Comprehensive Report: VIC Government Security Risks and Concerns
VerifiedAdded on 2020/03/02
|11
|2816
|230
Report
AI Summary
This report provides a comprehensive analysis of the security risks and concerns facing the Victorian Government, focusing on the Victorian Protective Data Security Framework (VPDSF). It categorizes risks into high, medium, medium-low, and low-risk exposures, detailing potential threats such as insider threats, availability risks, data breaches, and operational errors. The report differentiates between deliberate and accidental threats, offering a comparative analysis and examples, and highlights challenges in executing security and risk management strategies, including issues with skill gaps, insider privileges, and the cost of external solutions. It distinguishes between risks and uncertainties, emphasizing the need for risk control and mitigation through administrative, technical, and physical security approaches. The report concludes with recommendations for enhancing data security within the VIC Government, referencing various security standards and governance models.

VIC Government
Security Risks and Concerns
8/25/2017
Security Risks and Concerns
8/25/2017
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

VIC Government
Table of Contents
Introduction.................................................................................................................................................3
Explanation of the Diagram.........................................................................................................................3
High-Risk Exposure................................................................................................................................3
Medium Risk Exposure...........................................................................................................................3
Medium-Low Risk Exposure...................................................................................................................3
Low Risk Exposure.................................................................................................................................4
Deliberate and Accidental Threats...............................................................................................................4
Challenges for Execution of the Security/Risk Management Execution......................................................5
Difference between Risks and Uncertainty..................................................................................................6
Approaches for Risk Control and Mitigation...............................................................................................7
Administrative Approach........................................................................................................................7
Technical Approach.................................................................................................................................8
Physical Security Approach.....................................................................................................................8
Recommendations & Conclusion................................................................................................................8
References.................................................................................................................................................10
2
Table of Contents
Introduction.................................................................................................................................................3
Explanation of the Diagram.........................................................................................................................3
High-Risk Exposure................................................................................................................................3
Medium Risk Exposure...........................................................................................................................3
Medium-Low Risk Exposure...................................................................................................................3
Low Risk Exposure.................................................................................................................................4
Deliberate and Accidental Threats...............................................................................................................4
Challenges for Execution of the Security/Risk Management Execution......................................................5
Difference between Risks and Uncertainty..................................................................................................6
Approaches for Risk Control and Mitigation...............................................................................................7
Administrative Approach........................................................................................................................7
Technical Approach.................................................................................................................................8
Physical Security Approach.....................................................................................................................8
Recommendations & Conclusion................................................................................................................8
References.................................................................................................................................................10
2

VIC Government
Introduction
Victorian Protective Data Security Framework (VPDSF) is the scheme that has been launched by
the Victorian Government to manage the data security risks and attacks that are associated with
Victoria’s public sector and industries. There are three sections and classifications that are
included in VPDSF viz. security standards, assurance model and the supporting security guides
and resources. The framework provides the mechanism to deal to with the probable and possible
security risks and attacks. It is necessary for the Victorian Government to have a clear account of
the data security risks that may occur to develop the mechanisms and measures to control and
prevent them.
High-Risk Exposure
There are a number of security risks and attacks that may take place in the data that is associated
with the Victoria’s public sector. Some of the high-exposure risks include the insider threats
along with the availability risks. There is a lot of privilege and access that is provided to the staff
members, data owners and the public sector associates. These entities may take undue advantage
of the privileges that have been provided to them to cause severe damage. In case of the VIC
Government, there are multiple agencies, organizations, units and members that are involved.
There is also a huge presence of systems and applications that are used. This can result in the use
of a vulnerable access point to flood the network with unnecessary traffic to cause availability
attacks (Cpdp, 2016).
Medium Risk Exposure
There may also be integrity attacks and data breaches/leakage that may take place in the VIC
Government public sector setup. This is because of the reason that there is a huge amount of
public and personal data that is exchanged which may be breached by the malevolent entities by
altering the contents that are present.
Medium-Low Risk Exposure
There are a number of legal and regulatory obligations that may come up as a result of the
violation of the data security associated with an agency, organization, user or a member. These
obligations will result in certain cases and there probability is somewhat low. These risks are,
therefore place in the category of medium-low risk exposure.
3
Introduction
Victorian Protective Data Security Framework (VPDSF) is the scheme that has been launched by
the Victorian Government to manage the data security risks and attacks that are associated with
Victoria’s public sector and industries. There are three sections and classifications that are
included in VPDSF viz. security standards, assurance model and the supporting security guides
and resources. The framework provides the mechanism to deal to with the probable and possible
security risks and attacks. It is necessary for the Victorian Government to have a clear account of
the data security risks that may occur to develop the mechanisms and measures to control and
prevent them.
High-Risk Exposure
There are a number of security risks and attacks that may take place in the data that is associated
with the Victoria’s public sector. Some of the high-exposure risks include the insider threats
along with the availability risks. There is a lot of privilege and access that is provided to the staff
members, data owners and the public sector associates. These entities may take undue advantage
of the privileges that have been provided to them to cause severe damage. In case of the VIC
Government, there are multiple agencies, organizations, units and members that are involved.
There is also a huge presence of systems and applications that are used. This can result in the use
of a vulnerable access point to flood the network with unnecessary traffic to cause availability
attacks (Cpdp, 2016).
Medium Risk Exposure
There may also be integrity attacks and data breaches/leakage that may take place in the VIC
Government public sector setup. This is because of the reason that there is a huge amount of
public and personal data that is exchanged which may be breached by the malevolent entities by
altering the contents that are present.
Medium-Low Risk Exposure
There are a number of legal and regulatory obligations that may come up as a result of the
violation of the data security associated with an agency, organization, user or a member. These
obligations will result in certain cases and there probability is somewhat low. These risks are,
therefore place in the category of medium-low risk exposure.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
VIC Government
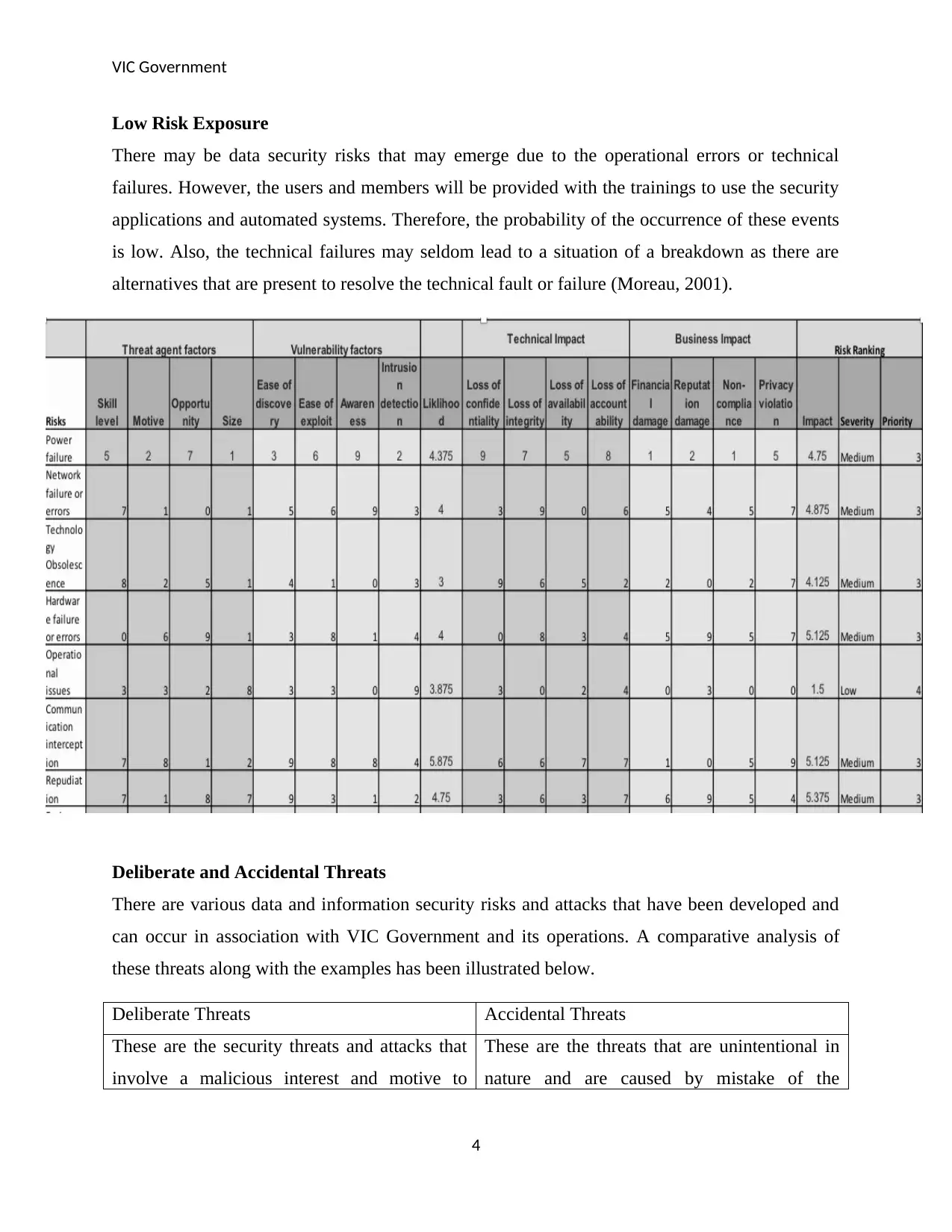
Low Risk Exposure
There may be data security risks that may emerge due to the operational errors or technical
failures. However, the users and members will be provided with the trainings to use the security
applications and automated systems. Therefore, the probability of the occurrence of these events
is low. Also, the technical failures may seldom lead to a situation of a breakdown as there are
alternatives that are present to resolve the technical fault or failure (Moreau, 2001).
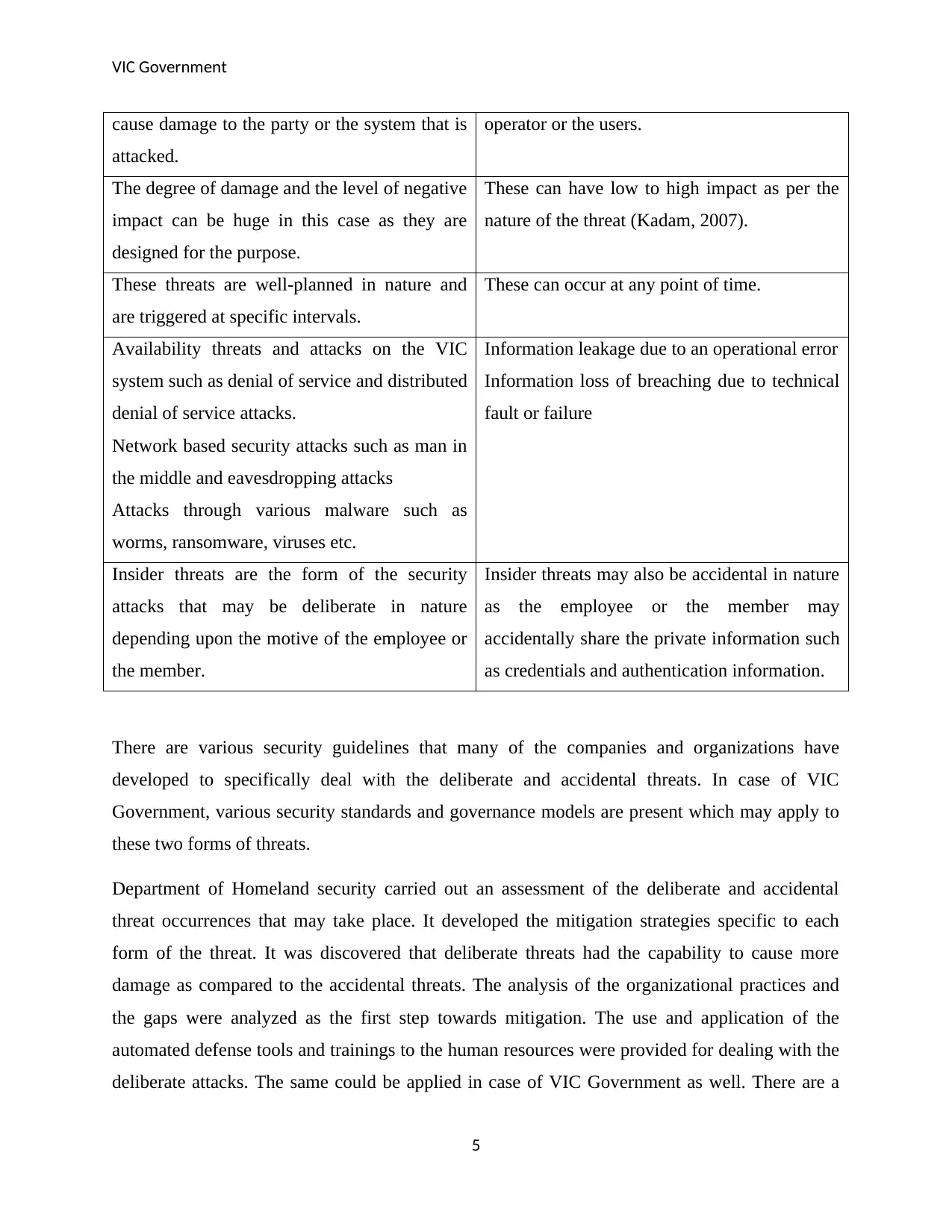
Deliberate and Accidental Threats
There are various data and information security risks and attacks that have been developed and
can occur in association with VIC Government and its operations. A comparative analysis of
these threats along with the examples has been illustrated below.
Deliberate Threats Accidental Threats
These are the security threats and attacks that
involve a malicious interest and motive to
These are the threats that are unintentional in
nature and are caused by mistake of the
4
Low Risk Exposure
There may be data security risks that may emerge due to the operational errors or technical
failures. However, the users and members will be provided with the trainings to use the security
applications and automated systems. Therefore, the probability of the occurrence of these events
is low. Also, the technical failures may seldom lead to a situation of a breakdown as there are
alternatives that are present to resolve the technical fault or failure (Moreau, 2001).
Deliberate and Accidental Threats
There are various data and information security risks and attacks that have been developed and
can occur in association with VIC Government and its operations. A comparative analysis of
these threats along with the examples has been illustrated below.
Deliberate Threats Accidental Threats
These are the security threats and attacks that
involve a malicious interest and motive to
These are the threats that are unintentional in
nature and are caused by mistake of the
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
VIC Government
cause damage to the party or the system that is
attacked.
operator or the users.
The degree of damage and the level of negative
impact can be huge in this case as they are
designed for the purpose.
These can have low to high impact as per the
nature of the threat (Kadam, 2007).
These threats are well-planned in nature and
are triggered at specific intervals.
These can occur at any point of time.
Availability threats and attacks on the VIC
system such as denial of service and distributed
denial of service attacks.
Network based security attacks such as man in
the middle and eavesdropping attacks
Attacks through various malware such as
worms, ransomware, viruses etc.
Information leakage due to an operational error
Information loss of breaching due to technical
fault or failure
Insider threats are the form of the security
attacks that may be deliberate in nature
depending upon the motive of the employee or
the member.
Insider threats may also be accidental in nature
as the employee or the member may
accidentally share the private information such
as credentials and authentication information.
There are various security guidelines that many of the companies and organizations have
developed to specifically deal with the deliberate and accidental threats. In case of VIC
Government, various security standards and governance models are present which may apply to
these two forms of threats.
Department of Homeland security carried out an assessment of the deliberate and accidental
threat occurrences that may take place. It developed the mitigation strategies specific to each
form of the threat. It was discovered that deliberate threats had the capability to cause more
damage as compared to the accidental threats. The analysis of the organizational practices and
the gaps were analyzed as the first step towards mitigation. The use and application of the
automated defense tools and trainings to the human resources were provided for dealing with the
deliberate attacks. The same could be applied in case of VIC Government as well. There are a
5
cause damage to the party or the system that is
attacked.
operator or the users.
The degree of damage and the level of negative
impact can be huge in this case as they are
designed for the purpose.
These can have low to high impact as per the
nature of the threat (Kadam, 2007).
These threats are well-planned in nature and
are triggered at specific intervals.
These can occur at any point of time.
Availability threats and attacks on the VIC
system such as denial of service and distributed
denial of service attacks.
Network based security attacks such as man in
the middle and eavesdropping attacks
Attacks through various malware such as
worms, ransomware, viruses etc.
Information leakage due to an operational error
Information loss of breaching due to technical
fault or failure
Insider threats are the form of the security
attacks that may be deliberate in nature
depending upon the motive of the employee or
the member.
Insider threats may also be accidental in nature
as the employee or the member may
accidentally share the private information such
as credentials and authentication information.
There are various security guidelines that many of the companies and organizations have
developed to specifically deal with the deliberate and accidental threats. In case of VIC
Government, various security standards and governance models are present which may apply to
these two forms of threats.
Department of Homeland security carried out an assessment of the deliberate and accidental
threat occurrences that may take place. It developed the mitigation strategies specific to each
form of the threat. It was discovered that deliberate threats had the capability to cause more
damage as compared to the accidental threats. The analysis of the organizational practices and
the gaps were analyzed as the first step towards mitigation. The use and application of the
automated defense tools and trainings to the human resources were provided for dealing with the
deliberate attacks. The same could be applied in case of VIC Government as well. There are a
5

VIC Government
number of employees and members that are engaged with different public sector setups in
Victoria (Sei, 2013). The human resources must be made capable to understand the likelihood of
the risk to deal with the same.
Challenges for Execution of the Security/Risk Management Execution
The security and risk management strategies and policies that the VIC Government is required to
carry out can be done through a number of different measures and processes.
There may be internal in-house development of the security tools and mechanisms that may be
distributed to the other agencies to make sure that the required policies and tools and
implemented across the entire public sector. It would be a cost-effective process as the internal
employees will be utilized for the required work. However, there may be issues in case of the
lack of skills or undue advantage taken out by an insider. The challenges that will come up in
case of the decision to go ahead with the internal execution are as listed below:
Lack of skills, knowledge or expertise will not serve the purpose of security mechanisms
to be applied as there will be security loopholes that will remain.
The insider employees will have the added privileges and complete knowledge about the
system and protocols which may be used negatively in the future.
The migration of the current system to the new system will be required to be done at a
rapid pace which may bring up operational and technical challenges.
There may also be acquiring of the tools and processes from the external sources. There are a
number of third-parties that work in the area of information and data security protocols and tools.
These parties may be contacted and the requirements must be outsources externally.
There will be certain challenges that will be associated with the external execution as well.
The process may be costly in nature as there will be additional costs that will be
associated (Taylor, 2015).
The third-parties may not cover all the requirements and specifications which may lead to
weaker security of the VIC Government processes.
There will be production data that will be required in certain cases for testing and
validation which may be misused.
6
number of employees and members that are engaged with different public sector setups in
Victoria (Sei, 2013). The human resources must be made capable to understand the likelihood of
the risk to deal with the same.
Challenges for Execution of the Security/Risk Management Execution
The security and risk management strategies and policies that the VIC Government is required to
carry out can be done through a number of different measures and processes.
There may be internal in-house development of the security tools and mechanisms that may be
distributed to the other agencies to make sure that the required policies and tools and
implemented across the entire public sector. It would be a cost-effective process as the internal
employees will be utilized for the required work. However, there may be issues in case of the
lack of skills or undue advantage taken out by an insider. The challenges that will come up in
case of the decision to go ahead with the internal execution are as listed below:
Lack of skills, knowledge or expertise will not serve the purpose of security mechanisms
to be applied as there will be security loopholes that will remain.
The insider employees will have the added privileges and complete knowledge about the
system and protocols which may be used negatively in the future.
The migration of the current system to the new system will be required to be done at a
rapid pace which may bring up operational and technical challenges.
There may also be acquiring of the tools and processes from the external sources. There are a
number of third-parties that work in the area of information and data security protocols and tools.
These parties may be contacted and the requirements must be outsources externally.
There will be certain challenges that will be associated with the external execution as well.
The process may be costly in nature as there will be additional costs that will be
associated (Taylor, 2015).
The third-parties may not cover all the requirements and specifications which may lead to
weaker security of the VIC Government processes.
There will be production data that will be required in certain cases for testing and
validation which may be misused.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

VIC Government
One of the common challenges that will come up in both the case would be the management of
the changes. There will be many changes that will be introduced in terms of the newer set of
processes and methods to be used along with improved security framework. However, the
employees and members will not be used to such changes and will require time to adapt to the
same.
Difference between Risks and Uncertainty
Risk is a predictable and a probable occurrence that may generally have a negative impact on the
parties that are affected. There are a number of data security risks that are associated with the
VIC Government. These risks include the availability, integrity, confidentiality and insider
threats and attacks.
The risks that are associated with the VIC government may have low to significant impact that
would be negative in nature. Some of the high-impact risks include the insider threats along with
the availability risks. case of the VIC Government, there are multiple agencies, organizations,
units and members that are involved. There is also a huge presence of systems and applications
that are used. This can result in the use of a vulnerable access point to flood the network with
unnecessary traffic to cause availability attacks. There may also be integrity attacks and data
breaches/leakage that may take place in the VIC Government public sector setup. There may be
data security risks that may emerge due to the operational errors or technical failures. However,
the users and members will be provided with the trainings to use the security applications and
automated systems (Kumar, 2013).
Uncertainties on the other hand are the occurrences that cannot be predicted or controlled. In
case of the VIC Government, there may be uncertainties involved in terms of the organizational
and Government policies and their impact on the security framework. For instance, there are a
number of data privacy rules and laws that have been setup by the Victorian Government. Also,
there are standards and rules that have been developed in association with the Governance model
or the security standards. There may be a sudden change, update or transformation in these
policies that may be executed. Such uncertainties will result in the requirements of the public
sector agencies to develop methodologies and procedures in accordance with the same. It may
result in either positive or negative impact.
7
One of the common challenges that will come up in both the case would be the management of
the changes. There will be many changes that will be introduced in terms of the newer set of
processes and methods to be used along with improved security framework. However, the
employees and members will not be used to such changes and will require time to adapt to the
same.
Difference between Risks and Uncertainty
Risk is a predictable and a probable occurrence that may generally have a negative impact on the
parties that are affected. There are a number of data security risks that are associated with the
VIC Government. These risks include the availability, integrity, confidentiality and insider
threats and attacks.
The risks that are associated with the VIC government may have low to significant impact that
would be negative in nature. Some of the high-impact risks include the insider threats along with
the availability risks. case of the VIC Government, there are multiple agencies, organizations,
units and members that are involved. There is also a huge presence of systems and applications
that are used. This can result in the use of a vulnerable access point to flood the network with
unnecessary traffic to cause availability attacks. There may also be integrity attacks and data
breaches/leakage that may take place in the VIC Government public sector setup. There may be
data security risks that may emerge due to the operational errors or technical failures. However,
the users and members will be provided with the trainings to use the security applications and
automated systems (Kumar, 2013).
Uncertainties on the other hand are the occurrences that cannot be predicted or controlled. In
case of the VIC Government, there may be uncertainties involved in terms of the organizational
and Government policies and their impact on the security framework. For instance, there are a
number of data privacy rules and laws that have been setup by the Victorian Government. Also,
there are standards and rules that have been developed in association with the Governance model
or the security standards. There may be a sudden change, update or transformation in these
policies that may be executed. Such uncertainties will result in the requirements of the public
sector agencies to develop methodologies and procedures in accordance with the same. It may
result in either positive or negative impact.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

VIC Government
Approaches for Risk Control and Mitigation
There are three different approaches that may be used by the Victorian Government for control
and mitigation of the risks.
Administrative Approach
The security framework and the set of the standards that have been developed will be required to
be updated from time to time. Also, it would be necessary to have enhanced administrative
policies and controls to ensure that these standards are correctly applied and the framework is as
per the current state of security.
The administrative approach will include the guidelines and processes that will be involved in
the upgrade of the security status. For instance, the senior management and the security team
shall be provided with the automated tools and schedule for the review and inspection activities.
Security auditors shall be deployed for carrying out the audits on the security.
Technical Approach
The technical approach that shall be applied and followed in the case of Victorian Government
shall include the logical and technical controls that are available for the maintenance and
enhancement of the security status.
For example, there are technical tools that are available for the detection and prevention of the
intruders on the networks. The use and implementation of the latest category of such tools will
lead to protection of the public and private information associated with the Victorian public
sector. There are also tools that have been developed in order to protect the denial and malware
attacks with the deployment of anti-denial and anti-malware tools (Rashvand, 2010).
The use of automated tools and mechanisms will lead to the creation and setting up of the
technical framework to control the risks associated with the VIC Government.
Physical Security Approach
The public sector of the VIC Government is composed of a number of organizations and
agencies that have their specific units, data centres and bases.
It is necessary to have an approach in place to deal with the data security risks and attacks.
Physical security is one of the methodologies that may be used for the control and mitigation of
8
Approaches for Risk Control and Mitigation
There are three different approaches that may be used by the Victorian Government for control
and mitigation of the risks.
Administrative Approach
The security framework and the set of the standards that have been developed will be required to
be updated from time to time. Also, it would be necessary to have enhanced administrative
policies and controls to ensure that these standards are correctly applied and the framework is as
per the current state of security.
The administrative approach will include the guidelines and processes that will be involved in
the upgrade of the security status. For instance, the senior management and the security team
shall be provided with the automated tools and schedule for the review and inspection activities.
Security auditors shall be deployed for carrying out the audits on the security.
Technical Approach
The technical approach that shall be applied and followed in the case of Victorian Government
shall include the logical and technical controls that are available for the maintenance and
enhancement of the security status.
For example, there are technical tools that are available for the detection and prevention of the
intruders on the networks. The use and implementation of the latest category of such tools will
lead to protection of the public and private information associated with the Victorian public
sector. There are also tools that have been developed in order to protect the denial and malware
attacks with the deployment of anti-denial and anti-malware tools (Rashvand, 2010).
The use of automated tools and mechanisms will lead to the creation and setting up of the
technical framework to control the risks associated with the VIC Government.
Physical Security Approach
The public sector of the VIC Government is composed of a number of organizations and
agencies that have their specific units, data centres and bases.
It is necessary to have an approach in place to deal with the data security risks and attacks.
Physical security is one of the methodologies that may be used for the control and mitigation of
8

VIC Government
the risks. There shall be advanced tools and security personnel that shall be made available on
every entry and exit gate of these agencies and organizations. Advanced identity management
and access control along with advanced monitoring of the security shall be carried out by the
physical entities present in all the location (Godlove, 2012).
It is necessary to have a combined approach to be followed in order to ensure that the overall
security of the VIC Government and the components that are associated with it are protected and
secured. It is also required to carry out continuous improvement and research work in the area of
security by the VIC Government to form a better state of security.
Recommendations & Conclusion
VIC Government is composed of a number of different units. The public sector components that
are present in Victoria play a significant role in the execution of a number of activities and
operations. There are a huge number of information and data sets that are associated with each of
the entity in the public sector. It is necessary to make sure that the security risks and attacks that
are probable in case of the VIC Government are controlled and prevented. The risks and attacks
in terms of the deliberate and accidental threats may take place which may violate the
availability, confidentiality and integrity of the information. It is required to have an integrated
approach towards security with the implementation of advanced administrative, technical and
physical security control (Leszczyna, 2011).
There are a number of automated tools that VIC Government can make use of along with the
implementation of Big Data tools for security. These Big Data tools will analyze the specific
patterns and trends followed by the attackers to give rise to the security risks and threats and will
therefore lead to the development of the methods and policies to put a check on the same (Early,
2015).
9
the risks. There shall be advanced tools and security personnel that shall be made available on
every entry and exit gate of these agencies and organizations. Advanced identity management
and access control along with advanced monitoring of the security shall be carried out by the
physical entities present in all the location (Godlove, 2012).
It is necessary to have a combined approach to be followed in order to ensure that the overall
security of the VIC Government and the components that are associated with it are protected and
secured. It is also required to carry out continuous improvement and research work in the area of
security by the VIC Government to form a better state of security.
Recommendations & Conclusion
VIC Government is composed of a number of different units. The public sector components that
are present in Victoria play a significant role in the execution of a number of activities and
operations. There are a huge number of information and data sets that are associated with each of
the entity in the public sector. It is necessary to make sure that the security risks and attacks that
are probable in case of the VIC Government are controlled and prevented. The risks and attacks
in terms of the deliberate and accidental threats may take place which may violate the
availability, confidentiality and integrity of the information. It is required to have an integrated
approach towards security with the implementation of advanced administrative, technical and
physical security control (Leszczyna, 2011).
There are a number of automated tools that VIC Government can make use of along with the
implementation of Big Data tools for security. These Big Data tools will analyze the specific
patterns and trends followed by the attackers to give rise to the security risks and threats and will
therefore lead to the development of the methods and policies to put a check on the same (Early,
2015).
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

VIC Government
References
Cpdp. (2016). Victorian Protective Data Security Framework. Retrieved 25 August 2017, from
https://www.cpdp.vic.gov.au/images/content/pdf/data_security/20160628%20VPDSF
%20Framework%20June%202016%20v1.0.pdf
Early, G. (2015). Preemptive Security Through Information Analytics. Information Security
Journal: A Global Perspective, 24(1-3), 48-56.
http://dx.doi.org/10.1080/19393555.2015.1042600
Godlove, T. (2012). Examination of the Factors that Influence Teleworkers' Willingness to
Comply with Information Security Guidelines. Information Security Journal: A Global
Perspective, 21(4), 216-229. http://dx.doi.org/10.1080/19393555.2012.668747
Kadam, A. (2007). Information Security Policy Development and Implementation. Information
Systems Security, 16(5), 246-256. http://dx.doi.org/10.1080/10658980701744861
Kumar, M. (2013). An exploration of risk management in global industrial investment. Risk
Management, 15(4), 272-300. http://dx.doi.org/10.1057/rm.2013.8
Leszczyna, R. (2011). Approach to security assessment of critical infrastructures’
information systems. IET Information Security, 5(3), 135. http://dx.doi.org/10.1049/iet-
ifs.2010.0261
Moreau, F. (2001). Managing technological catastrophic risks. Risk Decision And Policy, 6(1),
17-32. http://dx.doi.org/10.1017/s1357530901000242
Rashvand, H. (2010). Editorial: Multi-agent & distributed information security. IET Information
Security, 4(4), 185. http://dx.doi.org/10.1049/iet-ifs.2010.9128
Sei. (2013). Unintentional Insider Threats: A Foundational Study. Retrieved 25 August 2017,
from https://www.sei.cmu.edu/reports/13tn022.pdf
Taylor, R. (2015). Potential Problems with Information Security Risk Assessments. Information
Security Journal: A Global Perspective, 24(4-6), 177-184.
http://dx.doi.org/10.1080/19393555.2015.1092620
10
References
Cpdp. (2016). Victorian Protective Data Security Framework. Retrieved 25 August 2017, from
https://www.cpdp.vic.gov.au/images/content/pdf/data_security/20160628%20VPDSF
%20Framework%20June%202016%20v1.0.pdf
Early, G. (2015). Preemptive Security Through Information Analytics. Information Security
Journal: A Global Perspective, 24(1-3), 48-56.
http://dx.doi.org/10.1080/19393555.2015.1042600
Godlove, T. (2012). Examination of the Factors that Influence Teleworkers' Willingness to
Comply with Information Security Guidelines. Information Security Journal: A Global
Perspective, 21(4), 216-229. http://dx.doi.org/10.1080/19393555.2012.668747
Kadam, A. (2007). Information Security Policy Development and Implementation. Information
Systems Security, 16(5), 246-256. http://dx.doi.org/10.1080/10658980701744861
Kumar, M. (2013). An exploration of risk management in global industrial investment. Risk
Management, 15(4), 272-300. http://dx.doi.org/10.1057/rm.2013.8
Leszczyna, R. (2011). Approach to security assessment of critical infrastructures’
information systems. IET Information Security, 5(3), 135. http://dx.doi.org/10.1049/iet-
ifs.2010.0261
Moreau, F. (2001). Managing technological catastrophic risks. Risk Decision And Policy, 6(1),
17-32. http://dx.doi.org/10.1017/s1357530901000242
Rashvand, H. (2010). Editorial: Multi-agent & distributed information security. IET Information
Security, 4(4), 185. http://dx.doi.org/10.1049/iet-ifs.2010.9128
Sei. (2013). Unintentional Insider Threats: A Foundational Study. Retrieved 25 August 2017,
from https://www.sei.cmu.edu/reports/13tn022.pdf
Taylor, R. (2015). Potential Problems with Information Security Risk Assessments. Information
Security Journal: A Global Perspective, 24(4-6), 177-184.
http://dx.doi.org/10.1080/19393555.2015.1092620
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

VIC Government
11
11
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





