Network Security Project: VoIP Security Design and Implementation
VerifiedAdded on 2023/01/13
|14
|3926
|63
Project
AI Summary
This project delves into the realm of network security, specifically targeting VoIP systems. It begins with the configuration of an Asterisk IP-PBX, including logical addressing and the creation of a dial plan for a significant number of extensions. The project then moves to implementing Postfix MTA for voicemail, and configuring IAX trunks for connectivity between Asterisk servers. The core of the project involves a deep dive into VoIP security, including illustrating various attacks such as Denial of Service and Vishing, with a focus on pivoting attacks against user mailboxes. It also covers the design and implementation of comprehensive security policies, NIDS deployment, user agent authentication, and encryption of VoIP traffic. Furthermore, the project critically examines cyber resilience within unified communication. The project is comprehensive and provides a practical and theoretical overview of securing VoIP systems and communication networks.

Network Security
Table of Contents
Table of Contents
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction......................................................................................................................................1
Block A: Architecture & Communication.......................................................................................1
1. Configuration of Asterisk IP-PBX with logical addressing scheme.......................................1
2. Creation of dial plan for around 150 distinct extensions.........................................................3
3. Design as well as implementation Postfix MTA for voicemail from extensions to user
mailboxes.....................................................................................................................................5
4. Configuration of IAX trunks for demonstration of connectivity among Asterisk servers......6
Block B: Secured operations as well as service delivery................................................................7
5. Illustrate 3 attacks against VoIP system and one attack must illustrate pivoting against
mailbox of users...........................................................................................................................7
6. Designing as well as implementation of comprehensive security policies for VoIP system
along with relevant security controls...........................................................................................8
7. Implementation of comprehensive NIDS as well as test their efficiency with respect to
deployment..................................................................................................................................8
Block C: Research and Development............................................................................................10
8. Deployment of authentication mechanism for user agent.....................................................10
9. Encryption of VoIP traffic through usage of standardised security protocols.......................11
10. Critically illustrate ways in which cyber resilience can be attained within unified
communication..........................................................................................................................11
Conclusion.....................................................................................................................................11
References......................................................................................................................................12
Block A: Architecture & Communication.......................................................................................1
1. Configuration of Asterisk IP-PBX with logical addressing scheme.......................................1
2. Creation of dial plan for around 150 distinct extensions.........................................................3
3. Design as well as implementation Postfix MTA for voicemail from extensions to user
mailboxes.....................................................................................................................................5
4. Configuration of IAX trunks for demonstration of connectivity among Asterisk servers......6
Block B: Secured operations as well as service delivery................................................................7
5. Illustrate 3 attacks against VoIP system and one attack must illustrate pivoting against
mailbox of users...........................................................................................................................7
6. Designing as well as implementation of comprehensive security policies for VoIP system
along with relevant security controls...........................................................................................8
7. Implementation of comprehensive NIDS as well as test their efficiency with respect to
deployment..................................................................................................................................8
Block C: Research and Development............................................................................................10
8. Deployment of authentication mechanism for user agent.....................................................10
9. Encryption of VoIP traffic through usage of standardised security protocols.......................11
10. Critically illustrate ways in which cyber resilience can be attained within unified
communication..........................................................................................................................11
Conclusion.....................................................................................................................................11
References......................................................................................................................................12

Introduction
The activity that is designed for protecting usability along with integrity of data and
network is referred to as network security. This comprises of software as well as hardware
technologies which target different threats. Basically, it involves practices and policies which are
adopted for prevention as well as monitoring unauthorised access, denial of computer network
and modification (Bentall Airbus DS Ltd, 2019). Asterisk denotes an open source framework
that is liable for building up communication applications. To acknowledge the concept of
network security, Lotus Consulting International Limited which is a consultancy firm and
renders their services in areas like transactions, construction and commercial matters. This report
comprises architecture as well as communication, service delivery, along with research and
development.
Block A: Architecture & Communication
1. Configuration of Asterisk IP-PBX with logical addressing scheme.
The software execution of private branch exchange (PBX) is referred to as asterisk. This
is being utilised for establishment as well as controlling telephone calls among
telecommunication endpoints. IP PBX system is liable for handling internal traffic among
stations which act as gatekeeper (What Is A IP PBX?, 2020). This is liable for rendering features
such as VoIP ready, voice messaging, conferencing, reporting and mobility. Asterisk comprises
of components that are crucial for building up scalable and powerful business phone system. It is
liable for enabling Voice over Internet Protocol (VoIP) and Public Switched Telephone Network
(PSTN) connection for communicating with each other. The Asterisk PBX can be installed
within Ubuntu (Linux version), it is specified below:
sudo apt-get install asterisk
Type Y when user is prompted to do so.
Do you want to continue [Y/N]?
The figure with respect to this is shown below:
1
The activity that is designed for protecting usability along with integrity of data and
network is referred to as network security. This comprises of software as well as hardware
technologies which target different threats. Basically, it involves practices and policies which are
adopted for prevention as well as monitoring unauthorised access, denial of computer network
and modification (Bentall Airbus DS Ltd, 2019). Asterisk denotes an open source framework
that is liable for building up communication applications. To acknowledge the concept of
network security, Lotus Consulting International Limited which is a consultancy firm and
renders their services in areas like transactions, construction and commercial matters. This report
comprises architecture as well as communication, service delivery, along with research and
development.
Block A: Architecture & Communication
1. Configuration of Asterisk IP-PBX with logical addressing scheme.
The software execution of private branch exchange (PBX) is referred to as asterisk. This
is being utilised for establishment as well as controlling telephone calls among
telecommunication endpoints. IP PBX system is liable for handling internal traffic among
stations which act as gatekeeper (What Is A IP PBX?, 2020). This is liable for rendering features
such as VoIP ready, voice messaging, conferencing, reporting and mobility. Asterisk comprises
of components that are crucial for building up scalable and powerful business phone system. It is
liable for enabling Voice over Internet Protocol (VoIP) and Public Switched Telephone Network
(PSTN) connection for communicating with each other. The Asterisk PBX can be installed
within Ubuntu (Linux version), it is specified below:
sudo apt-get install asterisk
Type Y when user is prompted to do so.
Do you want to continue [Y/N]?
The figure with respect to this is shown below:
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
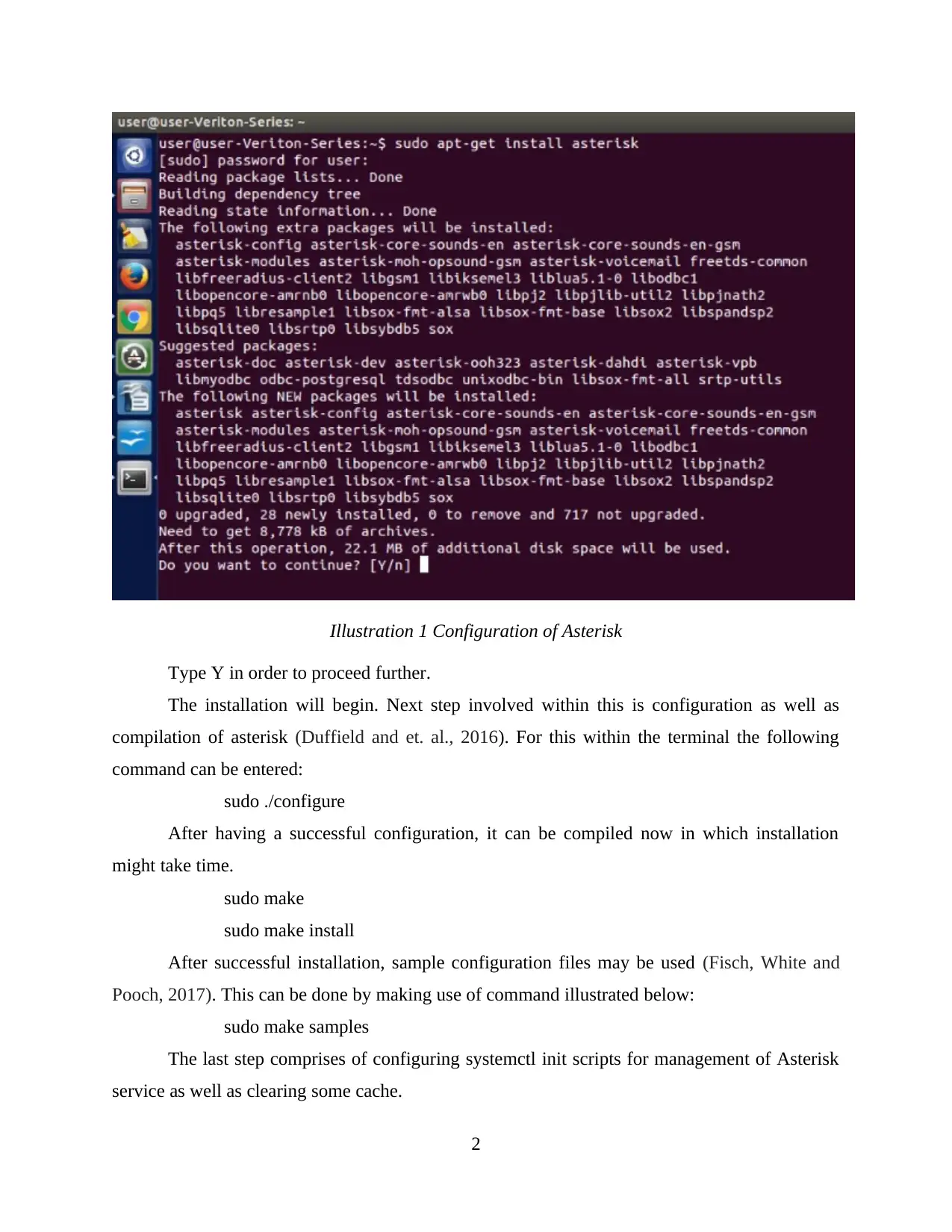
Illustration 1 Configuration of Asterisk
Type Y in order to proceed further.
The installation will begin. Next step involved within this is configuration as well as
compilation of asterisk (Duffield and et. al., 2016). For this within the terminal the following
command can be entered:
sudo ./configure
After having a successful configuration, it can be compiled now in which installation
might take time.
sudo make
sudo make install
After successful installation, sample configuration files may be used (Fisch, White and
Pooch, 2017). This can be done by making use of command illustrated below:
sudo make samples
The last step comprises of configuring systemctl init scripts for management of Asterisk
service as well as clearing some cache.
2
Type Y in order to proceed further.
The installation will begin. Next step involved within this is configuration as well as
compilation of asterisk (Duffield and et. al., 2016). For this within the terminal the following
command can be entered:
sudo ./configure
After having a successful configuration, it can be compiled now in which installation
might take time.
sudo make
sudo make install
After successful installation, sample configuration files may be used (Fisch, White and
Pooch, 2017). This can be done by making use of command illustrated below:
sudo make samples
The last step comprises of configuring systemctl init scripts for management of Asterisk
service as well as clearing some cache.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

sudo make config
sudo Idconfig
The next step involved within this is setting up non-root account the reason behind this is
security reason. Command which can be used for this is;
sudo groupadd asterisk
sudo adduser --system --group --home /var/lib/asterisk --no-create-home –gecos
“Asterisk PBX” asterisk
This is liable for creation of user and a group named “asterisk” with their home directory
which is as illustrated here /var/lib/asterisk (How to Install Asterisk on Ubuntu 18.04. 2017).
Now, the other step involved within this is to built-in Asterisk users with (audio and
dialout) for “asterisk” group, this is done by:
sudo usermod -a -G dialout, audio asterisk
Now for setting up Asterisk for working with new user, the files have to have modified.
This can be done via:
sudo nano /etc/default/asterisk
The files can be uncommented and new user which have been created can be added
within this (Grahn, Westerlund and Pulkkis, 2017). It is being carried out by making use of:
AST_USER=”asterisk”
AST_GROUP=”asterisk”
Similar to this, it can be done within other file through:
runuser = asterisk
rungroup = asterisk
The next step which has to be carried out within Ubuntu server is testing. For this asterisk
service has to be automatically started on the server boot(Kwon and et. al., 2017).
sudo systemct1 enable asterisk
Now Asterisk service can be started by making use of command shown beneath:
sudo systemct1 start asterisk
For verifying that, it has been started the “active (running)” message can be seen after
execution of:
sudo systemct1 status asterisk
3
sudo Idconfig
The next step involved within this is setting up non-root account the reason behind this is
security reason. Command which can be used for this is;
sudo groupadd asterisk
sudo adduser --system --group --home /var/lib/asterisk --no-create-home –gecos
“Asterisk PBX” asterisk
This is liable for creation of user and a group named “asterisk” with their home directory
which is as illustrated here /var/lib/asterisk (How to Install Asterisk on Ubuntu 18.04. 2017).
Now, the other step involved within this is to built-in Asterisk users with (audio and
dialout) for “asterisk” group, this is done by:
sudo usermod -a -G dialout, audio asterisk
Now for setting up Asterisk for working with new user, the files have to have modified.
This can be done via:
sudo nano /etc/default/asterisk
The files can be uncommented and new user which have been created can be added
within this (Grahn, Westerlund and Pulkkis, 2017). It is being carried out by making use of:
AST_USER=”asterisk”
AST_GROUP=”asterisk”
Similar to this, it can be done within other file through:
runuser = asterisk
rungroup = asterisk
The next step which has to be carried out within Ubuntu server is testing. For this asterisk
service has to be automatically started on the server boot(Kwon and et. al., 2017).
sudo systemct1 enable asterisk
Now Asterisk service can be started by making use of command shown beneath:
sudo systemct1 start asterisk
For verifying that, it has been started the “active (running)” message can be seen after
execution of:
sudo systemct1 status asterisk
3

To check access for Asterisk CLI, command which can be implemented is:
sudo asterisk -rvvv
For seeing that, Asterisk can be executed by making use of non-root account:
Running as user 'asterisk'
Running under group 'asterisk'
Now latest version of Asterisk have been installed successfully on cloud VPS.
2. Creation of dial plan for around 150 distinct extensions.
It is crucial for carrying out interaction with individuals and for this voice interaction
must be established. For an instance “ Welcome to ABC organisation”, please dial on zero or
extension number for assistance. Same has to be done within this the extensions have to be made
along with two soft phones. This implies that Voice over internet protocol has to be utilised
which acts as a transmission technology for delivering interaction over IP network like internet
or any other kind of packet-switched network (Liyanage and et. al., 2016). This will enable
within reduction of infrastructure and communication cost. The Asterisk dialplan is liable for
routing calls and dialplan is written by making use of peculiar scripting language which is very
powerful. For an instance call flow can be created in following manner:
An external call comes within Asterisk which involves standard telephone number.
The user may be asked for entering basic information by IVR (Interactive Voice
Response) like their account number.
This will enable asterisk to accept response made by user. Here, IVR will look into their
accounts as well as present information present with them.
Optionally, user will be routed to queue which is available for customer service
representatives. When a call is being received by customer, system liable for providing
them with all the details as well as save some time of caller (Muddu and Tryfonas Splunk
Inc, 2016).
There are four major components related with Asterisk dialplan. They are mentioned
beneath: Contexts: It shows logical section within the dialplan and it involves one or more than
one extensions. Extensions: It denotes grouping of steps which are being utilised for handling specific
call. There can be a extension named “mainIVR” if it is required.
4
sudo asterisk -rvvv
For seeing that, Asterisk can be executed by making use of non-root account:
Running as user 'asterisk'
Running under group 'asterisk'
Now latest version of Asterisk have been installed successfully on cloud VPS.
2. Creation of dial plan for around 150 distinct extensions.
It is crucial for carrying out interaction with individuals and for this voice interaction
must be established. For an instance “ Welcome to ABC organisation”, please dial on zero or
extension number for assistance. Same has to be done within this the extensions have to be made
along with two soft phones. This implies that Voice over internet protocol has to be utilised
which acts as a transmission technology for delivering interaction over IP network like internet
or any other kind of packet-switched network (Liyanage and et. al., 2016). This will enable
within reduction of infrastructure and communication cost. The Asterisk dialplan is liable for
routing calls and dialplan is written by making use of peculiar scripting language which is very
powerful. For an instance call flow can be created in following manner:
An external call comes within Asterisk which involves standard telephone number.
The user may be asked for entering basic information by IVR (Interactive Voice
Response) like their account number.
This will enable asterisk to accept response made by user. Here, IVR will look into their
accounts as well as present information present with them.
Optionally, user will be routed to queue which is available for customer service
representatives. When a call is being received by customer, system liable for providing
them with all the details as well as save some time of caller (Muddu and Tryfonas Splunk
Inc, 2016).
There are four major components related with Asterisk dialplan. They are mentioned
beneath: Contexts: It shows logical section within the dialplan and it involves one or more than
one extensions. Extensions: It denotes grouping of steps which are being utilised for handling specific
call. There can be a extension named “mainIVR” if it is required.
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Priorities: This is step for handling order as well as attaching label by which call can be
jumped as per the requirements (Muddu, Tryfonas and Bulusu Splunk Inc, 2018).
Applications: They are identical to functions within the programming language which
tells Asterisk what they have to do with a specific call.
The dialplan is generally configured within /etc/asterisk/extensions.conf:
exten => 1001,1, Dial (PJSIP/A-softphone)
exten => 1002,1,Dial (PJSIP/B-softphone)
This allows two phones for making call to one other. 1001 and 1002 illustrates extension,
1 after it denotes priority and each have single priorities. Dial denotes extension which is being
utilised to make a ring to remote devices which takes place through VoIP, SIP or any other
signalling protocols (Pathan, 2016).
Furthermore, miniSIPServer will be installed and that will be connected to softphone. Sip
file is created below:
#vi sip.conf
[general]
port=5060
bindaddr=0.0.0.0 : 0.0.0.150
[1000]
type=friend
host=dynamic
secret=abc
[1001]
type=friend
host=dynamic
secret= abc
port- Number which is being utilised by Asterisk for carrying out communication.
bindaddr – Illustrate the IP range to which server will listen, here it is 150
5
jumped as per the requirements (Muddu, Tryfonas and Bulusu Splunk Inc, 2018).
Applications: They are identical to functions within the programming language which
tells Asterisk what they have to do with a specific call.
The dialplan is generally configured within /etc/asterisk/extensions.conf:
exten => 1001,1, Dial (PJSIP/A-softphone)
exten => 1002,1,Dial (PJSIP/B-softphone)
This allows two phones for making call to one other. 1001 and 1002 illustrates extension,
1 after it denotes priority and each have single priorities. Dial denotes extension which is being
utilised to make a ring to remote devices which takes place through VoIP, SIP or any other
signalling protocols (Pathan, 2016).
Furthermore, miniSIPServer will be installed and that will be connected to softphone. Sip
file is created below:
#vi sip.conf
[general]
port=5060
bindaddr=0.0.0.0 : 0.0.0.150
[1000]
type=friend
host=dynamic
secret=abc
[1001]
type=friend
host=dynamic
secret= abc
port- Number which is being utilised by Asterisk for carrying out communication.
bindaddr – Illustrate the IP range to which server will listen, here it is 150
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

type- type of connection (user — incoming calls, peer — outcoming calls only, friend —
both outcoming and incoming calls)
host- Dynamic Host name
secret- Passsword utilised for authenticating user
After this, within the Asterisk CLI reload dialplan by typing the command “dialplan
reload” and for verification that it is being done in appropriate manner configuration plan can be
read at CLI by making use of:
dialplan show from-internal
This will allow to make call to different 150 extensions.
3. Design as well as implementation Postfix MTA for voicemail from extensions to user
mailboxes.
Postfix illustrates free as well as open-source mail transfer agent that is liable for routing
as well as delivering electronic mail. The Postfix service is being installed by making use of
Yum repository (warehouse of linux software which holds RPM package file as well as allows
download and installation of new software on virtual private server) (Perlman, Kaufman and
Speciner, 2016). Mail transfer agent is responsible for sending email from configured
domain,there is no need for setting SMTP server as user need not to login. But these mails might
be considered as spam by target server. The commands which are needed for doing this as
illustrated below:
#yum install postfix
Now turn on Postfix service and ensure that it is started mechanically on reboot.
#service postfix start
#chkconfig postfix on
Now the service can be configured by making use of “/etc/postfix/main.cf” file. As
alterations have been made then system has to be restarted (Sheleheda and et. al., 2016).
#service postfix restart
# # or
#service postfix reload
6
both outcoming and incoming calls)
host- Dynamic Host name
secret- Passsword utilised for authenticating user
After this, within the Asterisk CLI reload dialplan by typing the command “dialplan
reload” and for verification that it is being done in appropriate manner configuration plan can be
read at CLI by making use of:
dialplan show from-internal
This will allow to make call to different 150 extensions.
3. Design as well as implementation Postfix MTA for voicemail from extensions to user
mailboxes.
Postfix illustrates free as well as open-source mail transfer agent that is liable for routing
as well as delivering electronic mail. The Postfix service is being installed by making use of
Yum repository (warehouse of linux software which holds RPM package file as well as allows
download and installation of new software on virtual private server) (Perlman, Kaufman and
Speciner, 2016). Mail transfer agent is responsible for sending email from configured
domain,there is no need for setting SMTP server as user need not to login. But these mails might
be considered as spam by target server. The commands which are needed for doing this as
illustrated below:
#yum install postfix
Now turn on Postfix service and ensure that it is started mechanically on reboot.
#service postfix start
#chkconfig postfix on
Now the service can be configured by making use of “/etc/postfix/main.cf” file. As
alterations have been made then system has to be restarted (Sheleheda and et. al., 2016).
#service postfix restart
# # or
#service postfix reload
6

The Postfix have been installed. Now the steps involved within implementation of Postfix
for sending voicemail (computer based system which permits subscribers as well as users for
exchanging voice messages) from extension to users mailboxes have been mentioned below:
relayhost =192.169.0.1
This aids Postfix within accepting relay (forward) email, the file “/etc/postfix/main.cf”
has to be edited. It has to be reloaded or restarted so that changes can occur
#service postfix restart
Now test the changes which have been made by sending email
#echo “This is test” | mail -s “Relay Test” ab@example.com
This will allow all voicemail from extension to forward to mailbox of users.
4. Configuration of IAX trunks for demonstration of connectivity among Asterisk servers.
Inter-Asterisk eXchange is interaction protocol which is native to Asterisk PBX and is
also supported by softphones, PBX systems and softswitches. It is utilised for transportation of
VoIP telephony sessions among servers to terminal devices (Stallings, 2016). The steps
illustrated in this are:
Configure Asterisk servers within both ends in iax.conf, one is user and other is peer.
Set up dialplan for users in extensions.conf by which can be made from user to peer.
Register peer with user and repeat steps within the opposite manner.
Declaration of IAX2 User: A peer will receive calls, to identification of user before calls
are allowed.
[username] type=user
auth=md5
secret=secretword
context=iax2users
The setup will allow remote users to register in system from host.
Declaration of IAX2 Peer: The user will make calls, it will be required within iax.conf
on the machine of user for identification of peer for taking call (Connecting two Asterisk servers,
2020).
[peername] type=peer
host=hostname.domain.tld
7
for sending voicemail (computer based system which permits subscribers as well as users for
exchanging voice messages) from extension to users mailboxes have been mentioned below:
relayhost =192.169.0.1
This aids Postfix within accepting relay (forward) email, the file “/etc/postfix/main.cf”
has to be edited. It has to be reloaded or restarted so that changes can occur
#service postfix restart
Now test the changes which have been made by sending email
#echo “This is test” | mail -s “Relay Test” ab@example.com
This will allow all voicemail from extension to forward to mailbox of users.
4. Configuration of IAX trunks for demonstration of connectivity among Asterisk servers.
Inter-Asterisk eXchange is interaction protocol which is native to Asterisk PBX and is
also supported by softphones, PBX systems and softswitches. It is utilised for transportation of
VoIP telephony sessions among servers to terminal devices (Stallings, 2016). The steps
illustrated in this are:
Configure Asterisk servers within both ends in iax.conf, one is user and other is peer.
Set up dialplan for users in extensions.conf by which can be made from user to peer.
Register peer with user and repeat steps within the opposite manner.
Declaration of IAX2 User: A peer will receive calls, to identification of user before calls
are allowed.
[username] type=user
auth=md5
secret=secretword
context=iax2users
The setup will allow remote users to register in system from host.
Declaration of IAX2 Peer: The user will make calls, it will be required within iax.conf
on the machine of user for identification of peer for taking call (Connecting two Asterisk servers,
2020).
[peername] type=peer
host=hostname.domain.tld
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

auth=md5
secret=secretword
username=username-at-the-peer
Block B: Secured operations as well as service delivery
5. Illustrate 3 attacks against VoIP system and one attack must illustrate pivoting against mailbox
of users.
They are illustrated below: Denial of service attack: This possess great threat to VoIP system of organisation. They
are intended for slowing down voice network for peculiar frame of time as DOS will
overwhelm system. With respect to this hackers might opt for infecting system with
viruses and worms for preventing VoIP service from getting accessed. Vishing: This is other emerging VoIP threat in which voice phising is done; it takes place
when malicious actor redirect legitimate calls from VoIP network instead of connecting
them with online predators (Stute and Paly, Masergy Communications Inc, 2018). From
perspective of employees call might seem legitimate through which users are convinced
for rendering credit card or any other information.
SPIT: It is variant of email spam which is being taken as social threat and comprises of
generation of unsolicited interaction like unsolicited advertisements and unwanted calls
that are being utilised to perturb users and also involves telemarketing calls which
influences users within sales of product. This creates an impact on cost and bandwidth.
6. Designing as well as implementation of comprehensive security policies for VoIP system
along with relevant security controls.
Certain policies have been formulated with respect to each attack and the ways in which they
can be handled in context of VoIP. They are illustrated below:
Denial of service: To deal with this, security audit must be carried out before VoIP is
being added. For handling these threats, security audit is to be carried out for network
before VoIP is added (Vaidya and et. al., 2018). Along with this, identify third-party
applications, insecure endpoints as well as physical devices which serve as jumping-off
points to attackers. Along with this legacy apps can also be assessed and identify if
security needs with respect to internet-based telephony are handled or not. For this
8
secret=secretword
username=username-at-the-peer
Block B: Secured operations as well as service delivery
5. Illustrate 3 attacks against VoIP system and one attack must illustrate pivoting against mailbox
of users.
They are illustrated below: Denial of service attack: This possess great threat to VoIP system of organisation. They
are intended for slowing down voice network for peculiar frame of time as DOS will
overwhelm system. With respect to this hackers might opt for infecting system with
viruses and worms for preventing VoIP service from getting accessed. Vishing: This is other emerging VoIP threat in which voice phising is done; it takes place
when malicious actor redirect legitimate calls from VoIP network instead of connecting
them with online predators (Stute and Paly, Masergy Communications Inc, 2018). From
perspective of employees call might seem legitimate through which users are convinced
for rendering credit card or any other information.
SPIT: It is variant of email spam which is being taken as social threat and comprises of
generation of unsolicited interaction like unsolicited advertisements and unwanted calls
that are being utilised to perturb users and also involves telemarketing calls which
influences users within sales of product. This creates an impact on cost and bandwidth.
6. Designing as well as implementation of comprehensive security policies for VoIP system
along with relevant security controls.
Certain policies have been formulated with respect to each attack and the ways in which they
can be handled in context of VoIP. They are illustrated below:
Denial of service: To deal with this, security audit must be carried out before VoIP is
being added. For handling these threats, security audit is to be carried out for network
before VoIP is added (Vaidya and et. al., 2018). Along with this, identify third-party
applications, insecure endpoints as well as physical devices which serve as jumping-off
points to attackers. Along with this legacy apps can also be assessed and identify if
security needs with respect to internet-based telephony are handled or not. For this
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

firewall can be installed and network protection protocols must be analysed as well as if
any changes are required then they must be followed.
Vishing: It is important that knowledge with respect to this attack is being possessed by
each individual but still if they do not have then also it is advisable the links given in
websites must not be clicked on and if it seems authenticated then they must be entered
manually by typing. Along with this, any kind of information related with them must not
be given on calls (Vanerio and Casas, 2017).
SPIT: For dealing with this, dedicated internet connection can be installed which will
allow to monitor entire traffic.
Apart from this, some other policies in this context have been shown beneath:
Confidentiality of data must be maintained through mandatory and discretionary
access controls.
No external service or internet access must be allowed from or to IP telephony data
centre and there must be calling restrictions which are executed globally on different
call-control clusters (Bentall Airbus DS Ltd, 2019).
7. Implementation of comprehensive NIDS as well as test their efficiency with respect to
deployment.
The devices which are intelligently distributed across network that passively inspect
traversing of traffic devices on which they rely is referred to as network-based intrusion
detection system. Implementation of NIDS comprises of two steps, they are illustrated below:
Step 1: This involves installation of antivirus internet security within the central server. It
has in-built intrusion detection system along with database alert rules which are being
updated in an automatic manner via official website. Here, all the systems connected in
network operate like a client as well as retrieve updates from server that involves
intrusion detection signature.
9
any changes are required then they must be followed.
Vishing: It is important that knowledge with respect to this attack is being possessed by
each individual but still if they do not have then also it is advisable the links given in
websites must not be clicked on and if it seems authenticated then they must be entered
manually by typing. Along with this, any kind of information related with them must not
be given on calls (Vanerio and Casas, 2017).
SPIT: For dealing with this, dedicated internet connection can be installed which will
allow to monitor entire traffic.
Apart from this, some other policies in this context have been shown beneath:
Confidentiality of data must be maintained through mandatory and discretionary
access controls.
No external service or internet access must be allowed from or to IP telephony data
centre and there must be calling restrictions which are executed globally on different
call-control clusters (Bentall Airbus DS Ltd, 2019).
7. Implementation of comprehensive NIDS as well as test their efficiency with respect to
deployment.
The devices which are intelligently distributed across network that passively inspect
traversing of traffic devices on which they rely is referred to as network-based intrusion
detection system. Implementation of NIDS comprises of two steps, they are illustrated below:
Step 1: This involves installation of antivirus internet security within the central server. It
has in-built intrusion detection system along with database alert rules which are being
updated in an automatic manner via official website. Here, all the systems connected in
network operate like a client as well as retrieve updates from server that involves
intrusion detection signature.
9
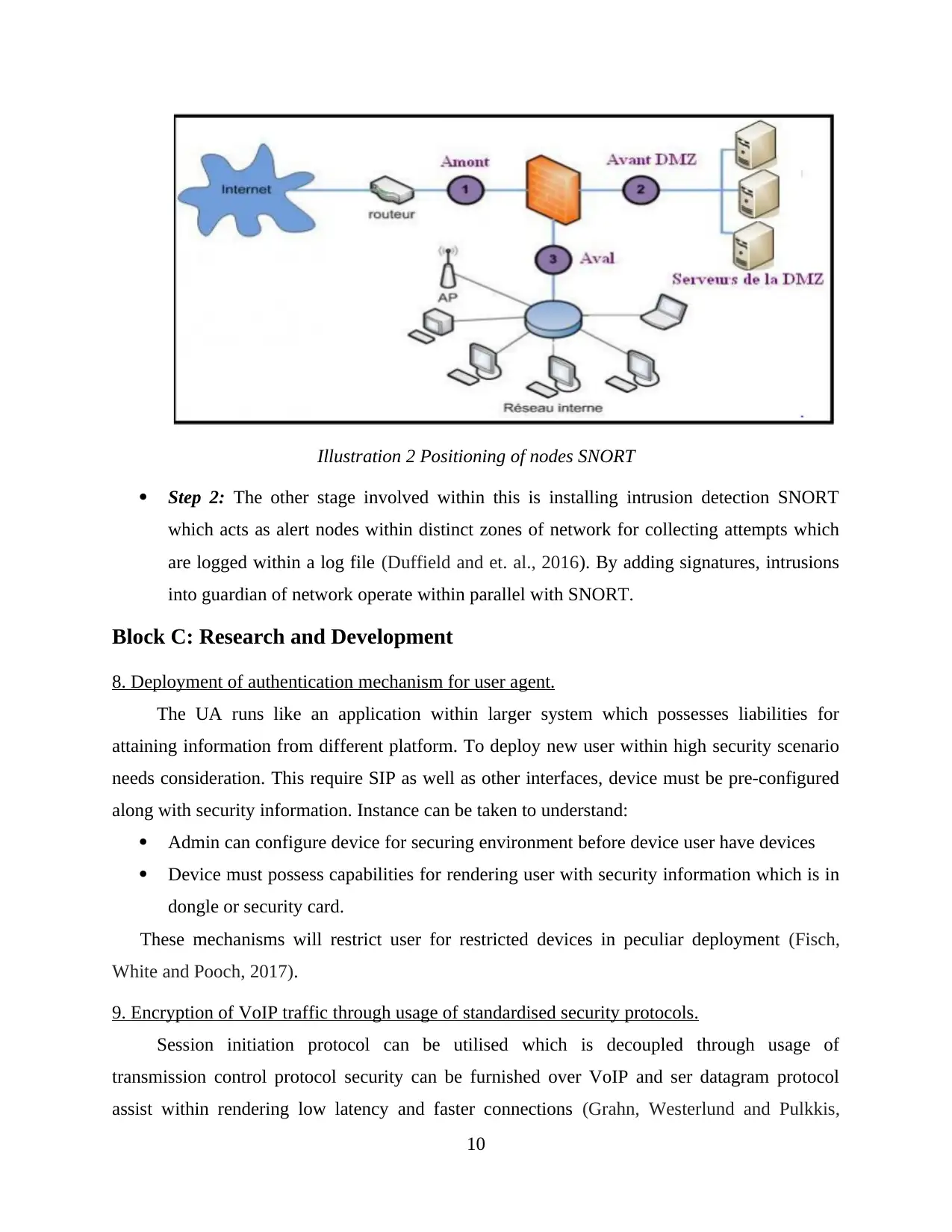
Illustration 2 Positioning of nodes SNORT
Step 2: The other stage involved within this is installing intrusion detection SNORT
which acts as alert nodes within distinct zones of network for collecting attempts which
are logged within a log file (Duffield and et. al., 2016). By adding signatures, intrusions
into guardian of network operate within parallel with SNORT.
Block C: Research and Development
8. Deployment of authentication mechanism for user agent.
The UA runs like an application within larger system which possesses liabilities for
attaining information from different platform. To deploy new user within high security scenario
needs consideration. This require SIP as well as other interfaces, device must be pre-configured
along with security information. Instance can be taken to understand:
Admin can configure device for securing environment before device user have devices
Device must possess capabilities for rendering user with security information which is in
dongle or security card.
These mechanisms will restrict user for restricted devices in peculiar deployment (Fisch,
White and Pooch, 2017).
9. Encryption of VoIP traffic through usage of standardised security protocols.
Session initiation protocol can be utilised which is decoupled through usage of
transmission control protocol security can be furnished over VoIP and ser datagram protocol
assist within rendering low latency and faster connections (Grahn, Westerlund and Pulkkis,
10
Step 2: The other stage involved within this is installing intrusion detection SNORT
which acts as alert nodes within distinct zones of network for collecting attempts which
are logged within a log file (Duffield and et. al., 2016). By adding signatures, intrusions
into guardian of network operate within parallel with SNORT.
Block C: Research and Development
8. Deployment of authentication mechanism for user agent.
The UA runs like an application within larger system which possesses liabilities for
attaining information from different platform. To deploy new user within high security scenario
needs consideration. This require SIP as well as other interfaces, device must be pre-configured
along with security information. Instance can be taken to understand:
Admin can configure device for securing environment before device user have devices
Device must possess capabilities for rendering user with security information which is in
dongle or security card.
These mechanisms will restrict user for restricted devices in peculiar deployment (Fisch,
White and Pooch, 2017).
9. Encryption of VoIP traffic through usage of standardised security protocols.
Session initiation protocol can be utilised which is decoupled through usage of
transmission control protocol security can be furnished over VoIP and ser datagram protocol
assist within rendering low latency and faster connections (Grahn, Westerlund and Pulkkis,
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


