Comprehensive Risk Management Report: Victorian Government Security
VerifiedAdded on 2020/02/24
|14
|3625
|201
Report
AI Summary
This report provides a comprehensive analysis of risk management and information security within the Victorian government. It begins with an introduction to information security and the Victorian Protective Data Security Framework (VPDSF), outlining its objectives and the types of risks it addresses. The report then delves into a comparative analysis of both accidental and deliberate threats, providing examples and mitigation strategies for each. It explores the challenges of security and risk management, including the decision to outsource security operations and the advantages and disadvantages of doing so. The report clarifies the distinction between 'risk' and 'uncertainty' and details risk control and mitigation measures, emphasizing the importance of the VPDSF. It includes a risk factor table, categorizing risks by severity and offering recommendations for improving the government's security posture. Finally, the report concludes by summarizing the key findings and reiterating the importance of proactive risk management in protecting sensitive information.

Risk management
VIC
[Name]
VIC
[Name]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Introduction..............................................................................................................................3
Comparative analysis of Threats..............................................................................................4
Challenges of security/risk management approach...................................................................8
‘’Risk’’ and ‘’Uncertainty’’.....................................................................................................9
Risk control and mitigation....................................................................................................10
Recommendations..................................................................................................................11
Conclusion............................................................................................................................. 11
References..............................................................................................................................13
2
Introduction..............................................................................................................................3
Comparative analysis of Threats..............................................................................................4
Challenges of security/risk management approach...................................................................8
‘’Risk’’ and ‘’Uncertainty’’.....................................................................................................9
Risk control and mitigation....................................................................................................10
Recommendations..................................................................................................................11
Conclusion............................................................................................................................. 11
References..............................................................................................................................13
2
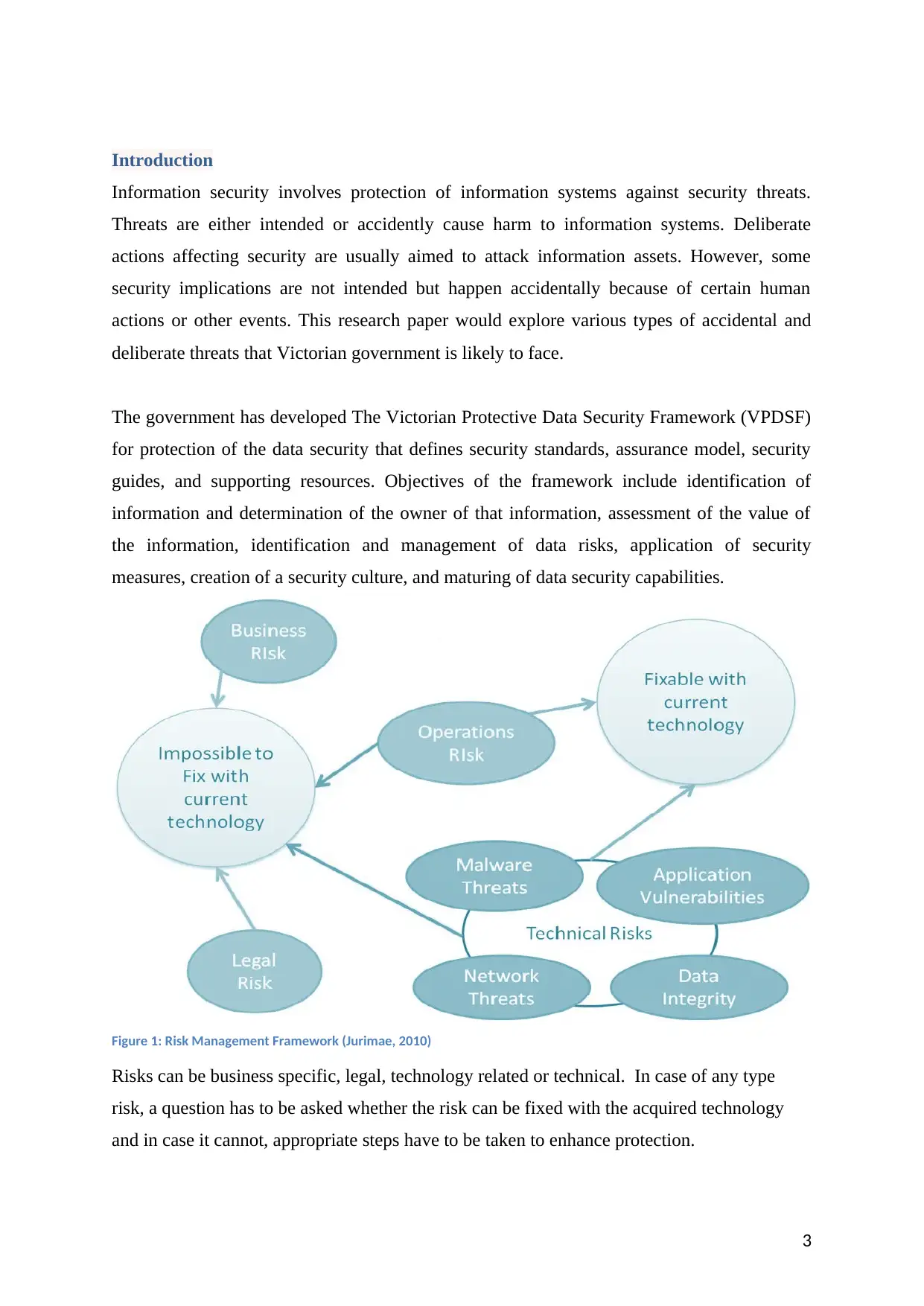
Introduction
Information security involves protection of information systems against security threats.
Threats are either intended or accidently cause harm to information systems. Deliberate
actions affecting security are usually aimed to attack information assets. However, some
security implications are not intended but happen accidentally because of certain human
actions or other events. This research paper would explore various types of accidental and
deliberate threats that Victorian government is likely to face.
The government has developed The Victorian Protective Data Security Framework (VPDSF)
for protection of the data security that defines security standards, assurance model, security
guides, and supporting resources. Objectives of the framework include identification of
information and determination of the owner of that information, assessment of the value of
the information, identification and management of data risks, application of security
measures, creation of a security culture, and maturing of data security capabilities.
Figure 1: Risk Management Framework (Jurimae, 2010)
Risks can be business specific, legal, technology related or technical. In case of any type
risk, a question has to be asked whether the risk can be fixed with the acquired technology
and in case it cannot, appropriate steps have to be taken to enhance protection.
3
Information security involves protection of information systems against security threats.
Threats are either intended or accidently cause harm to information systems. Deliberate
actions affecting security are usually aimed to attack information assets. However, some
security implications are not intended but happen accidentally because of certain human
actions or other events. This research paper would explore various types of accidental and
deliberate threats that Victorian government is likely to face.
The government has developed The Victorian Protective Data Security Framework (VPDSF)
for protection of the data security that defines security standards, assurance model, security
guides, and supporting resources. Objectives of the framework include identification of
information and determination of the owner of that information, assessment of the value of
the information, identification and management of data risks, application of security
measures, creation of a security culture, and maturing of data security capabilities.
Figure 1: Risk Management Framework (Jurimae, 2010)
Risks can be business specific, legal, technology related or technical. In case of any type
risk, a question has to be asked whether the risk can be fixed with the acquired technology
and in case it cannot, appropriate steps have to be taken to enhance protection.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Comparative analysis of Threats
Threats can either be accidental or deliberate. Accidental Threats are caused by users or
situations accidently causing risks to information systems. Some examples of accidental
threats include:
Natural disasters such as earthquake, hurricanes, tornadoes, cyclones, etc. causing
damage to infrastructure and thus, cause loss of data
Technical failures caused by breakdown of hardware
Errors or mistakes done by humans such as loss of devices, opening of emails from
unknown sources, lowering of security level, download of unsafe files, etc.
Some people may end up using social engineering by trying to trick some into
providing confidential information. This may not be a deliberate threat to cause harm
but it does pose risk to the person whose data is revealed (AlKalbani, Deng, & Kam,
2015).
Certain ways these accidental threats can be avoided or their impacts can be mitigated
include:
Any changes that are made to the critical data of an organization must be monitored
and the permissions to access or modify the data should only be with specific
designated people.
For controlling access, user manuals can be developed.
All the print outs that are obtained for the management must be shredded after use
People with different job functions should have differential access to information. For
example, a programmer may not be provided with an access to the storage systems.
The data that is being exchanged online can be encrypted (S, 2016)
IT auditors may be hired for checking if the company systems are secure such that
their guidance can help in improving security of the company.
Transaction logs of the usage can be stored to check who has used or seen which
programs in the system (Anderson, 1994)
Deliberate Threats are those intended to cause security harm to a system and it can be in
various forms such as espionage, extortion, sabotage, data theft, and software attacks such as
Trojan, virus, worm, denial of service, phishing, key logger, spyware, malware and spam
ware.
Risk rating model is based on the likelihood of the occurrence of a risk and its impact on an
organization. The determination of rating factors that cause these risks can be broken down
4
Threats can either be accidental or deliberate. Accidental Threats are caused by users or
situations accidently causing risks to information systems. Some examples of accidental
threats include:
Natural disasters such as earthquake, hurricanes, tornadoes, cyclones, etc. causing
damage to infrastructure and thus, cause loss of data
Technical failures caused by breakdown of hardware
Errors or mistakes done by humans such as loss of devices, opening of emails from
unknown sources, lowering of security level, download of unsafe files, etc.
Some people may end up using social engineering by trying to trick some into
providing confidential information. This may not be a deliberate threat to cause harm
but it does pose risk to the person whose data is revealed (AlKalbani, Deng, & Kam,
2015).
Certain ways these accidental threats can be avoided or their impacts can be mitigated
include:
Any changes that are made to the critical data of an organization must be monitored
and the permissions to access or modify the data should only be with specific
designated people.
For controlling access, user manuals can be developed.
All the print outs that are obtained for the management must be shredded after use
People with different job functions should have differential access to information. For
example, a programmer may not be provided with an access to the storage systems.
The data that is being exchanged online can be encrypted (S, 2016)
IT auditors may be hired for checking if the company systems are secure such that
their guidance can help in improving security of the company.
Transaction logs of the usage can be stored to check who has used or seen which
programs in the system (Anderson, 1994)
Deliberate Threats are those intended to cause security harm to a system and it can be in
various forms such as espionage, extortion, sabotage, data theft, and software attacks such as
Trojan, virus, worm, denial of service, phishing, key logger, spyware, malware and spam
ware.
Risk rating model is based on the likelihood of the occurrence of a risk and its impact on an
organization. The determination of rating factors that cause these risks can be broken down
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

into steps including risk identification, likelihood estimation, impact estimation,
determination of severity of risk, decision on what to fix and customization of the risk model
based on it (Brey, 2007).
Risk Identification: The first step to risk ranking is risk identification. In case of the
Victorian government, various risks that can occur include:
Power failure
Network failure or errors
Technology Obsolescence
Hardware failure or errors
Operational issues
Communication interception
Repudiation
Espionage
Infiltration
Social Engineering
Technical Failures
Data theft
Misuse of resources (CGI, 2013)
Staff shortage
Unauthorized communication
User Errors
Sabotage
Quality deviations
Environmental Threats
Intellectual property compromise (ESET, 2016)
Incomplete or missing data
Faulty planning
Financial Fraud
Equipment Theft
Terrorism
Natural Disasters (Shahri & Ismail, 2012)
In the next step, likelihood is estimated which measures the probability that a vulnerability in
the information system would be exploited by an attacker. There is a set of agent factors and
5
determination of severity of risk, decision on what to fix and customization of the risk model
based on it (Brey, 2007).
Risk Identification: The first step to risk ranking is risk identification. In case of the
Victorian government, various risks that can occur include:
Power failure
Network failure or errors
Technology Obsolescence
Hardware failure or errors
Operational issues
Communication interception
Repudiation
Espionage
Infiltration
Social Engineering
Technical Failures
Data theft
Misuse of resources (CGI, 2013)
Staff shortage
Unauthorized communication
User Errors
Sabotage
Quality deviations
Environmental Threats
Intellectual property compromise (ESET, 2016)
Incomplete or missing data
Faulty planning
Financial Fraud
Equipment Theft
Terrorism
Natural Disasters (Shahri & Ismail, 2012)
In the next step, likelihood is estimated which measures the probability that a vulnerability in
the information system would be exploited by an attacker. There is a set of agent factors and
5

vulnerability factors that can be used for this calculation such that each factor is given a
rating between 0 and 9. Agent factors include level of skills of the threat agents, motive of
attack, resources and opportunity requirement, size of the threat group. Vulnerability factors
include ease of the discovery of the vulnerability, ease of exploitation, awareness of the
vulnerability to the agent, and likelihood of an exploit getting detected (CenturyLink
Solutions Consulting, 2014).
After estimating this likelihood, the factors of impact are also rated on the scale of 0 to 9.
These factors include technical impacts like loss of confidentiality, integrity, availability and
accountability and business impacts like financial damage, reputation damage, non-
compliance, and privacy violation (Engine Yard, Inc., 2014).
The likelihood of occurrence and the impact factors are put together to assess the severity of
the impact of the risk which could be low, medium, high or critical. Based on this severity,
risks are categorized and given priority for resolution (Chen & Zhao, 2012). Risk severity can
be:
Low: When Likelihood is medium and impact is low and when likelihood is low but impact
is medium.
Medium: When Likelihood is Low and impact is High, when both are medium and when
likelihood is high but impact is low.
High: When Likelihood is medium and impact is high and when likelihood is high but impact
is medium.
Critical: When both Likelihood and impact are high then the risk can be considered as
critical (Gopinath, 2011).
The risks are decided to fix based on this categorization from critical to high, medium and
lastly, low.
Based on these factors, the risk model of Victorian Government can be modified with
addition of certain factors, tuning the model based on risks, and customizing testing options.
The table below presents the calculation of all the risk factors and the overall risk ranking for
all the identified risks for the case of Victoria.
6
rating between 0 and 9. Agent factors include level of skills of the threat agents, motive of
attack, resources and opportunity requirement, size of the threat group. Vulnerability factors
include ease of the discovery of the vulnerability, ease of exploitation, awareness of the
vulnerability to the agent, and likelihood of an exploit getting detected (CenturyLink
Solutions Consulting, 2014).
After estimating this likelihood, the factors of impact are also rated on the scale of 0 to 9.
These factors include technical impacts like loss of confidentiality, integrity, availability and
accountability and business impacts like financial damage, reputation damage, non-
compliance, and privacy violation (Engine Yard, Inc., 2014).
The likelihood of occurrence and the impact factors are put together to assess the severity of
the impact of the risk which could be low, medium, high or critical. Based on this severity,
risks are categorized and given priority for resolution (Chen & Zhao, 2012). Risk severity can
be:
Low: When Likelihood is medium and impact is low and when likelihood is low but impact
is medium.
Medium: When Likelihood is Low and impact is High, when both are medium and when
likelihood is high but impact is low.
High: When Likelihood is medium and impact is high and when likelihood is high but impact
is medium.
Critical: When both Likelihood and impact are high then the risk can be considered as
critical (Gopinath, 2011).
The risks are decided to fix based on this categorization from critical to high, medium and
lastly, low.
Based on these factors, the risk model of Victorian Government can be modified with
addition of certain factors, tuning the model based on risks, and customizing testing options.
The table below presents the calculation of all the risk factors and the overall risk ranking for
all the identified risks for the case of Victoria.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
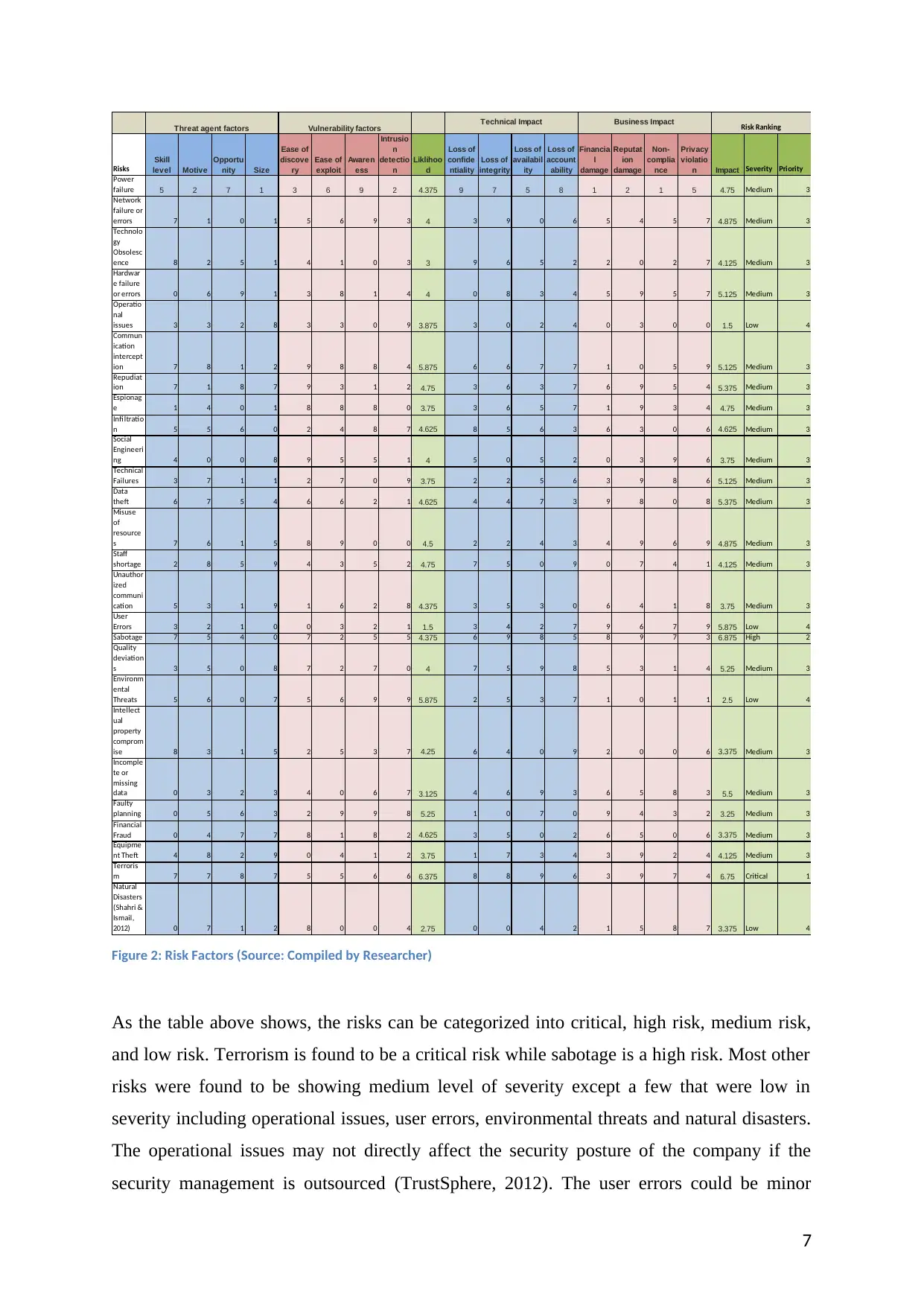
Risks
Skill
level Motive
Opportu
nity Size
Ease of
discove
ry
Ease of
exploit
Awaren
ess
Intrusio
n
detectio
n
Liklihoo
d
Loss of
confide
ntiality
Loss of
integrity
Loss of
availabil
ity
Loss of
account
ability
Financia
l
damage
Reputat
ion
damage
Non-
complia
nce
Privacy
violatio
n Impact Severity Priority
Power
failure 5 2 7 1 3 6 9 2 4.375 9 7 5 8 1 2 1 5 4.75 Medium 3
Network
failure or
errors 7 1 0 1 5 6 9 3 4 3 9 0 6 5 4 5 7 4.875 Medium 3
Technolo
gy
Obsolesc
ence 8 2 5 1 4 1 0 3 3 9 6 5 2 2 0 2 7 4.125 Medium 3
Hardwar
e failure
or errors 0 6 9 1 3 8 1 4 4 0 8 3 4 5 9 5 7 5.125 Medium 3
Operatio
nal
issues 3 3 2 8 3 3 0 9 3.875 3 0 2 4 0 3 0 0 1.5 Low 4
Commun
ication
intercept
ion 7 8 1 2 9 8 8 4 5.875 6 6 7 7 1 0 5 9 5.125 Medium 3
Repudiat
ion 7 1 8 7 9 3 1 2 4.75 3 6 3 7 6 9 5 4 5.375 Medium 3
Espionag
e 1 4 0 1 8 8 8 0 3.75 3 6 5 7 1 9 3 4 4.75 Medium 3
Infiltratio
n 5 5 6 0 2 4 8 7 4.625 8 5 6 3 6 3 0 6 4.625 Medium 3
Social
Engineeri
ng 4 0 0 8 9 5 5 1 4 5 0 5 2 0 3 9 6 3.75 Medium 3
Technical
Failures 3 7 1 1 2 7 0 9 3.75 2 2 5 6 3 9 8 6 5.125 Medium 3
Data
theft 6 7 5 4 6 6 2 1 4.625 4 4 7 3 9 8 0 8 5.375 Medium 3
Misuse
of
resource
s 7 6 1 5 8 9 0 0 4.5 2 2 4 3 4 9 6 9 4.875 Medium 3
Staff
shortage 2 8 5 9 4 3 5 2 4.75 7 5 0 9 0 7 4 1 4.125 Medium 3
Unauthor
ized
communi
cation 5 3 1 9 1 6 2 8 4.375 3 5 3 0 6 4 1 8 3.75 Medium 3
User
Errors 3 2 1 0 0 3 2 1 1.5 3 4 2 7 9 6 7 9 5.875 Low 4
Sabotage 7 5 4 0 7 2 5 5 4.375 6 9 8 5 8 9 7 3 6.875 High 2
Quality
deviation
s 3 5 0 8 7 2 7 0 4 7 5 9 8 5 3 1 4 5.25 Medium 3
Environm
ental
Threats 5 6 0 7 5 6 9 9 5.875 2 5 3 7 1 0 1 1 2.5 Low 4
Intellect
ual
property
comprom
ise 8 3 1 5 2 5 3 7 4.25 6 4 0 9 2 0 0 6 3.375 Medium 3
Incomple
te or
missing
data 0 3 2 3 4 0 6 7 3.125 4 6 9 3 6 5 8 3 5.5 Medium 3
Faulty
planning 0 5 6 3 2 9 9 8 5.25 1 0 7 0 9 4 3 2 3.25 Medium 3
Financial
Fraud 0 4 7 7 8 1 8 2 4.625 3 5 0 2 6 5 0 6 3.375 Medium 3
Equipme
nt Theft 4 8 2 9 0 4 1 2 3.75 1 7 3 4 3 9 2 4 4.125 Medium 3
Terroris
m 7 7 8 7 5 5 6 6 6.375 8 8 9 6 3 9 7 4 6.75 Critical 1
Natural
Disasters
(Shahri &
Ismail,
2012) 0 7 1 2 8 0 0 4 2.75 0 0 4 2 1 5 8 7 3.375 Low 4
Threat agent factors Vulnerability factors Technical Impact Business Impact Risk Ranking
Figure 2: Risk Factors (Source: Compiled by Researcher)
As the table above shows, the risks can be categorized into critical, high risk, medium risk,
and low risk. Terrorism is found to be a critical risk while sabotage is a high risk. Most other
risks were found to be showing medium level of severity except a few that were low in
severity including operational issues, user errors, environmental threats and natural disasters.
The operational issues may not directly affect the security posture of the company if the
security management is outsourced (TrustSphere, 2012). The user errors could be minor
7
Skill
level Motive
Opportu
nity Size
Ease of
discove
ry
Ease of
exploit
Awaren
ess
Intrusio
n
detectio
n
Liklihoo
d
Loss of
confide
ntiality
Loss of
integrity
Loss of
availabil
ity
Loss of
account
ability
Financia
l
damage
Reputat
ion
damage
Non-
complia
nce
Privacy
violatio
n Impact Severity Priority
Power
failure 5 2 7 1 3 6 9 2 4.375 9 7 5 8 1 2 1 5 4.75 Medium 3
Network
failure or
errors 7 1 0 1 5 6 9 3 4 3 9 0 6 5 4 5 7 4.875 Medium 3
Technolo
gy
Obsolesc
ence 8 2 5 1 4 1 0 3 3 9 6 5 2 2 0 2 7 4.125 Medium 3
Hardwar
e failure
or errors 0 6 9 1 3 8 1 4 4 0 8 3 4 5 9 5 7 5.125 Medium 3
Operatio
nal
issues 3 3 2 8 3 3 0 9 3.875 3 0 2 4 0 3 0 0 1.5 Low 4
Commun
ication
intercept
ion 7 8 1 2 9 8 8 4 5.875 6 6 7 7 1 0 5 9 5.125 Medium 3
Repudiat
ion 7 1 8 7 9 3 1 2 4.75 3 6 3 7 6 9 5 4 5.375 Medium 3
Espionag
e 1 4 0 1 8 8 8 0 3.75 3 6 5 7 1 9 3 4 4.75 Medium 3
Infiltratio
n 5 5 6 0 2 4 8 7 4.625 8 5 6 3 6 3 0 6 4.625 Medium 3
Social
Engineeri
ng 4 0 0 8 9 5 5 1 4 5 0 5 2 0 3 9 6 3.75 Medium 3
Technical
Failures 3 7 1 1 2 7 0 9 3.75 2 2 5 6 3 9 8 6 5.125 Medium 3
Data
theft 6 7 5 4 6 6 2 1 4.625 4 4 7 3 9 8 0 8 5.375 Medium 3
Misuse
of
resource
s 7 6 1 5 8 9 0 0 4.5 2 2 4 3 4 9 6 9 4.875 Medium 3
Staff
shortage 2 8 5 9 4 3 5 2 4.75 7 5 0 9 0 7 4 1 4.125 Medium 3
Unauthor
ized
communi
cation 5 3 1 9 1 6 2 8 4.375 3 5 3 0 6 4 1 8 3.75 Medium 3
User
Errors 3 2 1 0 0 3 2 1 1.5 3 4 2 7 9 6 7 9 5.875 Low 4
Sabotage 7 5 4 0 7 2 5 5 4.375 6 9 8 5 8 9 7 3 6.875 High 2
Quality
deviation
s 3 5 0 8 7 2 7 0 4 7 5 9 8 5 3 1 4 5.25 Medium 3
Environm
ental
Threats 5 6 0 7 5 6 9 9 5.875 2 5 3 7 1 0 1 1 2.5 Low 4
Intellect
ual
property
comprom
ise 8 3 1 5 2 5 3 7 4.25 6 4 0 9 2 0 0 6 3.375 Medium 3
Incomple
te or
missing
data 0 3 2 3 4 0 6 7 3.125 4 6 9 3 6 5 8 3 5.5 Medium 3
Faulty
planning 0 5 6 3 2 9 9 8 5.25 1 0 7 0 9 4 3 2 3.25 Medium 3
Financial
Fraud 0 4 7 7 8 1 8 2 4.625 3 5 0 2 6 5 0 6 3.375 Medium 3
Equipme
nt Theft 4 8 2 9 0 4 1 2 3.75 1 7 3 4 3 9 2 4 4.125 Medium 3
Terroris
m 7 7 8 7 5 5 6 6 6.375 8 8 9 6 3 9 7 4 6.75 Critical 1
Natural
Disasters
(Shahri &
Ismail,
2012) 0 7 1 2 8 0 0 4 2.75 0 0 4 2 1 5 8 7 3.375 Low 4
Threat agent factors Vulnerability factors Technical Impact Business Impact Risk Ranking
Figure 2: Risk Factors (Source: Compiled by Researcher)
As the table above shows, the risks can be categorized into critical, high risk, medium risk,
and low risk. Terrorism is found to be a critical risk while sabotage is a high risk. Most other
risks were found to be showing medium level of severity except a few that were low in
severity including operational issues, user errors, environmental threats and natural disasters.
The operational issues may not directly affect the security posture of the company if the
security management is outsourced (TrustSphere, 2012). The user errors could be minor
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

errors done by customers of the company and these can be handled by exceptions or can be
easily mitigated. Environmental threats and natural calamity may not have a direct impact on
the company’s information system unless the physical damage happens to data in which case
a backup can be obtained from the disaster recovery system there by resolving the risk impact
on the company and thus, would not affect the security posture of Victorian government
(Shahri & Ismail, 2012).
Challenges of security/risk management approach
Risk management or security management can either be established internally by developing
and using internal governance procedures and security policies or the same can be outsourced
to a third party security service provider. Initially, organizations used to establish their own
security systems but in past decade, many of them are outsourcing security management to
third party contractors. There are two key reasons behind this change (MYOB, 2016):
With increase in competition, it becomes imperative for organization employees to
focus on their core work. Security management is non-core support system and thus,
can be outsourced to experts in security by the companies while company’s internal
employees only focus on the core systems (Hu, Hart, & Cooke, 2007).
Because of increasing threats and sophistication in them day by day, costs of
establishing and updating security systems have drastically increased. Moreover, there
are many areas of work that have hidden costs needed for preventing personnel and
information resources from security threats (Chen, Longstaff, & Carley, 2004).
However, there are some concerns that cause challenges while taking decisions on whether to
outsource their security operations. Security directors of organizations are highly concerned
about outsourcing as the organization would then have less control over the security program.
Organizations would have to do an extensive background check of the security service
provider before the system is put in their control. However, organizations are looking for
outsourcing as an option as it can help a company improve its security posture (HP
Enterprise, 2015).
There are certain advantages of using contract arrangement for security management such as
Reduced overheads on office, administrative and operational costs
Increasing efficiency as well as productiveness of the security systems with the focus
of contractor on security as a core function
8
easily mitigated. Environmental threats and natural calamity may not have a direct impact on
the company’s information system unless the physical damage happens to data in which case
a backup can be obtained from the disaster recovery system there by resolving the risk impact
on the company and thus, would not affect the security posture of Victorian government
(Shahri & Ismail, 2012).
Challenges of security/risk management approach
Risk management or security management can either be established internally by developing
and using internal governance procedures and security policies or the same can be outsourced
to a third party security service provider. Initially, organizations used to establish their own
security systems but in past decade, many of them are outsourcing security management to
third party contractors. There are two key reasons behind this change (MYOB, 2016):
With increase in competition, it becomes imperative for organization employees to
focus on their core work. Security management is non-core support system and thus,
can be outsourced to experts in security by the companies while company’s internal
employees only focus on the core systems (Hu, Hart, & Cooke, 2007).
Because of increasing threats and sophistication in them day by day, costs of
establishing and updating security systems have drastically increased. Moreover, there
are many areas of work that have hidden costs needed for preventing personnel and
information resources from security threats (Chen, Longstaff, & Carley, 2004).
However, there are some concerns that cause challenges while taking decisions on whether to
outsource their security operations. Security directors of organizations are highly concerned
about outsourcing as the organization would then have less control over the security program.
Organizations would have to do an extensive background check of the security service
provider before the system is put in their control. However, organizations are looking for
outsourcing as an option as it can help a company improve its security posture (HP
Enterprise, 2015).
There are certain advantages of using contract arrangement for security management such as
Reduced overheads on office, administrative and operational costs
Increasing efficiency as well as productiveness of the security systems with the focus
of contractor on security as a core function
8
Assess the benefits that supplier of security services may have such as experience of
using best practices, professional training, screening of professionals, payrolls
management, operations, and so on.
More flexibility to change security posture and business conditions based on the need
of the time (MYOB, 2016).
Sharing of risks and the liability as multiple companies may be using the same
systems and thus, finding solutions would attract a combined effort.
Companies can leverage on the expertise, resources, and experience of the service
provider
Reduction in the cost that would otherwise be incurred in establishing the security
infrastructure for the organization (MYOB, 2016)
‘’Risk’’ and ‘’Uncertainty’’
Uncertainty is a potential outcome which is unpredictable and uncontrollable while risk
occurs when actions are taken despite the uncertainty of the outcome from the action. Risk is
a situation in which there is a possibility of facing a loss as an outcome while uncertainty is a
situation where the outcome is not clear. The comparison between the two can be made clear
using a comparison table as shown below:
Table A: Uncertainty vs Risk (NIST, 2014)
Basis of
comparison
Uncertainty Risk
Meaning Situation where the outcome
cannot be predicted
Probability that the outcome
would be a loss or a victory
Outcome Unknown Known
Probabilities Assigned Not assigned
Ascertainment Cannot measure Can measure
Minimization No Yes
Control Cannot be controlled Can be controlled (Xero, 2016)
A risk can be systematic such as market and inflation risks or unsystematic such as business
or financial risk (NIST, 2014).
9
using best practices, professional training, screening of professionals, payrolls
management, operations, and so on.
More flexibility to change security posture and business conditions based on the need
of the time (MYOB, 2016).
Sharing of risks and the liability as multiple companies may be using the same
systems and thus, finding solutions would attract a combined effort.
Companies can leverage on the expertise, resources, and experience of the service
provider
Reduction in the cost that would otherwise be incurred in establishing the security
infrastructure for the organization (MYOB, 2016)
‘’Risk’’ and ‘’Uncertainty’’
Uncertainty is a potential outcome which is unpredictable and uncontrollable while risk
occurs when actions are taken despite the uncertainty of the outcome from the action. Risk is
a situation in which there is a possibility of facing a loss as an outcome while uncertainty is a
situation where the outcome is not clear. The comparison between the two can be made clear
using a comparison table as shown below:
Table A: Uncertainty vs Risk (NIST, 2014)
Basis of
comparison
Uncertainty Risk
Meaning Situation where the outcome
cannot be predicted
Probability that the outcome
would be a loss or a victory
Outcome Unknown Known
Probabilities Assigned Not assigned
Ascertainment Cannot measure Can measure
Minimization No Yes
Control Cannot be controlled Can be controlled (Xero, 2016)
A risk can be systematic such as market and inflation risks or unsystematic such as business
or financial risk (NIST, 2014).
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Risk control and mitigation
For controlling and mitigating risks, the security data framework of VIC can be used. For
controlling the risks, the preventive measures can be taken using the guidelines given in the
security protocols defined in the framework. This includes:
Study of evolving security risks in the information systems and updating the security
framework accordingly
Recording of risks identified in the risk register
Monitoring and reviewing of all the risks recorded in the register
Implementation of the security requirements in the policies and procedures of the
organization, access management system, business continuity management, contract
services, service agreements, sharing practices, personnel management, ICT
management, and physical management of the company (Cisco, 2013)
Embedding security functions in routine functions as well as activities in the
organization
Identification and enforcement of the obligations all the people in the company
considering security aspects
Monitoring and review of all security requirements to identify possibility for
improvement or updating (OECD, 2008).
Creating awareness program and providing training on security to personnel
Implementation, monitoring and review of incident management system
Conducting annual assessment for security compliance for review (DHS, 2009)
The response and mitigation to the risks would be decided based on the severity of
each risk. Risks that are critical or high impact must be avoided but in case they still
occur, immediate actions have to be taken on priority. As in the case of VIC, terrorism
and sabotage are the critical and high risk categories, they have to be avoided which
may not be possible and thus, in case such a situation occurs, an immediate action
would be warranted. For risks that are of medium severity, a mitigation plan for
reduction of the impact of the risk on the security posture of the organization can be
taken. In case of the low severity risks, they can be avoided without any advanced
actions but if they occur then decision can be taken on whether to accept them or
mitigate their impacts depending on the actual rating of the severity of the risk
identified (Security Awareness Program Special Interest Group, 2014).
10
For controlling and mitigating risks, the security data framework of VIC can be used. For
controlling the risks, the preventive measures can be taken using the guidelines given in the
security protocols defined in the framework. This includes:
Study of evolving security risks in the information systems and updating the security
framework accordingly
Recording of risks identified in the risk register
Monitoring and reviewing of all the risks recorded in the register
Implementation of the security requirements in the policies and procedures of the
organization, access management system, business continuity management, contract
services, service agreements, sharing practices, personnel management, ICT
management, and physical management of the company (Cisco, 2013)
Embedding security functions in routine functions as well as activities in the
organization
Identification and enforcement of the obligations all the people in the company
considering security aspects
Monitoring and review of all security requirements to identify possibility for
improvement or updating (OECD, 2008).
Creating awareness program and providing training on security to personnel
Implementation, monitoring and review of incident management system
Conducting annual assessment for security compliance for review (DHS, 2009)
The response and mitigation to the risks would be decided based on the severity of
each risk. Risks that are critical or high impact must be avoided but in case they still
occur, immediate actions have to be taken on priority. As in the case of VIC, terrorism
and sabotage are the critical and high risk categories, they have to be avoided which
may not be possible and thus, in case such a situation occurs, an immediate action
would be warranted. For risks that are of medium severity, a mitigation plan for
reduction of the impact of the risk on the security posture of the organization can be
taken. In case of the low severity risks, they can be avoided without any advanced
actions but if they occur then decision can be taken on whether to accept them or
mitigate their impacts depending on the actual rating of the severity of the risk
identified (Security Awareness Program Special Interest Group, 2014).
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Recommendations
Based on the study of risks and uncertainties that are likely to be faced by VIC organization
while managing its security framework, certain recommendations can be made for the
company for enhancing its security posture such as:
The company can outsource its security and risk management to a third party which
would save on the cost of security personnel, management as well as provide them
access to an expertise of the security expert consultancy.
The company can provide training to the staff on the security frameworks and
unintentional risks such that the probability of posing such risks can be reduced with
the increased awareness in the staff
The company should keep its security systems updated with the latest happening such
that latest threats can be tackled for which the security audit can be conducted yearly
to identify loopholes for updating
A regular and monitoring of the security systems and the risk register must be done so
that it can be ensured that security systems are working as expected and in case of
problems, they can be resolved fast.
A number of different factors can be used for the assessment of risks for each type of
risk such that the severity of each risk can be known and accordingly a plan for
managing risks can be made including mitigation and control strategies.
The risks with medium level of the severity must be avoided with appropriate control
procedures implemented but in case they are still not prevented, mitigation actions
can be taken based on the level of severity such that high severity risks would be
tackled on priority.
The company should create a culture of security by embedding security
considerations in all its operations such that security risks are better prevented than
mitigated leaving company with lower probability of facing any major problems.
Conclusion
This paper was written to explore the current security posture of VIC upon studying its
security framework that is implemented in the organization. The paper explored the ideas of
unintended risks, deliberate risks, and uncertainties. It also identified various types of the
security risks that the company can face and identified their ranking based on the security of
each of the risks. It was found that there are a number of risk likelihood forming factors that
11
Based on the study of risks and uncertainties that are likely to be faced by VIC organization
while managing its security framework, certain recommendations can be made for the
company for enhancing its security posture such as:
The company can outsource its security and risk management to a third party which
would save on the cost of security personnel, management as well as provide them
access to an expertise of the security expert consultancy.
The company can provide training to the staff on the security frameworks and
unintentional risks such that the probability of posing such risks can be reduced with
the increased awareness in the staff
The company should keep its security systems updated with the latest happening such
that latest threats can be tackled for which the security audit can be conducted yearly
to identify loopholes for updating
A regular and monitoring of the security systems and the risk register must be done so
that it can be ensured that security systems are working as expected and in case of
problems, they can be resolved fast.
A number of different factors can be used for the assessment of risks for each type of
risk such that the severity of each risk can be known and accordingly a plan for
managing risks can be made including mitigation and control strategies.
The risks with medium level of the severity must be avoided with appropriate control
procedures implemented but in case they are still not prevented, mitigation actions
can be taken based on the level of severity such that high severity risks would be
tackled on priority.
The company should create a culture of security by embedding security
considerations in all its operations such that security risks are better prevented than
mitigated leaving company with lower probability of facing any major problems.
Conclusion
This paper was written to explore the current security posture of VIC upon studying its
security framework that is implemented in the organization. The paper explored the ideas of
unintended risks, deliberate risks, and uncertainties. It also identified various types of the
security risks that the company can face and identified their ranking based on the security of
each of the risks. It was found that there are a number of risk likelihood forming factors that
11

can contribute to the severity of risk such as threat agent factors like skill, motivation,
opportunity and size of threat agent, vulnerability factors like ease of discovery or
exploration, awareness of user, and intrusion detection capabilities. Some impact factors were
also identified including technical impact factors like loss of confidentiality, integrity,
availability or accountability and business impact factors like financial damage, reputation
damage, non-compliance and privacy violation. Based on these insights obtained in the study,
certain recommendations were made for VIC such as embedding of security considerations in
all business processes, outsourcing of security and risk management systems to a third party
service provider, and so on.
12
opportunity and size of threat agent, vulnerability factors like ease of discovery or
exploration, awareness of user, and intrusion detection capabilities. Some impact factors were
also identified including technical impact factors like loss of confidentiality, integrity,
availability or accountability and business impact factors like financial damage, reputation
damage, non-compliance and privacy violation. Based on these insights obtained in the study,
certain recommendations were made for VIC such as embedding of security considerations in
all business processes, outsourcing of security and risk management systems to a third party
service provider, and so on.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





