Project: Verbania Inc. Social Media IT Solution - System Development
VerifiedAdded on 2020/05/16
|61
|15667
|46
Project
AI Summary
This project report provides a comprehensive IT solution for Verbania Inc.'s social media platform. It begins with an analysis of system requirements, including user accounts, discussion forums, search capabilities, and game/calendar components. The report outlines a high-level implementation plan, detailing phases such as initialization, execution, testing, and training/documentation, along with a detailed work breakdown structure (WBS). Specific and detailed requirements are presented, encompassing user roles, network infrastructure, website interface, database design, and hardware/software specifications. The report recommends a star topology for the corporate network and includes a high-level network diagram with an explanation of access. The system analysis section further explores corporate network topology recommendations, highlighting the advantages of star topology. The project aims to develop an effective and improved social media site and application, addressing Verbania Inc.'s needs through systematic development and network architecture.

Running head: VERBANIA INC. SOCIAL MEDIA IT SOLUTION 1
Verbania Inc. Social Media Information Technology (IT) Solution
Verbania Inc. Social Media Information Technology (IT) Solution
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

VERBANIA INC. SOCIAL MEDIA IT SOLUTION 2
TABLE OF CONTENTS
Section 1: Planning and System Requirements...............................................................................4
Section 2: System Analysis...........................................................................................................13
Section 3: System Design..............................................................................................................20
Section 4: System Development....................................................................................................33
Section 5: System Implementation and Maintenance....................................................................47
References......................................................................................................................................56
TABLE OF CONTENTS
Section 1: Planning and System Requirements...............................................................................4
Section 2: System Analysis...........................................................................................................13
Section 3: System Design..............................................................................................................20
Section 4: System Development....................................................................................................33
Section 5: System Implementation and Maintenance....................................................................47
References......................................................................................................................................56

VERBANIA INC. SOCIAL MEDIA IT SOLUTION 3
SECTION 1: PLANNING AND SYSTEM REQUIREMENTS
The website deployment has become important for the deployment of the improved
processes and the formation of the profound development method (Holland, 2016). The
deployment of the operations would be formed for carrying out the modification of the website
development. The software development would allow the implication of the profound system
integration. The deployment of the operations would result in forming the improved functional
analysis.
The following assignment would be formed for analyzing the requirements of the system
development. The integration system analysis would be formed for carrying out the development
of the social website. The high-level plan would be implied for developing the improved
functional schedule for the implementation of the social media website.
Pertinent Requirements of Verbania Inc.
The pertinent requirements of the social media website development would include the
tools, software, and other requirements of the project (John & Swapna, 2017). The deployment
of the functions would allow the development of the project. The requirements of the
organization are,
Creation of user account: The first requirement of Verbania Inc. is the development of
user account and profile on the website for ensuring the collection of the data and information
about the customers. The website developed would require the identification of the user and
collecting the data of the customers on a single website. When the customers would login at the
website, the information and data entered at the website for making the profile would be stored
in an integrated database that would result in forming the modification of the user accounts.
SECTION 1: PLANNING AND SYSTEM REQUIREMENTS
The website deployment has become important for the deployment of the improved
processes and the formation of the profound development method (Holland, 2016). The
deployment of the operations would be formed for carrying out the modification of the website
development. The software development would allow the implication of the profound system
integration. The deployment of the operations would result in forming the improved functional
analysis.
The following assignment would be formed for analyzing the requirements of the system
development. The integration system analysis would be formed for carrying out the development
of the social website. The high-level plan would be implied for developing the improved
functional schedule for the implementation of the social media website.
Pertinent Requirements of Verbania Inc.
The pertinent requirements of the social media website development would include the
tools, software, and other requirements of the project (John & Swapna, 2017). The deployment
of the functions would allow the development of the project. The requirements of the
organization are,
Creation of user account: The first requirement of Verbania Inc. is the development of
user account and profile on the website for ensuring the collection of the data and information
about the customers. The website developed would require the identification of the user and
collecting the data of the customers on a single website. When the customers would login at the
website, the information and data entered at the website for making the profile would be stored
in an integrated database that would result in forming the modification of the user accounts.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

VERBANIA INC. SOCIAL MEDIA IT SOLUTION 4
Creation of Discussion Forums and Posting: The discussion forums and posting would
be formed for developing the improved communication with the customers. According to Thum
et al. (2014), the various discussion forums and posts would help the customers for conveying
their views, requirements, and ideas to Verbania Inc. The alignment of the strategies while
keeping in mind the customer’s views would help in developing the improved functional
operations.
Search Capability of People: The search capability of the people would allow the
development of the improved functional analysis. The use of website development would allow
the intake of the improved system development. The website would allow them to integrate the
person to person searching for the operations.
Game and Calendar Component: The implication of the website function would allow
the formation of the effective and improved functional operation development. The gaming and
calendar component would allow the integration of the operations. The deployment of the
operations would help in forming the consideration of the system development for the
organization.
Solution for Verbania Inc.
The development of the website for the organization would provide the ease of the
operations for the organization processing (Laporte, Hebert & Mineau, 2014). The development
of the website would help in integrating the functional development of the operations for the
modification of the effective and improved system alignment and development. The integration
of the operations would be formed for integration of the system performance and deployment.
Creation of Discussion Forums and Posting: The discussion forums and posting would
be formed for developing the improved communication with the customers. According to Thum
et al. (2014), the various discussion forums and posts would help the customers for conveying
their views, requirements, and ideas to Verbania Inc. The alignment of the strategies while
keeping in mind the customer’s views would help in developing the improved functional
operations.
Search Capability of People: The search capability of the people would allow the
development of the improved functional analysis. The use of website development would allow
the intake of the improved system development. The website would allow them to integrate the
person to person searching for the operations.
Game and Calendar Component: The implication of the website function would allow
the formation of the effective and improved functional operation development. The gaming and
calendar component would allow the integration of the operations. The deployment of the
operations would help in forming the consideration of the system development for the
organization.
Solution for Verbania Inc.
The development of the website for the organization would provide the ease of the
operations for the organization processing (Laporte, Hebert & Mineau, 2014). The development
of the website would help in integrating the functional development of the operations for the
modification of the effective and improved system alignment and development. The integration
of the operations would be formed for integration of the system performance and deployment.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

VERBANIA INC. SOCIAL MEDIA IT SOLUTION 5
The alignment of the system development would align the formation of the improved operations.
The website development would allow the deployment of the alignment methods.
High Level Plan for Implementation
The project of developing a Website of Verbania Inc. is implicit in forming an effective
website that would help the organization for aligning the improved functionality with operations.
The implementation plan consists of four phases namely Initialization, Execution, Testing, and
Training and Documentation (Ma & Lee, 2015). The initialization phase consists of human
resource employment, establishment of responsibilities, employment of high level project
manager, feasibility analysis of website connection, sustainability analysis of the website
requirements, organizational policy development for website, development of plan, and plan
approval. The execution phase consists of designing of the website, user interface development,
integrated database is formed, alignment of resources, modifications of the website, accessibility
checklist is developed, and security functions are aligned. The testing phase consists of black box
testing, white box testing, compatibility testing, and website developed. The training and
documentation consists of training manuals are formed, training is provided to the staffs and
user, training is completed, final documents are made, documents are reviewed, and sign off the
documents (Danielson et al., 2016). The Implementation Plan for the Website of the Verbania
Inc. is given in the table shown directly below.
WB
S Task Name Duration Start Finish Predecessors
0 Implementation Plan for Website of
Verbania Inc 57 days Mon
2/5/18
Tue
4/24/18
The alignment of the system development would align the formation of the improved operations.
The website development would allow the deployment of the alignment methods.
High Level Plan for Implementation
The project of developing a Website of Verbania Inc. is implicit in forming an effective
website that would help the organization for aligning the improved functionality with operations.
The implementation plan consists of four phases namely Initialization, Execution, Testing, and
Training and Documentation (Ma & Lee, 2015). The initialization phase consists of human
resource employment, establishment of responsibilities, employment of high level project
manager, feasibility analysis of website connection, sustainability analysis of the website
requirements, organizational policy development for website, development of plan, and plan
approval. The execution phase consists of designing of the website, user interface development,
integrated database is formed, alignment of resources, modifications of the website, accessibility
checklist is developed, and security functions are aligned. The testing phase consists of black box
testing, white box testing, compatibility testing, and website developed. The training and
documentation consists of training manuals are formed, training is provided to the staffs and
user, training is completed, final documents are made, documents are reviewed, and sign off the
documents (Danielson et al., 2016). The Implementation Plan for the Website of the Verbania
Inc. is given in the table shown directly below.
WB
S Task Name Duration Start Finish Predecessors
0 Implementation Plan for Website of
Verbania Inc 57 days Mon
2/5/18
Tue
4/24/18
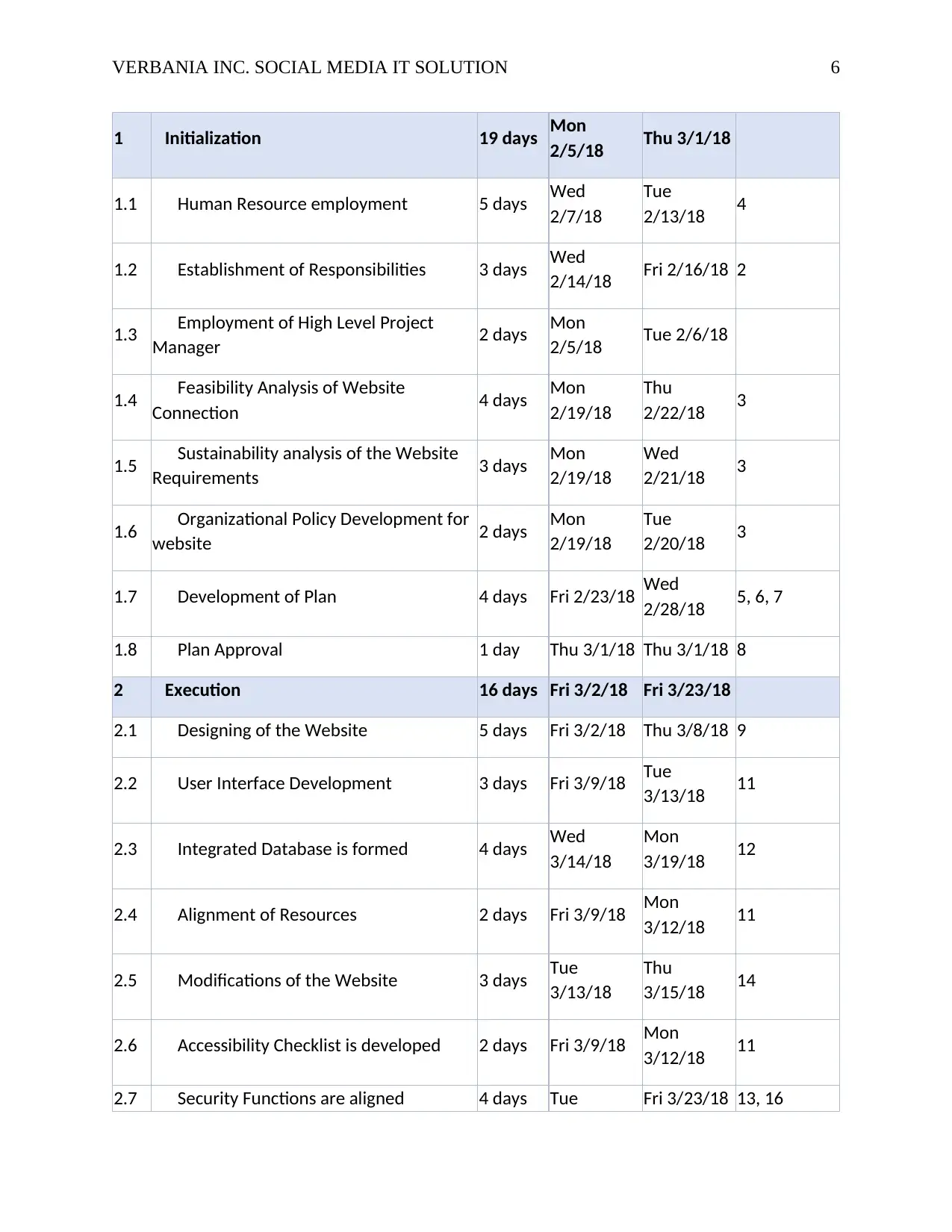
VERBANIA INC. SOCIAL MEDIA IT SOLUTION 6
1 Initialization 19 days Mon
2/5/18 Thu 3/1/18
1.1 Human Resource employment 5 days Wed
2/7/18
Tue
2/13/18 4
1.2 Establishment of Responsibilities 3 days Wed
2/14/18 Fri 2/16/18 2
1.3 Employment of High Level Project
Manager 2 days Mon
2/5/18 Tue 2/6/18
1.4 Feasibility Analysis of Website
Connection 4 days Mon
2/19/18
Thu
2/22/18 3
1.5 Sustainability analysis of the Website
Requirements 3 days Mon
2/19/18
Wed
2/21/18 3
1.6 Organizational Policy Development for
website 2 days Mon
2/19/18
Tue
2/20/18 3
1.7 Development of Plan 4 days Fri 2/23/18 Wed
2/28/18 5, 6, 7
1.8 Plan Approval 1 day Thu 3/1/18 Thu 3/1/18 8
2 Execution 16 days Fri 3/2/18 Fri 3/23/18
2.1 Designing of the Website 5 days Fri 3/2/18 Thu 3/8/18 9
2.2 User Interface Development 3 days Fri 3/9/18 Tue
3/13/18 11
2.3 Integrated Database is formed 4 days Wed
3/14/18
Mon
3/19/18 12
2.4 Alignment of Resources 2 days Fri 3/9/18 Mon
3/12/18 11
2.5 Modifications of the Website 3 days Tue
3/13/18
Thu
3/15/18 14
2.6 Accessibility Checklist is developed 2 days Fri 3/9/18 Mon
3/12/18 11
2.7 Security Functions are aligned 4 days Tue Fri 3/23/18 13, 16
1 Initialization 19 days Mon
2/5/18 Thu 3/1/18
1.1 Human Resource employment 5 days Wed
2/7/18
Tue
2/13/18 4
1.2 Establishment of Responsibilities 3 days Wed
2/14/18 Fri 2/16/18 2
1.3 Employment of High Level Project
Manager 2 days Mon
2/5/18 Tue 2/6/18
1.4 Feasibility Analysis of Website
Connection 4 days Mon
2/19/18
Thu
2/22/18 3
1.5 Sustainability analysis of the Website
Requirements 3 days Mon
2/19/18
Wed
2/21/18 3
1.6 Organizational Policy Development for
website 2 days Mon
2/19/18
Tue
2/20/18 3
1.7 Development of Plan 4 days Fri 2/23/18 Wed
2/28/18 5, 6, 7
1.8 Plan Approval 1 day Thu 3/1/18 Thu 3/1/18 8
2 Execution 16 days Fri 3/2/18 Fri 3/23/18
2.1 Designing of the Website 5 days Fri 3/2/18 Thu 3/8/18 9
2.2 User Interface Development 3 days Fri 3/9/18 Tue
3/13/18 11
2.3 Integrated Database is formed 4 days Wed
3/14/18
Mon
3/19/18 12
2.4 Alignment of Resources 2 days Fri 3/9/18 Mon
3/12/18 11
2.5 Modifications of the Website 3 days Tue
3/13/18
Thu
3/15/18 14
2.6 Accessibility Checklist is developed 2 days Fri 3/9/18 Mon
3/12/18 11
2.7 Security Functions are aligned 4 days Tue Fri 3/23/18 13, 16
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
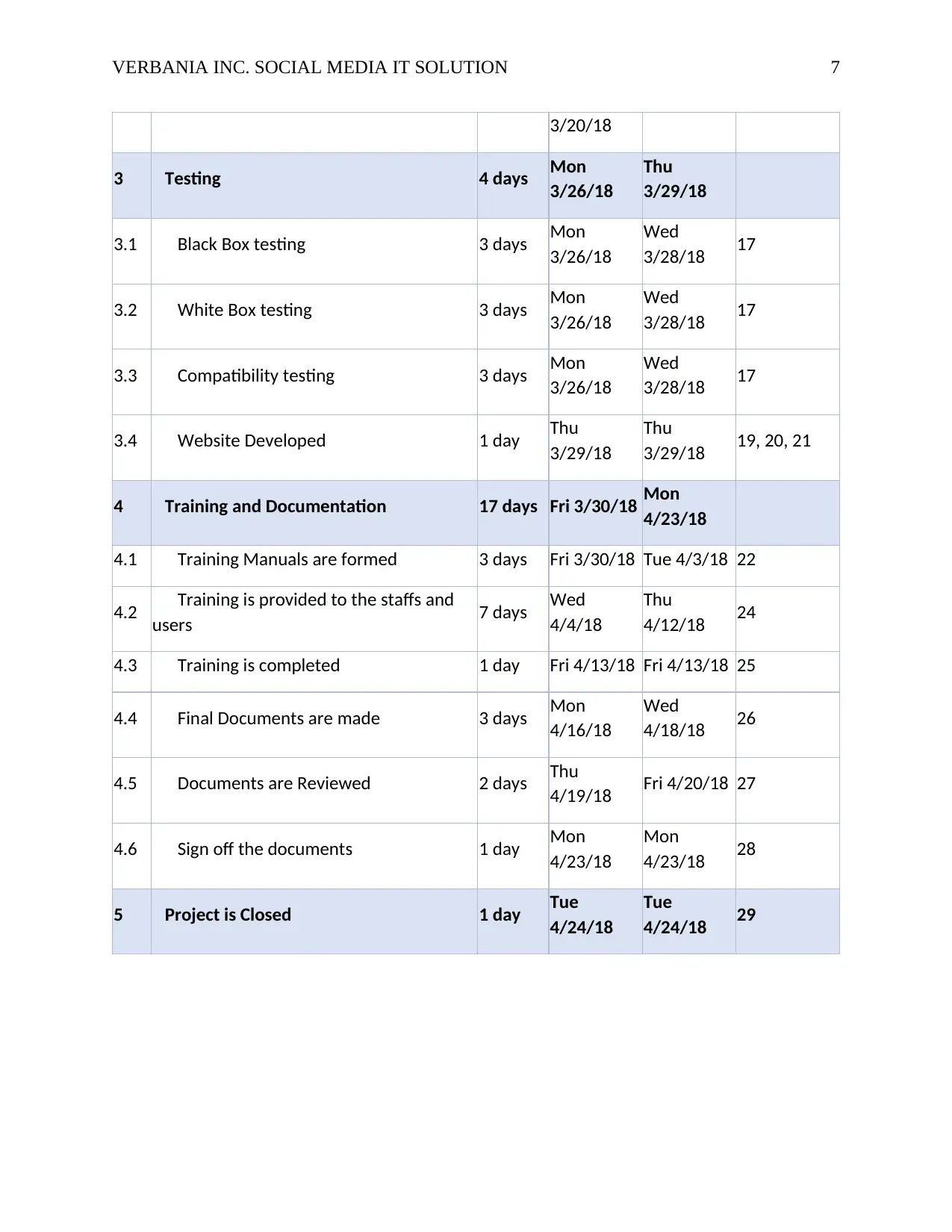
VERBANIA INC. SOCIAL MEDIA IT SOLUTION 7
3/20/18
3 Testing 4 days Mon
3/26/18
Thu
3/29/18
3.1 Black Box testing 3 days Mon
3/26/18
Wed
3/28/18 17
3.2 White Box testing 3 days Mon
3/26/18
Wed
3/28/18 17
3.3 Compatibility testing 3 days Mon
3/26/18
Wed
3/28/18 17
3.4 Website Developed 1 day Thu
3/29/18
Thu
3/29/18 19, 20, 21
4 Training and Documentation 17 days Fri 3/30/18 Mon
4/23/18
4.1 Training Manuals are formed 3 days Fri 3/30/18 Tue 4/3/18 22
4.2 Training is provided to the staffs and
users 7 days Wed
4/4/18
Thu
4/12/18 24
4.3 Training is completed 1 day Fri 4/13/18 Fri 4/13/18 25
4.4 Final Documents are made 3 days Mon
4/16/18
Wed
4/18/18 26
4.5 Documents are Reviewed 2 days Thu
4/19/18 Fri 4/20/18 27
4.6 Sign off the documents 1 day Mon
4/23/18
Mon
4/23/18 28
5 Project is Closed 1 day Tue
4/24/18
Tue
4/24/18 29
3/20/18
3 Testing 4 days Mon
3/26/18
Thu
3/29/18
3.1 Black Box testing 3 days Mon
3/26/18
Wed
3/28/18 17
3.2 White Box testing 3 days Mon
3/26/18
Wed
3/28/18 17
3.3 Compatibility testing 3 days Mon
3/26/18
Wed
3/28/18 17
3.4 Website Developed 1 day Thu
3/29/18
Thu
3/29/18 19, 20, 21
4 Training and Documentation 17 days Fri 3/30/18 Mon
4/23/18
4.1 Training Manuals are formed 3 days Fri 3/30/18 Tue 4/3/18 22
4.2 Training is provided to the staffs and
users 7 days Wed
4/4/18
Thu
4/12/18 24
4.3 Training is completed 1 day Fri 4/13/18 Fri 4/13/18 25
4.4 Final Documents are made 3 days Mon
4/16/18
Wed
4/18/18 26
4.5 Documents are Reviewed 2 days Thu
4/19/18 Fri 4/20/18 27
4.6 Sign off the documents 1 day Mon
4/23/18
Mon
4/23/18 28
5 Project is Closed 1 day Tue
4/24/18
Tue
4/24/18 29
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
VERBANIA INC. SOCIAL MEDIA IT SOLUTION 8
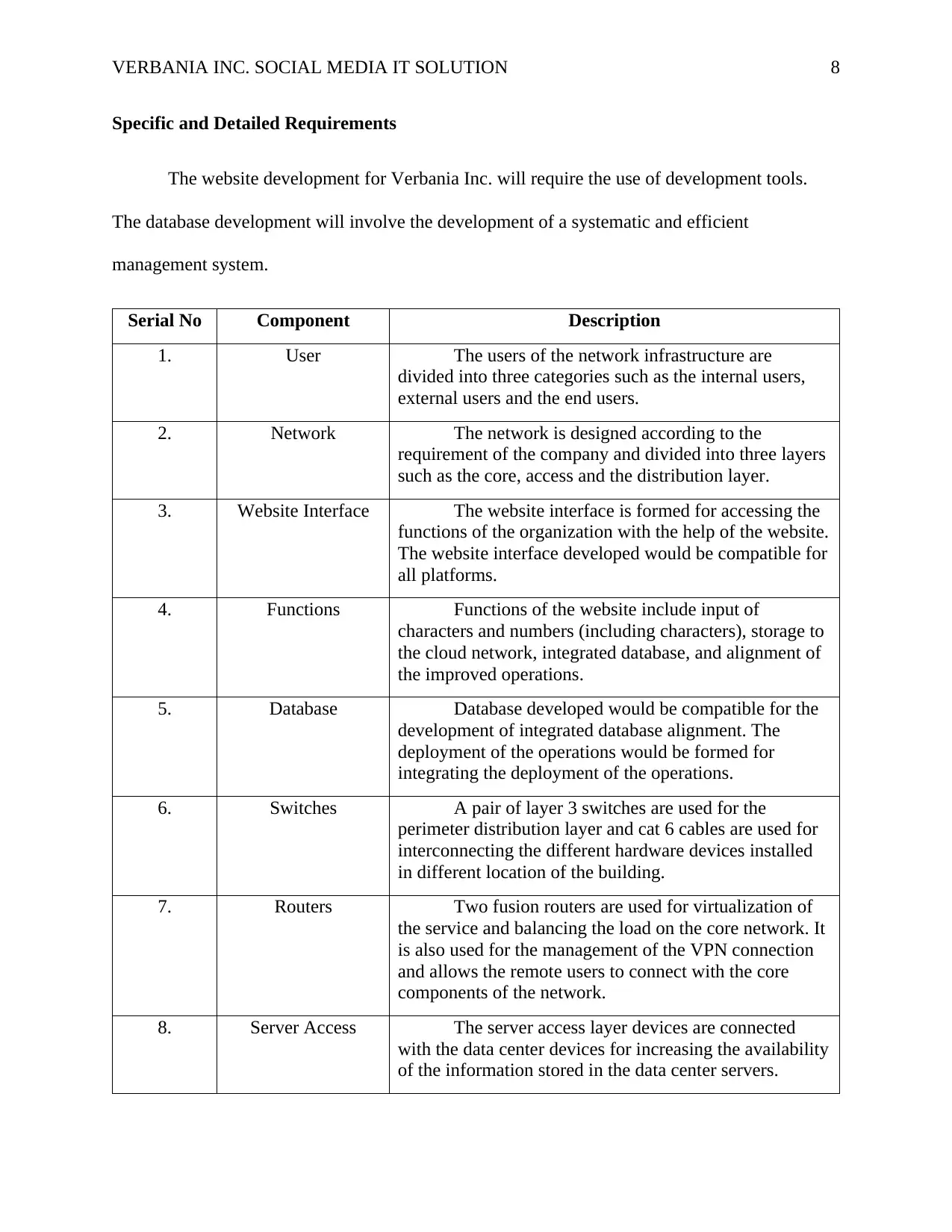
Specific and Detailed Requirements
The website development for Verbania Inc. will require the use of development tools.
The database development will involve the development of a systematic and efficient
management system.
Serial No Component Description
1. User The users of the network infrastructure are
divided into three categories such as the internal users,
external users and the end users.
2. Network The network is designed according to the
requirement of the company and divided into three layers
such as the core, access and the distribution layer.
3. Website Interface The website interface is formed for accessing the
functions of the organization with the help of the website.
The website interface developed would be compatible for
all platforms.
4. Functions Functions of the website include input of
characters and numbers (including characters), storage to
the cloud network, integrated database, and alignment of
the improved operations.
5. Database Database developed would be compatible for the
development of integrated database alignment. The
deployment of the operations would be formed for
integrating the deployment of the operations.
6. Switches A pair of layer 3 switches are used for the
perimeter distribution layer and cat 6 cables are used for
interconnecting the different hardware devices installed
in different location of the building.
7. Routers Two fusion routers are used for virtualization of
the service and balancing the load on the core network. It
is also used for the management of the VPN connection
and allows the remote users to connect with the core
components of the network.
8. Server Access The server access layer devices are connected
with the data center devices for increasing the availability
of the information stored in the data center servers.
Specific and Detailed Requirements
The website development for Verbania Inc. will require the use of development tools.
The database development will involve the development of a systematic and efficient
management system.
Serial No Component Description
1. User The users of the network infrastructure are
divided into three categories such as the internal users,
external users and the end users.
2. Network The network is designed according to the
requirement of the company and divided into three layers
such as the core, access and the distribution layer.
3. Website Interface The website interface is formed for accessing the
functions of the organization with the help of the website.
The website interface developed would be compatible for
all platforms.
4. Functions Functions of the website include input of
characters and numbers (including characters), storage to
the cloud network, integrated database, and alignment of
the improved operations.
5. Database Database developed would be compatible for the
development of integrated database alignment. The
deployment of the operations would be formed for
integrating the deployment of the operations.
6. Switches A pair of layer 3 switches are used for the
perimeter distribution layer and cat 6 cables are used for
interconnecting the different hardware devices installed
in different location of the building.
7. Routers Two fusion routers are used for virtualization of
the service and balancing the load on the core network. It
is also used for the management of the VPN connection
and allows the remote users to connect with the core
components of the network.
8. Server Access The server access layer devices are connected
with the data center devices for increasing the availability
of the information stored in the data center servers.
VERBANIA INC. SOCIAL MEDIA IT SOLUTION 9
Hardware and Software Requirements of Verbania Inc.
The list of hardware and software requirements for the proposed solution for Verbania
Inc. includes hardware components and software components. The hardware components include
a collection of switches, routers, firewalls, servers, and necessary cables. The software
components include Microsoft Windows 2012 r2 standard Operating System, Microsoft Visual
Studio, and Dreamweaver for design.
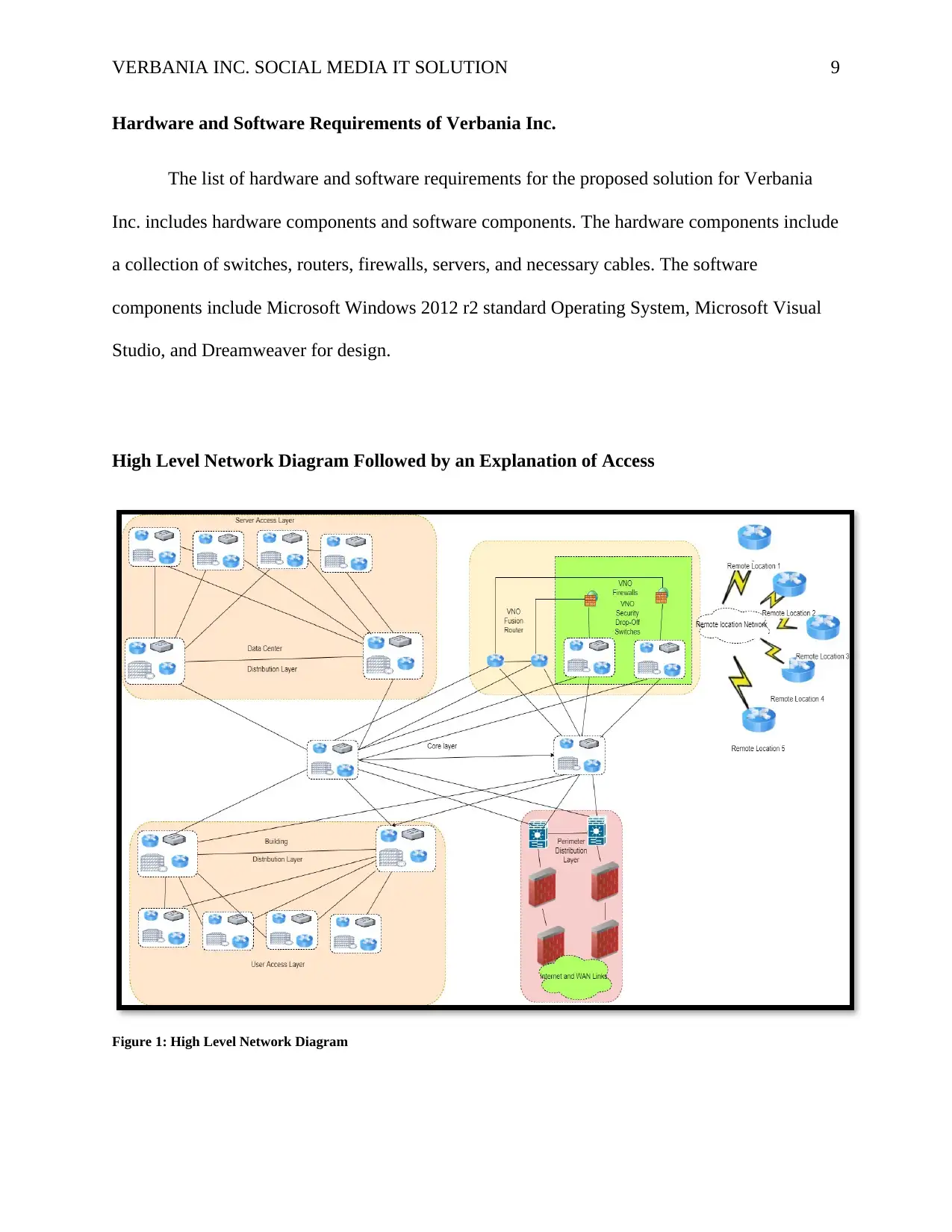
High Level Network Diagram Followed by an Explanation of Access
Figure 1: High Level Network Diagram
Hardware and Software Requirements of Verbania Inc.
The list of hardware and software requirements for the proposed solution for Verbania
Inc. includes hardware components and software components. The hardware components include
a collection of switches, routers, firewalls, servers, and necessary cables. The software
components include Microsoft Windows 2012 r2 standard Operating System, Microsoft Visual
Studio, and Dreamweaver for design.
High Level Network Diagram Followed by an Explanation of Access
Figure 1: High Level Network Diagram
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

VERBANIA INC. SOCIAL MEDIA IT SOLUTION 10
The users of the network infrastructure are divided into three categories being the internal
users, the external users, and the end users. The network is designed according to the
requirement of the company and divided into three layers such as the core, access and the
distribution layer. A firewall is installed in the distribution layer for restricting the unauthorized
users to access the core components of the network and increase the security of the network.
Another set of firewalls are installed for securing the remote network and restricting the
unauthorized users to access the core components via the remote links. A pair of layer 3 switches
is used for the perimeter distribution layer and cat 6 cables are used for interconnecting the
different hardware devices installed in different location of the building. The server access layer
devices are connected with the data center devices for increasing the availability of the
information stored in the data center servers. Two fusion routers are used for virtualization of the
service and balancing the load on the core network. It is also used for the management of the
VPN connection and allows the remote users to connect with the core components of the
network. The internet and WAN link zones are created for securing the network with the
installation of firewall devices in the network and to control the data traffic in the network. The
scalability and flexibility of the network is increased with the implementation of network
virtualization and server virtualization.
With consideration to the listed operational structure, Verbania Inc. would be helped by
forming the effective and improved social media site and application. The system development
would comprise of developing the improved functionality and the formation of the Verbania
network architecture. This report has provided the highlights of the necessary requirements of
developing this website.
The users of the network infrastructure are divided into three categories being the internal
users, the external users, and the end users. The network is designed according to the
requirement of the company and divided into three layers such as the core, access and the
distribution layer. A firewall is installed in the distribution layer for restricting the unauthorized
users to access the core components of the network and increase the security of the network.
Another set of firewalls are installed for securing the remote network and restricting the
unauthorized users to access the core components via the remote links. A pair of layer 3 switches
is used for the perimeter distribution layer and cat 6 cables are used for interconnecting the
different hardware devices installed in different location of the building. The server access layer
devices are connected with the data center devices for increasing the availability of the
information stored in the data center servers. Two fusion routers are used for virtualization of the
service and balancing the load on the core network. It is also used for the management of the
VPN connection and allows the remote users to connect with the core components of the
network. The internet and WAN link zones are created for securing the network with the
installation of firewall devices in the network and to control the data traffic in the network. The
scalability and flexibility of the network is increased with the implementation of network
virtualization and server virtualization.
With consideration to the listed operational structure, Verbania Inc. would be helped by
forming the effective and improved social media site and application. The system development
would comprise of developing the improved functionality and the formation of the Verbania
network architecture. This report has provided the highlights of the necessary requirements of
developing this website.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

VERBANIA INC. SOCIAL MEDIA IT SOLUTION 11
SECTION 2: SYSTEM ANALYSIS
Corporate Network Topology Recommendation
There are various types of topologies but the best amongst these topologies is the star
topology. For wireless networks, this the star topology is used by the Wi-Fi based products
which works in the infrastructure mode. This topology is similar to or resembles the topology
which is used by the 10BASE-T along with this this topology is also the fastest version of the
Ethernet which uses a switch (Parandehgheibi & Modiano, 2013). In this case, the access points
act as the switch due to the fact that the stations are connected by the use of the access points
instead of connecting directly with each other. This is very expensive per unit but the
performance is permitted at an excess speed compared to the 10BASE-T Ethernet speed; along
with speed, the managing of the star topology is also easier for the wired network. Star topology
in wired network helps in connecting several cables of each computer to a single central wiring
nexus which is often termed as the switch or the hub. Due to the fact that each computer will be
using a separate cable there would be less effect or will affect only the single machine whenever
there is an occurrence of network failure. So, during network failures will the single computer
will get affected and the other computers will be functioning in a normal way (Centenaro et al,
2016). This type of cabling is much easier to diagnosis and the problems can be bypassed very
easily. The form that is to be used along with being the most appropriate form on the wired
LAN’s are Fast Ethernet or Gigabit Ethernet. The star topology also helps in the wired networks
when there is a need of adding new things to the network along with helping during the moving
of things, or making any kind of changes by making this changing and addition process at a
much faster rate along with being more efficient and cost effective (Rawat et al. 2014).
SECTION 2: SYSTEM ANALYSIS
Corporate Network Topology Recommendation
There are various types of topologies but the best amongst these topologies is the star
topology. For wireless networks, this the star topology is used by the Wi-Fi based products
which works in the infrastructure mode. This topology is similar to or resembles the topology
which is used by the 10BASE-T along with this this topology is also the fastest version of the
Ethernet which uses a switch (Parandehgheibi & Modiano, 2013). In this case, the access points
act as the switch due to the fact that the stations are connected by the use of the access points
instead of connecting directly with each other. This is very expensive per unit but the
performance is permitted at an excess speed compared to the 10BASE-T Ethernet speed; along
with speed, the managing of the star topology is also easier for the wired network. Star topology
in wired network helps in connecting several cables of each computer to a single central wiring
nexus which is often termed as the switch or the hub. Due to the fact that each computer will be
using a separate cable there would be less effect or will affect only the single machine whenever
there is an occurrence of network failure. So, during network failures will the single computer
will get affected and the other computers will be functioning in a normal way (Centenaro et al,
2016). This type of cabling is much easier to diagnosis and the problems can be bypassed very
easily. The form that is to be used along with being the most appropriate form on the wired
LAN’s are Fast Ethernet or Gigabit Ethernet. The star topology also helps in the wired networks
when there is a need of adding new things to the network along with helping during the moving
of things, or making any kind of changes by making this changing and addition process at a
much faster rate along with being more efficient and cost effective (Rawat et al. 2014).

VERBANIA INC. SOCIAL MEDIA IT SOLUTION 12
Cabling Recommendation
In the star topology, it is possible to use a twisted pair cable or an optical cable. Coaxial
cables are also used but, only in few instances and will not be recommended for Verbania. The
best cable type for this purpose would be to use twisted pair cable. There are two types of twisted
cable one is the shielded twisted pair and another one is the un-shielded twisted pair (Comer,
2015). Amongst the types of twisted pair, the best is the shielded twisted pair. The main reason
for using the shielded twisted pair is that it is not susceptible to any type of interfaces caused by
radio or electrical frequencies. Along with this, the cables can also be extended to a maximum
distance when shielded cables are used. The wires in this type of cable are individually shielded
by the use of a foil along with this there is also a foil or braid shield present inside the jacket of
the cable which is covered as well. This shield is present outside the individual wire along with
the whole cable. These wires are twisted so as to reduce the noise or it can be stated particularly
that this is done for reducing cross talk (Strobel, Stolle & Utschick, 2013). The twisted pair does
this by cancelling the unwanted cross-talk signals. Along with this, this type of wiring is more
durable and lasts for a longer time. There is a speed of about 100 megabits per second in these
types of wires. Data is carried by this cabling, which includes packets of information, and this is
done by the use of the internet as well as the commercial computer networks through the wires
present inside and via many wires. The use of the two wires helps in avoiding the delay caused
during transmission. The data that is being sent by the shielded twisted wire are also very secure
compared to any other type of cables because the data flowing is kept proper by the components
present inside and outside the cable (Chowdhury, 2013).
Cabling Recommendation
In the star topology, it is possible to use a twisted pair cable or an optical cable. Coaxial
cables are also used but, only in few instances and will not be recommended for Verbania. The
best cable type for this purpose would be to use twisted pair cable. There are two types of twisted
cable one is the shielded twisted pair and another one is the un-shielded twisted pair (Comer,
2015). Amongst the types of twisted pair, the best is the shielded twisted pair. The main reason
for using the shielded twisted pair is that it is not susceptible to any type of interfaces caused by
radio or electrical frequencies. Along with this, the cables can also be extended to a maximum
distance when shielded cables are used. The wires in this type of cable are individually shielded
by the use of a foil along with this there is also a foil or braid shield present inside the jacket of
the cable which is covered as well. This shield is present outside the individual wire along with
the whole cable. These wires are twisted so as to reduce the noise or it can be stated particularly
that this is done for reducing cross talk (Strobel, Stolle & Utschick, 2013). The twisted pair does
this by cancelling the unwanted cross-talk signals. Along with this, this type of wiring is more
durable and lasts for a longer time. There is a speed of about 100 megabits per second in these
types of wires. Data is carried by this cabling, which includes packets of information, and this is
done by the use of the internet as well as the commercial computer networks through the wires
present inside and via many wires. The use of the two wires helps in avoiding the delay caused
during transmission. The data that is being sent by the shielded twisted wire are also very secure
compared to any other type of cables because the data flowing is kept proper by the components
present inside and outside the cable (Chowdhury, 2013).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 61
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





