Report: Victorian Protective Data Security Framework Overview
VerifiedAdded on 2020/03/04
|18
|3857
|81
Report
AI Summary
This report provides a comprehensive analysis of the Victorian Protective Data Security Framework (VPDSF), outlining the framework's purpose and its role in managing data security risks within the Victorian public sector. It delves into the standards and assurance models used to ensure the right access to information, referencing both national and international policies. The report identifies key security risks and concerns, categorizing them into high, medium, and low-risk areas, and presents a diagram illustrating these risks across domains like physical security, ICT, information, and personnel. It differentiates between deliberate and accidental threats, providing examples and highlighting the importance of security protocols and training. Furthermore, the report examines the challenges faced during internal and external risk assessments, detailing the responsibilities of both the organization and the Commissioner for Privacy and Data Protection (CPDP). It also touches upon the concepts of risk and uncertainty, emphasizing the need for proactive mitigation strategies and the use of digital protocols for efficient analysis. Overall, the report serves as a valuable resource for understanding the complexities of data security and risk management within the Victorian government context.

Running head: VICTORIAN PROTECTIVE DATA SECURITY FRAMEWORK
Victorian Protective Data Security Framework
Name of the student
Name of the University
Author note
Victorian Protective Data Security Framework
Name of the student
Name of the University
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1VICTORIAN PROTECTIVE DATA SECURITY FRAMEWORK
Executive summary
The following report discusses about the various risks and threats to the organization and the
standards that are made to address such threats by the Victorian government. The report also
includes a diagram to depict the risks present that are identified by the government concerned.
Executive summary
The following report discusses about the various risks and threats to the organization and the
standards that are made to address such threats by the Victorian government. The report also
includes a diagram to depict the risks present that are identified by the government concerned.

2VICTORIAN PROTECTIVE DATA SECURITY FRAMEWORK
Table of Contents
Introduction:....................................................................................................................................3
Discussion:.......................................................................................................................................3
Security risks and concerns:........................................................................................................4
Analyzing the diagram:................................................................................................................5
Deliberate and accidental threats:................................................................................................6
Challenges:..................................................................................................................................8
Risks and uncertainty:..................................................................................................................9
Control and mitigation:..............................................................................................................10
Conclusion:....................................................................................................................................11
References:....................................................................................................................................12
Table of Contents
Introduction:....................................................................................................................................3
Discussion:.......................................................................................................................................3
Security risks and concerns:........................................................................................................4
Analyzing the diagram:................................................................................................................5
Deliberate and accidental threats:................................................................................................6
Challenges:..................................................................................................................................8
Risks and uncertainty:..................................................................................................................9
Control and mitigation:..............................................................................................................10
Conclusion:....................................................................................................................................11
References:....................................................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3VICTORIAN PROTECTIVE DATA SECURITY FRAMEWORK
Introduction:
The Victorian Government (VIC government) is referred to as the administrative and the
democratic authority of the Australian state of Victoria. The government was formed in the year
1851, which is shown in its Constitution. Since the year 1901, Victoria has been represented as a
Commonwealth of Australian state. Under the constitution of Australia, Victoria got judicial and
legislative supremacy in terms of the Commonwealth. The Victorian Protective Data Security
Framework (VPDSF) is the scheme that is deployed for the management of the risks in data
security in the public sector of Victoria. The framework includes the Victorian Protective Data
Security Standards (VPDSS), the Assurance Model and the security guides and supporting
resources. These standards are used to assist the operations of the government to ensure that the
access to right resources is given to the right people.
This report discusses about the various risks considered by the VIC government, and the
analysis of these risks. This report also discusses about the analysis of the threats and challenges
faced by the government. The report further discusses about the risk and uncertainty concepts
and risk mitigation that is followed by the Victorian Government.
Discussion:
The VPDSF standards are used to help the government to ensure the right access of
information to the right people. The standards are based on the national as well as international
standards and policies, and are used to provide security measures (Toohey, 2016). They also help
in identifying the operations of the public sector as well as the agencies of the Victorian
government. The Assurance model is used to monitor and assure activities done by the
Introduction:
The Victorian Government (VIC government) is referred to as the administrative and the
democratic authority of the Australian state of Victoria. The government was formed in the year
1851, which is shown in its Constitution. Since the year 1901, Victoria has been represented as a
Commonwealth of Australian state. Under the constitution of Australia, Victoria got judicial and
legislative supremacy in terms of the Commonwealth. The Victorian Protective Data Security
Framework (VPDSF) is the scheme that is deployed for the management of the risks in data
security in the public sector of Victoria. The framework includes the Victorian Protective Data
Security Standards (VPDSS), the Assurance Model and the security guides and supporting
resources. These standards are used to assist the operations of the government to ensure that the
access to right resources is given to the right people.
This report discusses about the various risks considered by the VIC government, and the
analysis of these risks. This report also discusses about the analysis of the threats and challenges
faced by the government. The report further discusses about the risk and uncertainty concepts
and risk mitigation that is followed by the Victorian Government.
Discussion:
The VPDSF standards are used to help the government to ensure the right access of
information to the right people. The standards are based on the national as well as international
standards and policies, and are used to provide security measures (Toohey, 2016). They also help
in identifying the operations of the public sector as well as the agencies of the Victorian
government. The Assurance model is used to monitor and assure activities done by the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4VICTORIAN PROTECTIVE DATA SECURITY FRAMEWORK
organization or the companies involved. The Assurance Model also assists the government to
analyze and measure the securities, efficiencies and economy benefits. The VPDSF also
promotes cultural changes in the organization involved by ensuring the adoption of the security
protocols. This helps the organization to do their business while successfully complying with the
government standards.
Security risks and concerns:
Various risks and concerns are identified by the Victorian government. These risks and
concerns that are faced should be addressed in their respective fields. For the commissioner for
privacy and protection of data, various steps should be followed (Redley & Raggatt, 2017).
These include the establishment of a framework for monitoring public sector information,
promotion of security practices in the public sector, formal reporting regarding the security of the
public sector. The steps to be followed by the public sector organization are development and
maintenance of security assessment profile, development of maintenance of security plan and
annual attestation of CPDP ("VICTORIAN PROTECTIVE DATA SECURITY
FRAMEWORK", 2017). The VPDSS has analyzed the presence of 18 requirements for the
protection of public sector information data to aid in governing the four different domains, which
includes personnel, information, physical security and ICT.
organization or the companies involved. The Assurance Model also assists the government to
analyze and measure the securities, efficiencies and economy benefits. The VPDSF also
promotes cultural changes in the organization involved by ensuring the adoption of the security
protocols. This helps the organization to do their business while successfully complying with the
government standards.
Security risks and concerns:
Various risks and concerns are identified by the Victorian government. These risks and
concerns that are faced should be addressed in their respective fields. For the commissioner for
privacy and protection of data, various steps should be followed (Redley & Raggatt, 2017).
These include the establishment of a framework for monitoring public sector information,
promotion of security practices in the public sector, formal reporting regarding the security of the
public sector. The steps to be followed by the public sector organization are development and
maintenance of security assessment profile, development of maintenance of security plan and
annual attestation of CPDP ("VICTORIAN PROTECTIVE DATA SECURITY
FRAMEWORK", 2017). The VPDSS has analyzed the presence of 18 requirements for the
protection of public sector information data to aid in governing the four different domains, which
includes personnel, information, physical security and ICT.
5VICTORIAN PROTECTIVE DATA SECURITY FRAMEWORK
Fig: CIA triangle
(Source: By the author)
Fig: CIA triangle
(Source: By the author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
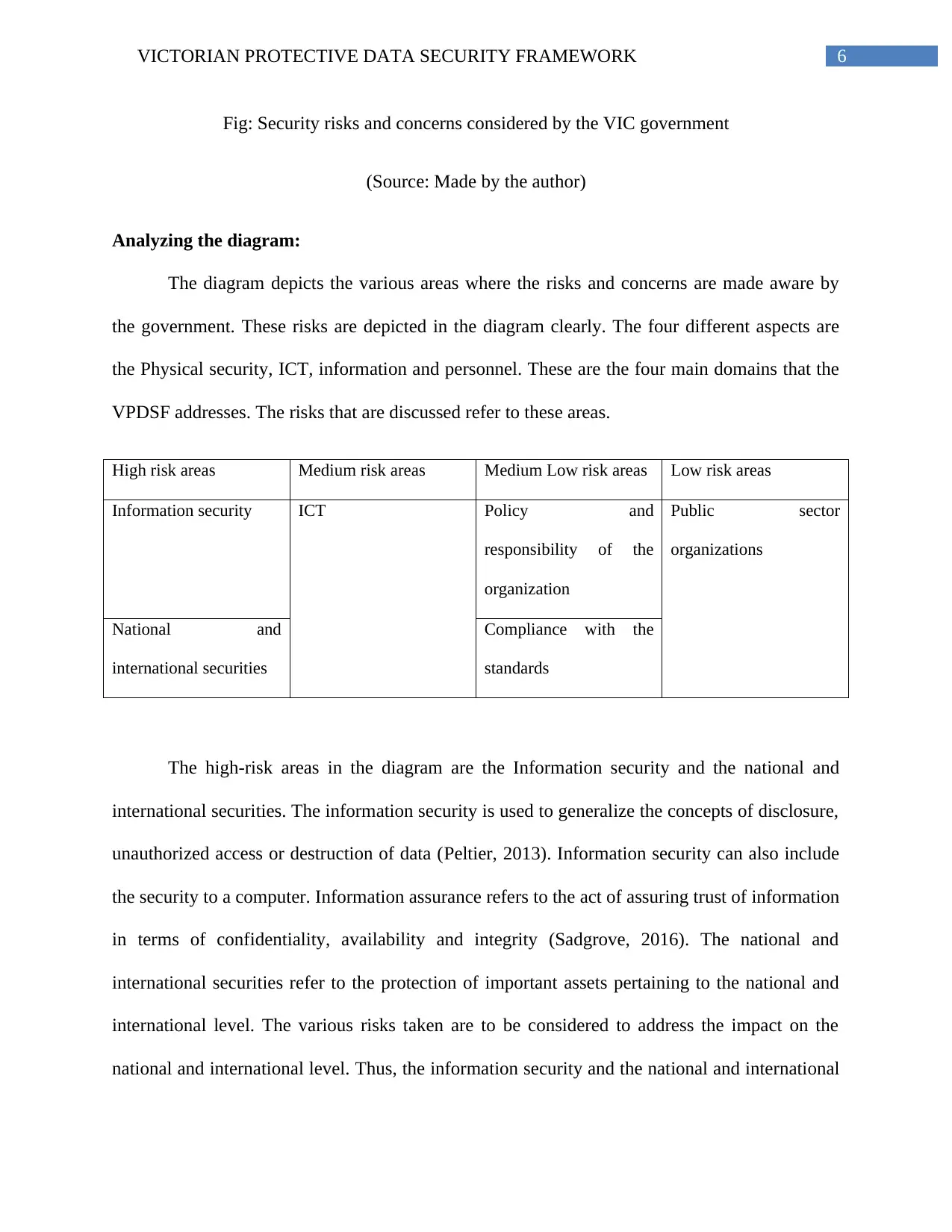
6VICTORIAN PROTECTIVE DATA SECURITY FRAMEWORK
Fig: Security risks and concerns considered by the VIC government
(Source: Made by the author)
Analyzing the diagram:
The diagram depicts the various areas where the risks and concerns are made aware by
the government. These risks are depicted in the diagram clearly. The four different aspects are
the Physical security, ICT, information and personnel. These are the four main domains that the
VPDSF addresses. The risks that are discussed refer to these areas.
High risk areas Medium risk areas Medium Low risk areas Low risk areas
Information security ICT Policy and
responsibility of the
organization
Public sector
organizations
National and
international securities
Compliance with the
standards
The high-risk areas in the diagram are the Information security and the national and
international securities. The information security is used to generalize the concepts of disclosure,
unauthorized access or destruction of data (Peltier, 2013). Information security can also include
the security to a computer. Information assurance refers to the act of assuring trust of information
in terms of confidentiality, availability and integrity (Sadgrove, 2016). The national and
international securities refer to the protection of important assets pertaining to the national and
international level. The various risks taken are to be considered to address the impact on the
national and international level. Thus, the information security and the national and international
Fig: Security risks and concerns considered by the VIC government
(Source: Made by the author)
Analyzing the diagram:
The diagram depicts the various areas where the risks and concerns are made aware by
the government. These risks are depicted in the diagram clearly. The four different aspects are
the Physical security, ICT, information and personnel. These are the four main domains that the
VPDSF addresses. The risks that are discussed refer to these areas.
High risk areas Medium risk areas Medium Low risk areas Low risk areas
Information security ICT Policy and
responsibility of the
organization
Public sector
organizations
National and
international securities
Compliance with the
standards
The high-risk areas in the diagram are the Information security and the national and
international securities. The information security is used to generalize the concepts of disclosure,
unauthorized access or destruction of data (Peltier, 2013). Information security can also include
the security to a computer. Information assurance refers to the act of assuring trust of information
in terms of confidentiality, availability and integrity (Sadgrove, 2016). The national and
international securities refer to the protection of important assets pertaining to the national and
international level. The various risks taken are to be considered to address the impact on the
national and international level. Thus, the information security and the national and international
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7VICTORIAN PROTECTIVE DATA SECURITY FRAMEWORK
security are place of high risk. These risks are to be addressed first before the mitigating the
other lists of risks (Almeida, Hankins & Williams, 2016). The medium risk area is the ICT
security. ICT refers to those technologies that are used to provide information via
communications. It is same as the information technology with a more direct emphasis on
telecommunications. The telecommunication aspects give people the exclusive advantages to
communicate to each other. The medium-low risk areas are the policy and responsibility of the
organization and the necessary compliance with the standards. The policies and responsibilities
of an organization should be complied with the government needs. The organizations should be
complied with the policies made by the government for effective business process (Cole, Giné &
Vickery, 2017). The low risk areas are the public sector organizations. The public sector
organizations are those whose resources are made exclusively for the people. The aspects of the
sector are made public. These areas are sometimes prone to risks and thus needs appliance of
certain protocols to increase the security.
Deliberate and accidental threats:
The main problems associated with the provided document are the need for protection of
public sector data (Nurse et al., 2014). The security risks are identified and recorded according to
the standards followed in the standard of risk management. Public sector organizations may ask
for user data and individuals may provide them for efficient and smooth running of the
organization. In the same way, the organization needs to inform the individual concerned about
their information being used by them (Pritchard & PMP, 2014). Thus, it is recommended that
though the information gained can help in efficient and smooth running of the organization,
assurance to the individual must be given to the individuals concerned about the less misuse of
the information. According to an organization, the deliberate threats to an organization are the
security are place of high risk. These risks are to be addressed first before the mitigating the
other lists of risks (Almeida, Hankins & Williams, 2016). The medium risk area is the ICT
security. ICT refers to those technologies that are used to provide information via
communications. It is same as the information technology with a more direct emphasis on
telecommunications. The telecommunication aspects give people the exclusive advantages to
communicate to each other. The medium-low risk areas are the policy and responsibility of the
organization and the necessary compliance with the standards. The policies and responsibilities
of an organization should be complied with the government needs. The organizations should be
complied with the policies made by the government for effective business process (Cole, Giné &
Vickery, 2017). The low risk areas are the public sector organizations. The public sector
organizations are those whose resources are made exclusively for the people. The aspects of the
sector are made public. These areas are sometimes prone to risks and thus needs appliance of
certain protocols to increase the security.
Deliberate and accidental threats:
The main problems associated with the provided document are the need for protection of
public sector data (Nurse et al., 2014). The security risks are identified and recorded according to
the standards followed in the standard of risk management. Public sector organizations may ask
for user data and individuals may provide them for efficient and smooth running of the
organization. In the same way, the organization needs to inform the individual concerned about
their information being used by them (Pritchard & PMP, 2014). Thus, it is recommended that
though the information gained can help in efficient and smooth running of the organization,
assurance to the individual must be given to the individuals concerned about the less misuse of
the information. According to an organization, the deliberate threats to an organization are the

8VICTORIAN PROTECTIVE DATA SECURITY FRAMEWORK
trespassing to get access, extortion, sabotaging, theft and software attacks (Luiijf, 2012). These
threats are those, which includes the mistreatment of security standards to get access to the
organization concerned. The organizations should implement stronger security protocols for
addressing such threats as these can affect the operation of a day or a month in some extreme
cases. The Sabotaging and software attacks are the most important threats and organization
should follow the security standards to address them. The information security and the ICT
security are the places where deliberate threats are possible. Strong security policies must be in
place to address them. The compliance of the service providers are also another place of
deliberate threat (Davies, 2014). The service provider may not agree to comply and new risks are
taken during implementation of the product. The information security and the ICT security
comes in the first order of importance and must be addressed when faced. The compliance of
service providers comes next in the chain of importance. An example of a deliberate attack
includes the Catalonia deliberate attack on civilians. A van was deliberately made to go through
crowded places and this led to injuries to many people.
trespassing to get access, extortion, sabotaging, theft and software attacks (Luiijf, 2012). These
threats are those, which includes the mistreatment of security standards to get access to the
organization concerned. The organizations should implement stronger security protocols for
addressing such threats as these can affect the operation of a day or a month in some extreme
cases. The Sabotaging and software attacks are the most important threats and organization
should follow the security standards to address them. The information security and the ICT
security are the places where deliberate threats are possible. Strong security policies must be in
place to address them. The compliance of the service providers are also another place of
deliberate threat (Davies, 2014). The service provider may not agree to comply and new risks are
taken during implementation of the product. The information security and the ICT security
comes in the first order of importance and must be addressed when faced. The compliance of
service providers comes next in the chain of importance. An example of a deliberate attack
includes the Catalonia deliberate attack on civilians. A van was deliberately made to go through
crowded places and this led to injuries to many people.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9VICTORIAN PROTECTIVE DATA SECURITY FRAMEWORK
Fig: Threats
(Source: Created by the author)
The accidental attacks are those attacks, which cannot be controlled. These attacks
include the natural disasters, or technical failures or human errors (Jouini, Rabai & Aissa, 2014).
The technical failures and the human errors are the most important as these can be reduced to a
reasonable level by proper management. Training must be given from authorized personnel and
the employees must be made aware of those training to be followed form time to time. The
natural disasters cannot be controlled at all (Heazle et al., 2013). These disasters can damage the
flow of operation and lead to effective problems. Thus, it is necessary to take preventive
measures to fight the problems that could have been associated. Presence of backup and system
recovery are the first measure that must be taken as a precaution for extreme cases (Paschen &
Beilin, 2017). The organizational polices and the securities of national and international level are
accidental as the failure to comply with the organizational policy is not always intentional. In the
Fig: Threats
(Source: Created by the author)
The accidental attacks are those attacks, which cannot be controlled. These attacks
include the natural disasters, or technical failures or human errors (Jouini, Rabai & Aissa, 2014).
The technical failures and the human errors are the most important as these can be reduced to a
reasonable level by proper management. Training must be given from authorized personnel and
the employees must be made aware of those training to be followed form time to time. The
natural disasters cannot be controlled at all (Heazle et al., 2013). These disasters can damage the
flow of operation and lead to effective problems. Thus, it is necessary to take preventive
measures to fight the problems that could have been associated. Presence of backup and system
recovery are the first measure that must be taken as a precaution for extreme cases (Paschen &
Beilin, 2017). The organizational polices and the securities of national and international level are
accidental as the failure to comply with the organizational policy is not always intentional. In the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10VICTORIAN PROTECTIVE DATA SECURITY FRAMEWORK
same way, national and international threat is not always intentional as well. One such accidental
attack was reported when a ransomware virus attacked a Russian biggest oil company. The
company faced such accidental attacks and the IT operations of the business were halted to
overcome the problems. This attack were made by various hackers but the organization was not
targeted which makes this an accidental attack.
Challenges:
During internal assessment of the risks, the organization needs to follow their standards
and policies that are already set but during external reporting of the risks, all the public sector
organizations are required to submit the deliverables to the Commissioner for Privacy and Data
Protection (CPDP). During the internal assessment, the organization involved is responsible for
conducting the assessment (DeAngelo & Stulz, 2015). The organization is accounted and
responsible for carrying out the assessment required. The CPDP is responsible for helping the
organization for assistance. The reporting of the assessment is done to the CPDP for reporting
the assessment. However, during the external assessment needed, the CPDP is accounted and
responsible for conducting it. The organizations are then consulted for assistance. They are then
reported about the assessment.
The CPDP is responsible for the establishment of a framework to help to monitor and
maintain the data in the public sector. They are also responsible for the promotion of security
practices in the public sector (Glendon, Clarke & McKenna, 2016). The maintenance and
requirement of audits are made so that compliance to standards is maintained. They are also
responsible for recommendations and formal reporting regarding the security of information. In
addition, CPDP conducts research to upgrade the security provides in the public sector and
maintains copies of them to report such security plans.
same way, national and international threat is not always intentional as well. One such accidental
attack was reported when a ransomware virus attacked a Russian biggest oil company. The
company faced such accidental attacks and the IT operations of the business were halted to
overcome the problems. This attack were made by various hackers but the organization was not
targeted which makes this an accidental attack.
Challenges:
During internal assessment of the risks, the organization needs to follow their standards
and policies that are already set but during external reporting of the risks, all the public sector
organizations are required to submit the deliverables to the Commissioner for Privacy and Data
Protection (CPDP). During the internal assessment, the organization involved is responsible for
conducting the assessment (DeAngelo & Stulz, 2015). The organization is accounted and
responsible for carrying out the assessment required. The CPDP is responsible for helping the
organization for assistance. The reporting of the assessment is done to the CPDP for reporting
the assessment. However, during the external assessment needed, the CPDP is accounted and
responsible for conducting it. The organizations are then consulted for assistance. They are then
reported about the assessment.
The CPDP is responsible for the establishment of a framework to help to monitor and
maintain the data in the public sector. They are also responsible for the promotion of security
practices in the public sector (Glendon, Clarke & McKenna, 2016). The maintenance and
requirement of audits are made so that compliance to standards is maintained. They are also
responsible for recommendations and formal reporting regarding the security of information. In
addition, CPDP conducts research to upgrade the security provides in the public sector and
maintains copies of them to report such security plans.

11VICTORIAN PROTECTIVE DATA SECURITY FRAMEWORK
For assessing the requirements, the public sector organizations need to follow certain
responsibilities as well. They are responsible for the development and maintenance of Security
Risk Profile Assessment (SRPA) and Protective data Security Plan (PDSP). They are also
responsible to provide the CPDP access to all the information when requested. The organizations
also need to participate in any kind of surveys done by the CPDP (Hopkin, 2017). In addition,
the organizations need to ensure that any service provider do not engage in any kid of activities
that jeopardizes the security standard of the government. They are also responsible to perform
and maintain internal audits and risk management that associates all the various entities they are
involved in business.
Thus, the VIC government is required to make use of digital protocols that will help
smooth analysis by the government. The security protocols for such actions are to be heightened
and constant review of the protocols is to be done. This will facilitate better analysis of the
assessment done for the risks and threats involved.
Risks and uncertainty:
Risks are defined as a state where there can be loss or profit pertaining to a decision.
Risks can also be associated with an interaction of uncertainty (Howes et al., 2015). Risks are an
event, which is considered beforehand, and if there is a presence of risks, impact is made on at
least one portion. In terms of finance, the possibility that the profit will be less than the desired
one is termed as a risk.
For assessing the requirements, the public sector organizations need to follow certain
responsibilities as well. They are responsible for the development and maintenance of Security
Risk Profile Assessment (SRPA) and Protective data Security Plan (PDSP). They are also
responsible to provide the CPDP access to all the information when requested. The organizations
also need to participate in any kind of surveys done by the CPDP (Hopkin, 2017). In addition,
the organizations need to ensure that any service provider do not engage in any kid of activities
that jeopardizes the security standard of the government. They are also responsible to perform
and maintain internal audits and risk management that associates all the various entities they are
involved in business.
Thus, the VIC government is required to make use of digital protocols that will help
smooth analysis by the government. The security protocols for such actions are to be heightened
and constant review of the protocols is to be done. This will facilitate better analysis of the
assessment done for the risks and threats involved.
Risks and uncertainty:
Risks are defined as a state where there can be loss or profit pertaining to a decision.
Risks can also be associated with an interaction of uncertainty (Howes et al., 2015). Risks are an
event, which is considered beforehand, and if there is a presence of risks, impact is made on at
least one portion. In terms of finance, the possibility that the profit will be less than the desired
one is termed as a risk.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





