BN305 - VPN Network Design for SME Networks and VPN Services Report
VerifiedAdded on 2023/06/04
|15
|1015
|292
Report
AI Summary
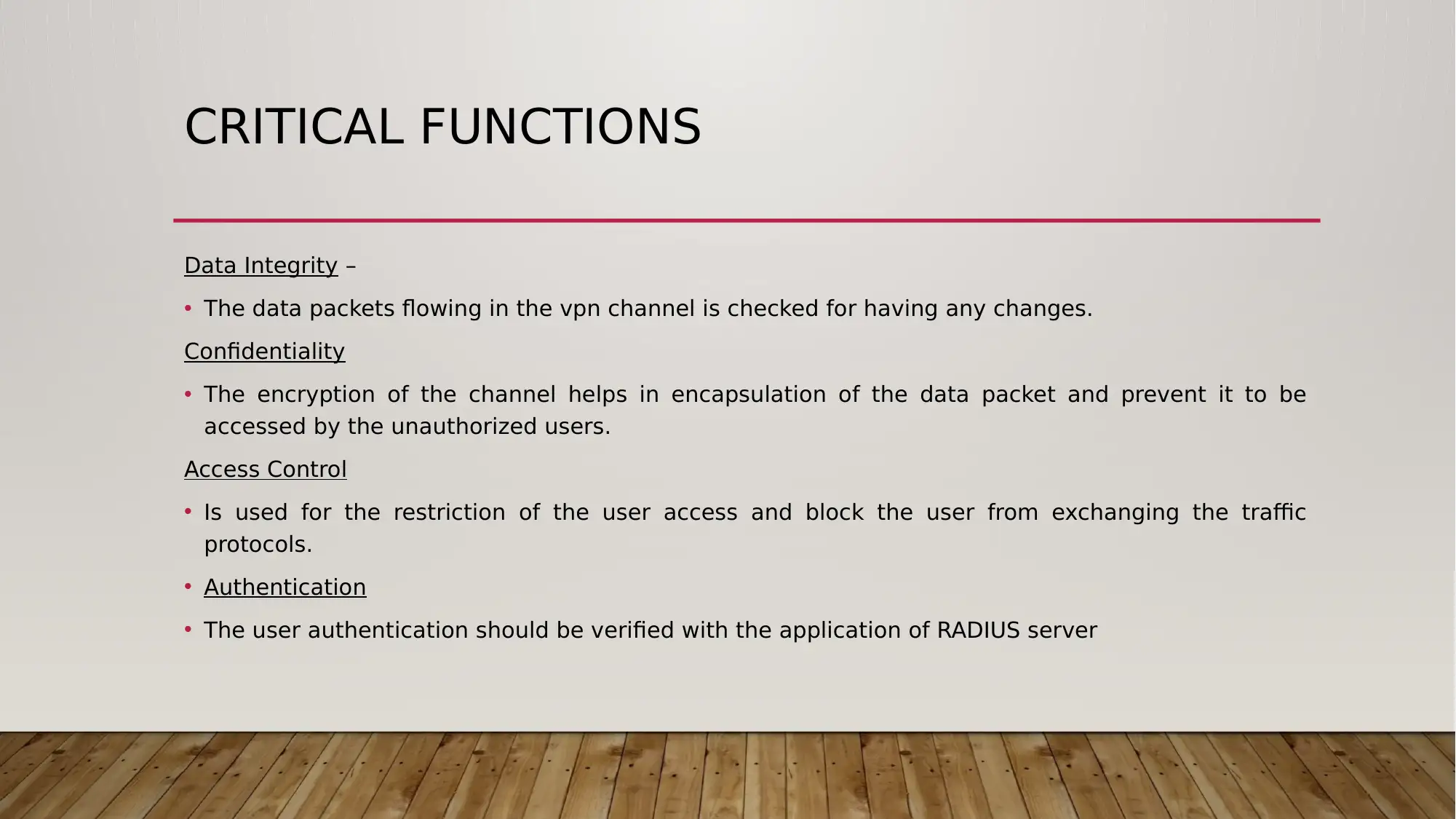
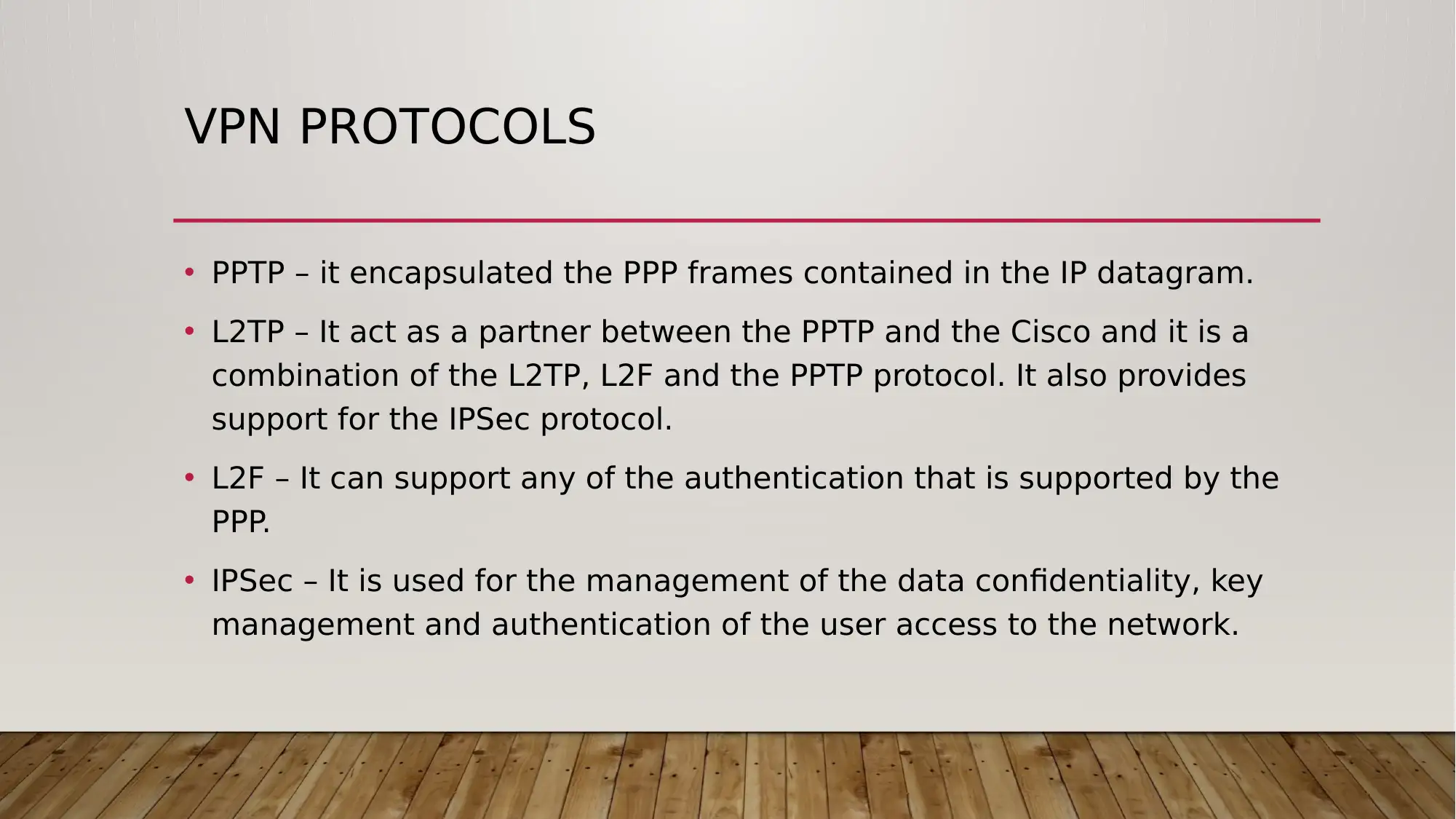
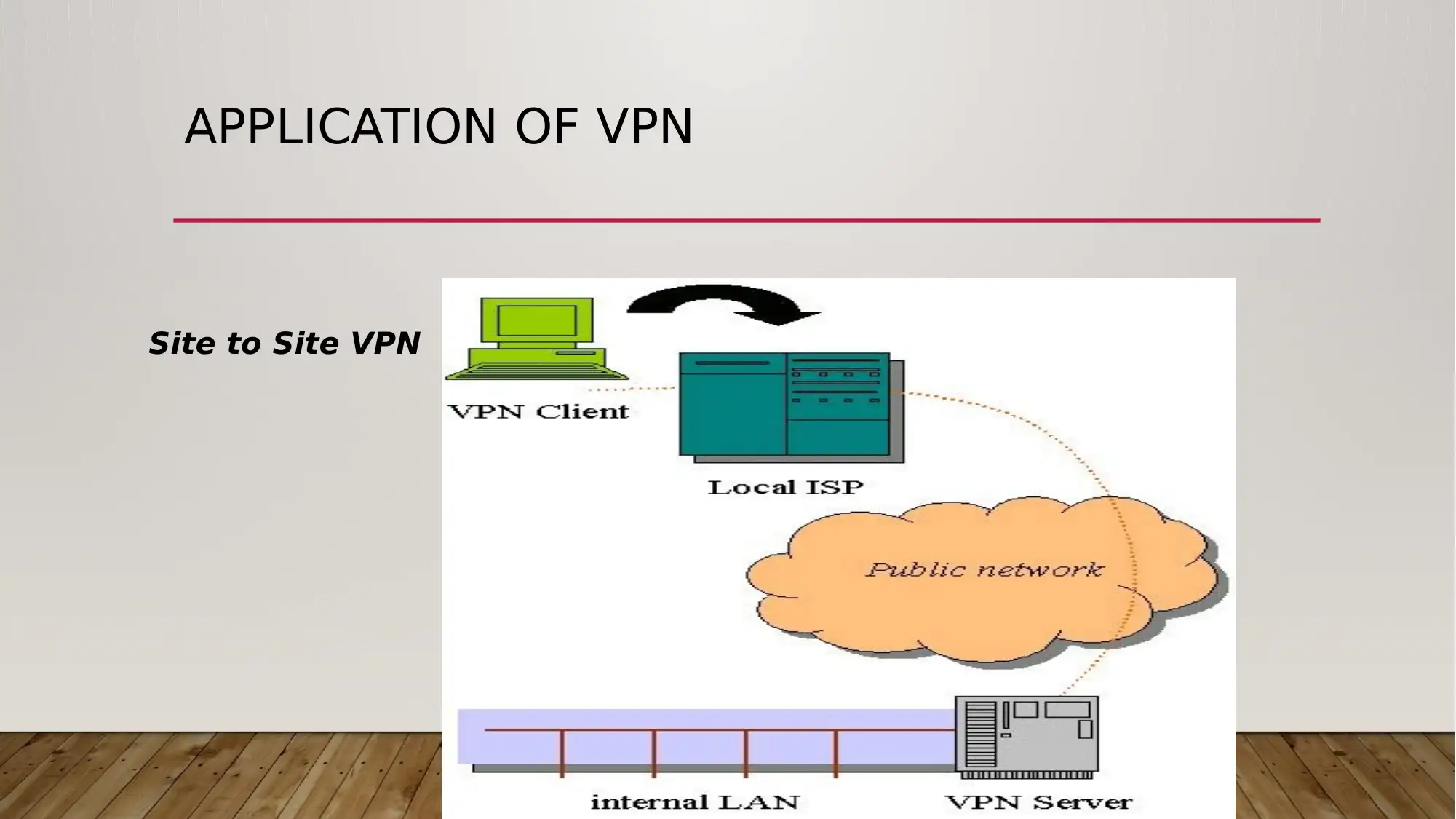
This report outlines a VPN network design tailored for Small and Medium Enterprises (SMEs), focusing on VPN services and security considerations. It defines VPNs, explains their functionality, and highlights benefits such as cost reduction and enhanced security. The report details critical functions like data integrity, confidentiality, access control, and authentication, emphasizing the importance of robust security measures. It also discusses tunneling, VPN protocols including PPTP, L2TP, L2F, and IPSec, and various VPN implementation scenarios such as intranet, remote access, extranet, and site-to-site connections. The report acknowledges the disadvantages of using public networks and the need for careful management. Applications of VPNs across different industries like manufacturing, retail, healthcare, and finance are explored, along with a bibliography referencing key sources. Desklib provides access to this report and other valuable study resources.
1 out of 15














![[object Object]](/_next/static/media/star-bottom.7253800d.svg)