Project: Virtualization Implementation for Google Cloud Security
VerifiedAdded on 2020/04/13
|7
|872
|158
Project
AI Summary
This project focuses on implementing virtualization within Google Cloud operations to enhance client data security and build customer trust. It explores both hardware-based (e.g., ESX Server) and software-based (e.g., VMware GSX Server) virtualization approaches. The project details potential risks, such as unauthorized hypervisor access and lack of network visibility, and proposes a 24-week timeline for completion, including data collection, approach selection, budget review, and final implementation. The project aims to develop a robust risk management strategy to ensure optimal data security post-virtualization, referencing relevant academic sources.

Running head: VIRTUALIZATION FOR GOOGLE CLOUD
VIRTUALIZATION FOR GOOGLE CLOUD
Name of the student:
Name of the university:
Author note:
VIRTUALIZATION FOR GOOGLE CLOUD
Name of the student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1VIRTUALIZATION FOR GOOGLE CLOUD
Table of Contents
Expected deliverables of the project:...............................................................................................2
Approach towards the solution:.......................................................................................................2
Hardware based approach:...........................................................................................................2
Software based approach:............................................................................................................3
Potential risks associated to virtualization of Google cloud:...........................................................4
Proposed study timeline:..................................................................................................................4
References:......................................................................................................................................6
Table of Contents
Expected deliverables of the project:...............................................................................................2
Approach towards the solution:.......................................................................................................2
Hardware based approach:...........................................................................................................2
Software based approach:............................................................................................................3
Potential risks associated to virtualization of Google cloud:...........................................................4
Proposed study timeline:..................................................................................................................4
References:......................................................................................................................................6

2VIRTUALIZATION FOR GOOGLE CLOUD
Expected deliverables of the project:
This project aims to implement virtualization within the working operations of Google
cloud. Virtualization will enhance the security of the client data that is stored in the Google cloud
servers and at the same time help in building the customer trust thereby ensuring improved client
satisfaction. The Project will also help in developing a proper risk management strategy in to
ensure optimum data security post the implementation of virtualization in Google cloud.
Approach towards the solution:
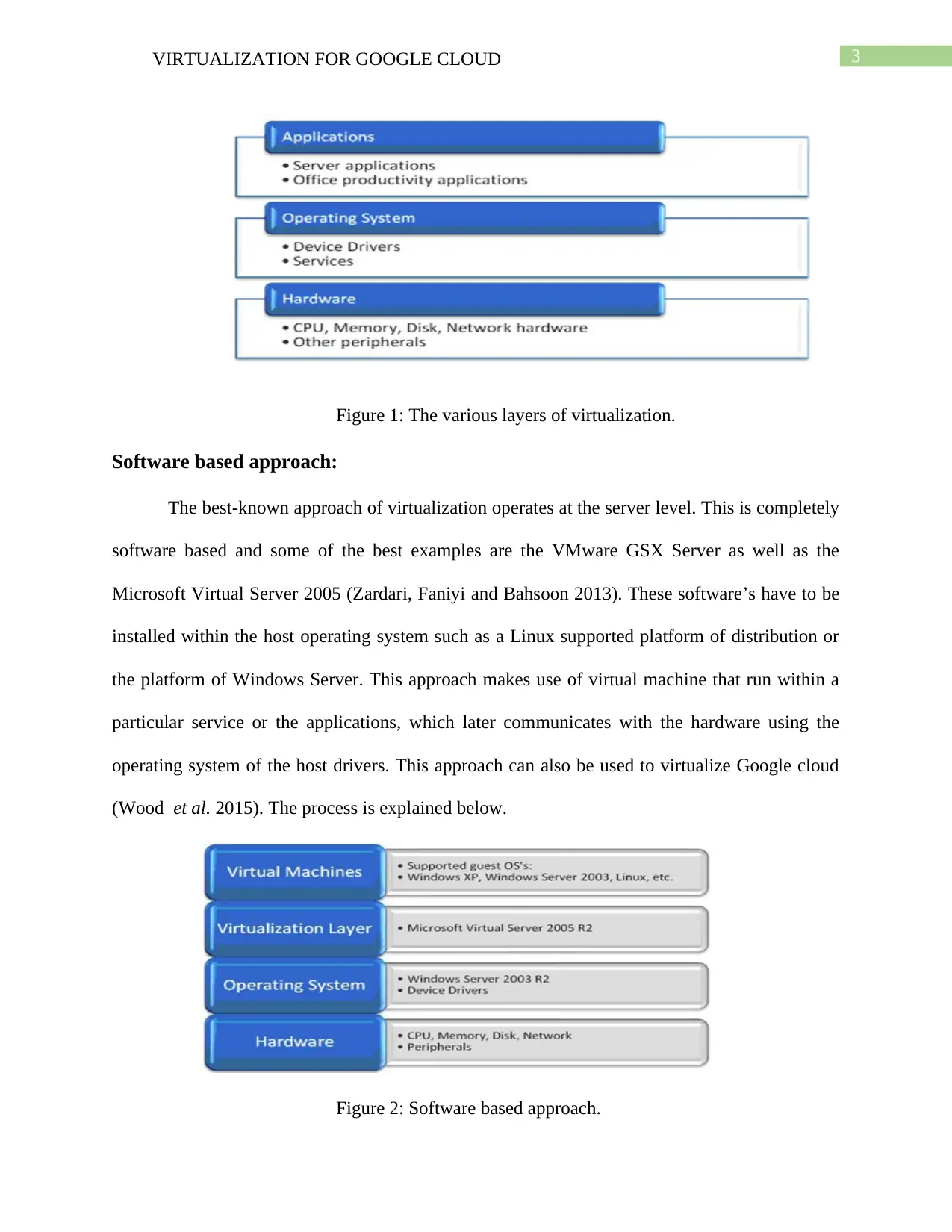
Virtualization can be applied to a vast range of technologies within Google cloud. For
instance, data storage systems, databases as well as organizational networks can all be
virtualized. Server virtualization is also possible which allows different operating systems to run
on a common hardware platform simultaneously. There are two commonly used approaches of
virtualization, which are hardware based and software based. They are explained below as:
Hardware based approach:
Theoretically, virtualization platforms running directly on the hardware base provide the
best possible performance by minimizing the overhead (ESX Server from VM ware). ESX
Server The administration can be performed using an internet-based application that is accessed
via a Web browser. A hypervisor runs directly between the operating system as well as the
hardware and is a very thin layer (Cheng et al. 2017). The aim of this approach is avoiding the
overhead associated to the host operating system. The steps of the hardware-based approach is
explained below:
Expected deliverables of the project:
This project aims to implement virtualization within the working operations of Google
cloud. Virtualization will enhance the security of the client data that is stored in the Google cloud
servers and at the same time help in building the customer trust thereby ensuring improved client
satisfaction. The Project will also help in developing a proper risk management strategy in to
ensure optimum data security post the implementation of virtualization in Google cloud.
Approach towards the solution:
Virtualization can be applied to a vast range of technologies within Google cloud. For
instance, data storage systems, databases as well as organizational networks can all be
virtualized. Server virtualization is also possible which allows different operating systems to run
on a common hardware platform simultaneously. There are two commonly used approaches of
virtualization, which are hardware based and software based. They are explained below as:
Hardware based approach:
Theoretically, virtualization platforms running directly on the hardware base provide the
best possible performance by minimizing the overhead (ESX Server from VM ware). ESX
Server The administration can be performed using an internet-based application that is accessed
via a Web browser. A hypervisor runs directly between the operating system as well as the
hardware and is a very thin layer (Cheng et al. 2017). The aim of this approach is avoiding the
overhead associated to the host operating system. The steps of the hardware-based approach is
explained below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3VIRTUALIZATION FOR GOOGLE CLOUD
Figure 1: The various layers of virtualization.
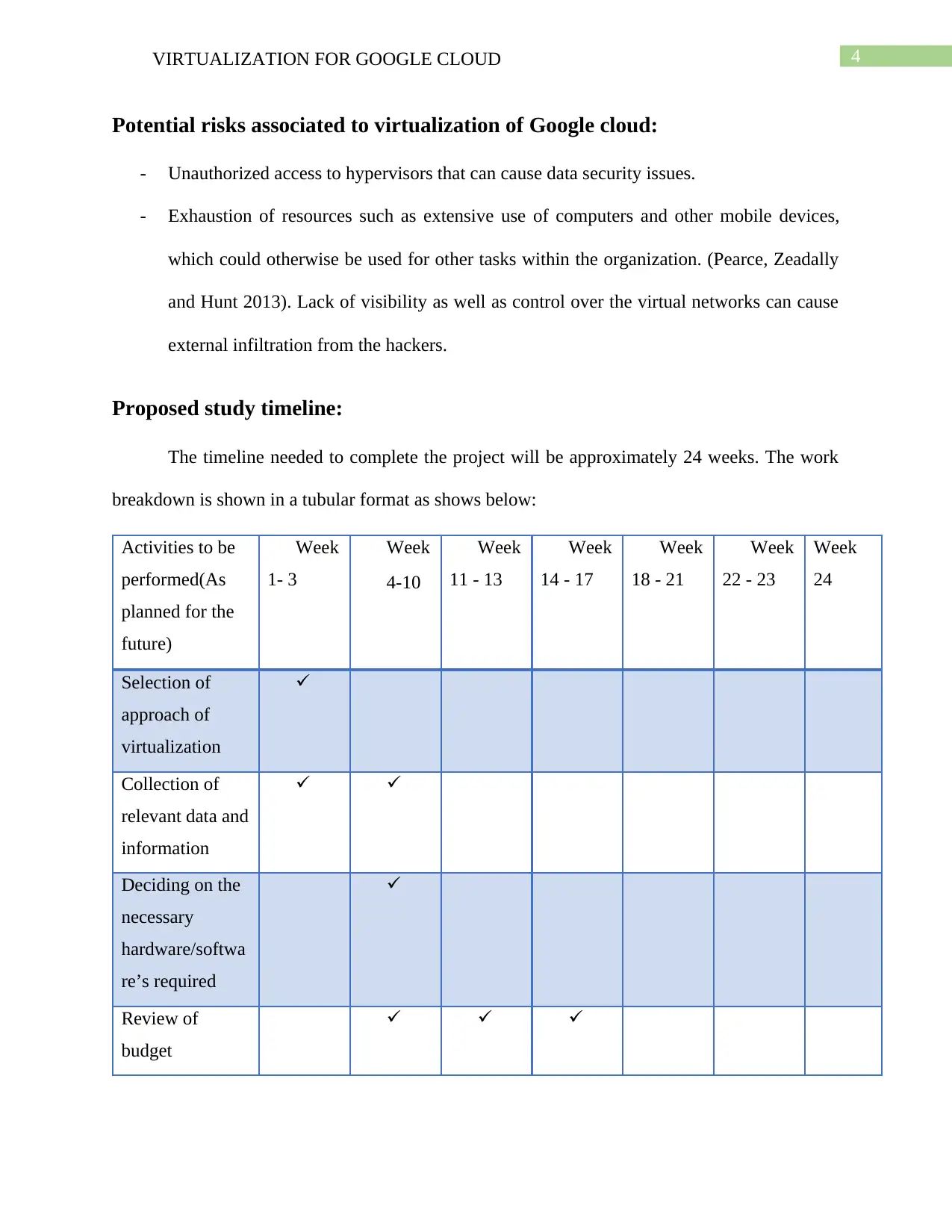
Software based approach:
The best-known approach of virtualization operates at the server level. This is completely
software based and some of the best examples are the VMware GSX Server as well as the
Microsoft Virtual Server 2005 (Zardari, Faniyi and Bahsoon 2013). These software’s have to be
installed within the host operating system such as a Linux supported platform of distribution or
the platform of Windows Server. This approach makes use of virtual machine that run within a
particular service or the applications, which later communicates with the hardware using the
operating system of the host drivers. This approach can also be used to virtualize Google cloud
(Wood et al. 2015). The process is explained below.
Figure 2: Software based approach.
Figure 1: The various layers of virtualization.
Software based approach:
The best-known approach of virtualization operates at the server level. This is completely
software based and some of the best examples are the VMware GSX Server as well as the
Microsoft Virtual Server 2005 (Zardari, Faniyi and Bahsoon 2013). These software’s have to be
installed within the host operating system such as a Linux supported platform of distribution or
the platform of Windows Server. This approach makes use of virtual machine that run within a
particular service or the applications, which later communicates with the hardware using the
operating system of the host drivers. This approach can also be used to virtualize Google cloud
(Wood et al. 2015). The process is explained below.
Figure 2: Software based approach.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4VIRTUALIZATION FOR GOOGLE CLOUD
Potential risks associated to virtualization of Google cloud:
- Unauthorized access to hypervisors that can cause data security issues.
- Exhaustion of resources such as extensive use of computers and other mobile devices,
which could otherwise be used for other tasks within the organization. (Pearce, Zeadally
and Hunt 2013). Lack of visibility as well as control over the virtual networks can cause
external infiltration from the hackers.
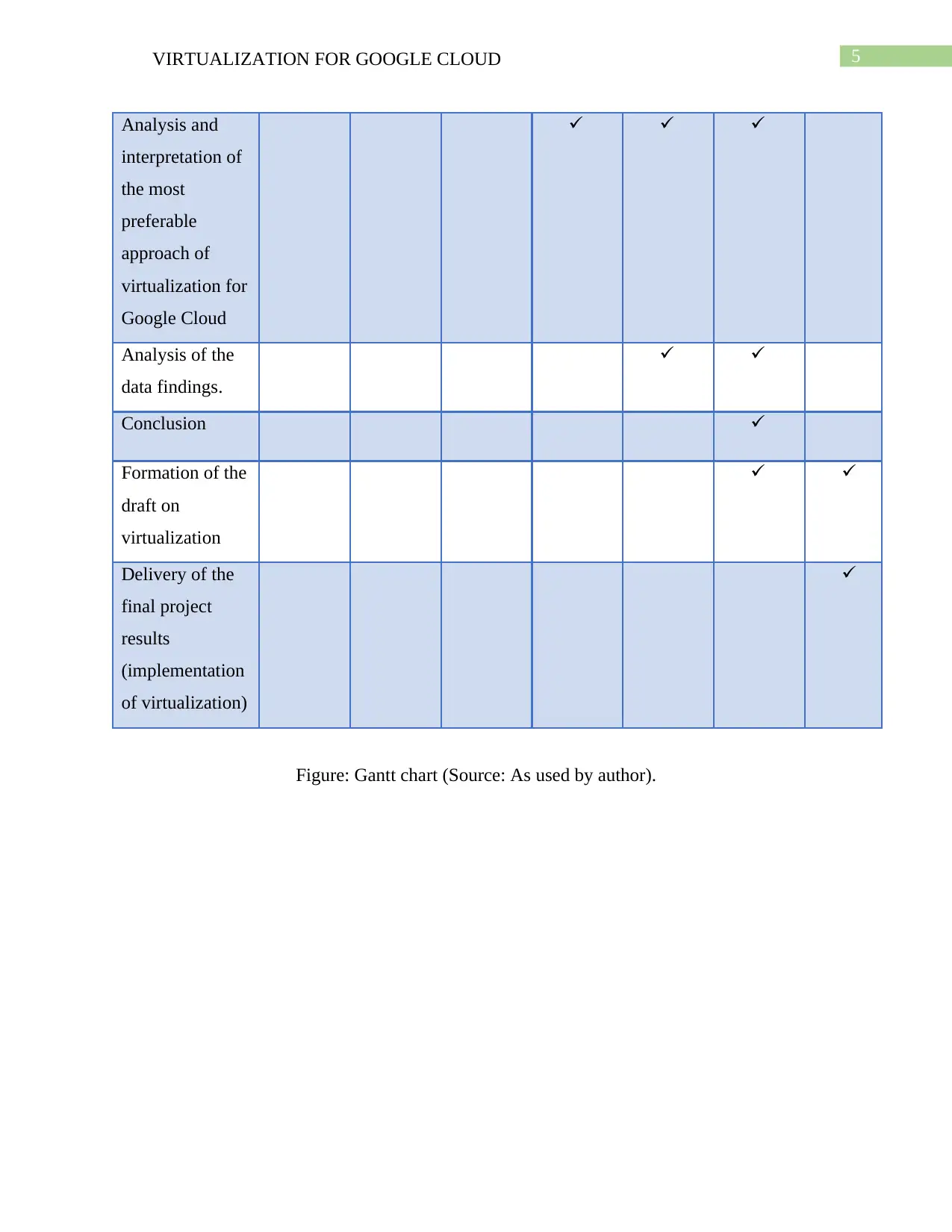
Proposed study timeline:
The timeline needed to complete the project will be approximately 24 weeks. The work
breakdown is shown in a tubular format as shows below:
Activities to be
performed(As
planned for the
future)
Week
1- 3
Week
4-10
Week
11 - 13
Week
14 - 17
Week
18 - 21
Week
22 - 23
Week
24
Selection of
approach of
virtualization
Collection of
relevant data and
information
Deciding on the
necessary
hardware/softwa
re’s required
Review of
budget
Potential risks associated to virtualization of Google cloud:
- Unauthorized access to hypervisors that can cause data security issues.
- Exhaustion of resources such as extensive use of computers and other mobile devices,
which could otherwise be used for other tasks within the organization. (Pearce, Zeadally
and Hunt 2013). Lack of visibility as well as control over the virtual networks can cause
external infiltration from the hackers.
Proposed study timeline:
The timeline needed to complete the project will be approximately 24 weeks. The work
breakdown is shown in a tubular format as shows below:
Activities to be
performed(As
planned for the
future)
Week
1- 3
Week
4-10
Week
11 - 13
Week
14 - 17
Week
18 - 21
Week
22 - 23
Week
24
Selection of
approach of
virtualization
Collection of
relevant data and
information
Deciding on the
necessary
hardware/softwa
re’s required
Review of
budget
5VIRTUALIZATION FOR GOOGLE CLOUD
Analysis and
interpretation of
the most
preferable
approach of
virtualization for
Google Cloud
Analysis of the
data findings.
Conclusion
Formation of the
draft on
virtualization
Delivery of the
final project
results
(implementation
of virtualization)
Figure: Gantt chart (Source: As used by author).
Analysis and
interpretation of
the most
preferable
approach of
virtualization for
Google Cloud
Analysis of the
data findings.
Conclusion
Formation of the
draft on
virtualization
Delivery of the
final project
results
(implementation
of virtualization)
Figure: Gantt chart (Source: As used by author).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6VIRTUALIZATION FOR GOOGLE CLOUD
References:
Cheng, Y., Fu, X., Du, X., Luo, B. and Guizani, M., 2017. A lightweight live memory forensic
approach based on hardware virtualization. Information Sciences, 379, pp.23-41.
Pearce, M., Zeadally, S. and Hunt, R., 2013. Virtualization: Issues, security threats, and
solutions. ACM Computing Surveys (CSUR), 45(2), p.17.
Wood, T., Ramakrishnan, K.K., Hwang, J., Liu, G. and Zhang, W., 2015. Toward a software-
based network: integrating software defined networking and network function virtualization.
IEEE Network, 29(3), pp.36-41.
Zardari, S., Faniyi, F. and Bahsoon, R., 2013. Using obstacles for systematically modeling,
analysing, and mitigating risks in cloud adoption. In Aligning Enterprise, System, and Software
Architectures (pp. 275-296). IGI Global.
References:
Cheng, Y., Fu, X., Du, X., Luo, B. and Guizani, M., 2017. A lightweight live memory forensic
approach based on hardware virtualization. Information Sciences, 379, pp.23-41.
Pearce, M., Zeadally, S. and Hunt, R., 2013. Virtualization: Issues, security threats, and
solutions. ACM Computing Surveys (CSUR), 45(2), p.17.
Wood, T., Ramakrishnan, K.K., Hwang, J., Liu, G. and Zhang, W., 2015. Toward a software-
based network: integrating software defined networking and network function virtualization.
IEEE Network, 29(3), pp.36-41.
Zardari, S., Faniyi, F. and Bahsoon, R., 2013. Using obstacles for systematically modeling,
analysing, and mitigating risks in cloud adoption. In Aligning Enterprise, System, and Software
Architectures (pp. 275-296). IGI Global.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





