CO4509 Computer Security: VM Security Investigation & Proposal
VerifiedAdded on 2023/06/11
|17
|3681
|185
Report
AI Summary
This report details a security investigation of a VMware virtual machine provided by Benny Vandergast Inc to WidgetsInc for testing a new web-based store. The investigation reveals a lack of password protection on the "Administrator" account, making the system vulnerable. The report outlines the steps taken to discover usernames and passwords, including using tools like mimikatz and nmap. SQL injection vulnerabilities were also identified. To secure the system, the report proposes implementing a firewall, securing open ports, and enforcing stronger password policies. It also discusses the importance of segregation of duties and monitoring virtual machine usage to prevent unauthorized access. The report concludes with recommendations for improving the overall security posture of the virtual machine.

Running head: COMPUTER SECURITY
CO4509 – Computer Security
Assignment 2
Name of the Student:
Name of the University:
CO4509 – Computer Security
Assignment 2
Name of the Student:
Name of the University:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1COMPUTER SECURITY
Table of Contents
Introduction......................................................................................................................................2
Description of investigation procedure for security of the system..................................................2
Description of the obtained results..................................................................................................6
Proposal to secure the system..........................................................................................................8
Conclusion.....................................................................................................................................13
References......................................................................................................................................15
Table of Contents
Introduction......................................................................................................................................2
Description of investigation procedure for security of the system..................................................2
Description of the obtained results..................................................................................................6
Proposal to secure the system..........................................................................................................8
Conclusion.....................................................................................................................................13
References......................................................................................................................................15

2COMPUTER SECURITY
Introduction
This report based on investigating the security of a VMware virtual machine being
provided by Benny Vandergast Inc to WidgetsInc for testing as they have decided to develop
their new web-based store. In this report, the discussion are carried out on the security evaluation
of the virtual machine image being provided by Benny Vandergast Inc. The focus of the report is
to demonstrate the results that has been gathered from security evaluation of the system. The
purpose of this investigation is to discover the usernames and passwords in the system along
with testing security of the system. Further, some suggestions are also provided to secure the
system from the identified issues.
Description of investigation procedure for security of the system
In the provided virtual machine image provided by Benny Vandergast Inc, it has been
identified that the “Administrator” account is not secured with any password so it was easier to
gain access to the system. The access to SAM accounts could have been gained through the
administrator account which was possible to be decrypted with the help of password dumping
tool that is mimikatz or impacket (Rehman et al. 2014). As the administrator password is empty,
it would have been easier to export and the get access to the SAM file. The SAM (Security
Account Manager) is a database file within system which contains the information of users and
cryptographic measures are being used by SAM to restrict unauthorized access to the system
(Win, Tianfield and Mair 2014). However, the steps that has been followed for investigating the
provided system for security issues along with finding the usernames and passwords is discussed
in details with the help of screenshots. Installation of the VMM in the system will also enable the
evaluation of the virtual firewall because the virtual firewall switches are unable to work without
Introduction
This report based on investigating the security of a VMware virtual machine being
provided by Benny Vandergast Inc to WidgetsInc for testing as they have decided to develop
their new web-based store. In this report, the discussion are carried out on the security evaluation
of the virtual machine image being provided by Benny Vandergast Inc. The focus of the report is
to demonstrate the results that has been gathered from security evaluation of the system. The
purpose of this investigation is to discover the usernames and passwords in the system along
with testing security of the system. Further, some suggestions are also provided to secure the
system from the identified issues.
Description of investigation procedure for security of the system
In the provided virtual machine image provided by Benny Vandergast Inc, it has been
identified that the “Administrator” account is not secured with any password so it was easier to
gain access to the system. The access to SAM accounts could have been gained through the
administrator account which was possible to be decrypted with the help of password dumping
tool that is mimikatz or impacket (Rehman et al. 2014). As the administrator password is empty,
it would have been easier to export and the get access to the SAM file. The SAM (Security
Account Manager) is a database file within system which contains the information of users and
cryptographic measures are being used by SAM to restrict unauthorized access to the system
(Win, Tianfield and Mair 2014). However, the steps that has been followed for investigating the
provided system for security issues along with finding the usernames and passwords is discussed
in details with the help of screenshots. Installation of the VMM in the system will also enable the
evaluation of the virtual firewall because the virtual firewall switches are unable to work without
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3COMPUTER SECURITY
the assistance of the hypervisor/VMM. Hence, it is important to develop effective system that
can be helpful for the organization.
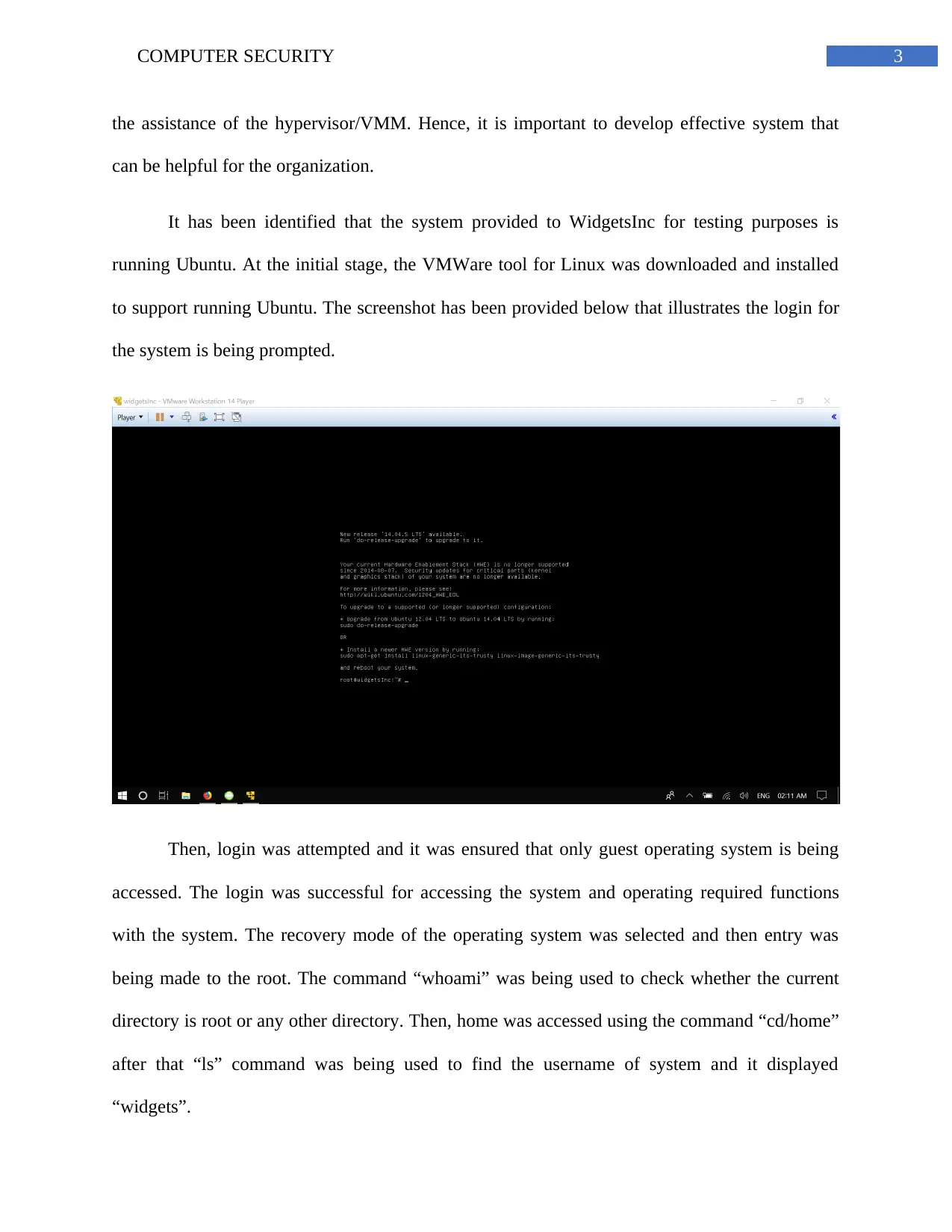
It has been identified that the system provided to WidgetsInc for testing purposes is
running Ubuntu. At the initial stage, the VMWare tool for Linux was downloaded and installed
to support running Ubuntu. The screenshot has been provided below that illustrates the login for
the system is being prompted.
Then, login was attempted and it was ensured that only guest operating system is being
accessed. The login was successful for accessing the system and operating required functions
with the system. The recovery mode of the operating system was selected and then entry was
being made to the root. The command “whoami” was being used to check whether the current
directory is root or any other directory. Then, home was accessed using the command “cd/home”
after that “ls” command was being used to find the username of system and it displayed
“widgets”.
the assistance of the hypervisor/VMM. Hence, it is important to develop effective system that
can be helpful for the organization.
It has been identified that the system provided to WidgetsInc for testing purposes is
running Ubuntu. At the initial stage, the VMWare tool for Linux was downloaded and installed
to support running Ubuntu. The screenshot has been provided below that illustrates the login for
the system is being prompted.
Then, login was attempted and it was ensured that only guest operating system is being
accessed. The login was successful for accessing the system and operating required functions
with the system. The recovery mode of the operating system was selected and then entry was
being made to the root. The command “whoami” was being used to check whether the current
directory is root or any other directory. Then, home was accessed using the command “cd/home”
after that “ls” command was being used to find the username of system and it displayed
“widgets”.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4COMPUTER SECURITY
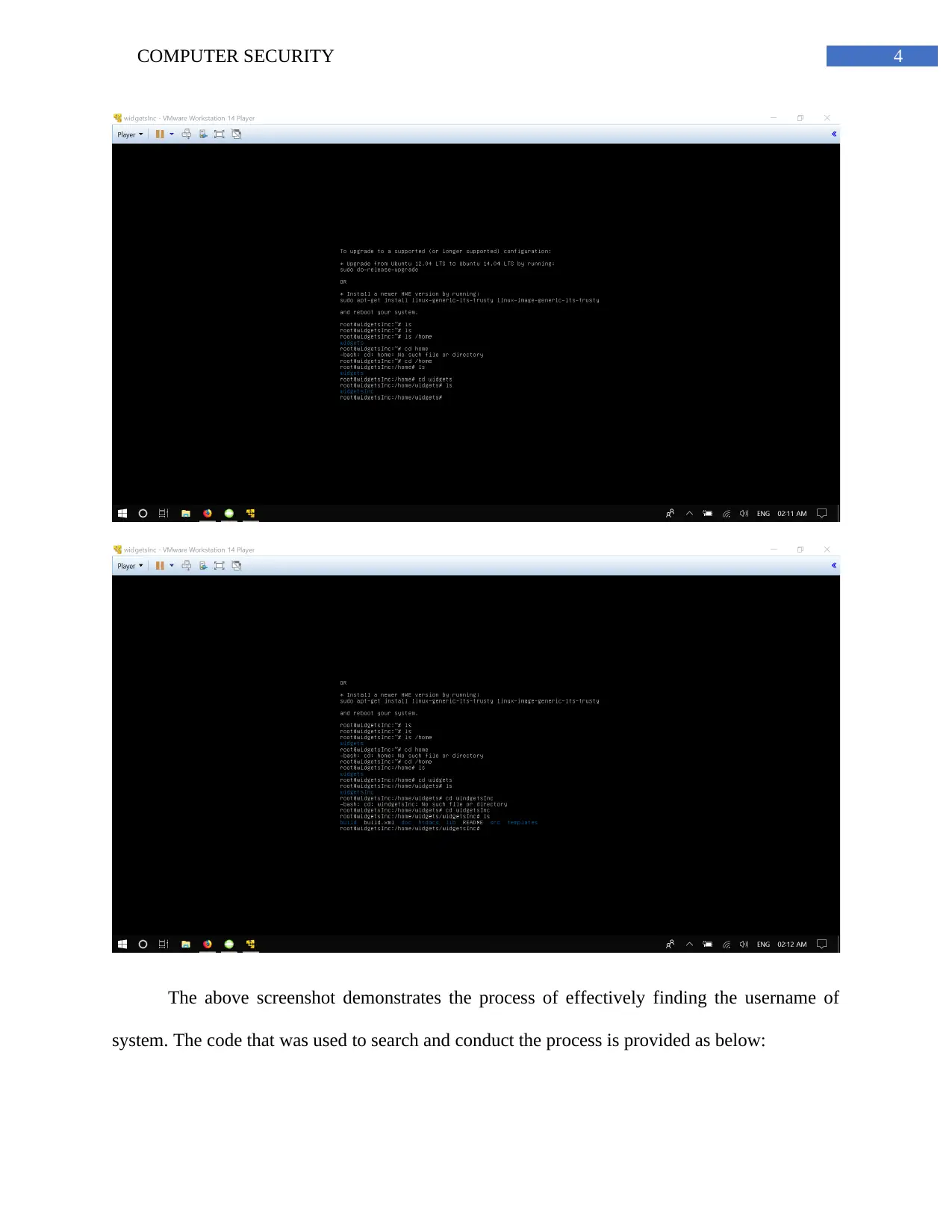
The above screenshot demonstrates the process of effectively finding the username of
system. The code that was used to search and conduct the process is provided as below:
The above screenshot demonstrates the process of effectively finding the username of
system. The code that was used to search and conduct the process is provided as below:
5COMPUTER SECURITY
Shutdown: init 0. Shutdown –h now. –a: Use file/etc/shutdown.allow. –c: Cancel
scheduled shutdown. Halt –p. –p: Turn power off after shutdown. poweroff.
Reboot: init 6. Shutdown –r now. Reboot.
Enter single user mode: init 1
Check current runlevel: runlevel.
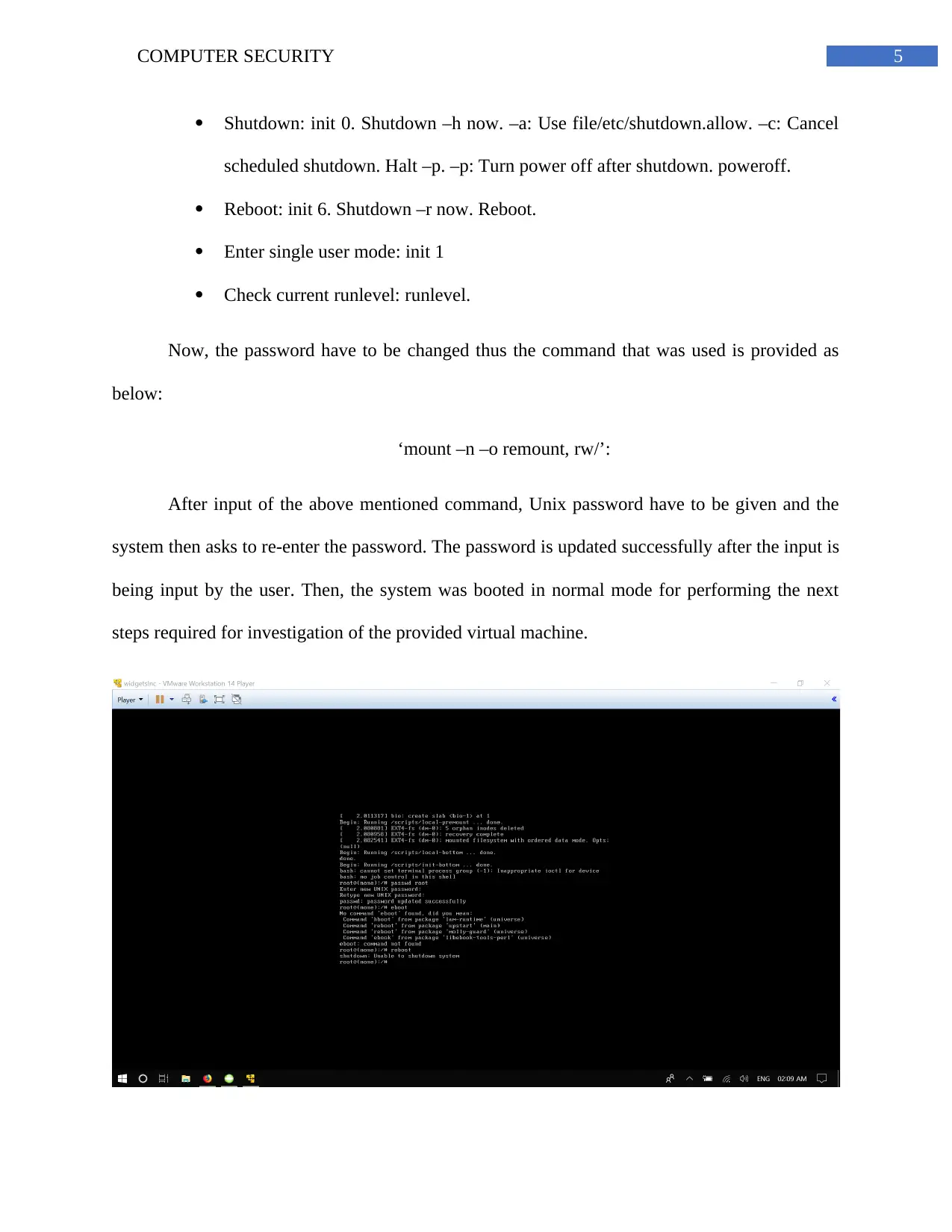
Now, the password have to be changed thus the command that was used is provided as
below:
‘mount –n –o remount, rw/’:
After input of the above mentioned command, Unix password have to be given and the
system then asks to re-enter the password. The password is updated successfully after the input is
being input by the user. Then, the system was booted in normal mode for performing the next
steps required for investigation of the provided virtual machine.
Shutdown: init 0. Shutdown –h now. –a: Use file/etc/shutdown.allow. –c: Cancel
scheduled shutdown. Halt –p. –p: Turn power off after shutdown. poweroff.
Reboot: init 6. Shutdown –r now. Reboot.
Enter single user mode: init 1
Check current runlevel: runlevel.
Now, the password have to be changed thus the command that was used is provided as
below:
‘mount –n –o remount, rw/’:
After input of the above mentioned command, Unix password have to be given and the
system then asks to re-enter the password. The password is updated successfully after the input is
being input by the user. Then, the system was booted in normal mode for performing the next
steps required for investigation of the provided virtual machine.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6COMPUTER SECURITY
Now, the system is logged in using the credentials set for the system and the IP address
has been discovered using the ‘ifconfig’ command. The command helped to gather details about
IP address of the system. Then, the present condition of the virtual machine was checked to
determine whether it is connected to the internet facility. The status of the device can be
achieved from the virtual machine settings.
The nmap tool helped to find the details of particular ports to check whether those or
open or closed. The information was easily collected as the operating system of the machine was
UNIX. The needed requirements were installed accordingly for using the “nmap” command as it
requires different repositories. The code used to install nmap is provided as below:
‘sudo apt-get install nmap’.
The nmap command was used with identified IP address of the system and then manual
IP address was assigned to the system for the checking the process and finally, it was connected
to the IP address.
Description of the obtained results
The results obtained from the investigation shows that there is weak password protection
policy being enforced in the system. The weak password policy has helped to acquire the
usernames and passwords in the system. First and the foremost important threat that has been
identified is that the “Administrator” account is not secured with any password and it is open to
all so that anyone can get access to the system. The administrator password has been left empty
and it can be seen in the image below:
Now, the system is logged in using the credentials set for the system and the IP address
has been discovered using the ‘ifconfig’ command. The command helped to gather details about
IP address of the system. Then, the present condition of the virtual machine was checked to
determine whether it is connected to the internet facility. The status of the device can be
achieved from the virtual machine settings.
The nmap tool helped to find the details of particular ports to check whether those or
open or closed. The information was easily collected as the operating system of the machine was
UNIX. The needed requirements were installed accordingly for using the “nmap” command as it
requires different repositories. The code used to install nmap is provided as below:
‘sudo apt-get install nmap’.
The nmap command was used with identified IP address of the system and then manual
IP address was assigned to the system for the checking the process and finally, it was connected
to the IP address.
Description of the obtained results
The results obtained from the investigation shows that there is weak password protection
policy being enforced in the system. The weak password policy has helped to acquire the
usernames and passwords in the system. First and the foremost important threat that has been
identified is that the “Administrator” account is not secured with any password and it is open to
all so that anyone can get access to the system. The administrator password has been left empty
and it can be seen in the image below:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7COMPUTER SECURITY
The “Empty” word in password column shown in the above figure shows that the system
is vulnerable to the attacks as anyone can easily gain access and steal valuable information. The
security of administrator account is required to ensure security of the entire system. An attacker
may easily get into the system and operate it as per their requirement.
In the provided virtual machine, it has been identified that SQL injection could be easily
performed on the system which is used by attackers for accessing resources of the system. This
method is a type of attack method which is mainly used for data driven applications (Ibrahim,
Hamlyn-Harris and Grundy 2016). Hence, for maintaining security of the system, it is essential
that process have to be integrated such that recovery could be easily carried out in case of SQL
vulnerabilities. The testing for SQL vulnerabilities have to be done on a regular basis so that
commands can be sent as communication requests and the attackers are not able to gain access to
the database.
The “Empty” word in password column shown in the above figure shows that the system
is vulnerable to the attacks as anyone can easily gain access and steal valuable information. The
security of administrator account is required to ensure security of the entire system. An attacker
may easily get into the system and operate it as per their requirement.
In the provided virtual machine, it has been identified that SQL injection could be easily
performed on the system which is used by attackers for accessing resources of the system. This
method is a type of attack method which is mainly used for data driven applications (Ibrahim,
Hamlyn-Harris and Grundy 2016). Hence, for maintaining security of the system, it is essential
that process have to be integrated such that recovery could be easily carried out in case of SQL
vulnerabilities. The testing for SQL vulnerabilities have to be done on a regular basis so that
commands can be sent as communication requests and the attackers are not able to gain access to
the database.

8COMPUTER SECURITY
The vulnerability testing of the provided system was done int two different phases in
which first phase was conducted using Ubuntu terminal. The credentials that is username and
password were provided accordingly and SQL injection was performed to check the
vulnerabilities of the system (Felter et al. 2015). The web server was accessed by using the login
page using IP address of the system. Secondly, Http request method was being used by following
the GET method because and as it shows username and password details in the URL so it is not
suitable for sensitive information. The test results showed that there are security loopholes in the
system which is making it vulnerable to SQL injection attacks.
Proposal to secure the system
From the testing done on provided virtual machine by Benny Vandergast Inc, it has been
found that the system has very low security and proper measures have not been implemented to
secure the virtual machine. Therefore, there is a need to increase the security by implementing
suitable measures to avoid malicious attacks or hacking of confidential information. The user
information is also valuable for the organization so security have to be implemented properly to
secure sensitive information.
The implementation of firewall will help to increase security of the system so that it is not
prone to external attacks. The firewall will check the incoming requests and block if any
malicious information is found to avoid unauthorized access to the system (Ahmad et al. 2015).
The firewall have to be updated on a regular basis so that recent threats can be also identified in
the incoming requests. The configuration of firewall with UFW will help to easily create IPV4
firewall and hence, there is a need to enable UFW in the system. For .enabling UFW on a
system, the following command have to be entered as shown in the attached screenshot:
The vulnerability testing of the provided system was done int two different phases in
which first phase was conducted using Ubuntu terminal. The credentials that is username and
password were provided accordingly and SQL injection was performed to check the
vulnerabilities of the system (Felter et al. 2015). The web server was accessed by using the login
page using IP address of the system. Secondly, Http request method was being used by following
the GET method because and as it shows username and password details in the URL so it is not
suitable for sensitive information. The test results showed that there are security loopholes in the
system which is making it vulnerable to SQL injection attacks.
Proposal to secure the system
From the testing done on provided virtual machine by Benny Vandergast Inc, it has been
found that the system has very low security and proper measures have not been implemented to
secure the virtual machine. Therefore, there is a need to increase the security by implementing
suitable measures to avoid malicious attacks or hacking of confidential information. The user
information is also valuable for the organization so security have to be implemented properly to
secure sensitive information.
The implementation of firewall will help to increase security of the system so that it is not
prone to external attacks. The firewall will check the incoming requests and block if any
malicious information is found to avoid unauthorized access to the system (Ahmad et al. 2015).
The firewall have to be updated on a regular basis so that recent threats can be also identified in
the incoming requests. The configuration of firewall with UFW will help to easily create IPV4
firewall and hence, there is a need to enable UFW in the system. For .enabling UFW on a
system, the following command have to be entered as shown in the attached screenshot:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9COMPUTER SECURITY
Now, the ports have to be secured as Port 22 is open and therefore, it is more vulnerable
to attacks. Therefore, it is required that the port have to be secured using SSH. For allowing SSH
in port 22, the command that have to be used is provided and the update rules for port 22 is
shown as below:
“sudo ufw enable”
Next, for stopping the SSH service in port 22, the command that have to be input for
checking the updated rules is displayed as below:
The conflict is generally caused through combination of the system as well as underlying
virtual machine monitor. The security services require reason regarding guest VM state on the
higher level. The challenges for the security services have malicious software that has
Now, the ports have to be secured as Port 22 is open and therefore, it is more vulnerable
to attacks. Therefore, it is required that the port have to be secured using SSH. For allowing SSH
in port 22, the command that have to be used is provided and the update rules for port 22 is
shown as below:
“sudo ufw enable”
Next, for stopping the SSH service in port 22, the command that have to be input for
checking the updated rules is displayed as below:
The conflict is generally caused through combination of the system as well as underlying
virtual machine monitor. The security services require reason regarding guest VM state on the
higher level. The challenges for the security services have malicious software that has
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10COMPUTER SECURITY
fingerprint virtual machines. The virtual machines running security services could hurt security
system. For an instance, VM-based logging tool Revirt has log system. It is one of the security
concerns for several organizations. The capabilities of virtual machines develop attractive to
develop an instruction detection system. Software running is considered as virtual machine that
cannot have access for that. Presence of privileged instructions forces allow the existing
conventional system. A simple counter measure is important for primary human input
collaboration so that the system cant benefits.
Separation and deployment of the duties
One of the basic tenets of the Information system (IS) is segregation and deployment of
the duties. It enables the system to restrict unauthorized use of the system by limiting the
accessibility of the privileged users to their task requirement. Hence taking the basis of the
above-mentioned statement another vulnerability of the security that needs to be identified has
been detected (Ahmed et al. 2015). The discussed vulnerability is the difficulty level associated
with the segregation of the duty. To identify the discussed threat the SSH administrative console
access can be used. Additionally, the firewall filters rules that limit the administrative
virtualization console. Doing so will identify the predetermination, authorization and the internal
network addresses that are vulnerable to the outside attacks.
Another potential measure that can be adopted to identify the discussed security
vulnerability is adoption of the system that is capable of checking and balances with the
processes that are associated with the split functions and the capable of enforcing dual controls
for the crucial duties. Verification of the approval processes for development of the new virtual
machine and migration of the new application to other virtual machines can be evaluated.
Additionally, the verification on existence of the auditing and monitoring log of the virtual
fingerprint virtual machines. The virtual machines running security services could hurt security
system. For an instance, VM-based logging tool Revirt has log system. It is one of the security
concerns for several organizations. The capabilities of virtual machines develop attractive to
develop an instruction detection system. Software running is considered as virtual machine that
cannot have access for that. Presence of privileged instructions forces allow the existing
conventional system. A simple counter measure is important for primary human input
collaboration so that the system cant benefits.
Separation and deployment of the duties
One of the basic tenets of the Information system (IS) is segregation and deployment of
the duties. It enables the system to restrict unauthorized use of the system by limiting the
accessibility of the privileged users to their task requirement. Hence taking the basis of the
above-mentioned statement another vulnerability of the security that needs to be identified has
been detected (Ahmed et al. 2015). The discussed vulnerability is the difficulty level associated
with the segregation of the duty. To identify the discussed threat the SSH administrative console
access can be used. Additionally, the firewall filters rules that limit the administrative
virtualization console. Doing so will identify the predetermination, authorization and the internal
network addresses that are vulnerable to the outside attacks.
Another potential measure that can be adopted to identify the discussed security
vulnerability is adoption of the system that is capable of checking and balances with the
processes that are associated with the split functions and the capable of enforcing dual controls
for the crucial duties. Verification of the approval processes for development of the new virtual
machine and migration of the new application to other virtual machines can be evaluated.
Additionally, the verification on existence of the auditing and monitoring log of the virtual

11COMPUTER SECURITY
machine usage and other activities within the data center and at the ends will assist in
identification of the discussed security vulnerabilities. Another one of the prominent measure
that can cite the security vulnerabilities of the technology in consideration ids the evaluation of
the non-virtual environment of the tool which when compared and reported per policy will offer
the monitoring weaknesses. Host-intrusion prevention, host base firewalls support capability and
other capability of the tool can be taken in account to determine and discuss the deemed security
concern.
The computer programs include several instructions. Implementation of the programs
runs inside virtual machine as well as instructions that can execute on processor. Hence, it is
important to have underlying software. In addition, real machine can utilize execution directly. In
addition, the extreme process is complete software machine that interprets the machine gram. It
needs complete software interpreter machine. On the other hand, CSIM can translate as well as
emulate single processor performance that can be helpful for the organization to improve the
process. Statistical dominant subset of program has directly impact on processor. Virtual
machine would be helpful to generate proper plan so that it would be helpful for the
organization. It can execute statistical dominant subset of program in the subsections. Virtual
machine can monitor the system that can be categorized into two groups. Whether TCM is
compromised in the system, TCB is compromised. VM-based security services are required
including dedicated secure VM as the part of TCB.
Moreover, having a small code base as well as identifiers to VMM along with dedicated
security becomes simpler. Virtual machine has various benefits that can be helpful to develop
better suited to give security services compared to the standard physical machine. It can monitor
the state of virtual machine. The technologies related to virtual machine can provide isolation
machine usage and other activities within the data center and at the ends will assist in
identification of the discussed security vulnerabilities. Another one of the prominent measure
that can cite the security vulnerabilities of the technology in consideration ids the evaluation of
the non-virtual environment of the tool which when compared and reported per policy will offer
the monitoring weaknesses. Host-intrusion prevention, host base firewalls support capability and
other capability of the tool can be taken in account to determine and discuss the deemed security
concern.
The computer programs include several instructions. Implementation of the programs
runs inside virtual machine as well as instructions that can execute on processor. Hence, it is
important to have underlying software. In addition, real machine can utilize execution directly. In
addition, the extreme process is complete software machine that interprets the machine gram. It
needs complete software interpreter machine. On the other hand, CSIM can translate as well as
emulate single processor performance that can be helpful for the organization to improve the
process. Statistical dominant subset of program has directly impact on processor. Virtual
machine would be helpful to generate proper plan so that it would be helpful for the
organization. It can execute statistical dominant subset of program in the subsections. Virtual
machine can monitor the system that can be categorized into two groups. Whether TCM is
compromised in the system, TCB is compromised. VM-based security services are required
including dedicated secure VM as the part of TCB.
Moreover, having a small code base as well as identifiers to VMM along with dedicated
security becomes simpler. Virtual machine has various benefits that can be helpful to develop
better suited to give security services compared to the standard physical machine. It can monitor
the state of virtual machine. The technologies related to virtual machine can provide isolation
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





