Master of Networking (MN610) - Virtual Private Networks Presentation
VerifiedAdded on 2023/03/31
|14
|743
|173
Presentation
AI Summary
This presentation analyzes the network requirements of AgriDigital, focusing on VPN services. It outlines the project's scope, limitations, and requirements for integrating new branches with the headquarters' network through VPN tunnels. The presentation covers VPN security measures like firewalls, WPA2 encryption, and logical/physical network designs. It includes IP addressing schemes, network diagrams, and redundancy strategies. The presentation concludes with a summary of the discussed topics and references used in the design and implementation of the VPN network, emphasizing the importance of VPNs in securing the network from external threats and ensuring secure communication between the headquarters and its branches.

A Presentation on VPN
networks
networks
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
The following report analyses the network based requirements of the
company AgriDigital and proceeds to identifies the VPN services used.
At first the scope of the project is given, followed by Limitations
The report also goes on to provide the summary of requirements related
to the network and the VPN services being used.
The following report analyses the network based requirements of the
company AgriDigital and proceeds to identifies the VPN services used.
At first the scope of the project is given, followed by Limitations
The report also goes on to provide the summary of requirements related
to the network and the VPN services being used.

Scope & Limitations
New networking equipment is to be acquired and implemented to implement
the network of AgriDigital.
These equipment should then be installed, build as per requirements for
configuring new networks through the edge router [4].
The new networks are the networks of newly set up branches of the company
These branch networks are to be integrated with the main network through
VPN tunnels.
Overall network is secured by VPN firewall, and WPA2 for encrypted keys in
wireless connectivity.
IPsec VPNs make it difficult for even organizational members to access the
company network from public Wi-Fi regions or other areas.
New networking equipment is to be acquired and implemented to implement
the network of AgriDigital.
These equipment should then be installed, build as per requirements for
configuring new networks through the edge router [4].
The new networks are the networks of newly set up branches of the company
These branch networks are to be integrated with the main network through
VPN tunnels.
Overall network is secured by VPN firewall, and WPA2 for encrypted keys in
wireless connectivity.
IPsec VPNs make it difficult for even organizational members to access the
company network from public Wi-Fi regions or other areas.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Requirement analysis
Two new branches of the organization AgriDigital is newly built.
Both these branches require their network to be integrated with that of
the Headquarters to avail important server side functions.
The integration the headquarters needs to happen with comprehensive
security measures in place.
Two new branches of the organization AgriDigital is newly built.
Both these branches require their network to be integrated with that of
the Headquarters to avail important server side functions.
The integration the headquarters needs to happen with comprehensive
security measures in place.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Virtual Private Network (VPN)
Virtual Private Networks (VPNs)
are essential in hiding the
network from external threats
like hackers [3].
User account verification and
authentication processes is also
employed by VPN.
Firewalls are necessary in fool-
proofing VPN based networks.
Virtual Private Networks (VPNs)
are essential in hiding the
network from external threats
like hackers [3].
User account verification and
authentication processes is also
employed by VPN.
Firewalls are necessary in fool-
proofing VPN based networks.

Firewalls
Firewalls are used to filter data
packets, both inbound and
outbound.
Firewalls can also be used to
conduct authentication of users
connected to the network.
The ports and rules used by
firewalls ensure only trusted
connections are allow.
Firewalls are used to filter data
packets, both inbound and
outbound.
Firewalls can also be used to
conduct authentication of users
connected to the network.
The ports and rules used by
firewalls ensure only trusted
connections are allow.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Encryption in Wireless Connectivity
WPA2 or Wi-Fi Protected Access
is the recommended encryption
technique for generating keys
for devices connected to
wireless networks.
These are security protocols as
also security certifications for
securing wireless networks.
These protocols have been
developed by Wi-Fi Alliance.
WPA2 or Wi-Fi Protected Access
is the recommended encryption
technique for generating keys
for devices connected to
wireless networks.
These are security protocols as
also security certifications for
securing wireless networks.
These protocols have been
developed by Wi-Fi Alliance.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Logical Network Design
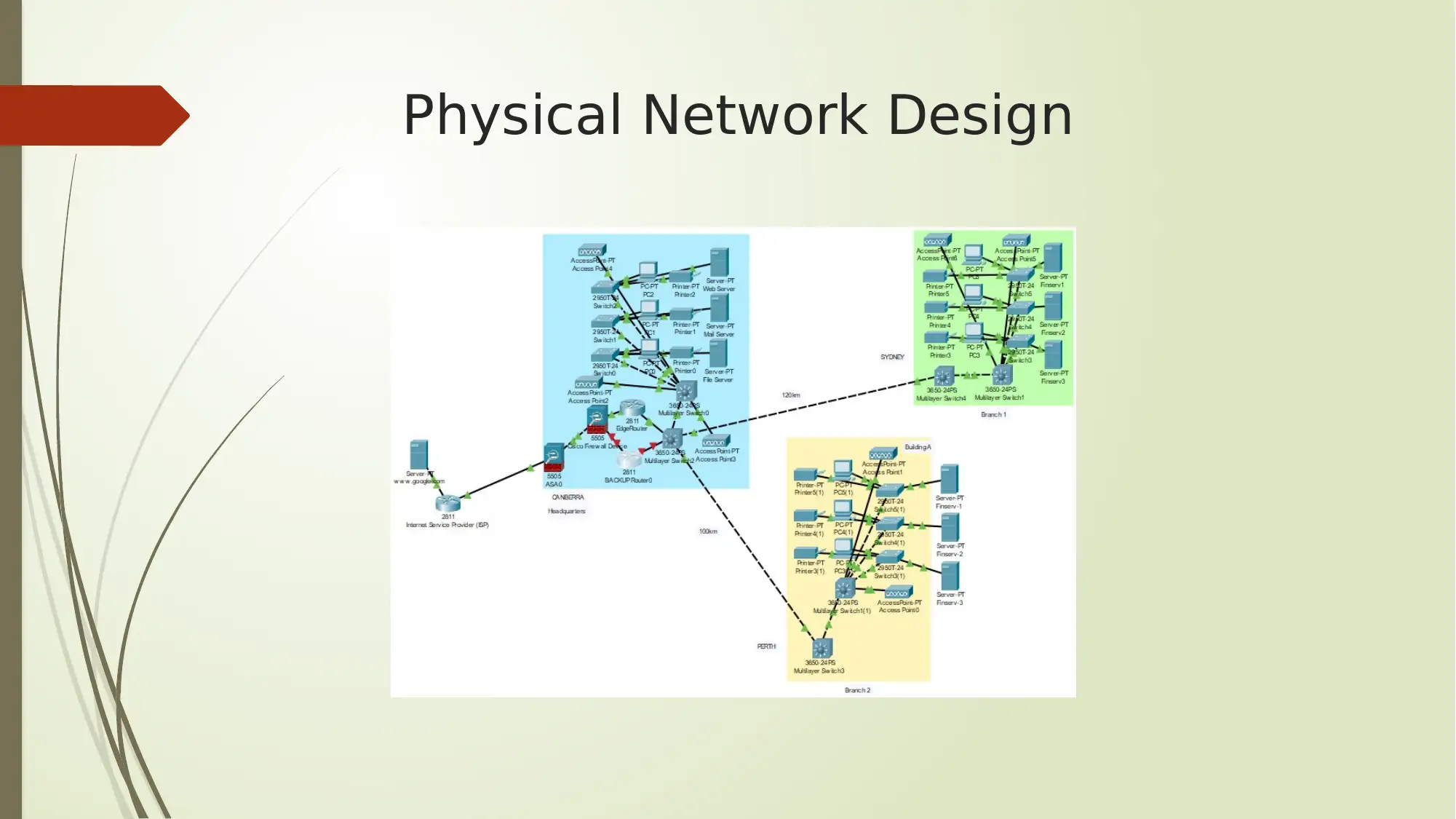
Physical Network Design
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Network Design
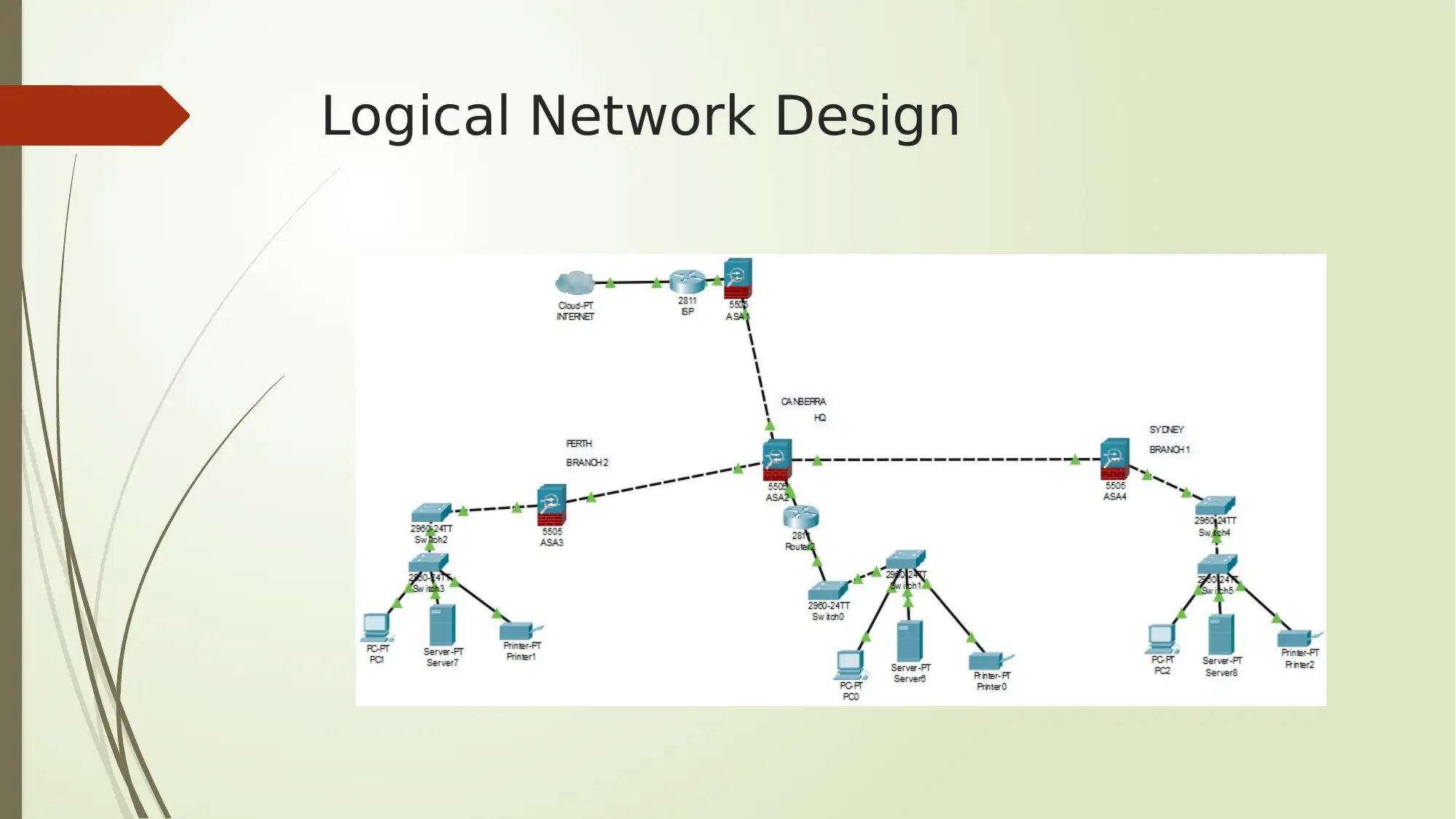
In the logical network diagram it can be seen how VPN networks are
configured between networks of headquarters to Branch 1,
Headquarters and branch 2 and the network between HQ and ISP [1].
Redundancies are ensured by having multiple firewall devices set up for
safeguarding the endpoint devices.
Distribution and access layer switches also add to the existing
redundancy in the network.
In physical diagram layout of numerous access points are given. Thus
redundancy of wireless access points ensure signal issues get eliminated
[2].
In the logical network diagram it can be seen how VPN networks are
configured between networks of headquarters to Branch 1,
Headquarters and branch 2 and the network between HQ and ISP [1].
Redundancies are ensured by having multiple firewall devices set up for
safeguarding the endpoint devices.
Distribution and access layer switches also add to the existing
redundancy in the network.
In physical diagram layout of numerous access points are given. Thus
redundancy of wireless access points ensure signal issues get eliminated
[2].
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
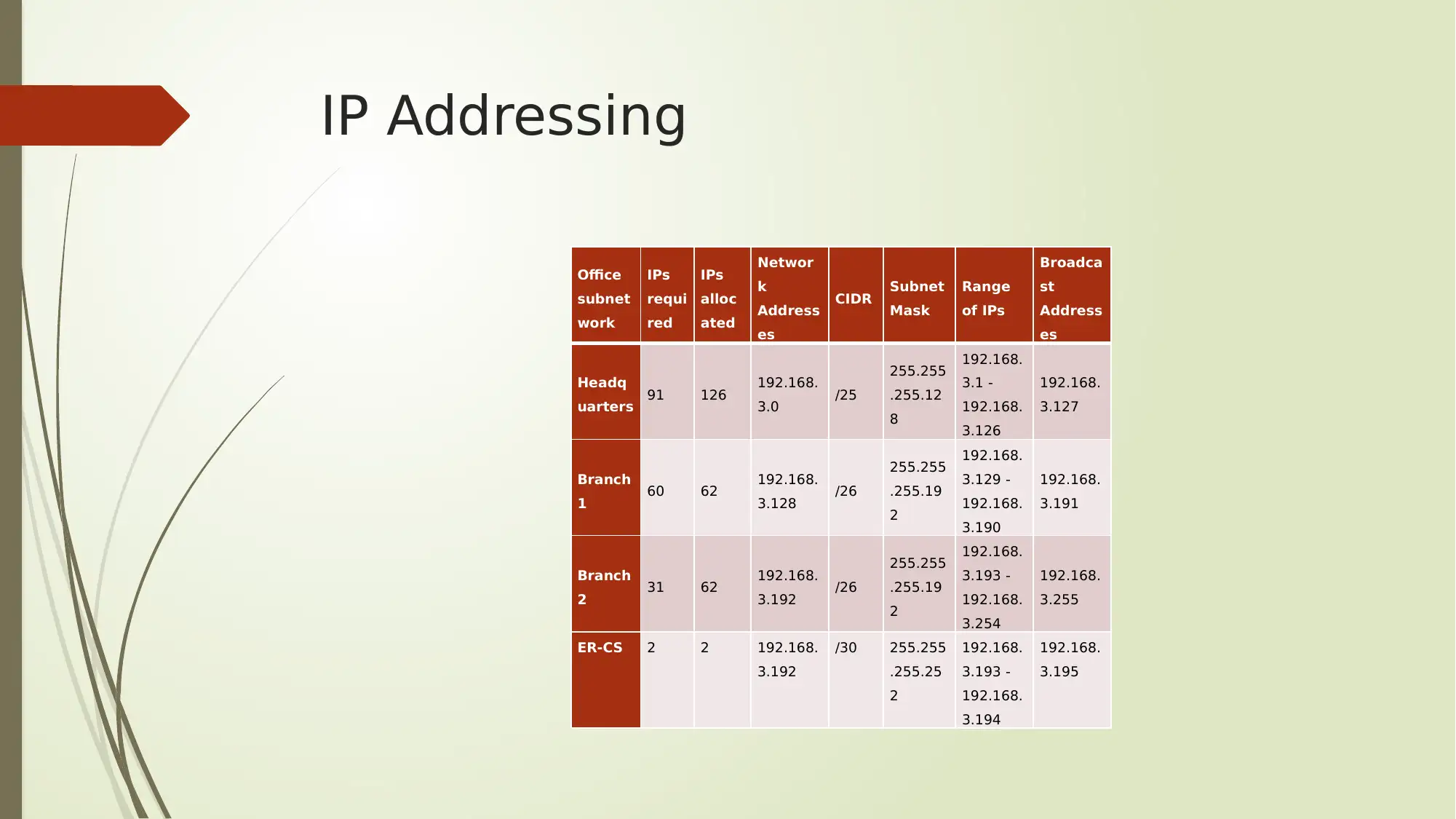
IP Addressing
Office
subnet
work
IPs
requi
red
IPs
alloc
ated
Networ
k
Address
es
CIDR Subnet
Mask
Range
of IPs
Broadca
st
Address
es
Headq
uarters 91 126 192.168.
3.0 /25
255.255
.255.12
8
192.168.
3.1 -
192.168.
3.126
192.168.
3.127
Branch
1 60 62 192.168.
3.128 /26
255.255
.255.19
2
192.168.
3.129 -
192.168.
3.190
192.168.
3.191
Branch
2 31 62 192.168.
3.192 /26
255.255
.255.19
2
192.168.
3.193 -
192.168.
3.254
192.168.
3.255
ER-CS 2 2 192.168.
3.192
/30 255.255
.255.25
2
192.168.
3.193 -
192.168.
3.194
192.168.
3.195
Office
subnet
work
IPs
requi
red
IPs
alloc
ated
Networ
k
Address
es
CIDR Subnet
Mask
Range
of IPs
Broadca
st
Address
es
Headq
uarters 91 126 192.168.
3.0 /25
255.255
.255.12
8
192.168.
3.1 -
192.168.
3.126
192.168.
3.127
Branch
1 60 62 192.168.
3.128 /26
255.255
.255.19
2
192.168.
3.129 -
192.168.
3.190
192.168.
3.191
Branch
2 31 62 192.168.
3.192 /26
255.255
.255.19
2
192.168.
3.193 -
192.168.
3.254
192.168.
3.255
ER-CS 2 2 192.168.
3.192
/30 255.255
.255.25
2
192.168.
3.193 -
192.168.
3.194
192.168.
3.195

Conclusions
In conclusion the presentation successfully assesses the requirements
and talks about the scope and limitations of the project.
The presentation then lists the requirements for setting up the network.
Thereafter the presentation talks about the security measures present in
the network followed by the network diagrams.
After presenting the network, the design is explained and the IP address
allocation is provided.
In conclusion the presentation successfully assesses the requirements
and talks about the scope and limitations of the project.
The presentation then lists the requirements for setting up the network.
Thereafter the presentation talks about the security measures present in
the network followed by the network diagrams.
After presenting the network, the design is explained and the IP address
allocation is provided.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





