Comprehensive Security Evaluation Report of VMware Virtual Machine
VerifiedAdded on 2023/06/11
|18
|4885
|275
Report
AI Summary
This report presents a security evaluation of a VMware virtual machine, undertaken to assess its security posture. The evaluation involves investigating the existing security system, exploring various security audit methods and tools, and applying specific techniques to identify vulnerabilities. The report details the steps taken to access the virtual machine, including resetting passwords and determining IP addresses. It also discusses existing security methods such as architectural, software, and configuration risk analysis. Key issues such as data isolation, threats like shared clipboard vulnerabilities, and the potential for VM escape are examined. The tools used in the audit, including the VMware software application and a custom questionnaire, are described. The report concludes with a proposal to secure the system, addressing identified security issues and providing recommendations for enhanced security measures. Desklib offers this and many other solved assignments for students.

Security Evaluation of the VMware Virtual Machine
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Overview...............................................................................................................................................3
Investigation of the Security System.....................................................................................................3
Existing Methods...............................................................................................................................5
Tools Used.........................................................................................................................................7
Techniques Applied.........................................................................................................................10
Results.................................................................................................................................................11
Proposal to secure system...................................................................................................................15
Security Issues.................................................................................................................................16
Conclusion...........................................................................................................................................16
References...........................................................................................................................................17
Overview...............................................................................................................................................3
Investigation of the Security System.....................................................................................................3
Existing Methods...............................................................................................................................5
Tools Used.........................................................................................................................................7
Techniques Applied.........................................................................................................................10
Results.................................................................................................................................................11
Proposal to secure system...................................................................................................................15
Security Issues.................................................................................................................................16
Conclusion...........................................................................................................................................16
References...........................................................................................................................................17

Overview
This report highlights the security evaluation of the virtual environment within the VMware Player.
As WidgetsInc contracted to Benny Vendergast for web store development, Benny Vandergast
provided a virtual machine for the purpose of the testing. WidgetsInc wanted to test the
environment for the security. Thus, the security evaluation process is involved in the study to
determine the security of the virtual machine in the VMware. There are numerous steps involved in
the analysis and security evaluation. Various issues are figured out in the process. The security audit
protocols for the provided scenario are well explain within the VMware player for the virtual
machine. The virtual machine is similar to the computer system that operates as virtual host for the
users that perform all the operations within the virtual environment. The virtual system works better
as compared to other system as they are available in virtual environment. No risks are present in
accessing virtual system with guest operating system. However, there requires assessment of
security in the virtual environment. Without proper security measures, the virtual machine have the
chance to get affected easily. The machine in the virtual environment must be ensured to operate
with security measures. There are chances for the security breach to occur in the virtual machine
(Alberts, C.J. and Dorofee, A., 2002).
The virtualization acts as a significant method for sharing storage space and CPU. The virtualization
requires the appropriate risk mitigation strategy to reduce any kind of risks associated with their
environment. Security audits and auditors play a key role in determining the issues and risks related
to the security. Information security audits are conducted regularly to measure the security features
and their provision. In this case, VMware virtual machine is considered for the security evaluation.
The virtual machine consists of the Linux operating system that has major advantages over the
Windows operating system. The security features in the virtual machine are assessed through
various audit protocols as per security standards to assess and to enhance further for the security
operations. The credentials such as the username and password are not provided for accessing the
virtual machine which can be easily viewed through the appropriate system (Devine, S.W., et.al,
2002).
Investigation of the Security System
The security features of the virtual machine are assessed one by one by adopting certain protocols.
The virtual machine in the VMWare software is accessed easily. Since the username and passwords
for the virtual machine are not provided, few steps are required for accessing the system. The virtual
machine requires changes in the username and password that can be achieved with the use of the
terminal program for command line actions.
This report highlights the security evaluation of the virtual environment within the VMware Player.
As WidgetsInc contracted to Benny Vendergast for web store development, Benny Vandergast
provided a virtual machine for the purpose of the testing. WidgetsInc wanted to test the
environment for the security. Thus, the security evaluation process is involved in the study to
determine the security of the virtual machine in the VMware. There are numerous steps involved in
the analysis and security evaluation. Various issues are figured out in the process. The security audit
protocols for the provided scenario are well explain within the VMware player for the virtual
machine. The virtual machine is similar to the computer system that operates as virtual host for the
users that perform all the operations within the virtual environment. The virtual system works better
as compared to other system as they are available in virtual environment. No risks are present in
accessing virtual system with guest operating system. However, there requires assessment of
security in the virtual environment. Without proper security measures, the virtual machine have the
chance to get affected easily. The machine in the virtual environment must be ensured to operate
with security measures. There are chances for the security breach to occur in the virtual machine
(Alberts, C.J. and Dorofee, A., 2002).
The virtualization acts as a significant method for sharing storage space and CPU. The virtualization
requires the appropriate risk mitigation strategy to reduce any kind of risks associated with their
environment. Security audits and auditors play a key role in determining the issues and risks related
to the security. Information security audits are conducted regularly to measure the security features
and their provision. In this case, VMware virtual machine is considered for the security evaluation.
The virtual machine consists of the Linux operating system that has major advantages over the
Windows operating system. The security features in the virtual machine are assessed through
various audit protocols as per security standards to assess and to enhance further for the security
operations. The credentials such as the username and password are not provided for accessing the
virtual machine which can be easily viewed through the appropriate system (Devine, S.W., et.al,
2002).
Investigation of the Security System
The security features of the virtual machine are assessed one by one by adopting certain protocols.
The virtual machine in the VMWare software is accessed easily. Since the username and passwords
for the virtual machine are not provided, few steps are required for accessing the system. The virtual
machine requires changes in the username and password that can be achieved with the use of the
terminal program for command line actions.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
The virtual environment IP is not known which is not provided. For accessing the virtual environment
and assessing the security features within the virtual environment, there is a great requirement for
determination of the IP (Dhillon et.al, 2006).
IP is determined in the terminal through the following commands
arp-a
ipconfig
For changing the password, we can adopt the similar ways as in Linux. Need to reset the password
and access the boot parameters. The user access is easily facilitated within the virtual environment
as the operation system is the linux-based one. The virtual environment access is made easy. The
security for the virtual environment is defined based on the requirements and audit steps are
focused for evaluating the security system.
Using GRUB loader, it is easy to identify the username, password, and identifying the IP details. The
environment allows numerous changes to the system for entry. For security evaluation, there are
numerous steps and protocol are present. For virtual images, the security evaluation is made easy by
identifying suitable steps necessary to reduce the risks of the security. Since the provided virtual
image is Linux based, the security features are easily audited in the virtual environment (Dunlap,
et.al, 2002).
and assessing the security features within the virtual environment, there is a great requirement for
determination of the IP (Dhillon et.al, 2006).
IP is determined in the terminal through the following commands
arp-a
ipconfig
For changing the password, we can adopt the similar ways as in Linux. Need to reset the password
and access the boot parameters. The user access is easily facilitated within the virtual environment
as the operation system is the linux-based one. The virtual environment access is made easy. The
security for the virtual environment is defined based on the requirements and audit steps are
focused for evaluating the security system.
Using GRUB loader, it is easy to identify the username, password, and identifying the IP details. The
environment allows numerous changes to the system for entry. For security evaluation, there are
numerous steps and protocol are present. For virtual images, the security evaluation is made easy by
identifying suitable steps necessary to reduce the risks of the security. Since the provided virtual
image is Linux based, the security features are easily audited in the virtual environment (Dunlap,
et.al, 2002).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Existing Methods
There are various existing methods for the security auditing and protocols. These security audits and
protocols are utilized for assessing the features. Virtualization replaces the physical resources such
as the server into virtual systems. The virtual system supports consolidation of the physical
resources, administration, deployment, and reduction in power wastage. There are different types of
the virtualization such as storage virtualization, network virtualization, and server virtualization. The
virtual system is installed over the host system with guest operating system. The guest operating
system have the own system, operating system, hard disk, and physical machines (Figueiredo, et.al,
2003).
The security risks and analysis are usually performed in the virtual machines are as follows:
Architectural vulnerability analysis – it can be achieved by comparison of the current system
with the reference sets. The regular updates are made on VMs with security measures
updated to current date and appropriate patch management on VMs. The best networking
practices are adopted regularly in the Virtual machines.
Software vulnerability analysis – Most important software is the hypervisor in which certain
security analysis is performed such as prevention of failure, updates to the hypervisor,
access to the VMs, host OS security, VM security organizational policies and much more.
Configuration risk analysis – Configuration drifts are considered and they are mitigated
through the continuous assessments, configuration checks, authorisation of changes, audits
and controlling, templates approval for VM deployments, monitoring of the events,
database management for configurations.
There are various existing methods for the security auditing and protocols. These security audits and
protocols are utilized for assessing the features. Virtualization replaces the physical resources such
as the server into virtual systems. The virtual system supports consolidation of the physical
resources, administration, deployment, and reduction in power wastage. There are different types of
the virtualization such as storage virtualization, network virtualization, and server virtualization. The
virtual system is installed over the host system with guest operating system. The guest operating
system have the own system, operating system, hard disk, and physical machines (Figueiredo, et.al,
2003).
The security risks and analysis are usually performed in the virtual machines are as follows:
Architectural vulnerability analysis – it can be achieved by comparison of the current system
with the reference sets. The regular updates are made on VMs with security measures
updated to current date and appropriate patch management on VMs. The best networking
practices are adopted regularly in the Virtual machines.
Software vulnerability analysis – Most important software is the hypervisor in which certain
security analysis is performed such as prevention of failure, updates to the hypervisor,
access to the VMs, host OS security, VM security organizational policies and much more.
Configuration risk analysis – Configuration drifts are considered and they are mitigated
through the continuous assessments, configuration checks, authorisation of changes, audits
and controlling, templates approval for VM deployments, monitoring of the events,
database management for configurations.

Apart from these steps, the IT systems adopt certain security policies for securing the data, network,
and all other usage. IT managers need to securely work for deployment and need to analyze period
too. The compliance and trainings are enhanced with the programs for ensuring the security in
virtual machines. Disaster recovery and backup policies are created and mentioned with the factors
such as the loss of data, host-level backups, and guest-level backups. The malware in the
virtualization layer provide access to virtual machines easily, hence the intrusion and accesses must
be made strong through the increased security measures (Garfinkel et.al, 3005).
Apart from these issues, various issues exist in the virtual environment with guest operating system
and the host operating system. These issues will result the system to risk if not taken with care (Kuhn
et.al, 2010)
Data isolation
This is one of the issues that exist in the virtual system in which the data are separated from the
physical system. The virtual system has the ability to isolate the data from the other guests. This
issue however utilized in determination of the deployment and implementation. The virtual
environment is capable of isolating the data and securing the data away from the other systems.
Threats
There are various threats, which are present in the virtualization. The features of communication
will lead to several problems causing unwanted security issues. The sharing of the computer among
different companies. The use of single physical system and provision of common hardware platform
for host operating systems require the security (Kinoshita, 2009).
Use of the technologies like shared clipboard supports sharing the data between the virtual machine
and the host. This function enables the users to transfer data among various malicious programs in
the virtual machines.
In Virtual machines, these threats are supposed to occur. In the given case, these issues replicate
too. Some machines do not have focus on the data isolation giving the acceptance for the resources
to host such as the file access in the file system (Lunsford, D.L., 2009).
Virtual Machines support us to depict about the time of the host computer and provide isolation
between VMs and their host. In a great world, a program working within a virtual machine would not
manage to monitor, have an effect on, or contact another program on the host or another VM.
Unfortunately, certain limitations, the VM vendor's approach to isolation, or issues in the software
of virtualization may bring about to be able to compensate isolation (Mayer, N., 2009).
VM Escape
To the worst part, a program executing within a virtual machine can have the ability to completely
bypass the VM layer, providing full gain to the host system, which is known as "VM escape.” As the
host position is present, the outcome is a complete breakdown within the system’s security model.
and all other usage. IT managers need to securely work for deployment and need to analyze period
too. The compliance and trainings are enhanced with the programs for ensuring the security in
virtual machines. Disaster recovery and backup policies are created and mentioned with the factors
such as the loss of data, host-level backups, and guest-level backups. The malware in the
virtualization layer provide access to virtual machines easily, hence the intrusion and accesses must
be made strong through the increased security measures (Garfinkel et.al, 3005).
Apart from these issues, various issues exist in the virtual environment with guest operating system
and the host operating system. These issues will result the system to risk if not taken with care (Kuhn
et.al, 2010)
Data isolation
This is one of the issues that exist in the virtual system in which the data are separated from the
physical system. The virtual system has the ability to isolate the data from the other guests. This
issue however utilized in determination of the deployment and implementation. The virtual
environment is capable of isolating the data and securing the data away from the other systems.
Threats
There are various threats, which are present in the virtualization. The features of communication
will lead to several problems causing unwanted security issues. The sharing of the computer among
different companies. The use of single physical system and provision of common hardware platform
for host operating systems require the security (Kinoshita, 2009).
Use of the technologies like shared clipboard supports sharing the data between the virtual machine
and the host. This function enables the users to transfer data among various malicious programs in
the virtual machines.
In Virtual machines, these threats are supposed to occur. In the given case, these issues replicate
too. Some machines do not have focus on the data isolation giving the acceptance for the resources
to host such as the file access in the file system (Lunsford, D.L., 2009).
Virtual Machines support us to depict about the time of the host computer and provide isolation
between VMs and their host. In a great world, a program working within a virtual machine would not
manage to monitor, have an effect on, or contact another program on the host or another VM.
Unfortunately, certain limitations, the VM vendor's approach to isolation, or issues in the software
of virtualization may bring about to be able to compensate isolation (Mayer, N., 2009).
VM Escape
To the worst part, a program executing within a virtual machine can have the ability to completely
bypass the VM layer, providing full gain to the host system, which is known as "VM escape.” As the
host position is present, the outcome is a complete breakdown within the system’s security model.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
This issue may be added as significant one by inappropriate configuration of the host/guest
connection.
Security and Monitoring
The VM monitoring is not usually assumed an issue when one can initiate the action of the
monitoring, update, or interaction with virtual machine applications from the host system. The host
is assumed to present in a secured position. This is why the host system requires more strict
protection than the individual VMs during the management.
Information security auditors are involved to measure each policies and procedures followed in the
firm to improve techniques for security evaluation. The vulnerability techniques are adopted for
collaborations with the penetration testing. As per Gartner, 60 % of the virtual servers will have less
security when compared to other physical systems. The information security does not play role in
the architecture or infrastructure development of virtual environment and planning stages. The
application, which is misconfigured have flaws as mentioned and even have the vulnerabilities on
virtual environment without appropriate firewalls (Nair et.al, 2008).
Tools Used
Various tools are used in the virtual machine security audits. The process of the security audits
includes consideration of the various monitoring activities in the tool.
VMWare Software application is used as the basic tool for accessing the Virtual machine. The virtual
image of the given software is loaded into the VMWare software application.
The application loads the virtual machine and runs the machine as similar to that of the host system.
This virtual machine runs by the use of the guest operating system. The assumed operating system is
Ubuntu, which is linux-based operating system. As network password, username, and id are not
provided, they are obtained using linux terminal program.
connection.
Security and Monitoring
The VM monitoring is not usually assumed an issue when one can initiate the action of the
monitoring, update, or interaction with virtual machine applications from the host system. The host
is assumed to present in a secured position. This is why the host system requires more strict
protection than the individual VMs during the management.
Information security auditors are involved to measure each policies and procedures followed in the
firm to improve techniques for security evaluation. The vulnerability techniques are adopted for
collaborations with the penetration testing. As per Gartner, 60 % of the virtual servers will have less
security when compared to other physical systems. The information security does not play role in
the architecture or infrastructure development of virtual environment and planning stages. The
application, which is misconfigured have flaws as mentioned and even have the vulnerabilities on
virtual environment without appropriate firewalls (Nair et.al, 2008).
Tools Used
Various tools are used in the virtual machine security audits. The process of the security audits
includes consideration of the various monitoring activities in the tool.
VMWare Software application is used as the basic tool for accessing the Virtual machine. The virtual
image of the given software is loaded into the VMWare software application.
The application loads the virtual machine and runs the machine as similar to that of the host system.
This virtual machine runs by the use of the guest operating system. The assumed operating system is
Ubuntu, which is linux-based operating system. As network password, username, and id are not
provided, they are obtained using linux terminal program.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Security audits are conducted based on the means of the use of tools and techniques. The tools
involve the use of the questionnaire, which have questions as per the types of risks. Based on the
risks, the scores are selected from 0 to 4 indicating the applicability as follows:
0 – Not applicable
1 – Disagree
2 – Somewhat agree
3 – Agree
4 – Strongly Agree
Questionnaire is given as follows:
A questionnaire is created in light of the distinctive dangers thought as takes after: The following
questionnaire is received as an apparatus for the security appraisals.
Administrative
1. Are all the operational strategies and dangers methods consistently refreshed?
2. Do you have controls for ensuring integrity?
3 Do the reports for change control allude to the right segment on the right server?
4 Evaluate backup/DR capabilities.
5 Is a physically isolated administrative utilized for management dangers capacities, for example,
creating new VMs or changing existing pictures?
6. Are there management-affirmed initiatives to forestall caricature source address attacks, dangers
association hijacking, route hijacking and man-in-the-middle attacks?
7. Is a recorded setup management process used for all VM increments, changes or erasures of
clients, gatherings, parts and consents?
8. Coherent access controls, for example, application security and isolation of obligations ought to be
connected for all levels of clients.
9. Training the staff on virtualization innovation and security includes in a virtual IT framework
Application dangers
10. Do you have application excess?
11. Is every one of the applications tried for usefulness and performance?
12. Are the product's created to address application security issues? (issues, for example, sql
injection, buffer flood and so on.,)
involve the use of the questionnaire, which have questions as per the types of risks. Based on the
risks, the scores are selected from 0 to 4 indicating the applicability as follows:
0 – Not applicable
1 – Disagree
2 – Somewhat agree
3 – Agree
4 – Strongly Agree
Questionnaire is given as follows:
A questionnaire is created in light of the distinctive dangers thought as takes after: The following
questionnaire is received as an apparatus for the security appraisals.
Administrative
1. Are all the operational strategies and dangers methods consistently refreshed?
2. Do you have controls for ensuring integrity?
3 Do the reports for change control allude to the right segment on the right server?
4 Evaluate backup/DR capabilities.
5 Is a physically isolated administrative utilized for management dangers capacities, for example,
creating new VMs or changing existing pictures?
6. Are there management-affirmed initiatives to forestall caricature source address attacks, dangers
association hijacking, route hijacking and man-in-the-middle attacks?
7. Is a recorded setup management process used for all VM increments, changes or erasures of
clients, gatherings, parts and consents?
8. Coherent access controls, for example, application security and isolation of obligations ought to be
connected for all levels of clients.
9. Training the staff on virtualization innovation and security includes in a virtual IT framework
Application dangers
10. Do you have application excess?
11. Is every one of the applications tried for usefulness and performance?
12. Are the product's created to address application security issues? (issues, for example, sql
injection, buffer flood and so on.,)

Design dangers
13. Do you have fault tolerant system?
14. Do you have Fault tolerance Data stockpiling?
15 Are the virtual machines isolated by affectability?
16. Is all system activity managed on a devoted virtual neighborhood (VLAN) or system section?
Setup dangers
17. Do you have firewall assurance for each VM?
18. Are the setups of virtual machines are secured with the end goal that vulnerabilities in a single
capacity can't affect the security of other capacities?
19. Does the management reassure of the virtual machine manager have tight access controls,
secured to particular clients and particular parcels or machines?
20. Are there controls for particular clients that farthest point access and read/compose capabilities?
21. Does the framework have stranded pictures?
22. Are the host firewalls equipped for detecting intrusions/malware examination?
23. Is the host arranged to log changes to the VMs including incidents of copying, moving, or
deleting from the host?
24. Do you have a Configuration management database (CMDB)
Information spillage dangers
25. Is there an arrangement to anticipate file stealing using outer media (e.g., floppy, CD/DVDRW,
USB/streak drives)?
26. Is there an arrangement to catch movement coming into or out of the system interfaces?
Monitoring Risks
27. Do you have a different log server with limited access?
13. Do you have fault tolerant system?
14. Do you have Fault tolerance Data stockpiling?
15 Are the virtual machines isolated by affectability?
16. Is all system activity managed on a devoted virtual neighborhood (VLAN) or system section?
Setup dangers
17. Do you have firewall assurance for each VM?
18. Are the setups of virtual machines are secured with the end goal that vulnerabilities in a single
capacity can't affect the security of other capacities?
19. Does the management reassure of the virtual machine manager have tight access controls,
secured to particular clients and particular parcels or machines?
20. Are there controls for particular clients that farthest point access and read/compose capabilities?
21. Does the framework have stranded pictures?
22. Are the host firewalls equipped for detecting intrusions/malware examination?
23. Is the host arranged to log changes to the VMs including incidents of copying, moving, or
deleting from the host?
24. Do you have a Configuration management database (CMDB)
Information spillage dangers
25. Is there an arrangement to anticipate file stealing using outer media (e.g., floppy, CD/DVDRW,
USB/streak drives)?
26. Is there an arrangement to catch movement coming into or out of the system interfaces?
Monitoring Risks
27. Do you have a different log server with limited access?
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Techniques Applied
Based on the VM technology, the host systems are influenced by the virtual machines that remain as
the basic techniques for accessing. These techniques act as the validation techniques for the security
evaluation (Payne et.al, 2007).
Validation of Data isolation
Evaluation of Virtualization mode either Full/Para/Hardware supported
System call proxy
Threats
Interaction of host system and virtual system
Shared clipboard
Log keystrokes
Screen updates
VM Escape
Monitoring from host and another virtual image
Denial of services
External modifications of VM/Hypervisor
These techniques are adopted for the virtual system to assess the security. Each technique has
significance in distinct ways (Popovic, K. and Hocenski, Ž., 2010). Each technique will provide the
significant results as follows:
Validation of Data isolation
The data isolation is tested for the virtual image. The data are validated for the isolation. The data
security needs to be isolated. The data isolation is present in the virtual image with security.
Evaluation of Virtualization mode either Full/Para/Hardware supported
The virtual image is provided with the full virtualization mode that allows guest operating system for
execution. The virtual image is supported with the hardware as appropriate.
System call proxy
The VM layer works based only on the system call proxy and the system is validated.
Threats
The following threats in the security are analyzed with the host and the security audit adopts the
following techniques appropriately for the assessment.
Interaction of host system and virtual system
The system is validated for the working and the system determined to be operating with security.
The virtual image is provided in a hardware platform for hosting single guest operating system.
Based on the VM technology, the host systems are influenced by the virtual machines that remain as
the basic techniques for accessing. These techniques act as the validation techniques for the security
evaluation (Payne et.al, 2007).
Validation of Data isolation
Evaluation of Virtualization mode either Full/Para/Hardware supported
System call proxy
Threats
Interaction of host system and virtual system
Shared clipboard
Log keystrokes
Screen updates
VM Escape
Monitoring from host and another virtual image
Denial of services
External modifications of VM/Hypervisor
These techniques are adopted for the virtual system to assess the security. Each technique has
significance in distinct ways (Popovic, K. and Hocenski, Ž., 2010). Each technique will provide the
significant results as follows:
Validation of Data isolation
The data isolation is tested for the virtual image. The data are validated for the isolation. The data
security needs to be isolated. The data isolation is present in the virtual image with security.
Evaluation of Virtualization mode either Full/Para/Hardware supported
The virtual image is provided with the full virtualization mode that allows guest operating system for
execution. The virtual image is supported with the hardware as appropriate.
System call proxy
The VM layer works based only on the system call proxy and the system is validated.
Threats
The following threats in the security are analyzed with the host and the security audit adopts the
following techniques appropriately for the assessment.
Interaction of host system and virtual system
The system is validated for the working and the system determined to be operating with security.
The virtual image is provided in a hardware platform for hosting single guest operating system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Shared clipboard
The shared clipboard in the virtual environment is limited and hence there is no security threat for
the loss of the data of transfer of the data
Log keystrokes and Screen updates
The keystrokes and screen updates are used for the virtual terminals in the virtual machine. All the
logs of the keystrokes are encrypted efficiently.
VM Escape
VM escape issue is not present in the virtual environment. Security issues not occur in the virtual
machine.
Monitoring from host and another virtual image
The monitoring from the host machine and virtual image provides the assessment of the security.
The host environment is assessed with the security for the following activities such as accessing
virtual images, monitoring and configuration of the resources, adjusting number of CPUs, hard disk
size, monitoring applications, and all other data related to VM virtual disks.
Denial of services
The resources for the access are limited that lead to reduce the denial of services. The denial of
services are limited for the allocation of the resources.
External modifications of VM/Hypervisor
Virtual Machine is signed digitally with the protection and the environment is secured. These
techniques are audited and validated (Yeh, Q.J. and Chang, A.J.T., 2007).
Results
The results are identified based on the tools and techniques used. The responses of the
questionnaire are considered and most of the results had resulted to the positive response
indicating the virtual image is presented in secured environment.
The shared clipboard in the virtual environment is limited and hence there is no security threat for
the loss of the data of transfer of the data
Log keystrokes and Screen updates
The keystrokes and screen updates are used for the virtual terminals in the virtual machine. All the
logs of the keystrokes are encrypted efficiently.
VM Escape
VM escape issue is not present in the virtual environment. Security issues not occur in the virtual
machine.
Monitoring from host and another virtual image
The monitoring from the host machine and virtual image provides the assessment of the security.
The host environment is assessed with the security for the following activities such as accessing
virtual images, monitoring and configuration of the resources, adjusting number of CPUs, hard disk
size, monitoring applications, and all other data related to VM virtual disks.
Denial of services
The resources for the access are limited that lead to reduce the denial of services. The denial of
services are limited for the allocation of the resources.
External modifications of VM/Hypervisor
Virtual Machine is signed digitally with the protection and the environment is secured. These
techniques are audited and validated (Yeh, Q.J. and Chang, A.J.T., 2007).
Results
The results are identified based on the tools and techniques used. The responses of the
questionnaire are considered and most of the results had resulted to the positive response
indicating the virtual image is presented in secured environment.
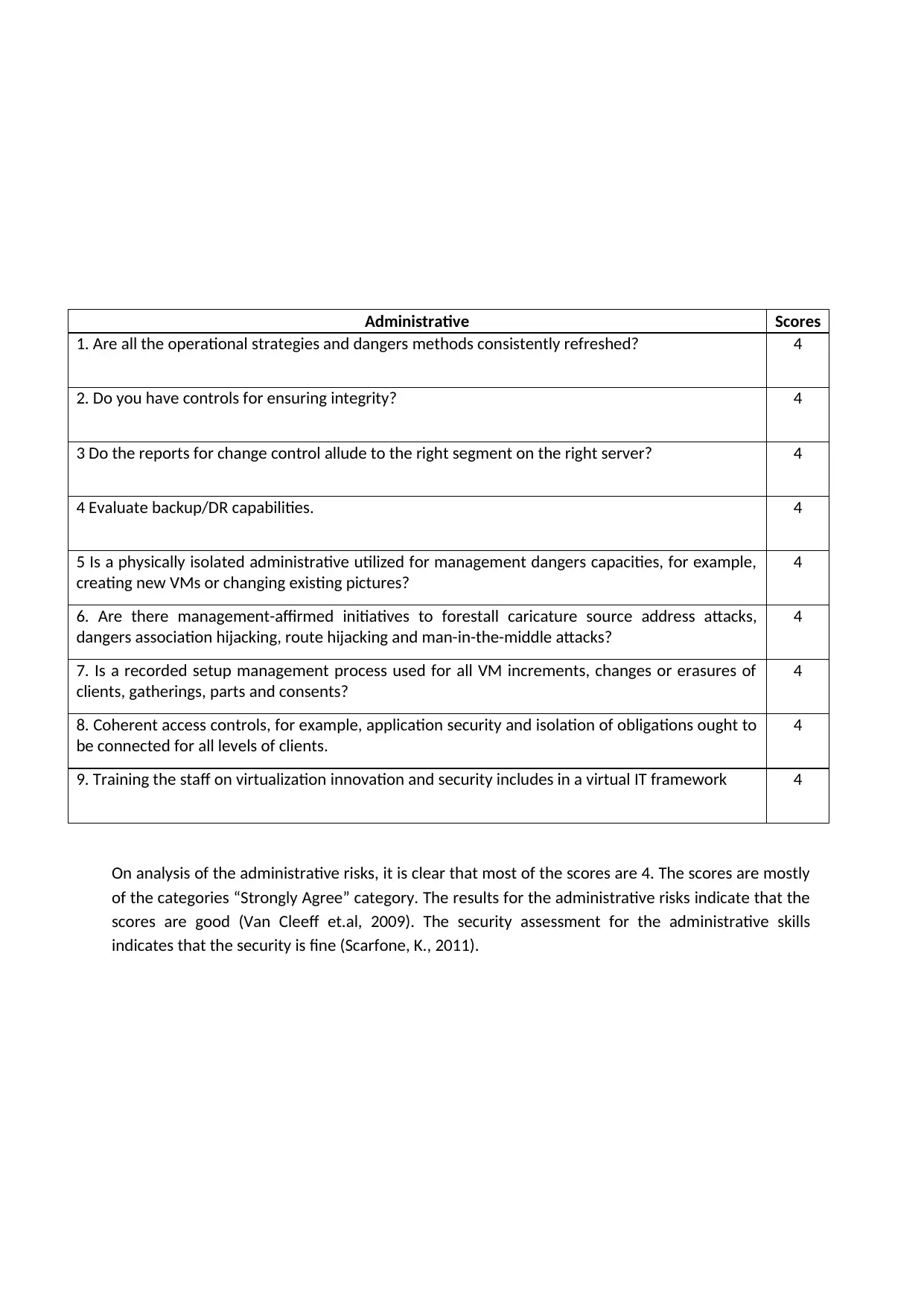
Administrative Scores
1. Are all the operational strategies and dangers methods consistently refreshed? 4
2. Do you have controls for ensuring integrity? 4
3 Do the reports for change control allude to the right segment on the right server? 4
4 Evaluate backup/DR capabilities. 4
5 Is a physically isolated administrative utilized for management dangers capacities, for example,
creating new VMs or changing existing pictures?
4
6. Are there management-affirmed initiatives to forestall caricature source address attacks,
dangers association hijacking, route hijacking and man-in-the-middle attacks?
4
7. Is a recorded setup management process used for all VM increments, changes or erasures of
clients, gatherings, parts and consents?
4
8. Coherent access controls, for example, application security and isolation of obligations ought to
be connected for all levels of clients.
4
9. Training the staff on virtualization innovation and security includes in a virtual IT framework 4
On analysis of the administrative risks, it is clear that most of the scores are 4. The scores are mostly
of the categories “Strongly Agree” category. The results for the administrative risks indicate that the
scores are good (Van Cleeff et.al, 2009). The security assessment for the administrative skills
indicates that the security is fine (Scarfone, K., 2011).
1. Are all the operational strategies and dangers methods consistently refreshed? 4
2. Do you have controls for ensuring integrity? 4
3 Do the reports for change control allude to the right segment on the right server? 4
4 Evaluate backup/DR capabilities. 4
5 Is a physically isolated administrative utilized for management dangers capacities, for example,
creating new VMs or changing existing pictures?
4
6. Are there management-affirmed initiatives to forestall caricature source address attacks,
dangers association hijacking, route hijacking and man-in-the-middle attacks?
4
7. Is a recorded setup management process used for all VM increments, changes or erasures of
clients, gatherings, parts and consents?
4
8. Coherent access controls, for example, application security and isolation of obligations ought to
be connected for all levels of clients.
4
9. Training the staff on virtualization innovation and security includes in a virtual IT framework 4
On analysis of the administrative risks, it is clear that most of the scores are 4. The scores are mostly
of the categories “Strongly Agree” category. The results for the administrative risks indicate that the
scores are good (Van Cleeff et.al, 2009). The security assessment for the administrative skills
indicates that the security is fine (Scarfone, K., 2011).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





