Role of Virtual Networks in Hardware Networking Functions Thesis
VerifiedAdded on 2022/10/01
|16
|770
|20
Thesis and Dissertation
AI Summary
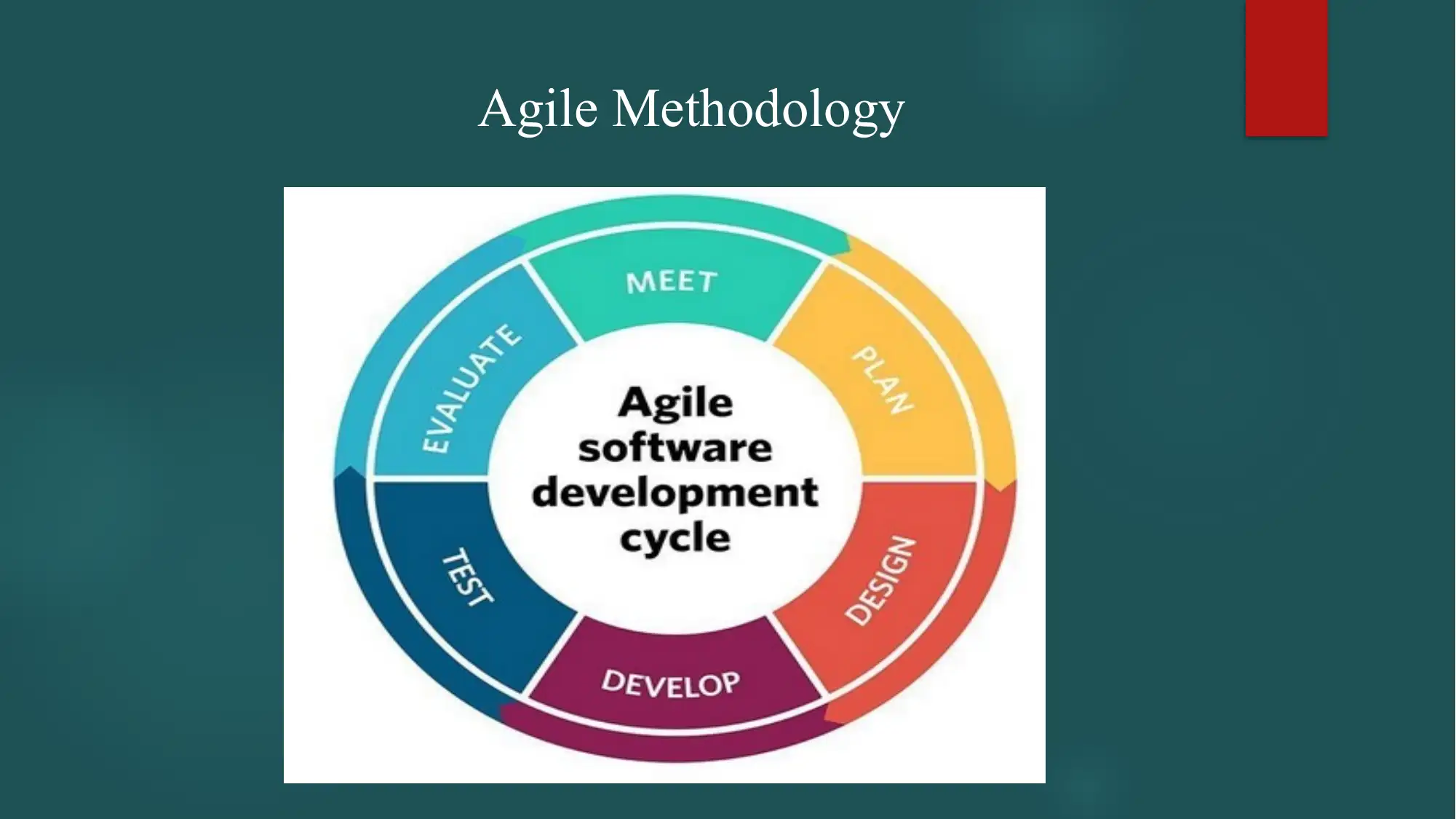
This thesis explores the role of virtual networks in hardware networking, focusing on security breaches and countermeasures. The study begins with an introduction to virtual networking, its advantages, and its growing importance. A literature review examines existing research on the subject, followed by the aims and objectives of the research, which include defining how virtual machines connect and communicate, identifying security risks, and developing solutions to protect connected devices. The research methodology, using the Agile method, involves qualitative and quantitative research, data collection from various sources, and experimental setups to analyze hardware functionalities. The thesis details the data analysis process, experimental design, and system testing, including the identification of vulnerabilities and the implementation of countermeasures. The results are presented, discussed, and used to formulate conclusions and recommendations. The research emphasizes the need for control measures, risk analysis, and the analysis of secure virtual network hardware devices. The thesis concludes with a discussion on data collection, analysis, and the importance of resolving research problems, fully testing systems, and implementing effective countermeasures to address threats and security breaches.
1 out of 16


















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)