IT Risk Management Report: Risks and Solutions in Victoria Government
VerifiedAdded on 2020/03/04
|21
|4206
|86
Report
AI Summary
This report provides a comprehensive analysis of IT risk management within the Victoria Government in Australia. It begins with an executive summary and table of contents, then introduces the core concepts of risk management, including the importance of data and information protection, the application of the Victorian Protective Data Security Framework (VPDSF) and the Privacy and Data Protection Act 2014 (PDPA). The report details various risks such as cyber-attacks, data breaches, and natural disasters, ranking them based on severity, and explores the RACI table for defining roles and responsibilities. It examines deliberate and accidental threats, environmental threats like natural disasters, and denial-of-service attacks. Furthermore, it delves into the Assurance Model, its challenges, and the distinction between risk and uncertainty. The report also discusses approaches for risk control by the Victorian government, providing a thorough overview of IT risk management in the context of governmental agencies and the strategies for risk mitigation.

Running head: IT RISK MANAGEMENT
IT Risk Management
Name of the Student
Name of the University
Author’s Note
IT Risk Management
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT RISK MANAGEMENT
Executive Summary
This report deals with the risks involved in the Victoria Government in Australia. These risks are
prevailing in the government and causing serious problems in the state. The different risks are
listed in the report with its ranking and justification. There are various models and theories
provided to analyses the risks management in the government. The use of the various approaches
and acts has been described in the report. The solutions to the risks in the Victoria government
has been provided in the report.
IT RISK MANAGEMENT
Executive Summary
This report deals with the risks involved in the Victoria Government in Australia. These risks are
prevailing in the government and causing serious problems in the state. The different risks are
listed in the report with its ranking and justification. There are various models and theories
provided to analyses the risks management in the government. The use of the various approaches
and acts has been described in the report. The solutions to the risks in the Victoria government
has been provided in the report.

2
IT RISK MANAGEMENT
Table of Contents
Introduction......................................................................................................................................3
Risk Management............................................................................................................................3
The RACI Table..............................................................................................................................5
Deliberate and accidental threat.......................................................................................................8
Environmental threats......................................................................................................................8
Denial of Service.............................................................................................................................9
Theories and Models......................................................................................................................10
The Assurance Model....................................................................................................................10
Challenges......................................................................................................................................11
Risk vs Uncertainty........................................................................................................................12
Approaches for Risk Control by VIC government........................................................................13
References......................................................................................................................................17
IT RISK MANAGEMENT
Table of Contents
Introduction......................................................................................................................................3
Risk Management............................................................................................................................3
The RACI Table..............................................................................................................................5
Deliberate and accidental threat.......................................................................................................8
Environmental threats......................................................................................................................8
Denial of Service.............................................................................................................................9
Theories and Models......................................................................................................................10
The Assurance Model....................................................................................................................10
Challenges......................................................................................................................................11
Risk vs Uncertainty........................................................................................................................12
Approaches for Risk Control by VIC government........................................................................13
References......................................................................................................................................17
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
IT RISK MANAGEMENT
Introduction
The protection of data and information in any organization including Victoria
government in Australia is prioritized in the market. The Victoria government is concerned with
its security and privacy issues of the data and information. The standards and policies of the
government are maintained for the security of the rights and financial status of the company.
This report deals with the risks involved in the huge volumes of data and information of
the Victorian government agencies in the locality. A proper risk assessment of the risks involved
are mentioned in the report.
This report outlines an effective solution to the risks and strategies for risk management
in the Victoria government.
Risk Management
Decision-making is done by analyzing the risks involved in the organization. In this case,
various types of risks are identified in the Victoria government that helps in initializing the risk
assessment procedure in the government (McNeil, Frey & Embrechts, 2015). Decisions are made
with the help of outcomes of the risk assessment procedure that helps in making risk free
decisions in the government. There are two types of risk-based decisions including Informal and
formal decision. The informal decisions are made with the help of discussion and conversations
of the daily routine. On the other hand, formal decision is based on a defined approach and
process. Risk management is done to improve performance of the government by achieving
goals and objectives (Glendon, Clarke & McKenna, 2016).
IT RISK MANAGEMENT
Introduction
The protection of data and information in any organization including Victoria
government in Australia is prioritized in the market. The Victoria government is concerned with
its security and privacy issues of the data and information. The standards and policies of the
government are maintained for the security of the rights and financial status of the company.
This report deals with the risks involved in the huge volumes of data and information of
the Victorian government agencies in the locality. A proper risk assessment of the risks involved
are mentioned in the report.
This report outlines an effective solution to the risks and strategies for risk management
in the Victoria government.
Risk Management
Decision-making is done by analyzing the risks involved in the organization. In this case,
various types of risks are identified in the Victoria government that helps in initializing the risk
assessment procedure in the government (McNeil, Frey & Embrechts, 2015). Decisions are made
with the help of outcomes of the risk assessment procedure that helps in making risk free
decisions in the government. There are two types of risk-based decisions including Informal and
formal decision. The informal decisions are made with the help of discussion and conversations
of the daily routine. On the other hand, formal decision is based on a defined approach and
process. Risk management is done to improve performance of the government by achieving
goals and objectives (Glendon, Clarke & McKenna, 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
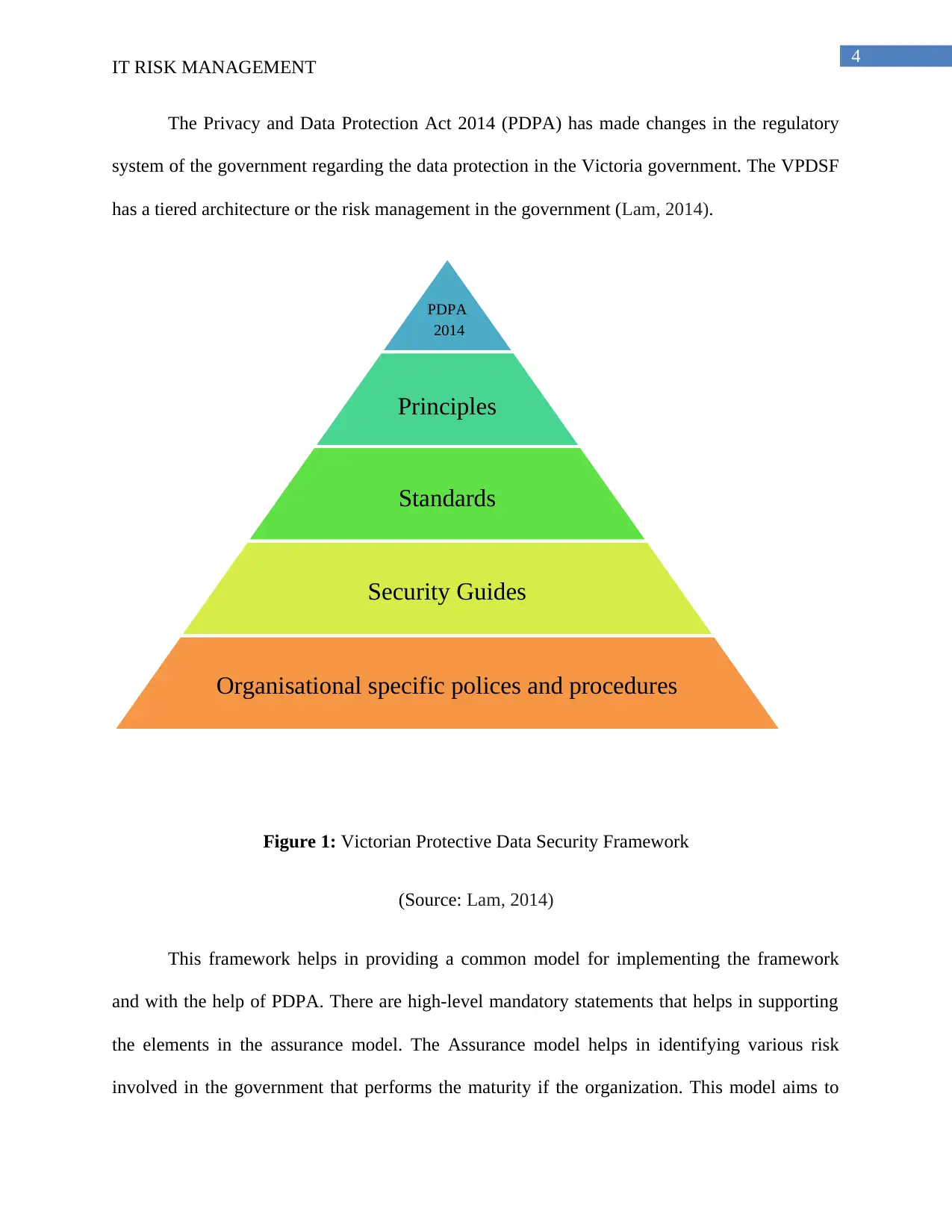
4
IT RISK MANAGEMENT
The Privacy and Data Protection Act 2014 (PDPA) has made changes in the regulatory
system of the government regarding the data protection in the Victoria government. The VPDSF
has a tiered architecture or the risk management in the government (Lam, 2014).
Figure 1: Victorian Protective Data Security Framework
(Source: Lam, 2014)
This framework helps in providing a common model for implementing the framework
and with the help of PDPA. There are high-level mandatory statements that helps in supporting
the elements in the assurance model. The Assurance model helps in identifying various risk
involved in the government that performs the maturity if the organization. This model aims to
PDPA
2014
Principles
Standards
Security Guides
Organisational specific polices and procedures
IT RISK MANAGEMENT
The Privacy and Data Protection Act 2014 (PDPA) has made changes in the regulatory
system of the government regarding the data protection in the Victoria government. The VPDSF
has a tiered architecture or the risk management in the government (Lam, 2014).
Figure 1: Victorian Protective Data Security Framework
(Source: Lam, 2014)
This framework helps in providing a common model for implementing the framework
and with the help of PDPA. There are high-level mandatory statements that helps in supporting
the elements in the assurance model. The Assurance model helps in identifying various risk
involved in the government that performs the maturity if the organization. This model aims to
PDPA
2014
Principles
Standards
Security Guides
Organisational specific polices and procedures
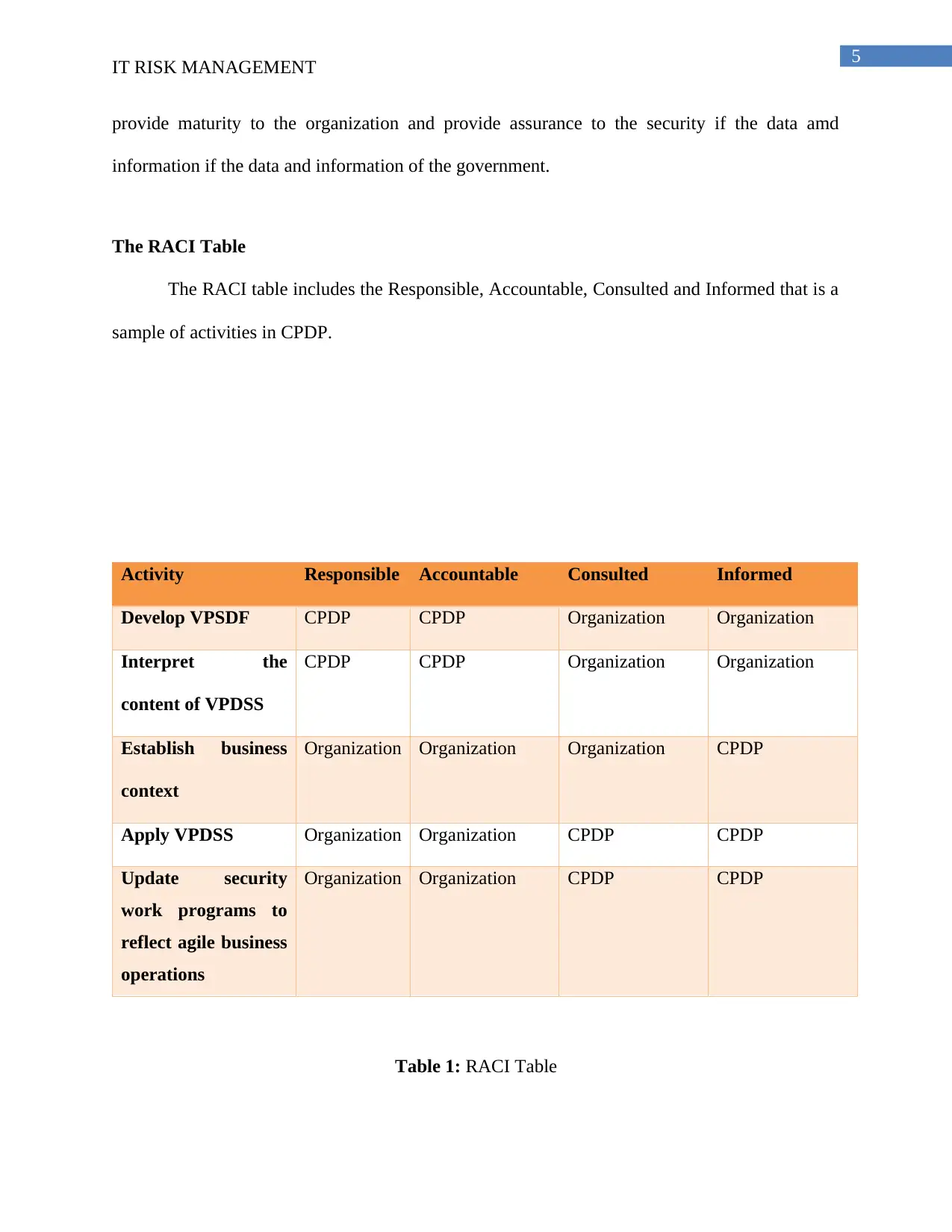
5
IT RISK MANAGEMENT
provide maturity to the organization and provide assurance to the security if the data amd
information if the data and information of the government.
The RACI Table
The RACI table includes the Responsible, Accountable, Consulted and Informed that is a
sample of activities in CPDP.
Activity Responsible Accountable Consulted Informed
Develop VPSDF CPDP CPDP Organization Organization
Interpret the
content of VPDSS
CPDP CPDP Organization Organization
Establish business
context
Organization Organization Organization CPDP
Apply VPDSS Organization Organization CPDP CPDP
Update security
work programs to
reflect agile business
operations
Organization Organization CPDP CPDP
Table 1: RACI Table
IT RISK MANAGEMENT
provide maturity to the organization and provide assurance to the security if the data amd
information if the data and information of the government.
The RACI Table
The RACI table includes the Responsible, Accountable, Consulted and Informed that is a
sample of activities in CPDP.
Activity Responsible Accountable Consulted Informed
Develop VPSDF CPDP CPDP Organization Organization
Interpret the
content of VPDSS
CPDP CPDP Organization Organization
Establish business
context
Organization Organization Organization CPDP
Apply VPDSS Organization Organization CPDP CPDP
Update security
work programs to
reflect agile business
operations
Organization Organization CPDP CPDP
Table 1: RACI Table
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
IT RISK MANAGEMENT
(Source: DeAngelo & Stulz, 2015)
The risk management in the Victoria government is depended on various factors that
includes the governmental agencies in the locality, organization, design and implementation of
the strategies in the government (DeAngelo & Stulz, 2015). Therefore, the risks that are
involving in the Victoria Government regarding the IT securities are the security of the data and
information, risks of losing the data, Cyber-attacks and hardware crash. These risks are found in
various governmental agencies under Victoria government.
These risks are prevailing in the Victoria Government for several years. These risks have
been categorized in the high, medium and low-level risks. Cyber-attack has been identified to be
high-level risks in the government. The cyber-attack has been increased in the Victoria that has
caused a huge risk of losing data and information of the government agencies and other
important documents (Pritchard & PMP, 2014). This can be informed to the governmental
agencies regarding the data and breach. The database of the government has been at high risk
from cyber-attack. These has alarmed the cyber security in the government. Cyber security has
become an essential part of the organization that has led to secure the data and information of
Victoria government. Therefore, there is a huge maintenance in the cyber world of the state. This
can helped in maintaining the cyber security of the data and information in the government.
Various ethical considerations are involved during the maintenance of the security protocols in
the organization. This helps in maintaining proper strategies to maintain risks in the government.
The governance committee helps in analyzing the level of risks involved in the state. These
threats can be ranked in ascending order as follows: Managerial problems, financial problems,
Cyber Security, Breach of data and information, Earthquakes, Fire and Flood (Glendon, Clarke
& McKenna, 2016).
IT RISK MANAGEMENT
(Source: DeAngelo & Stulz, 2015)
The risk management in the Victoria government is depended on various factors that
includes the governmental agencies in the locality, organization, design and implementation of
the strategies in the government (DeAngelo & Stulz, 2015). Therefore, the risks that are
involving in the Victoria Government regarding the IT securities are the security of the data and
information, risks of losing the data, Cyber-attacks and hardware crash. These risks are found in
various governmental agencies under Victoria government.
These risks are prevailing in the Victoria Government for several years. These risks have
been categorized in the high, medium and low-level risks. Cyber-attack has been identified to be
high-level risks in the government. The cyber-attack has been increased in the Victoria that has
caused a huge risk of losing data and information of the government agencies and other
important documents (Pritchard & PMP, 2014). This can be informed to the governmental
agencies regarding the data and breach. The database of the government has been at high risk
from cyber-attack. These has alarmed the cyber security in the government. Cyber security has
become an essential part of the organization that has led to secure the data and information of
Victoria government. Therefore, there is a huge maintenance in the cyber world of the state. This
can helped in maintaining the cyber security of the data and information in the government.
Various ethical considerations are involved during the maintenance of the security protocols in
the organization. This helps in maintaining proper strategies to maintain risks in the government.
The governance committee helps in analyzing the level of risks involved in the state. These
threats can be ranked in ascending order as follows: Managerial problems, financial problems,
Cyber Security, Breach of data and information, Earthquakes, Fire and Flood (Glendon, Clarke
& McKenna, 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
IT RISK MANAGEMENT
Figure 2: Risks involved in Victoria Government
(Source: Learner)
The systematic approach to the rank of the risks involved in the Victoria Government has
been done to mitigate the risks. The managerial and financial problems have the low-level risks,
as these can be resolved with proper communication among the employees and staffs in the
organizations and governmental agencies. Cyber security and Data breach is considered to be in
medium-level risks as these risks might cause a huge loss to the organizations (Almeida, Hankins
& Williams, 2016). The natural disasters including earthquakes, fire and flood are categorized in
high-level risks, as these risks are not under control. There might be risk management can be
done for these risks involved in the Victoria government. Therefore, the ranking if the risks
involved are justified.
Risks
High-level
Natural Disasters
Medium-level
Cyber security,
Data Breach
Low-level
Managerial and
Financial
problems
IT RISK MANAGEMENT
Figure 2: Risks involved in Victoria Government
(Source: Learner)
The systematic approach to the rank of the risks involved in the Victoria Government has
been done to mitigate the risks. The managerial and financial problems have the low-level risks,
as these can be resolved with proper communication among the employees and staffs in the
organizations and governmental agencies. Cyber security and Data breach is considered to be in
medium-level risks as these risks might cause a huge loss to the organizations (Almeida, Hankins
& Williams, 2016). The natural disasters including earthquakes, fire and flood are categorized in
high-level risks, as these risks are not under control. There might be risk management can be
done for these risks involved in the Victoria government. Therefore, the ranking if the risks
involved are justified.
Risks
High-level
Natural Disasters
Medium-level
Cyber security,
Data Breach
Low-level
Managerial and
Financial
problems

8
IT RISK MANAGEMENT
Deliberate and accidental threat
Deliberate threats are consisting of the environmental threats and accidental threats.
These threats are vulnerable to the governmental strategies to maintain the risk management in
the society. The data and information regarding these threats are not adequately related to the
risk involved in the threats. This can be mentioned as the accidental risks in the Victoria
government (Hopkin, 2017). The probability of the attacks are not measured properly due to its
consequences values and strategies to cope up with it. Deliberate threats are complicated with the
uncertainty of its nature that creates difficulties in risk analysis.
Figure 3: Three level risk analysis approach
(Source: Sadgrove, 2016)
Environmental threats
These threats include the natural disaster and calamities including earthquake, Flood and
Fire. These threats causes loss in data and information that lead to incorrect decisions, financial
loss, resource loss and additional costs are being incurred. According to Emergency Management
IT RISK MANAGEMENT
Deliberate and accidental threat
Deliberate threats are consisting of the environmental threats and accidental threats.
These threats are vulnerable to the governmental strategies to maintain the risk management in
the society. The data and information regarding these threats are not adequately related to the
risk involved in the threats. This can be mentioned as the accidental risks in the Victoria
government (Hopkin, 2017). The probability of the attacks are not measured properly due to its
consequences values and strategies to cope up with it. Deliberate threats are complicated with the
uncertainty of its nature that creates difficulties in risk analysis.
Figure 3: Three level risk analysis approach
(Source: Sadgrove, 2016)
Environmental threats
These threats include the natural disaster and calamities including earthquake, Flood and
Fire. These threats causes loss in data and information that lead to incorrect decisions, financial
loss, resource loss and additional costs are being incurred. According to Emergency Management
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
IT RISK MANAGEMENT
Australia, natural calamities causes massive destruction in the data and information and facilities
(Sadgrove, 2016).
Many cases of fire in the area that causes huge loss to lives in the building. This act
deliberatively to the governmental agencies in the Victoria. The data and information of the
government agencies are lost due to these risks. Therefore, natural disasters are categorized in
the high level of risks.
Denial of Service
Denial of Service attack completely denies service for legitimating users, resources and
systems (Cole, Giné & Vickery, 2017). These attacks are generally the cyber-attacks that targets
the online websites including government websites and social media websites. These attacks
causes huge loss to the companies in the market. Denial of service have caused various impacts
in the e-commerce industry over the internet in Victoria government. Denial of service attacks
are carried out by various programming codes and phishing of websites. The starvation attack
consumes the system resources including bandwidth, CPU and RAM. These attacks are caused
due to lack of firewall in the network server of the organization (Paschen, & Beilin, 2017). The
latest version of the operating system helps in maintaining security measures in the computer.
Computer viruses, malwares and worms are responsible for the illegal attacks in the network
server in the Victoria government. This causes hardware crash and data breaching form the
database of the government agencies.
IT RISK MANAGEMENT
Australia, natural calamities causes massive destruction in the data and information and facilities
(Sadgrove, 2016).
Many cases of fire in the area that causes huge loss to lives in the building. This act
deliberatively to the governmental agencies in the Victoria. The data and information of the
government agencies are lost due to these risks. Therefore, natural disasters are categorized in
the high level of risks.
Denial of Service
Denial of Service attack completely denies service for legitimating users, resources and
systems (Cole, Giné & Vickery, 2017). These attacks are generally the cyber-attacks that targets
the online websites including government websites and social media websites. These attacks
causes huge loss to the companies in the market. Denial of service have caused various impacts
in the e-commerce industry over the internet in Victoria government. Denial of service attacks
are carried out by various programming codes and phishing of websites. The starvation attack
consumes the system resources including bandwidth, CPU and RAM. These attacks are caused
due to lack of firewall in the network server of the organization (Paschen, & Beilin, 2017). The
latest version of the operating system helps in maintaining security measures in the computer.
Computer viruses, malwares and worms are responsible for the illegal attacks in the network
server in the Victoria government. This causes hardware crash and data breaching form the
database of the government agencies.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IT RISK MANAGEMENT
Theories and Models
There are different models that are helping in risk management in the Victoria
government.
The Assurance Model
The Assurance model resembles the activities that is performed by the CPDP for
monitoring and measuring the security level of the data and information in the governmental
agencies. The assurance model help in eradicating the risks by implementing the organizational
strategies. This foster partnership with the CPDP and take several decisions to eradicate the risks
in the Victoria government (De Bortoli et al., 2017). These strategies help in maintaining the
protection of the data and information in the company and the governmental agencies.
This model helps in providing a measuring level of protection to the organization’s data
and information accompanied by PDPA. It also enhances the protection of the data and
information in the organization by accomplishing the strategies regarding the security practices.
It helps in establishing roles and responsibilities with all the parties in the governmental agencies
that helping maintaining the protection of the data and information in the market (Redley &
Raggatt, 2017). It also identifies the security tools for monitoring the efficiency and effectiveness
of the strategies inbuilt by the governmental agencies. The assurance model focuses in the need
of continuous improvement in the strategies to protect the data and I formation regarding the
organization in the market.
IT RISK MANAGEMENT
Theories and Models
There are different models that are helping in risk management in the Victoria
government.
The Assurance Model
The Assurance model resembles the activities that is performed by the CPDP for
monitoring and measuring the security level of the data and information in the governmental
agencies. The assurance model help in eradicating the risks by implementing the organizational
strategies. This foster partnership with the CPDP and take several decisions to eradicate the risks
in the Victoria government (De Bortoli et al., 2017). These strategies help in maintaining the
protection of the data and information in the company and the governmental agencies.
This model helps in providing a measuring level of protection to the organization’s data
and information accompanied by PDPA. It also enhances the protection of the data and
information in the organization by accomplishing the strategies regarding the security practices.
It helps in establishing roles and responsibilities with all the parties in the governmental agencies
that helping maintaining the protection of the data and information in the market (Redley &
Raggatt, 2017). It also identifies the security tools for monitoring the efficiency and effectiveness
of the strategies inbuilt by the governmental agencies. The assurance model focuses in the need
of continuous improvement in the strategies to protect the data and I formation regarding the
organization in the market.

11
IT RISK MANAGEMENT
Challenges
There are various challenges faced by the government of the Victoria during the
implementation of the models theories in the organizational strategies. The employee and other
staffs of the governmental agencies and organizations are not able to understand these new
principles and strategies propounded by assurance model in the market (Lane et al., 2017).
Therefore, there is a lack of awareness and information among the employee and other staffs in
the organization. Therefore, there are different training and motivations provided to the
employees of the organizations that helps in maintaining the awareness of the assurance model
among them. Lack of experience among the employees and other staffs that declines the
importance of the model in the organization. Therefore, there is need of seminars and programs
that helps in providing training to this employee for the implementation of these strategies in the
organization. Therefore, importance of the training and motivation is experienced in the
organization for the implementation of the assurance mode in organization.
There are various political challenges during implementing these models for risk
management. The rules and regulation in the local area have to be maintained buy the model
before implementing it in the organization (O'Donahoo & Simmonds, 2016). These laws helps in
controlling the duplicity in the model in the Victoria government. Therefore, government have to
execute some political pressure and rules for maintaining the proper use of the model in the
organization for managing risks involved in the organization. There are various principles in the
assurance model that help in providing a bright look to the implementation of the strategies. The
outsourcing technique helps in following different strategies and market it outside the Victoria
government to apply it (Loke et al., 2016). This outsourcing strategy helps in maintaining the
significance of the models and theories in the government.
IT RISK MANAGEMENT
Challenges
There are various challenges faced by the government of the Victoria during the
implementation of the models theories in the organizational strategies. The employee and other
staffs of the governmental agencies and organizations are not able to understand these new
principles and strategies propounded by assurance model in the market (Lane et al., 2017).
Therefore, there is a lack of awareness and information among the employee and other staffs in
the organization. Therefore, there are different training and motivations provided to the
employees of the organizations that helps in maintaining the awareness of the assurance model
among them. Lack of experience among the employees and other staffs that declines the
importance of the model in the organization. Therefore, there is need of seminars and programs
that helps in providing training to this employee for the implementation of these strategies in the
organization. Therefore, importance of the training and motivation is experienced in the
organization for the implementation of the assurance mode in organization.
There are various political challenges during implementing these models for risk
management. The rules and regulation in the local area have to be maintained buy the model
before implementing it in the organization (O'Donahoo & Simmonds, 2016). These laws helps in
controlling the duplicity in the model in the Victoria government. Therefore, government have to
execute some political pressure and rules for maintaining the proper use of the model in the
organization for managing risks involved in the organization. There are various principles in the
assurance model that help in providing a bright look to the implementation of the strategies. The
outsourcing technique helps in following different strategies and market it outside the Victoria
government to apply it (Loke et al., 2016). This outsourcing strategy helps in maintaining the
significance of the models and theories in the government.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





