BN305 Virtual Private Networks: SSL VPN Technologies Literature Review
VerifiedAdded on 2023/06/11
|8
|1189
|63
Report
AI Summary
This report provides an analytical overview of SSL VPN technologies, addressing key aspects such as web browser and server communication via TCP/IP, digital signatures, and server-to-server communication within a site. It delves into determining cipher suites used by servers and clients, the role of public key integration and symmetric key encryption in transport layer security, and the dangers of relay attacks on encrypted communication channels. The report references various research papers and patents to support its analysis, offering a comprehensive understanding of VPN security and related protocols. Desklib provides access to this and similar solved assignments.

Running head: VIRTUAL PRIVATE NETWORKS
Unit Title: BN305
Virtual Private Networks
Name of the Student:
Name of the University:
Author note:
Unit Title: BN305
Virtual Private Networks
Name of the Student:
Name of the University:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1VIRTUAL PRIVATE NETWORKS
Table of Contents
1.1 Analytical tasks..............................................................................................................3
2.1 Analytical Tasks............................................................................................................4
3.1 Analytical task...............................................................................................................5
References............................................................................................................................7
Table of Contents
1.1 Analytical tasks..............................................................................................................3
2.1 Analytical Tasks............................................................................................................4
3.1 Analytical task...............................................................................................................5
References............................................................................................................................7
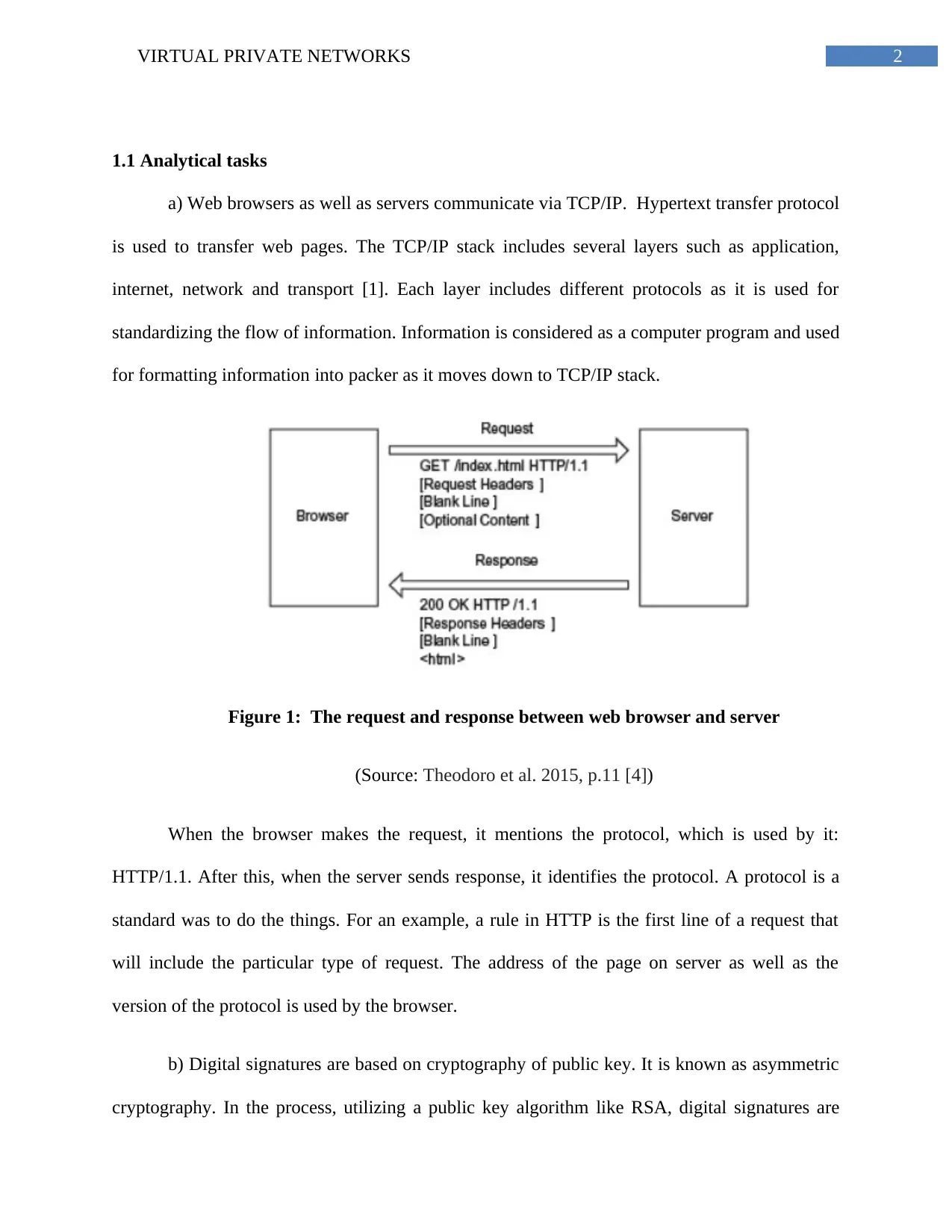
2VIRTUAL PRIVATE NETWORKS
1.1 Analytical tasks
a) Web browsers as well as servers communicate via TCP/IP. Hypertext transfer protocol
is used to transfer web pages. The TCP/IP stack includes several layers such as application,
internet, network and transport [1]. Each layer includes different protocols as it is used for
standardizing the flow of information. Information is considered as a computer program and used
for formatting information into packer as it moves down to TCP/IP stack.
Figure 1: The request and response between web browser and server
(Source: Theodoro et al. 2015, p.11 [4])
When the browser makes the request, it mentions the protocol, which is used by it:
HTTP/1.1. After this, when the server sends response, it identifies the protocol. A protocol is a
standard was to do the things. For an example, a rule in HTTP is the first line of a request that
will include the particular type of request. The address of the page on server as well as the
version of the protocol is used by the browser.
b) Digital signatures are based on cryptography of public key. It is known as asymmetric
cryptography. In the process, utilizing a public key algorithm like RSA, digital signatures are
1.1 Analytical tasks
a) Web browsers as well as servers communicate via TCP/IP. Hypertext transfer protocol
is used to transfer web pages. The TCP/IP stack includes several layers such as application,
internet, network and transport [1]. Each layer includes different protocols as it is used for
standardizing the flow of information. Information is considered as a computer program and used
for formatting information into packer as it moves down to TCP/IP stack.
Figure 1: The request and response between web browser and server
(Source: Theodoro et al. 2015, p.11 [4])
When the browser makes the request, it mentions the protocol, which is used by it:
HTTP/1.1. After this, when the server sends response, it identifies the protocol. A protocol is a
standard was to do the things. For an example, a rule in HTTP is the first line of a request that
will include the particular type of request. The address of the page on server as well as the
version of the protocol is used by the browser.
b) Digital signatures are based on cryptography of public key. It is known as asymmetric
cryptography. In the process, utilizing a public key algorithm like RSA, digital signatures are
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3VIRTUAL PRIVATE NETWORKS
used that help in generating the keys are mathematically link like one private as well as one
public. In order to create digital signature, signing software creates a one-way hash of electronic
data that is signed [2]. The private key is used for encrypting hash. In the process between
connecting web browser and server, the digital signatures verify that is talking directly to the
server and ensure that the server is able to read that is sent back to server.
c) When the exception of communication from the site server to the distribute point,
communication between sever-to-server in a particular site occur at any time and has any use of
mechanism for controlling network bandwidth. Clients initiate communication to the roles of the
system along with active directory domain services [3]. In order to enable the communication,
the firewalls need to allow network traffic between clients as well as endpoints of
communication. With the help of application catalog website point, cloud based resources, it
consists of Microsoft Azure as well as Microsoft Intune that ensure the server is communicating
with the account owner.
d) There are a number of elements engaged in accomplishing the objectives. One of the
major ways for assigning the access permissions to the resources specify the users access the
resources and under the circumstances. Some operating systems can permit Oracle for using
information maintained in order to authenticate users. After authenticated by operating system,
the users connect to Oracle in convenient way without making any type of specification of user
name and password.
2.1 Analytical Tasks
a) In order to determine the cipher suite used by the sever and clients and agreed on, it
required to be familiar with Secure Sockets Layer 2.0 and 3.0 specifications as well as transport
used that help in generating the keys are mathematically link like one private as well as one
public. In order to create digital signature, signing software creates a one-way hash of electronic
data that is signed [2]. The private key is used for encrypting hash. In the process between
connecting web browser and server, the digital signatures verify that is talking directly to the
server and ensure that the server is able to read that is sent back to server.
c) When the exception of communication from the site server to the distribute point,
communication between sever-to-server in a particular site occur at any time and has any use of
mechanism for controlling network bandwidth. Clients initiate communication to the roles of the
system along with active directory domain services [3]. In order to enable the communication,
the firewalls need to allow network traffic between clients as well as endpoints of
communication. With the help of application catalog website point, cloud based resources, it
consists of Microsoft Azure as well as Microsoft Intune that ensure the server is communicating
with the account owner.
d) There are a number of elements engaged in accomplishing the objectives. One of the
major ways for assigning the access permissions to the resources specify the users access the
resources and under the circumstances. Some operating systems can permit Oracle for using
information maintained in order to authenticate users. After authenticated by operating system,
the users connect to Oracle in convenient way without making any type of specification of user
name and password.
2.1 Analytical Tasks
a) In order to determine the cipher suite used by the sever and clients and agreed on, it
required to be familiar with Secure Sockets Layer 2.0 and 3.0 specifications as well as transport
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4VIRTUAL PRIVATE NETWORKS
layer security 1.0 protocol [4]. It is considered as the latest version of SSL 3.0. The following
track is used for demonstrating the process to determine the cipher suite used in secured
communication.
b) Public key integration as well as symmetric key encryption are the functional
cryptographic systems and these are driving force behind the protocol of transport layer security
protocol. Through interacting with the server employing TLS, it can ensured that the information
is sending over the browser client to the server is encrypted in way that the server decrypts it.
The encryption starts after encoding the messages in way that authorized members can read it
[6]. It differs from a hash function of cryptography and in the sense that encrypted message is
intended to be coded as well as decoded in order to reveal initial message. A common as well as
secure method for applications to store the password is the hashed version to store original
password.
3.1 Analytical task
a) In relay attacks, the attackers can intercept as well as resend network packets that are
belong to them. These are considered as extremely dangerous as well as can cause damage. It
makes the types of attacks more noisome and staged on the encrypted channels of
communication without obtaining access to the decryption keys [5]. In addition, attackers have
eavesdrop on the line as well as have general knowledge regarding the tasks of a set of packets
layer security 1.0 protocol [4]. It is considered as the latest version of SSL 3.0. The following
track is used for demonstrating the process to determine the cipher suite used in secured
communication.
b) Public key integration as well as symmetric key encryption are the functional
cryptographic systems and these are driving force behind the protocol of transport layer security
protocol. Through interacting with the server employing TLS, it can ensured that the information
is sending over the browser client to the server is encrypted in way that the server decrypts it.
The encryption starts after encoding the messages in way that authorized members can read it
[6]. It differs from a hash function of cryptography and in the sense that encrypted message is
intended to be coded as well as decoded in order to reveal initial message. A common as well as
secure method for applications to store the password is the hashed version to store original
password.
3.1 Analytical task
a) In relay attacks, the attackers can intercept as well as resend network packets that are
belong to them. These are considered as extremely dangerous as well as can cause damage. It
makes the types of attacks more noisome and staged on the encrypted channels of
communication without obtaining access to the decryption keys [5]. In addition, attackers have
eavesdrop on the line as well as have general knowledge regarding the tasks of a set of packets
5VIRTUAL PRIVATE NETWORKS
that are performing. In addition, the client makes the process of a GET request by typing URL
and page through clicking on the particular link.
that are performing. In addition, the client makes the process of a GET request by typing URL
and page through clicking on the particular link.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6VIRTUAL PRIVATE NETWORKS
References
[1]M. Liyanage and A. Gurtov, "Securing virtual private LAN service by efficient key
management", Security and Communication Networks, vol. 7, no. 1, pp. 1-13, 2013.
[2]M. Rossberg and G. Schaefer, "A survey on automatic configuration of virtual private
networks", Computer Networks, vol. 55, no. 8, pp. 1684-1699, 2011.
[3]Larson, V., Short III, R.D., Munger, E.C. and Williamson, M., VirnetX Inc,. Method for
establishing secure communication link between computers of virtual private network. U.S.
Patent 9,094,399. 2015
[4]Theodoro, L.C., Leite, P.M., de Freitas, H.P., Passos, A.C.S., de Souza Pereira, J.H., de
Oliveira Silva, F., Rosa, P.F. and Cardoso, A.,. Revisiting Virtual Private Network Service at
Carrier Networks: Taking Advantage of Software Defined Networking and Network Function
Virtualisation. ICN 2015, p.84. 2015
[5]Border, J., Dillon, D. and Pardee, P., Hughes Network Systems LLC,. Method and
system for communicating over a segmented virtual private network (VPN). U.S. Patent
8,976,798. 2015
[6]Border, J., Dillon, D. and Pardee, P., Hughes Network Systems LLC,. Method and system for
communicating over a segmented virtual private network (VPN). U.S. Patent 9,832,169. 2017
References
[1]M. Liyanage and A. Gurtov, "Securing virtual private LAN service by efficient key
management", Security and Communication Networks, vol. 7, no. 1, pp. 1-13, 2013.
[2]M. Rossberg and G. Schaefer, "A survey on automatic configuration of virtual private
networks", Computer Networks, vol. 55, no. 8, pp. 1684-1699, 2011.
[3]Larson, V., Short III, R.D., Munger, E.C. and Williamson, M., VirnetX Inc,. Method for
establishing secure communication link between computers of virtual private network. U.S.
Patent 9,094,399. 2015
[4]Theodoro, L.C., Leite, P.M., de Freitas, H.P., Passos, A.C.S., de Souza Pereira, J.H., de
Oliveira Silva, F., Rosa, P.F. and Cardoso, A.,. Revisiting Virtual Private Network Service at
Carrier Networks: Taking Advantage of Software Defined Networking and Network Function
Virtualisation. ICN 2015, p.84. 2015
[5]Border, J., Dillon, D. and Pardee, P., Hughes Network Systems LLC,. Method and
system for communicating over a segmented virtual private network (VPN). U.S. Patent
8,976,798. 2015
[6]Border, J., Dillon, D. and Pardee, P., Hughes Network Systems LLC,. Method and system for
communicating over a segmented virtual private network (VPN). U.S. Patent 9,832,169. 2017
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7VIRTUAL PRIVATE NETWORKS
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





