Secure Remote Access: VPN Solutions for JKS Accounting Data Protection
VerifiedAdded on 2023/05/23
|8
|898
|465
Report
AI Summary
This report emphasizes the critical role of Virtual Private Networks (VPNs) in securing remote access to client data for JKS Accounting. It explains that a VPN establishes an encrypted connection over the internet, protecting data from potential eavesdropping. The report highlights the benefits of VPNs, including cost reduction and network versatility, and suggests complementary security measures like wireless access point encryption and hiding the SSID. By not using a VPN, JKS Accounting risks exposing sensitive information to unauthorized parties. The report recommends that JKS Accounting implement VPNs along with other security components to ensure the confidentiality, integrity, and availability of its data.

Accounting Information
System
System
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table Of Contents
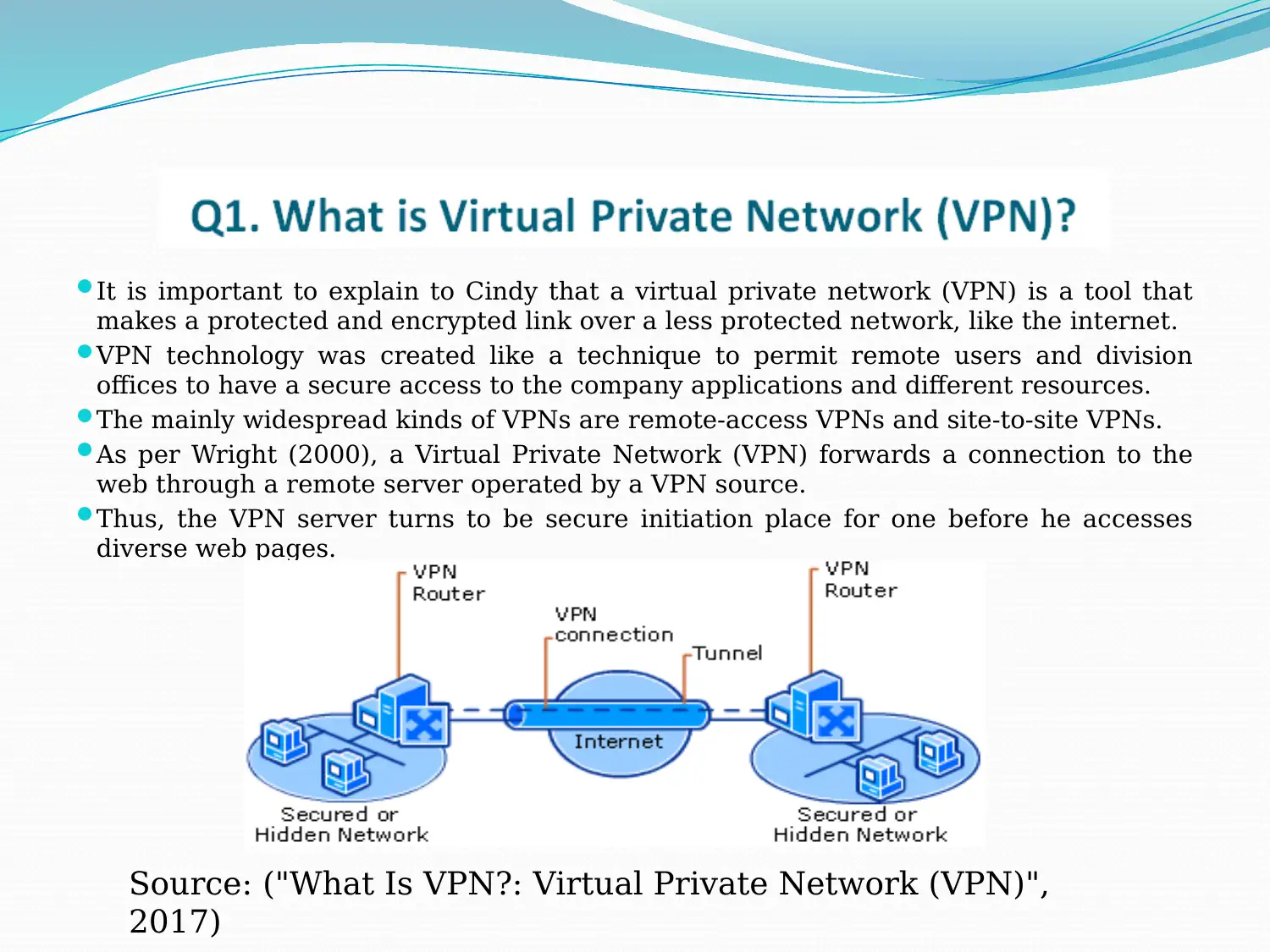
It is important to explain to Cindy that a virtual private network (VPN) is a tool that
makes a protected and encrypted link over a less protected network, like the internet.
VPN technology was created like a technique to permit remote users and division
offices to have a secure access to the company applications and different resources.
The mainly widespread kinds of VPNs are remote-access VPNs and site-to-site VPNs.
As per Wright (2000), a Virtual Private Network (VPN) forwards a connection to the
web through a remote server operated by a VPN source.
Thus, the VPN server turns to be secure initiation place for one before he accesses
diverse web pages.
Source: ("What Is VPN?: Virtual Private Network (VPN)",
2017)
makes a protected and encrypted link over a less protected network, like the internet.
VPN technology was created like a technique to permit remote users and division
offices to have a secure access to the company applications and different resources.
The mainly widespread kinds of VPNs are remote-access VPNs and site-to-site VPNs.
As per Wright (2000), a Virtual Private Network (VPN) forwards a connection to the
web through a remote server operated by a VPN source.
Thus, the VPN server turns to be secure initiation place for one before he accesses
diverse web pages.
Source: ("What Is VPN?: Virtual Private Network (VPN)",
2017)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

When any staff member of JKS Accounting remotely
accesses the client data and doesn’t use a VPN, then
any data passed on throughout the online session will
possibly be in danger of snooping by outsiders
utilising the same network.
The encryption and secrecy that a VPN gives,
defends the entire of online acts like posting emails,
online purchases, or payment of bills.
Moreover VPNs assist in maintain the anonymity of
Web browsing (Rowan, 2007).
By not using a VPN, JKS Accounting will be at risk of
losing the important details to outsiders.
accesses the client data and doesn’t use a VPN, then
any data passed on throughout the online session will
possibly be in danger of snooping by outsiders
utilising the same network.
The encryption and secrecy that a VPN gives,
defends the entire of online acts like posting emails,
online purchases, or payment of bills.
Moreover VPNs assist in maintain the anonymity of
Web browsing (Rowan, 2007).
By not using a VPN, JKS Accounting will be at risk of
losing the important details to outsiders.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
VPN is one way out for building up remote, long-distant and additionally
secured network links.
VPNs are typically carried out (applied) by firms instead of by those, yet
virtual networks can be accessed from within a home network.
In contrast with different advancements, VPNs provide with a few benefits,
especially advantages for wireless LANs.
For JKS Accounting which is hoping to give a protected network foundation to
its customer base, a VPN provides with two primary benefits over other
innovations: cost reductions, and network versatility.
To the customers who access these networks, VPNs fetch a few advantages of
effortlessness too (Perez, 2014).
A VPN is beneficial for the staffs working remotely as it can be a replacement
for remote access servers and long-distanced dial-up network links ordinarily
utilized historically by business explorers expecting to access to their
corporate intranet.
For instance, through an Internet VPN, customers require just link with the
closest service provider’s accessibility point that is normally local.
secured network links.
VPNs are typically carried out (applied) by firms instead of by those, yet
virtual networks can be accessed from within a home network.
In contrast with different advancements, VPNs provide with a few benefits,
especially advantages for wireless LANs.
For JKS Accounting which is hoping to give a protected network foundation to
its customer base, a VPN provides with two primary benefits over other
innovations: cost reductions, and network versatility.
To the customers who access these networks, VPNs fetch a few advantages of
effortlessness too (Perez, 2014).
A VPN is beneficial for the staffs working remotely as it can be a replacement
for remote access servers and long-distanced dial-up network links ordinarily
utilized historically by business explorers expecting to access to their
corporate intranet.
For instance, through an Internet VPN, customers require just link with the
closest service provider’s accessibility point that is normally local.
JKS Accounting can make use of other components along with VPN, like:
Utilization of encryption on the wireless access points (WAP). Lots of site reviews have
seen that 50% or a higher amount of all of the remote networks are entirely open, all set
for anyone to gather all the doings and maybe documentation of the elusive data by
placing in an adjoining vehicle. Some of the individuals are not serious with securing
MAC addresses, yet that illustrates signs of enhancement is utilizing WPA2 encryption.
WPA2 is observably improvisation of other encryption policies. There are a few encryption
tools for remote settings, like the WEP, (WPA-Personal), and WPA2 (Wi-Fi Protected
Access form 2). WEP is the foremost encryption and so minimum protected (i.e., it can be
successfully cracked, on the other hand is good with an far-reaching variety of gadgets
having more veteran utensils, yet WPA2 is the most protected however is just wonderful
with hardware created subsequent to 2006 (HAO, FENG & LAI, 2009).
JKS Accounting needs to conceal its SSID (services set identifier), or possibly is different
from its name to something customary. Every remote switch has to include cloud IDs
when they report to the world. Opposing to added to any genuine data that can make it
understandable who holds the switch or that can divulge the business name, for example,
"JKS Accounting Systems".
JKS Accounting ought to seldom test out the manufacturer’s site to confirm that its router
is operating the most up-to-date firmware.
Utilization of encryption on the wireless access points (WAP). Lots of site reviews have
seen that 50% or a higher amount of all of the remote networks are entirely open, all set
for anyone to gather all the doings and maybe documentation of the elusive data by
placing in an adjoining vehicle. Some of the individuals are not serious with securing
MAC addresses, yet that illustrates signs of enhancement is utilizing WPA2 encryption.
WPA2 is observably improvisation of other encryption policies. There are a few encryption
tools for remote settings, like the WEP, (WPA-Personal), and WPA2 (Wi-Fi Protected
Access form 2). WEP is the foremost encryption and so minimum protected (i.e., it can be
successfully cracked, on the other hand is good with an far-reaching variety of gadgets
having more veteran utensils, yet WPA2 is the most protected however is just wonderful
with hardware created subsequent to 2006 (HAO, FENG & LAI, 2009).
JKS Accounting needs to conceal its SSID (services set identifier), or possibly is different
from its name to something customary. Every remote switch has to include cloud IDs
when they report to the world. Opposing to added to any genuine data that can make it
understandable who holds the switch or that can divulge the business name, for example,
"JKS Accounting Systems".
JKS Accounting ought to seldom test out the manufacturer’s site to confirm that its router
is operating the most up-to-date firmware.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
HAO, Y., FENG, Y., & LAI, P. (2009). VPN identity
certification technology based on fingerprint
identification. Journal Of Computer Applications, 29(2),
350-352.
Perez, A. (2014). Network Security. London: ISTE.
Rowan, T. (2007). VPN technology: IPSEC vs SSL.
Network Security, 2007(12), 13-17.
What Is VPN?: Virtual Private Network (VPN). (2017).
Technet.microsoft.com. Retrieved 11 August 2017, from
https://technet.microsoft.com/en-us/library/cc739294(v=
ws.10).aspx
Wright, M. (2000). Virtual Private Network Security.
Network Security, 2000(7), 11-14.
HAO, Y., FENG, Y., & LAI, P. (2009). VPN identity
certification technology based on fingerprint
identification. Journal Of Computer Applications, 29(2),
350-352.
Perez, A. (2014). Network Security. London: ISTE.
Rowan, T. (2007). VPN technology: IPSEC vs SSL.
Network Security, 2007(12), 13-17.
What Is VPN?: Virtual Private Network (VPN). (2017).
Technet.microsoft.com. Retrieved 11 August 2017, from
https://technet.microsoft.com/en-us/library/cc739294(v=
ws.10).aspx
Wright, M. (2000). Virtual Private Network Security.
Network Security, 2000(7), 11-14.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

THE END
*********************
*********************
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





