Security Risk Assessment for VIC Government: A Comprehensive Analysis
VerifiedAdded on 2020/03/02
|15
|2520
|51
Report
AI Summary
This report analyzes the security risks and concerns faced by the VIC government, focusing on the protection of public and private data, as defined by the Privacy and Data Protection Act 2014. It assesses risks based on the CIA triad (Confidentiality, Integrity, Availability), categorizing threats as high, medium, and low risk. The report provides a comparative analysis of deliberate and accidental threats, ranking them in order of importance, and discusses the challenges the VIC government faces in deciding between internal and external security/risk management, drawing on relevant frameworks and guidelines. It further explores the difference between risk and uncertainty in the context of data security, and evaluates different approaches for risk control and mitigation available to the VIC government, referencing the VPDSF Framework. The report provides a comprehensive overview of data security, risk assessment, and management strategies for the VIC government.
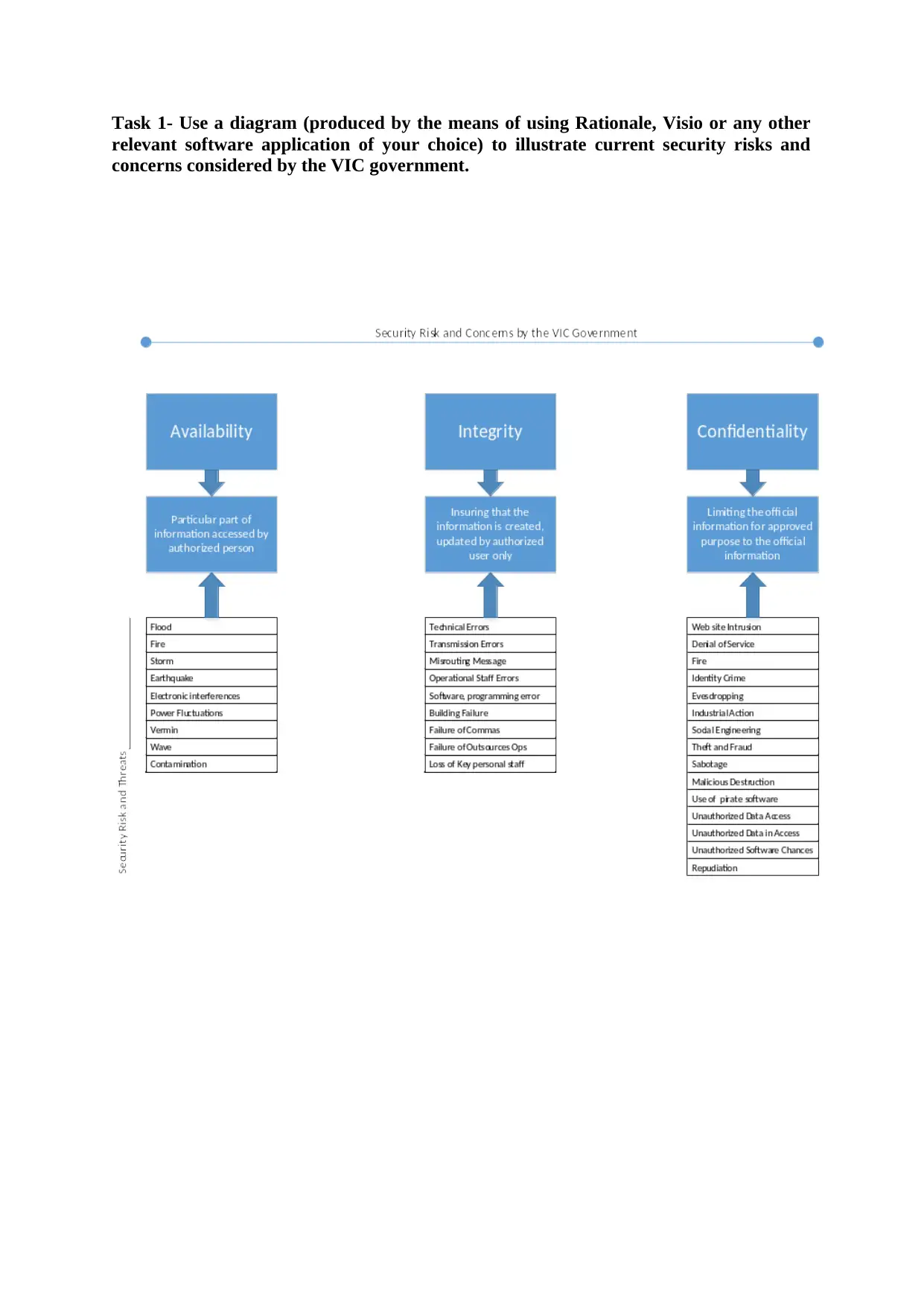
Task 1- Use a diagram (produced by the means of using Rationale, Visio or any other
relevant software application of your choice) to illustrate current security risks and
concerns considered by the VIC government.
relevant software application of your choice) to illustrate current security risks and
concerns considered by the VIC government.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Task 2- Provide detailed explanation of the diagram and identify the areas of: high,
medium, medium-low, and low risk exposure.
Diagram Overview
The government of VIC has some objective for securing the public and private data which is
in digital information form. These objectives they try to achieve with Privacy and Data
Protection Act 2014. These objectives have some hierarchy in the defined security objective
which are given in the boxes in the above diagram.
Availability - Whenever an authorized party needs access to the information, it
ensures that they can access. Only right person can access the right information at the
right time. If in case any denial seems in accessing the information than it is very
normal attack now a day. News of DDoS attacks are very frequent or can say once in
a week we see this kind of news. Some other parameters like power outage, natural
disaster, floods etc could also lead to lack of availability.
Integrity – Maintaining the state of information. Integrity is all about protecting the
information from unauthorized parties. In online money transaction, it happens many
times that person was trying to send $100 but the information was tempered and
transaction was dome of actual amount $10,000. So, cryptography plays very
important role for ensuring the data integrity.
Confidentiality – When we start talking about the confidentiality of information then
definitely we are talking about protecting information from unauthorized
users/parties. Each information has some value like bank statements, credit card
number, educational documents, government documents etc. So, protecting
information is major concern. So, encryption of information is about confidentiality of
information. Which ensures that only the right person can access/read the information
with Key.
The objectives were obtained from the VIC Government Information Security Guidelines in
Part One – Introduction, Page 12.
It is important for us to understand that every threat and risk can arise in any of area either
private data or public data.
In this case study, public data is taken as information (for security).
medium, medium-low, and low risk exposure.
Diagram Overview
The government of VIC has some objective for securing the public and private data which is
in digital information form. These objectives they try to achieve with Privacy and Data
Protection Act 2014. These objectives have some hierarchy in the defined security objective
which are given in the boxes in the above diagram.
Availability - Whenever an authorized party needs access to the information, it
ensures that they can access. Only right person can access the right information at the
right time. If in case any denial seems in accessing the information than it is very
normal attack now a day. News of DDoS attacks are very frequent or can say once in
a week we see this kind of news. Some other parameters like power outage, natural
disaster, floods etc could also lead to lack of availability.
Integrity – Maintaining the state of information. Integrity is all about protecting the
information from unauthorized parties. In online money transaction, it happens many
times that person was trying to send $100 but the information was tempered and
transaction was dome of actual amount $10,000. So, cryptography plays very
important role for ensuring the data integrity.
Confidentiality – When we start talking about the confidentiality of information then
definitely we are talking about protecting information from unauthorized
users/parties. Each information has some value like bank statements, credit card
number, educational documents, government documents etc. So, protecting
information is major concern. So, encryption of information is about confidentiality of
information. Which ensures that only the right person can access/read the information
with Key.
The objectives were obtained from the VIC Government Information Security Guidelines in
Part One – Introduction, Page 12.
It is important for us to understand that every threat and risk can arise in any of area either
private data or public data.
In this case study, public data is taken as information (for security).

For an Example – Use of pirate software can change security concern for CIA Model i.e.
Confidentiality, Integrity and Availability.
Risk Assessment – To identify the high, medium and low risk factors for the VIC
Government, I analysed that it can be on the basis of total number of security matters affected
by some particular threat.
Below given threats are according to the VIC Government mentioned in the document-
According to VIC government VMIA-Practice Guide we must define the objective to
determine the risk. One can consider the objective in HIGH, MEDIUM and LOW context for
future perspective.
HIGH – It is a threat which occurs very frequently and higher degree of effect like Web Site
Intrusion. Being a government organization VIC faces some similar issues with very high
effects for the loss of information (public data). I have listed down threats which are of high
risk category.
Unauthorised Software Changes
Web Site Intrusion
Social Engineering
Theft & Fraud
Outsourced Failure
Loss of Key work force
Re-Routing of Messages
Software/Programming Errors
Malicious Code
Operations
MEDIUM – Threat in this risk category can have major, moderate, minor or extreme effect
with probability of occasional, remote, probable or frequent like programming errors.
Because error in coding can cause major effect on the output in the form of security risk and
can result in loss of business information or any kind of information depends upon agency. I
have mentioned below categories of medium risk can happen. Each given threat is related to
VIC government Data Security Framework for Security Obligations Governance.
Unauthorised Data Access
Dial-in Access for unauthorized users
Confidentiality, Integrity and Availability.
Risk Assessment – To identify the high, medium and low risk factors for the VIC
Government, I analysed that it can be on the basis of total number of security matters affected
by some particular threat.
Below given threats are according to the VIC Government mentioned in the document-
According to VIC government VMIA-Practice Guide we must define the objective to
determine the risk. One can consider the objective in HIGH, MEDIUM and LOW context for
future perspective.
HIGH – It is a threat which occurs very frequently and higher degree of effect like Web Site
Intrusion. Being a government organization VIC faces some similar issues with very high
effects for the loss of information (public data). I have listed down threats which are of high
risk category.
Unauthorised Software Changes
Web Site Intrusion
Social Engineering
Theft & Fraud
Outsourced Failure
Loss of Key work force
Re-Routing of Messages
Software/Programming Errors
Malicious Code
Operations
MEDIUM – Threat in this risk category can have major, moderate, minor or extreme effect
with probability of occasional, remote, probable or frequent like programming errors.
Because error in coding can cause major effect on the output in the form of security risk and
can result in loss of business information or any kind of information depends upon agency. I
have mentioned below categories of medium risk can happen. Each given threat is related to
VIC government Data Security Framework for Security Obligations Governance.
Unauthorised Data Access
Dial-in Access for unauthorized users
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Operational Staff Faults
Technical Issues
Identity Crime
Sabotage
Malicious Destruction of Data and Facilities
Transmission Errors
Masquerade
MEDIUM LOW - It is about accessing information without authorization. If any agency
stored its user’s data in any form either excel or in SQL that only the authorized person
within the organization can access this information.
LOW – If any of employee within the organization uses pirate software then some issues can
occur occasionally. In VMIA Practice Guide they talked about the user’s detail for some sale
purchase data. So, in this case employee of the agency may not be able to properly access the
data as some threat effect it. Some other natural hazards also come under the category of Low
Risk category which are mentioned below -
Fire (environmental)
Flood
Extreme high or low of Humidity and Temperature
Denial of Service
Eavesdropping
Vermin
Fire (accidental)
Power Variations
Failure of Power Supply
Tidal Surge/Wave
Earthquake
Storm
Electronic Interference
Industrial Action
Use of Pirated Software
Building Fire
Technical Issues
Identity Crime
Sabotage
Malicious Destruction of Data and Facilities
Transmission Errors
Masquerade
MEDIUM LOW - It is about accessing information without authorization. If any agency
stored its user’s data in any form either excel or in SQL that only the authorized person
within the organization can access this information.
LOW – If any of employee within the organization uses pirate software then some issues can
occur occasionally. In VMIA Practice Guide they talked about the user’s detail for some sale
purchase data. So, in this case employee of the agency may not be able to properly access the
data as some threat effect it. Some other natural hazards also come under the category of Low
Risk category which are mentioned below -
Fire (environmental)
Flood
Extreme high or low of Humidity and Temperature
Denial of Service
Eavesdropping
Vermin
Fire (accidental)
Power Variations
Failure of Power Supply
Tidal Surge/Wave
Earthquake
Storm
Electronic Interference
Industrial Action
Use of Pirated Software
Building Fire
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Task 3 - Carry out comparative analysis of the Deliberate and Accidental Threats
and rank those threats in order of importance. Justify your rankings not only based
on the case study but also by the means of doing further research and drawing upon
other relevant case studies (e.g. Security guidelines for other private and public
organizations) that you can identify.
With the help of Given CIA security concern in VIC Government’s VICTORIAN
PROTECTIVE DATA SECURITY FRAMEWORK, I have tried to make some comparative
analysis of deliberate and accidental threats. The common threats which have very high risk
exposure for both type deliberate and accidental threats are mentioned below –
Malicious Code
Social Engineering
Theft & Fraud
Unauthorised Software Changes
Web Site Intrusions
Failure of Outsourced Operations
Loss or Absence of Key Personnel
Misrouting or Re-Routing Messages
Software or Programming Errors
According to ENISA threat landscape - Top 15 Cyber Threats 2015 –
Malware
Web-based attack
Web application attack
Botnets
Denial of service
Physical Damage Threat/loss
Insider Threat
Phishing
Spam
and rank those threats in order of importance. Justify your rankings not only based
on the case study but also by the means of doing further research and drawing upon
other relevant case studies (e.g. Security guidelines for other private and public
organizations) that you can identify.
With the help of Given CIA security concern in VIC Government’s VICTORIAN
PROTECTIVE DATA SECURITY FRAMEWORK, I have tried to make some comparative
analysis of deliberate and accidental threats. The common threats which have very high risk
exposure for both type deliberate and accidental threats are mentioned below –
Malicious Code
Social Engineering
Theft & Fraud
Unauthorised Software Changes
Web Site Intrusions
Failure of Outsourced Operations
Loss or Absence of Key Personnel
Misrouting or Re-Routing Messages
Software or Programming Errors
According to ENISA threat landscape - Top 15 Cyber Threats 2015 –
Malware
Web-based attack
Web application attack
Botnets
Denial of service
Physical Damage Threat/loss
Insider Threat
Phishing
Spam

Exploit Kits
Data Breaches
Identity Theft
Information Leakage
Ransomware
Cyber espionage
Based on the given task next threat category will be the medium risk exposure for deliberate
and accidental threats’
Identity Crime
Malicious Destruction of Data and Facilities
Masquerade
Sabotage
Unauthorised Data Access
Unauthorised Dial-In Access
Operational Staff Errors
Technical Failures
Transmission Errors
Looking at Enisa’s top 15 threats of 2015, the medium-risk threats are ranked accordingly
(Marinos, 2015).
1. Malicious Destruction of Data Facilities
2. Sabotage
3. Masquerade
4. Unauthorised Data Access
5. Identity Crime
6. Unauthorised Dial-In Access
7. Operational Staff Errors
8. Technical Failures
Data Breaches
Identity Theft
Information Leakage
Ransomware
Cyber espionage
Based on the given task next threat category will be the medium risk exposure for deliberate
and accidental threats’
Identity Crime
Malicious Destruction of Data and Facilities
Masquerade
Sabotage
Unauthorised Data Access
Unauthorised Dial-In Access
Operational Staff Errors
Technical Failures
Transmission Errors
Looking at Enisa’s top 15 threats of 2015, the medium-risk threats are ranked accordingly
(Marinos, 2015).
1. Malicious Destruction of Data Facilities
2. Sabotage
3. Masquerade
4. Unauthorised Data Access
5. Identity Crime
6. Unauthorised Dial-In Access
7. Operational Staff Errors
8. Technical Failures
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9. Transmission Errors
The final threat category is the low risk exposure for deliberate and accidental threats.
Contamination
Earthquake
Electronic Interference
Extremes of Temperature and Humidity
Failure of Power Supply
Fire
Flood
Power Fluctuations
Storm
Tidal Surge/Wave
Vermin
Denial of Service
Eavesdropping
Industrial Action
Use of Pirated Software
Building Fire
Failure of Communications Services
Some of low risk threats has common theme for all type of threats. So, this would rank higher
to lower risk threat.
Agency Personnel Security Responsibilities
For the support of protection for information, assets with people with sound work force
security practices were developed by the Australian Government personnel security
guidelines – Agency personnel security responsibilities. So, in this guideline provide some
advice to help in their application of control identification Australian Government personnel
security protocol. Few of the guidelines covers are given below –
the trusted insider threat
work force management and security risk management
sharing of information
some procedural fairness
The final threat category is the low risk exposure for deliberate and accidental threats.
Contamination
Earthquake
Electronic Interference
Extremes of Temperature and Humidity
Failure of Power Supply
Fire
Flood
Power Fluctuations
Storm
Tidal Surge/Wave
Vermin
Denial of Service
Eavesdropping
Industrial Action
Use of Pirated Software
Building Fire
Failure of Communications Services
Some of low risk threats has common theme for all type of threats. So, this would rank higher
to lower risk threat.
Agency Personnel Security Responsibilities
For the support of protection for information, assets with people with sound work force
security practices were developed by the Australian Government personnel security
guidelines – Agency personnel security responsibilities. So, in this guideline provide some
advice to help in their application of control identification Australian Government personnel
security protocol. Few of the guidelines covers are given below –
the trusted insider threat
work force management and security risk management
sharing of information
some procedural fairness
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

screening for agency employment
few ongoing proprietary for employment, including:
controlling and evaluating suitability
security experience training
security circumstances announcing and examination
agency actions on separation of personnel or those on extended leave
temporary access only for few minute
need of agency security clearance
eligibility remission
process of ongoing security authorization conservation
agency responsibilities to actively monitor security clearance holders, including:
health check on yearly basis
changes in reporting in circumstances
reporting scheme contacted by Australian Government contact
actions of agency on partition/ extended leave of work force with
security clearances
demands for the use of management of contractors’ clearances.
few ongoing proprietary for employment, including:
controlling and evaluating suitability
security experience training
security circumstances announcing and examination
agency actions on separation of personnel or those on extended leave
temporary access only for few minute
need of agency security clearance
eligibility remission
process of ongoing security authorization conservation
agency responsibilities to actively monitor security clearance holders, including:
health check on yearly basis
changes in reporting in circumstances
reporting scheme contacted by Australian Government contact
actions of agency on partition/ extended leave of work force with
security clearances
demands for the use of management of contractors’ clearances.

Task 4 - While drawing upon theories, tools and patterns covered in the subject as well
as your own research, explain the challenges that the VIC government is going to face
while deciding on whether security/risk management should be carried out internally or
externally (e.g. via outsourcing).
VIC government made by many agencies and each agency required to ensure that it act
according to the VIC government information security policy. Every department and agency
very based on staff size and its business complexities which is one of the challenge to decide
how they can manage risk/security either internally or externally.
According to the VPDSF Framework June 2016 v1.0 security/risk management should be
carried out internally by the agency.
Each organization must have complete control over establishing, implementing and maintain
security policies and procedures proportionate to their size, resources and risk posture. Some
challenges that VIC government may face are mentioned below:
Does VIC government have enough people employed in organization with technical
knowledge to manage the security/risk and system?
Would VIC government be able to define properly document, communication interval
and regularly review of security issues related to all persons with access to public
sector data?
Does organization will ensure about the contracted service providers with access to
public sector data that may do or do not involve in the practice the VPDSS?
Is the VIC government being able to start with the necessary security infrastructure to
carry the security/risk internally?
as your own research, explain the challenges that the VIC government is going to face
while deciding on whether security/risk management should be carried out internally or
externally (e.g. via outsourcing).
VIC government made by many agencies and each agency required to ensure that it act
according to the VIC government information security policy. Every department and agency
very based on staff size and its business complexities which is one of the challenge to decide
how they can manage risk/security either internally or externally.
According to the VPDSF Framework June 2016 v1.0 security/risk management should be
carried out internally by the agency.
Each organization must have complete control over establishing, implementing and maintain
security policies and procedures proportionate to their size, resources and risk posture. Some
challenges that VIC government may face are mentioned below:
Does VIC government have enough people employed in organization with technical
knowledge to manage the security/risk and system?
Would VIC government be able to define properly document, communication interval
and regularly review of security issues related to all persons with access to public
sector data?
Does organization will ensure about the contracted service providers with access to
public sector data that may do or do not involve in the practice the VPDSS?
Is the VIC government being able to start with the necessary security infrastructure to
carry the security/risk internally?
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

If the internal staff try to calculate error with the safety of the complete IT systems and
Networks also then there is no financial complex action when the event receives. Managing
security/risk internally is itself a risk as no other backup management will be there. So,
managing the security/risk internally also represent a contradiction with the real user error.
In this case VIC Government choose to manage its security/risk internally, so it will focus on
the following issues:
Managing physical security controls
Suitability and eligibility for accessing information i.e. data breach by external parties
Preventing unauthorized access of the information
Information assessment potential comprises to confidentiality, availability and
integrity
Ensuring adequate tracking
Networks also then there is no financial complex action when the event receives. Managing
security/risk internally is itself a risk as no other backup management will be there. So,
managing the security/risk internally also represent a contradiction with the real user error.
In this case VIC Government choose to manage its security/risk internally, so it will focus on
the following issues:
Managing physical security controls
Suitability and eligibility for accessing information i.e. data breach by external parties
Preventing unauthorized access of the information
Information assessment potential comprises to confidentiality, availability and
integrity
Ensuring adequate tracking
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Task 5 - 5. Explain the difference between the concepts of ‘’Risk’’ and ‘’Uncertainty’’
(make sure that your discussion is linked to the case considered).
“Risk is an uncertain event or condition that, if it occurs, has a positive or negative effect on
one or more project objective such as scope, schedule, cost, and quality.” PMBOK Guide
Fifth edition.
So, basically risk is a condition which is unplanned event and in any case if it occurs it can
affect any part of the organization/agency. Which can convert into loss of valuable
information. In some documents risk is divided into two types – positive risk and negative
risk. Is risk directly affects your information then it is positive risk and if it affects
information in some negative sense than it is negative risk. A future event is made for known
risk and organization use some future reserve to manage these risks.
Public Data stored on a server is down temporary because of electricity supply issue, so if
organization plan for UPS to avoid this risk.
Where uncertainty is lack of planning, resources etc. It is about the not having certainty in
some flow of managing risk/security because of frequent changes done in the system which
was designed for security of information of an organization. So, the output of uncertainty is
also not known and cannot be measured. In case if do not keep track of security threats in
past than we cannot guess what is most common threat we will receive in future very soon
and cannot protect our information as well.
(make sure that your discussion is linked to the case considered).
“Risk is an uncertain event or condition that, if it occurs, has a positive or negative effect on
one or more project objective such as scope, schedule, cost, and quality.” PMBOK Guide
Fifth edition.
So, basically risk is a condition which is unplanned event and in any case if it occurs it can
affect any part of the organization/agency. Which can convert into loss of valuable
information. In some documents risk is divided into two types – positive risk and negative
risk. Is risk directly affects your information then it is positive risk and if it affects
information in some negative sense than it is negative risk. A future event is made for known
risk and organization use some future reserve to manage these risks.
Public Data stored on a server is down temporary because of electricity supply issue, so if
organization plan for UPS to avoid this risk.
Where uncertainty is lack of planning, resources etc. It is about the not having certainty in
some flow of managing risk/security because of frequent changes done in the system which
was designed for security of information of an organization. So, the output of uncertainty is
also not known and cannot be measured. In case if do not keep track of security threats in
past than we cannot guess what is most common threat we will receive in future very soon
and cannot protect our information as well.

According to given in VPDSF Framework one must ensure about the organization threats
which were identified in past, risk through business decision while applying security controls
to prevent the information (public sector data) so uncertainty and risk can be avoided easily.
Task 6 - Discuss and evaluate (with examples) different approaches available to the VIC
government for risk control and mitigation.
According to VPDSF Framework there are two main result in which the PDPA that support a
planned, considered and risk-based approach which can be protective to data security:
Security Risk Profile Assessment (SRPA): It is the process of assessment of the information
which is public sector organization’s protective data security risks
Protective Data Security Plan (PDSP): This is main as it is a plan of action to identify and
recover protective data security of the organisation which also include the mitigation of
identified risks.
Business Context Treatment Plan
Identification of Risk Residual Plan
Analysis of Risk
Evaluation of Risk
Security Planning
Security Risk Profile
Assessment
Protective Data Security
Plan
which were identified in past, risk through business decision while applying security controls
to prevent the information (public sector data) so uncertainty and risk can be avoided easily.
Task 6 - Discuss and evaluate (with examples) different approaches available to the VIC
government for risk control and mitigation.
According to VPDSF Framework there are two main result in which the PDPA that support a
planned, considered and risk-based approach which can be protective to data security:
Security Risk Profile Assessment (SRPA): It is the process of assessment of the information
which is public sector organization’s protective data security risks
Protective Data Security Plan (PDSP): This is main as it is a plan of action to identify and
recover protective data security of the organisation which also include the mitigation of
identified risks.
Business Context Treatment Plan
Identification of Risk Residual Plan
Analysis of Risk
Evaluation of Risk
Security Planning
Security Risk Profile
Assessment
Protective Data Security
Plan
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





