Network and VPN Services: A Report on VPN Design for a SME Network
VerifiedAdded on 2020/05/16
|11
|2202
|48
Report
AI Summary
This report presents a comprehensive network solution designed for a medium-sized enterprise, focusing on the implementation of a Virtual Private Network (VPN). The report begins with an introduction to the project, outlining its scope and limitations, which include integrating existing networks, configuring network services, and ensuring high network security. It details the project's requirements, covering general, product, service, and security needs, emphasizing adherence to quality standards and the division of intranet and internet traffic. The core of the report is the solution design, including logical and physical designs, network topologies (ring and star), and IP addressing schemes. Security features such as multi-layer security, backup mechanisms, and network segmentation are discussed, along with redundancy and failover plans. The report also covers VPN service implementation, highlighting its benefits like extended connectivity and reduced costs, along with data confidentiality and integrity measures. The report concludes by summarizing the key findings and the importance of the proposed network solution in meeting the enterprise's needs. The report is well-structured and provides a detailed analysis of the network design and the VPN implementation.

Running head: VIRTUAL PRIVATE NETWORK
VPN Network Design for SME network and VPN services
Name of the Student
Name of the University
Author’s Note
VPN Network Design for SME network and VPN services
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
VIRTUAL PRIVATE NETWORK
Table of Contents
Introduction....................................................................................................................................2
Scopes and Limitations...................................................................................................................2
Requirements.................................................................................................................................3
Solution Design...............................................................................................................................4
a. Logical Design.........................................................................................................................4
b. Physical Design.......................................................................................................................4
c. Network Topologies................................................................................................................5
d. IP Addressing..........................................................................................................................5
e. Security features and policies.................................................................................................6
f. Redundancy and failover plans................................................................................................6
g. VPN service implementation...................................................................................................6
Conclusion......................................................................................................................................7
Bibliography....................................................................................................................................9
VIRTUAL PRIVATE NETWORK
Table of Contents
Introduction....................................................................................................................................2
Scopes and Limitations...................................................................................................................2
Requirements.................................................................................................................................3
Solution Design...............................................................................................................................4
a. Logical Design.........................................................................................................................4
b. Physical Design.......................................................................................................................4
c. Network Topologies................................................................................................................5
d. IP Addressing..........................................................................................................................5
e. Security features and policies.................................................................................................6
f. Redundancy and failover plans................................................................................................6
g. VPN service implementation...................................................................................................6
Conclusion......................................................................................................................................7
Bibliography....................................................................................................................................9

2
VIRTUAL PRIVATE NETWORK
Introduction
The report is prepared for a medium sized enterprise to connect all the departments if the
organization and improve the current capacity of the organization for the accommodation of its future
growth. The technologies that can be applied for the development of the solution are documented in
the report. The report contains the scope and limitation of the network and the requirements such as
the hardware and the software for the development of the network solution. The logical design, physical
design and the network topologies are developed and an IP addressing is created for each of the
department. The security measures that can be applied for increasing the security of the network are
also discussed in the report. Redundant link are created for responding to the network failover and
implementation of VPN service for allowing the remote users to connect with the resources of the
network.
Scopes and Limitations
The main scope identified for the development of the project are listed below:
To integrate the existing network of the organization with the new devices and
equipment for reducing the cost of the network.
Configuration of the network services and configuration of the routing devices as per
the requirement of the organization.
Up gradation of the existing servers of the organization and enabling virtualization of
the server for handling more number of request from the client.
Wireless access point should be installed in the network for allowing the users with
wireless devices to connect with organizational network.
Securing the access point for securing the network from illegal access.
Increasing the redundancy in the network for removing the failover point and increasing
the availability of the resources in the network.
The limitations identified for the development of the network solution are listed below:
Compatibility of the previously installed networking devices with the newly installed
devices.
The finance and budget of the proposed solution should be approved for deployment in
the organization
VIRTUAL PRIVATE NETWORK
Introduction
The report is prepared for a medium sized enterprise to connect all the departments if the
organization and improve the current capacity of the organization for the accommodation of its future
growth. The technologies that can be applied for the development of the solution are documented in
the report. The report contains the scope and limitation of the network and the requirements such as
the hardware and the software for the development of the network solution. The logical design, physical
design and the network topologies are developed and an IP addressing is created for each of the
department. The security measures that can be applied for increasing the security of the network are
also discussed in the report. Redundant link are created for responding to the network failover and
implementation of VPN service for allowing the remote users to connect with the resources of the
network.
Scopes and Limitations
The main scope identified for the development of the project are listed below:
To integrate the existing network of the organization with the new devices and
equipment for reducing the cost of the network.
Configuration of the network services and configuration of the routing devices as per
the requirement of the organization.
Up gradation of the existing servers of the organization and enabling virtualization of
the server for handling more number of request from the client.
Wireless access point should be installed in the network for allowing the users with
wireless devices to connect with organizational network.
Securing the access point for securing the network from illegal access.
Increasing the redundancy in the network for removing the failover point and increasing
the availability of the resources in the network.
The limitations identified for the development of the network solution are listed below:
Compatibility of the previously installed networking devices with the newly installed
devices.
The finance and budget of the proposed solution should be approved for deployment in
the organization
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
VIRTUAL PRIVATE NETWORK
The security of the network should be high and the flaws in the system should be
removed for increasing the quality of the network.
The network administrator should be efficient skills and knowledge for configuration of
the network devices according to the needs of the organization.
Requirements
The requirement for the development of the network solution can be categorized into different
sections such as general and product requirement, service and network requirement, security and
hardware cabling requirements.
The proposed network solution should be created following the quality of standards for
each of the device installed in the network.
The intranet and the internet traffic should be divided for reducing the response time of
the system and high level design should be shown for ease the management process.
The servers should be stored in a separate room under lock and key for restriction of the
physical access.
Virtualization should be applied on the server for balancing the loads and handle
number of request at a time.
The current network should be covered and it should be extended for inclusion of the
current network components for the development of the network solution.
A proper addressing plan should be created for allocation of IP address to different
VLAN and dividing different subnet for saving the address space.
Configuring the server with DHCP to allocate the IP address to the Pc connected in the
network automatically.
Installation of a firewall in the entry and exit point of the network for securing the
network traffic securing the network from unauthorized access.
Encryption of the communication channels for securing the network from different
types of attacks
Use of encryption and password in the wireless access points for reducing the risk of
illegal access
Use of proper cabling for interconnecting the device installed in different location of the
network.
VIRTUAL PRIVATE NETWORK
The security of the network should be high and the flaws in the system should be
removed for increasing the quality of the network.
The network administrator should be efficient skills and knowledge for configuration of
the network devices according to the needs of the organization.
Requirements
The requirement for the development of the network solution can be categorized into different
sections such as general and product requirement, service and network requirement, security and
hardware cabling requirements.
The proposed network solution should be created following the quality of standards for
each of the device installed in the network.
The intranet and the internet traffic should be divided for reducing the response time of
the system and high level design should be shown for ease the management process.
The servers should be stored in a separate room under lock and key for restriction of the
physical access.
Virtualization should be applied on the server for balancing the loads and handle
number of request at a time.
The current network should be covered and it should be extended for inclusion of the
current network components for the development of the network solution.
A proper addressing plan should be created for allocation of IP address to different
VLAN and dividing different subnet for saving the address space.
Configuring the server with DHCP to allocate the IP address to the Pc connected in the
network automatically.
Installation of a firewall in the entry and exit point of the network for securing the
network traffic securing the network from unauthorized access.
Encryption of the communication channels for securing the network from different
types of attacks
Use of encryption and password in the wireless access points for reducing the risk of
illegal access
Use of proper cabling for interconnecting the device installed in different location of the
network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
VIRTUAL PRIVATE NETWORK
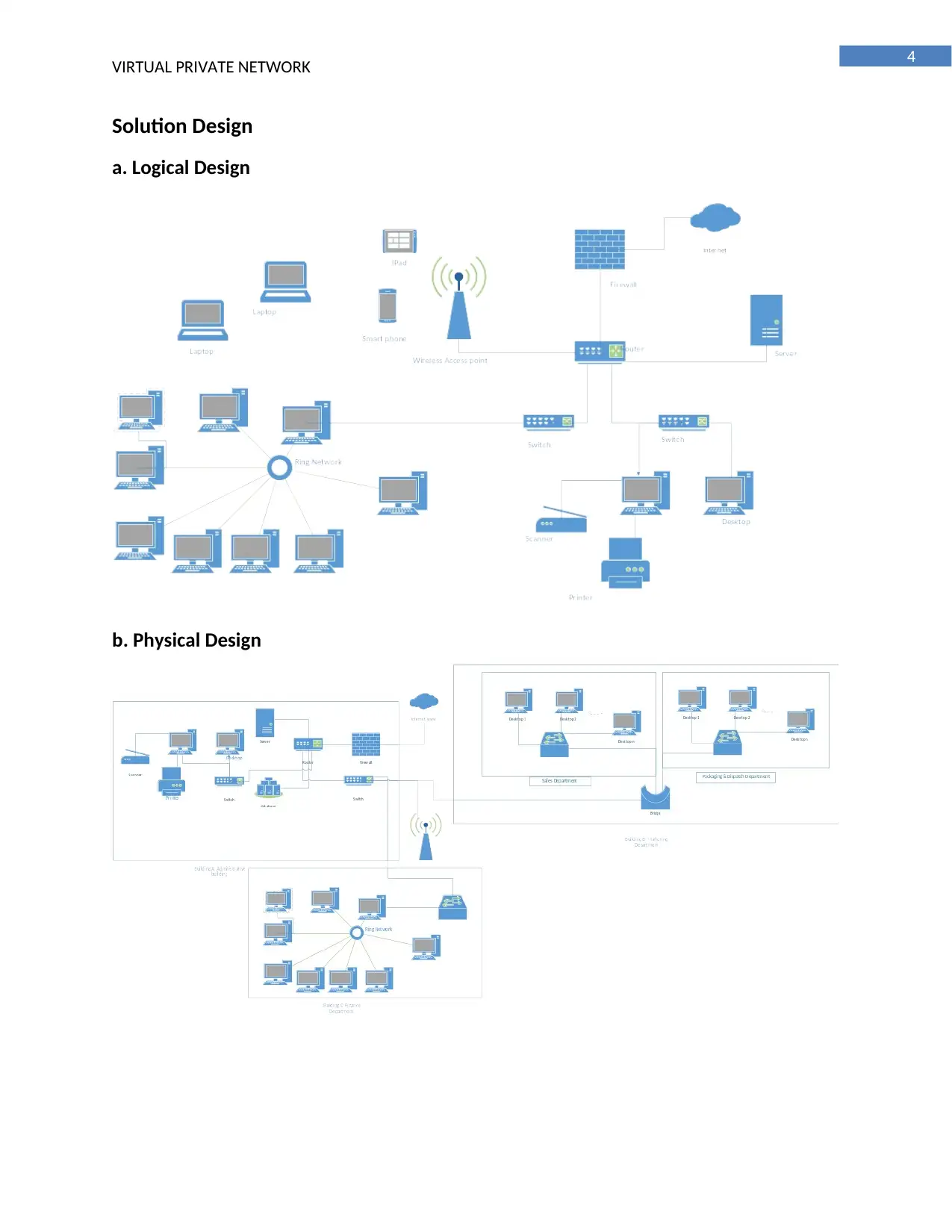
Solution Design
a. Logical Design
b. Physical Design
VIRTUAL PRIVATE NETWORK
Solution Design
a. Logical Design
b. Physical Design
5
VIRTUAL PRIVATE NETWORK
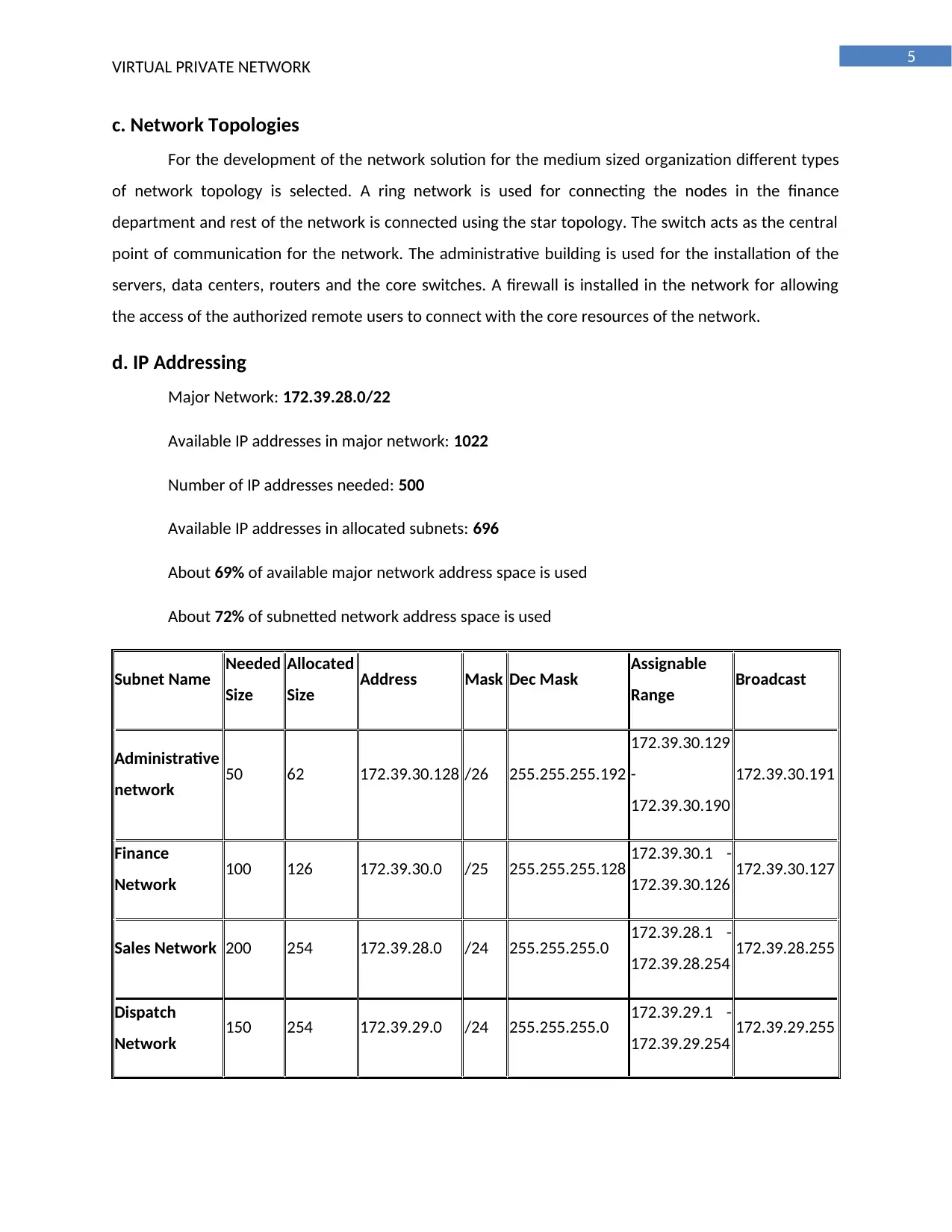
c. Network Topologies
For the development of the network solution for the medium sized organization different types
of network topology is selected. A ring network is used for connecting the nodes in the finance
department and rest of the network is connected using the star topology. The switch acts as the central
point of communication for the network. The administrative building is used for the installation of the
servers, data centers, routers and the core switches. A firewall is installed in the network for allowing
the access of the authorized remote users to connect with the core resources of the network.
d. IP Addressing
Major Network: 172.39.28.0/22
Available IP addresses in major network: 1022
Number of IP addresses needed: 500
Available IP addresses in allocated subnets: 696
About 69% of available major network address space is used
About 72% of subnetted network address space is used
Subnet Name Needed
Size
Allocated
Size Address Mask Dec Mask Assignable
Range Broadcast
Administrative
network 50 62 172.39.30.128 /26 255.255.255.192
172.39.30.129
-
172.39.30.190
172.39.30.191
Finance
Network 100 126 172.39.30.0 /25 255.255.255.128 172.39.30.1 -
172.39.30.126 172.39.30.127
Sales Network 200 254 172.39.28.0 /24 255.255.255.0 172.39.28.1 -
172.39.28.254 172.39.28.255
Dispatch
Network 150 254 172.39.29.0 /24 255.255.255.0 172.39.29.1 -
172.39.29.254 172.39.29.255
VIRTUAL PRIVATE NETWORK
c. Network Topologies
For the development of the network solution for the medium sized organization different types
of network topology is selected. A ring network is used for connecting the nodes in the finance
department and rest of the network is connected using the star topology. The switch acts as the central
point of communication for the network. The administrative building is used for the installation of the
servers, data centers, routers and the core switches. A firewall is installed in the network for allowing
the access of the authorized remote users to connect with the core resources of the network.
d. IP Addressing
Major Network: 172.39.28.0/22
Available IP addresses in major network: 1022
Number of IP addresses needed: 500
Available IP addresses in allocated subnets: 696
About 69% of available major network address space is used
About 72% of subnetted network address space is used
Subnet Name Needed
Size
Allocated
Size Address Mask Dec Mask Assignable
Range Broadcast
Administrative
network 50 62 172.39.30.128 /26 255.255.255.192
172.39.30.129
-
172.39.30.190
172.39.30.191
Finance
Network 100 126 172.39.30.0 /25 255.255.255.128 172.39.30.1 -
172.39.30.126 172.39.30.127
Sales Network 200 254 172.39.28.0 /24 255.255.255.0 172.39.28.1 -
172.39.28.254 172.39.28.255
Dispatch
Network 150 254 172.39.29.0 /24 255.255.255.0 172.39.29.1 -
172.39.29.254 172.39.29.255
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
VIRTUAL PRIVATE NETWORK
e. Security features and policies
A multilayer security design should be applied for the development of the secure network
solution. A backup mechanism should be created for each of the device installed in the network and a
dedicated hardware device should be installed in the network for limiting the access of the core network
resources to all the users connected in the network [8]. The network should be divided into modules
such as internet access, remote access or VPN, network management and services, wireless network
and user services. For securing the internet access packet filtering, authentication, audit logs and
physical security devices such as firewall, IPS should be applied. For securing the server it should be
installed in the DMZ zone and it should be configured to run only required services for protecting it from
intrusion attacks [12].
Thee remote access and the VPN should also be secured with the application of authentication
and authorization mechanism. The point to point established between the remote user and the remote
routers should use CHAP authentication and the RADIUS server can be used for centralizing the data
management and authenticating the dial in and the dial out service [1].
f. Redundancy and failover plans
If one of the link in the network the fails then a backup link should be used for reaching the
destination nodes connected in the network. The core network should have redundant links and dual
channels should be created for establishment of connection between the source port and the
destination address [3]. For the management of the business traffics in the medium scale enterprise
network a load balancing mechanism should be applied for increasing the reliability of the network. A
reliable data communication should be created for increasing the availability of the resources and
increasing the availability of the VPN connection.
g. VPN service implementation
A VPN software is required to be selected for establishment of a VPN tunnel between the user
and the organizational network for securely communicating with the network components. The internet
is used for establishment of the connection between the remote user and the network [11]. With the
implementation of the VPN service in the network the following benefits can be gained by the
organization such as:
Extension of the geographical connectivity
Reduction in the operation cost
VIRTUAL PRIVATE NETWORK
e. Security features and policies
A multilayer security design should be applied for the development of the secure network
solution. A backup mechanism should be created for each of the device installed in the network and a
dedicated hardware device should be installed in the network for limiting the access of the core network
resources to all the users connected in the network [8]. The network should be divided into modules
such as internet access, remote access or VPN, network management and services, wireless network
and user services. For securing the internet access packet filtering, authentication, audit logs and
physical security devices such as firewall, IPS should be applied. For securing the server it should be
installed in the DMZ zone and it should be configured to run only required services for protecting it from
intrusion attacks [12].
Thee remote access and the VPN should also be secured with the application of authentication
and authorization mechanism. The point to point established between the remote user and the remote
routers should use CHAP authentication and the RADIUS server can be used for centralizing the data
management and authenticating the dial in and the dial out service [1].
f. Redundancy and failover plans
If one of the link in the network the fails then a backup link should be used for reaching the
destination nodes connected in the network. The core network should have redundant links and dual
channels should be created for establishment of connection between the source port and the
destination address [3]. For the management of the business traffics in the medium scale enterprise
network a load balancing mechanism should be applied for increasing the reliability of the network. A
reliable data communication should be created for increasing the availability of the resources and
increasing the availability of the VPN connection.
g. VPN service implementation
A VPN software is required to be selected for establishment of a VPN tunnel between the user
and the organizational network for securely communicating with the network components. The internet
is used for establishment of the connection between the remote user and the network [11]. With the
implementation of the VPN service in the network the following benefits can be gained by the
organization such as:
Extension of the geographical connectivity
Reduction in the operation cost
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
VIRTUAL PRIVATE NETWORK
Reduction in the time taken for transmission for the remote users
Simplification of the topology of the network
Improvement in the productivity
For securing the data connection in VPN the following methods are used
Data confidentiality – The data is encrypted before sending to the user connected via the VPN
because the data is sent in a public network and it can be access by any third party user for
illegal use.
o IPsec – It is applied for increasing the security levels and using strong encryption algorithm
and comprehensive authentication mechanism for securing the network. The two modes
tunneling and transport are utilized, where in the tunnel mode the header of the data
packet is encrypted and in the transport the payload is encrypted [5]. For the application of
IPsec the system is required to be compliant with the protocol and same policy should be
set in the network.
o PPTP/ MPPE – multi protocols are used in PPTP utilizing the multiple point to point protocol.
40 bits and 128 bit encryption is used for encrypting the communication channel.
Data Integrity – It is important to check the data on deceiving on the other end for ensuring
that the data packet contains all the information and it has not been tampered.
Authentication of data origin – The source of the data should be identified and it should be
applied for protection against different types of attacks.
Data tunneling – In this process the data packets are encapsulated into another packet for
transmission in the network [2]. It is used for hiding the identity of the users and protecting the
source from where the packet is generated.
Conclusion
From the above report it can be concluded that the network solution is prepared after analyzing
the requirement of the medium sized organization. The internet security policy that can be applied for
increasing the security of the network is created aligning the business requirement. A list of the
equipment are created for analyzing the requirement and designing the network. A failover scenario is
also required to be created for responding against the needs emergency condition and mitigation of the
risk associated with the development of the network solution. Separate VLANs are created for each of
VIRTUAL PRIVATE NETWORK
Reduction in the time taken for transmission for the remote users
Simplification of the topology of the network
Improvement in the productivity
For securing the data connection in VPN the following methods are used
Data confidentiality – The data is encrypted before sending to the user connected via the VPN
because the data is sent in a public network and it can be access by any third party user for
illegal use.
o IPsec – It is applied for increasing the security levels and using strong encryption algorithm
and comprehensive authentication mechanism for securing the network. The two modes
tunneling and transport are utilized, where in the tunnel mode the header of the data
packet is encrypted and in the transport the payload is encrypted [5]. For the application of
IPsec the system is required to be compliant with the protocol and same policy should be
set in the network.
o PPTP/ MPPE – multi protocols are used in PPTP utilizing the multiple point to point protocol.
40 bits and 128 bit encryption is used for encrypting the communication channel.
Data Integrity – It is important to check the data on deceiving on the other end for ensuring
that the data packet contains all the information and it has not been tampered.
Authentication of data origin – The source of the data should be identified and it should be
applied for protection against different types of attacks.
Data tunneling – In this process the data packets are encapsulated into another packet for
transmission in the network [2]. It is used for hiding the identity of the users and protecting the
source from where the packet is generated.
Conclusion
From the above report it can be concluded that the network solution is prepared after analyzing
the requirement of the medium sized organization. The internet security policy that can be applied for
increasing the security of the network is created aligning the business requirement. A list of the
equipment are created for analyzing the requirement and designing the network. A failover scenario is
also required to be created for responding against the needs emergency condition and mitigation of the
risk associated with the development of the network solution. Separate VLANs are created for each of

8
VIRTUAL PRIVATE NETWORK
the department and groups for creation of separate channels of communication and reduce the
congestion in the network.
VIRTUAL PRIVATE NETWORK
the department and groups for creation of separate channels of communication and reduce the
congestion in the network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
VIRTUAL PRIVATE NETWORK
Bibliography
[1]. R. Brewer, "Advanced persistent threats: minimising the damage", Network Security, vol. 2014,
no. 4, pp. 5-9, 2014.
[2]. "IEEE/ACM Transactions on Networking society information", IEEE/ACM Transactions on
Networking, vol. 24, no. 5, pp. C3-C3, 2016.
[3]. D. Langenhan, VMware View Security Essentials. Packt Publishing, 2013.
[4]. "Optical Switching and Networking", Optical Switching and Networking, vol. 10, no. 4, pp. 463-
464, 2013.
[5]. S. Subramaniam, M. Brandt-Pearce, P. Demeester and C. Vijaya Saradhi, Cross-Layer Design in
Optical Networks. Boston, MA: Springer US, 2013.
[6]. "Introduction to Information Security", Network Security, vol. 2013, no. 12, p. 4, 2013.
[7]. "The Practice of Network Security Monitoring", Network Security, vol. 2014, no. 10, p. 4, 2014.
[8]. J. Wang, "The Design of Improved Elman Network Intrusion Detection Algorithm in Digital
Campus Network", Advanced Materials Research, vol. 1049-1050, pp. 2096-2099, 2014.
[9]. S. Kermanshahi, Y. Shafahi and M. Bagherian, "Application of a new rapid transit network design
model to bus rapid transit network design: case study Isfahan metropolitan area", Transport,
vol. 30, no. 1, pp. 93-102, 2013.
[10]. E. Yadegari, M. Zandieh and H. Najmi, "A hybrid spanning tree-based genetic/simulated
annealing algorithm for a closed-loop logistics network design problem", International Journal of
Applied Decision Sciences, vol. 8, no. 4, p. 400, 2015.
VIRTUAL PRIVATE NETWORK
Bibliography
[1]. R. Brewer, "Advanced persistent threats: minimising the damage", Network Security, vol. 2014,
no. 4, pp. 5-9, 2014.
[2]. "IEEE/ACM Transactions on Networking society information", IEEE/ACM Transactions on
Networking, vol. 24, no. 5, pp. C3-C3, 2016.
[3]. D. Langenhan, VMware View Security Essentials. Packt Publishing, 2013.
[4]. "Optical Switching and Networking", Optical Switching and Networking, vol. 10, no. 4, pp. 463-
464, 2013.
[5]. S. Subramaniam, M. Brandt-Pearce, P. Demeester and C. Vijaya Saradhi, Cross-Layer Design in
Optical Networks. Boston, MA: Springer US, 2013.
[6]. "Introduction to Information Security", Network Security, vol. 2013, no. 12, p. 4, 2013.
[7]. "The Practice of Network Security Monitoring", Network Security, vol. 2014, no. 10, p. 4, 2014.
[8]. J. Wang, "The Design of Improved Elman Network Intrusion Detection Algorithm in Digital
Campus Network", Advanced Materials Research, vol. 1049-1050, pp. 2096-2099, 2014.
[9]. S. Kermanshahi, Y. Shafahi and M. Bagherian, "Application of a new rapid transit network design
model to bus rapid transit network design: case study Isfahan metropolitan area", Transport,
vol. 30, no. 1, pp. 93-102, 2013.
[10]. E. Yadegari, M. Zandieh and H. Najmi, "A hybrid spanning tree-based genetic/simulated
annealing algorithm for a closed-loop logistics network design problem", International Journal of
Applied Decision Sciences, vol. 8, no. 4, p. 400, 2015.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
VIRTUAL PRIVATE NETWORK
[11]. F. Liu and W. Qu, "Design of Campus Network Database Access Based on
Encryption", Applied Mechanics and Materials, vol. 608-609, pp. 331-335, 2014.
A. Hosapujari and A. Verma, "Development of a Hub and Spoke Model for Bus Transit
Route Network Design", Procedia - Social and Behavioral Sciences, vol. 104, pp. 835-844,
2013.
[12]. "The Comprehensive Evaluation Research of Campus Network Security Based on the
Analytic Hierarchy Process (AHP)", INTERNATIONAL JOURNAL ON Advances in Information
Sciences and Service Sciences, vol. 5, no. 7, pp. 809-816, 2013.
VIRTUAL PRIVATE NETWORK
[11]. F. Liu and W. Qu, "Design of Campus Network Database Access Based on
Encryption", Applied Mechanics and Materials, vol. 608-609, pp. 331-335, 2014.
A. Hosapujari and A. Verma, "Development of a Hub and Spoke Model for Bus Transit
Route Network Design", Procedia - Social and Behavioral Sciences, vol. 104, pp. 835-844,
2013.
[12]. "The Comprehensive Evaluation Research of Campus Network Security Based on the
Analytic Hierarchy Process (AHP)", INTERNATIONAL JOURNAL ON Advances in Information
Sciences and Service Sciences, vol. 5, no. 7, pp. 809-816, 2013.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




