VPN Implementation: Secure Remote Access for JKS Accountants Network
VerifiedAdded on 2023/06/16
|13
|384
|69
Presentation
AI Summary
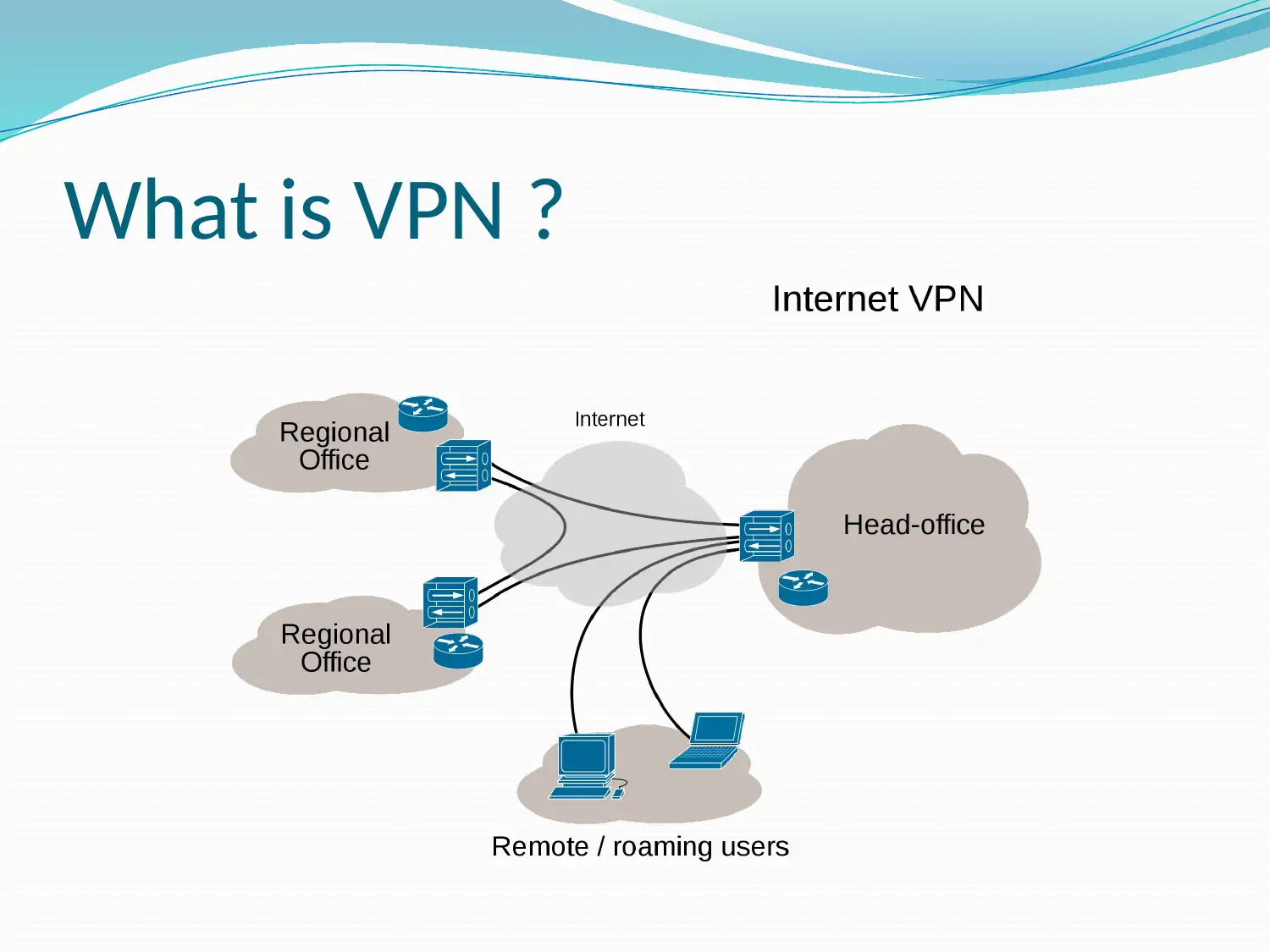
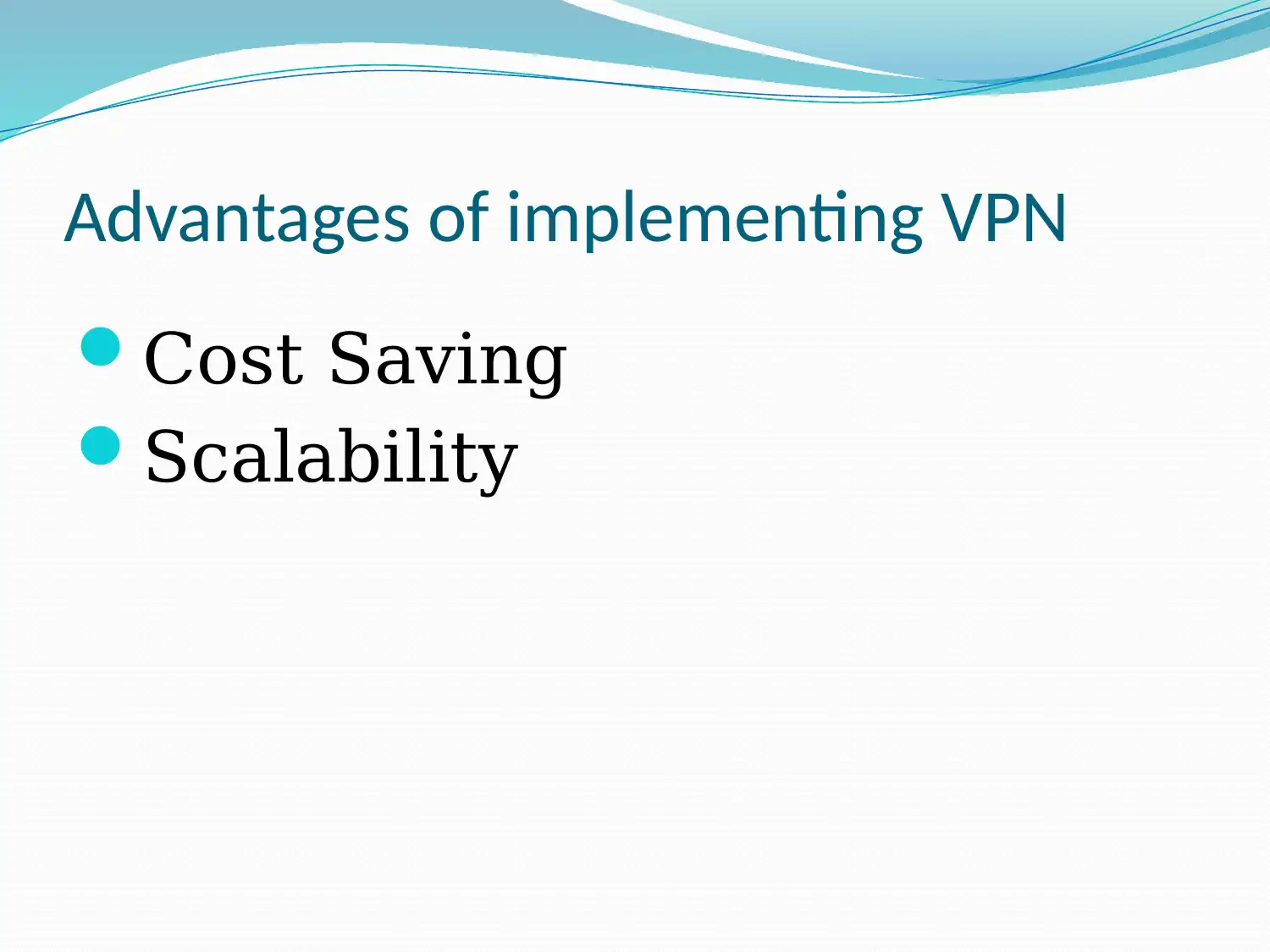
This presentation addresses the Managing Partner of JKS Accountants' need to evolve their corporate network for remote access while maintaining data confidentiality. It defines a Virtual Private Network (VPN), explains how it enables secure remote access, and outlines critical functions like authentication, access control, confidentiality, and data integrity. The presentation identifies risks associated with remote access without a VPN, such as data theft and external intrusion, and highlights the advantages of implementing a VPN, including cost savings and scalability. It concludes that VPN usage would be highly beneficial for JKS Accountants. Desklib provides students with access to this and many other solved assignments.
1 out of 13















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)