JKS Accountants: VPN Implementation and Alternate Security Measures
VerifiedAdded on 2023/06/16
|13
|1078
|392
Presentation
AI Summary
This presentation examines the application of Virtual Private Networks (VPNs) to enhance the security of JKS Accountants, a developing accounting firm in Sydney, Australia. It defines VPNs and analyzes the security risks the organization faces without them. The presentation highlights the advantages of incorporating VPNs, such as enhanced security and identity protection through fake IP addresses and high-quality encryption. It also suggests alternate security measures like cloud storage services, Hadoop, firewalls, and antivirus software to further protect sensitive client data and maintain a healthy system. The conclusion emphasizes the importance of these measures for companies like JKS Accounting that allow remote work, ensuring the protection of important data and enhanced network security.

APPLICATION OF VPN
TO JKS ACCOUNTANT
TO JKS ACCOUNTANT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
INTRODUCTION
This power point presentation is made based on the research conducted on the
organisation of JKS Accountants, which is a developing accounting firm in Sydney, Australia.
The objective of the presentation is to define Virtual Private Network (VPN); to analyse the
problems that is associated to the organisation in terms security that may arise without the use
of VPN and the advantages of application of VPN to the same. The situation of the company is
diagnosed thoroughly and suggestions are given related to the incorporation of other security
components to the system of the company that will enhance the security of the same.
INTRODUCTION
This power point presentation is made based on the research conducted on the
organisation of JKS Accountants, which is a developing accounting firm in Sydney, Australia.
The objective of the presentation is to define Virtual Private Network (VPN); to analyse the
problems that is associated to the organisation in terms security that may arise without the use
of VPN and the advantages of application of VPN to the same. The situation of the company is
diagnosed thoroughly and suggestions are given related to the incorporation of other security
components to the system of the company that will enhance the security of the same.

3
VIRTUAL PRIVATE NETWORK – WHAT IS IT ?
A Virtual Private Network or VPN is a service that is used to provide enhanced security
and identity protection to public and private networks, such as the Internet or Wi-Fi hotspots.
The user’s privacy is protected by a fake IP address that masks the original IP address and its
location. This will show the user location to any other gateway city rather than show the
original location. The incoming and outgoing data in a VPN network is protected with high
quality encryption. The service of VPN is very cost friendly and hence is availed by most
large scale enterprise. VPN
VIRTUAL PRIVATE NETWORK – WHAT IS IT ?
A Virtual Private Network or VPN is a service that is used to provide enhanced security
and identity protection to public and private networks, such as the Internet or Wi-Fi hotspots.
The user’s privacy is protected by a fake IP address that masks the original IP address and its
location. This will show the user location to any other gateway city rather than show the
original location. The incoming and outgoing data in a VPN network is protected with high
quality encryption. The service of VPN is very cost friendly and hence is availed by most
large scale enterprise. VPN
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4
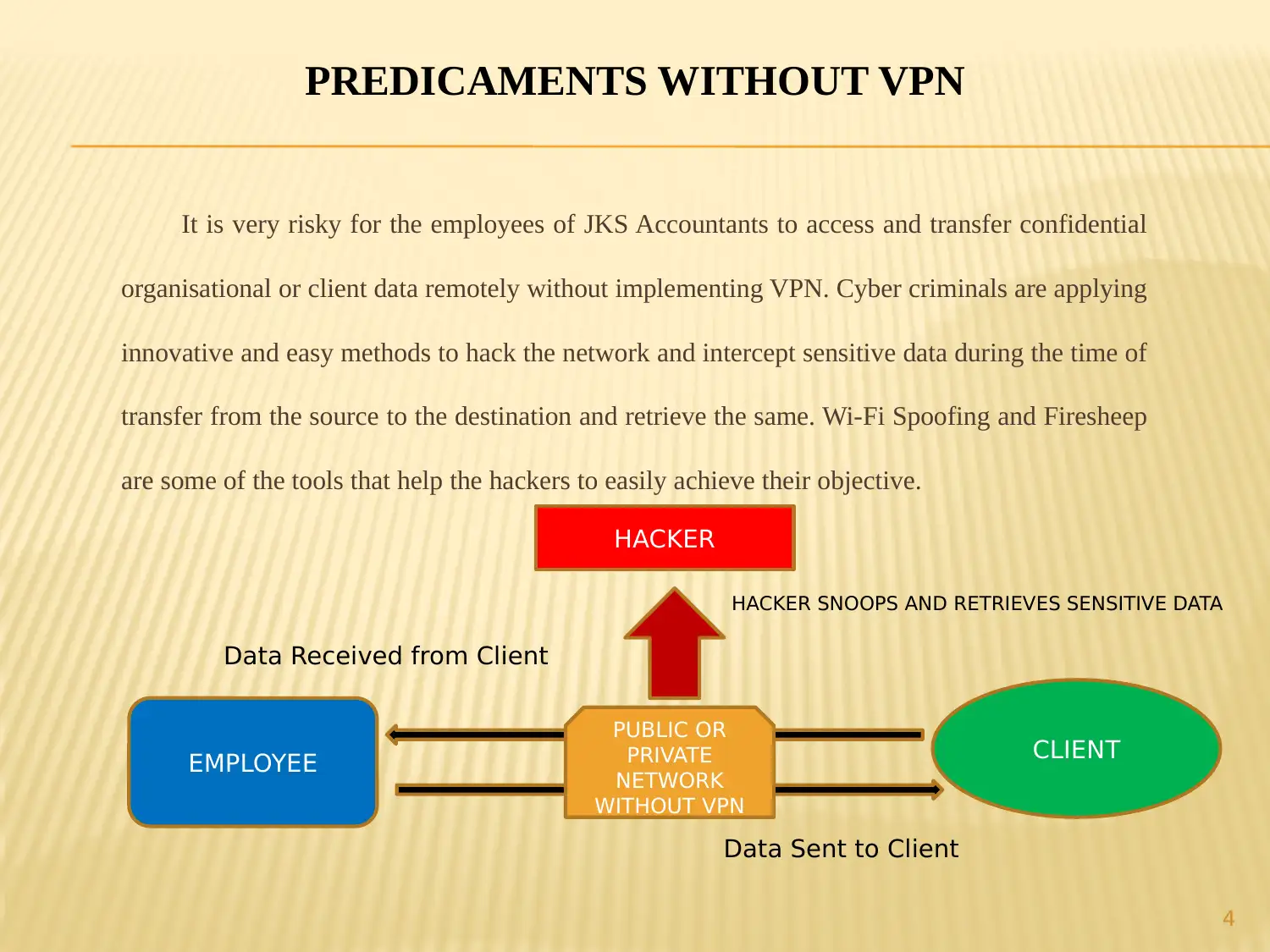
PREDICAMENTS WITHOUT VPN
It is very risky for the employees of JKS Accountants to access and transfer confidential
organisational or client data remotely without implementing VPN. Cyber criminals are applying
innovative and easy methods to hack the network and intercept sensitive data during the time of
transfer from the source to the destination and retrieve the same. Wi-Fi Spoofing and Firesheep
are some of the tools that help the hackers to easily achieve their objective.
EMPLOYEE
PUBLIC OR
PRIVATE
NETWORK
WITHOUT VPN
CLIENT
Data Received from Client
Data Sent to Client
HACKER
HACKER SNOOPS AND RETRIEVES SENSITIVE DATA
PREDICAMENTS WITHOUT VPN
It is very risky for the employees of JKS Accountants to access and transfer confidential
organisational or client data remotely without implementing VPN. Cyber criminals are applying
innovative and easy methods to hack the network and intercept sensitive data during the time of
transfer from the source to the destination and retrieve the same. Wi-Fi Spoofing and Firesheep
are some of the tools that help the hackers to easily achieve their objective.
EMPLOYEE
PUBLIC OR
PRIVATE
NETWORK
WITHOUT VPN
CLIENT
Data Received from Client
Data Sent to Client
HACKER
HACKER SNOOPS AND RETRIEVES SENSITIVE DATA
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5
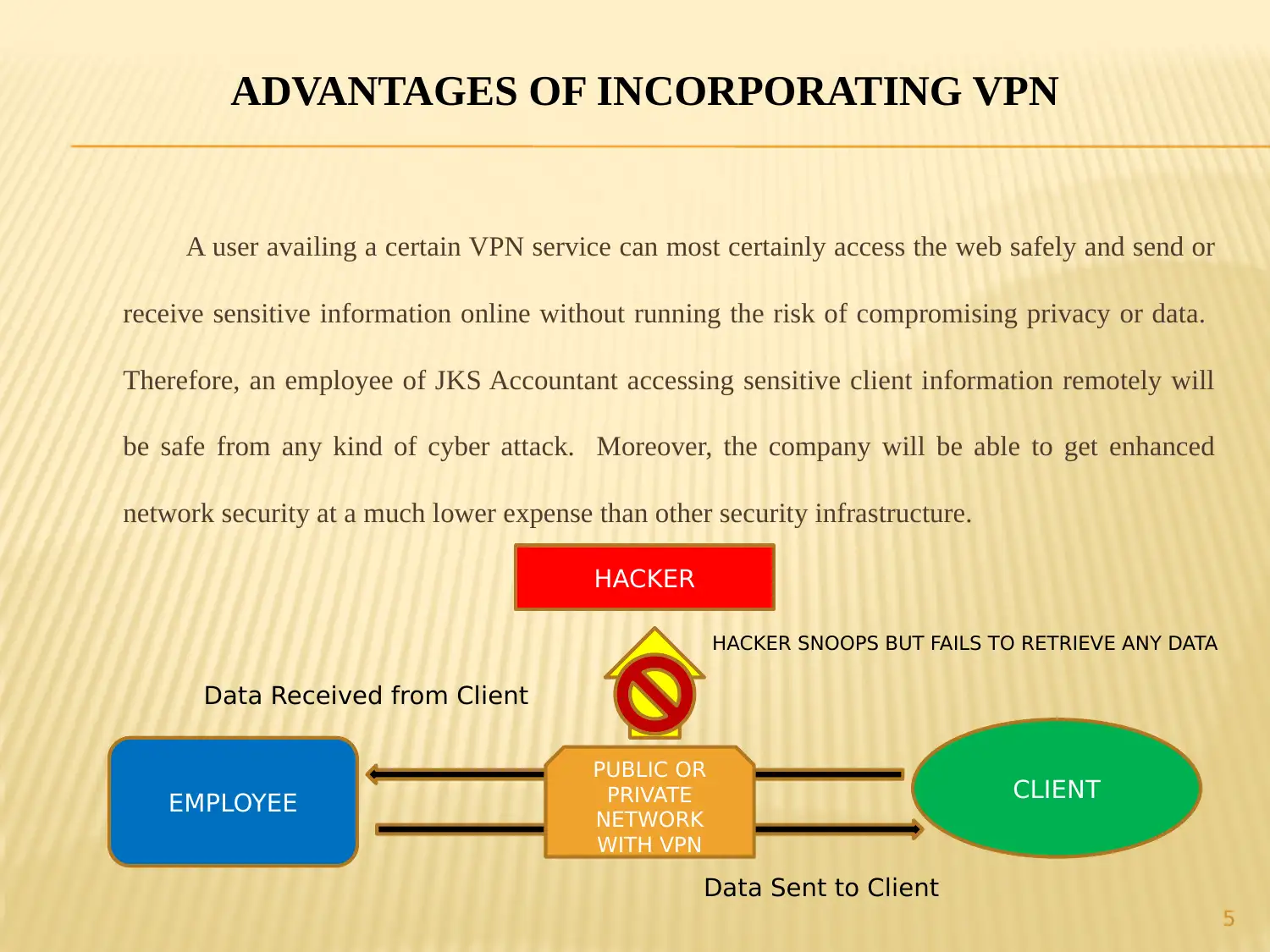
ADVANTAGES OF INCORPORATING VPN
A user availing a certain VPN service can most certainly access the web safely and send or
receive sensitive information online without running the risk of compromising privacy or data.
Therefore, an employee of JKS Accountant accessing sensitive client information remotely will
be safe from any kind of cyber attack. Moreover, the company will be able to get enhanced
network security at a much lower expense than other security infrastructure.
HACKER SNOOPS BUT FAILS TO RETRIEVE ANY DATA
EMPLOYEE
PUBLIC OR
PRIVATE
NETWORK
WITH VPN
CLIENT
Data Received from Client
Data Sent to Client
HACKER
ADVANTAGES OF INCORPORATING VPN
A user availing a certain VPN service can most certainly access the web safely and send or
receive sensitive information online without running the risk of compromising privacy or data.
Therefore, an employee of JKS Accountant accessing sensitive client information remotely will
be safe from any kind of cyber attack. Moreover, the company will be able to get enhanced
network security at a much lower expense than other security infrastructure.
HACKER SNOOPS BUT FAILS TO RETRIEVE ANY DATA
EMPLOYEE
PUBLIC OR
PRIVATE
NETWORK
WITH VPN
CLIENT
Data Received from Client
Data Sent to Client
HACKER
6
ALTERNATE SECURITY MEASURES
There are some other software components of corporate network that can be applied to an
JKS Accountant, like:
Cloud Storage Service.
Hadoop.
Firewall.
Antivirus.
ALTERNATE SECURITY MEASURES
There are some other software components of corporate network that can be applied to an
JKS Accountant, like:
Cloud Storage Service.
Hadoop.
Firewall.
Antivirus.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
CLOUD STORAGE SERVICES
Cloud Storage is a service which stores data in multiple servers that are situated in
multiple physical locations in the world. The use of a cloud storage service minimises the risk
of data loss or theft that can occur due to non-human or human activities. This is because cloud
storage is protected with latest security softwares and the network through which the data is
transferred is monitored with latest monitoring tool for any suspicious activities. The data are
encrypted with sophisticated encryption tool as well. It is a cost friendly service. Companies
like JKS Accountant will boost their security measures by using such a service.
CLOUD STORAGE SERVICES
Cloud Storage is a service which stores data in multiple servers that are situated in
multiple physical locations in the world. The use of a cloud storage service minimises the risk
of data loss or theft that can occur due to non-human or human activities. This is because cloud
storage is protected with latest security softwares and the network through which the data is
transferred is monitored with latest monitoring tool for any suspicious activities. The data are
encrypted with sophisticated encryption tool as well. It is a cost friendly service. Companies
like JKS Accountant will boost their security measures by using such a service.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
HADOOP
Hadoop is an open source framework, programmed in java platform that helps in the
processing and storage of large quantity of information in a distributed computing
environment. Hadoop also allows use of a system without any constraints even if multiple
nodes fail. This helps in minimising damage of data in the data centres. JKS Accountants will
find a lot of utility by implementing Hadoop to their system.
HADOO
P
HADOOP
Hadoop is an open source framework, programmed in java platform that helps in the
processing and storage of large quantity of information in a distributed computing
environment. Hadoop also allows use of a system without any constraints even if multiple
nodes fail. This helps in minimising damage of data in the data centres. JKS Accountants will
find a lot of utility by implementing Hadoop to their system.
HADOO
P

9
FIREWALL
A firewall is a software or a hardware component that prohibits the entry of any
malicious content and hackers to a system through internet and cause harm to the system or
the confidential data stored in the system. The implementation of firewall to the network
of JKS Accountant organisation will ensure the protection of data that is stored in the
systems as well as maintain a healthy system.
FIREWALL
A firewall is a software or a hardware component that prohibits the entry of any
malicious content and hackers to a system through internet and cause harm to the system or
the confidential data stored in the system. The implementation of firewall to the network
of JKS Accountant organisation will ensure the protection of data that is stored in the
systems as well as maintain a healthy system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
10
ANTIVIRUS
Antivirus is a program or software that diagnose and eradicates any harmful content such as spyware,
adware, malware and such that is present in a system and protects the system from future infections. Use
of such software will protect the systems used by the employees of JKS Accountant from any viral attack.
ANTIVIRUS
Antivirus is a program or software that diagnose and eradicates any harmful content such as spyware,
adware, malware and such that is present in a system and protects the system from future infections. Use
of such software will protect the systems used by the employees of JKS Accountant from any viral attack.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11
CONCLUSION
Therefore, it can be concluded that for a company like JKS
Accounting, who plans to make its employees work even from remote
locations, certain steps are required to be taken to determine protection
of important data that are being processed while working remotely. It is
understood that services like the VPN, Cloud Storage, Hadoop,
Firewall and Antivirus, if incorporated effectively within the enterprise
will aid in achieving an enhanced quality of network security.
CONCLUSION
Therefore, it can be concluded that for a company like JKS
Accounting, who plans to make its employees work even from remote
locations, certain steps are required to be taken to determine protection
of important data that are being processed while working remotely. It is
understood that services like the VPN, Cloud Storage, Hadoop,
Firewall and Antivirus, if incorporated effectively within the enterprise
will aid in achieving an enhanced quality of network security.

12
REFERENCES
Jain, R., & Paul, S. (2013). Network virtualization and software defined
networking for cloud computing: a survey. IEEE Communications
Magazine, 51(11), 24-31.
Amin, S., Schwartz, G. A., & Hussain, A. (2013). In quest of benchmarking
security risks to cyber-physical systems. IEEE Network, 27(1), 19-24.
Ryan, J. J., Mazzuchi, T. A., Ryan, D. J., De la Cruz, J. L., & Cooke, R.
(2012). Quantifying information security risks using expert judgment
elicitation. Computers & Operations Research, 39(4), 774-784.
Wang, C., Wang, Q., Ren, K., Cao, N., & Lou, W. (2012). Toward secure
and dependable storage services in cloud computing. IEEE transactions
on Services Computing, 5(2), 220-232.
White, T. (2012). Hadoop: The definitive guide. " O'Reilly Media, Inc.".
REFERENCES
Jain, R., & Paul, S. (2013). Network virtualization and software defined
networking for cloud computing: a survey. IEEE Communications
Magazine, 51(11), 24-31.
Amin, S., Schwartz, G. A., & Hussain, A. (2013). In quest of benchmarking
security risks to cyber-physical systems. IEEE Network, 27(1), 19-24.
Ryan, J. J., Mazzuchi, T. A., Ryan, D. J., De la Cruz, J. L., & Cooke, R.
(2012). Quantifying information security risks using expert judgment
elicitation. Computers & Operations Research, 39(4), 774-784.
Wang, C., Wang, Q., Ren, K., Cao, N., & Lou, W. (2012). Toward secure
and dependable storage services in cloud computing. IEEE transactions
on Services Computing, 5(2), 220-232.
White, T. (2012). Hadoop: The definitive guide. " O'Reilly Media, Inc.".
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





