802.11p, Multi-hop
communication, On-Board unit (OBU), and Roadside unit (RSU). Vehicle to vehicle (V2V)
uses multi-hop or multi-cast technique with two types of broadcasting which are native and
intelligent broadcasting. For Vehicle to infrastructure (V2I), it’s used roadside equipment
(RSU) to establish communication(Rizwan Ghori et al., 2018b). V2I communication modes
are inadequate for applications related to road safety because the infrastructure networks are
not performing as to delivery time. The combination of the V2V and V2I is called hybrid.
Figure 1 illustrated the VANET communication. In this study, I will review and analyze the
various types of VANET routing protocols.
1
Information system, an integrated set of components for collecting, storing, and processing
data and for providing information, knowledge, and digital products. Business firms and
other organizations rely on information systems to carry out and manage their operations,
interact with their customers and suppliers, and compete in the marketplace. Information
systems are used to run interorganizational supply chains and electronic markets. For
instance, corporations use information systems to process financial accounts, to manage their
human resources, and to reach their potential customers with online promotions. Many major
companies are built entirely around information systems. These include ebay, a largely
auction marketplace; amazon, an expanding electronic mall and provider of cloud
computing services; alibaba, a business-to-business e-marketplace; and google, a search
engine company that derives most of its revenue from keyword advertising
on internet searches. Governments deploy information systems to provide services cost-
effectively to citizens. Digital goods—such as electronic books, video products, and software
—and online services, such as gaming and social networking, are delivered with information
systems. Individuals rely on information systems, generally internet-based, for conducting
much of their personal lives: for socializing, study, shopping, banking, and entertainment
(Bengag et al., 2020).
The main reason why Vehicular Ad-hoc Network (VANET) has become the most popular
research study is due to the growing demand for smart road safety and management. VANET
is part or subclass of the mobile Ad-Hoc network (MANET)(Abu Taleb, 2018). Even though
VANET is the subclass of MANET but there is a difference between VANET and MANET.
The main difference between MANET and VANET is the mobility pattern and sudden
topologies changing. The basic component in VANET is Communication – Wireless Access
in Vehicular Environment (WAVE-IEEE 1609.2 also known as DSRC 802.11p, Multi-hop
communication, On-Board unit (OBU), and Roadside unit (RSU). Vehicle to vehicle (V2V)
uses multi-hop or multi-cast technique with two types of broadcasting which are native and
intelligent broadcasting. For Vehicle to infrastructure (V2I), it’s used roadside equipment
(RSU) to establish communication(Rizwan Ghori et al., 2018b). V2I communication modes
are inadequate for applications related to road safety because the infrastructure networks are
not performing as to delivery time. The combination of the V2V and V2I is called hybrid.
Figure 1 illustrated the VANET communication. In this study, I will review and analyze the
various types of VANET routing protocols.
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

As major new technologies for recording and processing information were invented over the
millennia, new capabilities appeared, and people became empowered. The invention of
the printing press by Johannes Gutenberg in the mid-15th century and the invention of a
mechanical calculator by Blaise Pascal in the 17th century are but two examples. These
inventions led to a profound revolution in the ability to record, process, disseminate, and
reach for information and knowledge. This led, in turn, to even deeper changes in individual
lives, business organization, and human governance.
The first large-scale mechanical information system was Herman Hollerith’s census
tabulator. Invented in time to process the 1890 U.S. census, Hollerith’s machine represented a
major step in automation, as well as an inspiration to develop computerized information
systems.
One of the first computers used for such information processing was the UNIVAC I, installed
at the U.S. Bureau of the Census in 1951 for administrative use and at General Electric in
1954 for commercial use. Beginning in the late 1970s, personal computers brought some of
the advantages of information systems to small businesses and to individuals. Early in the
same decade the Internet began its expansion as the global network of networks. In 1991
the World Wide Web, invented by Tim Berners-Lee as a means to access the interlinked
information stored in the globally dispersed computers connected by the Internet, began
operation and became the principal service delivered on the network. The global penetration
of the Internet and the Web has enabled access to information and other resources
and facilitated the forming of relationships among people and organizations on an
unprecedented scale. The progress of electronic commerce over the Internet has resulted in a
dramatic growth in digital interpersonal communications (via e-mail and social networks),
distribution of products (software, music, e-books, and movies), and business transactions
(buying, selling, and advertising on the Web). With the worldwide spread
of smartphones, tablets, laptops, and other computer-based mobile devices, all of which are
connected by wireless communication networks, information systems have been extended to
support mobility as the natural human condition (Bengag et al., 2020).
As information systems enabled more diverse human activities, they exerted a profound
influence over society. These systems quickened the pace of daily activities, enabled people
to develop and maintain new and often more-rewarding relationships, affected the structure
and mix of organizations, changed the type of products bought, and influenced the nature of
work. Information and knowledge became vital economic resources. Yet, along with new
opportunities, the dependence on information systems brought new threats. Intensive
industry innovation and academic research continually develop new opportunities while
aiming to contain the threats.
Components of information systems
2
millennia, new capabilities appeared, and people became empowered. The invention of
the printing press by Johannes Gutenberg in the mid-15th century and the invention of a
mechanical calculator by Blaise Pascal in the 17th century are but two examples. These
inventions led to a profound revolution in the ability to record, process, disseminate, and
reach for information and knowledge. This led, in turn, to even deeper changes in individual
lives, business organization, and human governance.
The first large-scale mechanical information system was Herman Hollerith’s census
tabulator. Invented in time to process the 1890 U.S. census, Hollerith’s machine represented a
major step in automation, as well as an inspiration to develop computerized information
systems.
One of the first computers used for such information processing was the UNIVAC I, installed
at the U.S. Bureau of the Census in 1951 for administrative use and at General Electric in
1954 for commercial use. Beginning in the late 1970s, personal computers brought some of
the advantages of information systems to small businesses and to individuals. Early in the
same decade the Internet began its expansion as the global network of networks. In 1991
the World Wide Web, invented by Tim Berners-Lee as a means to access the interlinked
information stored in the globally dispersed computers connected by the Internet, began
operation and became the principal service delivered on the network. The global penetration
of the Internet and the Web has enabled access to information and other resources
and facilitated the forming of relationships among people and organizations on an
unprecedented scale. The progress of electronic commerce over the Internet has resulted in a
dramatic growth in digital interpersonal communications (via e-mail and social networks),
distribution of products (software, music, e-books, and movies), and business transactions
(buying, selling, and advertising on the Web). With the worldwide spread
of smartphones, tablets, laptops, and other computer-based mobile devices, all of which are
connected by wireless communication networks, information systems have been extended to
support mobility as the natural human condition (Bengag et al., 2020).
As information systems enabled more diverse human activities, they exerted a profound
influence over society. These systems quickened the pace of daily activities, enabled people
to develop and maintain new and often more-rewarding relationships, affected the structure
and mix of organizations, changed the type of products bought, and influenced the nature of
work. Information and knowledge became vital economic resources. Yet, along with new
opportunities, the dependence on information systems brought new threats. Intensive
industry innovation and academic research continually develop new opportunities while
aiming to contain the threats.
Components of information systems
2

The main components of information systems are computer hardware and software,
telecommunications, databases and data warehouses, human resources, and procedures. The
hardware, software, and telecommunications constitute information technology (IT), which is
now ingrained in the operations and management of organizations (Bengag et al., 2020).
Computer hardware
Today throughout the world even the smallest firms, as well as many households, own or
lease computers. Individuals may own multiple computers in the form
of smartphones, tablets, and other wearable devices. Large organizations typically employ
distributed computer systems, from powerful parallel-processing servers located in data
centres to widely dispersed personal computers and mobile devices, integrated into the
organizational information systems.
Sensors are becoming ever more widely distributed throughout the physical and
biological environment to gather data and, in many cases, to effect control via devices known
as actuators. Together with the peripheral equipment—such as magnetic or solid-state storage
disks, input-output devices, and telecommunications gear—these constitute the hardware of
information systems. The cost of hardware has steadily and rapidly decreased, while
processing speed and storage capacity have increased vastly. This development has been
occurring under Moore’s law: the power of the microprocessors at the heart of computing
devices has been doubling approximately every 18 to 24 months. However, hardware’s use
of electric power and its environmental impact are concerns being addressed by designers.
Increasingly, computer and storage services are delivered from the cloud—from shared
facilities accessed over telecommunications networks.
Computer software
Computer software falls into two broad classes: system software and application software.
The principal system software is the operating system. It manages the hardware, data and
program files, and other system resources and provides means for the user to control the
computer, generally via a graphical user interface (GUI). Application software is programs
designed to handle specific tasks for users. Smartphone apps became a common way for
individuals to access information systems. Other examples include general-purpose
application suites with their spreadsheet and word-processing programs, as well as “vertical”
applications that serve a specific industry segment—for instance, an application that
schedules, routes, and tracks package deliveries for an overnight carrier. Larger firms use
licensed applications developed and maintained by specialized software companies,
customizing them to meet their specific needs, and develop other applications in-house or on
an outsourced basis. Companies may also use applications delivered as software-as-a-service
(SaaS) from the cloud over the Web. Proprietary software, available from and supported by
its vendors, is being challenged by open-source software available on the Web for free use
and modification under a license that protects its future availability (Bengag et al., 2020).
Telecommunications
3
telecommunications, databases and data warehouses, human resources, and procedures. The
hardware, software, and telecommunications constitute information technology (IT), which is
now ingrained in the operations and management of organizations (Bengag et al., 2020).
Computer hardware
Today throughout the world even the smallest firms, as well as many households, own or
lease computers. Individuals may own multiple computers in the form
of smartphones, tablets, and other wearable devices. Large organizations typically employ
distributed computer systems, from powerful parallel-processing servers located in data
centres to widely dispersed personal computers and mobile devices, integrated into the
organizational information systems.
Sensors are becoming ever more widely distributed throughout the physical and
biological environment to gather data and, in many cases, to effect control via devices known
as actuators. Together with the peripheral equipment—such as magnetic or solid-state storage
disks, input-output devices, and telecommunications gear—these constitute the hardware of
information systems. The cost of hardware has steadily and rapidly decreased, while
processing speed and storage capacity have increased vastly. This development has been
occurring under Moore’s law: the power of the microprocessors at the heart of computing
devices has been doubling approximately every 18 to 24 months. However, hardware’s use
of electric power and its environmental impact are concerns being addressed by designers.
Increasingly, computer and storage services are delivered from the cloud—from shared
facilities accessed over telecommunications networks.
Computer software
Computer software falls into two broad classes: system software and application software.
The principal system software is the operating system. It manages the hardware, data and
program files, and other system resources and provides means for the user to control the
computer, generally via a graphical user interface (GUI). Application software is programs
designed to handle specific tasks for users. Smartphone apps became a common way for
individuals to access information systems. Other examples include general-purpose
application suites with their spreadsheet and word-processing programs, as well as “vertical”
applications that serve a specific industry segment—for instance, an application that
schedules, routes, and tracks package deliveries for an overnight carrier. Larger firms use
licensed applications developed and maintained by specialized software companies,
customizing them to meet their specific needs, and develop other applications in-house or on
an outsourced basis. Companies may also use applications delivered as software-as-a-service
(SaaS) from the cloud over the Web. Proprietary software, available from and supported by
its vendors, is being challenged by open-source software available on the Web for free use
and modification under a license that protects its future availability (Bengag et al., 2020).
Telecommunications
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Telecommunications are used to connect, or network, computer systems and portable and
wearable devices and to transmit information. Connections are established via wired or
wireless media. Wired technologies include coaxial cable and fibre optics. Wireless
technologies, predominantly based on the transmission of microwaves and radio waves,
support mobile computing. Pervasive information systems have arisen with the computing
devices embedded in many different physical objects. For example, sensors such as radio
frequency identification devices (RFIDs) can be attached to products moving through the
supply chain to enable the tracking of their location and the monitoring of their condition.
Wireless sensor networks that are integrated into the Internet can produce massive amounts
of data that can be used in seeking higher productivity or in monitoring the environment.
Various computer network configurations are possible, depending on the needs of an
organization. Local area networks (LANs) join computers at a particular site, such as an
office building or an academic campus. Metropolitan area networks (MANs) cover a limited
densely populated area and are the electronic infrastructure of “smart cities.” Wide area
networks (WANs) connect widely distributed data centres, frequently run by different
organizations. Peer-to-peer networks, without a centralized control, enable broad sharing of
content. The Internet is a network of networks, connecting billions of computers located on
every continent. Through networking, users gain access to information resources, such as
large databases, and to other individuals, such as coworkers, clients, friends, or people who
share their professional or private interests. Internet-type services can be provided within an
organization and for its exclusive use by various intranets that are accessible through
a browser; for example, an intranet may be deployed as an access portal to a shared corporate
document base. To connect with business partners over the Internet in a private and secure
manner, extranets are established as so-called virtual private networks (VPNs) by encrypting
the messages massive “Internet of things” has emerged, as sensors and actuators have been
widely distributed in the physical environment and are supplying data, such as acidity of a
square yard of soil, the speed of a driving vehicle, or the blood pressure of an individual. The
availability of such information enables a rapid reaction when necessary as well as
sustained decision making based on processing of the massive accumulated data.
Extensive networking infrastructure supports the growing move to cloud computing, with the
information-system resources shared among multiple companies, leading to
utilization efficiencies and freedom in localization of the data centres. Software-defined
networking affords flexible control of telecommunications networks with algorithms that are
responsive to real-time demands and resource availabilities.
VEHICULAR AD-HOC NETWORK (VANET) ROUTING PROTOCOL
Based research paper (Bengag et al., 2020) some improvement has been made on VANET
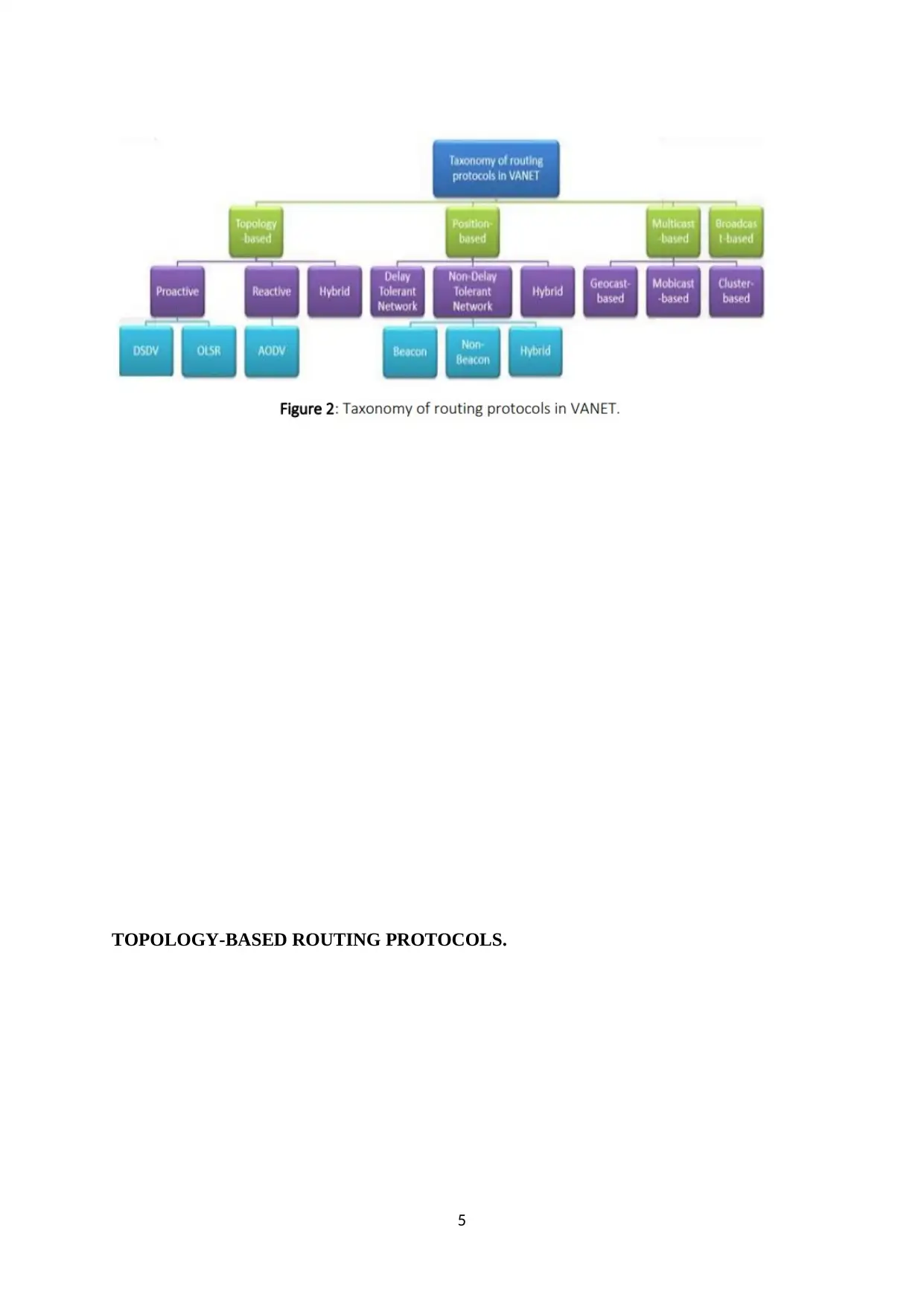
routing topology thus the routing split into four categories as follow [Figure 2];
1. Topology-based routing protocols
2. Position-based routing protocols
3. Multicast-based routing protocols
4. Broadcast-based routing protocols
4
wearable devices and to transmit information. Connections are established via wired or
wireless media. Wired technologies include coaxial cable and fibre optics. Wireless
technologies, predominantly based on the transmission of microwaves and radio waves,
support mobile computing. Pervasive information systems have arisen with the computing
devices embedded in many different physical objects. For example, sensors such as radio
frequency identification devices (RFIDs) can be attached to products moving through the
supply chain to enable the tracking of their location and the monitoring of their condition.
Wireless sensor networks that are integrated into the Internet can produce massive amounts
of data that can be used in seeking higher productivity or in monitoring the environment.
Various computer network configurations are possible, depending on the needs of an
organization. Local area networks (LANs) join computers at a particular site, such as an
office building or an academic campus. Metropolitan area networks (MANs) cover a limited
densely populated area and are the electronic infrastructure of “smart cities.” Wide area
networks (WANs) connect widely distributed data centres, frequently run by different
organizations. Peer-to-peer networks, without a centralized control, enable broad sharing of
content. The Internet is a network of networks, connecting billions of computers located on
every continent. Through networking, users gain access to information resources, such as
large databases, and to other individuals, such as coworkers, clients, friends, or people who
share their professional or private interests. Internet-type services can be provided within an
organization and for its exclusive use by various intranets that are accessible through
a browser; for example, an intranet may be deployed as an access portal to a shared corporate
document base. To connect with business partners over the Internet in a private and secure
manner, extranets are established as so-called virtual private networks (VPNs) by encrypting
the messages massive “Internet of things” has emerged, as sensors and actuators have been
widely distributed in the physical environment and are supplying data, such as acidity of a
square yard of soil, the speed of a driving vehicle, or the blood pressure of an individual. The
availability of such information enables a rapid reaction when necessary as well as
sustained decision making based on processing of the massive accumulated data.
Extensive networking infrastructure supports the growing move to cloud computing, with the
information-system resources shared among multiple companies, leading to
utilization efficiencies and freedom in localization of the data centres. Software-defined
networking affords flexible control of telecommunications networks with algorithms that are
responsive to real-time demands and resource availabilities.
VEHICULAR AD-HOC NETWORK (VANET) ROUTING PROTOCOL
Based research paper (Bengag et al., 2020) some improvement has been made on VANET
routing topology thus the routing split into four categories as follow [Figure 2];
1. Topology-based routing protocols
2. Position-based routing protocols
3. Multicast-based routing protocols
4. Broadcast-based routing protocols
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
TOPOLOGY-BASED ROUTING PROTOCOLS.
5
5
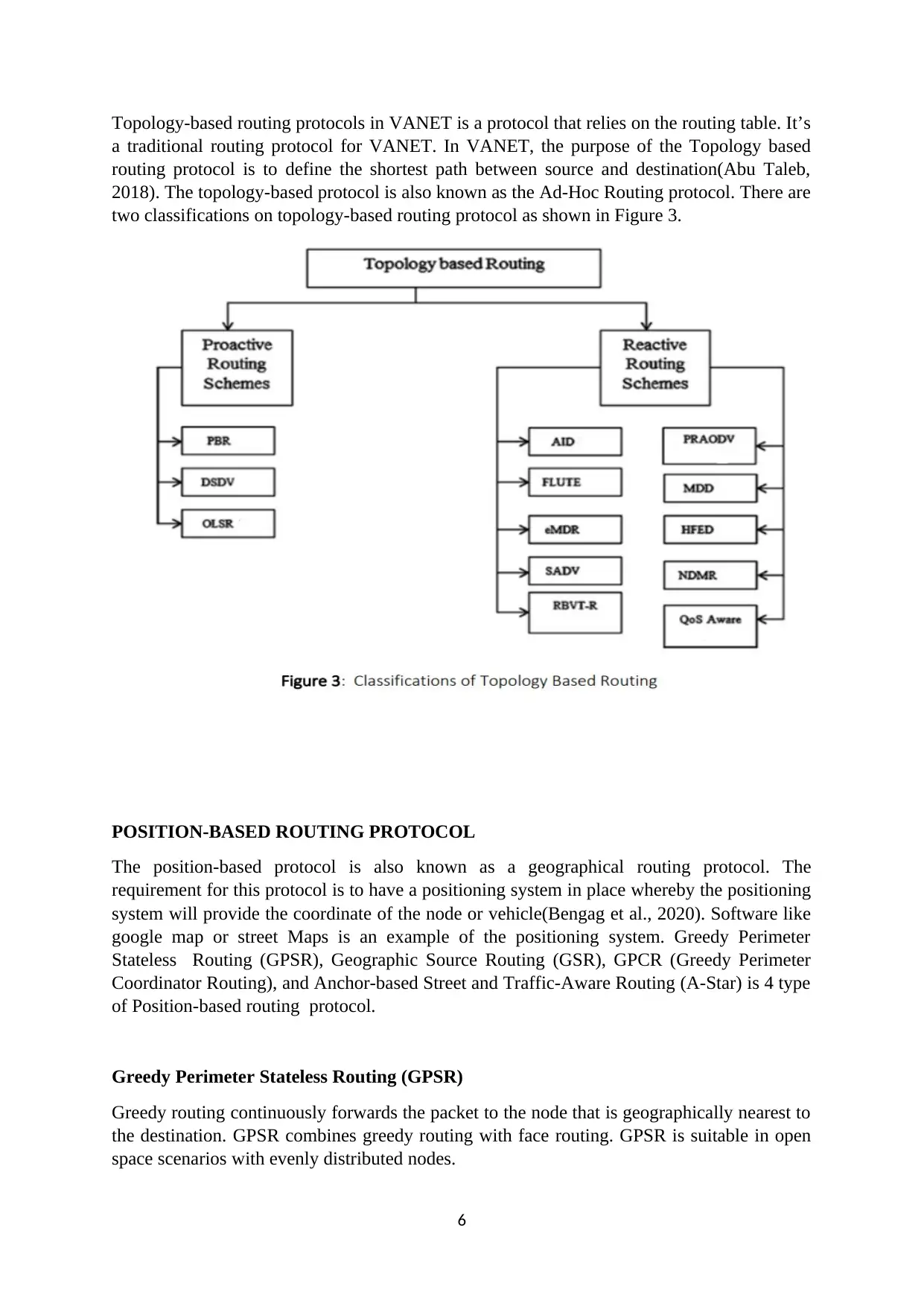
Topology-based routing protocols in VANET is a protocol that relies on the routing table. It’s
a traditional routing protocol for VANET. In VANET, the purpose of the Topology based
routing protocol is to define the shortest path between source and destination(Abu Taleb,
2018). The topology-based protocol is also known as the Ad-Hoc Routing protocol. There are
two classifications on topology-based routing protocol as shown in Figure 3.
POSITION-BASED ROUTING PROTOCOL
The position-based protocol is also known as a geographical routing protocol. The
requirement for this protocol is to have a positioning system in place whereby the positioning
system will provide the coordinate of the node or vehicle(Bengag et al., 2020). Software like
google map or street Maps is an example of the positioning system. Greedy Perimeter
Stateless Routing (GPSR), Geographic Source Routing (GSR), GPCR (Greedy Perimeter
Coordinator Routing), and Anchor-based Street and Traffic-Aware Routing (A-Star) is 4 type
of Position-based routing protocol.
Greedy Perimeter Stateless Routing (GPSR)
Greedy routing continuously forwards the packet to the node that is geographically nearest to
the destination. GPSR combines greedy routing with face routing. GPSR is suitable in open
space scenarios with evenly distributed nodes.
6
a traditional routing protocol for VANET. In VANET, the purpose of the Topology based
routing protocol is to define the shortest path between source and destination(Abu Taleb,
2018). The topology-based protocol is also known as the Ad-Hoc Routing protocol. There are
two classifications on topology-based routing protocol as shown in Figure 3.
POSITION-BASED ROUTING PROTOCOL
The position-based protocol is also known as a geographical routing protocol. The
requirement for this protocol is to have a positioning system in place whereby the positioning
system will provide the coordinate of the node or vehicle(Bengag et al., 2020). Software like
google map or street Maps is an example of the positioning system. Greedy Perimeter
Stateless Routing (GPSR), Geographic Source Routing (GSR), GPCR (Greedy Perimeter
Coordinator Routing), and Anchor-based Street and Traffic-Aware Routing (A-Star) is 4 type
of Position-based routing protocol.
Greedy Perimeter Stateless Routing (GPSR)
Greedy routing continuously forwards the packet to the node that is geographically nearest to
the destination. GPSR combines greedy routing with face routing. GPSR is suitable in open
space scenarios with evenly distributed nodes.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Geographic Source Routing (GSR)
GSR (Geographic Source Directing) is getting support from street maps in a city
environment. It’s gaining the information or input from global knowledge of the city
topology using the Reactive Location Service (RLS).
GPCR (Greedy Perimeter Coordinator Routing)
GPCR (Greedy Perimeter Coordinator Routing) is not using either source routing (DSR or
GSR) or street map. It’s used the nodes at a junction follow a natural planar graph. Junctions
are where the routing decisions are being taken. Thus, the packets should be forwarded on a
junction rather than past the junction.
Traffic-Aware Routing (A-Star)
A-Star directing is utilizing road outline to compute the arrangement of intersection through
which parcel is arranged to reach the destination. It's quite challenging to deploy A-Star
topology into the built city due the vehicle is not distributed evenly.
MULTICAST-BASED ROUTING PROTOCOLS
Multicast-based routing is a routing based on a multicast technique whereby the data is
transferred from the single source to the group of vehicles using a multi-hop communication
technique. Consists of three categories; protocols based on the geocast technique, based on
the Mobicast technique, and those based on clusters (Bengag et al., 2020).
BROADCAST-BASED ROUTING PROTOCOL
7
GSR (Geographic Source Directing) is getting support from street maps in a city
environment. It’s gaining the information or input from global knowledge of the city
topology using the Reactive Location Service (RLS).
GPCR (Greedy Perimeter Coordinator Routing)
GPCR (Greedy Perimeter Coordinator Routing) is not using either source routing (DSR or
GSR) or street map. It’s used the nodes at a junction follow a natural planar graph. Junctions
are where the routing decisions are being taken. Thus, the packets should be forwarded on a
junction rather than past the junction.
Traffic-Aware Routing (A-Star)
A-Star directing is utilizing road outline to compute the arrangement of intersection through
which parcel is arranged to reach the destination. It's quite challenging to deploy A-Star
topology into the built city due the vehicle is not distributed evenly.
MULTICAST-BASED ROUTING PROTOCOLS
Multicast-based routing is a routing based on a multicast technique whereby the data is
transferred from the single source to the group of vehicles using a multi-hop communication
technique. Consists of three categories; protocols based on the geocast technique, based on
the Mobicast technique, and those based on clusters (Bengag et al., 2020).
BROADCAST-BASED ROUTING PROTOCOL
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
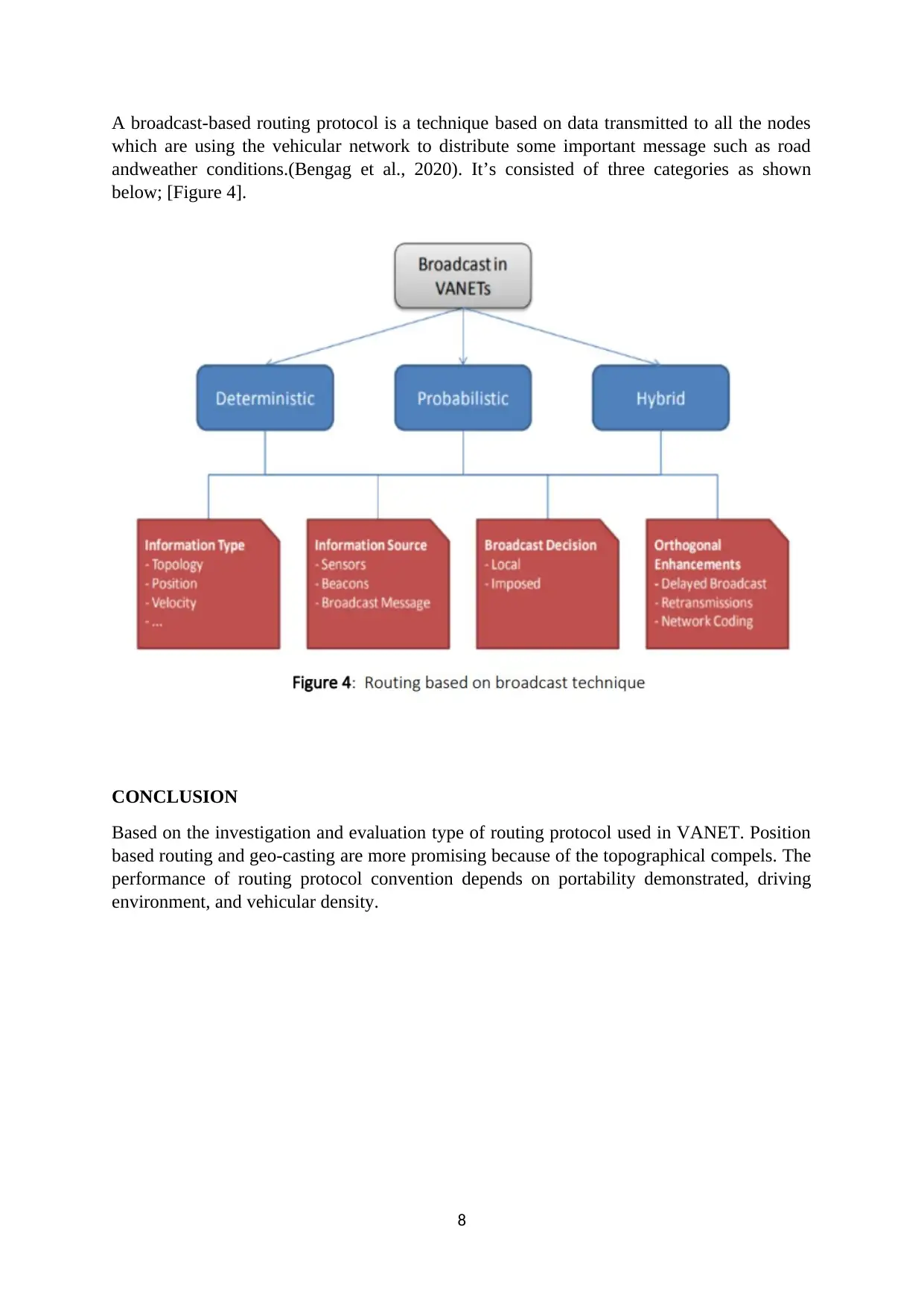
A broadcast-based routing protocol is a technique based on data transmitted to all the nodes
which are using the vehicular network to distribute some important message such as road
andweather conditions.(Bengag et al., 2020). It’s consisted of three categories as shown
below; [Figure 4].
CONCLUSION
Based on the investigation and evaluation type of routing protocol used in VANET. Position
based routing and geo-casting are more promising because of the topographical compels. The
performance of routing protocol convention depends on portability demonstrated, driving
environment, and vehicular density.
8
which are using the vehicular network to distribute some important message such as road
andweather conditions.(Bengag et al., 2020). It’s consisted of three categories as shown
below; [Figure 4].
CONCLUSION
Based on the investigation and evaluation type of routing protocol used in VANET. Position
based routing and geo-casting are more promising because of the topographical compels. The
performance of routing protocol convention depends on portability demonstrated, driving
environment, and vehicular density.
8

REFERENCE
Abu Taleb, A. (2018). VANET routing protocols and architectures: An overview. Journal of
Computer Science, 14(3), 423–434. https://doi.org/10.3844/jcssp.2018.423.434.
Bengag, A., Bengag, A., & Elboukhari, M. (2020). Routing protocols for VANETs: A
taxonomy, evaluation, and analysis. Advances in Science, Technology and
Engineering Systems, 5(1), 77–85. https://doi.org/10.25046/aj050110.
Rizwan Ghori, M., Safa Sadiq, A., & Ghani, A. (2018a). VANET Routing Protocols: Review,
Implementation, and Analysis. Journal of Physics: Conference Series, 1049(1).
https://doi.org/10.1088/1742-6596/1049/1/012064.
Rizwan Ghori, M., Safa Sadiq, A., & Ghani, A. (2018b). VANET Routing Protocols:
Review, Implementation, and Analysis. Journal of Physics: Conference Series,
1049(1). https://doi.org/10.1088/1742-6596/1049/1/012064.
9
Abu Taleb, A. (2018). VANET routing protocols and architectures: An overview. Journal of
Computer Science, 14(3), 423–434. https://doi.org/10.3844/jcssp.2018.423.434.
Bengag, A., Bengag, A., & Elboukhari, M. (2020). Routing protocols for VANETs: A
taxonomy, evaluation, and analysis. Advances in Science, Technology and
Engineering Systems, 5(1), 77–85. https://doi.org/10.25046/aj050110.
Rizwan Ghori, M., Safa Sadiq, A., & Ghani, A. (2018a). VANET Routing Protocols: Review,
Implementation, and Analysis. Journal of Physics: Conference Series, 1049(1).
https://doi.org/10.1088/1742-6596/1049/1/012064.
Rizwan Ghori, M., Safa Sadiq, A., & Ghani, A. (2018b). VANET Routing Protocols:
Review, Implementation, and Analysis. Journal of Physics: Conference Series,
1049(1). https://doi.org/10.1088/1742-6596/1049/1/012064.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




