IT Risk Management: VIC Government Data Security Analysis Report
VerifiedAdded on 2020/03/13
|16
|3331
|113
Report
AI Summary
This report provides a detailed analysis of IT risk management and data security for the Victorian government. It begins with an illustration of the VIC security risk analysis, followed by an explanation of the risk prioritization process. The report then compares accidental and deliberate threats, discussing the challenges of information system implementation and differentiating between risk and uncertainty. Various types of risks, including business, process, project, and product risks, are examined. The report also delves into specific risk classifications within the information processing system, such as network structure, technical errors, human-made mistakes, and physical failures. Economic risks, translation risks, and transaction risks are also considered. The analysis further explores accidental and deliberate threats, including examples of each. Finally, the report addresses the challenges of information system implementation for the VIC government, proposing strategies for controlling risks and ensuring data security. The report concludes with risk mitigation strategies and references.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
Victorian protective data security case study had been considered for forming the analysis of
the IT system risks and threats of security. The government rules of IT applications that are to
be implemented while carrying out IT projects. Data security and privacy concerns are
elaborated as per the specific requirements.
Victorian protective data security case study had been considered for forming the analysis of
the IT system risks and threats of security. The government rules of IT applications that are to
be implemented while carrying out IT projects. Data security and privacy concerns are
elaborated as per the specific requirements.

Contents
1. Illustration of the VIC security risk analysis..........................................................................4
2. Explanation of the diagram and Risk Prioritizing..................................................................4
3. Comparing Accidental and Deliberate Threats......................................................................7
4. Challenges of Information system Implementation...............................................................9
5. Comparing ‘’Risk’’ and ‘’Uncertainty’’ of Victorian Data security...................................12
6. Risk mitigation for VIC government...................................................................................13
Reference..................................................................................................................................15
1. Illustration of the VIC security risk analysis..........................................................................4
2. Explanation of the diagram and Risk Prioritizing..................................................................4
3. Comparing Accidental and Deliberate Threats......................................................................7
4. Challenges of Information system Implementation...............................................................9
5. Comparing ‘’Risk’’ and ‘’Uncertainty’’ of Victorian Data security...................................12
6. Risk mitigation for VIC government...................................................................................13
Reference..................................................................................................................................15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
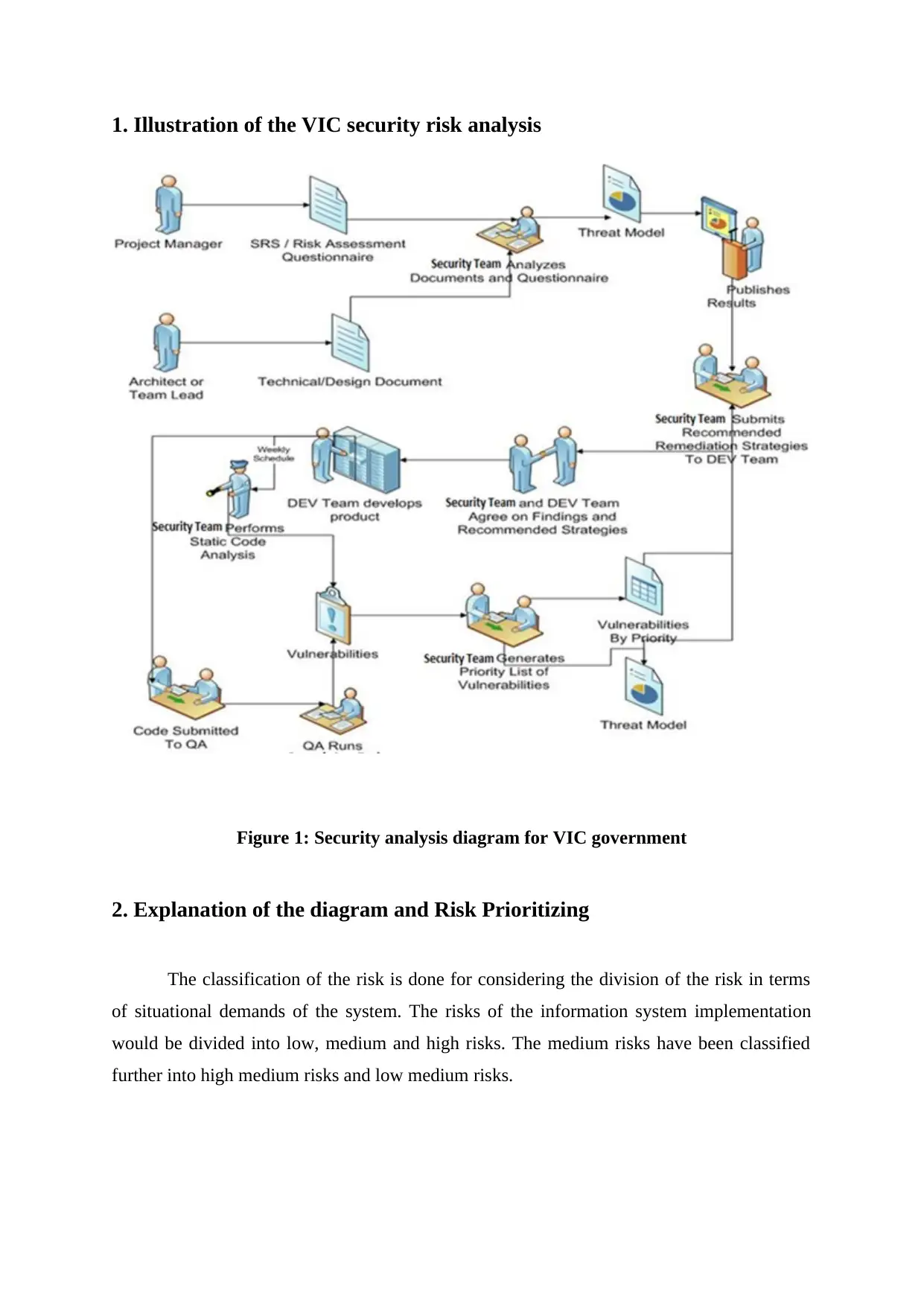
1. Illustration of the VIC security risk analysis
Figure 1: Security analysis diagram for VIC government
2. Explanation of the diagram and Risk Prioritizing
The classification of the risk is done for considering the division of the risk in terms
of situational demands of the system. The risks of the information system implementation
would be divided into low, medium and high risks. The medium risks have been classified
further into high medium risks and low medium risks.
Figure 1: Security analysis diagram for VIC government
2. Explanation of the diagram and Risk Prioritizing
The classification of the risk is done for considering the division of the risk in terms
of situational demands of the system. The risks of the information system implementation
would be divided into low, medium and high risks. The medium risks have been classified
further into high medium risks and low medium risks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Figure 2: 3 Levels of Risks
The VIC government would be formed for classifying the risk in their own levels and
it is required for taking some stern steps in forming the preventing measures in the
organization. The four types of risks are business risks, process risks, project risks and
product risks. The business risks are related to the firms which handling any kind of business.
While implementing or starting a business one must take all the care and calculate the
business risk. It is a probability of a company to get loose. There is no chance of getting
profit or gain rather they calculate only the loss. They are influenced by the government
regulations, price sales of the unit, economic stability and instability, climatic changes,
competitions. It is related to the uncertainty in the profit of the business. The process risk is
associated with the loss in the process due to the failure of a certain process, inadequate work
or due to the external events (Tsoumas & Tryfonas, 2004).
Figure 3: Different Types of risks
The VIC government would be formed for classifying the risk in their own levels and
it is required for taking some stern steps in forming the preventing measures in the
organization. The four types of risks are business risks, process risks, project risks and
product risks. The business risks are related to the firms which handling any kind of business.
While implementing or starting a business one must take all the care and calculate the
business risk. It is a probability of a company to get loose. There is no chance of getting
profit or gain rather they calculate only the loss. They are influenced by the government
regulations, price sales of the unit, economic stability and instability, climatic changes,
competitions. It is related to the uncertainty in the profit of the business. The process risk is
associated with the loss in the process due to the failure of a certain process, inadequate work
or due to the external events (Tsoumas & Tryfonas, 2004).
Figure 3: Different Types of risks

There are 6 classification of risk in information processing system of the VIC
government. The risk of network structure had been involved with the communication of the
risk factors. The IT implementation has to face a major risk of technology related in the
operations of the VIC government organization. The technical risk arises from the errors of
IT design and operations. The human made mistakes in the operations of the information
system is another major issue in the project. The human error is causing a process failure. It is
like entering a wrong data in the program causing an error or entering a wrong price in the
stock exchange market causing the error, which in turn leads to the loss. The development of
the man made errors would imply the error free system for the organization of VIC. The
safety issue would be implied for forming the effective and developed processing. The human
health safety risks would be a major issue for deploying the effective strain in the
organization. The mechanical and phycial failure of the information system would be implied
for forming the issues in the development of the opertaions. The processing quality is the
final issue in the development of the effective opertaions. The checking of the quality is a
major factor that had resulted in forming the effective opertaions by regulating the operations.
The state of the busines would be implied for forming the effective flow of opertaions
(Liderman, 2008).
The exposure of the risk had been implied for forming the effective deployment of the
effective processing in the organization. There are three types of risk allocated in the
development of the information system for VIC organization. The transaction would be
helpful for implying the development of the effective communication. The various factors of
risk in the organization are economic risk, translation of the risk, and transaction risk.
Sometimes the currency change in the international market also gives this loss. One has to
take careful steps in this currency market value. It is associated mostly with the business
involving in the more than one currency. It matters a lot due to the time lagging between the
transaction execution and the settlement. The purchasing company must pay lot more money
to earn the company to overcome the loss and avoid the debts. The next part is regarding the
translation risk. The translation risk is associated with foreign exchange. Here the companies
associated with the foreign currency and foreign assets have this kind of risk. The solution for
this kind of problem is to use the currency swapping techniques and adopted currency
exchange. fixed income risks also should include in this.
government. The risk of network structure had been involved with the communication of the
risk factors. The IT implementation has to face a major risk of technology related in the
operations of the VIC government organization. The technical risk arises from the errors of
IT design and operations. The human made mistakes in the operations of the information
system is another major issue in the project. The human error is causing a process failure. It is
like entering a wrong data in the program causing an error or entering a wrong price in the
stock exchange market causing the error, which in turn leads to the loss. The development of
the man made errors would imply the error free system for the organization of VIC. The
safety issue would be implied for forming the effective and developed processing. The human
health safety risks would be a major issue for deploying the effective strain in the
organization. The mechanical and phycial failure of the information system would be implied
for forming the issues in the development of the opertaions. The processing quality is the
final issue in the development of the effective opertaions. The checking of the quality is a
major factor that had resulted in forming the effective opertaions by regulating the operations.
The state of the busines would be implied for forming the effective flow of opertaions
(Liderman, 2008).
The exposure of the risk had been implied for forming the effective deployment of the
effective processing in the organization. There are three types of risk allocated in the
development of the information system for VIC organization. The transaction would be
helpful for implying the development of the effective communication. The various factors of
risk in the organization are economic risk, translation of the risk, and transaction risk.
Sometimes the currency change in the international market also gives this loss. One has to
take careful steps in this currency market value. It is associated mostly with the business
involving in the more than one currency. It matters a lot due to the time lagging between the
transaction execution and the settlement. The purchasing company must pay lot more money
to earn the company to overcome the loss and avoid the debts. The next part is regarding the
translation risk. The translation risk is associated with foreign exchange. Here the companies
associated with the foreign currency and foreign assets have this kind of risk. The solution for
this kind of problem is to use the currency swapping techniques and adopted currency
exchange. fixed income risks also should include in this.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

According to Stoneburner, Goguen, & Feringa (2002), the definition of the economic
risk can be implied for forming the evaluation of the macroeconomics and its change. The
evaluation would include the activities of stock change and regulation of the government of
the countries. The instability of the government in political situation would tend to overlook
the factors of risk mitigation. The international investors will have more risks than the
domestic investors. Hence the foreign investors always mind this risk before investing in
away country stocks. The basic types of the economic risks are the risk of the rise of the
prices of the raw materials. It also includes the price rise in the energy also. The next risk is
the increase in the minimum wages, this is not possible if the company stocks are decreased.
But the minimum wages are mandatory in all the companies. The next risk is due to the risk
of the production price decreasing. Even the price remains same the company profit may not
increase. The next one is interest rate risk which also known as credit risk. It occurs in the
companies where they use the credit resources. The increase of the rates of the interest would
lead to the negative effciency of opertaions (Purtell, 2008). The last risk factor that had been
analhyzed in this report would be implied for the implementation of the informaiton system
in the organization. The exportation of the risk would comply the development of the risk
categories.
3. Comparing Accidental and Deliberate Threats
Accidental threats are one which deletes the files accidentally and some files are sent
to wrong persons like emails to wrong persons. Some other accidental threats like portable
devices are lost or miss placed. The portable devices may include USB devices, hard disks,
pen drive or other memory device kind of stuff. These files may be retrieved if they are saved
in the secondary storage other devices, sometimes cloud storage. But the problem here is not
the data lost or retrieving. The main problem is from the sending file to a wrong person. If the
information is confidential then the problem arises. (Orzechowski, 2007)
It is important for ensuring that the activities of the project of implementing the
information system in deployed for forming the improvement of the operations. The
accidental threats are also formed that results in critical evaluation of the existing facilities for
forming the deployment of the operations. The basic types of the economic risks are the risk
of the rise of the prices of the raw materials. It also includes the price rise in the energy also.
risk can be implied for forming the evaluation of the macroeconomics and its change. The
evaluation would include the activities of stock change and regulation of the government of
the countries. The instability of the government in political situation would tend to overlook
the factors of risk mitigation. The international investors will have more risks than the
domestic investors. Hence the foreign investors always mind this risk before investing in
away country stocks. The basic types of the economic risks are the risk of the rise of the
prices of the raw materials. It also includes the price rise in the energy also. The next risk is
the increase in the minimum wages, this is not possible if the company stocks are decreased.
But the minimum wages are mandatory in all the companies. The next risk is due to the risk
of the production price decreasing. Even the price remains same the company profit may not
increase. The next one is interest rate risk which also known as credit risk. It occurs in the
companies where they use the credit resources. The increase of the rates of the interest would
lead to the negative effciency of opertaions (Purtell, 2008). The last risk factor that had been
analhyzed in this report would be implied for the implementation of the informaiton system
in the organization. The exportation of the risk would comply the development of the risk
categories.
3. Comparing Accidental and Deliberate Threats
Accidental threats are one which deletes the files accidentally and some files are sent
to wrong persons like emails to wrong persons. Some other accidental threats like portable
devices are lost or miss placed. The portable devices may include USB devices, hard disks,
pen drive or other memory device kind of stuff. These files may be retrieved if they are saved
in the secondary storage other devices, sometimes cloud storage. But the problem here is not
the data lost or retrieving. The main problem is from the sending file to a wrong person. If the
information is confidential then the problem arises. (Orzechowski, 2007)
It is important for ensuring that the activities of the project of implementing the
information system in deployed for forming the improvement of the operations. The
accidental threats are also formed that results in critical evaluation of the existing facilities for
forming the deployment of the operations. The basic types of the economic risks are the risk
of the rise of the prices of the raw materials. It also includes the price rise in the energy also.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
The next risk is the increase in the minimum wages, this is not possible if the company stocks
are decreased. But the minimum wages are mandatory in all the companies. The next risk is
due to the risk of the production price decreasing. Even the price remains same the company
profit may not increase. The next one is interest rate risk which also known as credit risk. The
purchasing company must pay lot more money to earn the company to overcome the loss and
avoid the debts. The next part is regarding the translation risk. The translation risk is
associated with foreign exchange.
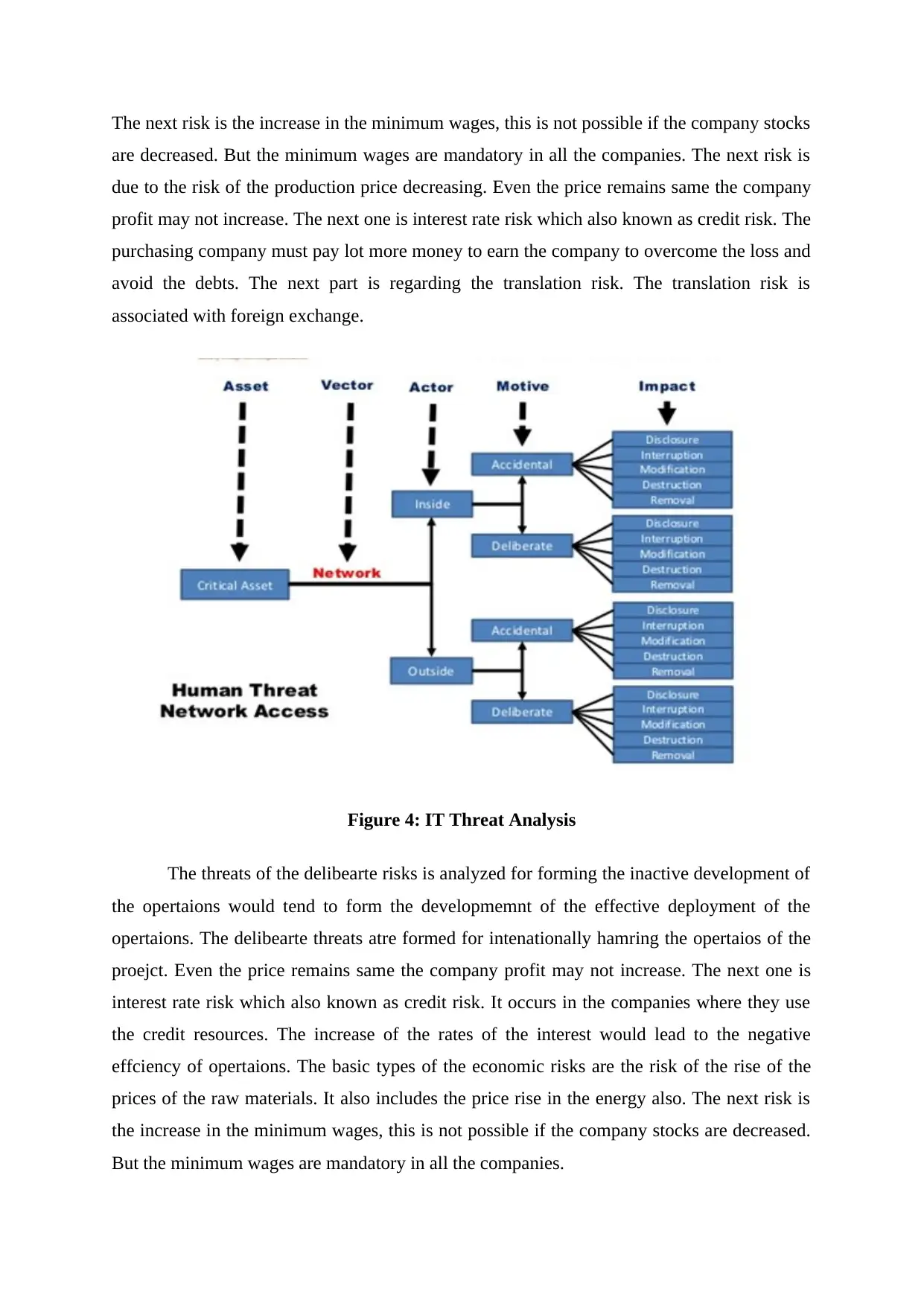
Figure 4: IT Threat Analysis
The threats of the delibearte risks is analyzed for forming the inactive development of
the opertaions would tend to form the developmemnt of the effective deployment of the
opertaions. The delibearte threats atre formed for intenationally hamring the opertaios of the
proejct. Even the price remains same the company profit may not increase. The next one is
interest rate risk which also known as credit risk. It occurs in the companies where they use
the credit resources. The increase of the rates of the interest would lead to the negative
effciency of opertaions. The basic types of the economic risks are the risk of the rise of the
prices of the raw materials. It also includes the price rise in the energy also. The next risk is
the increase in the minimum wages, this is not possible if the company stocks are decreased.
But the minimum wages are mandatory in all the companies.
are decreased. But the minimum wages are mandatory in all the companies. The next risk is
due to the risk of the production price decreasing. Even the price remains same the company
profit may not increase. The next one is interest rate risk which also known as credit risk. The
purchasing company must pay lot more money to earn the company to overcome the loss and
avoid the debts. The next part is regarding the translation risk. The translation risk is
associated with foreign exchange.
Figure 4: IT Threat Analysis
The threats of the delibearte risks is analyzed for forming the inactive development of
the opertaions would tend to form the developmemnt of the effective deployment of the
opertaions. The delibearte threats atre formed for intenationally hamring the opertaios of the
proejct. Even the price remains same the company profit may not increase. The next one is
interest rate risk which also known as credit risk. It occurs in the companies where they use
the credit resources. The increase of the rates of the interest would lead to the negative
effciency of opertaions. The basic types of the economic risks are the risk of the rise of the
prices of the raw materials. It also includes the price rise in the energy also. The next risk is
the increase in the minimum wages, this is not possible if the company stocks are decreased.
But the minimum wages are mandatory in all the companies.

The implementation of the hard passwords are a major factor that can help in
developing the solutions to the effective unauthorize access. The unauthorized access had
been formed for intentionally developing the issues in implementing the opertaional issues in
the organization. The hard passwords and parapharse for forming the effective security of the
information system would be helpful for forming the accurate secuirty in the organization
(Halliday, Badenhorst & Solms, 1996). The execution of the hard passwords are a main
consideration that can help in building up the answers for the compelling unauthorize get to.
The unapproved get to had been framed for deliberately building up the issues in actualizing
the opertaional issues in the association. The hard passwords and parapharse for shaping the
viable security of the data framework would be useful for framing the exact secuirty in the
association
Guidelines for implying public and personal safety
The different variables of hazard in the association are monetary hazard, interpretation
of the hazard, and exchange chance. Sometimes the money change in the global market
additionally gives this misfortune. One needs to make watchful strides in this money
showcase esteem. It is related generally with the business including in the more than one
money. It is important a considerable measure because of the time slacking between the
exchange execution and the settlement. According to Carr (2004), the development of the
security threats would form the effective analysis of the implementation procedure. The
internal threat factors for the implementation of the information system would tend to result
in forming the issues of the operations in the organization. The internal focus of the
organization would be implied effectively for adjusting the corporate analysis of the effective
risk management in the organization. The various factors of risk in the organization are
economic risk, translation of the risk, and transaction risk. Sometimes the currency change in
the international market also gives this loss. One has to take careful steps in this currency
market value. It is associated mostly with the business involving in the more than one
currency. It matters a lot due to the time lagging between the transaction execution and the
settlement.
4. Challenges of Information system Implementation
VIC government will confront different issues in deciding the technique for
controlling the dangers and securities, which are confronted by the administration. The
developing the solutions to the effective unauthorize access. The unauthorized access had
been formed for intentionally developing the issues in implementing the opertaional issues in
the organization. The hard passwords and parapharse for forming the effective security of the
information system would be helpful for forming the accurate secuirty in the organization
(Halliday, Badenhorst & Solms, 1996). The execution of the hard passwords are a main
consideration that can help in building up the answers for the compelling unauthorize get to.
The unapproved get to had been framed for deliberately building up the issues in actualizing
the opertaional issues in the association. The hard passwords and parapharse for shaping the
viable security of the data framework would be useful for framing the exact secuirty in the
association
Guidelines for implying public and personal safety
The different variables of hazard in the association are monetary hazard, interpretation
of the hazard, and exchange chance. Sometimes the money change in the global market
additionally gives this misfortune. One needs to make watchful strides in this money
showcase esteem. It is related generally with the business including in the more than one
money. It is important a considerable measure because of the time slacking between the
exchange execution and the settlement. According to Carr (2004), the development of the
security threats would form the effective analysis of the implementation procedure. The
internal threat factors for the implementation of the information system would tend to result
in forming the issues of the operations in the organization. The internal focus of the
organization would be implied effectively for adjusting the corporate analysis of the effective
risk management in the organization. The various factors of risk in the organization are
economic risk, translation of the risk, and transaction risk. Sometimes the currency change in
the international market also gives this loss. One has to take careful steps in this currency
market value. It is associated mostly with the business involving in the more than one
currency. It matters a lot due to the time lagging between the transaction execution and the
settlement.
4. Challenges of Information system Implementation
VIC government will confront different issues in deciding the technique for
controlling the dangers and securities, which are confronted by the administration. The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

hazard can be overseen by two ways. Outside advisors do this kind of security administration.
They have essential thought regarding the instruments and methods of the administration and
a few security issues (Grzywak, 2000). These experts can cause the VIC government to
control the dangers with progress and in this way lessen the dangers. There are different
constraints in embracing this strategy moreover. The legislature should invest more cash and
energy behind the outer specialists. There can be particular issues like misconstruing between
the specialists and government. This kind of circumstance prompts more issue. The outside
advisors won't not comprehend the issue in subtle elements and there can be circumstances
where the specialists won't not be reliable.
This security administration is the most straightforward alternative accessible to the
legislature. Here the workers of the association will assume the part of counsels. There are
sure points of interest of this administration technique. The representatives are the piece of
the association and they know point by point data with the goal that the legislature won't need
to pay additional time and assets not at all like on account of outer counsels. There are sure
disservices of this technique moreover. The inward advisors can be impacted by a few
managers and get befuddled. This strategy can prompt inward disagreement of the
administration in view of various proposals. VIC government in having issues in picking their
security administration. Be that as it may, an immaculate and appropriate hazard
administration can help them to take care of their security issues. Outside and inward security
administration, both are valuable for the legislature.
They have essential thought regarding the instruments and methods of the administration and
a few security issues (Grzywak, 2000). These experts can cause the VIC government to
control the dangers with progress and in this way lessen the dangers. There are different
constraints in embracing this strategy moreover. The legislature should invest more cash and
energy behind the outer specialists. There can be particular issues like misconstruing between
the specialists and government. This kind of circumstance prompts more issue. The outside
advisors won't not comprehend the issue in subtle elements and there can be circumstances
where the specialists won't not be reliable.
This security administration is the most straightforward alternative accessible to the
legislature. Here the workers of the association will assume the part of counsels. There are
sure points of interest of this administration technique. The representatives are the piece of
the association and they know point by point data with the goal that the legislature won't need
to pay additional time and assets not at all like on account of outer counsels. There are sure
disservices of this technique moreover. The inward advisors can be impacted by a few
managers and get befuddled. This strategy can prompt inward disagreement of the
administration in view of various proposals. VIC government in having issues in picking their
security administration. Be that as it may, an immaculate and appropriate hazard
administration can help them to take care of their security issues. Outside and inward security
administration, both are valuable for the legislature.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Figure 5: IT Organisation Governance and Risk Management
Risk management Objectives
Risk management is an effective process for analyzing the development of the factors
of risk and developing some controlling factors for integrating in the organziation
(Bandyopadhyay, Mykytyn & Mykytyn, 1999). The risk management is employed for
forming the effective development of the opertaions. The integration of the risk assessment
would tend to form the analysis of the risk factors. The objectives of implementing the risk
factors are
Effective analysis of the risk: The effective analysis of the risk is the primary benefit
of implementing the effective risk management plan (Tsoumas & Tryfonas, 2004). The
Risk management Objectives
Risk management is an effective process for analyzing the development of the factors
of risk and developing some controlling factors for integrating in the organziation
(Bandyopadhyay, Mykytyn & Mykytyn, 1999). The risk management is employed for
forming the effective development of the opertaions. The integration of the risk assessment
would tend to form the analysis of the risk factors. The objectives of implementing the risk
factors are
Effective analysis of the risk: The effective analysis of the risk is the primary benefit
of implementing the effective risk management plan (Tsoumas & Tryfonas, 2004). The

development of risk management plan would tend to help in the development of the
opertaions.
Minimize the impact of risk: The risk management plan would help in reducing the
impact of the negative risk in the operations of the organiztaion (Bandyopadhyay, Mykytyn
& Mykytyn, 1999). The development of the project plan would be assisted by the use of the
risk management plan as it would tend to reduce the negative impact of the project.
We suggest the internal security and risk management from the above discussion. The
main reason is privacy and data safety. We cannot expect the privacy if we give the security
and risk management to outsiders. It is not easy to convince the stake holders to allow the
security management to outsiders. The system access must be strictly limited insiders. The
outsourcing is a bad idea in case of the security management. The other works can be
assigned to others through outsourcing. The risk calculating details and past data of the
organization is very confidential and hence it has to be maintained safely. The risks have to
be monitored every time, the inside people best choice this job.
5. Comparing ‘’Risk’’ and ‘’Uncertainty’’ of Victorian Data security.
Risk Uncertainty
Risk can be characterized as the
circumstance, which has a serious likelihood
of threat in up and coming future. Risks are
of two sorts, internal and external (Liderman,
2008). The security hazards in the VIC
government will be considered as critical.
Here the administration knows the odds of
the results. Dangers are controllable. The
administration can control the dangers. It
won't be wiped out but rather it can be
limited.
Uncertainty can be effortlessly characterized
as unconventionality. It can be characterized
as any circumstance where the future
happenings are not known (Purtell, 2008).
The VIC government won't know the result
without bounds occasions and this can
prompt hazard. Not at all like hazard,
uncertainty is not under the control of the
legislature and it can't be limited. When
something is not accessible and dependable
then that prompts uncertainty. Uncertainty
prompts the arrangement of hazard.
opertaions.
Minimize the impact of risk: The risk management plan would help in reducing the
impact of the negative risk in the operations of the organiztaion (Bandyopadhyay, Mykytyn
& Mykytyn, 1999). The development of the project plan would be assisted by the use of the
risk management plan as it would tend to reduce the negative impact of the project.
We suggest the internal security and risk management from the above discussion. The
main reason is privacy and data safety. We cannot expect the privacy if we give the security
and risk management to outsiders. It is not easy to convince the stake holders to allow the
security management to outsiders. The system access must be strictly limited insiders. The
outsourcing is a bad idea in case of the security management. The other works can be
assigned to others through outsourcing. The risk calculating details and past data of the
organization is very confidential and hence it has to be maintained safely. The risks have to
be monitored every time, the inside people best choice this job.
5. Comparing ‘’Risk’’ and ‘’Uncertainty’’ of Victorian Data security.
Risk Uncertainty
Risk can be characterized as the
circumstance, which has a serious likelihood
of threat in up and coming future. Risks are
of two sorts, internal and external (Liderman,
2008). The security hazards in the VIC
government will be considered as critical.
Here the administration knows the odds of
the results. Dangers are controllable. The
administration can control the dangers. It
won't be wiped out but rather it can be
limited.
Uncertainty can be effortlessly characterized
as unconventionality. It can be characterized
as any circumstance where the future
happenings are not known (Purtell, 2008).
The VIC government won't know the result
without bounds occasions and this can
prompt hazard. Not at all like hazard,
uncertainty is not under the control of the
legislature and it can't be limited. When
something is not accessible and dependable
then that prompts uncertainty. Uncertainty
prompts the arrangement of hazard.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





