Computer Network Concepts: VDI, Wi-Fi, and IP Subnetting Explained
VerifiedAdded on 2020/01/23
|25
|5916
|39
Homework Assignment
AI Summary
This assignment delves into crucial aspects of computer networking, presenting a comprehensive analysis of Virtual Desktop Infrastructure (VDI), Wi-Fi scaling, and IP subnetting. Task A1 provides a comparative analysis of VDI, exploring its advantages and disadvantages by examining its impact on server infrastructure, equipment costs, and administrative overhead. Task A2 investigates the practical limitations of Wi-Fi network scaling, considering factors like access point capacity, the impact of numerous connected devices, and potential performance degradation due to radio interference and overheating. Finally, Task A3 focuses on IP subnetting, explaining the underlying concepts and providing a step-by-step guide to understanding and configuring IP subnets, including an explanation of IP addresses, subnet masks, and network interface cards, and their role in organizing and managing network resources. The assignment concludes with Task B1, which highlights the importance of hierarchical network design for structured network environments, contrasting it with unstructured, or 'hide ball' network topologies, and emphasizing how hierarchical designs improve network efficiency and reduce costs.

Task A1:
Numerous associations keep on running Windows XP on numerous or the greater part of their
desktop PCs, either on the grounds that relocation commonly requires expensive equipment
updates, tedious exchanges of settings, and client retraining, or on the grounds that there's
basically no convincing motivation to move clients to another OS and the new application
programming that accompanies it. At times, both supports apply. In any case, when you consider
that Microsoft has effectively quit issuing non-security hotfixes for Windows XP and will end all
support for the OS in 2014, that system won't be legitimate for any longer.
Virtual desktop base (VDI) uses server equipment to run desktop working frameworks and
application programming inside a virtual machine. Clients get to these virtual desktops utilizing
their current PCs. This not just disposes of the requirement for workstation equipment redesigns,
additionally empowers the client to switch between working situations, for example, Windows
XP and Windows 7.
Besides, renders regulatory and administration assignments much less demanding, in light of the
fact that each connected workstation can utilize similar picture. Introduce OS and application
programming upgrades and fixes to the one picture, and each desktop framework utilizing that
picture is consequently redesigned and fixed. VDI offers clear advantages, however there are two
sides to each coin. Here's a brief take a gander at the advantages and disadvantages of utilizing
virtual desktop framework:
Each desktop client can use similar picture.
Star: Having every client use similar picture - the working framework and the introduced
applications decreases managerial and bolster costs.
Numerous associations keep on running Windows XP on numerous or the greater part of their
desktop PCs, either on the grounds that relocation commonly requires expensive equipment
updates, tedious exchanges of settings, and client retraining, or on the grounds that there's
basically no convincing motivation to move clients to another OS and the new application
programming that accompanies it. At times, both supports apply. In any case, when you consider
that Microsoft has effectively quit issuing non-security hotfixes for Windows XP and will end all
support for the OS in 2014, that system won't be legitimate for any longer.
Virtual desktop base (VDI) uses server equipment to run desktop working frameworks and
application programming inside a virtual machine. Clients get to these virtual desktops utilizing
their current PCs. This not just disposes of the requirement for workstation equipment redesigns,
additionally empowers the client to switch between working situations, for example, Windows
XP and Windows 7.
Besides, renders regulatory and administration assignments much less demanding, in light of the
fact that each connected workstation can utilize similar picture. Introduce OS and application
programming upgrades and fixes to the one picture, and each desktop framework utilizing that
picture is consequently redesigned and fixed. VDI offers clear advantages, however there are two
sides to each coin. Here's a brief take a gander at the advantages and disadvantages of utilizing
virtual desktop framework:
Each desktop client can use similar picture.
Star: Having every client use similar picture - the working framework and the introduced
applications decreases managerial and bolster costs.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Con: You'll require a novel picture for every client who requires an alternate arrangement of
uses, needs to spare individual settings, or requires the opportunity to introduce their own
applications. This will quickly increase stockpiling utilization on the VDI server.
Handling moves from individual workstations to a VDI server.
Genius: There's no compelling reason to overhaul various PCs to meet the new OS's base
equipment necessities.
Con: VDI will require a noteworthy interest in server equipment, and potentially away and
organize foundation. The aggregate cost of the server equipment, stockpiling, and system gear
may surpass that of acquiring a fundamental PC for every client.
Equipment expenses can be all the more effectively overseen, since nearly everything will
live in the server farm.
Master: Instead of purchasing a pile of PCs that will be scattered around the workplace - or even
outside the workplace in case you're supporting a versatile workforce or representatives who
work remotely- - you'll gain one premium framework with repetitive power supplies, an UPS,
superior stockpiling, and high-data transfer capacity organizing that will convey skilled
equipment to all clients similarly.
Con: Procuring one major server implies an expansive introductory expense, versus economical
PCs that can be obtained in stages or overhauled a couple at once. In the event that that one
server goes down, each client depending on that machine will be not able work. On the off
chance that a solitary PC goes down, stand out client is affected.
Keeping up a solitary OS picture can lessen administration and bolster costs.
Master: Install applications, patches, and drivers once, and each client depending on that picture
profits by the overhaul.
uses, needs to spare individual settings, or requires the opportunity to introduce their own
applications. This will quickly increase stockpiling utilization on the VDI server.
Handling moves from individual workstations to a VDI server.
Genius: There's no compelling reason to overhaul various PCs to meet the new OS's base
equipment necessities.
Con: VDI will require a noteworthy interest in server equipment, and potentially away and
organize foundation. The aggregate cost of the server equipment, stockpiling, and system gear
may surpass that of acquiring a fundamental PC for every client.
Equipment expenses can be all the more effectively overseen, since nearly everything will
live in the server farm.
Master: Instead of purchasing a pile of PCs that will be scattered around the workplace - or even
outside the workplace in case you're supporting a versatile workforce or representatives who
work remotely- - you'll gain one premium framework with repetitive power supplies, an UPS,
superior stockpiling, and high-data transfer capacity organizing that will convey skilled
equipment to all clients similarly.
Con: Procuring one major server implies an expansive introductory expense, versus economical
PCs that can be obtained in stages or overhauled a couple at once. In the event that that one
server goes down, each client depending on that machine will be not able work. On the off
chance that a solitary PC goes down, stand out client is affected.
Keeping up a solitary OS picture can lessen administration and bolster costs.
Master: Install applications, patches, and drivers once, and each client depending on that picture
profits by the overhaul.

Con: Administrators should take in the VDI programming's capacities and restrictions. Obliging
clients who require novel applications or their own personalization settings can bring about
picture multiplication, which can wind up being more hard to oversee than working separate
workstations.
When you experience issues, you'll for the most part have only one framework to
investigate.
Star: Problems can by and large be determined from inside the server farm; there's no compelling
reason to head out to the real PCs. Since pictures can normally be gotten to from any associated
workstation, a client encountering equipment inconvenience on their standard PC can basically
go to another workstation and get to their information and applications.
Con: Server-side issues can influence numerous clients - everybody utilizing that server or that
picture. Consequently, it's a smart thought to set up repetitive servers as a safeguard.
clients who require novel applications or their own personalization settings can bring about
picture multiplication, which can wind up being more hard to oversee than working separate
workstations.
When you experience issues, you'll for the most part have only one framework to
investigate.
Star: Problems can by and large be determined from inside the server farm; there's no compelling
reason to head out to the real PCs. Since pictures can normally be gotten to from any associated
workstation, a client encountering equipment inconvenience on their standard PC can basically
go to another workstation and get to their information and applications.
Con: Server-side issues can influence numerous clients - everybody utilizing that server or that
picture. Consequently, it's a smart thought to set up repetitive servers as a safeguard.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Task A2:
PCs and different gadgets on a Wi-Fi must share a limited limit of assets. As far as possible for
what number of gadgets can interface with and utilize a remote system rely on upon different
variables.
What number of Access Points?
Most home systems and open Wi-Fi hotspots work with a solitary remote get to point (a
broadband switch on account of home systems administration). Then again, bigger business PC
systems introduce different get to focuses to extend the remote system's scope to a much bigger
physical zone. Every get to point has limits for the quantity of associations and measure of
system load it can deal with, yet by incorporating numerous of them into a bigger system, the
general scale can be expanded.
Hypothetical Limits of Wi-Fi Network Scaling
Numerous individual remote switches and different get to focuses bolster up to roughly 250
associated gadgets. Switches can empower a little number (for the most part somewhere around
one and four) of wired Ethernet customers with the rest associated through Wi-Fi joins.
The speed rating of get to focuses speaks to the most extreme hypothetical system data transfer
capacity they can bolster. Wi-Fi switches appraised at 300 Mbps with 100 gadgets associated, for
instance, can just offer by and large 3 Mbps to each of them. Actually, most customers just
utilize their system association sometimes, and a switch moves its accessible data transmission to
the customers that need it.
Down to earth Limits of Wi-Fi Network Scaling
Interfacing 250 gadgets to a solitary Wi-Fi get to point, while hypothetically conceivable, is not
possible by and by for a couple reasons:
PCs and different gadgets on a Wi-Fi must share a limited limit of assets. As far as possible for
what number of gadgets can interface with and utilize a remote system rely on upon different
variables.
What number of Access Points?
Most home systems and open Wi-Fi hotspots work with a solitary remote get to point (a
broadband switch on account of home systems administration). Then again, bigger business PC
systems introduce different get to focuses to extend the remote system's scope to a much bigger
physical zone. Every get to point has limits for the quantity of associations and measure of
system load it can deal with, yet by incorporating numerous of them into a bigger system, the
general scale can be expanded.
Hypothetical Limits of Wi-Fi Network Scaling
Numerous individual remote switches and different get to focuses bolster up to roughly 250
associated gadgets. Switches can empower a little number (for the most part somewhere around
one and four) of wired Ethernet customers with the rest associated through Wi-Fi joins.
The speed rating of get to focuses speaks to the most extreme hypothetical system data transfer
capacity they can bolster. Wi-Fi switches appraised at 300 Mbps with 100 gadgets associated, for
instance, can just offer by and large 3 Mbps to each of them. Actually, most customers just
utilize their system association sometimes, and a switch moves its accessible data transmission to
the customers that need it.
Down to earth Limits of Wi-Fi Network Scaling
Interfacing 250 gadgets to a solitary Wi-Fi get to point, while hypothetically conceivable, is not
possible by and by for a couple reasons:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

On home systems, all gadgets regularly share a solitary Internet association. The execution of
customers' Internet get to will begin to debase as more gadgets join the system and begin
utilizing it at the same time. Indeed, even only a modest bunch of dynamic gadgets doing video
gushing or substantial Web downloading can rapidly maximize a mutual Internet connect. Get to
focuses overheat (and quit working) when working at outrageous burdens for expanded periods,
regardless of the possibility that taking care of just nearby movement and not getting to the
Internet.
Having extensive number of Wi-Fi customers gathered in close physical closeness like a home or
office building produces critical remote flag obstruction. Radio obstruction among Wi-Fi
customers debases arranges execution (because of successive re-broadcasting of messages that
neglect to achieve their goal) and in the end causes association drops.
Some home switches incorporate an element that permits directors to control the quantity of
customers that can at the same time interface. Numerous Linksys switches, for instance, set a
default most extreme of 50 greatest customers. Brilliant overseers regularly keep a farthest point
like this set up to keep the switch and system running dependably. Introducing a second switch
or get to point on a home system can significantly convey the system stack. By adding more get
to focuses to the system, adequately any number of gadgets can be upheld (however the system
turns out to be dynamically harder to oversee).
customers' Internet get to will begin to debase as more gadgets join the system and begin
utilizing it at the same time. Indeed, even only a modest bunch of dynamic gadgets doing video
gushing or substantial Web downloading can rapidly maximize a mutual Internet connect. Get to
focuses overheat (and quit working) when working at outrageous burdens for expanded periods,
regardless of the possibility that taking care of just nearby movement and not getting to the
Internet.
Having extensive number of Wi-Fi customers gathered in close physical closeness like a home or
office building produces critical remote flag obstruction. Radio obstruction among Wi-Fi
customers debases arranges execution (because of successive re-broadcasting of messages that
neglect to achieve their goal) and in the end causes association drops.
Some home switches incorporate an element that permits directors to control the quantity of
customers that can at the same time interface. Numerous Linksys switches, for instance, set a
default most extreme of 50 greatest customers. Brilliant overseers regularly keep a farthest point
like this set up to keep the switch and system running dependably. Introducing a second switch
or get to point on a home system can significantly convey the system stack. By adding more get
to focuses to the system, adequately any number of gadgets can be upheld (however the system
turns out to be dynamically harder to oversee).

Task A3:
Understanding IP sub-netting is a major prerequisite for any geek - whether you're a coder, a
database director or the CTO. Be that as it may, as basic as the ideas seem to be, there is a
general trouble in comprehension the theme.
Here we'll break this subject into eight basic strides and help you set up the pieces together to
completely comprehend IP subnetting.
These means will give you the fundamental data required with a specific end goal to design
switches or see how IP locations are separated and how subnetting functions. You'll likewise
figure out how to arrange a fundamental home or little office organize.
A fundamental comprehension of how twofold and decimal numbers function is required. What's
more, these definitions and terms will kick you off:
IP Address: A coherent numeric delivers that is doled out to each and every PC, printer, switch,
switch or whatever other gadget that is a piece of a TCP/IP-based system
Subnet: A different and identifiable partition of an association's system, regularly organized on
one story, building or topographical area
Subnet Mask: A 32-bit number used to separate the system segment of an IP address by
partitioning the IP address into a system address and host address
Organize Interface Card (NIC): A PC equipment part that permits a PC to associate with a
system.
To comprehend why we require subnets (short for subnetwork), how about we begin right from
the earliest starting point and perceive that we have to converse with "things" on systems. Clients
need to converse with printers, email programs need to converse with servers, and each of these
"things" needs some kind of address. This is the same as a house address, however with one
Understanding IP sub-netting is a major prerequisite for any geek - whether you're a coder, a
database director or the CTO. Be that as it may, as basic as the ideas seem to be, there is a
general trouble in comprehension the theme.
Here we'll break this subject into eight basic strides and help you set up the pieces together to
completely comprehend IP subnetting.
These means will give you the fundamental data required with a specific end goal to design
switches or see how IP locations are separated and how subnetting functions. You'll likewise
figure out how to arrange a fundamental home or little office organize.
A fundamental comprehension of how twofold and decimal numbers function is required. What's
more, these definitions and terms will kick you off:
IP Address: A coherent numeric delivers that is doled out to each and every PC, printer, switch,
switch or whatever other gadget that is a piece of a TCP/IP-based system
Subnet: A different and identifiable partition of an association's system, regularly organized on
one story, building or topographical area
Subnet Mask: A 32-bit number used to separate the system segment of an IP address by
partitioning the IP address into a system address and host address
Organize Interface Card (NIC): A PC equipment part that permits a PC to associate with a
system.
To comprehend why we require subnets (short for subnetwork), how about we begin right from
the earliest starting point and perceive that we have to converse with "things" on systems. Clients
need to converse with printers, email programs need to converse with servers, and each of these
"things" needs some kind of address. This is the same as a house address, however with one
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

minor special case: the locations should be in numerical frame. It is impractical to have a gadget
on a system that has in order characters in its address like "23rd Street." Its name can be
alphanumeric - and we could make an interpretation of that name to a numeric address - however
the address itself must be numbers alone. These numbers are called IP locations, and they have
the critical capacity of making sense of the address of "things," as well as how correspondence
can happen between them. It is insufficient to simply have an address. It is important to make
sense of how a message can be sent starting with one address then onto the next. This is the place
a little association becomes an integral factor.
It is frequently important to gathering things on a system together for both hierarchical and
proficiency's purpose. For instance, suppose you have a gathering of printers in your
organization's showcasing division and an alternate group in the business workplaces. You need
to constrain the printers that every client sees to those of every division. You could achieve this
by arranging the locations of these printers into one of kind subnets. A subnet then, is a sensible
association of associated system gadgets.
Every gadget on each subnet has an address that sensibly relates it with the others on similar
subnet. This likewise keeps gadgets on one subnet from getting mistook for hosts on the other
subnet. Regarding IP tending to and subnets, these gadgets are alluded to as hosts. Along these
on a system that has in order characters in its address like "23rd Street." Its name can be
alphanumeric - and we could make an interpretation of that name to a numeric address - however
the address itself must be numbers alone. These numbers are called IP locations, and they have
the critical capacity of making sense of the address of "things," as well as how correspondence
can happen between them. It is insufficient to simply have an address. It is important to make
sense of how a message can be sent starting with one address then onto the next. This is the place
a little association becomes an integral factor.
It is frequently important to gathering things on a system together for both hierarchical and
proficiency's purpose. For instance, suppose you have a gathering of printers in your
organization's showcasing division and an alternate group in the business workplaces. You need
to constrain the printers that every client sees to those of every division. You could achieve this
by arranging the locations of these printers into one of kind subnets. A subnet then, is a sensible
association of associated system gadgets.
Every gadget on each subnet has an address that sensibly relates it with the others on similar
subnet. This likewise keeps gadgets on one subnet from getting mistook for hosts on the other
subnet. Regarding IP tending to and subnets, these gadgets are alluded to as hosts. Along these
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
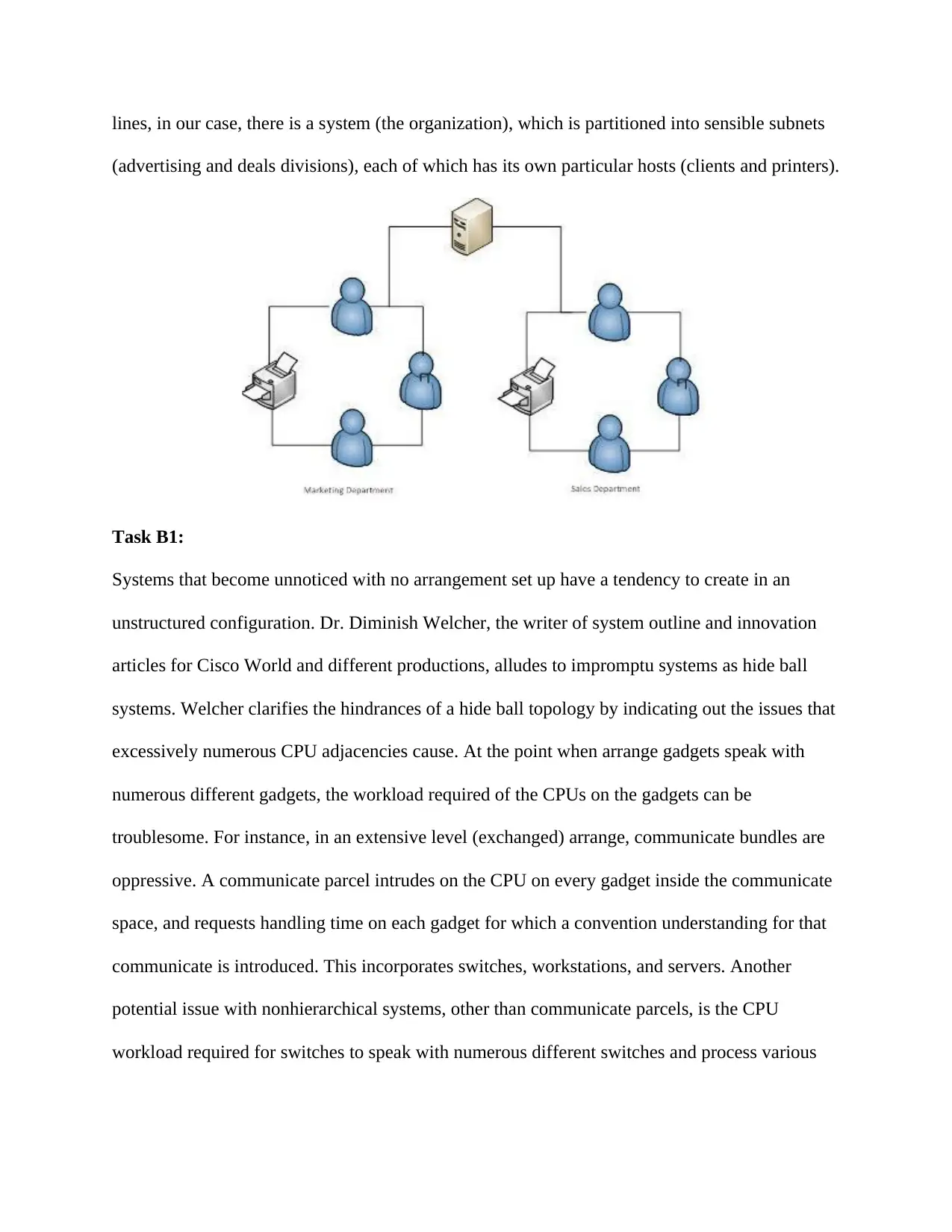
lines, in our case, there is a system (the organization), which is partitioned into sensible subnets
(advertising and deals divisions), each of which has its own particular hosts (clients and printers).
Task B1:
Systems that become unnoticed with no arrangement set up have a tendency to create in an
unstructured configuration. Dr. Diminish Welcher, the writer of system outline and innovation
articles for Cisco World and different productions, alludes to impromptu systems as hide ball
systems. Welcher clarifies the hindrances of a hide ball topology by indicating out the issues that
excessively numerous CPU adjacencies cause. At the point when arrange gadgets speak with
numerous different gadgets, the workload required of the CPUs on the gadgets can be
troublesome. For instance, in an extensive level (exchanged) arrange, communicate bundles are
oppressive. A communicate parcel intrudes on the CPU on every gadget inside the communicate
space, and requests handling time on each gadget for which a convention understanding for that
communicate is introduced. This incorporates switches, workstations, and servers. Another
potential issue with nonhierarchical systems, other than communicate parcels, is the CPU
workload required for switches to speak with numerous different switches and process various
(advertising and deals divisions), each of which has its own particular hosts (clients and printers).
Task B1:
Systems that become unnoticed with no arrangement set up have a tendency to create in an
unstructured configuration. Dr. Diminish Welcher, the writer of system outline and innovation
articles for Cisco World and different productions, alludes to impromptu systems as hide ball
systems. Welcher clarifies the hindrances of a hide ball topology by indicating out the issues that
excessively numerous CPU adjacencies cause. At the point when arrange gadgets speak with
numerous different gadgets, the workload required of the CPUs on the gadgets can be
troublesome. For instance, in an extensive level (exchanged) arrange, communicate bundles are
oppressive. A communicate parcel intrudes on the CPU on every gadget inside the communicate
space, and requests handling time on each gadget for which a convention understanding for that
communicate is introduced. This incorporates switches, workstations, and servers. Another
potential issue with nonhierarchical systems, other than communicate parcels, is the CPU
workload required for switches to speak with numerous different switches and process various

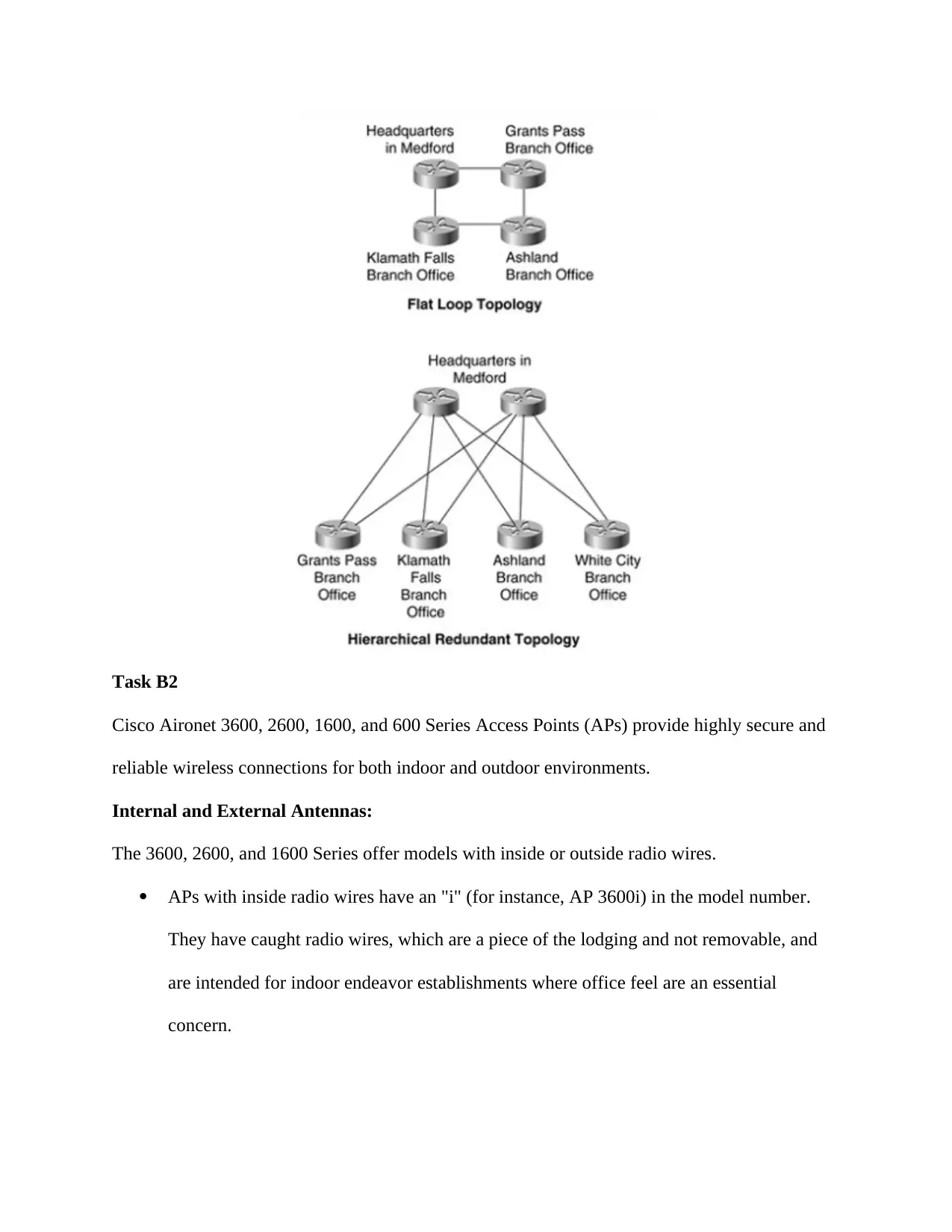
course promotions. A various leveled arrange outline procedure gives you a chance to plan a
secluded topology that confines the quantity of imparting switches.
Utilizing a progressive model can help you minimize costs. You can buy the fitting
internetworking gadgets for every layer of the chain of importance, along these lines abstaining
from burning through cash on superfluous components for a layer. Likewise, the measured way
of the progressive outline show empowers exact scope organization inside every layer of the
chain of importance, in this way lessening squandered transmission capacity. Arrange
administration obligation and system administration frameworks can be dispersed to the diverse
layers of a secluded system design to control administration costs. Measured quality gives you a
chance to keep every plan component straightforward and straightforward. Effortlessness
minimizes the requirement for broad preparing for system operations work force and speeds up
the execution of an outline. Testing a system outline is made simple in light of the fact that there
is clear usefulness at every layer. Blame separation is enhanced on the grounds that system
professionals can undoubtedly perceive the move indicates in the system help them disconnect
conceivable disappointment focuses. Various leveled plan encourages changes. As components
in a system require change, the cost of making a redesign is contained to a little subset of the
general system. In substantial level or fit system designs, changes tend to affect an expansive
number of frameworks. Supplanting one gadget can influence various systems in view of the
mind boggling interconnections.
At the point when adaptability is a noteworthy objective, a various leveled topology is prescribed
on the grounds that measured quality in an outline empowers making plan components that can
be reproduced as the system develops. Since every occurrence of a module is steady,
development is anything but difficult to arrange and actualize. For instance, arranging a grounds
secluded topology that confines the quantity of imparting switches.
Utilizing a progressive model can help you minimize costs. You can buy the fitting
internetworking gadgets for every layer of the chain of importance, along these lines abstaining
from burning through cash on superfluous components for a layer. Likewise, the measured way
of the progressive outline show empowers exact scope organization inside every layer of the
chain of importance, in this way lessening squandered transmission capacity. Arrange
administration obligation and system administration frameworks can be dispersed to the diverse
layers of a secluded system design to control administration costs. Measured quality gives you a
chance to keep every plan component straightforward and straightforward. Effortlessness
minimizes the requirement for broad preparing for system operations work force and speeds up
the execution of an outline. Testing a system outline is made simple in light of the fact that there
is clear usefulness at every layer. Blame separation is enhanced on the grounds that system
professionals can undoubtedly perceive the move indicates in the system help them disconnect
conceivable disappointment focuses. Various leveled plan encourages changes. As components
in a system require change, the cost of making a redesign is contained to a little subset of the
general system. In substantial level or fit system designs, changes tend to affect an expansive
number of frameworks. Supplanting one gadget can influence various systems in view of the
mind boggling interconnections.
At the point when adaptability is a noteworthy objective, a various leveled topology is prescribed
on the grounds that measured quality in an outline empowers making plan components that can
be reproduced as the system develops. Since every occurrence of a module is steady,
development is anything but difficult to arrange and actualize. For instance, arranging a grounds
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

organize for another site may just involve repeating a current grounds organize plan. Today's
quick focalizing directing conventions were intended for progressive topologies. Course
rundown, which Chapter 6, "Planning Models for Addressing and Naming," covers in more
detail, is encouraged by various leveled arrange outline. To control steering CPU overhead and
data transfer capacity utilization, particular various leveled topologies ought to be utilized with
so much conventions as Open Shortest Path First (OSPF), Intermediate System-to-Intermediate
System (IS-IS), Border Gateway Protocol (BGP), and Enhanced Interior Gateway Routing
Protocol (Enhanced IGRP).
Level Versus Hierarchical Topologies
A level system topology is sufficient for little systems. With a level system plan, there is no
order. Each internetworking gadget has basically similar employment, and the system is not
isolated into layers or modules. A level system topology is anything but difficult to outline and
execute, and it is anything but difficult to keep up, the length of the system stays little. At the
point when the system develops, in any case, a level system is undesirable. The absence of
progression makes investigating troublesome. As opposed to having the capacity to move
investigating endeavors in only one zone of the system, you may need to assess the whole
system.
Level WAN Topologies A wide-range arrange (WAN) for a little organization can comprise of a
couple destinations associated in a circle. Every site has a WAN switch that interfaces with two
other adjoining destinations by means of indicate point joins. For whatever length of time that
the WAN is little (a couple locales), steering conventions can focalize rapidly, and
correspondence with some other site can recuperate when a connection fizzles. (For whatever
quick focalizing directing conventions were intended for progressive topologies. Course
rundown, which Chapter 6, "Planning Models for Addressing and Naming," covers in more
detail, is encouraged by various leveled arrange outline. To control steering CPU overhead and
data transfer capacity utilization, particular various leveled topologies ought to be utilized with
so much conventions as Open Shortest Path First (OSPF), Intermediate System-to-Intermediate
System (IS-IS), Border Gateway Protocol (BGP), and Enhanced Interior Gateway Routing
Protocol (Enhanced IGRP).
Level Versus Hierarchical Topologies
A level system topology is sufficient for little systems. With a level system plan, there is no
order. Each internetworking gadget has basically similar employment, and the system is not
isolated into layers or modules. A level system topology is anything but difficult to outline and
execute, and it is anything but difficult to keep up, the length of the system stays little. At the
point when the system develops, in any case, a level system is undesirable. The absence of
progression makes investigating troublesome. As opposed to having the capacity to move
investigating endeavors in only one zone of the system, you may need to assess the whole
system.
Level WAN Topologies A wide-range arrange (WAN) for a little organization can comprise of a
couple destinations associated in a circle. Every site has a WAN switch that interfaces with two
other adjoining destinations by means of indicate point joins. For whatever length of time that
the WAN is little (a couple locales), steering conventions can focalize rapidly, and
correspondence with some other site can recuperate when a connection fizzles. (For whatever
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

length of time that stand out connection comes up short, correspondence recuperates. At the
point when more than one connection comes up short, a few locales are secluded from others.)
Level LAN Topologies In the early and mid-1990s, an average outline for a LAN was PCs and
servers joined to one or more center points in a level topology. The PCs and servers actualized a
media-get to control process, for example, token passing or transporter sense various access with
crash location (CSMA/CD) to control access to the mutual data transfer capacity. The gadgets
were all part of similar transmission capacity space and had the capacity to adversely influence
deferral and throughput for different gadgets. Nowadays, organize creators generally prescribe
joining the PCs and servers to information interface (Layer 2) switches rather than center points.
For this situation, the system is divided into little data transmission spaces so that a set number of
gadgets vie for transfer speed at any one time. Switches forward communicate outlines out all
ports. Switches, then again, fragment systems into particular communicate spaces. A solitary
communicate space ought to be restricted to a couple of hundred gadgets so gadgets are not
overpowered by the assignment of handling communicate movement. By bringing chain of
importance into a system outline by including switches, communicate radiation is abridged. With
a various leveled outline, internetworking gadgets can be sent to carry out the occupation they do
best. Switches can be added to a grounds arrange outline to seclude communicate activity. Top
of the line switches can be sent to augment transfer speed for high-activity applications, and low-
end switches can be utilized when basic, reasonable get to is required. Augmenting general
execution by modularizing the assignments required of internetworking gadgets is one of the
numerous advantages of utilizing a progressive plan demonstrate.
point when more than one connection comes up short, a few locales are secluded from others.)
Level LAN Topologies In the early and mid-1990s, an average outline for a LAN was PCs and
servers joined to one or more center points in a level topology. The PCs and servers actualized a
media-get to control process, for example, token passing or transporter sense various access with
crash location (CSMA/CD) to control access to the mutual data transfer capacity. The gadgets
were all part of similar transmission capacity space and had the capacity to adversely influence
deferral and throughput for different gadgets. Nowadays, organize creators generally prescribe
joining the PCs and servers to information interface (Layer 2) switches rather than center points.
For this situation, the system is divided into little data transmission spaces so that a set number of
gadgets vie for transfer speed at any one time. Switches forward communicate outlines out all
ports. Switches, then again, fragment systems into particular communicate spaces. A solitary
communicate space ought to be restricted to a couple of hundred gadgets so gadgets are not
overpowered by the assignment of handling communicate movement. By bringing chain of
importance into a system outline by including switches, communicate radiation is abridged. With
a various leveled outline, internetworking gadgets can be sent to carry out the occupation they do
best. Switches can be added to a grounds arrange outline to seclude communicate activity. Top
of the line switches can be sent to augment transfer speed for high-activity applications, and low-
end switches can be utilized when basic, reasonable get to is required. Augmenting general
execution by modularizing the assignments required of internetworking gadgets is one of the
numerous advantages of utilizing a progressive plan demonstrate.
Task B2
Cisco Aironet 3600, 2600, 1600, and 600 Series Access Points (APs) provide highly secure and
reliable wireless connections for both indoor and outdoor environments.
Internal and External Antennas:
The 3600, 2600, and 1600 Series offer models with inside or outside radio wires.
APs with inside radio wires have an "i" (for instance, AP 3600i) in the model number.
They have caught radio wires, which are a piece of the lodging and not removable, and
are intended for indoor endeavor establishments where office feel are an essential
concern.
Cisco Aironet 3600, 2600, 1600, and 600 Series Access Points (APs) provide highly secure and
reliable wireless connections for both indoor and outdoor environments.
Internal and External Antennas:
The 3600, 2600, and 1600 Series offer models with inside or outside radio wires.
APs with inside radio wires have an "i" (for instance, AP 3600i) in the model number.
They have caught radio wires, which are a piece of the lodging and not removable, and
are intended for indoor endeavor establishments where office feel are an essential
concern.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 25
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
