Virtual Private Networks: Security Benefits and Implementation Details
VerifiedAdded on 2023/06/16
|14
|762
|297
Presentation
AI Summary
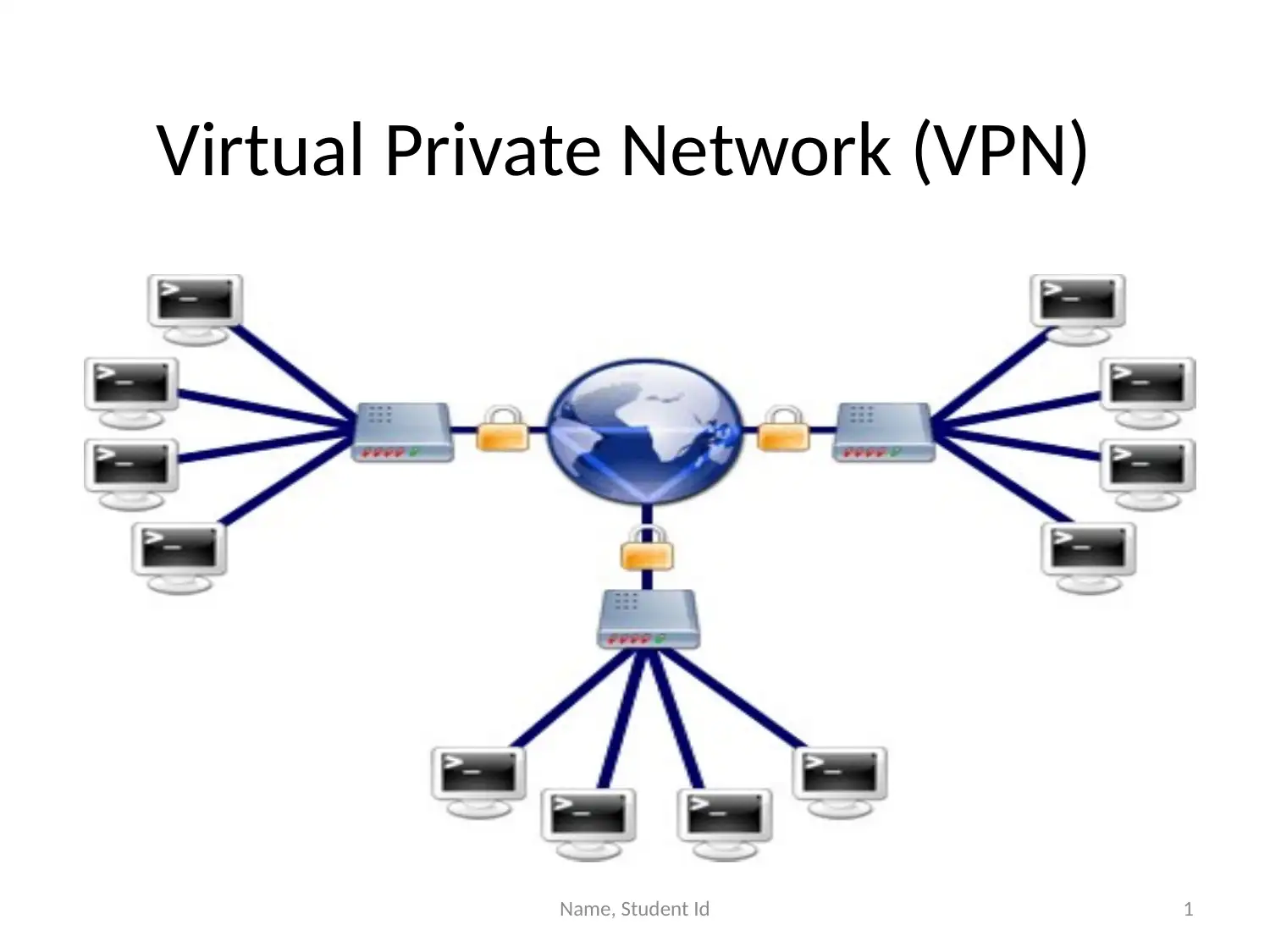
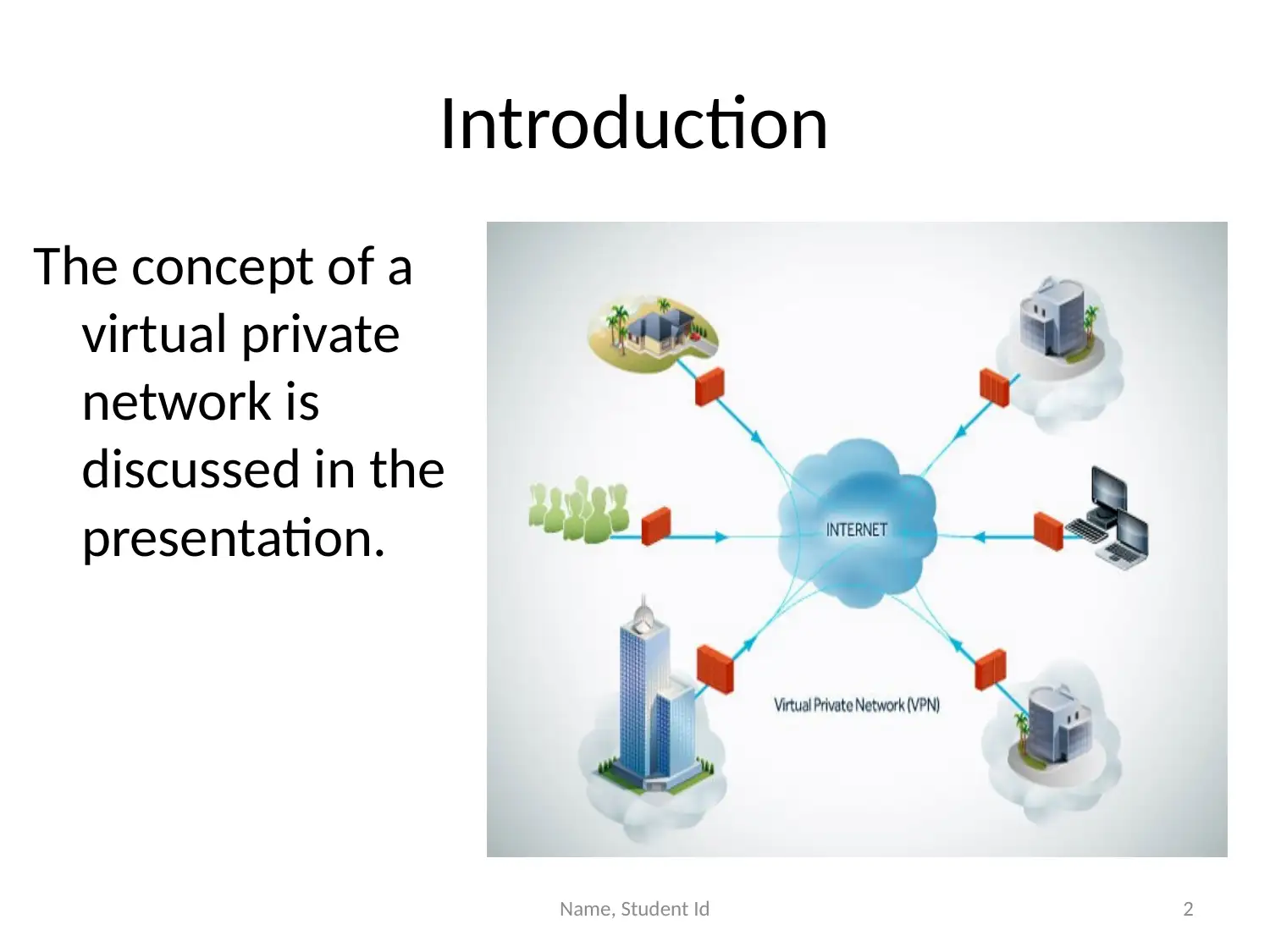
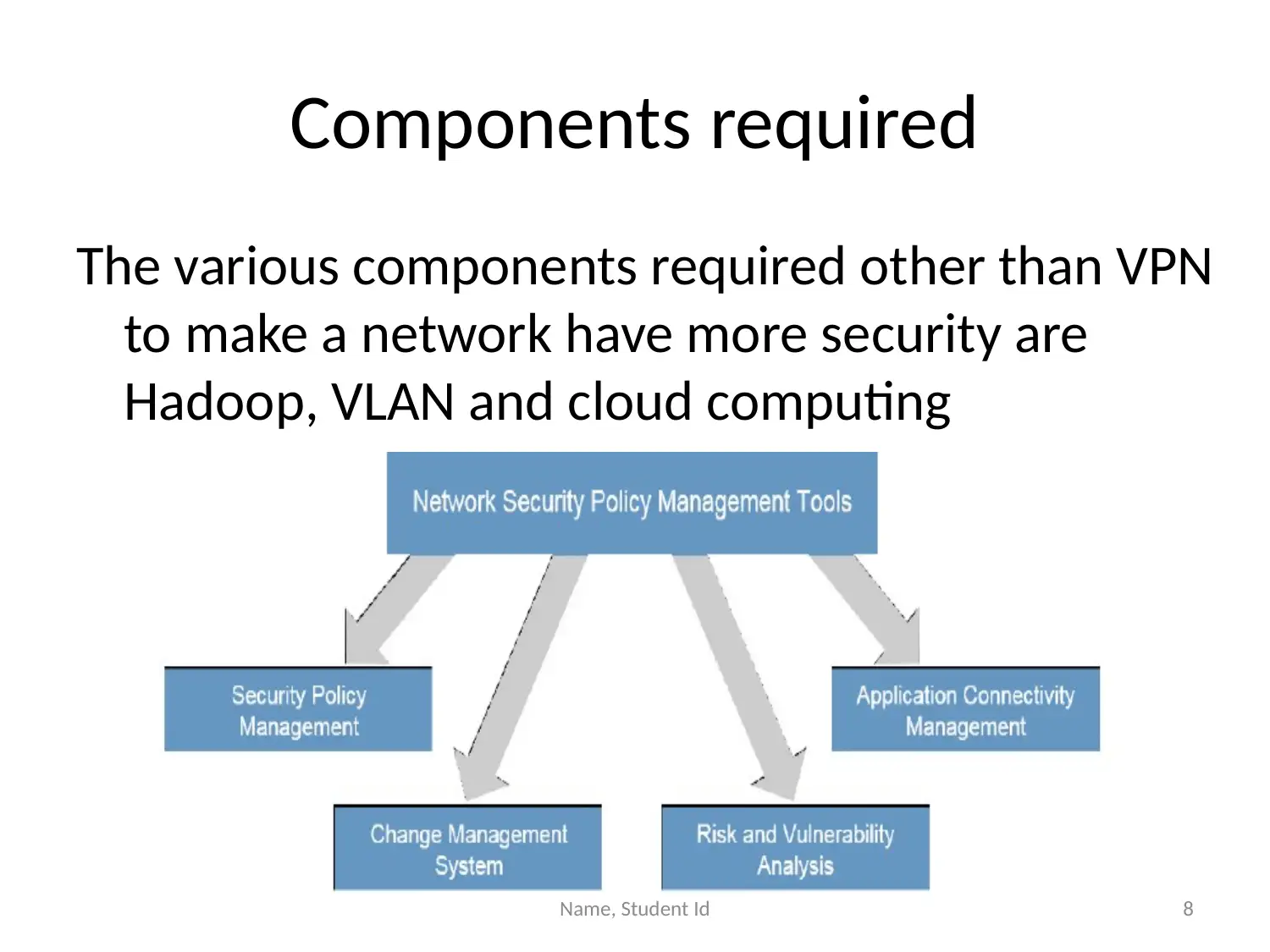
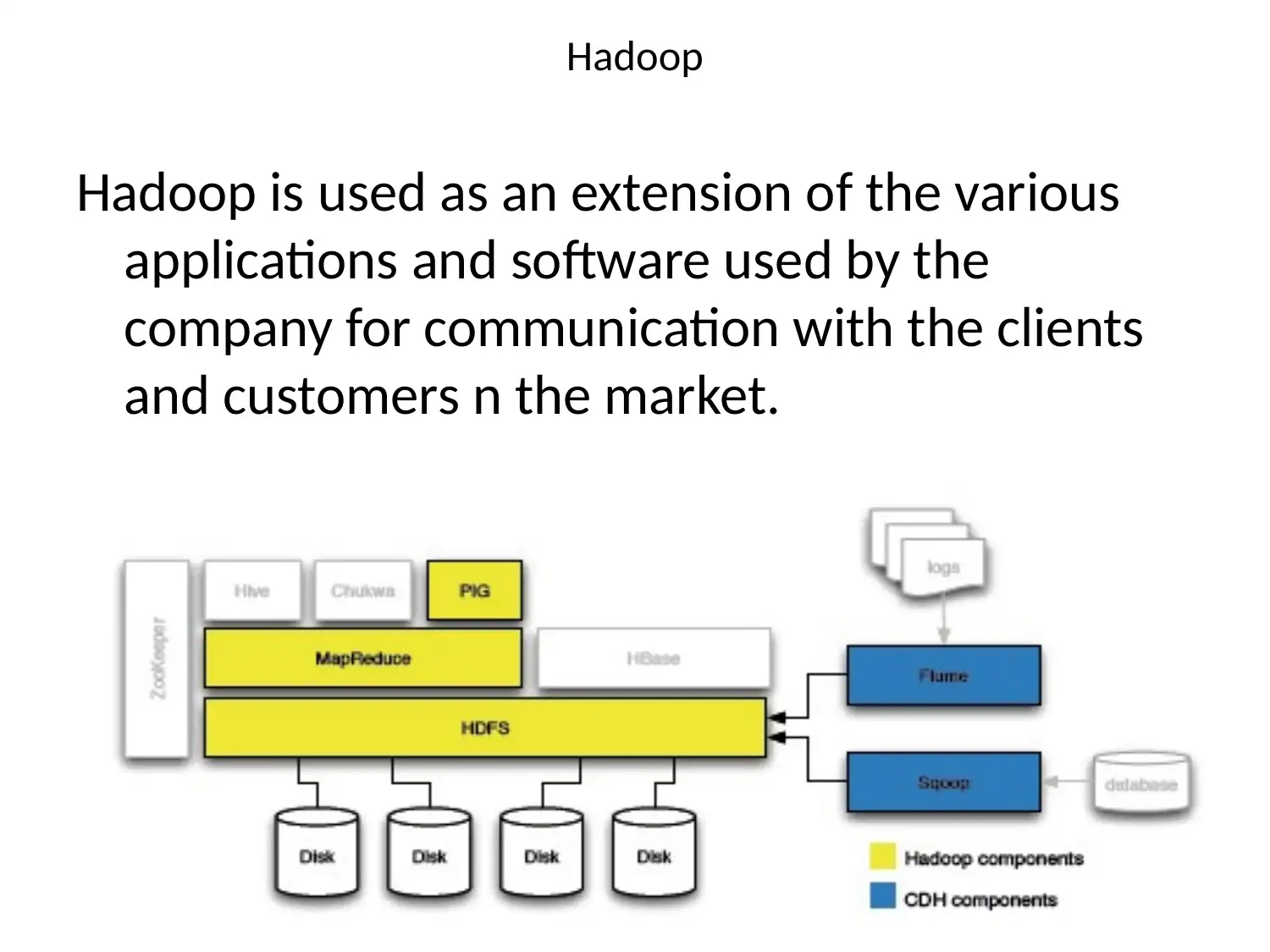
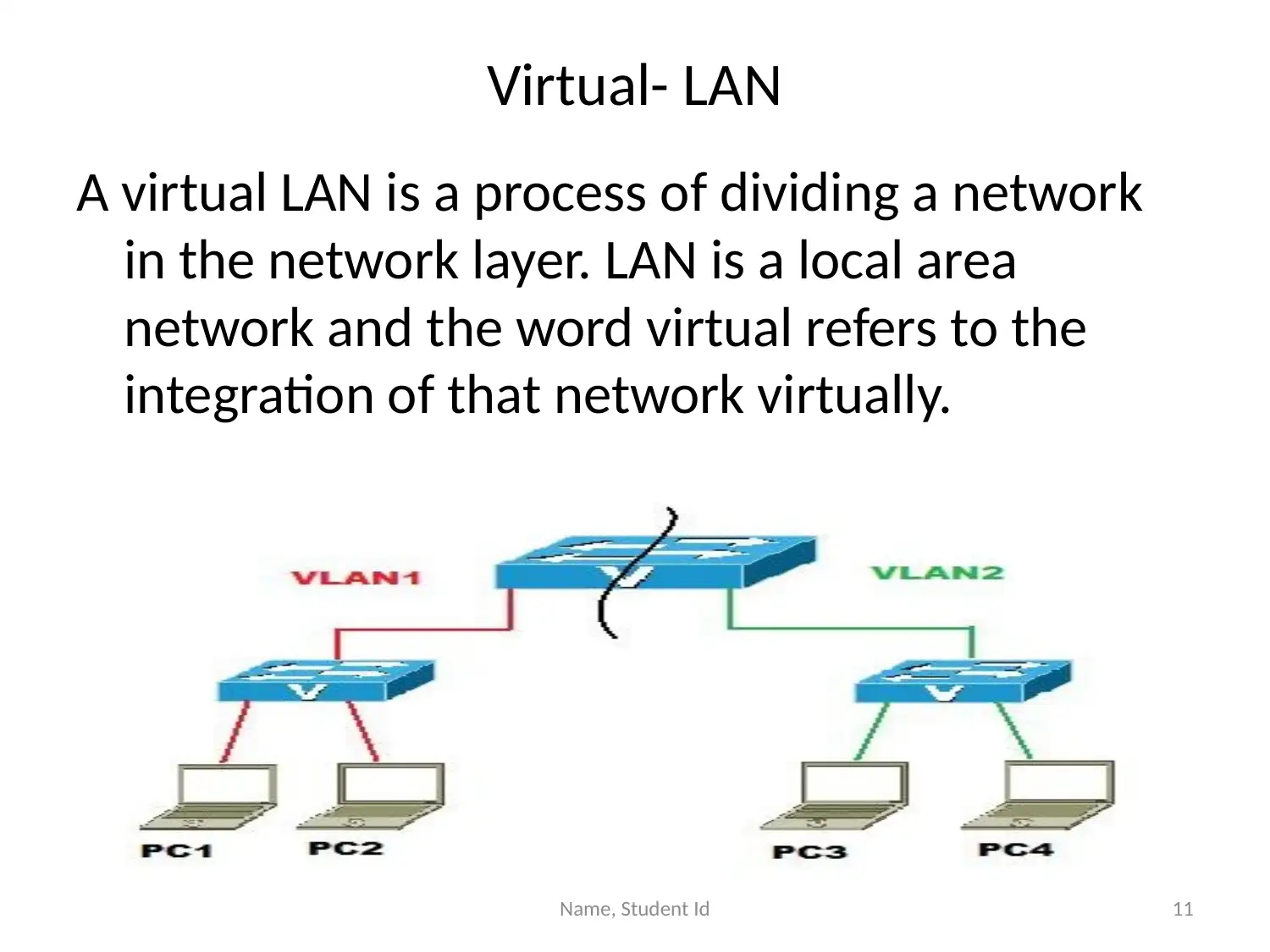
This presentation provides an overview of Virtual Private Networks (VPNs) and their importance in enhancing network security. It discusses how VPNs extend private network connections, enabling secure remote access and protecting against unauthorized access and data breaches. The presentation highlights the benefits of VPNs, including improved security, privacy, and the ability to filter IP addresses. It also explores complementary components such as Hadoop, cloud computing, and Virtual LANs (VLANs) that, when used in conjunction with VPNs, further strengthen network security. Hadoop is presented as an extension for company communication, cloud computing as a method for secure data storage, and VLANs as a means of network segmentation. The presentation concludes that implementing VPNs alongside these components significantly improves network security and enables secure remote access.
1 out of 14










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)