Virtual Private Network: Implementation, Security, and Threats
VerifiedAdded on 2024/04/26
|11
|617
|156
Presentation
AI Summary
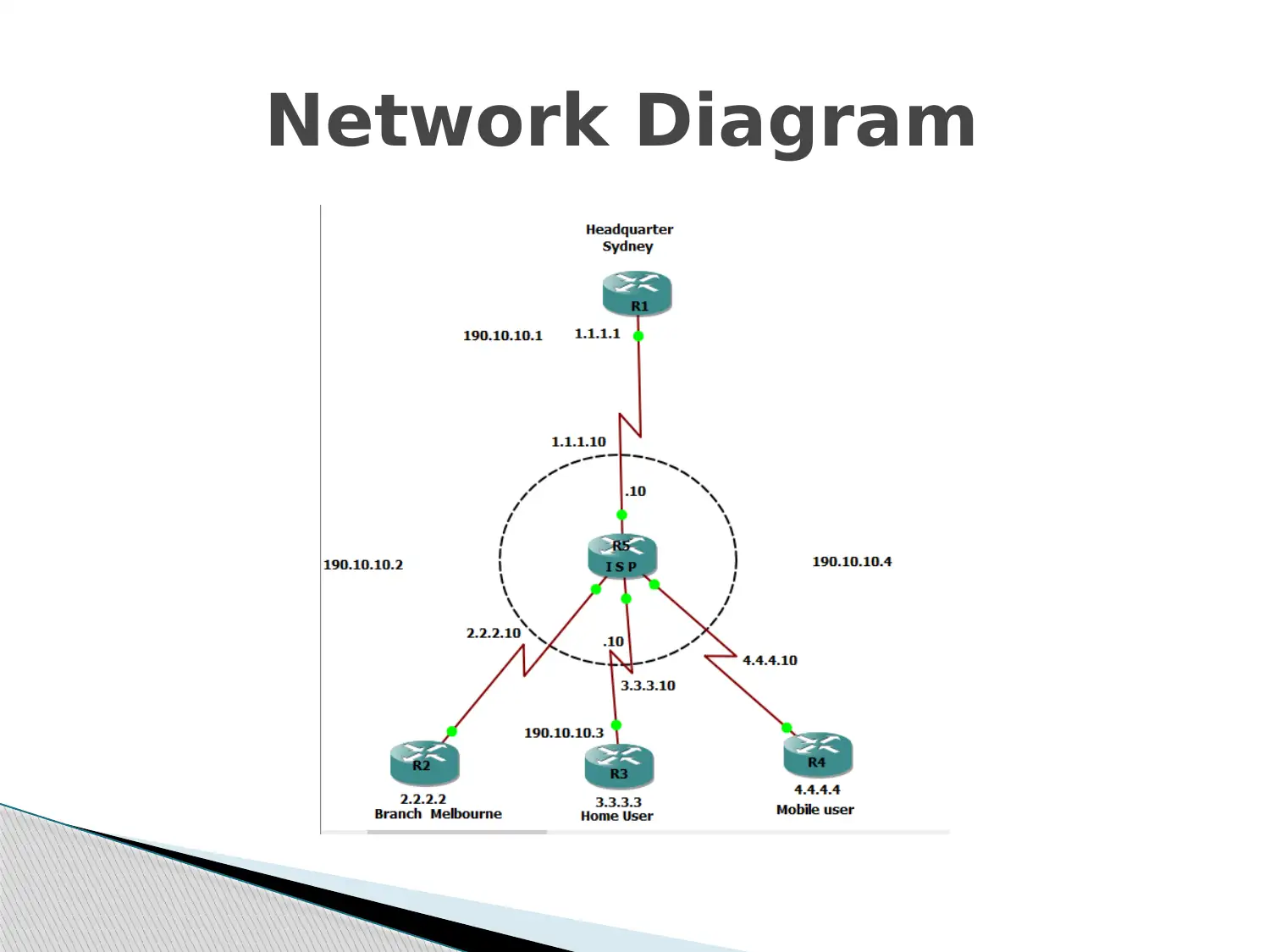
This presentation provides an overview of Virtual Private Networks (VPNs), emphasizing their role in establishing secure connections for users, particularly within local area networks. It details the IP infrastructure requirements, including LAN connections, BYOD policies, and the use of servers like mail, web, and DNS. A network diagram illustrates a setup with four routers connected via tunneling over an ISP internet, ensuring secure data packet transmission between the main branch and headquarters. Security mechanisms such as IPSec and SSL are discussed to safeguard user information from network vulnerabilities, alongside potential threats like denial of service and intrusion. The presentation also covers encryption techniques like AES and MD5 used to maintain data security. It concludes by highlighting the successful implementation of VPN for Avita’s corporate network and referencing key sources for further information, available on Desklib.
1 out of 11












![[object Object]](/_next/static/media/star-bottom.7253800d.svg)