VANETs: Attacks, Connectivity, and Security
VerifiedAdded on 2019/09/18
|13
|3404
|210
Report
AI Summary
This report provides a comprehensive overview of Vehicular Ad Hoc Networks (VANETs), focusing on their applications, challenges, and future research directions. It delves into the intricacies of Vehicle-to-Vehicle (V2V) and Vehicle-to-Infrastructure (V2I) communication, examining connectivity options, security threats, and potential solutions. The report also explores the use of cognitive radio technologies to address channel limitations and proposes a trust-based security model for V2V communication. Furthermore, it discusses the importance of Quality of Service (QoS) in VANETs and highlights the need for continuous research in this field to enhance road safety and information services. The report concludes by emphasizing the potential of VANETs to improve transportation systems and the need for secure and reliable communication networks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Abstract............................................................................................................................................2
Introduction......................................................................................................................................2
Problem Statement.......................................................................................................................5
Motivation....................................................................................................................................5
Future Research...............................................................................................................................7
Conclusion.......................................................................................................................................8
Abstract............................................................................................................................................2
Introduction......................................................................................................................................2
Problem Statement.......................................................................................................................5
Motivation....................................................................................................................................5
Future Research...............................................................................................................................7
Conclusion.......................................................................................................................................8

Abstract
Vehicle ad hoc network is a champion among the most charming investigation zones in light of
straightforwardness, versatility, adjustment to inside disappointment, high distinguishing
steadiness, making various new and empowering application zones for remote recognizing.
Along these lines, it has ascended as a promising gadget for watching the physical world with
remote sensor that can recognize, process and grant. Their applications reach out from security
and crash avoidance to Internet get to and intuitive media.
VANETs are considered as one of the uniquely selected framework real application enabling
exchanges among adjoining vehicles and moreover among vehicles and close-by settled rigging,
by and large portrayed as roadside equipment. In this paper, we are most stressed over the
examination of VANET applications as it is a propelling field which offers scope for investigate.
Vehicular Ad hoc Networks (VANETs) have created starting late as a champion among the most
charming subjects for researchers and auto wanders in light of their enormous potential to
upgrade development security, viability and other included organizations.
This report shows an outline of VANETs attacks and plans in purposely considering other near
fills in and reviving new ambushes and requesting them into different classes. The report also
explains about an evaluation of the various connectivity options available for V2V is considered,
with an approach considering the communication range, speed, travel direction etc. Also, a trust-
based security model for V2V communication is proposed.
Introduction
The current advances in specially appointed systems have permitted different usage of structures
for vehicular systems. These structures bolster distinctive prerequisites, and fulfill diverse
imperatives. At the point when a thought process is acquainted with the idea of vehicular
systems, whatever he can consider is vehicles conversing with each other. This idea is known as
vehicle-to-vehicle (V2V) specially appointed system, which will be the focal point of this
section.
V2V organize permits the immediate correspondence between vehicles without de-pending on a
settled foundation bolsters. It is just the remote transmission of information between engine
Vehicle ad hoc network is a champion among the most charming investigation zones in light of
straightforwardness, versatility, adjustment to inside disappointment, high distinguishing
steadiness, making various new and empowering application zones for remote recognizing.
Along these lines, it has ascended as a promising gadget for watching the physical world with
remote sensor that can recognize, process and grant. Their applications reach out from security
and crash avoidance to Internet get to and intuitive media.
VANETs are considered as one of the uniquely selected framework real application enabling
exchanges among adjoining vehicles and moreover among vehicles and close-by settled rigging,
by and large portrayed as roadside equipment. In this paper, we are most stressed over the
examination of VANET applications as it is a propelling field which offers scope for investigate.
Vehicular Ad hoc Networks (VANETs) have created starting late as a champion among the most
charming subjects for researchers and auto wanders in light of their enormous potential to
upgrade development security, viability and other included organizations.
This report shows an outline of VANETs attacks and plans in purposely considering other near
fills in and reviving new ambushes and requesting them into different classes. The report also
explains about an evaluation of the various connectivity options available for V2V is considered,
with an approach considering the communication range, speed, travel direction etc. Also, a trust-
based security model for V2V communication is proposed.
Introduction
The current advances in specially appointed systems have permitted different usage of structures
for vehicular systems. These structures bolster distinctive prerequisites, and fulfill diverse
imperatives. At the point when a thought process is acquainted with the idea of vehicular
systems, whatever he can consider is vehicles conversing with each other. This idea is known as
vehicle-to-vehicle (V2V) specially appointed system, which will be the focal point of this
section.
V2V organize permits the immediate correspondence between vehicles without de-pending on a
settled foundation bolsters. It is just the remote transmission of information between engine
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
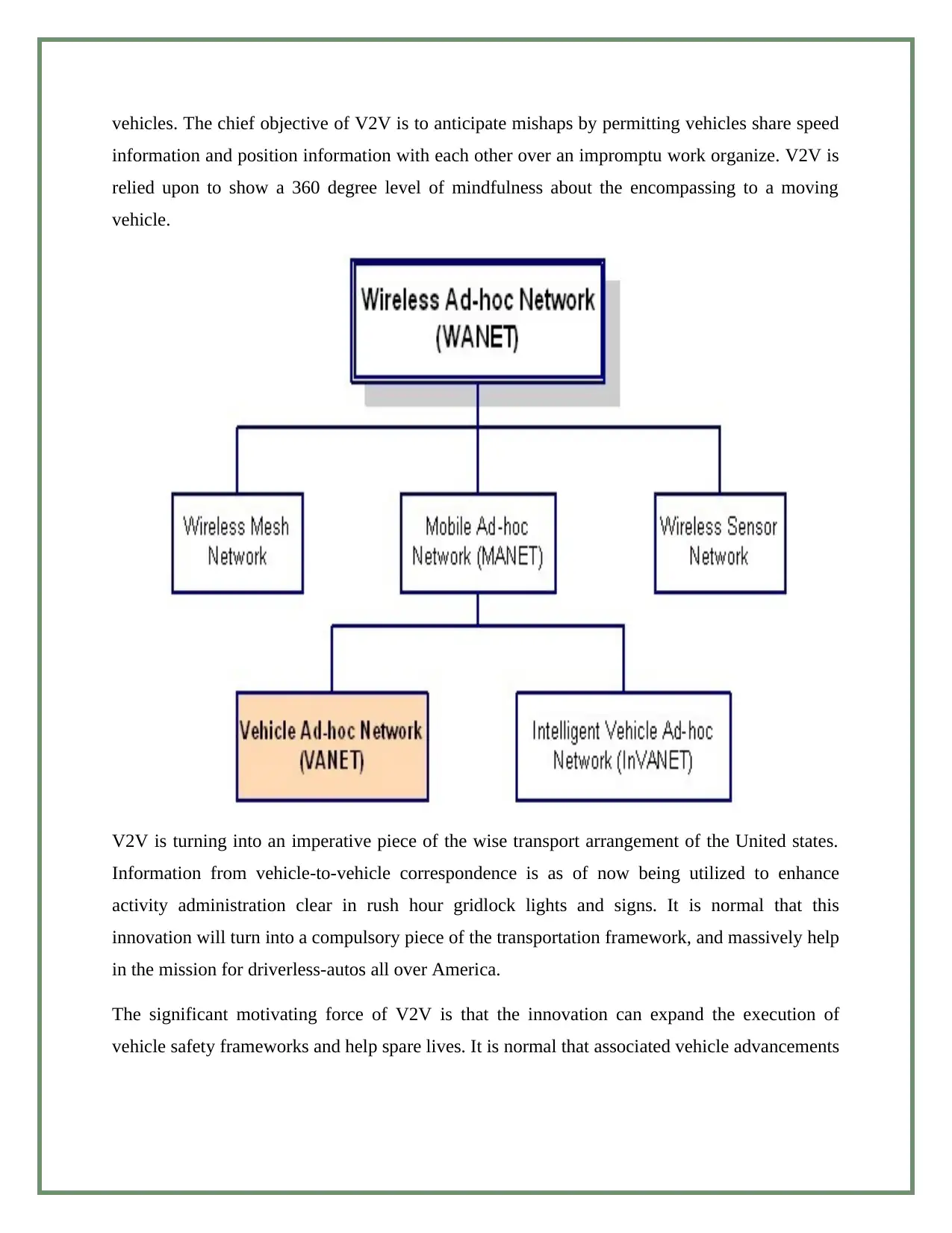
vehicles. The chief objective of V2V is to anticipate mishaps by permitting vehicles share speed
information and position information with each other over an impromptu work organize. V2V is
relied upon to show a 360 degree level of mindfulness about the encompassing to a moving
vehicle.
V2V is turning into an imperative piece of the wise transport arrangement of the United states.
Information from vehicle-to-vehicle correspondence is as of now being utilized to enhance
activity administration clear in rush hour gridlock lights and signs. It is normal that this
innovation will turn into a compulsory piece of the transportation framework, and massively help
in the mission for driverless-autos all over America.
The significant motivating force of V2V is that the innovation can expand the execution of
vehicle safety frameworks and help spare lives. It is normal that associated vehicle advancements
information and position information with each other over an impromptu work organize. V2V is
relied upon to show a 360 degree level of mindfulness about the encompassing to a moving
vehicle.
V2V is turning into an imperative piece of the wise transport arrangement of the United states.
Information from vehicle-to-vehicle correspondence is as of now being utilized to enhance
activity administration clear in rush hour gridlock lights and signs. It is normal that this
innovation will turn into a compulsory piece of the transportation framework, and massively help
in the mission for driverless-autos all over America.
The significant motivating force of V2V is that the innovation can expand the execution of
vehicle safety frameworks and help spare lives. It is normal that associated vehicle advancements
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

will furnish drivers with the devices to survive crashes, as well as to stay away from it through
and through.
Without the utilization of a put stock in expert, executing V2V brings up issues about the
correspondence instrument to guarantee successful network, and in addition address-ing the
characteristic security challenges in this type of correspondence. Dialog of V2V in this section
will be as far as the availability instrument and safety efforts. A way to deal with guaranteeing
compelling and secured correspondence in V2V will be talked about.
Although Vehicle Ad-hoc Network (VANET) isn't another theme, it keeps on giving new
research difficulties and issues. The principle target of VANET is to help a gathering of vehicles
to set up and keep up a correspondence arrange among them without utilizing any focal base
station or any controller. One of the real utilizations of VANET is in the basic medicinal crisis
circumstances where there is no foundation while it is basic to pass on the data for sparing
human lives.
Be that as it may, alongside these helpful utilizations of VANET, rise new difficulties and issues.
Absence of foundation in VANET puts extra duties on vehicles. Each vehicle turns out to be a
piece of the system and furthermore oversees and controls the correspondence on this system
alongside its own particular correspondence necessities. Vehicular impromptu systems are in
charge of the correspondence between moving vehicles in a specific domain.
A vehicle can speak with another vehicle straight forwardly that is called as Vehicle to Vehicle
(V2V) correspondence, or a vehicle can impart to a framework, for example, a Road Side Unit is
known as Vehicle-to-Infrastructure (V2I). The fundamental commitments of this paper are to
current situation with the craftsmanship in VANET innovation.
An itemized investigation of system design with various topologies and system demonstrating is
exhibited in this paper. A key plan territory in VANET keeping in mind the end goal to
appropriately frame a correspondence organize is steering the bundles in compelling way. The
paper talks about various directing calculations for VANET and presents restrictions of those
calculations.
and through.
Without the utilization of a put stock in expert, executing V2V brings up issues about the
correspondence instrument to guarantee successful network, and in addition address-ing the
characteristic security challenges in this type of correspondence. Dialog of V2V in this section
will be as far as the availability instrument and safety efforts. A way to deal with guaranteeing
compelling and secured correspondence in V2V will be talked about.
Although Vehicle Ad-hoc Network (VANET) isn't another theme, it keeps on giving new
research difficulties and issues. The principle target of VANET is to help a gathering of vehicles
to set up and keep up a correspondence arrange among them without utilizing any focal base
station or any controller. One of the real utilizations of VANET is in the basic medicinal crisis
circumstances where there is no foundation while it is basic to pass on the data for sparing
human lives.
Be that as it may, alongside these helpful utilizations of VANET, rise new difficulties and issues.
Absence of foundation in VANET puts extra duties on vehicles. Each vehicle turns out to be a
piece of the system and furthermore oversees and controls the correspondence on this system
alongside its own particular correspondence necessities. Vehicular impromptu systems are in
charge of the correspondence between moving vehicles in a specific domain.
A vehicle can speak with another vehicle straight forwardly that is called as Vehicle to Vehicle
(V2V) correspondence, or a vehicle can impart to a framework, for example, a Road Side Unit is
known as Vehicle-to-Infrastructure (V2I). The fundamental commitments of this paper are to
current situation with the craftsmanship in VANET innovation.
An itemized investigation of system design with various topologies and system demonstrating is
exhibited in this paper. A key plan territory in VANET keeping in mind the end goal to
appropriately frame a correspondence organize is steering the bundles in compelling way. The
paper talks about various directing calculations for VANET and presents restrictions of those
calculations.

Security issues in VANET condition are additionally tended to in the paper with the goal that
reliable system engineering can be demonstrated. The report additionally talks about a portion of
the key research territories and difficulties in this field.
Vehicular Ad Hoc Networks (VANETs) have become out of the need to help the developing
number of remote items that would now be able to be utilized as a part of vehicles. These items
incorporate remote keyless section gadgets, individual computerized aides (PDAs), workstations
and cell phones. As versatile remote gadgets and systems turn out to be progressively vital, the
interest for Vehicle to Vehicle (V2V) and Vehicle-to-Roadside (VRC) or Vehicle-to-
Infrastructure (V2I) Communication will keep on growing.
VANETs can be used for an expansive scope of wellbeing and non-security applications, take
into consideration esteem included administrations, for example, vehicle security, robotized toll
installment, movement administration, improved route, area based administrations, for example,
finding the nearest fuel station, eatery or travel cabin and infotainment applications, for example,
giving access to the Internet.
Problem Statement
Devoted for remote vehicular correspondences is the IEEE 802.11p standard where 6 out of the 7
accessible channels are utilized for real correspondence and the last channel for control
messages. Be that as it may, with the general objective of having every single transferable auto
on US streets, these channels could be effortlessly overpowered.
Inside a mile range, there could be a few autos particularly on occupied streets in very crowded
land locale all normal to give transportation insight through V2V correspondence. This presents
a prerequisite for a for all intents and purposes boundless accessible correspondence direct in
vehicular correspondence. The timeliness limitation of V2V systems should likewise be
considered as time-basic crisis messages can't be postponed.
Along these lines in this section, an assessment of the different network alternatives accessible
for V2V is considered, with an approach considering the correspondence extend, speed, tavel
course and so forth. Likewise, a trust-based security display for V2V correspondence is
proposed.
reliable system engineering can be demonstrated. The report additionally talks about a portion of
the key research territories and difficulties in this field.
Vehicular Ad Hoc Networks (VANETs) have become out of the need to help the developing
number of remote items that would now be able to be utilized as a part of vehicles. These items
incorporate remote keyless section gadgets, individual computerized aides (PDAs), workstations
and cell phones. As versatile remote gadgets and systems turn out to be progressively vital, the
interest for Vehicle to Vehicle (V2V) and Vehicle-to-Roadside (VRC) or Vehicle-to-
Infrastructure (V2I) Communication will keep on growing.
VANETs can be used for an expansive scope of wellbeing and non-security applications, take
into consideration esteem included administrations, for example, vehicle security, robotized toll
installment, movement administration, improved route, area based administrations, for example,
finding the nearest fuel station, eatery or travel cabin and infotainment applications, for example,
giving access to the Internet.
Problem Statement
Devoted for remote vehicular correspondences is the IEEE 802.11p standard where 6 out of the 7
accessible channels are utilized for real correspondence and the last channel for control
messages. Be that as it may, with the general objective of having every single transferable auto
on US streets, these channels could be effortlessly overpowered.
Inside a mile range, there could be a few autos particularly on occupied streets in very crowded
land locale all normal to give transportation insight through V2V correspondence. This presents
a prerequisite for a for all intents and purposes boundless accessible correspondence direct in
vehicular correspondence. The timeliness limitation of V2V systems should likewise be
considered as time-basic crisis messages can't be postponed.
Along these lines in this section, an assessment of the different network alternatives accessible
for V2V is considered, with an approach considering the correspondence extend, speed, tavel
course and so forth. Likewise, a trust-based security display for V2V correspondence is
proposed.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Motivation
With regards to V2V, an opportunity to takes to completely travel crisis messages can mean the
distinction amongst life and demise. In any case, messages might be deferred because of a
restriction in the channel accessibility of the IEEE 802.11 channels, which are represented by the
IEEE 802.11p standard for remote vehicular interchanges. IEEE 802.11 comprises of seven
diverts altogether. One of these goes about as the normal control channel while the staying six
are utilized for vehicular correspondences.
As the fame and commonness of vehicles that can speak with each other remotely increments,
there is a solid plausibility that the IEEE 802.11 channel will progress toward becoming
overpowered, and this could bring about postponements in messages and shortage in the radio
range.
In that capacity, psychological radio advances could speak to a suitable arrangement by which it
is conceivable to accomplish the low idleness between vehicles interchanges require while
additionally averting range shortage.
Psychological radio is a generally new innovation that includes improving the range by misusing
unutilized range gaps. The intellectual radio system normally utilizes three diverse ways to deal
with recognize and abuse unused channels: geo-area database, guides, and range detecting. Every
one of these techniques will be analyzed in more profundity beneath:
Reference points use motions by multiplying signals crosswise over various channels with the
goal of recognizing a free channel. Guides have been coordinated in a scope of various
applications; for instance and. One region in which reference points have been especially helpful
inside the setting of IoV is using signs to identify the speed, heading, and position of different
vehicles inside a system. Reference points are not without their drawbacks.
One noteworthy issue with the utilization of reference points to distinguish unexploited channels
is that their utilization decreases the effectiveness of the range since they depend on a high and
satisfactory radio recurrence. What's more, the signs sent and got by signals may experience the
ill effects of elective sources.
The geo-area database is a computerized chronicle that acquires forms, arranges, and multiplies
data about the range band. The CR framework gets to the geo location database plot, which
With regards to V2V, an opportunity to takes to completely travel crisis messages can mean the
distinction amongst life and demise. In any case, messages might be deferred because of a
restriction in the channel accessibility of the IEEE 802.11 channels, which are represented by the
IEEE 802.11p standard for remote vehicular interchanges. IEEE 802.11 comprises of seven
diverts altogether. One of these goes about as the normal control channel while the staying six
are utilized for vehicular correspondences.
As the fame and commonness of vehicles that can speak with each other remotely increments,
there is a solid plausibility that the IEEE 802.11 channel will progress toward becoming
overpowered, and this could bring about postponements in messages and shortage in the radio
range.
In that capacity, psychological radio advances could speak to a suitable arrangement by which it
is conceivable to accomplish the low idleness between vehicles interchanges require while
additionally averting range shortage.
Psychological radio is a generally new innovation that includes improving the range by misusing
unutilized range gaps. The intellectual radio system normally utilizes three diverse ways to deal
with recognize and abuse unused channels: geo-area database, guides, and range detecting. Every
one of these techniques will be analyzed in more profundity beneath:
Reference points use motions by multiplying signals crosswise over various channels with the
goal of recognizing a free channel. Guides have been coordinated in a scope of various
applications; for instance and. One region in which reference points have been especially helpful
inside the setting of IoV is using signs to identify the speed, heading, and position of different
vehicles inside a system. Reference points are not without their drawbacks.
One noteworthy issue with the utilization of reference points to distinguish unexploited channels
is that their utilization decreases the effectiveness of the range since they depend on a high and
satisfactory radio recurrence. What's more, the signs sent and got by signals may experience the
ill effects of elective sources.
The geo-area database is a computerized chronicle that acquires forms, arranges, and multiplies
data about the range band. The CR framework gets to the geo location database plot, which
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

contains information about the essential client frameworks, to recognize empty groups. At the
point when this plan is utilized, there is no prerequisite for the CR clients to perform range
detecting on the groups; in that capacity, in contrast with alternate strategies for recognizing
unused channels, the overheads related with utilizing the geo-area database are moderately low.
Moreover, as this approach does not include any detecting mistakes, it is less demanding to
ensure the essential clients. To utilize this plan viably, there is a necessity to set up a steady
association between the range database and the CR clients. Accordingly, while it is moderately
simple to utilize this plan in a cell CR framework, it is more unpredictable to utilize it a specially
appointed circumstance on the grounds that an association of this nature may not exist. Hence, it
is impossible that the geo location database plan will discover application in a specially
appointed CR condition.
Future Research
It's fundamentally a system of autos that are in consistent correspondence. Every auto knows
where it is, the place it's going and fundamentally whatever other amount that it can quantify.
Not just has each auto been made "mindful", it can likewise speak with some other auto out and
about. Simply pause for a moment to think about every one of the conceivable outcomes. The
first that strikes a chord is street wellbeing.
On the off chance that all autos know where every single other auto are, autos set out toward a
fast approaching accident can caution their separate drivers and even apply self-ruling control to
maintain a strategic distance from mishaps. Not just drivers can be educated about deferrals to
their goal, yet activity lights can be associated with the correspondence system to most
effectively course movement continuously.
In spite of the fact that there has been an adequate measure of research in VANET, still there are
numerous territories which should be investigated. Because of the distinctive idea of VANET
shape numerous different remote correspondence systems and hard outline prerequisites, there
are numerous fascinating examination issues in this field. The paper abridges a portion of the key
research regions and difficulties as under. In any case, it must be noticed that the examination
challenges in VANET are not constrained to just these zones.
point when this plan is utilized, there is no prerequisite for the CR clients to perform range
detecting on the groups; in that capacity, in contrast with alternate strategies for recognizing
unused channels, the overheads related with utilizing the geo-area database are moderately low.
Moreover, as this approach does not include any detecting mistakes, it is less demanding to
ensure the essential clients. To utilize this plan viably, there is a necessity to set up a steady
association between the range database and the CR clients. Accordingly, while it is moderately
simple to utilize this plan in a cell CR framework, it is more unpredictable to utilize it a specially
appointed circumstance on the grounds that an association of this nature may not exist. Hence, it
is impossible that the geo location database plan will discover application in a specially
appointed CR condition.
Future Research
It's fundamentally a system of autos that are in consistent correspondence. Every auto knows
where it is, the place it's going and fundamentally whatever other amount that it can quantify.
Not just has each auto been made "mindful", it can likewise speak with some other auto out and
about. Simply pause for a moment to think about every one of the conceivable outcomes. The
first that strikes a chord is street wellbeing.
On the off chance that all autos know where every single other auto are, autos set out toward a
fast approaching accident can caution their separate drivers and even apply self-ruling control to
maintain a strategic distance from mishaps. Not just drivers can be educated about deferrals to
their goal, yet activity lights can be associated with the correspondence system to most
effectively course movement continuously.
In spite of the fact that there has been an adequate measure of research in VANET, still there are
numerous territories which should be investigated. Because of the distinctive idea of VANET
shape numerous different remote correspondence systems and hard outline prerequisites, there
are numerous fascinating examination issues in this field. The paper abridges a portion of the key
research regions and difficulties as under. In any case, it must be noticed that the examination
challenges in VANET are not constrained to just these zones.

Quality of Service (QoS): Provision of certain nature of administration levels in VANET is an
essential undertaking. A system with least deferral for information conveyance, less
retransmissions, and high network time can give certain QoS ensured to the clients. Promising
this sort of QoS with various client applications and dynamic system condition is a fascinating
and testing errand in VANET outline.
Conclusion
As featured before, one of the utilizations of V2I is the help for emergency administrations. This
means the requirement for continuous information activity amongst vehicles and foundation in a
vehicular specially appointed system. This is regularly the necessity for proactive security
applications. Having ensured defer limits is imperative for the unwavering quality of drivers on
such applications particularly in basic circumstances.
This need additionally reaches out to non-basic frameworks where data transmission is planned
to be better figured out how to energize client appropriation and lessen improvement cost. In
customary V2I frameworks, all vehicles report their area and speed to a RSU. Another essential
element of the V2I system is the capacity to run inquiries of this information. In any case, the
framework speaks to a solitary purpose of disappointment in this system.
Likewise, when numerous vehicles endeavor to report their statutory information to the RSU in
the meantime, it lines the transmissions however expanding the deferral for information transfer
in some piece of the system which brings about a diminishment in the precision of the endorsed
activity/warning to the vehicles.
In unadulterated V2V engineering, every one of the vehicles report their information to neighbor
vehicles who engenders the information advance in the system without the utilization of a put
stock in focal expert. Notwithstanding, the proposed approach influences on such
correspondence as a connection to the framework. In the proposed amassed vehicle to foundation
engineering (AV2I), an over-burden of the correspondence channel to RSUs is meant to be
diminished.
Consequently, it is normal that this outcomes in a quicker uplink transmission by vehicles to
RSUs and downlink from RSUs to vehicles. There is a lot of information that must be gotten by
essential undertaking. A system with least deferral for information conveyance, less
retransmissions, and high network time can give certain QoS ensured to the clients. Promising
this sort of QoS with various client applications and dynamic system condition is a fascinating
and testing errand in VANET outline.
Conclusion
As featured before, one of the utilizations of V2I is the help for emergency administrations. This
means the requirement for continuous information activity amongst vehicles and foundation in a
vehicular specially appointed system. This is regularly the necessity for proactive security
applications. Having ensured defer limits is imperative for the unwavering quality of drivers on
such applications particularly in basic circumstances.
This need additionally reaches out to non-basic frameworks where data transmission is planned
to be better figured out how to energize client appropriation and lessen improvement cost. In
customary V2I frameworks, all vehicles report their area and speed to a RSU. Another essential
element of the V2I system is the capacity to run inquiries of this information. In any case, the
framework speaks to a solitary purpose of disappointment in this system.
Likewise, when numerous vehicles endeavor to report their statutory information to the RSU in
the meantime, it lines the transmissions however expanding the deferral for information transfer
in some piece of the system which brings about a diminishment in the precision of the endorsed
activity/warning to the vehicles.
In unadulterated V2V engineering, every one of the vehicles report their information to neighbor
vehicles who engenders the information advance in the system without the utilization of a put
stock in focal expert. Notwithstanding, the proposed approach influences on such
correspondence as a connection to the framework. In the proposed amassed vehicle to foundation
engineering (AV2I), an over-burden of the correspondence channel to RSUs is meant to be
diminished.
Consequently, it is normal that this outcomes in a quicker uplink transmission by vehicles to
RSUs and downlink from RSUs to vehicles. There is a lot of information that must be gotten by
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the server when all vehicles are sending their information and in addition questioning for other
data. AV2I endeavors to lessen these impediments by expanding on the V2I engineering.
In this report, the different parts that structures the rudiments of a useful V2I correspondence
organize have been talked about. The significance of RSUs and outsider trusted expert as a
feature of the V2I engineering has likewise been talked about. Also, a collected vehicle to
framework design was talked about where the transportation organize is isolated into pre-
characterized lattices. Every matrix at that point has a super vehicle which totals messages sent
to the RSU framework.
The super vehicle is chosen in light of the evaluated remaining time it is relied upon to spend in
the network. As an additional safety effort to maintain a strategic distance from noxious vehicles
developing as super vehicle, a probabilistic way to deal with vindictive vehicle distinguishing
proof was likewise examined.
It has turned out to be progressively hard to ensure all of security, protection while likewise
considering execution prerequisites for V2I correspondence systems. A secured and productive
gathering based encryption instrument has been proposed in light of the super vehicle's hashed
area. Been proposed in view of the total vehicle to framework design, the security and protection
system proposed can be scaled extensive execution of Internet of Vehicles.
The significance of V2V coordinate concerning network and security has been examined so far
in this section. An investigation of the effect of optional vehicular client versatility and essential
client action has been directed for dynamic range get to. Hence, a probabilistic approach was
defined for trust count in keeping up respectability of vehicle-vehicle informing through middle
of the road vehicles.
The execution of the proposed formal models is assessed utilizing numerical outcomes got from
Monte Carlo reenactments. It is discovered that the likelihood of misdetection of essential client
action over a channel increments with expanded vehicular speed and diminishing expected
covering time term per age. Likewise, in view of investigations played out, the normal trust an
incentive for vehicles increment with expanding SNR, with fair vehicles indicating substantially
higher confide in an incentive than malignant vehicles.
data. AV2I endeavors to lessen these impediments by expanding on the V2I engineering.
In this report, the different parts that structures the rudiments of a useful V2I correspondence
organize have been talked about. The significance of RSUs and outsider trusted expert as a
feature of the V2I engineering has likewise been talked about. Also, a collected vehicle to
framework design was talked about where the transportation organize is isolated into pre-
characterized lattices. Every matrix at that point has a super vehicle which totals messages sent
to the RSU framework.
The super vehicle is chosen in light of the evaluated remaining time it is relied upon to spend in
the network. As an additional safety effort to maintain a strategic distance from noxious vehicles
developing as super vehicle, a probabilistic way to deal with vindictive vehicle distinguishing
proof was likewise examined.
It has turned out to be progressively hard to ensure all of security, protection while likewise
considering execution prerequisites for V2I correspondence systems. A secured and productive
gathering based encryption instrument has been proposed in light of the super vehicle's hashed
area. Been proposed in view of the total vehicle to framework design, the security and protection
system proposed can be scaled extensive execution of Internet of Vehicles.
The significance of V2V coordinate concerning network and security has been examined so far
in this section. An investigation of the effect of optional vehicular client versatility and essential
client action has been directed for dynamic range get to. Hence, a probabilistic approach was
defined for trust count in keeping up respectability of vehicle-vehicle informing through middle
of the road vehicles.
The execution of the proposed formal models is assessed utilizing numerical outcomes got from
Monte Carlo reenactments. It is discovered that the likelihood of misdetection of essential client
action over a channel increments with expanded vehicular speed and diminishing expected
covering time term per age. Likewise, in view of investigations played out, the normal trust an
incentive for vehicles increment with expanding SNR, with fair vehicles indicating substantially
higher confide in an incentive than malignant vehicles.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

VANET is a promising remote correspondence development for improving thoroughfare
prosperity and information organizations. In this paper, we propose an ensured and application
organized framework design structure in which the essentials of potential VANET applications
are considered. We in like manner think about a couple of utilizations as a promising gadget for
checking the physical world with remote sensor that can recognize process and confer.
VANET applications keep running from prosperity and crash avoidance to Internet access and
media. We assume that our examination can give a lead to more helpful VANET. The
association of enlisting, media correspondences (settled and adaptable), and distinctive sorts of
organizations are engaging the course of action of different kinds of VANET propels. In the
earlier decade, various VANET stretches out far and wide have been endeavored and a couple of
VANET benchmarks have been made to upgrade vehicle-to-vehicle or vehicle-to-structure
trades.
In this work, we assessed a segment of the crucial areas that authorities have focused on finished
the latest couple of years and these join security, coordinating, QoS, and broadcasting techniques
and we included the most striking results achieved to date. We displayed a thorough examination
of various entertainment instruments that are open for VANET reenactments. We believe this
logical classification on VANET test frameworks will be valuable to future VANET experts in
picking the perfect VANET test framework most fitting for their VANET design targets.
Finally, we inspected a bit of the troubles that still ought to be tended to remembering the
ultimate objective to enable the course of action of VANET advances, establishments, and
organizations cost-satisfactorily, securely, and reliably.
prosperity and information organizations. In this paper, we propose an ensured and application
organized framework design structure in which the essentials of potential VANET applications
are considered. We in like manner think about a couple of utilizations as a promising gadget for
checking the physical world with remote sensor that can recognize process and confer.
VANET applications keep running from prosperity and crash avoidance to Internet access and
media. We assume that our examination can give a lead to more helpful VANET. The
association of enlisting, media correspondences (settled and adaptable), and distinctive sorts of
organizations are engaging the course of action of different kinds of VANET propels. In the
earlier decade, various VANET stretches out far and wide have been endeavored and a couple of
VANET benchmarks have been made to upgrade vehicle-to-vehicle or vehicle-to-structure
trades.
In this work, we assessed a segment of the crucial areas that authorities have focused on finished
the latest couple of years and these join security, coordinating, QoS, and broadcasting techniques
and we included the most striking results achieved to date. We displayed a thorough examination
of various entertainment instruments that are open for VANET reenactments. We believe this
logical classification on VANET test frameworks will be valuable to future VANET experts in
picking the perfect VANET test framework most fitting for their VANET design targets.
Finally, we inspected a bit of the troubles that still ought to be tended to remembering the
ultimate objective to enable the course of action of VANET advances, establishments, and
organizations cost-satisfactorily, securely, and reliably.

References
Aadil, Farhan. Vehicular Ad Hoc Networks (VANETs), Past Present and Future: A survey. 2013.
<https://www.researchgate.net/publication/280314446_Vehicular_Ad_Hoc_Networks_VANETs
_Past_Present_and_Future_A_survey>.
Eichler, Stephan. Car-to-Car Communication. 2015.
<https://pdfs.semanticscholar.org/6848/2153affabb278c34654940bdd3cc4e23bb09.pdf>.
Jain, Ruchin. A Congestion Control System Based on VANET for Small Length Roads. 2018.
<https://arxiv.org/ftp/arxiv/papers/1801/1801.06448.pdf>.
Kaur, Manjot. VEHICULAR AD HOC NETWORKS. 2012. <http://www.rroij.com/open-
access/vehicular-ad-hoc-networks-61-64.pdf>.
LA, Vinh Hoa. SECURITY ATTACKS AND SOLUTIONS IN VEHICULAR AD HOC
NETWORKS: A SURVEY. 2014. <http://airccse.org/journal/ijans/papers/4214ijans01.pdf>.
Offor, Patrick I. Vehicle Ad Hoc Network (VANET): Safety Benefits and Security Challenges.
2012.
<https://www.researchgate.net/publication/254953231_Vehicle_Ad_Hoc_Network_VANET_Saf
ety_Benefits_and_Security_Challenges>.
Prasan, U D. An Analysis on Vehicular Ad-Hoc Networks: Research Issues, Challenges and
Applications. 2016. <https://www.ripublication.com/ijaer16/ijaerv11n6_139.pdf>.
Rehman, Sabih ur. Vehicular Ad-Hoc Networks (VANETs) - An Overview ) - An Overview.
2013. <https://pdfs.semanticscholar.org/4863/147915b4c2bcb3a8c7bdfa785fb817847ba9.pdf>.
Zeadally, Sherali. Vehicular Ad Hoc Networks (VANETS): Status, Results, and Challenges.
2014. <http://citeseerx.ist.psu.edu/viewdoc/download?
doi=10.1.1.188.7416&rep=rep1&type=pdf>.
Zhang, Hongyang. Vehicular Ad Hoc Networks: Architectures, Research Issues, Methodologies,
Challenges, and Trends. 2015.
Aadil, Farhan. Vehicular Ad Hoc Networks (VANETs), Past Present and Future: A survey. 2013.
<https://www.researchgate.net/publication/280314446_Vehicular_Ad_Hoc_Networks_VANETs
_Past_Present_and_Future_A_survey>.
Eichler, Stephan. Car-to-Car Communication. 2015.
<https://pdfs.semanticscholar.org/6848/2153affabb278c34654940bdd3cc4e23bb09.pdf>.
Jain, Ruchin. A Congestion Control System Based on VANET for Small Length Roads. 2018.
<https://arxiv.org/ftp/arxiv/papers/1801/1801.06448.pdf>.
Kaur, Manjot. VEHICULAR AD HOC NETWORKS. 2012. <http://www.rroij.com/open-
access/vehicular-ad-hoc-networks-61-64.pdf>.
LA, Vinh Hoa. SECURITY ATTACKS AND SOLUTIONS IN VEHICULAR AD HOC
NETWORKS: A SURVEY. 2014. <http://airccse.org/journal/ijans/papers/4214ijans01.pdf>.
Offor, Patrick I. Vehicle Ad Hoc Network (VANET): Safety Benefits and Security Challenges.
2012.
<https://www.researchgate.net/publication/254953231_Vehicle_Ad_Hoc_Network_VANET_Saf
ety_Benefits_and_Security_Challenges>.
Prasan, U D. An Analysis on Vehicular Ad-Hoc Networks: Research Issues, Challenges and
Applications. 2016. <https://www.ripublication.com/ijaer16/ijaerv11n6_139.pdf>.
Rehman, Sabih ur. Vehicular Ad-Hoc Networks (VANETs) - An Overview ) - An Overview.
2013. <https://pdfs.semanticscholar.org/4863/147915b4c2bcb3a8c7bdfa785fb817847ba9.pdf>.
Zeadally, Sherali. Vehicular Ad Hoc Networks (VANETS): Status, Results, and Challenges.
2014. <http://citeseerx.ist.psu.edu/viewdoc/download?
doi=10.1.1.188.7416&rep=rep1&type=pdf>.
Zhang, Hongyang. Vehicular Ad Hoc Networks: Architectures, Research Issues, Methodologies,
Challenges, and Trends. 2015.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.