VPN Technologies: Securing Communications on the Internet Report
VerifiedAdded on 2021/04/24
|9
|2285
|38
Report
AI Summary
This report provides a comprehensive overview of Virtual Private Networks (VPNs), explaining their function in securing communications over the internet. It details how VPNs create encrypted connections to enhance privacy and security, using tunneling mechanisms to protect data transmission. The report distinguishes VPNs from Virtual Network Computing (VNC), highlighting their different purposes: VPNs for secure network connections and VNC for remote desktop control. It also explores the concept of remote access technology, discussing its components such as Network Access Servers (NAS) and client software, and its role in enabling access to networks from a distance. Furthermore, it covers the setup of VPNs, detailing the roles of client software and the involvement of Enterprise Service Providers (ESP). The report concludes by emphasizing the importance of VPNs for maintaining anonymity and securing vital data, especially in an era where privacy is a major concern. All this and more is available on Desklib.

Running head: VIRTUAL PRIVATE NETWORK
Virtual Private Network
Name of the Student
Name of the University
Author’s note:
Virtual Private Network
Name of the Student
Name of the University
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
VIRTUAL PRIVATE NETWORK
1.
(a) Explanation of VPN and use of VPN in securing communications on the Internet
A Virtual Private Network (VPN) is a form of technology that is able to create a
secure and encrypted connection over a network that is expected to be less secure. This
technology is meant to add a layer of privacy and security to public and private networks.
VPN technology is constructed using public wires in order to connect to regional offices or
distant users to the private and internal network of a company (Jain & Paul, 2013).
The privacy issues are increased with the help of a VPN as because the initials of the
user’s IP address is substituted with one from the provider of the VPN. This method allows a
user to achieve an IP address from any gateway. For example, with the help of VPN, a person
who is living in San Francisco may appear to reside in Amsterdam or any other gateway city.
A VPN protocol makes use of a set of instructions that are used to convey a secure encrypted
connection between computers. Such type of protocols is mainly supported by the use of
commercial VPN services. The most important of these protocols are PPTP, OpenVPN,
SSTP, L2TP/IPSec and IKEv2 (Modi et al., 2013).
The VPN makes use of encryption technology in order to provide confidentiality of
data. Once the system is connected to the internet, the VPN technology makes use of the
mechanism of tunneling. The mechanism of tunneling can be used to compress the encrypted
information and data into a protected tunnel that has open read headers, which can cross a
public network. The information packets that are delivered over a public network cannot be
read without proper keys of decryption (Chung et al., 2013). This can ensure that the
important data is not changed or revealed during the transmission of data.
As internet connections have become faster, reliable and widely available, the use of
VPNs has continuously expanded. Many large companies have shifted their remote office
VIRTUAL PRIVATE NETWORK
1.
(a) Explanation of VPN and use of VPN in securing communications on the Internet
A Virtual Private Network (VPN) is a form of technology that is able to create a
secure and encrypted connection over a network that is expected to be less secure. This
technology is meant to add a layer of privacy and security to public and private networks.
VPN technology is constructed using public wires in order to connect to regional offices or
distant users to the private and internal network of a company (Jain & Paul, 2013).
The privacy issues are increased with the help of a VPN as because the initials of the
user’s IP address is substituted with one from the provider of the VPN. This method allows a
user to achieve an IP address from any gateway. For example, with the help of VPN, a person
who is living in San Francisco may appear to reside in Amsterdam or any other gateway city.
A VPN protocol makes use of a set of instructions that are used to convey a secure encrypted
connection between computers. Such type of protocols is mainly supported by the use of
commercial VPN services. The most important of these protocols are PPTP, OpenVPN,
SSTP, L2TP/IPSec and IKEv2 (Modi et al., 2013).
The VPN makes use of encryption technology in order to provide confidentiality of
data. Once the system is connected to the internet, the VPN technology makes use of the
mechanism of tunneling. The mechanism of tunneling can be used to compress the encrypted
information and data into a protected tunnel that has open read headers, which can cross a
public network. The information packets that are delivered over a public network cannot be
read without proper keys of decryption (Chung et al., 2013). This can ensure that the
important data is not changed or revealed during the transmission of data.
As internet connections have become faster, reliable and widely available, the use of
VPNs has continuously expanded. Many large companies have shifted their remote office
2
VIRTUAL PRIVATE NETWORK
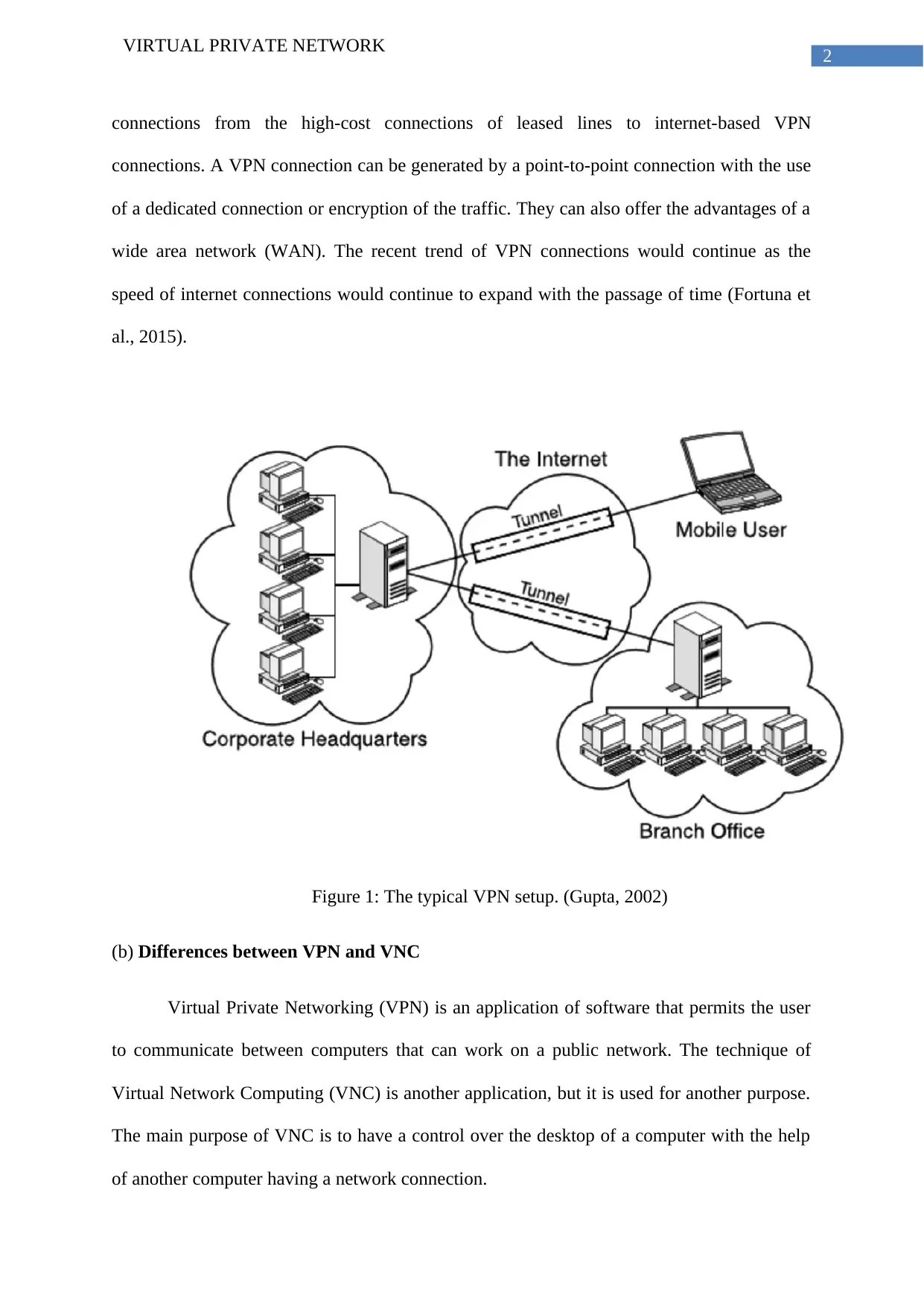
connections from the high-cost connections of leased lines to internet-based VPN
connections. A VPN connection can be generated by a point-to-point connection with the use
of a dedicated connection or encryption of the traffic. They can also offer the advantages of a
wide area network (WAN). The recent trend of VPN connections would continue as the
speed of internet connections would continue to expand with the passage of time (Fortuna et
al., 2015).
Figure 1: The typical VPN setup. (Gupta, 2002)
(b) Differences between VPN and VNC
Virtual Private Networking (VPN) is an application of software that permits the user
to communicate between computers that can work on a public network. The technique of
Virtual Network Computing (VNC) is another application, but it is used for another purpose.
The main purpose of VNC is to have a control over the desktop of a computer with the help
of another computer having a network connection.
VIRTUAL PRIVATE NETWORK
connections from the high-cost connections of leased lines to internet-based VPN
connections. A VPN connection can be generated by a point-to-point connection with the use
of a dedicated connection or encryption of the traffic. They can also offer the advantages of a
wide area network (WAN). The recent trend of VPN connections would continue as the
speed of internet connections would continue to expand with the passage of time (Fortuna et
al., 2015).
Figure 1: The typical VPN setup. (Gupta, 2002)
(b) Differences between VPN and VNC
Virtual Private Networking (VPN) is an application of software that permits the user
to communicate between computers that can work on a public network. The technique of
Virtual Network Computing (VNC) is another application, but it is used for another purpose.
The main purpose of VNC is to have a control over the desktop of a computer with the help
of another computer having a network connection.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
VIRTUAL PRIVATE NETWORK
Although the VPN is usually referred to a secure method of the transmission of a
network, the VNC is merely related to the administration of a network. VPN allows a user to
connect with a public network in a secured manner by using the same switch but VNC allows
the control of a desktop from any other computer (Sathiaseelan et al., 2014).
Though VPNs are much more complicated during the setup process than VNC
connections, yet they allow the users to use local applications on a remote network. The task
of VPNs is to enable VNC connections to desktop computers with the help of remote
networks. It thus makes sure that the servers are not kept bare to the public internet. This
helps in improving the security with the help of VPN and the use of a local client of VNC in
order to access desktops (Sharkh et al., 2013). VPN can allow a user to transfer files from a
remote folder to a local folder, print the documents on a remote server to a local printer, but a
VNC can allow accessing a primary remote computer.
In the recent times, the major issue of concern is privacy. The VPN is an efficient way
in order to maintain anonymity and privacy. The VPNs is able to encrypt the traffic between
the personal computer of a user and the entry point of a VPN. They can also be helpful when
a user would be avoiding online censorship or they are using an IP address, which is
indirectly associated. VNC could be a great factor for individual persons and businesses who
would be willing to access a remote computer but a VPN is good for those people who wish
to encrypt and secure their vital files and data (Selvi, Sankar & Umarani, 2014).
2. The Concept of Remote Access
The company can make use of the Remote Access Technology in order to gain
accessibility to a network or computer from a longer distance. In the corporate sector, persons
who are working at offices, home-workers and people who travel might need to gain access
to the office network. Internet Service Provider (ISP) can help users to get an access to the
VIRTUAL PRIVATE NETWORK
Although the VPN is usually referred to a secure method of the transmission of a
network, the VNC is merely related to the administration of a network. VPN allows a user to
connect with a public network in a secured manner by using the same switch but VNC allows
the control of a desktop from any other computer (Sathiaseelan et al., 2014).
Though VPNs are much more complicated during the setup process than VNC
connections, yet they allow the users to use local applications on a remote network. The task
of VPNs is to enable VNC connections to desktop computers with the help of remote
networks. It thus makes sure that the servers are not kept bare to the public internet. This
helps in improving the security with the help of VPN and the use of a local client of VNC in
order to access desktops (Sharkh et al., 2013). VPN can allow a user to transfer files from a
remote folder to a local folder, print the documents on a remote server to a local printer, but a
VNC can allow accessing a primary remote computer.
In the recent times, the major issue of concern is privacy. The VPN is an efficient way
in order to maintain anonymity and privacy. The VPNs is able to encrypt the traffic between
the personal computer of a user and the entry point of a VPN. They can also be helpful when
a user would be avoiding online censorship or they are using an IP address, which is
indirectly associated. VNC could be a great factor for individual persons and businesses who
would be willing to access a remote computer but a VPN is good for those people who wish
to encrypt and secure their vital files and data (Selvi, Sankar & Umarani, 2014).
2. The Concept of Remote Access
The company can make use of the Remote Access Technology in order to gain
accessibility to a network or computer from a longer distance. In the corporate sector, persons
who are working at offices, home-workers and people who travel might need to gain access
to the office network. Internet Service Provider (ISP) can help users to get an access to the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
VIRTUAL PRIVATE NETWORK
internet with the help of the remote access technology (Maiti, Maxwell & Kist, 2014). The
most common method of remote access is through a dial-up connection with the help of a
notebook, desktop or even with the help of a handheld modem over telephone lines.
The remote access technology can permit files to be read and written to the target
without the capability of remote computer. This technology provides a remote login to the
system. It also helps in the accessibility of the files across WANs. A VPN involves the
software of the client to be present on the system of the host and the VPN server that are
installed on the target network (Kist et al., 2014).
The technology is makes use of a dedicated line between a local network and the
computer. The Integrated Services Digital Network (ISDN) is the most commonly used
method of the remote access technology. This can combine dial-up connection with faster
rates of data. Other technologies that offer different possibilities for remote access are cable,
wireless, Digital Subscriber Line (DSL) and modem.
VIRTUAL PRIVATE NETWORK
internet with the help of the remote access technology (Maiti, Maxwell & Kist, 2014). The
most common method of remote access is through a dial-up connection with the help of a
notebook, desktop or even with the help of a handheld modem over telephone lines.
The remote access technology can permit files to be read and written to the target
without the capability of remote computer. This technology provides a remote login to the
system. It also helps in the accessibility of the files across WANs. A VPN involves the
software of the client to be present on the system of the host and the VPN server that are
installed on the target network (Kist et al., 2014).
The technology is makes use of a dedicated line between a local network and the
computer. The Integrated Services Digital Network (ISDN) is the most commonly used
method of the remote access technology. This can combine dial-up connection with faster
rates of data. Other technologies that offer different possibilities for remote access are cable,
wireless, Digital Subscriber Line (DSL) and modem.
5
VIRTUAL PRIVATE NETWORK
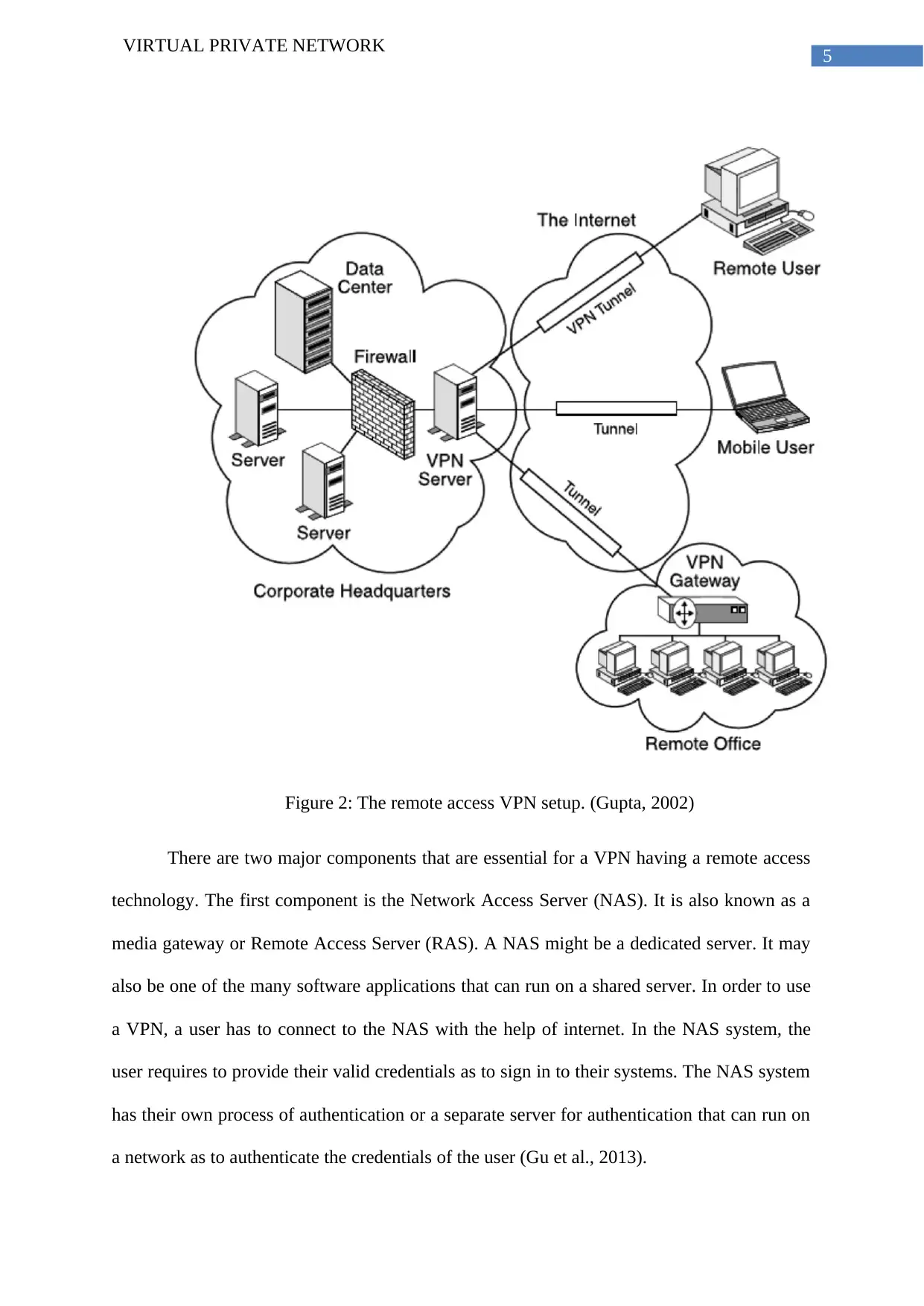
Figure 2: The remote access VPN setup. (Gupta, 2002)
There are two major components that are essential for a VPN having a remote access
technology. The first component is the Network Access Server (NAS). It is also known as a
media gateway or Remote Access Server (RAS). A NAS might be a dedicated server. It may
also be one of the many software applications that can run on a shared server. In order to use
a VPN, a user has to connect to the NAS with the help of internet. In the NAS system, the
user requires to provide their valid credentials as to sign in to their systems. The NAS system
has their own process of authentication or a separate server for authentication that can run on
a network as to authenticate the credentials of the user (Gu et al., 2013).
VIRTUAL PRIVATE NETWORK
Figure 2: The remote access VPN setup. (Gupta, 2002)
There are two major components that are essential for a VPN having a remote access
technology. The first component is the Network Access Server (NAS). It is also known as a
media gateway or Remote Access Server (RAS). A NAS might be a dedicated server. It may
also be one of the many software applications that can run on a shared server. In order to use
a VPN, a user has to connect to the NAS with the help of internet. In the NAS system, the
user requires to provide their valid credentials as to sign in to their systems. The NAS system
has their own process of authentication or a separate server for authentication that can run on
a network as to authenticate the credentials of the user (Gu et al., 2013).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
VIRTUAL PRIVATE NETWORK
Another essential component of remotely accessible VPNs is a client software. In this
type of component, if an employee desires to use the VPN from their computer system, they
would require a particular software on those computer that would establish and maintain a
connection with the VPN. Nowadays some modern operating systems possess an inbuilt
system software that is capable of connecting to remote accessible VPNs although some of
the VPNs might require users to install a precise form of application. The software of the
client is set up with the help of a tunneled connection to a NAS. The user is indicated of this
activity with the help of the internet address. The client software is also responsible for
managing the required encryption in order to maintain a secure connection.
Many big businesses and large corporations that possess high knowledgeable IT staff
are often used to buying, deploy and maintain their own remote accessible VPNs. Many
businesses could easily opt to outsource their remotely accessed VPN services with the help
of an Enterprise Service Provider (ESP). The ESP can easily set up a NAS for a business and
thus try to maintain in keeping the NAS to run smoothly (Avram, 2014).
A remote access technology is the type of system and the software, which is
associated with it. It is often set up to handle those users who are seeking to gain access to a
remote network. It is sometimes referred as a server for communication. This kind of server
is often linked with a firewall server in order to safeguard the level of security. It is also able
to forward the remotely accessible request to another part of the corporate sector. The remote
access technology can contain the work with a modem pool manager such that a small group
of modems could be shared with a larger group of irregularly present users of remote access
server technology.
VIRTUAL PRIVATE NETWORK
Another essential component of remotely accessible VPNs is a client software. In this
type of component, if an employee desires to use the VPN from their computer system, they
would require a particular software on those computer that would establish and maintain a
connection with the VPN. Nowadays some modern operating systems possess an inbuilt
system software that is capable of connecting to remote accessible VPNs although some of
the VPNs might require users to install a precise form of application. The software of the
client is set up with the help of a tunneled connection to a NAS. The user is indicated of this
activity with the help of the internet address. The client software is also responsible for
managing the required encryption in order to maintain a secure connection.
Many big businesses and large corporations that possess high knowledgeable IT staff
are often used to buying, deploy and maintain their own remote accessible VPNs. Many
businesses could easily opt to outsource their remotely accessed VPN services with the help
of an Enterprise Service Provider (ESP). The ESP can easily set up a NAS for a business and
thus try to maintain in keeping the NAS to run smoothly (Avram, 2014).
A remote access technology is the type of system and the software, which is
associated with it. It is often set up to handle those users who are seeking to gain access to a
remote network. It is sometimes referred as a server for communication. This kind of server
is often linked with a firewall server in order to safeguard the level of security. It is also able
to forward the remotely accessible request to another part of the corporate sector. The remote
access technology can contain the work with a modem pool manager such that a small group
of modems could be shared with a larger group of irregularly present users of remote access
server technology.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
VIRTUAL PRIVATE NETWORK
References
Avram, M. G. (2014). Advantages and challenges of adopting cloud computing from an
enterprise perspective. Procedia Technology, 12, 529-534.
Chung, C. J., Khatkar, P., Xing, T., Lee, J., & Huang, D. (2013). NICE: Network intrusion
detection and countermeasure selection in virtual network systems. IEEE transactions
on dependable and secure computing, 10(4), 198-211.
Fortuna, C., Ruckebusch, P., Van Praet, C., Moerman, I., Kaminski, N., DaSilva, L., ... &
Chwalisz, M. (2015). Wireless software and hardware platforms for flexible and
unified radio and network control. In European Conference on Networks and
Communications (EUCNC 2015) (pp. 712-717).
Gu, Y., Kim, M., Cui, Y., Lee, H., Choi, O., Pyeon, M., & Kim, J. (2013, June). Design and
implementation of UPnP-based surveillance camera system for home security.
In Information Science and Applications (ICISA), 2013 International Conference
on (pp. 1-4). IEEE.
Gupta, M. (2002). Building a Virtual Private Network. USA: Premier Press.
Jain, R., & Paul, S. (2013). Network virtualization and software defined networking for cloud
computing: a survey. IEEE Communications Magazine, 51(11), 24-31.
Kist, A. A., Maiti, A., Maxwell, A. D., Orwin, L., Midgley, W., Noble, K., & Ting, W. (2014,
February). Overlay network architectures for peer-to-peer Remote Access
Laboratories. In Remote Engineering and Virtual Instrumentation (REV), 2014 11th
International Conference on (pp. 274-280). IEEE.
VIRTUAL PRIVATE NETWORK
References
Avram, M. G. (2014). Advantages and challenges of adopting cloud computing from an
enterprise perspective. Procedia Technology, 12, 529-534.
Chung, C. J., Khatkar, P., Xing, T., Lee, J., & Huang, D. (2013). NICE: Network intrusion
detection and countermeasure selection in virtual network systems. IEEE transactions
on dependable and secure computing, 10(4), 198-211.
Fortuna, C., Ruckebusch, P., Van Praet, C., Moerman, I., Kaminski, N., DaSilva, L., ... &
Chwalisz, M. (2015). Wireless software and hardware platforms for flexible and
unified radio and network control. In European Conference on Networks and
Communications (EUCNC 2015) (pp. 712-717).
Gu, Y., Kim, M., Cui, Y., Lee, H., Choi, O., Pyeon, M., & Kim, J. (2013, June). Design and
implementation of UPnP-based surveillance camera system for home security.
In Information Science and Applications (ICISA), 2013 International Conference
on (pp. 1-4). IEEE.
Gupta, M. (2002). Building a Virtual Private Network. USA: Premier Press.
Jain, R., & Paul, S. (2013). Network virtualization and software defined networking for cloud
computing: a survey. IEEE Communications Magazine, 51(11), 24-31.
Kist, A. A., Maiti, A., Maxwell, A. D., Orwin, L., Midgley, W., Noble, K., & Ting, W. (2014,
February). Overlay network architectures for peer-to-peer Remote Access
Laboratories. In Remote Engineering and Virtual Instrumentation (REV), 2014 11th
International Conference on (pp. 274-280). IEEE.

8
VIRTUAL PRIVATE NETWORK
Maiti, A., Maxwell, A. D., & Kist, A. A. (2014). Features, trends and characteristics of
remote access laboratory management systems. International Journal of Online
Engineering (iJOE), 10(2), 30-37.
Modi, C., Patel, D., Borisaniya, B., Patel, A., & Rajarajan, M. (2013). A survey on security
issues and solutions at different layers of Cloud computing. The journal of
supercomputing, 63(2), 561-592.
Sathiaseelan, A., Mortier, R., Goulden, M., Greiffenhagen, C., Radenkovic, M., Crowcroft,
J., & McAuley, D. (2014, December). A feasibility study of an in-the-wild
experimental public access wifi network. In Proceedings of the Fifth ACM
Symposium on Computing for Development (pp. 33-42). ACM.
Selvi, V., Sankar, R., & Umarani, R. (2014). The design and implementation of on-line
examination using firewall security. IOSR Journal of Computer Engineering, 16(6),
20-24.
Sharkh, M. A., Jammal, M., Shami, A., & Ouda, A. (2013). Resource allocation in a network-
based cloud computing environment: design challenges. IEEE Communications
Magazine, 51(11), 46-52.
VIRTUAL PRIVATE NETWORK
Maiti, A., Maxwell, A. D., & Kist, A. A. (2014). Features, trends and characteristics of
remote access laboratory management systems. International Journal of Online
Engineering (iJOE), 10(2), 30-37.
Modi, C., Patel, D., Borisaniya, B., Patel, A., & Rajarajan, M. (2013). A survey on security
issues and solutions at different layers of Cloud computing. The journal of
supercomputing, 63(2), 561-592.
Sathiaseelan, A., Mortier, R., Goulden, M., Greiffenhagen, C., Radenkovic, M., Crowcroft,
J., & McAuley, D. (2014, December). A feasibility study of an in-the-wild
experimental public access wifi network. In Proceedings of the Fifth ACM
Symposium on Computing for Development (pp. 33-42). ACM.
Selvi, V., Sankar, R., & Umarani, R. (2014). The design and implementation of on-line
examination using firewall security. IOSR Journal of Computer Engineering, 16(6),
20-24.
Sharkh, M. A., Jammal, M., Shami, A., & Ouda, A. (2013). Resource allocation in a network-
based cloud computing environment: design challenges. IEEE Communications
Magazine, 51(11), 46-52.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




