Victoria University: NIT6001 Security in Mobile Cloud Computing Report
VerifiedAdded on 2022/08/12
|41
|11151
|17
Report
AI Summary
This report investigates the critical security challenges in Mobile Cloud Computing (MCC). It begins with an introduction to MCC, its architecture, and significance, followed by an exploration of research background and stakeholder analysis. The literature review covers MCC, security issues such as malware and vulnerabilities, and related works. The report identifies key security problems and proposes solutions. The methodology section details the research philosophy, design, and data collection methods. The study also includes a discussion of future research directions and concludes with a summary of findings. The report emphasizes the importance of security for service providers, consumers, and platform providers, highlighting the need for robust security mechanisms to protect data and ensure platform reliability. The report also contains tables and figures to support its findings.

Running head: SECURITY IN MCC
SECURITY IN MOBILE CLOUD COMPUTING
Name of the Student:
Name of the University:
Author Note:
SECURITY IN MOBILE CLOUD COMPUTING
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SECURITY IN MCC
Table of Contents
1. Introduction..............................................................................................................................2
1.1 Research background........................................................................................................5
1.2 Significance...........................................................................................................................6
1.3 Research Problem:.................................................................................................................9
1.4 Research Question:................................................................................................................9
2. Literature Review......................................................................................................................10
2.1 Mobile Cloud Computing....................................................................................................10
2.2 Security in Mobile Cloud Computing..................................................................................12
Security of Mobile Network User..............................................................................................13
Securing Information on the Cloud...........................................................................................17
2.3 Related works in security of mobile cloud computing........................................................18
Application Security..................................................................................................................18
Security of Data.........................................................................................................................19
2.4 Security Issues in Mobile Cloud Computing.......................................................................19
2.5 Solution................................................................................................................................22
2.6 The Future of Cloud.............................................................................................................24
2.7 Effectiveness in Business Organizations.............................................................................25
3. Methodology..............................................................................................................................27
3.1 Introduction to Methodology:..............................................................................................27
3.2 Research Philosophy:...........................................................................................................27
3.3 Research Design:.................................................................................................................28
3.4 Method for collecting the data for the research:..................................................................28
3.5 Research Ethics:...................................................................................................................30
3.6 Research Limitations:..............................................................................................................30
4. Future Research......................................................................................................................31
5. Conclusion..............................................................................................................................32
References......................................................................................................................................34
Table of Contents
1. Introduction..............................................................................................................................2
1.1 Research background........................................................................................................5
1.2 Significance...........................................................................................................................6
1.3 Research Problem:.................................................................................................................9
1.4 Research Question:................................................................................................................9
2. Literature Review......................................................................................................................10
2.1 Mobile Cloud Computing....................................................................................................10
2.2 Security in Mobile Cloud Computing..................................................................................12
Security of Mobile Network User..............................................................................................13
Securing Information on the Cloud...........................................................................................17
2.3 Related works in security of mobile cloud computing........................................................18
Application Security..................................................................................................................18
Security of Data.........................................................................................................................19
2.4 Security Issues in Mobile Cloud Computing.......................................................................19
2.5 Solution................................................................................................................................22
2.6 The Future of Cloud.............................................................................................................24
2.7 Effectiveness in Business Organizations.............................................................................25
3. Methodology..............................................................................................................................27
3.1 Introduction to Methodology:..............................................................................................27
3.2 Research Philosophy:...........................................................................................................27
3.3 Research Design:.................................................................................................................28
3.4 Method for collecting the data for the research:..................................................................28
3.5 Research Ethics:...................................................................................................................30
3.6 Research Limitations:..............................................................................................................30
4. Future Research......................................................................................................................31
5. Conclusion..............................................................................................................................32
References......................................................................................................................................34

2SECURITY IN MCC
1. Introduction
MCC (Mobile Cloud Computing) is a technology with the help of which data processing as
well as storage is performed. It provides more than one IT resources and services to the mobile
network for on-demand self-service (Kumar 2020). Mobile service providers give different types
of services and facilities to the consumers. It can be performed by taking entire benefit of the
cloud computing. Resources in the MCC are situated in many virtual distributed computer
systems. There are many companies who offer various cloud based products like android.
Google maps and Geographic search are new cloud based products in Google.
Security is a crucial problem in this particular context. There are three levels of security in
the system of MCC:
Mobile terminal
This is a kind of open operating system. It provides wireless access to the internet.
It also provides support to the third party software and personalisation (Ibtihal and
Hassan 2020). For that reason, this can be said that, security issues of MCC are a big
deal. Following are some security issues in the mobile cloud computing.
Malware
This helps intruders to get necessary access of a particular user (Labati et
al. 2020). They are able to down load all the details of the users automatically. A
huge number of anti-malware software is developed. But they do not have many
resources. There is a huge capacity of the mobile terminals that are significant to
the various computing resources.
1. Introduction
MCC (Mobile Cloud Computing) is a technology with the help of which data processing as
well as storage is performed. It provides more than one IT resources and services to the mobile
network for on-demand self-service (Kumar 2020). Mobile service providers give different types
of services and facilities to the consumers. It can be performed by taking entire benefit of the
cloud computing. Resources in the MCC are situated in many virtual distributed computer
systems. There are many companies who offer various cloud based products like android.
Google maps and Geographic search are new cloud based products in Google.
Security is a crucial problem in this particular context. There are three levels of security in
the system of MCC:
Mobile terminal
This is a kind of open operating system. It provides wireless access to the internet.
It also provides support to the third party software and personalisation (Ibtihal and
Hassan 2020). For that reason, this can be said that, security issues of MCC are a big
deal. Following are some security issues in the mobile cloud computing.
Malware
This helps intruders to get necessary access of a particular user (Labati et
al. 2020). They are able to down load all the details of the users automatically. A
huge number of anti-malware software is developed. But they do not have many
resources. There is a huge capacity of the mobile terminals that are significant to
the various computing resources.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SECURITY IN MCC
Software vulnerabilities
For application software, the log in creadentials are moved to the
network with the help of File Transfer Protocol (Stergiou et al. 2020). These
are preserved as a clear text. These provide an unauthorized access of the cell
phones from computers within similar network. For that reason, personal
information is not at all secured.
Mobile Network Security
Mobile gadgets has the ability for accessing the network by adopting various
phone services, sending of Short message services and other services related to the
internet (Wamsi, Pandey and Kakade 2020). Smart phones can access the Wi-Fi and
Bluetooth Network. For that reason, these accesses are responsible for security threats as
well as malicious attack.
Mobile Cloud
Security in MCC is highlighted with respect two problems- privacy protection of
data and platform reliability. These are as follows:
Platform Reliability
Cloud services give a huge amount of storage for the resources of
important resources (Xia, Jiu and Fan 2020). For that reason, there is always a
threat of being attacked. There are various types of attacks such as malwareor
any other malicious program, cloud users or insiders. Main intention of
intruders is for destroying the cloud services. The Denial of Service terminates
cloud services by dissolving the availability of the platform.
Software vulnerabilities
For application software, the log in creadentials are moved to the
network with the help of File Transfer Protocol (Stergiou et al. 2020). These
are preserved as a clear text. These provide an unauthorized access of the cell
phones from computers within similar network. For that reason, personal
information is not at all secured.
Mobile Network Security
Mobile gadgets has the ability for accessing the network by adopting various
phone services, sending of Short message services and other services related to the
internet (Wamsi, Pandey and Kakade 2020). Smart phones can access the Wi-Fi and
Bluetooth Network. For that reason, these accesses are responsible for security threats as
well as malicious attack.
Mobile Cloud
Security in MCC is highlighted with respect two problems- privacy protection of
data and platform reliability. These are as follows:
Platform Reliability
Cloud services give a huge amount of storage for the resources of
important resources (Xia, Jiu and Fan 2020). For that reason, there is always a
threat of being attacked. There are various types of attacks such as malwareor
any other malicious program, cloud users or insiders. Main intention of
intruders is for destroying the cloud services. The Denial of Service terminates
cloud services by dissolving the availability of the platform.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
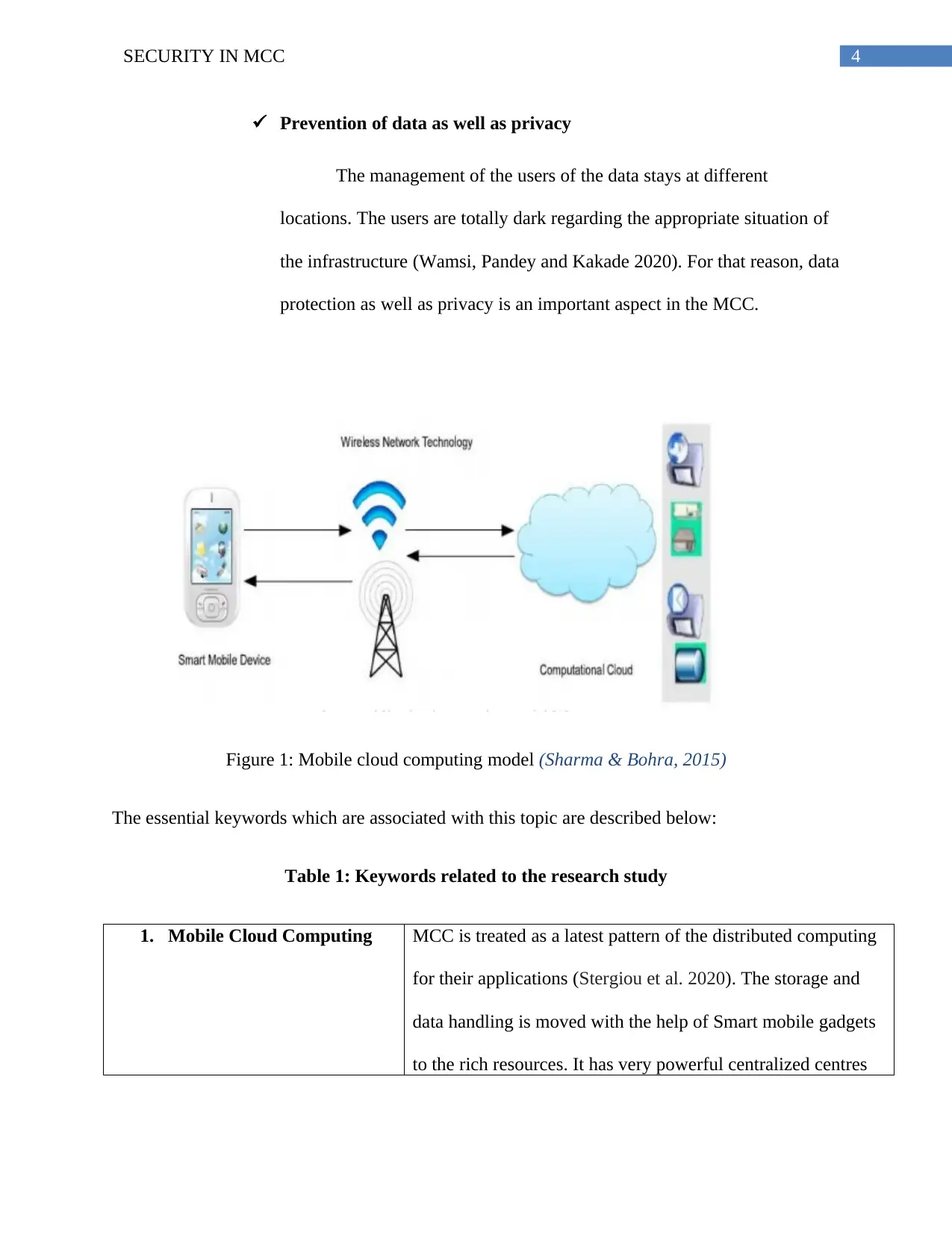
4SECURITY IN MCC
Prevention of data as well as privacy
The management of the users of the data stays at different
locations. The users are totally dark regarding the appropriate situation of
the infrastructure (Wamsi, Pandey and Kakade 2020). For that reason, data
protection as well as privacy is an important aspect in the MCC.
Figure 1: Mobile cloud computing model (Sharma & Bohra, 2015)
The essential keywords which are associated with this topic are described below:
Table 1: Keywords related to the research study
1. Mobile Cloud Computing MCC is treated as a latest pattern of the distributed computing
for their applications (Stergiou et al. 2020). The storage and
data handling is moved with the help of Smart mobile gadgets
to the rich resources. It has very powerful centralized centres
Prevention of data as well as privacy
The management of the users of the data stays at different
locations. The users are totally dark regarding the appropriate situation of
the infrastructure (Wamsi, Pandey and Kakade 2020). For that reason, data
protection as well as privacy is an important aspect in the MCC.
Figure 1: Mobile cloud computing model (Sharma & Bohra, 2015)
The essential keywords which are associated with this topic are described below:
Table 1: Keywords related to the research study
1. Mobile Cloud Computing MCC is treated as a latest pattern of the distributed computing
for their applications (Stergiou et al. 2020). The storage and
data handling is moved with the help of Smart mobile gadgets
to the rich resources. It has very powerful centralized centres

5SECURITY IN MCC
for the computation of data within the computational cloud.
2. User Authentication It is a process of performing the authentication of the
uniqueness of the mobile user to make sure that he is an
authentic user for accessing the resources of the mobile cloud
(Stergiou and Psannis 2020).
3. Information security issues There are some very common problems of the information
security issues of mobile cloud computing (Pérez et val. 2020).
These are System security of server and database, security in
networks, protection of data, protection of storage as well as
systems.
Figure 2: Table of mobile cloud computing
1.1 Research background
In this particular case, various research background of the mobile cloud computing as well as
software architecture is discussed.
Mobile Cloud Computing was invented as a very popular technology and it is used as the
replacement of the old theories of the cloud computing (Neware et al. 2020). According to a
survey, there are approximately seven million mobile devices in the entire globe. It indicates that
the number of mobile devices are enhancing five times faster than the human population (Labati
et al. 2020). It is treated as the combination of the mobile gadgets, mobile applications as well as
remote server. It also offers some portable solutions in the area of the MCC. It can be treated as
the backbone of mobile computing. It highlights some gadgets (Mahmud et al. 2020). It helps the
for the computation of data within the computational cloud.
2. User Authentication It is a process of performing the authentication of the
uniqueness of the mobile user to make sure that he is an
authentic user for accessing the resources of the mobile cloud
(Stergiou and Psannis 2020).
3. Information security issues There are some very common problems of the information
security issues of mobile cloud computing (Pérez et val. 2020).
These are System security of server and database, security in
networks, protection of data, protection of storage as well as
systems.
Figure 2: Table of mobile cloud computing
1.1 Research background
In this particular case, various research background of the mobile cloud computing as well as
software architecture is discussed.
Mobile Cloud Computing was invented as a very popular technology and it is used as the
replacement of the old theories of the cloud computing (Neware et al. 2020). According to a
survey, there are approximately seven million mobile devices in the entire globe. It indicates that
the number of mobile devices are enhancing five times faster than the human population (Labati
et al. 2020). It is treated as the combination of the mobile gadgets, mobile applications as well as
remote server. It also offers some portable solutions in the area of the MCC. It can be treated as
the backbone of mobile computing. It highlights some gadgets (Mahmud et al. 2020). It helps the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6SECURITY IN MCC
users to perform various computation of the mobile cloud computing. It helps to share various
information regarding the research.
The software architecture highlights the blueprint or high level view of particular
software. It is proved to be a successful abstraction of several complexities of various
modules of the source code (Kumar 2020). It is used to highlight some components of the
architecture. There are some main computational elements for giving the abstraction of the
complicated details. It also gives some context-sensitivity (Li and Zhu 2020). The mobile
cloud software system is observed as a layered architecture model. It gives some storage
facilities and it can be treated as a part of the layer of cloud computing.
1.2 Significance
There are various stakeholders involved in this type of the research. These are as follows:
Service
Providers
Platform
providers
Consumers
users to perform various computation of the mobile cloud computing. It helps to share various
information regarding the research.
The software architecture highlights the blueprint or high level view of particular
software. It is proved to be a successful abstraction of several complexities of various
modules of the source code (Kumar 2020). It is used to highlight some components of the
architecture. There are some main computational elements for giving the abstraction of the
complicated details. It also gives some context-sensitivity (Li and Zhu 2020). The mobile
cloud software system is observed as a layered architecture model. It gives some storage
facilities and it can be treated as a part of the layer of cloud computing.
1.2 Significance
There are various stakeholders involved in this type of the research. These are as follows:
Service
Providers
Platform
providers
Consumers
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7SECURITY IN MCC
Figure 2: Stakeholder diagram
Service Providers
If strong security mechanism is applied to the mobile cloud computing services,
then service providers can easily provide the services to the consumers (Kocabas and
Soyata 2020). Service providers can provide some efficient service to their consumers.
Using the cloud services, the service providers can provide services to their potential
consumers from any location in the globe.
Consumers
If the consumers are getting secured mobile services from the service provider
then the consumers will feel secure regarding these services. As a result of that, the
number of consumers will be increased rapidly (Ibtihal and Hassan 2020). As there is no
chance of the data loss or stolen gadgets, details of the consumer will be secured. As a
result of that, it will increase the popularity of the consumers on the services. As there is
a strong security in the MCC services, then this will provide less vulnerability of the
gadgets, operating system and third party services. As a better methodology of malicious
code detection is applied in the mobile cloud computing services, so that it is possible for
service provider to provide secure services to the consumer. It automatically increases the
popularity of the services to the consumer (Bhattacharya et al. 2020). For that reason,
consumers can enjoy best services from the end of the service provider. As better security
mechanism is implemented, so that consumers can face lesser amount of risk while using
these services.
Platform providers
Figure 2: Stakeholder diagram
Service Providers
If strong security mechanism is applied to the mobile cloud computing services,
then service providers can easily provide the services to the consumers (Kocabas and
Soyata 2020). Service providers can provide some efficient service to their consumers.
Using the cloud services, the service providers can provide services to their potential
consumers from any location in the globe.
Consumers
If the consumers are getting secured mobile services from the service provider
then the consumers will feel secure regarding these services. As a result of that, the
number of consumers will be increased rapidly (Ibtihal and Hassan 2020). As there is no
chance of the data loss or stolen gadgets, details of the consumer will be secured. As a
result of that, it will increase the popularity of the consumers on the services. As there is
a strong security in the MCC services, then this will provide less vulnerability of the
gadgets, operating system and third party services. As a better methodology of malicious
code detection is applied in the mobile cloud computing services, so that it is possible for
service provider to provide secure services to the consumer. It automatically increases the
popularity of the services to the consumer (Bhattacharya et al. 2020). For that reason,
consumers can enjoy best services from the end of the service provider. As better security
mechanism is implemented, so that consumers can face lesser amount of risk while using
these services.
Platform providers

8SECURITY IN MCC
With the help of this research, platform providers can provide secure mobile
application framework to their consumers (Stergiou and Psannis 2020). Developers of the
platform providing company use many tools like software developer kit and some unified
Application Programmable Interface (Bakhshi and Rodriguez-Navas 2020). They can use
MBaaS. In this framework, better security is implemented. For that reason, it is first
choice of the developers. With the help of this, a huge amount of backend framework has
been reduced like geolocation, pushing of notification, transactions performed in mobile
devices, storage of data and performing the analysis (Li and Zhu 2020). With the help of
this research, the platform providers can use a high computing and storage based
framework (Abuarqoub 2020). With the help of this, the developer can preserve a large
amount of data of the consumers. Storage needs to be borrowed from the cloud resources.
Gadgets like high end navigators, store maps and routes can be used. It is required to
retrieve the real life information on the planning of the routes and updating various
traffics. It becomes the growing need in current scenario.
1.3 Research Problem:
The emergence of the latest technology has given rise to numerous other technologies
which includes mobile cloud computing as well. The cloud computing’s entire system is under
continuous threat of exposure to the hackers and other sort of attacks. Ensuring the security of
the Mobile Cloud Computing services is main reason for which the research is undertaken. The
study discusses about the security issues which arises due to the usage of the cloud computing on
mobile devices such that the techniques can be developed for mitigating them. Analysis and
research helps in finding efficient solution for the security issues that arises in the system.
With the help of this research, platform providers can provide secure mobile
application framework to their consumers (Stergiou and Psannis 2020). Developers of the
platform providing company use many tools like software developer kit and some unified
Application Programmable Interface (Bakhshi and Rodriguez-Navas 2020). They can use
MBaaS. In this framework, better security is implemented. For that reason, it is first
choice of the developers. With the help of this, a huge amount of backend framework has
been reduced like geolocation, pushing of notification, transactions performed in mobile
devices, storage of data and performing the analysis (Li and Zhu 2020). With the help of
this research, the platform providers can use a high computing and storage based
framework (Abuarqoub 2020). With the help of this, the developer can preserve a large
amount of data of the consumers. Storage needs to be borrowed from the cloud resources.
Gadgets like high end navigators, store maps and routes can be used. It is required to
retrieve the real life information on the planning of the routes and updating various
traffics. It becomes the growing need in current scenario.
1.3 Research Problem:
The emergence of the latest technology has given rise to numerous other technologies
which includes mobile cloud computing as well. The cloud computing’s entire system is under
continuous threat of exposure to the hackers and other sort of attacks. Ensuring the security of
the Mobile Cloud Computing services is main reason for which the research is undertaken. The
study discusses about the security issues which arises due to the usage of the cloud computing on
mobile devices such that the techniques can be developed for mitigating them. Analysis and
research helps in finding efficient solution for the security issues that arises in the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9SECURITY IN MCC
1.4 Research Question:
1. What are the basic components of the mobile security and how has cloud technology
helped in process of evolution of mobile cloud computing technology?
2. What are main functions of the mobile cloud computing security that can be incorporated
in the system?
3. What are the issues in the security that should initiate the mitigation process in the
organizations?
2. Literature Review
2.1 Mobile Cloud Computing
As per Kandavel and Kumaravel (2019), several factors are there which could contribute
to decision for introducing Mobile Cloud Computing (MCC). These consist of wireless
communication, cloud computing, services based on location, portable devices, mobile internet
and infrastructure. MCC made this possible for the users in having both unlimited storage and
computing power. MCC has become model for the transparent augmentation of capabilities that
are available within mobile devices by using wireless network accessing to computational
resources and cloud storage along with dynamic offloading which changes as per operating
conditions. Though, these mobile devices operate on batteries and have limited power for
processing, storage, low capacity storage, low energy, problematic connectivity and some few
features. These would always create problems for the applications which need high capabilities
of computation and require large capacity of storage to run within mobile environment. For
augmenting computing capability, mobile devices’ battery life and storage capacity, the large
1.4 Research Question:
1. What are the basic components of the mobile security and how has cloud technology
helped in process of evolution of mobile cloud computing technology?
2. What are main functions of the mobile cloud computing security that can be incorporated
in the system?
3. What are the issues in the security that should initiate the mitigation process in the
organizations?
2. Literature Review
2.1 Mobile Cloud Computing
As per Kandavel and Kumaravel (2019), several factors are there which could contribute
to decision for introducing Mobile Cloud Computing (MCC). These consist of wireless
communication, cloud computing, services based on location, portable devices, mobile internet
and infrastructure. MCC made this possible for the users in having both unlimited storage and
computing power. MCC has become model for the transparent augmentation of capabilities that
are available within mobile devices by using wireless network accessing to computational
resources and cloud storage along with dynamic offloading which changes as per operating
conditions. Though, these mobile devices operate on batteries and have limited power for
processing, storage, low capacity storage, low energy, problematic connectivity and some few
features. These would always create problems for the applications which need high capabilities
of computation and require large capacity of storage to run within mobile environment. For
augmenting computing capability, mobile devices’ battery life and storage capacity, the large
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10SECURITY IN MCC
capacity of storage and high computational demanding activities must be transferred into cloud.
Data security, however, is still concern as well as major obstacle within MCC from being
adopted widely. By using base stations, the mobile devices could connect with mobile networks.
Such base stations for mobile establish functional interfaces among both mobile as well s
networks devices. Mobile users’ ID as well as location is given to central processors where
connection is made with servers which provide services of mobile network. By this setup,
operators of mobile network could give services of authentication, accounting and authorization
to the mobile users depending on subscribers information and home agent stored within database.
Cloud is sent the requests of subscribers by internet where cloud controller processes the
requests. Hence, the users are provided with cloud services.
Zhang, Wu and Delsey (2018), in past years, as tremendous developments’ result within
mobile technologies and networks, MCC is emerging area for research. As per the surveys,
people would like to use the mobile devices like smartphones, laptops and tablets instead of
desktop computers. Computing by mobile devices is now a feasible concept when compared with
conventional approach. However, there are still few drawbacks like computational power,
shortage of storage as well as limited battery for mobile devices are the issues of technology of
MCC. For overcoming such issues, cloud could be used as useful solution. The cloud is
virtualization’s combination of high quantity of the resources with computing paradigm that is
incorporated with Platform as a Service (PaaS), Software as a Service (SaaS) and Infrastructure
as a Service (IaaS). Several could providers like Amazon EC2 and Microsoft Azure provide
elastic storage. Hence, Mobile computing’s integration with the cloud computing has provided
birth to better and newer technological approach known as Mobile Cloud Computing. Mobile
capacity of storage and high computational demanding activities must be transferred into cloud.
Data security, however, is still concern as well as major obstacle within MCC from being
adopted widely. By using base stations, the mobile devices could connect with mobile networks.
Such base stations for mobile establish functional interfaces among both mobile as well s
networks devices. Mobile users’ ID as well as location is given to central processors where
connection is made with servers which provide services of mobile network. By this setup,
operators of mobile network could give services of authentication, accounting and authorization
to the mobile users depending on subscribers information and home agent stored within database.
Cloud is sent the requests of subscribers by internet where cloud controller processes the
requests. Hence, the users are provided with cloud services.
Zhang, Wu and Delsey (2018), in past years, as tremendous developments’ result within
mobile technologies and networks, MCC is emerging area for research. As per the surveys,
people would like to use the mobile devices like smartphones, laptops and tablets instead of
desktop computers. Computing by mobile devices is now a feasible concept when compared with
conventional approach. However, there are still few drawbacks like computational power,
shortage of storage as well as limited battery for mobile devices are the issues of technology of
MCC. For overcoming such issues, cloud could be used as useful solution. The cloud is
virtualization’s combination of high quantity of the resources with computing paradigm that is
incorporated with Platform as a Service (PaaS), Software as a Service (SaaS) and Infrastructure
as a Service (IaaS). Several could providers like Amazon EC2 and Microsoft Azure provide
elastic storage. Hence, Mobile computing’s integration with the cloud computing has provided
birth to better and newer technological approach known as Mobile Cloud Computing. Mobile

11SECURITY IN MCC
devices within MCC are used as thin clients. The data would be offloaded in cloud from the
mobile devices for storage and computation.
According to Walia (2017), MCC could defined as rich technology for mobile computing
which controls the elastic resources for different network and cloud technologies for unlimited
mobility, storage and functionality in order for serving huge amount of the mobile equipment
anytime and anywhere through Internet or Ethernet. MCC is infrastructure where processing and
storing of data could be performed out of the mobile device, however within the cloud. Within
MCC, data storage as well as computing power are shifted away from smartphones, then
performed within cloud, thus bringing applications of mobile cloud as well as mobile computing
to smartphones as well as to mobile subscribers’ wide range. Hence, MCC is infrastructure
which combines domains of cloud computing and mobile computing where processing of the
data and storing of data take place outside mobile devices. This is not that the offloading would
be the remote cloud, however it could be mobile devices’ collective resources in local vicinity.
Motivation for MCC is removing mobile computing’s existing drawbacks. Several limitations
are there of mobile computing that are discussed as follows:
Limited capacity of storage for mobile devices. There is limited internal memory
for every mobile device. However, these could be expanded by using external
memory.
Limited life of battery for mobile devices. As for mobility of device, this is
impossible in finding external source of power. The mobile devices depend on
internal battery that has charge life for few hours only. In several applications are
continuously running or computation is continuous, battery would drain soon.
devices within MCC are used as thin clients. The data would be offloaded in cloud from the
mobile devices for storage and computation.
According to Walia (2017), MCC could defined as rich technology for mobile computing
which controls the elastic resources for different network and cloud technologies for unlimited
mobility, storage and functionality in order for serving huge amount of the mobile equipment
anytime and anywhere through Internet or Ethernet. MCC is infrastructure where processing and
storing of data could be performed out of the mobile device, however within the cloud. Within
MCC, data storage as well as computing power are shifted away from smartphones, then
performed within cloud, thus bringing applications of mobile cloud as well as mobile computing
to smartphones as well as to mobile subscribers’ wide range. Hence, MCC is infrastructure
which combines domains of cloud computing and mobile computing where processing of the
data and storing of data take place outside mobile devices. This is not that the offloading would
be the remote cloud, however it could be mobile devices’ collective resources in local vicinity.
Motivation for MCC is removing mobile computing’s existing drawbacks. Several limitations
are there of mobile computing that are discussed as follows:
Limited capacity of storage for mobile devices. There is limited internal memory
for every mobile device. However, these could be expanded by using external
memory.
Limited life of battery for mobile devices. As for mobility of device, this is
impossible in finding external source of power. The mobile devices depend on
internal battery that has charge life for few hours only. In several applications are
continuously running or computation is continuous, battery would drain soon.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 41
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





